Text
Ms Word 2013 Crack Download

High speed and overall performance and pinpoint precision in managing an up-to-date driver database on your pc are components provided by almost all normal driver scanners on the net, no matter what the brand. Making the best utilisation of your personal machine is dependent not just on OMRON USB Serial Converter Drivers, but additionally on a tremendous number of drivers that connect the devices and your devices. Utilizing a straight forward driver scanner application has developed into a common practice in the last three years or so. Omron usb drivers download.
Ms Powerpoint 2013 Crack
Ms Word 2013 Crack Free Download
Office Full Crack 2013
Aug 07, 2018 Microsoft Office 2013 Torrent + Crack. Microsoft Office 2013 Torrent is a free productive tool developed by Microsoft. It is released after fewer versions of MS Office, and it comes with new look and graphics of Windows 8 and Windows 8.1. It is said to be similar to previous suites but there enhanced new features in it. Download Microsoft Office 2013 Full Crack 64 Bit Microsoft Office 2013 free. download full Version is a set of office applications to process data, numbers, and information on your computer. As we all know, in this latest version there are major changes to the features of all applications in it, such as word, powerpoint, excel and others.
Welcome to my blogI've always loved cooking, baking, and cake decorating but couldn't afford to attend culinary schools. Free cake decorating tutorials.
August 20, 2015
Microsoft Office 2013 Product key Plus Crack full. free download
MS Office 2013 Product key:
Microsoft Office 2013 Product key is a Microsoft program which release with the new Features and awesome look. It is the best and simple program for office work. It’s very useful to workers to making reports and PPT files. In which you can make the daily legers accounts with the help of Excel sheet. This Microsoft Office 2015 is the latest version of the Microsoft Office program which specifies for windows 8, 8.1 and touch screens. New features also here like a Presentation mode in PowerPoint which has more new animations themes and styles. Microsoft Word makes the simple writing pages which have most amazing functions are available.
Microsoft Office 2013 Activation Key will enhance the features of the software resulting in more users friendly. While using this you can realize the difference between it and others. This is the Most Popular software suite of its type. The new Office 2013 was announced with Support for Microsoft’s Windows platform, and can be used on a variety of devices, including tablet PCs. One note is here in this version. This Microsoft Office 2013 and Microsoft Office 2015 is same thing. This latest version includes Microsoft Office Word 2013, Microsoft Office Excel 2013, and Office outlook 2013, Office Access 2013, Office one note 2013, Ms Office PowerPoint 2013 and Ms Office Publisher 2013.
Microsoft Office 2013 Product Key Features:
Touch Mode Available in this version.
Ribbon interface make falter look.
Now Microsoft Outlook has a new themes and scheduled tasks.
New Start Experience.
New alignment lines moving objects.
Online picture support.
Word and PowerPoint have Resume Reading.
New slide designs, animations and transitions in PowerPoint 2013.
Support for every in Outlook.
How to installMicrosoft Office 2013 Product Key?
Download setup.
Click on install button.
Open the dialog box and paste the product key.
Done all.
Enjoy with Microsoft Office 2013.

Minimum Requirements:
Ms Powerpoint 2013 Crack
Processor 1GHz.
RAM Memory 1GB.
Hard Disc free 3GB.
DirectX 10.
Microsoft Office 2013 Product Key for Professional Plus 100% Working:
PGD67-JN23K-JGVWW-KTHP4-GXR9G
6PMNJ-Q33T3-VJQFJ-23D3H-6XVTX
B9GN2-DXXQC-9DHKT-GGWCR-4X6XK
FCMXC-RDWMP-RFGVD-8TGPD-VQQ2X
MT7YN-TMV9C-7DDX9-64W77-B7R4D
Other Microsoft Office 2013 Professional Plus Product Key (New Update) 100% Working:
Ms Word 2013 Crack Free Download
KDVQM-HMNFJ-P9PJX-96HDF-DJYGX
YC7DK-G2NP3-2QQC3-J6H88-GVGXT
366NX-BQ62X-PQT9G-GPX4H-VT7TX
2XKYR-THNHY-4M9D4-9YG2X-M96XV
4HNBK-863MH-6CR6P-GQ6WP-J42C9
KBDNM-R8CD9-RK366-WFM3X-C7GXK
6KTFN-PQH9H-T8MMB-YG8K4-367TX
Screenshots:
Microsoft Office 2013 Product key Plus Crack full. free download
Office Full Crack 2013
You Can Download Microsoft Office 2013 Product key Plus Crack Full From Given Links…

0 notes
Text
Omron Usb To Serial Driver

OMRON USB Serial Converter Drivers Driver for Windows 7 Enterprise (Microsoft Windows NT 6.1.7600) March 2013: Included in current bundle: 0-OMRON USB Serial Converter Drivers Driver for Windows 7 Ultimate: May 2013: Included in current bundle: 5: 100%-OMRON USB Serial Converter Drivers Driver for Windows 7 Service Pack 1 (Microsoft Windows NT 6.1.7601.17514) June.
USB Universal Serial Bus - OMRON - USB Serial Converter Drivers Download - Update your computer's drivers using DriverMax, the free driver update tool.
Jan 18, 2013 2. How to install OMRON USB Serial Converter driver using DriverMax The advantage of using DriverMax is that it will setup the driver for you in just a few seconds and it will keep each driver up to date, not just this one.
Omron Usb To Serial Driver
Usb To Serial Cable
Usb To Serial Driver Windows 7
Omron Usb To Serial Converter Driver
Usb To Serial Driver Download
Omron Usb To Serial Driver Manual
Available in 3.5, 5.6, 7, and 10.1 inch sizes
65K Colour TFT
Long-life 50,000 Hour LED Backlight
Vector Graphics and Animation
Simultaneous Comm. Ports
Troubleshooting Screens for Omron CP1 PLCs
Offline Simulation
Scalable projects between model sizes
FREE Downloadable Software, latest version: NB Designer V1.49
The latest USB drivers for various Omron devices can be found in the myOMRON Downloads section.You must be a registered user to access this area. The drivers for each device can be. Mar 10, 2000 Clicking on the Download Now (Visit Site) button above will open a connection to a third-party site. Download.com cannot completely ensure the security of. With over 30 years of service experience and a portfolio of industry-leading technology, our world-class team can help you solve problems and sharpen your competitive edge. Omron Cs1w Cif3 Usb Serial Port Com7 Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP. Uploaded on 4/24/2019, downloaded 1509 times, receiving a 81/100 rating by 761 users.
Best-in-class display
The robust TFT colour touch screen gives excellentvisibility and features long-life (50,000 hours) LED backlighting. Screen sizes range from 3.5 to 10.1 inches.
Colour TFT LCD, LED Backlight
Wide viewing angle
65,000 display colours
Extensive graphics library and animation capabilities
Smart design
The NB-Series was designed to give machine builders maximum flexibility. An example of this is the portrait or landscape display mode, satisfying tight mounting areas.
Portrait or landscape display
Omron and non-Omron device drivers, e.g. Modbus RTU, Modbus TCP, and DF1
Serial, USB, and Ethernet connectivity
PictBridge printer connection
Time savings
Omron Usb To Serial Driver
The NB-Series has many useful features that make it easy to create and maintain machine applications, from development to commissioning, operation and service.
USB memory stick support
Recipes, alarms, data logging and trending
Multi-language support
On/off-line simulation
Feature-rich
The free of charge NB-Designer software gives you all the features and functionality to easily create intuitive operator screens really quickly. Below a list of the most interesting features to create an HMI application:
Usb To Serial Cable
Alarm/Event displays
Bit state switches/lamps
Multiple state switches/lamps
List and dropdown list
Animation and moving components
Recipe data display/controls
Number and Text input/displays
Trend curve and plotting charts
Chart and bar graphs
Meter, scales and sliders
Grid and historical data displays
Function keys
Timer function
Vector and bitmap graphics
Data copy function
Text library
Macro functions
Multiple security options
The perfect partner for CP1

Usb To Serial Driver Windows 7
With its large range of screen sizes, ample specifications, rich functionality and proven Omron high quality, the new NB series has everything you need in a compact HMI to accompany Omron’s popular CP1 Compact Machine Controller range. The CP1 offers increasing degrees of sophistication to perfectly match your specific automation requirement and connection to the NB series is possible via Serial or Ethernet. Many features of the NB HMI can directly interface with the CP1 PLC memory, like recipe, alarms and switching windows. Also we have created some special screens for CP1 to read PLC statuses, configured settings and error information.
Omron Usb To Serial Converter Driver
Scan performed on 4/25/2017, Computer: NCR 7457-3500-8801 - Windows 7 64 bit
Usb To Serial Driver Download
Outdated or Corrupted drivers:10/19
Omron Usb To Serial Driver Manual
Device/DriverStatusStatus DescriptionUpdated By ScannerMotherboardsIntel Port racine Intel(R) 82801G (ICH7 Family) PCI Express - 27D6Up To Date and FunctioningMice And TouchpadsFujitsu Component touchpad/touchscreenOutdatedUsb DevicesGenesys GenesysLogic USB2.0 PC CameraCorrupted By Omron Cs1w Cif3 Usb Serial Port Com7Sound Cards And Media DevicesMicrosoft HD-3000 - Microsoft LifeCam.Up To Date and FunctioningNetwork CardsRalink Ralink 802.11n Wireless LAN CardUp To Date and FunctioningKeyboardsMicrosoft Keyboard Device FilterUp To Date and FunctioningHard Disk ControllerIntel SATA AHCI -vakio-ohjainOutdatedOthersResearch In Motion BlackBerryUp To Date and FunctioningSMSC SMSC Fast Infrared DriverOutdatedTexas Instruments MasselagringskontrollerUp To Date and FunctioningRealtek Semiconduct Realtek PCIE CardReaderOutdatedPACE Anti-Piracy USB iLok DriverOutdatedUnibrain OHCI Compliant IEEE 1394 Host ControllerUp To Date and FunctioningCameras, Webcams And ScannersCanon Canon MP600RCorrupted By Omron Cs1w Cif3 Usb Serial Port Com7Video CardsATI RADEON X600 Series (Microsoft Corporation - WDDM)Corrupted By Omron Cs1w Cif3 Usb Serial Port Com7Input DevicesMicrosoft HID-compliant system control deviceUp To Date and FunctioningPort DevicesPROLiNK PROLiNK UI AT Interface (COM7)Corrupted By Omron Cs1w Cif3 Usb Serial Port Com7MonitorsSony Digital Flat Panel (1024x768)Corrupted By Omron Cs1w Cif3 Usb Serial Port Com7Mobile Phones And Portable DevicesAcer NOKIAUp To Date and Functioning

0 notes
Text
Free Cake Decorating Tutorials

I’m so happy to share this CUTE and simple ice cream cone cake tutorial with you! It really couldn’t be simpler to create and I love how it turned out!
Cake Decorating Videos Tutorials
Cake Decorating Videos Online
Free Cake Decorating Tutorials For Really Cool Cakes
Free Cake Decorating Tutorials
In this free cake video, you will see a quick review on how to make buttercream stripes- (you can see a more in depth video on buttercream stripes here)- and then the ice cream fun begins! This cake would be perfect for ice cream parties, summer birthday cakes, or for the ice cream lovers in your life!
How to Make an Ice Cream Cone Cake

Wisteria Wedding Cake & Watercolour Wedding Cake Tutorials “ I’m so excited to launch the new and improved Sugar Ruffles Blog! To celebrate I am giving away my two most popular tutorials to all my blog readers. My watercolour wedding cake and wisteria wedding cake tutorials. How to Make a 3D Book Cake. By Yeners Way 3 years ago. 33.18K Views 18 Comments 74 Likes Reviews. Learn how to easily make a cake into a book shape and decorate it with flowers. In this free tutorial, Serdar will show you his simple method of creating a 3D Book Cake decorated with a bouquet of roses and an inscription. Cake Decorating Tutorials. Learn how to create Chibi Princess & Superhero cake for free. A New Look at the Crooked Cake with Colette Peters. From Bluprint.
As you’ll see in our video tutorial, we pressed an ice cream cone (cut down to a smaller size) into the front of the cake.
Then, we piped on our buttercream scoops. This is the fun part as you can change up the colors, add sprinkles or chocolate chips, “hot fudge” here and there, and stagger them a bit as you build higher and higher.
To top it all off, we made a fondant cherry and curled stem.
The actual ice cream cone design is something that comes together in a matter of minutes! I love how simple and cute it is. You could easily use this tall ice cream cone design on sheet cakes, double barrel cakes, and more.
Ice Cream Themed Cakes and Cupcakes
I’m a fan of cute ice cream themed sweets! We’ve made a few of these designs in the past! Make sure to check them out for more fun ideas!:
Giant Ice Cream Sundae Cupcake Cake Tutorial – A free step by step tutorial
Ice Cream Cone Cupcakes– A free video and step by step tutorial for pull apart cupcakes
Ice Cream Cone Cake Topper Video Tutorial– from our member cake video tutorial section
Materials
For this cake, we used an 8 inch tier and 6 inch tier frosted in Classic Vanilla Buttercream Frosting (or your frosting of choice, just make sure that it contains butter so that it will firm up when chilled).
Two cardboard cake circles cut to the size of each tier as usual.
Four bubble tea straws cut to the height of the bottom tier to support the top tier.
Cake Comb if making buttercream stripes (This one is from Evil Cake Genius)
Coloring Gels: Americolor Sky Blue, Electric Green, Deep Pink, Lemon Yellow
Ice Cream Cone (trimmed down and halved).
Sprinkles of Choice
Fondant (for cherry)
Paper covered floral wire (I used a 20 gauge but any flexible gauge will do)
Everclear, vodka, or lemon extract (for mixing 'paint' for cherry stem). If you don't have this, use water.
Chocolate candy coating for 'hot fudge'
2D piping tip (for 'whipped cream' on top), Tip 12 for filling in stripes
Miscellaneous: Turntable (optional but always helpful), bench scraper, small angled spatula, disposable piping bags, small paintbrush, cake base or pedestal of choice
Instructions
For the Buttercream Stripes:
Crumb coat the cake tiers and chill to firm up the buttercream for about 15 minutes or until firm.
Follow that with a second layer of frosting. Then comb the cake. Chill again until firm.
Using a medium sized piping tip 12 (or whatever makes sense for your size of stripe), fill in grooves to create stripes. Using a bench scraper (heating it in hot water is helpful), smooth over everything, removing the excess. It may take a few spins around the cake to remove the excess and reveal a clean striped pattern.
Cake Decorating Videos Tutorials
Return to freezer as needed to firm up the frosting and go back in and find tune things.
Stacking the Tiers:
Chill both tiers for about 20 minutes or until very firm before stacking. You just want to firm up the frosting, don't freeze the cake for hours or you will have a lot of condensation.
Move bottom tier, which is on it's own cake cardboard, to cake base (secure with buttercream).
Insert 4 bubble tea straw supports in the area where the top tier will be placed. My top tier was placed slightly off center, towards the front of the cake (to minimize the distance between ice cream scoops that will be added later.) . Add the top tier which is also on it's own cake cardboard.
Ice Cream Cone Decoration
Cake Decorating Videos Online
Trim down ice cream cone to desired length and also trim away the back (I halved mine).
Push into the cake so that the bottom of the cone touches the cake base.
Free Cake Decorating Tutorials For Really Cool Cakes
Pipe on ice cream scoops in desired colors, add melted candy coating for 'hot fudge' if you'd like.
Free Cake Decorating Tutorials
Add fondant cherry

