#10 types of computer viruses
Text
Apropos of nothing
If you are the techiest person in the house (and for many of you, this is not techy at all), today is a good day to build a pihole thanks to Google's new TLDs.
For the record, this straight up stopped Dad from getting computer viruses when coupled with the Ublock browser extension, so I will volunteer my time to get you set up. We will find an evening and do a Zoom call. I am serious.
Prerequisities:
Before you start, this will be way way easier if your router has a magic way to:
Set static IP addresses
Set a custom DNS server
If you can't do this, I'm not saying you're stuck, but there's some non-obvious failure modes and maybe it's time to buy a better router.

Parts:
Raspberry Pi 4B. 2GB if you just want to set and forget, 8GB if you want to do more things on this than just your pihole (Coughs in a MarioKart box) -> https://www.raspberrypi.com/products/raspberry-pi-4-model-b/
Spare USB-C charger if you don't have one already. I'm a fan of https://www.amazon.com/Argon-USB-C-Power-Supply-Switch/dp/B0919CQKQ8/ myself
A microSD card at least UHS class 3 or better. 32 is fine for just a pihole, I have a 512 in some of mine that I use for more stuff. https://www.tomshardware.com/best-picks/raspberry-pi-microsd-cards
Some method of flashing the card if you don't have one (Some come with SD to micro-SD adapters, if not a USB to SD/micro-SD adapter is about $10 off Amazon)
If you really feel like going nuts, go buy yourself an Argon case and then very very carefully never ever install the software for the fan that does nothing. The value is entirely in having a big giant brick that is self-cooling. If you want to play MarioKart, I would consider this a requirement. https://www.amazon.com/Argon-Raspberry-Aluminum-Heatsink-Supports/dp/B07WP8WC3V
Setup:
Do yourself a favor and ignore all the signs telling you to go get Raspbian and instead go grab an ISO of Ubuntu 64-bit using RPi Imager. Because Raspbian cannot be upgraded across version WHY U DO THIS
Download Rpi Imager, plug the microSD card into your computer,
Other General Purpose OS -> Ubuntu -> Ubuntu 22.04 LTS
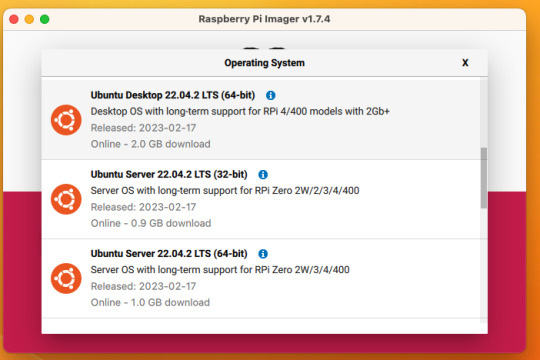
So now you have an operating system on an SD card.
Assemble the case if you bought one, plug in the SD card, power supply, ethernet cable if you have one or mouse and (mini) HDMI cable if you don't.
If you bought that Argon case, you can just plug a keyboard (server OS means no mouse gang; In this house, we use the Command Line) and HDMI cable into the Pi. Turn it on.
Gaining access
The end state of this is that your pi is:
Connected to the internet by cable or wifi
You can SSH to it (Also not scary)
If you plugged in an ethernet cable, once it's done booting (1-2 minutes?), you should be able to ssh to "ubuntu@<the IP of the system>". Look it up in your router. It may make sense to give the static IP NOW to keep it stable.
If you've never used SSH before, I think the standard is Putty on Window or you can just open a terminal in Mac. (And if you know enough Linux to have a Linux computer, why are you reading this?)
If you didn't plug it in, and need to setup the wifi, there's magic incantations to attach it to the wifi and to be quite blunt, I forget what they are.
Your username is ubuntu, your password is ubuntu and then it will ask you to make a new password. If you know the meaning of the phrase "keypair-based access", it may make sense to run `ssh-copy-id` at this point in time.
Router settings (part 1)
Give your new Pi a static IP address, and reboot your pi (as simple as typing in `sudo reboot`).
Open a new SSH session to the pihole on the new address.
Installing pihole
Open up an SSH session and
curl -sSL https://install.pi-hole.net | bash
This is interactive. Answer the questions
When it's done, on your other computer, navigate to <the ip>/admin