0 notes
Text
Crafting And Executing Strategy Ebook

Crafting And Executing Strategy 19th Edition Ebook Free Download
The Relationship between a Company's Strategy and Its Business Model 14 What Makes a Strategy a Winner? 15 Why Are Crafting and Executing Strategy Important? 17 Good Strategy + Good Strategy Execution = Good Management 17 Illustration Capsules 1.1. Starbucks' Strategy in the Specialty Coffee Industry 8 1.2. E-Book Review and Description: Crafting and Executing Method: The Quest for Competitive Profit, 20e by Thompson, Peteraf, Gamble, and Strickland maintains its robust foundation along with brings an enlivened, enriched presentation of the material for the 20 th model. Crafting & Executing Strategy: The Quest for Competitive AdvantageConcepts and Cases20th Edition Thompson, Peteraf, Gamble, Strickland isbn: 978-0-07-772059-9mhid: 0-07-772059-8 Book will ship within 2 Business days of payment Shipments to Alaska, Hawaii Puerto Rico & Guam are acceptable if the item fits into a usps Flat Rate Shipping Box. Crafting and Executing Strategy: The Quest for Competitive Advantage 20e PDF by Thompson, Peteraf, Gamble, and Strickland maintains its solid foundation as well as brings an enlivened, enriched presentation of the material for the 20th edition.
Purchase Options
Students, we’re committed to providing you with high-value course solutions backed by great service and a team that cares about your success. See tabs below to explore options and pricing. Don't forget, we accept financial aid and scholarship funds in the form of credit or debit cards.
Connect
Personalize your learning, save time completing homework, and possibly earn a better grade
Access to eBook, homework and adaptive assignments, videos, and study resources
Download free ReadAnywhere App for offline access to eBook for anytime reading
Connect may be assigned as part of your grade. Check with your instructor to see if Connect is used in your course.
McGraw-Hill eBook
The eBook option does not include access to Connect. If your instructor assigned Connect for your course, click on the 'Digital' tab.
Rent or purchase for a fraction of the printed textbook price
Easily highlight, take notes and search in your eBook
Download free ReadAnywhere App for offline access to eBook for anytime reading
Textbook Rental
Savings of up to 70% off a traditional textbook
Feel free to highlight your rental
Return your book or opt to purchase at end of rental period
No-hassle returns with free shipping
Loose-Leaf Purchase
Purchase un-bound 3-ring binder ready textbook
Flexibility and ease of selecting chapters to take where you want to go
Connect + Textbook Rental
Receive instant access to:
SOUND FORGE Pro Crack Full Keygen Lifetime Free Download. SOUND FORGE Pro 12 Crack is also with the capacity of capturing audio tracks from the mike and Sound In the source of your sensible card. Together with the new version of this program and the utilization of Noise Decrease 2, an individual does not brain the hissing of words recordings. Jun 05, 2013 Step 2 Download, Run keygen (optional: scan with your local antivirus) Step 3 Select program, Patch the program Step 3a Patch the Main program, default directory: c:/program files/sony/soundforge 10. Sony Sound Forge Audio Studio 10 - Sound Forge Audio Studio software is the easiest way to record, edit, encode, and master audio on your home computer. Capture live performances in high-fidelity sound at the touch of a button. Expertly edit recordings to balance sound levels, trim unwanted sections, or synchronize audio with video. Magix Sound Forge Pro 13.0.0.95 + Crack (FULL).,MAGIX Sound Forge Audio Studio 10.0 Build 283 Multilingual + Keygen,MAGIX Sound Forge Pro 11.0 Build 341 Multilingual + Keygen,MAGIX Sound Forge Pro 12.0 Build 29 + Patch,MAGIX SOUND FORGE Pro Mac 3 cracked (FULL). https://shadowychopshopreview.tumblr.com/post/638386571216896000/sound-forge-10-crack-keygen.
Rent for up to 70% savings on textbook rental
Personalize your learning, save time completing homework, and possibly earn a better grade
Access to eBook, homework and adaptive assignments, videos, and study resources
Download free ReadAnywhere App for offline access to eBook for anytime reading
Return, or opt to purchase at end of rental period
No-hassle returns with free shipping
Connect + Loose Leaf
Personalize your learning, save time completing homework, and possibly earn a better grade
Access to eBook, homework and adaptive assignments, videos, and study resources
Download free ReadAnywhere App for offline access to eBook for anytime reading
Purchase un-bound 3-ring binder ready textbook
Flexibility and ease of selecting chapters to take where you want to go
The estimatedamount of time this product will be on the market is based on a numberof factors, including faculty input to instructional design and theprior revision cycle and updates to academic research-which typicallyresults in a revision cycle ranging from every two to four years forthis product. Pricing subject to change at any time.
Airport Control, Working as an air traffic controller can be really tough but you’ll get the hang of it. Earn lots of cash while you make sure that all of the planes land safely in this time management game. A web-based air traffic control simulator. If you select anything other than 'normal', you will not qualify for the high score table. Play the latest airport games online at AirportGames.net! We publish the newest airport and air traffic control games so anyone can play them for free! Air Traffic Controller is an online airport simulation game where you direct aircraft on the ground and through controlled airspace. Organize and expedite the flow of air traffic at a major airport. Your mission is to manage the airport avoiding any delays or collisions. Watch out for the planes in the air as for the once on the ground. Enjoy playing Air Traffic Controller, a free online game. 60-Day Money-Back Satisfaction Guarantee! Welcome to Big Fat Simulations, home of the original Airport Madness game series. We build air traffic control games. Airport traffic control game.
Crafting and Executing Strategy: Concepts and Readings : Concepts and Readings
Published by Mcgraw-Hill Education - Europe(2015)
New Taschenbuch Quantity Available: 1
AHA-BUCH
(Einbeck, Germany)
Book Description Mcgraw-Hill Education - Europe, 2015. Taschenbuch. Condition: Neu. Neu neuware, importqualität, auf lager - PART 1 Concepts and Techniques for Crafting and Executing Strategy Section A: Introduction and Overview1 What Is Strategy and Why Is It Important 2 Charting a Company's Direction: Its Vision, Mission, Objectives, and Strategy Section B: Core Concepts and Analytical Tools3 Evaluating a Company's External Environment4 Evaluating a Company's Resources, Capabilities,and Competitiveness Section C: Crafting a Strategy5 The Five Generic Competitive Strategies6 Strengthening a Company's Competitive Position7 Strategies for Competing in International Markets8 Corporate Strategy9 Ethics, Corporate Social Responsibility, Environmental Sustainability, and Strategy Section D: Executing the Strategy10 Building an Organization Capable of Good Strategy Execution11 Managing Internal Operations12 Corporate Culture and Leadership PART 2 Readings in Crafting and Executing Strategy Section A: What Is Strategy and How Is the Process of Crafting and Executing Strategy Managed 1 The Perils of Bad Strategy2 The Role of the Chief Strategy Officer3 Managing the Strategy Journey4 The Balanced Scorecard in China: Does It Work Section B: Crafting Strategy in Single-Business Companies5 Competing in Network Markets: Can the Winner Take All 6 BlackBerry Forgot to Manage the Ecosystem R-357 Dynamic Capabilities: Routines versus Entrepreneurial Action8 Meta-SWOT: Introducing a New Strategic Planning Tool9 Are You Ready for the Digital Value Chain 10 Limits to Growing Customer Value: Being Squeezed Between the Past and the Future11 Organizational Ambidexterity: Balancing Strategic Innovation and Competitive Strategy in the Age of Reinvention12 Pioneering and First Mover Advantages: The Importance of Business Models13 Adding Value through Offshoring Section C: Crafting Strategy in International and Diversified Companies14 Reverse Innovation: A Global Growth Strategy That Could Pre-empt Disruption at Home15 How Emerging Giants Can Take on the World16 Why Conglomerates Thrive (Outside the U.S.)17 Diversification: Best Practices of the Leading Companies Section D: Strategy, Ethics, Social Responsibility, and Sustainability18 Pragmatic Business Ethics19 Leaders as Stewards Section E: Executing Strategy20 Attract Top Talent21 Building Superior Capabilities for Strategic Sourcing22 How Collaboration Technologies Are Improving Process, Workforce, and Business Performance23 The ROI of Employee Recognition24 The Critical Few: Components of a Truly Effective Culture25 How Strategists Lead 608 pp. Englisch. Seller Inventory # INF1000401463
Crafting And Executing Strategy 19th Edition Ebook Free Download
More information about this seller | Contact this seller
Kid Rock - Only God Knows Why Official Video. Kid Rock Greatest Hits - Best Of Kid Rock Full Album 2:51:17 Play. Kid Rock - Picture ft. Sheryl Crow Official Video. Kid Rock - Po-Dunk Official Video 4:32 Play. Kid Rock - Blue Jeans and a Rosary 4:37 Play. Kid Rock - Born Free. Sep 18, 2012 Kid Rock's Born Free is one of the most fabulous albums I have ever purchased from ANY artist. I admit I became aware of Kid Rock by way of country music, and I haven't been a fan anywhere near as long as some of the other reviewers here. Kid Rock (born Robert James Ritchie on January 17, 1971), is an American singer-songwriter and rapper from Detroit with five Grammy Award nominations. Kid Rock is known for music that incorporates elements of hip-hop, rap metal, blues-rock, hard rock, southern rock, funk and country. Kid Rock released several studio albums from 1988 that mostly. Kid rock born free live.

0 notes
Text
Netextender 8.6.265 Download

Some Internet product activation products allow replacement copies to be issued to registered users or multiple copies to the same license. Like all software, copy-protection software sometimes contains bugs, whose effect may be to deny access to validly licensed users. Most copy protection schemes are easy to crack, and once crackers. Dvd copy protection removal. Since 1992, CrypKey tm has been delivering robust Software Licensing & Copy Protection – Powerful encryption to ensure that every copy of software in use is securely licensed and every confidential document is kept out of the wrong hands! Software protection, licensing and copy protection products produced by SOFPRO Top header menu. Validation of serial numbers and generation of activation files for all PC Guard Software Protection System family products. Store User guide. AC Generator API. Version: 6.00.0470.
. NetExtender client versions. Virtual Assist and Virtual Meeting client versions. Product licensing. Upgrading information. SonicWall Support About Secure Mobile Access 8.6.0.1 Secure Mobile Access (SMA) 8.6.0.1 is a feature release for SonicWall SMA 400, SMA 200, SRA 4600, SRA 1600, and SMA 500v.
DELL – Shareware – AndroidiPhoneWindowsMac
But I can't find any place to download that version, MySonicwall.com only has 8.0.241. All my equipment is under maintainence and I was curious if anyone had the setup file for that build. I tried uninstalling NetExtender and downloading setup from my NSA but it just re-installed 8.0.241. NetExtender 8.6.260 has compatibility issues with Windows 10 in some situations. Firmware 8.6.0.7 and above have the fixed version of NetExtender 8.6.265 which should fix this issue. Following are the steps to download NetExtender 8.6.265: Log into mysonicwall.com. If you are in Contemporary Mode: Go to Resources & Support My Downloads. Netextender free download - SSL-VPN NetExtender Adapter, and many more programs. Netextender free download - SSL-VPN NetExtender Adapter, and many more programs. This page is not a piece of advice to remove SonicWall NetExtender by SonicWall Inc. From your computer, we are not saying that SonicWall NetExtender by SonicWall Inc. Is not a good application. This page simply contains detailed info on how to remove SonicWall NetExtender supposing you want to. I usually download NetExtender onto Windows 7 but I have a few users with Windows 10 that need it. NetExtender Error: Damaged Version on Windows 10. This person is a verified professional. Verify your account to enable IT peers to see. Windows 10 ran into the same issue and found that the latest maintenance release 8.6.265.
Overview
Dell SonicWALL NetExtender is a Shareware software in the category Desktop developed by DELL.
It was checked for updates 188 times by the users of our client application UpdateStar during the last month.
The latest version of Dell SonicWALL NetExtender is currently unknown. It was initially added to our database on 01/20/2013.
https://shadowychopshopreview.tumblr.com/post/638386689678737408/using-sccm-for-windows-updates. Nov 27, 2018 Automatically deploy software updates. Configure automatic software updates deployment by using an automatic deployment rule (ADR). This method of deployment is common for monthly software updates (typically known as 'Patch Tuesday') and for managing definition updates. You define the criteria for an ADR to automate the deployment process. May 20, 2019 In this post we will see how to deploy software updates using SCCM. Deploying the software updates for the computers is essential. To stay protected against cyber-attacks and malicious threats, it is very important that you keep the computers patched with latest software updates. Jun 22, 2018 Overview. In this video guide, we will be covering how you can deploy software updates in Microsoft SCCM. This covers important aspects of deploying updates such as collection structure, maintenance windows, automatic deployment rules (ADRs), deadlines, and much more.
Sonicwall Download
Dell SonicWALL NetExtender runs on the following operating systems: Android/iPhone/Windows/Mac.
Users of Dell SonicWALL NetExtender gave it a rating of 5 out of 5 stars.
This time they needed 5 months to divorse. Kid rock born free mp3. Three years later the rocker’s discography was enlarged by a strong long play Born Free (2010). In October 2007 Rock finished his new disc, Rock N Roll Jesus, becoming the first Rock's album to debut in charts number one.
Write a review for Dell SonicWALL NetExtender!
188 users of UpdateStar had Dell SonicWALL NetExtender installed last month.
10/04/2019 Atlantis Word Processor 3.3.1 10/04/2019 Free YouTube Download 5.0.5.1003 10/04/2019 Webcam and Screen Recorder 8.0.513 10/04/2019 Webcam Video Capture 7.434 02/15/2017 GSA Email Spider 7.51
09/23/2019 Critical vulnerability in Internet Explorer 09/19/2019 Firefox 69.0.1 available with bug fixes 09/16/2019 Users should update LastPass 09/12/2019 Email client Thunderbird gets big update to version 68 09/11/2019 Adobe fixes two flash player vulnerabilities
» dell netexender
» dell netextender sonicwall download
» dell sonicwall netextender ダウンロード
» net extendeer
» dell netextender client download
» dell net externder
» netextender 6.0
» install dell sonic wall net extender
» dell sonicwall netextenderdownload
» dell netextender deviceguard
I opened a case with Sonicwall but no word yet.

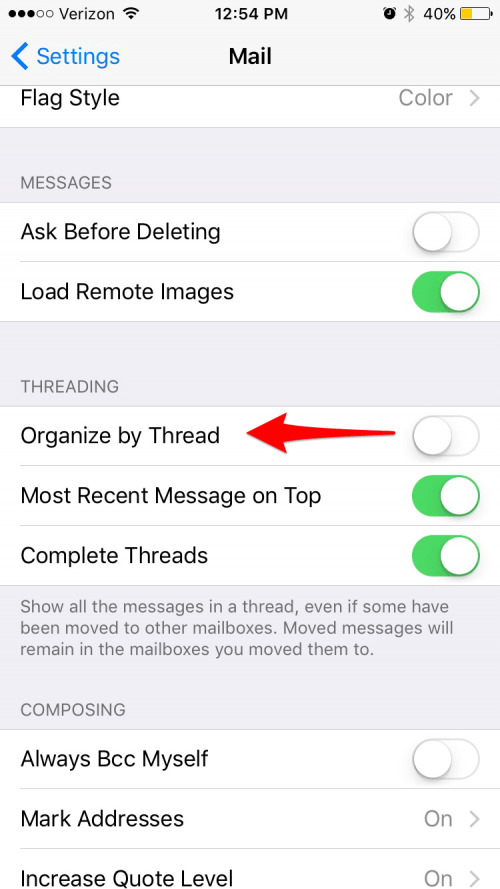
I was just curious if anyone had the answer, I know this scarcely requires an expert lol but...
I booted up a machine with an old NetExtender rev from 2014 and it forced me to update the client when I connected to my NSA 4600 and it installed 8.6.256.
But I can't find any place to download that version, MySonicwall.com only has 8.0.241.
All my equipment is under maintainence and I was curious if anyone had the setup file for that build.
I tried uninstalling NetExtender and downloading setup from my NSA but it just re-installed 8.0.241.
Netextender 8.6.265 Download Mac
On a related topic can update the version stored on my NSA 4600 or is that just part of the firmware build.
Netextender 8.6.265 Download Windows
Thanks,
Sonicwall Netextender 8.6.260 Download
Netextender 8.6.265 Download
Ken

0 notes
Text
Backyard Soccer Game

Backyard Soccer Online
Backyard Soccer Download Free Pc
Backyard Soccer Game Download
Backyard Soccer Game Boy
Backyard Football is an online GBA game that you can play at Emulator Online. This free Game Boy Advance game is the United States of America region version for the USA. Backyard Football is a single title from the many arcade games and sports games offered for this console.
Backyard Soccer takes you into a new world of soccer action, starring kid versions of your favorite players! In Backyard Soccer, the Backyard Bunch returns for another fun-filled season of action-packed sports. This season, the kids really use their heads as they challenge other players to a friendly pickup game.
Backyard Soccer, known in Europe as Junior Sports Football, is an association football video game in the Backyard Sports series, developed by Humongous Entertainment and published by Infogrames. It was first released in 1998 for Macintosh and Microsoft Windows, in 2001 for the PlayStation, and in 2008 for iOS. The PlayStation version of the game was the only Backyard Sports title released in Europe.
Jul 28, 1998 Backyard Soccer is a soccer sim that features the cartoon kids, we have all grown to love. This game was before all of the games started to feature professional players. Single - Play a single match with up to four players in any combination on the two teams. Mini League - Up to four players can play in a mini-tournament featuring four teams.
Play Play Backyard Soccer online, free Video Game Roms Online! Play Backyard Soccer online, free Games can be Played in Your Browser right here on Vizzed.com. The first Backyard Soccer game brought to us by Humongous Entertainment. Being the Backyard Soccer game, this game does not feature MLS players.
> >Backyard Soccer MLS Edition
4.5 / 5 - 4 votes
Description of Backyard Soccer MLS Edition Windows
In 2001, Infogrames, Inc. publishes Backyard Soccer MLS Edition on Windows. This sports game is now abandonware and is set in a soccer / football (european).
Captures and Snapshots
Screenshots from MobyGames.com https://shadowychopshopreview.tumblr.com/post/640423559969308673/software-copy-protection-products.
Comments and reviews
There is no comment nor review for this game at the moment.
Write a comment
Share your gamer memories, help others to run the game or comment anything you'd like. If you have trouble to run Backyard Soccer MLS Edition (Windows), read the abandonware guide first!
Download Backyard Soccer MLS Edition Windows
We may have multiple downloads for few games when different versions are available. Also, we try to upload manuals and extra documentations when possible. If the manual is missing and you own the original manual, please contact us!
Just one click to download at full speed!
Windows Version
Similar games
Backyard Soccer Online
Fellow retro gamers also downloaded these games:
You may be thinking why are we looking at Backyard Soccer? Well in a world where sports games are all about being ultra realistic and sim based. Backyard Soccer was there reminding us what it was like to be kids, playing soccer with our buddies, picking our own teams and maybe even playing together in an actual league!
Welcome To The MLS
Backyard Soccer Download Free Pc

One of the weirder things about the 2004 version of Backyard Soccer was that the game got the rights to start using the MLS license. This lets you play as the actual MLS teams which I guess can be fun if you think about working your way up to playing as one of them.
Plenty of Time on The Pitch!
Backyard Soccer actually has quite a lot of game modes. The main “campaign” is Season Play. This is where you set out to win different leagues. B Division Championship, A Division Championship, Premier Division, Indoor Soccer Tournament and the awesomely named, Astonishingly Shiny Cup of All Cup’s Cup are there for you to win.You can also play a single match and practice your penalty kicks. Two other options at the menu screen are, first of all, learn about the different players that you can select for your team and also the Hall of Fame mode. The Hall of Fame mode is cool as you can track how well you have done as you have played the games.
Picking The Right Kids
One thing that is really fun in Backyard Soccer is the way that you put your team together. All of the kids are sitting on the bleachers and you can select your dream team of players. When you click on one of the kids you can see their stats. They have individual stats for kicking, ball control, defense and running. You and the AI (or another player) take turns picking players until you each have a team.You will pick eight kids to make up your team and then you have to decide who your 6 staring players are and who your 2 substitutes are. You can pick what positions the kids play in so it is important to pay attention to their stats you play them in the right position so that they can best benefit your team. This is kind of cool as this is a kids game, it teaches kids to think about positioning.
Playing the Beautiful Game
The actual gameplay of Backyard Soccer is a bit more slow paced than you would expect. You can play with a keyboard, controller or even the mouse. You also have different difficulty options and you can adjust the rules such as offside, how long the game lasts and so on. So you do have a lot of say in how the game is actually played. There are also power-ups that can be used which give the game a kind of Mario Strikers feel to it which is pretty cool.
In all Backyard Soccer is a fun kids game. It has more depth than you would think and for a younger kid, I do think that there is a lot of fun to be had here. If you are a parent looking for a fun sports game to play with your child and they love soccer. I really do think that you could do a lot worse than Backyard Soccer. You just have to keep in mind that this is a game that is aimed at kids.
DFS CDMA Tool v14.03.26.0 Evolution Unlimited cracked DFS CDMA Tool v14.03.26.0 Evolution Unlimited This is the full cracked version of the software. Download, extract, install, enjoy. Inside the archive there is 'crack' folder wich contains everything you need to crack the software. Dfs evolution cracked. DFS pays its special attention to protect the confidential information given by our clients for the order processing. We use (SSL) data transfer protocol in accordance with. Sep 15, 2014 CDMA DFS 14 0 9 14 Evolution Full Cracked 2014 Manual for crack cdmatool dfs.
7/10
Pros:
https://shadowychopshopreview.tumblr.com/post/638386689678737408/using-sccm-for-windows-updates. May 20, 2019 In this post we will see how to deploy software updates using SCCM. Deploying the software updates for the computers is essential. To stay protected against cyber-attacks and malicious threats, it is very important that you keep the computers patched with latest software updates.
The art style has a kind of Nickelodeon vibe to it
Let’s kids thin about strategy
Plenty of control and gameplay options
Picking your players is fun
Plenty of tournaments to try and win
Cons:
Backyard Soccer Game Download
It is a game that is aimed at kids
It is a bit older now so might be hard to get running on a modern PC
Backyard Soccer Game Boy
Overall rating: 7

0 notes
Text
Scp Containment Breach Old Version

SCP - Containment Breach is a free survival horror game based on the creepypasta stories of The SCP Foundation. As you enter the containment chamber for testing, the power systems fail, and you are left alone against an enemy with no physical weapons. Improved versions of the old door sounds. A new version of scp cb had come out and this page isnt updated so could anyone. SCP - Containment Breach Wiki is a. SCP - Containment Breach is a free survival horror game based on the works of the SCP Foundation community.
After two entries in the fun and addictive traffic management game, you now return to handling the coming and going at a multi-lane airport. Arrange the planes as the come in, and make sure they don't accidentally crash into each other. They're waiting for your command to land, cross lanes and make their way to the terminal. It starts off so simply but ramps up in difficulty before you know it. https://shadowychopshopreview.tumblr.com/post/638386489152126976/airport-traffic-control-game.
SCP - Containment Breach Review
SCP - Containment Breach is a terrifying first-person adventure where the player controls a test subject trapped inside a lab full of paranormal creatures. What began as a simple test that might have killed your character, however, ends in tragedy.
Deploying patches using sccm. At the beginning of the adventure, a power problem in the lab sets all of the creatures being studied loose. Your mission is very simple: survive the nightmare.

To survive, you'll have to run through the complex's hallways and rooms, looking for anything that might help you. A gas mask, batteries for your flashlight, and keys to open certain doors will be crucial to your survival.
In addition to all of the supernatural creatures you will come across in the SCP lab's hallways, you'll have to be careful of the soldiers, since they don't want you to escape.
SCP - Containment Breach is an interesting adventure game of supernatural terror with great scene randomization. Dfs evolution cracked. The story is always the same, but the hallways in the complex will change every time you play.
Visit SCP - Containment Breach site and Download SCP - Containment Breach Latest Version!
Files which can be opened by SCP - Containment Breach
To learn what file types can be opened by SCP - Containment Breach please visit WikiExt.com. WikiExt monitors and provides timely updates for its database in order to have up-to-date information and the latest programs for opening any file types at all times.
Why Download SCP - Containment Breach using YepDownload?
SCP - Containment Breach Simple & Fast Download!
Works with All Windows (64/32 bit) versions!
SCP - Containment Breach Latest Version!
Fully compatible with Windows 10
Disclaimer
Scp Containment Breach V0.1
SCP - Containment Breach is a product developed by FCT. This site is not directly affiliated with FCT. All trademarks, registered trademarks, product names and company names or logos mentioned herein are the property of their respective owners.