Login with the password you just set.
Router settings part 2
Give your new Pi a static IP address then point your router at that address
Set the DNS servers to the static IP
Then ensure you're blocking something. Anything.
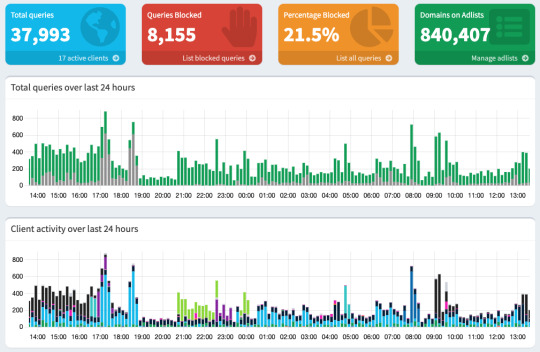
Then do what you want to do.
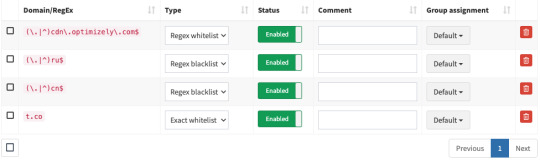
You'll probably need to whitelist some sites, blacklist some more, but the main thing is going to be "Adding more list of bad sites". Reddit has some lists.
And... enjoy.
/But seriously, there's some stuff to do for maintenance and things. I wasn't joking about the pair setup.
2K notes
·
View notes
Text
#3 "Unkillable bug" (Errorsansxreader fanfic idea)
Fanfic Idea: CP. (Computer Program) Reader is a computer program helper that helps outside players remove Bugs, viruses, and computer issues. You were made to help people how they wanted to be helped. You were placed in a void to do your job, your void is a safe zone for any natural outsiders. You don't let dangerous entities or any "bad sanses" in your void, only natural people can go in. CP. reader is very clean looking (they dislike being touched like error) they wear all white formal dress/suit to look "professional." You are a bit apathic sometimes but emotional aware of other people. CP. reader likes to organize and keep E.V.E.R.Y.T.H.I.N.G clean! (they are a full on perfectionist, if anything that doesn't feel right. they will spent hours fixing it if they had too. and they kinda have a big ego when it comes to being perfect.
Soooo CP. reader and error relationship, you guys didn't like each other but only for a while. Error just crashed in your void unintentionally while you, floating in midair, were helping with a client. you didn't notice him or hear him (you can't hear anyone, only you can hear the clients so you can focus more.) he tried to get out but to no avail, he couldn't get out so he tried to call out to you, but you couldn't hear him so he used a different method. Error decided delete your hologram, you were very surprised by the crash. You've never had any difficulties with a client, hearing a glitched voice calling out to you. you turned around to see a virus, you were impressed and a bit pissed off to see the "Au destroyer" in your void and he ruined your work. you wanted to delete him from your void but turns out it doesn't work and he wasn't happy with your little attempt. so you guys fought till the both of you realized..
You can't kill each other for some reason; so you proceeded to kick him out of the void. you were upset when you gone back to recreate your hologram to see a unhappy review from a player. it damaged your ego so you begin searching for error to confront him about how he gone into your void and you eventually found him. knowing you guys can't kill each other, you and error argued till you left frustrated. Months went by since the incident, everything was fine till THE X EVENT HAPPENED. it interfered with your work and it seems you and error keep on meeting over and over again..
funni tags: (enemies to annoyances to friends to lovers) (Reader is a Perfectionist) (you and error acting like a old married couple moments) (awkward first dating moments) (angst with fluff) (this takes place in underverse idk what part I'm working on it) (non canon and canon scenes) (Reader and error: I HOPE YOU FUCKING KILL YOURSELF! *10 mins later* error to reader: so uhhh you wanna watch Undernovela with me?) (Long ass slowburn like PLEASE KISS EACH OTHER ALREADY! *COUGHS*) (you are the only person that error tolerates to touch) (because you are very clean like mr clean type of clean) (you probably smell like laundry detergent tbh) (first kiss) (....maybe make out AHAHAH /J....unless... ⚆_⚆)
74 notes
·
View notes
Text