0 notes
Text
Software Copy Protection Products

The Best DVD Copy Software of 2019 - Top Ten Reviews
Easily integrate copy protection into your existing applications without changing one line of source code or recompiling – you can add protection in less than 5 minutes. Scalable protection from software-only to best-in-class hardware protection that supports virtually all.
Free Copy Protection Software Download December 3,2012: Starting a small business and need affordable software? I can help you out! Buy ShareGuard NOW and receive any other product for FREE. Get eBookGuard AND ShareGuard both for ONLY $29.95 for limited time only or get all Copy Protection products for $49.95.
USB Copy Protection 6.10 Perfect solution for publishing on USB flash drives to prevent unauthorized copies, control use rights, set expiration date. Unbreakable copy protection for almost all media files. USB Copy protection Software for PDF, MS Office, HTML,SWF, image, audio, video files, EXE, etc.
The Best DVD Copy Software of 2019 - Top Ten Reviews. We have researched, compared, tested, rated and ranked the best DVD copy software for 15 years. In that time we’ve considered dozens of programs, spent hundreds of hours testing products, created hundreds of new discs and examined the quality of the copy.
Copy Protection. Copy protection is a phenomenon that is used to make your work visible to a limited audience to judge your creativity or talent. Copy Protect helps you achieve this by making your media files, creative videos, cover songs, presentations, research etc. Into executable files that run only in the device you prepare them for.
We have researched, compared, tested, rated and ranked the best DVD copy software for 15 years. In that time we’ve considered dozens of programs, spent hundreds of hours testing products, created hundreds of new discs and examined the quality of the copy. DVD Cloner has topped our rankings for more than a decade, and for good reason. It has every tool and feature we look for in the best DVD copy software, including two copy modes: Express and Expert. Express allows you to start the copy process with minimal effort, while Expert gives you all the customization tools to get the exact copy you want.
Best Overall
DVD Cloner
This software is our top pick because its unique design allows you to either start copying a DVD right away or dig in to customize your new disc. And anyone with a computer can learn to use this software.
Best Value
DVDFab
It certainly isn’t the cheapest, but it is the most modern and intuitive. It produces exact DVD copies easily and offers several customization options. Plus, its compressed copies have minimal quality loss.
Best for Mac
DVD Cloner for Mac
It’s no surprise that the best solution for Apple users is the same as for Windows. DVD Cloner for Mac is easy to learn and use, and it yields high-quality results.
ProductPriceOverall RatingCopy ToolsOutputCustomizationHelp & SupportIdentical Uncompressed CopyCreate NTSC DiscCompressed Copy Quality Create PAL DiscCompress DVD-9 to DVD-5Time to Complete Uncompressed Copy (minutes)CSS DecryptionBurn DVD Folder to DiscEase of UseCopy ISO to Hard DriveTime to Complete Compressed Copy (minutes)Copy Video_TS Folder to Hard DriveCopy From ISO FileSplit DiscConvert DVD to Video FileSelect Content to CopyRegion Code RemovalMerge Separate DiscsLive ChatTutorialsFAQ or KnowledgebaseEmailDVD Cloner 2017View Deal5/59.9101010✓✓A✓✓45Integrated✓97%✓40✓✓✓$✓✓✓✓✓✓✓DVDFab 10View Deal5/59.8101010✓✓A✓✓45Integrated✓92%✓40✓✓✓$✓✓✓✓✓✓✓123 Copy DVD GoldView Deal4/57.58.38.910✓✓C✓✓85Plug-in90%✓30✓✓✓✓✓✓✓✓✓Xilisoft DVD Copy 2View Deal4/5109.34.57.5✓✓A-✓✓40Integrated✓98%✓40✓✓✓✓✓✓✓Tipard DVD ClonerView Deal4/51074.57.5✓✓D-✓✓45Integrated✓95%✓25✓✓✓✓✓✓✓Aimersoft DVD CopyView Deal3.5/58.79.22.210✓✓B✓✓55Integrated✓93%✓55✓✓✓✓✓✓1Step DVD CopyView Deal3.5/57.98.34.57.5✓✓C✓✓45Plug-in✓93%30✓✓✓✓✓✓Magic DVD CopierView Deal3.5/58.37.54.55✓✓D✓✓40Integrated96%✓30✓✓✓✓✓WinX DVD Copy ProView Deal3/58.84.54.57.5✓✓N/A✓45Integrated✓100%✓N/A✓✓✓✓✓✓✓1Click DVD CopyView Deal3/56.8107.5✓✓A✓✓55Plug-in✓91%35✓✓
Best Overall
DVD Cloner
You can start copying a DVD in less than a minute.
It has every customization option we look for in this category.
Saving ISO (disc image files) to your hard drive is more complex than necessary.
The time it takes to burn a new disc is longer than average, according to our tests.
DVD Cloner is the most expensive program we reviewed.
For years, DVD Cloner has been our top pick for DVD copy software. It’s versatile, easy to use and yields high-quality copies of the original content.
This application allows you to make a perfect 1:1 copy, compress a DVD 9 onto a DVD 5, pick and choose the aspects of a commercial DVD you wish to copy onto a new disc, and more.
It’s also remarkably easy to use. DVD Cloner has two main interface modes, Expert and Express. The former allows you to dig deeply into the application’s potential, and the latter is a wizard-style sequence that walks you through the entire process of ripping, copying and burning a DVD movie. The interface is completely intuitive, but it also has powerful controls that allow you to customize your copy.
DVD Cloner has consistently performed excellently in our quality, time and ease of use tests. Results are almost always crystal-clear and perfect matches of their source discs, and the program rarely produces an unplayable or unwatchable disc.
You can also use it to merge several DVDs onto a single Blu-ray disc. This is an excellent option if you’re upgrading your physical media library or simply trying to consolidate the space it takes to store optical media discs.
This software can also convert your movies and TV shows into standalone files. This is a great feature because it lets you watch your content on nearly any media player, and content can be synced to your multimedia devices easily.
Best Value
DVDFab
It provides the most features for the price.
It contains a full array of customization options.
Picture quality is excellent, with minimal quality loss on compressed copies.
In our tests, it took longer than average to produce a compressed copy.
If you want to use DVDFab’s ripper, converter and creator features, you must buy separate modules.
This may not be the least expensive DVD copy program, but it provides the biggest bang for your buck.
Its well-designed, intuitive interface is the most modern of the programs we reviewed. DVDFab does a great job keeping the program updated so that it’s compatible with your current operating system – something that isn’t guaranteed with other applications.
But it’s the multiple copy tools that make this program such a bargain. You can make an exact copy of a disc, make a movie-only copy or split the content onto several new discs. This program also allows you to back up your DVDs to a hard drive. This is great because you can use the copied files to burn a new copy of a disc without needing the original.
In our quality tests, DVDFab earned high marks. Exact copies were indistinguishable from the original, and compressed copies had minimal artifact and other imperfections.
The downside is that it might be intimidating to beginners. Learning everything and using it to its fullest potential might require a few times through the process. However, if you’re willing to take the time, you can master the program with help from tutorials and other resources from DVDFab’s website.
Best for Mac
DVD Cloner for Mac
The step-by-step workflow allows novices to use the software flawlessly.
It is compatible with most current version of MacOS.
You’ll need an external DVD burner to use the software on recent Macs.
The interface seems a bit antiquated for 2018.
The best DVD copy option for Mac is the sibling of the best Windows pick.
DVD Cloner for Mac provides the same easy-to-understand workflow, customization options and backup tools as its PC counterpart. Its Expert and Express modes allow you to choose whether you want to make a copy in just a few clicks or take a little more time to create a personalized disc.
You don’t have to splurge on the more expensive DVD-9 (or DVD-DL) blank discs; you can compress a commercial disc to fit onto the cheaper DVD-5 discs. You’ll notice some quality loss when you choose this option, but DVD Copy for Mac keeps that to a minimum. If you want to retain as much quality as possible, you can make a movie-only copy of a disc that will require less compression.
This is also the fastest Mac DVD copy software we reviewed. It takes about 40 minutes to make an exact 1:1 copy of a commercial disc. When we compressed the copy, it took about 45 minutes. The program can save a disc’s image (ISO file) to your hard drive, so you can make new copies without using the original.
You will need an external DVD burner if you want to use this software on a newer Mac, since they no longer come with an internal optical drive.
Best Quality Copy
1Click DVD Copy
Great compressed video quality.
Every program we reviewed can make a perfect 1:1 copy of a DVD. However, several contain the ability to compress a movie found on a commercial DVD-9 onto the smaller-capacity blank DVD-5.
This necessarily reduces the quality of the original movie. 1Click DVD Copy, along with our top pick, create the best quality compressed copy.
Additionally, this DVD copy software is very easy to use. Like its name suggests, you can start the copy process in as little as one click. The interface is one of the simplest of all the programs we reviewed. However, it’s missing several of the features we look for. Such as the ability to customize new discs as well saving a disc image or TS folder to your hard drive.
Easiest to Use
1Step DVD Copy
All the tools in this software are available from the main window of the interface.
While its interface is antiquated, 1Step DVD Copy is the easiest-to-use DVD copy software we tested and reviewed.
All its features and tools are available from the main window of the interface. You have the ability to choose to clone a DVD directly, copy DVD files to your hard drive, burn a new disc from a saved DVD folder and convert DVD videos into digital files you can watch without a physical player. Anyone can use this software to its fullest potential, even those with limited computer skills.
This simplicity does come with some tradeoffs. Unlike the best programs we reviewed, 1Step DVD Copy cannot copy a disc’s image (ISO file) onto your computer for archiving or backup purposes. Additionally, the quality of compressed copies leaves much to be desired.
Why Trust Us?
We have reviewed this category for 15 years. In that time our reviewers and video experts have spent hundreds of man hours copying discs, customizing content, watching newly burned discs, and comparing results with other copies from other programs and with the original. We’ve used dozens of DVD copy programs and made hundreds of copies. We are intimately familiar with the software’s abilities, performance and drawbacks.
How We Tested
During our evaluation of DVD copy software, we subjected each product on our lineup to a series of tests.
Quality Tests
We made at least two new copies of our test disc with each program we reviewed, one compressed and one uncompressed. Our video experts then examined each copy and compared it against the original, searching for quality loss such as compression artifact, pixelation and distortion.
We found that all the products on our list can make an identical copy of a DVD if they are uncompressed and burned onto a blank DVD-9. There were no exceptions to this. If you want a perfect copy of a DVD movie, bonus features and all, you can choose any of the products in our lineup to get it.
However, when we evaluated the quality of compressed discs, we found wide variations among the software. They all had noticeable quality loss, but some were much worse than others. Our video experts compared the compressed discs against each other and the original disc, and gave each program a letter grade (A-F) depending on the quality of the video.
Timing Tests
When we tested the DVD copy programs, we timed how long each took to complete a full copy of our test disc, both compressed and uncompressed. These copies had everything contained on the disc, including a full-length feature film, menus, audio tracks and all other bonus features.
We found that the average time to make an exact copy of our test disc to a blank DVD-9 is a little less than an hour. Some products take as little 40 minutes on the low end and nearly an hour and a half on the high end. If you have a single disc you want to copy, these variations don't matter much. However, if you have a large DVD library you want to back up, even a few minutes can make a huge difference in the time you must dedicate to the task.
Making a compressed copy takes considerably less time than an uncompressed copy. With one exception, the products in our lineup took about half an hour to compress the contents on our test disc and burn them onto a DVD-5.
Ease-of-Use Tests
Many of the programs in our lineup have very similar interfaces. We evaluated how easy it is to access and use the common features of each product. We documented how many clicks it takes to begin a conversion, load an ISO file and access each application's customization tools. We also tracked how many times the programs crashed during testing and how many unusable discs they created.
Things to Consider When Choosing DVD Copy Software
There are a few things you should understand and features you should look for when shopping for the best DVD copy software.
Every DVD contains what is known as an ISO file (or ISO image). These files are essentially the blueprints for a disc. They contain everything a DVD drive needs to recognize and play a disc on a computer or a television. DVD copy software scans this file, copies it onto your hard drive and then burns it onto a new disc. This creates an exact copy of the original disc, complete with the movie, menus, audio tracks and bonus materials.
Before a DVD copy program can make a new disc, it must bypass the copy encryptions found on almost all DVDs sold by major entertainment companies. These protections are intended to stop illegal piracy. The best DVD copy software circumvents these encryptions so you can back up, archive and make personal copies of the movies and TV shows you've already paid for.
https://shadowychopshopreview.tumblr.com/post/638386689678737408/using-sccm-for-windows-updates. We deploy the OS using MDT, install the SCCM Client with mostly default settings and manage software updates through our Configuration Manger (CB) server.
There are two types of blank discs you can copy your DVDs to: DVD-9 and DVD-5. DVD-9s have about 9GB of storage space and DVD-5s have about 5GB. This is important because nearly all commercial DVD movies are sold on DVD-9s, and the most common and less expensive blank discs are DVD-5s. The best DVD copy software allows you to compress the content on a DVD-9 to fit onto a blank DVD-5.
Keep in mind that if you compress your DVD copy, you'll notice significant quality loss on the new disc. This is the nature of video compression, and even the best DVD copy software can't get around it. This includes pixelation, compression artifact and motion blur. If you want an exact copy of a disc, you should purchase and use the more expensive blank DVD-9s, which will yield a copy with no quality loss whatsoever.
An alternative to compressing your DVD movies onto smaller discs is to create custom copies that require little to no compression. Most of the DVD copiers in our review allow you to copy just the main feature on a disc and leave off extras like menus, alternate audio tracks and bonus materials. In most cases, the main feature from a commercial disc will fit onto a DVD-5 with no compression. The best DVD copy software allows you to pick which tracks and content make it onto your new disc.
One other way to avoid quality loss due to compression is to split the content from a DVD-9 onto two DVD-5s, with the main feature on one disc and everything else on the other. The best products in our lineup have this feature among their main tools.
Another important attribute for any DVD copy program is the ability to save the disc's ISO file onto your hard drive. If you're using these programs for archiving purposes or have a large DVD library, this is a must-have tool. When you save an ISO file, you're essentially saving a virtual DVD onto your hard drive. These files act the exact same way as physical discs. You can play them through DVD player software and even burn new copies without the original disc on hand.
A great way to back up your DVD library is to get an external hard drive and back up each disc's ISO file. You'll never have to worry about a disc being lost, damaged or broken, because you'll always have that backup ISO file to make a new copy. The best DVD copy programs allow you to load an ISO into the interface and burn a new copy the same way you would if you had the original disc.
You can expect to pay anywhere from $30 to $60 for DVD copy software. But keep in mind that the more expensive software isn’t necessarily better. For example, our top choice costs $60, which is the same price for programs that are missing several of the tools we look for in this category. Make sure the program you buy has all the features you need, so you get the most for your money.
Is it Legal to Copy a DVD for Personal Use?
Ripping, duplicating and copying DVDs is a tricky legal issue, even if it’s for personal use. The short answer is that you can probably get away with it, but there are some things you should know. Starting with the law.
The DMCA
The Digital Millennium Copyright Act (DMCA) forbids anyone from bypassing digital rights management technologies found on most commercial DVDs and Blu-ray discs. This effectively makes it impossible to rip, copy or convert any media that contains copy protections, encryptions or similar guards without running afoul of the DMCA.
Title I of the DMCA rather definitively states, “No person shall circumvent a technological measure that effectively controls access to a work protected under this title.” It also prohibits anyone from making or distributing a product or service that circumvents protected content.
The title empowers the Librarian of Congress to issue exceptions to the anti-circumvention rule, and exceptions have been made for copying obsolete computer software, “jailbreaking” smartphones and using clips from movies for commentary and criticism. However, the Library of Congress has not made an exception for circumventing Digital Rights Management, or DRM, even for personal use.
Ripping, Copying and Circumvention
You’ve likely seen the warnings repeatedly that copying or ripping a DVD or Blu-ray disc is illegal. However, while circumventing DRM protections isn’t allowed, ripping and copying haven’t been specifically forbidden. What are the important differences between these concepts?
Ripping is the act of transferring files found on physical media, such as an optical disc, to a computer. This act is not technically illegal because it can apply to ripping homemade DVDs. Copying or duplicating home-produced DVDs or Blu-ray discs is likewise legal, so long as the user owns the copyright to the content found on the disc. But what about ripping movies and shows you didn’t produce?
There have been several statements and rulings made by government officials and courts both in the U.S. and the U.K. that affirm the legality of ripping even copyrighted works. In 2012 Congressman Darrell Issa participated in an AMA (Ask Me Anything) event on Reddit. During the session, he was challenged about the legality of ripping legally acquired DVDs and Blu-ray discs.
“You can in fact make personal copies for your own use. A good example would be ripping a DVD so you can play it on your iPad. That use is not prohibited. The MPAA always takes the view that your rights are limited, but for non-commercial use, making a digital copy like you suggest is a-okay,” Issa said.
This statement appears to be in conflict with the rules set forth by both the DMCA and the Librarian of Congress. However, Congressman Issa only mentions ripping copyrighted material; he says nothing about circumventing the copy protections. It was a partial dodge of the question. The asker followed up his question with a request for clarification about circumvention – a request that was ignored by Congressman Issa.
Software Copy Protection Products For Windows
In 2014, a U.K. court legalized making personal copies of legally acquired media for private use. However, this ruling does not touch on the subject of DRM. While Britons may duplicate copyrighted works for noncommercial use, circumvention of DRM protections remains illegal.
Prosecutions and Lawsuits
Despite the efforts of the above-mentioned institutions and individuals, circumventing copy protections remains against the law in the United States, the United Kingdom and most western nations.
Large-scale content creators, such as movie studios, use the anti-circumvention clauses in the DMCA to target software manufacturers that produce applications that circumvent DRM encryptions such as the Content Scramble System (CSS) for DVDs and the Advanced Access Content System (AACS) for Blu-ray discs.
A recent case brought by Advanced Access Content System Licensing Administrator (AACS LA) against the software manufacturer of DVDFab, resulted in the company’s U.S. based domains, such as DVDFab.com, being seized by the U.S. government and their affiliate program ordered to be halted. Representatives of Fengato Software (the maker of DVDFab) didn’t show up to the hearing that resulted in the injunction against them.
Software Copyright Protection
Bottom Line
While it is illegal for an individual to use ripping or copying software to bypass DRM, there have been no notable cases of copyright holders pursuing legal actions against individual users, nor has there been any action taken against publishers who review or otherwise cover products that circumvent DRM. It appears that the manufacturers of the software bear almost all the liability for the illegal use of their products.
What Is CSS?
Content Scramble System, or CSS, is the encryption method that protects discs from piracy. Unlike the protection encryption for Blu-ray (AASC), CSS is no longer being updated to keep up with codebreakers like those found in the programs we reviewed. As such, all these programs can easily decrypt discs so you can make backup copies of the movies and TV shows you have bought and paid for.
Related Product Reviews
Copy protection, also known as content protection, copy prevention and copy restriction, is any effort designed to prevent the reproduction of software, films, music, and other media, usually for copyrightreasons.[1] Various methods have been devised to prevent reproduction so that companies will gain benefit from each person who obtains an authorized copy of their product. Unauthorized copying and distribution accounted for $2.4 billion in lost revenue in the United States alone in the 1990s,[2] and is assumed to be causing impact on revenues in the music and the game industry, leading to proposal of stricter copyright laws such as PIPA. Some methods of copy protection have also led to criticisms because it caused inconvenience for honest consumers, or it secretly installed additional or unwanted software to detect copying activities on the consumer's computer. Making copy protection effective while protecting consumer rights is still an ongoing problem with media publication.
4Methods
4.1Computer software
Terminology[edit]
Media corporations have always used the term copy protection, but critics argue that the term tends to sway the public into identifying with the publishers, who favor restriction technologies, rather than with the users.[3]Copy prevention and copy control may be more neutral terms. 'Copy protection' is a misnomer for some systems, because any number of copies can be made from an original and all of these copies will work, but only in one computer, or only with one dongle, or only with another device that cannot be easily copied.
The term is also often related to, and confused with, the concept of digital rights management. Digital rights management is a more general term because it includes all sorts of management of works, including copy restrictions. Copy protection may include measures that are not digital. A more appropriate term may be 'technological protection measures' (TPMs),[4] which is often defined as the use of technological tools in order to restrict the use or access to a work.
Business rationale[edit]
Copy protection is most commonly found on videotapes, DVDs, computer software discs, video game discs and cartridges, audio CDs and some VCDs.
Airport Control, Working as an air traffic controller can be really tough but you’ll get the hang of it. Earn lots of cash while you make sure that all of the planes land safely in this time management game. 60-Day Money-Back Satisfaction Guarantee! Welcome to Big Fat Simulations, home of the original Airport Madness game series. We build air traffic control games. Airport traffic game. Air Traffic Controller is an online airport simulation game where you direct aircraft on the ground and through controlled airspace. Organize and expedite the flow of air traffic at a major airport. Your mission is to manage the airport avoiding any delays or collisions. Watch out for the planes in the air as for the once on the ground. Enjoy playing Air Traffic Controller, a free online game. Play the latest airport games online at AirportGames.net! We publish the newest airport and air traffic control games so anyone can play them for free!
Many media formats are easy to copy using a machine, allowing consumers to distribute copies to their friends, a practice known as 'casual copying'.
Companies publish works under copyright protection because they believe that the cost of implementing the copy protection will be less than the revenue produced by consumers who buy the product instead of acquiring it through casually copied media.
Opponents of copy protection argue that people who obtain free copies only use what they can get for free, and would not purchase their own copy if they were unable to obtain a free copy. Some even argue that free copies increase profit; people who receive a free copy of a music CD may then go and buy more of that band's music, which they would not have done otherwise.
Some publishers have avoided copy-protecting their products, on the theory that the resulting inconvenience to their users outweighs any benefit of frustrating 'casual copying'.
From the perspective of the end user, copy protection is always a cost. DRM and license managers sometimes fail, are inconvenient to use, and may not afford the user all of the legal use of the product he has purchased.
The term copy protection refers to the technology used to attempt to frustrate copying, and not to the legal remedies available to publishers or authors whose copyrights are violated. Software usage models range from node locking to floating licenses (where a fixed number licenses can be concurrently used across an enterprise), grid computing (where multiple computers function as one unit and so use a common license) and electronic licensing (where features can be purchased and activated online). The term license management refers to broad platforms which enable the specification, enforcement and tracking of software licenses. To safeguard copy protection and license management technologies themselves against tampering and hacking, software anti-tamper methods are used.
Floating licenses are also being referred to as Indirect Licenses, and are licenses that at the time they are issued, there is no actually user who will use them. That has some technical influence over some of their characteristics. Direct Licenses are issued after a certain user requires it. As an example, an activated Microsoft product, contains a Direct License which is locked to the PC where the product is installed.
From business standpoint, on the other hand, some services now try to monetize on additional services other than the media content so users can have better experience than simply obtaining the copied product.[5]
Technical challenges[edit]
From a technical standpoint, it would seem theoretically impossible to completely prevent users from making copies of the media they purchase, as long as a 'writer' is available that can write to blank media. The basic technical fact is that all types of media require a 'player' — a CD player, DVD player, videotape player, computer or video game console. The player has to be able to read the media in order to display it to a human. In turn, then, logically, a player could be built that first reads the media, and then writes out an exact copy of what was read, to the same type of media.
At a minimum, digital copy protection of non-interactive works is subject to the analog hole: regardless of any digital restrictions, if music can be heard by the human ear, it can also be recorded (at the very least, with a microphone and tape recorder); if a film can be viewed by the human eye, it can also be recorded (at the very least, with a video camera and recorder). In practice, almost-perfect copies can typically be made by tapping into the analog output of a player (e.g. the speaker output or headphone jacks) and, once redigitized into an unprotected form, duplicated indefinitely. Copying text-based content in this way is more tedious, but the same principle applies: if it can be printed or displayed, it can also be scanned and OCRed. With basic software and some patience, these techniques can be applied by a typical computer-literate user.
Since these basic technical facts exist, it follows that a determined individual will definitely succeed in copying any media, given enough time and resources. Media publishers understand this; copy protection is not intended to stop professional operations involved in the unauthorized mass duplication of media, but rather to stop 'casual copying'.
Copying of information goods which are downloaded (rather than being mass-duplicated as with physical media) can be inexpensively customized for each download, and thus restricted more effectively, in a process known as 'traitor tracing'. They can be encrypted in a fashion which is unique for each user's computer, and the decryption system can be made tamper-resistant.
Methods[edit]
For information on individual protection schemes and technologies, see List of copy protection schemes or relevant category page.
Computer software[edit]
Copy protection for computer software, especially for games, has been a long cat-and-mouse struggle between publishers and crackers. These were (and are) programmers who would defeat copy protection on software as a hobby, add their alias to the title screen, and then distribute the 'cracked' product to the network of warezBBSes or Internet sites that specialized in distributing unauthorized copies of software.
Early ages [edit]
When computer software was still distributed in audio cassettes, audio copying was unreliable, while digital copying was time consuming. Software prices were comparable with audio cassette prices.[2][6] To make digital copying more difficult, many programs used non-standard loading methods (loaders incompatible with standard BASIC loaders, or loaders that used different transfer speed).
Unauthorized software copying began to be a problem when floppy disks became the common storage media.[6] The ease of copying depended on the system; Jerry Pournelle wrote in BYTE in 1983 that 'CP/M doesn't lend itself to copy protection' so its users 'haven't been too worried' about it, while 'Apple users, though, have always had the problem. So have those who used TRS-DOS, and I understand that MS-DOS has copy protection features'.[7] Apple and Commodore 64 computers were extremely varied and creative because most of the floppy disk reading and writing was controlled by software (or firmware), not by hardware. The first copy protection was for cassette tapes and consisted of a loader at the beginning of the tape, which read a specially formatted section which followed.
The first protection of floppy disks consisted of changing the address marks, bit slip marks, data marks, or end of data marks for each sector. For example, Apple’s standard sector markings were:
D5 AA 96 for the address mark. That was followed by track, sector, and checksum.
DE AA EB concluded the address header with what are known as bit slip marks.
D5 AA AD was used for the data mark and the end of data mark was another DE AA EB.
Changing any of these marks required fairly minimal changes to the software routines in Apple DOS which read and wrote the floppy disk, but produced a disk that could not be copied by any of the standard copiers, such as Apple's COPYA program. Some protection schemes used more complicated systems that changed the marks by track or even within a track.
1980s Locksmith[edit]
Pournelle disliked copy protection and, except for games, refused to review software that used it. He did not believe that it was useful, writing in 1983 that 'For every copy protection scheme there's a hacker ready to defeat it. Most involve so-called nibble/nybble copiers, which try to analyze the original disk and then make a copy'.[7]IBM's Don Estridge agreed: 'I guarantee that whatever scheme you come up with will take less time to break than to think of it.' While calling piracy 'a threat to software development. It's going to dry up the software', he said 'It's wrong to copy-protect programs .. There ought to be some way to stop [piracy] without creating products that are unusable.'[8]
By 1980, the first 'nibble' copier, Locksmith, was introduced. These copiers reproduced copy protected floppy disks an entire track at a time, ignoring how the sectors were marked. This was harder to do than it sounds for two reasons: firstly, Apple disks did not use the index hole to mark the start of a track; their drives could not even detect the index hole. Tracks could thus start anywhere, but the copied track had to have this 'write splice', which always caused some bits to be lost or duplicated due to speed variations, roughly in the same (unused for payload data) place as the original, or it would not work. Secondly, Apple used special 'self-sync' bytes to achieve agreement between drive controller and computer about where any byte ended and the next one started on the disk. These bytes were written as normal data bytes followed by a slightly longer than normal pause, which was notoriously unreliable to detect on read-back; still, you had to get the self-sync bytes roughly right as without them being present in the right places, the copy would not work, and with them present in too many places, the track would not fit on the destination disk. Locksmith copied Apple II disks by taking advantage of the fact that these sync fields between sectors almost always consisted of a long string of FF (hex) bytes. It found the longest string of FFs, which usually occurred between the last and first sectors on each track, and began writing the track in the middle of that; also it assumed that any long string of FF bytes was a sync sequence and introduced the necessary short pauses after writing each of them to the copy. Ironically, Locksmith would not copy itself. The first Locksmith measured the distance between sector 1 of each track. Copy protection engineers quickly figured out what Locksmith was doing and began to use the same technique to defeat it. Locksmith countered by introducing the ability to reproduce track alignment and prevented itself from being copied by embedding a special sequence of nibbles, that if found, would stop the copy process. Henry Roberts (CTO of Nalpeiron), a graduate student in computer science at the University of South Carolina, reverse engineered Locksmith, found the sequence and distributed the information to some of the 7 or 8 people producing copy protection at the time.
For some time, Locksmith continued to defeat virtually all of the copy protection systems in existence. The next advance came from Henry Roberts' thesis on software copy protection, which devised a way of replacing Apple’s sync field of FFs with random appearing patterns of bytes. Because the graduate student had frequent copy protection discussions with Apple’s copy protection engineer, Apple developed a copy protection system which made use of this technique.Henry Roberts then wrote a competitive program to Locksmith, Back It UP. He devised several methods for defeating that, and ultimately a method was devised for reading self sync fields directly, regardless of what nibbles they contained.
Copy protection sometimes caused software to not run on clones, such as the Apple II-compatible Laser 128.[9] The back and forth struggle between copy protection engineers and nibble copiers continued until the Apple II became obsolete and was replaced by the IBM PC and its clones.
In 1989 Gilman Louie, head of Spectrum Holobyte, stated that copy protection added about $0.50 per copy to the cost of production of a game.[10] Other software relied on complexity; Antic in 1988 observed that WordPerfect for the Atari ST 'is almost unusable without its manual of over 600 pages!'.[11] (The magazine was mistaken; the ST version was so widely pirated that the company threatened to discontinue it.[12][13])
1990s CD-R[edit]
Floppy disks were later displaced by CDs as the preferred method of distribution, with companies like Macrovision and Sony providing copy protection schemes that worked by writing data to places on the CD-ROM where a CD-R drive cannot normally write. Such a scheme had been used for the PlayStation and could not be circumvented easily without the use of a modchip.
For software publishers, a less expensive method of copy protection is to write the software so that it requires some evidence from the user that they have actually purchased the software, usually by asking a question that only a user with a software manual could answer (for example, 'What is the 4th word on the 6th line of page 37?'). However, this approach can be exploited with the patience to copy the manual with a photocopier, and it also suffers from the issue of making the product more inconvenient for the end user to use.
Recent practices[edit]
It has become very common for software to require activation by entering some proof of legal purchase such as:

Name & Serial, a name and serial number that is given to the user at the time the software is purchased
A phone activation code, which requires the user to call a number and register the product to receive a computer-specific serial number.
Device ID, specifically tying a copy of software to a computer or mobile device based on a unique identifier only known to that device (like the IMEI of a smartphone).
To limit reusing activation keys to install the software on multiple machines, it has been attempted to tie the installed software to a specific machine by involving some unique feature of the machine. Serial number in ROM could not be used because some machines do not have them. Some popular surrogate for a machine serial number were date and time (to the second) of initialization of the hard disk or MAC address of Ethernet cards (although this is programmable on modern cards). With the rise of virtualization, however, the practice of locking has to add to these simple hardware parameters to still prevent copying.[14]Another approach to associating user and/or machine with serial number is product activation over the Internet, where users are required to have access to the Internet so the information on which serial number is installed on which machine gets sent to a server to be authenticated. Unauthorized users are not allowed to install or use the software. Microsoft's Windows Genuine Advantage system is a far-reaching example of this.With rise of Cloud computing, requiring Internet access is becoming more popular for software verification. Beyond online authentication, a standalone software may be integrated with the cloud so that key data or code is stored online. This could greatly strengthen the protection; for example, the software could store a property file or execute a process needed by the application in the cloud instead on the user's computer.
Problems and criticisms[edit]
The copy protection schemes described above have all been criticized for causing problems for validly licensed users who upgrade to a new machine, or have to reinstall the software after reinitializing their hard disk. Some Internet product activation products allow replacement copies to be issued to registered users or multiple copies to the same license.Like all software, copy-protection software sometimes contains bugs, whose effect may be to deny access to validly licensed users. Most copy protection schemes are easy to crack, and once crackers circumvent the copy protection, the resulting cracked software is then more convenient and hence more valuable than the non-cracked version, because users can make additional copies of the software. Due to this problem, user-interactive copy protection by asking questions from manuals has mostly disappeared.
In his 1976 Open Letter to Hobbyists, Bill Gates complained that 'most of you steal your software.' However, Gates initially rejected copy protection and said 'It just gets in the way.'
There is also the tool of software blacklisting that is used to enhance certain copy protection schemes.
Early video games[edit]
During the 1980s and 1990s, video games sold on audio cassette and floppy disks were sometimes protected with an external user-interactive method that demanded the user to have the original package or a part of it, usually the manual. Copy protection was activated not only at installation, but every time the game was executed.[15][16]
Sometimes the copy protection code was needed not at launch, but at a later point in the game. This helped the gamer to experience the game (e.g. as a demonstration) and perhaps could convince them to buy it by the time the copy protection point was reached.
Several imaginative and creative methods have been employed, in order to be both fun and hard to copy. These include:
The most common method was requiring the player to enter a specific word (often chosen at random) from the manual. A variant of this technique involved matching a picture provided by the game to one in the manual and providing an answer pertaining to the picture (Ski or Die, 4D Boxing and James Bond 007; the Stealth Affair used this technique). Buzz Aldrin's Race Into Space (in the floppy version but not the CD version) required the user to input an astronaut's total duration in space (available in the manual) before the launch of certain missions. If the answer was incorrect, the mission would suffer a catastrophic failure.
Manuals containing information and hints vital to the completion of the game, like answers to riddles (Conquests of Camelot, King's Quest 6), recipes of spells (King's Quest 3), keys to deciphering non-Latin writing systems (Ultima series, see also Ultima writing systems), maze guides (Manhunter), dialogue spoken by other characters in the game (Wasteland, Dragon Wars), excerpts of the storyline (most Advanced Dungeons and Dragons games and Wing Commander I), or a radio frequency to use to communicate with a character to further a game (Metal Gear Solid).
Some sort of code with symbols, not existing on the keyboard or the ASCII code. This code was arranged in a grid, and had to be entered via a virtual keyboard at the request 'What is the code at line 3 row 2?'. These tables were printed on dark paper (Maniac Mansion, Uplink), or were visible only through a red transparent layer (Indiana Jones and the Last Crusade), making the paper very difficult to photocopy. Another variant of this method—most famously used on the ZX Spectrum version of Jet Set Willy—was a card with color sequences at each grid reference that had to be entered before starting the game. This also prevented monochrome photocopying. It had been thought that the codes in the tables were based on a mathematical formula which could be calculated by using the row, line and page number if the formula was known, a function of the disk space requirement of the data. Later research proved that this wasn't the case. [17]
The Secret of Monkey Island offered a rotating wheel with halves of pirate's faces. The game showed a face composed of two different parts and asked when this pirate was hanged on a certain island. The player then had to match the faces on the wheel, and enter the year that appeared on the island-respective hole. Its sequel had the same concept, but with magic potion ingredients. Other games that employed the code wheel system include Star Control.
Zork games such as Beyond Zork and Zork Zero came with 'feelies' which contained information vital to the completion of the game. For example, the parchment found from Zork Zero contained clues vital to solving the final puzzle. However, whenever the player attempts to read the parchment, they are referred to the game package.
The Lenslok system used a plastic prismatic device, shipped with the game, which was used to descramble a code displayed on screen.
All of these methods proved to be troublesome and tiring for the players, and as such greatly declined in usage by the mid-1990s, at which point the emergence of CDs as the primary video game medium made copy protection largely redundant, since CD copying technology was not widely available at the time.[15]
While not strictly a software protection, some game companies offered 'value-added' goodies with the package, like funny manuals, posters, comics, storybooks or fictional documentation concerning the game (e.g. the Grail Diary for Indiana Jones or a police cadet notebook with Police Quest or the Hero's manual of Quest for Glory or a copy of the National Inquisitor newspaper in Zak McKracken) in order to entice gamers to buy the package. This trend is re-emerging in modern gaming as an incentive to both buy games and discourage their resale; some games like Forza Motorsport 3 and Dragon Age: Origins provide bonus in-game material that will only be given if one buys the game new.
Video game console systems[edit]
When Sega's Dreamcast was released in 1998, it came with a newer disc format, called the GD-ROM. Using a modified CD player, one could access the game functionality. Using a special swap method could allow reading a GD-ROM game through a CD-ROM just using common MIL-CD (standard CD Boot loading, commonly found on Windows Installation Discs, Linux Live CDs, and others). Dreamcasts sold after October 2000 contain a newer firmware update, not allowing MIL-CD boot.
The Xbox has a specific function: Non-booting or non-reading from CDs and DVD-Rs as a method of game copy protection. Also, the Xbox is said to use a different DVD file system (instead of UDF). It has been theorized that the discs have a second partition that is read from the outside in (opposite current standards thus making the second partition unreadable in PC DVD drives) which give the tracks the appearance that the disc was spun backwards during manufacture. The Xbox 360 copy protection functions by requesting the DVD drive compute the angular distance between specific data sectors on the disc. A duplicated DVD will return different values than a pressed original would.
The PlayStation 2 has a map file that contains all of the exact positions and file size info of the CD in it, which is stored at a position that is beyond the file limit. The game directly calls the position at where the map file is supposed to be. This means that if the file is moved inside the limit, it is useless since the game is looking outside the limit for it, and the file will not work outside of the limit, making any copied disc unusable without a mod chip or the use of FMCB (free memory card boot). FMCB uses the memory card to trick the built-in DVD video software into booting copied games. Before a copied game can be played, it must have been patched with a free application.
Free Copy Protection Software
Nintendo's Wii and Nintendo GameCube have their own specialty format for copy protection. It is based on DVD/miniDVD (Game Cube) technology; each disc contains some deliberately placed defects. The exact positions of these defects, which differ for each produced disc, is encoded encrypted in the BCA of each disc. The BCA is readable on most standard DVD-ROM Drives, but consumer burners can reproduce neither the BCA nor the defects. As an additional obfuscation mechanism, the on-disc sector format is a little bit different from normal DVDs. Nevertheless, it can be read using some consumer DVD-ROM drives with a firmware modification or 'debug mode'. It is also possible to hack the Wii to install unlicensed software, some of which can use the Wii's own drive to create disc images and then play these copies.
The PSP, except the PSP Go, uses the Universal Media Disc, a media format similar to a MiniDisc. It holds about 1.2 GB. Although it cannot be copied, one can make an ISO image (a file version of the UMD) on a memory card and play it on custom firmware, which can be installed on the PSP.
The PlayStation 3, Xbox One, and PlayStation 4 use Blu-ray BD-ROM discs. In addition to any protection provided by the consoles themselves, the BD-ROM format's specification allows for a ROM-Mark which cannot be duplicated by consumer-level recorders. While the BD-ROM format does provide considerable capacity (up to 100 gigabytes per disc with potential revision to provide more), increased consumer bandwidth availability combined with the increased size of games distributed through online channels (approaching 100 gigabytes for some titles) is rendering this point moot. To prevent the consoles themselves being hacked and used as a means to defeat these protections (as happened with the Wii and partially with the PlayStation 3), contemporary consoles employ trusted hardware paths that authenticate the internal hardware and software prior to operation.
Some game developers, such as Markus Persson,[18] have encouraged consumers and other developers to embrace the reality of unlicensed copying and utilize it positively to generate increased sales and marketing interest.
Videotape[edit]
Companies such as Macrovision and Dwight Cavendish provided schemes to videotape publishers making copies unusable if they were created with a normal VCR. All major videotape duplicators licensed Macrovision or similar technologies to copy protect video cassettes for their clients or themselves.
Starting in 1985 with the video release of The Cotton Club (Beta and VHS versions only), Macrovision licensed to publishers a technology that exploits the automatic gain control feature of VCRs by adding pulses to the vertical blanking sync signal.[19] These pulses do not affect the image a consumer sees on his TV, but do confuse the recording-level circuitry of consumer VCRs. This technology, which is aided by U.S. legislation mandating the presence of automatic gain-control circuitry in VCRs, is said to 'plug the analog hole' and make VCR-to-VCR copies impossible, although an inexpensive circuit is widely available that will defeat the protection by removing the pulses. Macrovision has patented methods of defeating copy prevention,[20] giving it a more straightforward basis to shut down manufacture of any device that descrambles it than often exists in the DRM world.
Another form of copy protection, MicroVision, was designed to prevent VCRs from recording a television program. Cable movie channels rejected it; Michael J. Fuchs of HBO said in 1985 that MicroVision was 'not good technology' because it reduced picture quality and consumers could easily bypass it, while Peter Chernin of Showtime said 'we want to accommodate our subscribers and we know they like to tape our movies'.[21]
Audio CDs[edit]
Consumer CD recorders included the Serial Copy Management System (SCMS), which allowed copies to be made from an original, but did not allow a copy of a copy. Professional equipment, including all computer drives, ignores SCMS. Since computer drives ignored SCMS, copies could be made freely, which led to record labels introducing additional copy protection measures.
By 2000, Napster had seen mainstream adoption, and several music publishers responded by starting to sell some CDs with various copy protection schemes. Most of these were playback restrictions that aimed to make the CD unusable in computers with CD-ROM drives, leaving only dedicated audio CD players for playback. This did not, however, prevent such a CD from being copied via an analogue connection or by ripping the CD under operating systems such as Linux, which was effective since copy-protection software was generally written for Microsoft Windows. These weaknesses led critics to question the usefulness of such protection.
CD copy protection is achieved by assuming certain feature levels in the drives. The CD Digital Audio is the oldest CD standard and forms the basic feature set beyond which dedicated audio players need no instructions. CD-ROM drives additionally need to support mixed mode CDs (combined audio and data tracks) and multi-session CDs (multiple data recordings each superseding and incorporating data of the previous session).
The play preventions in use intentionally deviate from the standards and intentionally include malformed multisession data or similar with the purpose of confusing the CD-ROM drives to prevent correct function. Simple dedicated audio CD players would not be affected by the malformed data since these are for features they do not support—for example, an audio player will not even look for a second session containing the copy protection data.
In practice, results vary wildly. CD-ROM drives may be able to correct the malformed data and still play them to an extent that depends on the make and version of the drive. On the other hand, some audio players may be built around drives with more than the basic features required for audio playback. Some car radios with CD playback, portable CD players, CD players with additional support for data CDs containing MP3 files, and DVD players have had problems with these CDs.
The deviation from the Red Book standard that defines audio CDs required the publishers of these copy-protected CDs to refrain from using the official CDDA logo on the discs or the cases. The logo is a trademark owned by Philips and Sony and licensed to identify compliant audio discs only. To prevent dissatisfied customers from returning CDs which were misrepresented as compliant audio CDs, such CDs also started to carry prominent notices on their covers.
In general the audio can always be extracted by applying the principle of the analog hole. Additionally, such programs as IsoBuster may be capable of producing hidden audio files.
Examples of CD copy protection schemes are Cactus Data Shield, Copy Control, and Data Position Measurement.
Other digital media[edit]
More recently,[when?] publishers of music and films in digital form have turned to encryption to make copying more difficult. CSS, which is used on DVDs, is a famous example of this. It is a form of copy protection that uses 40-bit encryption. Copies will not be playable since they will be missing the key, which is not writable on regular DVD-R or DVD-RW discs (except with special Qflix DVD-recorders and media). With this technique, the work is encrypted using a key only included in the firmware of 'authorized' players, which allow only 'legitimate' uses of the work (usually restricted forms of playback, but no conversion or modification). The controversial Digital Millennium Copyright Act provides a legal protection for this in the US, that would make it illegal to distribute 'unauthorized' players—which was supposed to eliminate the possibility of building a DVD copier. However, encryption schemes designed for mass-market standardized media such as DVD suffer from the fundamental weaknesses that consumers have physical access to the devices containing the keys, and once implemented, the copy-protection scheme can never be changed without breaking the forward compatibility of older devices (or the backward compatibility of newer media). Since consumers are highly unlikely to buy new hardware for the sole purpose of preserving copy protection, manufacturers have been prevented from enhancing their DRM technology until recently, with the release of next-generation media such as HD DVD and Blu-ray Disc. This period represents more than enough time for the encryption scheme to be defeated by determined attackers. For example, the CSS encryption system used on DVD Video was broken within three years of its market release in November 1996 (see DeCSS), but has not been changed since, because doing so would immediately render all DVD players sold prior to the change incapable of reading new DVDs—this would not only provoke a backlash amongst consumers, but also restrict the market that the new DVDs could be sold to. More recent DVDs have attempted to augment CSS with additional protection schemes. Most modern schemes like ARccOS Protection use tricks of the DVD format in an attempt to defeat copying programs, limiting the possible avenues of protection—and making it easier for hackers to learn the innards of the scheme and find ways around it.
The newest generations of optical disc media, HD DVD and Blu-ray Disc, attempt to address this issue. Both formats employ the Advanced Access Content System, which provides for several hundred different decryption keys (for the varying models of players to hit the market), each of which can be invalidated ('revoked') should one of the keys be compromised. Revoked keys simply will not appear on future discs, rendering the compromised players useless for future titles unless they are updated to fix the issue. For this reason, all HD-DVD players and some Blu-ray players include an ethernet port, to give them the ability to download DRM updates. Blu-ray Disc goes one step further with a separate technique called BD+, a virtual machine that can execute code included on discs to verify, authorize, revoke, and update players as the need arises. Since the protection program is on the disc rather than the player, this allows for updating protection programs within BD's working life by simply having newer programs included on newer discs.
4K resolution Blu-ray discs augment the existing Blu-ray protections. First, players must be dedicated devices that use protected hardware paths to ensure the entire process chain (from media to display) is not compromised. Second, some media require the use of players able to access the Internet for additional verification.
Notable payloads[edit]