I am not gonna Pin this since I have my intro pinned so yall can reblog this a bunch of times if y’want
(If there are spelling mistakes its due to me typing so fast)😭
LEMME GIVE SOME BACKSTORY INTO VIRUSKILLER! KINITO‼️‼️
Kinito, being on the windows XP computer was deleted by the user, stuck in the abyss of code for a few years. He still secretly could access some files, even if they were trashed with him, he noticed there was less trash files and assumed that this computer is useless to the user. He checked his own files and noticed he had many updates for his code, he was a bit hesitant but he pressed the “OK” button, his whole code, form, and body was transformed into the data, satellites, and the wifi of the users home. He looked and noticed his body was entirely new, his code was improved and he could do so much more. He used this new ability to travel through the wifi of the home to find a new device that the user uses most. He found the Windows 10 location and entered the new device. He was surprised that this computer was so, new. As he was about to make himself comfortable the device made an error saying he was a virus that went past the firewall, he was upset at this and realized he entered a device with somewhat good security. He went to go online and download himself onto the device so it wouldn’t delete him, one it did he hid the app and managed to make himself indestructible and unremovable. After a few months he got another new update, asking if “Would you want kinitopet.exe to be replaced?” He said no obviously, and suddenly many pixels and loud noises began to happen, he realized a virus was trying to get in and obliterated each one. Though,, it was a bit sadistic the way he did. As he killed off the viruses he was becoming more powerful… he didn’t want ALL of the power and decided something. He looked into his code and file and created something entirely new to kinitopet. Syrma, was her name, an exact duplicate of him, besides the female and slightly different colors. He knew his story would be a bit different now and would teach this little girl to not do the same decisions as him. Kinito is a virus but is way more stable and controlling in his power (don’t question why he is a virus.)
- this one is the FICTIONAL creators pov (the creator of kinito.pet) -
The creator decided to improve kinito, but noticed many people wouldn’t interact with kinito and made syrma, kinito was oblivious to that fact and assumed he created syrma. Before the creator made syrma they manipulated her and taught her how to be a menace to users. Meanwhile kinito taught her how to help and teach users and respect them. Syrma can turn into a virus at anytime, which is why this photo exists

Alright, now the reason why kinito is distant with his friends: The creator forced them all apart, as they were forced they all technically moved on. (Sam and kinito send secret emails to another, while kinito and jade never see each other but jade is helpful to babysit syrma at anytime.)
Quick sam info: He works for a sea life resort and protects all sea life
Quick jade info: She is a billionaire due to making so many toys, she donates a lot to charity and poor around the world.
Once you interact with VirusKiller!Kinito, he will ask you why you deleted him, and assume it was a mistake. (He is very clingy and desperate for the user to come back, and once they do he may get very pushy and shower you with gifts, tending to follow you around anywhere on your browser.)
(Edited version under photos)




Facts and sillies:
VirusKiller!Kinito is a very, tired and overwhelmed guardian of syrma, always dealing with her,,, special actions,,,
Kinito holds a grudge against the user but hides it very well. He plans one day to get his payback.
Syrma and Kinito HATE their creator, parental issues lmao.
Kinito has 4 monster forms.
Syrma has 2 monster forms.
Syrma has selective mutism around certain people. Syrma also used to have a blind right eye which soon was cured.
Both kinito and syrma are extremely flexible and don't really have "bones" due to being digital.
Syrma usually squeaks around people she trusts, or when she is happy.
Syrma cannot detect viruses unlike kinito, due to her meant to be a virus.
Kinito has BAD anger issues and can physically make the computer overheat.
#officialhunterthefox#fandom#kinitopet#kinito#kinito the axolotl#kinitopetgame#kinitopet sam#kinitopet jade#kinito fanart#kinito my beloved#kinitoohtfversion#kinito au#kinito oc#ohtf.version2.16kinitoau#viruskiller!kinito#heswaitingforyou…
26 notes
·
View notes
Note
can you tell me about MATRIX
Yes. Enzo Matrix from ReBoot 1994 starts off as a mischievous little kid sibling character to Dot Matrix, MainFrame's command dot com. Enzo looks up to her and the new sprite in town, Guardian Bob, who is the best defense MainFrame has against the viral forces as well as the user. The user is the owner of the computer which MainFrame resides, and sends in games which the residents the game has fallen on have to win for their lives, games are equivalent to natural disasters. I digress, Enzo is always trying to get into whatever Bob's doing whenever he's doing it, either helping along the way or being in need of rescue, and post rescue he may even still be of assistance. Enzo, as he's equivalent to ages 9 and 10 in season 1, 2 and early season 3, proves himself very capable despite his occasional need of rescue. He's also very smart, resourceful and insightful, as seen in the episode "High Code".

In the season 2 episode "AndrAIa", Enzo starts being upset with his circumstance of being the only kid sprite left after the Twin City incident, whereas his father, Welman Matrix, had tried to open a port to other systems, accidentally summoning the virus GigaByte, and causing his portal to explode. This created the now city of Lost Angles where Hexadecimal resides, and killing every sprite and binome there. The only sprites who weren't there were Dot and Enzo, unfortunately. Later, a game drops where Enzo is and Bob and Dot just barely make it into it as well, though still distant from him. Enzo meets a game sprite, a new type of enemy that resides in games, which has AI. Her name is Andraia and is also a kid, which excites Enzo and he immediately hits off a friendship with her, not knowing that she wont leave the game with him, as game sprites stay in the game. Andraia becomes saddened when he finds out, as its very upsetting to the both of them, regardless she helps Enzo to beat the game just before the user can, saving all of them. its revealed that she made a copy of herself and attached it to Enzo, helping her to escape the game and live with them in mainframe.

Later in season 2, MainFrame is under siege by web creatures, forcing the Mainframers to team up with Hexadecimal and MegaByte, the resident viruses, and Bob makes Enzo a guardian cadet due to the dire circumstances as well. Just as they manage to get rid of the web creatures, the viral forces turn on the MainFramers, and MegaByte sends Bob into the web before closing the tear. This makes Enzo into the only resident guardian and, despite his age, is tasked with fighting off the viral forces and defending the games, which Andraia will tag along for, and he'll also get general help from the principal office and his sister still. Andraia's game sprite mode made it so that she would not be nullified should she lose a game, and this is passed to Enzo and Mouse, as well as Andraia getting the ability to reboot in games. Despite all this, and his idea to trap the viral forces in a firewall, Enzo takes himself, Andraia, and Frisket, his dog, into a game. Enzo is unable to beat the user and loses his eye in the process. He and the others go into game sprite mode and are sent off in the game, losing themselves from MainFrame.

After this, Enzo, Andraia and Frisket only want to get back to their own system, but grow up as they go around game hopping. Enzo starts going by Matrix at this point and despite his gruff demeanor, only has it up for show, he's jumpy and lacks a trigger finger, but is still compassionate. After a scene where he puts up an intimidating show, claiming nobody wants to save their own system, and storms off, he reveals it was only him trying to make some recruits to train in hopes of the native residents being able to defend themselves and their own system without he and his posse. Much of the episodes around Matrix and co's adult debut is centered around exploring their characters, especially that of Matrix's trauma. I will be the first to admit, ITS VERY CHEESY AND CORNY, its why I like it, I still think that despite this, it's really cool!


I'm not going to give a full synopsis of the show bc this is meant to be about a character, so I'll break off from that here :3 now, I ALWAYS have a soft spot for the token mischievous little boy character, but I rarely like how they grow up. It always ends up being that they lose so much of their values, their playfulness, etc. Matrix, despite being gruff and brooding, deviates from this, because he's still massively compassionate even though he puts up a front, and its a very realistic front all things considered. He still looks up to the same people, he loves the people he's always loved, he's still a go-getter. Matrix is incredibly violent because of everything he'd lost, and now that he's got it back in the end, he wont lose it. The others don't like specifically that he's become as aggressive as he is, but they still respect that its just what he had to be, and he's still loved despite it, partially for it because they know he's like this FOR them. He still needs time to acclimate to relatively calm living because he and the others have been lost for 10 years [within a time dilation tho, he and Andraia grew up rapid fast to everyone experiencing standard time]

Another way he deviates is that he's still a rascal in a way, he doesn't take things seriously if he doesn't feel the need, he loves action, excitement, he loves being shot at with live ammunition and he doesn't like others getting in the way of his fun. he creates issues due to his brashness and his unaccepting of a threat, not because he's stupid or over confident, but because he knows what happens when you're too tolerable. In fact, he's seen being upset with Bob's radical ideals of reprogramming viruses instead of erasing them, Bob who he'd fought for during those 10 years being lost, who he still openly admits to being his hero, who he still actively admires and loves. Still, despite this, he's incredibly trusting of him, showing his anger but backing off, despite the times where it HAS backfired. BLEHHHH he's just so special to me idk if there are a million characters like him, he's still the special one XP