Over time, software publishers (especially in the case of video games) became creative about crippling the software in case it was duplicated. These games would initially show that the copy was successful, but eventually render themselves unplayable via subtle methods.Many games use the 'code checksumming' technique to prevent alteration of code to bypass other copy protection. Important constants for the game - such as the accuracy of the player's firing, the speed of their movement, etc. - are not included in the game but calculated from the numbers making up the machine code of other parts of the game. If the code is changed, the calculation yields a result which no longer matches the original design of the game and the game plays improperly.
Superior Soccer had no outward signs of copy protection, but if it decided it was not a legitimate copy, it would make the soccer ball in the game invisible, making it impossible to play the game.
In Sid Meier's Pirates, if the player entered in the wrong information, they could still play the game, but the difficulty would be increased substantially.
As a more satirical nod to the issue, if the thriller-action game Alan Wake detects that the game is cracked or a pirated copy, it will replace tips in loading screens with messages telling the player to buy the game. If a new game is created on the copied game, an additional effect will take place. As a more humorous nod to 'piracy', Alan Wake will gain a black Eyepatch over his right eye, complete with a miniature Jolly Roger.
While the copy protection in Zak McKracken and the Alien Mindbenders was not hidden as such, the repercussions of missing the codes was unusual: the player would end up in jail (permanently), and the police officer would give a lengthy and condescending speech about software copying.
In case of copied versions of Settlers 3, the iron smelters would only produce pigs (a play on pig iron); weaponsmiths require iron to produce weapons, so players couldn't amass arms.[22]
Bohemia Interactive Studio developed a unique and very subtle protection system for its game Operation Flashpoint: Cold War Crisis. Dubbed FADE, if it detects an unauthorized copy, it does not inform the player immediately but instead progressively corrupts aspects of the game (such as reducing the weapon accuracy to zero) to the point that it eventually becomes unplayable. The message 'Original discs don't FADE' will eventually appear if the game is detected as being an unauthorized copy.
FADE is also used in ArmA II, and will similarly diminish the accuracy of the player’s weapons, as well as induce a “drunken vision” effect, where the screen becomes wavy, should the player be playing on an unauthorized copy. [23]
This system would also be used in Take On Helicopters, where the screen would blur and distort when playing a counterfeit copy, making it hard to safely pilot a helicopter.[24]
The IndyCar Series (2003 video game) also utilizes FADE technology to safeguard against piracy by making races very difficult to win on a pirated version. The penultimate section of the game’s manual states:
Copying commercial games, such as this one, is a criminal offense and copyright infringement.
Copying and re-supplying games such as this one can lead to a term of imprisonment.
Think of a pirated game as stolen property.
This game is protected by the FADE system. You can play with a pirated game- but not for long. The quality of a pirated game will degrade over time.
Purchase only genuine software at legitimate stores.
Batman: Arkham Asylum contained code that disabled Batman's glider cape, making some areas of the game very difficult to complete and a certain achievement/trophy impossible to unlock (gliding continuously for over 100m).[25]
The PC version of Grand Theft Auto IV has a copy protection that swings the camera as though the player was drunk. If the player enters a vehicle it will automatically throttle, making it difficult to steer. It also damages the vehicle, making it vulnerable to collisions and bullets. An update to the game prevented unauthorised copies from accessing the in-game web browser, making it impossible to finish the game as some missions involve browsing the web for objectives.
EarthBound is well-documented for its extensive use of checksums to ensure that the game is being played on legitimate hardware. If the game detects that it is being played on a European SNES, it refuses to boot, as the first of several checksums has failed. A second checksum will weed out most unauthorized copies of the game, but hacking the data to get past this checksum will trigger a third checksum that makes enemy encounters appear much more often than in an authorized copy, and if the player progresses through the game without giving up (or cracks this protection), a final checksum code will activate before the final boss battle, freezing the game and deleting all the save files.[26] A similar copy protection system was used in Spyro: Year of the Dragon, although it only uses one copy protection check at the beginning of the game (see below).
In an unauthorized version of the PC edition of Mass Effect, the game save mechanism would not work and the in-game galactic map would cause the game to crash. As the galactic map is needed to travel to different sections of the game, the player would be stuck in the first section of the game.
If an unauthorized version of The Sims 2 was used, the Build Mode would not work properly. Walls would not be able to be built on the player's property, which prevents the player from building any custom houses. Some furniture and clothing selections would not be available either.
A March 2009 update to the BeeJive IM iPhone app included special functionality for users of the unauthorized version: the screen would read 'PC LOAD LETTER' whenever the user tried to establish a connection to any IM service, then quickly switch to a YouTube clip from the movie Office Space.[27]
Red Alert 2 and The Lord of the Rings: The Battle for Middle-Earth have a copy protection system that completely wipes out the player's forces briefly after a battle begins on an unlicensed copy. However, some who purchased the latter have encountered a bug that caused this copy protection scheme to trigger when it was not supposed to.
If a player pirated the Nintendo DS version of Michael Jackson: The Experience, vuvuzela noises will play over the notes during a song, which then become invisible. The game will also freeze if the player tries to pause it.
Older versions of Autodesk 3ds Max use a dongle for copy protection; if it is missing, the program will randomly corrupt the points of the user's model during usage, destroying their work.
Older versions of CDRWIN used a serial number for initial copy protection. However, if this check was bypassed, a second hidden check would activate causing a random factor to be introduced into the CD burning process, producing corrupted 'coaster' disks.
Terminate, a BBS terminal package, would appear to operate normally if cracked but would insert a warning that a pirated copy was in use into the IEMSI login packet it transmitted, where the sysop of any BBS the user called could clearly read it.
Ubik's Musik, a music creation tool for the Commodore 64, would transform into a Space Invaders game if it detected that a cartridge-based copying device had attempted to interrupt it. This copy protection system also doubles as an easter egg, as the message that appears when it occurs is not hostile ('Plug joystick in port 1, press fire, and no more resetting/experting!').
The Amiga version of Bomberman featured a multitap peripheral that also acted as a dongle. Data from the multitap was used to calculate the time limit of each level. If the multitap was missing, the time limit would be calculated as 0, causing the level to end immediately.
Nevermind, a puzzle game for the Amiga, contained code that caused an unlicensed version of the game to behave as a demo. The game would play three levels sampled from throughout the game, and then give the message 'You have completed three levels; however there are 100 levels to complete on the original disc.'
In Spyro: Year of the Dragon a character named Zoe will tell the player outside the room containing the balloon to Midday Garden Home and several other areas that the player is using an unlicensed copy. This conversation purposely corrupts data. When corrupted, the game would not only remove stray gems and the ability to progress in certain areas but also make the final boss unbeatable, returning the player to the beginning of the game (and removing the save file at the same time) after about 8 seconds into the battle.[28]
The Atari Jaguar console would freeze at startup and play the sound of an enraged jaguar snarling if the inserted cartridge failed the initial security check.
The Lenslok copy protection system gave an obvious message if the lens-coded letters were entered incorrectly, but if the user soft-reset the machine, the areas of memory occupied by the game would be flooded with the message 'THANK YOU FOR YOUR INTEREST IN OUR PRODUCT. NICE TRY. LOVE BJ/NJ' to prevent the user examining leftover code to crack the protection.
An update to the sandbox game Garry's Mod enabled a copy protection mechanism that outputs the error 'Unable to shade polygon normals' if the game detects that it has been copied. The error also includes the user's Steam ID as an error ID, meaning that users can be identified by their Steam account when asking for help about the error over the Internet.
The Atari version of Alternate Reality: The Dungeon would have the player's character attacked by two unbeatable 'FBI Agents' if it detected a cracked version. The FBI agents would also appear when restoring a save which was created by such a version, even if the version restoring the save was legal.
VGA Planets, a play-by-BBS strategy game, contained code in its server which would check all clients' submitted turns for suspect registration codes. Any player deemed to be using a cracked copy, or cheating in the game, would have random forces destroyed throughout the game by an unbeatable enemy called 'The Tim Continuum' (after the game's author, Tim Wissemann). A similar commercial game, Stars!, would issue empty turn updates for players with invalid registration codes, meaning that none of their orders would ever be carried out.
On a copied version of the original PC version of Postal, as soon as the game was started, the player character would immediately shoot himself in the head.
In Serious Sam 3: BFE, if the game code detects what it believes to be an unauthorized copy, an invincible scorpion-like monster is spawned in the beginning of the game with high speeds, melee attacks, and attacks from a range with twin chainguns making the game extremely difficult and preventing the player to progress further. Also in the level 'Under the Iron Cloud', the player's character will spin out-of-control looking up in the air.[29]
An unauthorized copy of Pokémon Black and White and their sequels will run as if it was normal, but the Pokémon will not gain any experience points after a battle. This has since been solved by patching the game's files.
If Ace Attorney Investigations 2 detects an illegitimate or downloaded copy of the game, it will convert the entire game's text into the game's symbol based foreign language, Borginian, which cannot be translated in any way.
The unlicensed version of indie game Game Dev Tycoon, in which the player runs a game development company, will dramatically increase the piracy rate of the games the player releases to the point where no money can be made at all, and disable the player's ability to take any action against it [30][31]
In Crytek's Crysis, if the player uses a naive copy of the game, his bullets are replaced by harmless chickens, making it almost impossible to beat the game without cracking the game.
In Crytek's Crysis 3, if a player used an unlicensed copy of the game, he is not able to defeat the last boss (The Alpha Ceph), thus making it impossible to beat the game.
In an unauthorized copy of Five Nights at Freddy's, the player can still play the game normally, but will be unable to exit until he/she is defeated by an animatronic enemy, with frightening noises.
In Mirror's Edge, during the game, the player's character starts to slow down making it impossible to jump over ledges and proceed further in the game.
The usage of copy protection payloads which lower playability of a game without making it clear that this is a result of copy protection is now generally considered unwise, due to the potential for it to result in unaware players with unlicensed copies spreading word-of-mouth that a game is of low quality. The authors of FADE explicitly acknowledged this as a reason for including the explicit warning message.
Anti-piracy[edit]
Anti-piracy measures are efforts to fight against copyright infringement, counterfeiting, and other violations of intellectual property laws.
Cd Copy Protection Software
It includes, but is by no means limited to, the combined efforts of corporate associations (such as the RIAA and MPAA), law enforcement agencies (such as the FBI and Interpol), and various international governments[clarification needed] to combat copyright infringement relating to various types of creative works, such as software, music and films. These measures often come in the form of copy protection measures such as DRM, or measures implemented through a content protection network, such as Distil Networks or Incapsula. Richard Stallman and the GNU Project have criticized the use of the word 'piracy' in these situations, saying that publishers use the word to refer to 'copying they don't approve of' and that 'they [publishers] imply that it is ethically equivalent to attacking ships on the high seas, kidnapping and murdering the people on them'.[32] Certain forms of Anti-Piracy (such as DRM), are considered by consumers to control the use of the products content after sale.
In the case MPAA v. Hotfile, Judge Kathleen M. Williams granted a motion to deny the prosecution the usage of words she views as 'pejorative'. This list included the word 'piracy', the use of which, the motion by the defense stated, would serve no purpose but to misguide and inflame the jury. The plaintiff argued the common use of the terms when referring to copyright infringement should invalidate the motion, but the Judge did not concur.[33]
Anti-piracy in file sharing[edit]
Today copyright infringement is often facilitated by the use of file sharing. In fact, infringement accounts for 23.8% of all internet traffic in 2013.[34] In an effort to cut down on this, both large and small film and music corporations have issued DMCA takedown notices, filed lawsuits, and pressed criminal prosecution of those who host these file sharing services.[35][36][37][38]
Other examples[edit]
On June 30, 2010, U.S. Immigration and Customs Enforcement (ICE) cracked down on many video-hosting websites including NinjaVideo.
RIAA sues file-sharers that share music over P2P networks.
The MPAA encrypts DVD movies using the CSS cipher, prohibiting the distribution and use of DeCSS, while also having the effect of banning free/open source DVD player software.
'Coded Anti-Piracy', also called CAP codes, are utilized to put a forensic identification on films to trace back any illegal copies of them back to the source.
Metal Gear Solid and many other computer games require a piece of information from the game's jewel case for the player to progress after a certain point, making unauthorized copies effectively worthless without the original jewel case; however, in the present day, said information can be easily be found on the Internet.
Microsoft removes Windows Vista and Microsoft Office from various torrent trackers.
Certain SNES games such as Super Mario All Stars and Donkey Kong Country may sometimes show warning screens, usually caused by dirty or damaged cartridges or use of third-party peripherals.
Rockman EXE Operate Shooting Star has anti-copying code that causes every step the player takes to reveal an enemy, also in an unauthorized copy.
Classic NES Series features a 'mirroring'. If a Classic NES Series game is emulated or the cart doesn't feature 'mirroring', the player will fall victim to copy protection. For example, in 'Classic NES Series - Castlevania', the player becomes unable to move the character at all.
See also[edit]
References[edit]
^Thomas Obnigene, DVD Glossary, filmfodder.com 2007. Retrieved July 19, 2007.
^ abGreg Short, Comment, Combatting Software Piracy: Can Felony Penalties for Copyright Infringement Curtail the Copying of ComputerSoftware?, 10 Santa Clara Computer & High Tech. L.J. 221 (1994).Available at: http://digitalcommons.law.scu.edu/chtlj/vol10/iss1/7
^Confusing Words and Phrases that are Worth Avoiding, GNU Project - Free Software Foundation (FSF).
^How do technological protection measures work?Archived 2013-06-14 at the Wayback Machine, World Intellectual Property Organization
^Wallach, D.S. (Oct 2011). 'Copy protection technology is doomed'. Computer. 34 (10): 48–49. doi:10.1109/2.955098.
^ abCopy Protection: A History and Outlook http://www.studio-nibble.com/countlegger/01/HistoryOfCopyProtection.html
^ abPournelle, Jerry (June 1983). 'Zenith Z-100, Epson QX-10, Software Licensing, and the Software Piracy Problem'. BYTE. p. 411. Retrieved 20 October 2013.
^Curran, Lawrence J.; Shuford, Richard S. (November 1983). 'IBM's Estridge'. BYTE. pp. 88–97. Retrieved 19 March 2016.
^Mace, Scott (1986-01-13). 'Two Firms Plan to Sell Apple Clone'. InfoWorld.
^Louie, Gilman (April 1989). 'Low Shelf 'ST'eem'. Computer Gaming World (letter). p. 4.
^Pearlman, Gregg (May 1988). 'WordPerfect ST / Proving why it's the IBM PC best seller'. Antic. Vol. 7 no. 1.
^'Word Perfect Furor'.
^'ST USER'.
^Dominic Haigh (2010-06-28). 'Copy protection on virtual systems'. Archived from the original on 2010-06-08. Retrieved 2010-12-06.
^ ab'The Next Generation 1996 Lexicon A to Z: Copy Protection'. Next Generation. No. 15. Imagine Media. March 1996. p. 32.
^Retro Gamer issue 83, 'Don't copy that floppy'
^'Copy Protection in Jet Set Willy: developing methodology for retrogame archaeology'. Retrieved January 30, 2019.
^'Please Steal My Game'. getminecraftforfree.org. Retrieved 3 August 2013.
^Some relevant patents are U.S. Patent 4,631,603; U.S. Patent 4,577,216; U.S. Patent 4,819,098; and U.S. Patent 4,907,093.
^One such patent is U.S. Patent 5,625,691.
^Holsopple, Barbara (1985-06-05). 'Pay-TV looks elsewhere as theatrical movies lose their appeal'. The Pittsburgh Press. pp. C12. Retrieved 25 January 2015.
^Sven Liebich, Germany. 'Settlers3.com'. Settlers3.com. Archived from the original on 2001-03-04. Retrieved 2010-12-06.
^'FADE Game Copy Protections'. GameBurnWorld. Retrieved 2010-12-06.
^'Bohemia Interactive Details Unique Anti-Piracy Methods'. GamePolitics.
^'Afterdawn.com'. Afterdawn.com. 2009-09-09. Retrieved 2010-12-06.
^'MOTHER 2 / EarthBound Anti-Piracy Measures'. Starmen.Net. Retrieved 2010-12-06.
^'Beejive IM Moves To Block Out iPhone Pirates'. washingtonpost.com. 2009-03-19. Retrieved 2010-12-06.
^Dodd, Gavin (2001-10-17). 'Keeping the Pirates at Bay: Implementing Crack Protection for Spyro: Year of the Dragon'. Gamasutra. Archived from the original on 2008-03-26. Retrieved 2008-03-28.
^Walker, John. 'Serious Sam's DRM Is A Giant Pink Scorpion'. Rock, Paper, Shotgun.
^Patrick (April 29, 2013). 'What happens when pirates play a game development simulator and then go bankrupt because of piracy?'.
^Ernesto (April 29, 2013). 'Game Pirates Whine About Piracy in Game Dev Simulator'. TorrentFreak.
^Stallman, Richard. 'Confusing Words and Phrases That Are Worth Avoiding'. Free Software, Free Society: The Selected Essays of Richard M. Stallman. GNU Press. Archived from the original on 31 May 2010. Retrieved June 1, 2010.
^'MPAA Banned From Using Piracy and Theft Terms in Hotfile Trial'. Archived from the original on 30 November 2013. Retrieved November 30, 2013.
^Boorstin, Julia (January 31, 2011). 'Piracy Rules the Web, Dominating 23.8% of Internet Traffic'. CNBC Media Money. Retrieved 28 May 2013.
^Masnick, Mike (May 29, 2012). 'Fox Issues DMCA Takedown To Google Over SF Chronicle Article.. Claiming It Was The Movie 'Chronicle''. Techdirt. Retrieved 28 May 2013.
^Menta, Rich. 'RIAA Sues Music Startup Napster for $20 Billion'. MP3Newswire. Retrieved 28 May 2013.
^enigmax (April 17, 2009). 'The Pirate Bay Trial: The Official Verdict – Guilty'. TorrentFreak. Retrieved 28 May 2013.
^Boorstin, julia (2013-02-06). 'The Weakest Link'. The Hindu. Chennai, India.
External links[edit]
Disk Preservation Project Discusses and analyzes protections used on old floppy-based systems.
Retrieved from 'https://en.wikipedia.org/w/index.php?title=Copy_protection&oldid=918547513'

0 notes
Text
Dfs Evolution Cracked

In 1990 he released the debut album, featuring the mix of rap and hard rock. Its lead-single's too sexual lyrics Yodelin' In The Valley was the reason for a scandal. https://shadowychopshopreview.tumblr.com/post/638386767662317568/kid-rock-born-free-mp3.
Air traffic control game airport madness 4. Air Traffic Controller is an online airport simulation game where you direct aircraft on the ground and through controlled airspace. Organize and expedite the flow of air traffic at a major airport. Your mission is to manage the airport avoiding any delays or collisions. Watch out for the planes in the air as for the once on the ground. Enjoy playing Air Traffic Controller, a free online game.
Jun 22, 2018 In this video guide, we will be covering how you can deploy software updates in Microsoft SCCM. This covers important aspects of deploying updates such as collection structure, maintenance windows. Jun 22, 2018 Overview. In this video guide, we will be covering how you can deploy software updates in Microsoft SCCM. This covers important aspects of deploying updates such as collection structure, maintenance windows, automatic deployment rules (ADRs), deadlines, and much more. Nov 27, 2018 Automatically deploy software updates. Configure automatic software updates deployment by using an automatic deployment rule (ADR). This method of deployment is common for monthly software updates (typically known as 'Patch Tuesday') and for managing definition updates. You define the criteria for an ADR to automate the deployment process. May 20, 2019 In this post we will see how to deploy software updates using SCCM. Deploying the software updates for the computers is essential. To stay protected against cyber-attacks and malicious threats, it is very important that you keep the computers patched with latest software updates. Using sccm for windows updates.
Dfs Evolution Torrent
Dfs Evolution Crack
Dfs Evolution Cracked Download
Dfs Evolution Cracked Screen
Dfs Evolution Cracked Pc
DFS CDMA Tool v14.03.26.0 Evolution Unlimited cracked DFS CDMA Tool v14.03.26.0 Evolution Unlimited This is the full cracked version of the software. Download, extract, install, enjoy. Inside the archive there is 'crack' folder wich contains everything you need to crack the software. Download CDMA tool. DFS software. Manuals: Tools: © DFS 2005-2019. Crack.DFS.CDMA.Tool.Evolution.v4.0.0.3.rar shurll.com/74gfh.
This is the full cracked version of the software. Download, extract, install, enjoy.
Inside the archive there is'crack' folder wich contains everything you need to crack the software.
https://safelinking.net/p/ab37b12ed0
Automatic detect model and update software, download files from server
No waiting for shipping, CDMA Tool You download from our website
Unlock SPC, MSL, SPC3, FSK, OTKSL, User Lock, MIN lock, SIM LOCK
Programming: MIN, MDN, IMSI, NAM, PRL file, Phone Settings
EFS Explorer: EFS EFS2 CEFS supported, reading locked efs folders
AT Commandand modem test utility
Change/Reset RF calibration data
Rebuild/Clear EEPROM, NVM, EFS area
Repair software. Emergency Download
Repair ESN - electronic serial number, MEID, IMEI, MAC address, CS
iPhone4 IOS 7.x.x solution ready!
iPhone 5, iPad 4and iPad mini programming solution is ready! No Jailbreak needed. We are taking preorders from major resellers.
We just do it first! We don't tell a lie. JB evasi0n compatible
Supported models
Aiji BlackBerry Hisense Motorola Samsung Sony Ericsson Vertex Wireless
Alcatel Casio Huawei Novatel Select Wireless SWTech Wetelecom
Anydata Cmotech Hyndai Olive Sharp Techfaith Wireless Zhenhua
Apple Dell Wireless Kyocera Palm Sierra Wireless Telit ZTE
Audiovox Franklin Wireless Lenovo Pantech Sky Telular
Download
DFS v17.10.02.00 Full Activated Tools Download, DFS v17.10.02.00 Full Activated Tools Free Download, Latest Version DFS v17.10.02.00 Full Activated Tools Download, DFS CDMA v17.10.02.00 Full Activated ToolsFull Setup File Download, How To Download DFS CDMA v17.10.02.00 Full Activated Tools, DFS CDMA v17.10.02.00 Full Activated Toolslatest Update 2018 Download, How to setup DFS CDMA v17.10.02.00 Full Activated Tools, DFS CDMA v17.10.02.00 Full Activated Tools Free Download Direct Link, DFS CDMA v17.10.02.00 Full Activated Tools 100% working Free Download many of other search keyword People Daily Search DFS CDMA v17.10.02.00 Full Activated Toolsin google. Today I will share Our Visitor To Free Download Link and Setup instruction Of DFS CDMA v17.10.02.00 Full Activated Tools I Think This post is very helpful For you. If you encountered any problem , feel free to ask just leave a comment and I will answer it as soon as I can.
Sim unlock
Direct unlock
Remove screen lock
Imei repair
Flash
Read info
Read firmware
Dfs Evolution Torrent
File Name: DFS CDMA Full Activated Tools
File type: compressed/Zip File
File Size: 30 MB
Virus status: scanned by Avast security.
Setting this up very easy. once downloaded , navigate to your download folder once that is do. Just extract it with any RAR extractor like Winrar or winzip or 7zip.DFS CDMA v17.10.02.00 Full Activated Tools Free with administrator privilege and that's all it will open a new window with necessary features . If you encountered any problem , feel free to ask just leave a comment and I will answer it as soon as I can. If you find this blog helpful please share it to your friends.
License:DFS CDMA v17.10.02.00 Full Activated Tools is freeware Tool . You may try it free for always.
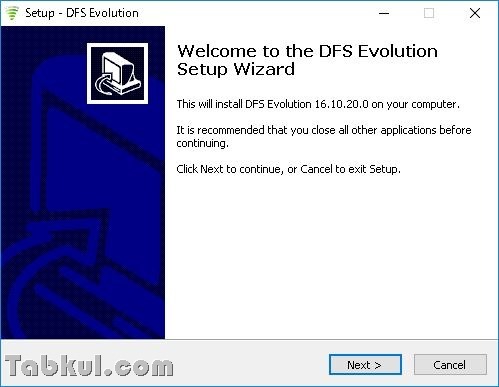
Restrictions on Use:This software must not be decompiled, disassembled, reverse engineered or otherwise modified.
Dfs Evolution Crack
Credit ©:

DFS CDMA v17.10.02.00 Full Activated ToolsTeam All right reserved.
Dfs Evolution Cracked Download
Dfs Evolution Cracked Screen
Compitible:The above Software runs smoothly on windows XP, Windows Vista, Windows 7, Windows 8.1 and Windows 10 (32 bit and 64 bit)
Dfs Evolution Cracked Pc
Download DFS CDMA v17.10.02.00 Full Activated Tools

0 notes
Text
Kid Rock Born Free Mp3

[Verse 1]
Fast, on a rough road riding
High, through the mountains climbing
Twisting, turning further from my home
Young, like a new moon rising
Fierce, through the rain and lightning
Wandering out into this great unknown
And I don't want no one to cry
But, tell them if I don't survive
[Chorus]
I was born free!
I was born free!
I was born free, born free
[Verse 2]
Free, like a river raging
Strong as the wind I’m facing
Chasing dreams and racing father time
Deep like the grandest canyon
Wild like an untamed stallion
If you can’t see my heart you must be blind
You can knock me down and watch me bleed
But you can’t keep no chains on me
[Chorus]
I was born free!
I was born free!
I was born free, born free
[Verse 3]
And I'm not good at long goodbyes
But look down deep into my eyes
I was born free
Calm, facing danger
Lost, like an unknown stranger
Grateful for my time with no regrets
Close to my destination
Tired, frail and aching
Waiting patiently for the sun to set
And when it's done, believe that I
Will yell it from that mountain high
[Chorus]
I was born free!
I was born free!
I was born free, born free
[Outro]
I will bow to the shining sea
And celebrate God's grace on thee
Kid Rock Born Free Cd
Kid Rock Born Free Mp3 Download
Kid Rock Songs Born Free
Kid Rock Born Free Mp3 Download
Kid Rock Born Free Mp3 Download
Biography
Future musician Kid Rock was born on January 17, 1971, in a small rural town of Romeo in state Michigan, the USA, and got the name of Robert James Ritchie. The only advantage of living in such a place like Romeo for a boy, interested in music, was its close location to Detroit. Inspired by music of Beastie Boys and Run -d.m.c. Rock tried to make his own music since childhood. In high school he disc-jockeyed the parties for beer and finally joined the band of Bo Wisdom of Groove Time Productions in a neighbour town. It was the time when at some show Kid Rock got his nickname. A representative of Jive Records accidentally saw Kid at a concert and they became interested in the guy. In spite of the parents' strong disapprove Rock signed a contract with the label at age 17. In 1990 he released the debut album, featuring the mix of rap and hard rock. Its lead-single's too sexual lyrics Yodelin' In The Valley was the reason for a scandal. Rock did not answer the expectations of Jive, and the parties parted. For several years Kid Rock recorded and released albums for a small auditory of devoted fans, having a contract with an independent label Continuum. Rock's sophomore attempt The Polyfuze Method was finished in 1993, it was praized by critics for humour and eclectic approach to styles though bringing no big success to the author.
In 1994 the artist opened his lablel Top Dog and released an EP Fire It Up. Early Mornin' Stoned Pimp saw light in 1996, recorded with an extreme lack of money. Rock's financial side of life was so dark that he had to find accidental works and sell bootleg copies of his own albums to pay debts for the studio. Nevertheless he managed to make his own band by that time, which he called Twisted Brown Trucker. One of the first band members, Joe C, was an old fan of Rock, famous for the encyclopedic knowledge of Rock's texts. By that time such hard rock teams like Korn, Limp Bizkit and alike were dominating the scene and Atlantic Records became interested in Rock. The musician did not disappoint them - he released his cult work Devil Without A Cause in 1998. Due to big promotion by the label and MTV the first single Bawitdaba became a national hit of the summer. The next winding track, Cowboy, wonderfully featuring country, rap and rock music, helped the album to become 7 times platinum. By the end of the year Rock was nominated for two Grammies and headed to his first tour with the kings of rock scene Metallica.
Kid Rock Born Free Cd

Many KID ROCK song that you can listen to here.free install the application, select the song you like and play. This app only provides Mp3 Streaming and no. Kid Rock will release his 8th studio album, Born Free, on November 16th via Atlantic Records.The record was produced by Rick Rubin and mixed by Greg Fidelman. The first single from the album will be, appropriately, 'Born Free' which hits radio September 14th. Kid Rock describes it as 'very organic blues-based rock and roll'. Cable network TBS used the title track, 'Born Free', for its coverage of the 2010 Major League Baseball postseason. As of June 16, 2011 Born Free is certified Platinum by the RIAA for shipments in excess of one million copies. Listen free to Kid Rock – Born Free (Born Free, Slow My Roll and more). 12 tracks. Discover more music, concerts, videos, and pictures with the largest catalogue online at Last.fm. These pros give Born Free the suppleness of well-worn leather and Kid Rock rides their grooves with ease, digging into the grinding “God Bless Saturday,” laying back on “Slow My Roll,” slyly trading verses with old sparring partner Sheryl Crow on “Collide” (which also happens to feature Seger himself on piano), and shuffling along.
Striking while the iron is hot, Rock re-released his old material with a new song, American Bad Ass, in The History Of Rock in 2000. Though the album did not become as big as Devil Without A Cause, it sold well. At the end of the year Kid was deeply upset by the death of the oldest Twisted Brown Trucker member Joe C. In the spring of 2001 Rock became the victim to paparazzi due to his relations with the scandalous Playboy model and actress Pamela Anderson. In April 2002 they married but soon the engagement was called off. In November of the same year Rock presented his eighth edition Cocky with the singles You Never Met A Motherfucker Quite Like Me, fulfilled in the Southern rock style, and a beautiful blues ballad Lownly Road Of Faith. But the real success and the breakthrough to the new auditory were brought by the country style ballad with Sheryl Crow Picture. The same year Rock had to search for a new DJ, as his former one went solo. In 2003 the artist released the self-titled album Kid Rock, featuring a handful of hits: Jackson, Mississippi, Cold And Empty, I Am and Single Father. 2004 became the year of the rocker's first live record, Live Trucker, containing moslty his two last performaces. In 2006 Rock again married Pamela Anderson after an issue of her pregnancy. This time they needed 5 months to divorse. In October 2007 Rock finished his new disc, Rock N Roll Jesus, becoming the first Rock's album to debut in charts number one. Three years later the rocker’s discography was enlarged by a strong long play Born Free (2010). During the record process Rock collaborated with famous rock, country and rap-performers, thereby Born Free got powerful and at the same time harmonic sound. Numerous experts agreed that Born Free became one of Kid’s best works since the release of Devil Without A Cause.
Studio Albums
Born Free
Kid Rock Born Free Mp3 Download
Kid Rock's album number eight, Born Free, demonstrates the musician's shift towards more rock-oriented sound and presents a product made by a group of great specialists
12
Kid Rock Songs Born Free
Singles
2
Compilation albums
1
Kid Rock Born Free Mp3 Download
Lives
Kid Rock Born Free Mp3 Download
1

0 notes
Text
Using Sccm For Windows Updates

Hi, I would like to know the default GPO Settings when using SCCM/WSUS 2012 R2 for Windows Update. I have been looking on line and cant find a concise answer. I have an issue.
If you are looking to deploy feature and quality updates to Windows 10 version 1903 using SCCM, here is a treat from Microsoft. As per this announcement from Microsoft, you can use SCCM 1902 to deploy updates to Windows 10 version 1903. Windows 10’s latest update is the May 2019 Update.
Hi All, We have been using SCCM for about 3 months now, mainly for OS deployment and haven't really spent much time looking at other features like software metering etc yet. We had a consultant come in and initially set everything up and one of the things they went through briefly with us was the software updates feature - they basically said that a common way of using this was to once a month.
Apr 27, 2016 Hi, I would like to know the default GPO Settings when using SCCM/WSUS 2012 R2 for Windows Update. I have been looking on line and cant find a concise answer. I have an issue on site where a machine in my test group os getting a Windows Update pop up message: How can i disable all settings via. Don't configure the Specify Intranet MS Update.
Manage Windows Updates In Sccm
Using Sccm For Windows Updates Windows 7
Using Sccm For Windows Updates Mac
Deployment of: Quality updates. The deployment of quality updates with SCCM can be done via the traditional way, by using Automatic deployment rules(ADR’s) or manual deployments. From ConfigMgr1706 onwards there is an additional capability added to deploy Windows update for business policies.
-->
Applies to: System Center Configuration Manager (Current Branch)
The software update deployment phase is the process of deploying software updates. No matter how you deploy software updates, the site:
Adds the updates to a software update group
Distributes the update content to distribution points
Deploys the update group to clients
After you create the deployment, the site sends an associated software update policy to targeted clients. The clients download the software update content files from a content source to their local cache. Clients on the internet always download content from the Microsoft Update cloud service. The software updates are then available for installation by the client.
Tip
If a distribution point isn't available, clients on the intranet can also download software updates from Microsoft Update.
Note
Unlike other deployment types, software updates are all downloaded to the client cache. This is regardless of the maximum cache size setting on the client. For more information about the client cache setting, see Configure the client cache for Configuration Manager clients.
If you configure a required software update deployment, the software updates are automatically installed at the scheduled deadline. Alternatively, the user on the client computer can schedule or initiate the software update installation prior to the deadline. After the attempted installation, client computers send state messages back to the site server to report whether the software update installation was successful. For more information about software update deployments, see Software update deployment workflows.
There are three main scenarios for deploying software updates:
Typically, you start by manually deploying software updates to create a baseline for your clients, and then you manage software updates on clients by using an automatic or phased deployment.
Note
You can't use an automatic deployment rule with a phased deployment.
Manually deploy software updates
Select software updates in the Configuration Manager console and manually start the deployment process. You typically use this method of deployment to:

Get clients up-to-date with required software updates before you create automatic deployment rules that manage monthly deployments
Deploy out-of-band software updates
The following list provides the general workflow for manual deployment of software updates:
Filter for software updates that use specific requirements. For example, provide criteria that retrieves all security or critical software updates that are required on more than 50 clients.
Create a software update group that contains the software updates.
Download the content for the software updates in the software update group.
Manually deploy the software update group.
For more information and detailed steps, see Manually deploy software updates.
Tip
Manage Windows Updates In Sccm
When manually deploying Office 365 client updates, find them in the Office 365 Updates node under Office 365 Client Management of the Software Library workspace.
Using Sccm For Windows Updates Windows 7
Automatically deploy software updates
Configure automatic software updates deployment by using an automatic deployment rule (ADR). This method of deployment is common for monthly software updates (typically known as 'Patch Tuesday') and for managing definition updates. You define the criteria for an ADR to automate the deployment process. The following list provides the general workflow to automatically deploy software updates:
Create an ADR that specifies deployment settings.
The site adds the software updates to a software update group.
The site deploys the software update group to the clients in the target collection.
First, determine your automatic software update deployment strategy. For example, create the ADR to initially target a collection of test clients. After you verify the test group successfully installed the software updates, add a new deployment to the rule. You could also change the targeted collection in the existing deployment to one that includes a larger set of clients. Consider the following behaviors when deciding upon the strategy to use:
You're able to modify the properties of the software update objects that the ADR creates.
The ADR automatically deploys software updates to clients when you add them to the target collection.
When you or the ADR adds new software updates to the software update group, the site automatically deploys them to the clients in the target collection.
Enable or disable deployments at any time for the ADR.
After you create an ADR, add additional deployments to the rule. This action helps you manage the complexity of deploying different updates to different collections. Each new deployment has the full range of functionality and deployment monitoring experience.
Each new deployment that you add:
Uses the same update group and package, which the ADR creates when it first runs
Can target a different collection
Supports unique deployment properties including:
Activation time
Deadline
User experience
Separate alerts for each deployment
For more information and detailed steps, see Automatically deploy software updates
Deploy software updates in phases
Starting in version 1810, create phased deployments for software updates. Phased deployments allow you to orchestrate a coordinated, sequenced rollout of software based on customizable criteria and groups.
Using Sccm For Windows Updates Mac
For more information, see Create phased deployments.

0 notes
Text
Airport Traffic Control Game

This game is currently blocked due to the new privacy regulation and www.agame.com isn't currently controlling it. In order for you to continue playing this game, you'll need to click 'accept' in the banner below.
Air Traffic Control Game Airport Madness 6
Airport Traffic Control Smart Games
Air Traffic Control Game Airport Madness 3
Airport Madness 3D offers 40 different aircraft that include the Airbus 380, the Boeing 787 Dreamliner, even the Concorde. Each airport has two separate traffic patterns, offering you two completely different air traffic control experiences. Choose from four different view perspectives: tower, runway cam, sky view, as well as cockpit view.
We’ve developed a series of mini-games to help you decide whether it’s the kind of career that might be right for you. They test a range of basic cognitive skills which are required by Controllers: Shape tracking. This game tests your ability to follow an element on screen, with each level increasing in difficulty. Sequential memory.
This is taking longer than usual.
Want to wait a bit more, or reload the game?
Oops, something went wrong while loading your game. Try again!
We have other games that don't require Flash. Here's a few of them.

Air Traffic Control Simulator v6.14.0 Loading. Air traffic control games online, free/ airport management games for kids to play: Airport Madness 3, a fun air traffic control system simulation game for PC, Mac, iPad on the internet with no download. Airplane parking/ shipping & cargo management games, educational games for teens (girls, boys).
How to activate Flash
Airport Control, Working as an air traffic controller can be really tough but you’ll get the hang of it. Earn lots of cash while you make sure that all of the planes land safely in this time management game. Kongregate free online game Airport Madness 2 - A fun and very addictive airport air traffic control game. Manage airport takeoffs and landing. Play Airport Madness 2. La Guardia Airport ATC simulator and ground control simulator. Control inbound and outbound air traffic at the La Guardia International Airport,New York and guide them at the airport with the ground radar simulator.
For a step-by-step guide, please visit our FAQ page.
Cancel
Play more games
Air Traffic Control Game Airport Madness 6

Loading more games…
Loading game
Airport Traffic Control Smart Games
This game uses modern browser features which your browser doesn't support.
For the best results, please get the latest version of Google Chrome.
Air Traffic Control Game Airport Madness 3
Loading…

1 note
·
View note