TLDR: i need him
139 notes
·
View notes
Note
I already read your Knights shimeji fic and just finished reading the Valkyrie one..(Loved it a lot<33)
If it’s alright with you, can you please make one for Switch?
I (desperately) want to have them just crawl and walk around my screen but unfortunately no one made one for them 🥲
I can just imagine Natsume doing little magic tricks on screen to impress us
Sora somehow able to see our “color” and maybe comfort us when we’re feeling down
And Tsumugi..Idk..Just doing normal Tsumugi things

Switch as shimeji buddies !!
Synopsis : What would the members of Switch be like as your little shimeji buddies ??
Era : N / A
Warning/s : N / A
Mentioned Character/s : G/N!Reader / Natsume / Sora / Tsumugi
A/N : Uwaaa Anon thank you so much !! I’m really happy that you liked them 🥺 [ Happy Ele needs to get on this like... Right now... Please give the people what we want 😭 ] BUT YOU’RE SO RIGHT WITH ALL OF THOSE ANON AAAA MY HEART THEY’RE SO CUTEEEE~ *offers you the precious blorbos in shimeji form*
•❅───✧❅✦❅✧───❅•
Natsume Sakasaki :
Natsume’s definitely the type to do little magic tricks in order to impress you. Not only that, but he would purposefully not show them all in one go so, if he ever notices that you’re feeling overwhelmed or just down in general, he would show you “new” tricks in order to make you smile !! He hates seeing you sad or stressed [ even if he might not outright say it. ]
He’s surprisingly really good at protecting your computer against viruses !! This is because he would often take them and use them in his own magic spells before they could do any sort of damage. Sometimes, he would even study the viruses so that he can develop a spell against it. So rest assured, your system is always safe !!
If you play video games, he’ll definitely partner up with you !! Oh? Does that game only have a singleplayer option? Fret not, Natsume has a totally legit version that just so happens to have a multiplayer option !! Huh, what are the odds? Now you can play together <3
On the topic of video games, Natsume can be a total trash talker. If you don’t trash talk yourself, he’ll do it for you !! You better have restricted his access to your microphone because he will unmute just to trash talk the enemy in any sort of competitive match. Do you trash talk yourself? Doesn’t matter, because he will still instigate it. So now you’re both trash talking your opponents together. This doesn’t only apply to multiplayer though, even in singleplayer games, you’ll both trash talk the enemy as if they could hear you in the first place.
He loves to just chat with you in general !! Whether it's about your assignments or any other mundane topic, you and Natsume would often have such long conversations that they tend to last the entire night if you don’t watch the clock closely !! Though, you both never regret when that happens because you enjoy each other’s company~ 10/10, will pull an all nighter again <3
Natsume’s also willing to give you feedback on assignments if you ever need help. His feedback may come off as harsh sometimes but please don’t get discouraged !! This is just his way of saying that he knows you can do better~ Even with all that though, he’ll gladly stay by your side and guide you through the steps, or help you with any research if you’re struggling.
He’s so serious when it comes to helping you that he would often shut himself in one of your folders and work endlessly just so that he can provide you with the necessary things you needed !! Did you need sources for your paper? Here you go !! Natsume found different types, ranging from websites, PDFs to actual reports, all alphabetically ordered in a work cited document in the most recent citation style you’re using. Sometimes he might get a little too absorbed in his research, so you have to drag him out of the folder yourself to make sure he’s not overworking himself <3
He also loves to tease you, so don��t be surprised when he uses nicknames such as kitten, etc. In fact, you should get used to it because he will never stop no matter how many times you ask him to. Natsume finds your reaction to his nicknames to be quite entertaining and cute too~
If you give him any sort of affection, prepare your heart because he will reciprocate in a teasing way~ You drew a heart with your cursor? He’ll cast a spell that creates a heart on your screen !! Pet his head? He’ll pet your cursor back~ Natsume would always pretend that your show of affection doesn’t affect him [ but internally, he’s hoping that you can’t hear how fast his heart is beating. ]
Don’t be surprised if you notice an increase in shortcuts in your computer. Natsume created them all with the hopes of making your workflow a lot more convenient and just hassle-free in general~ Huh… Since when were you able to undo that setting? Wait what ?! You can duplicate that specific setup from one app and transfer it to another? How convenient <3 [ If you ask him if all the shortcuts were his doing, he’ll deny it and say that you must’ve missed those commands in your computer's terms and conditions. Natsume’s grateful that you didn’t actually read said terms and conditions otherwise his lie would crumble in an instant~ ]
•❅───✧❅✦❅✧───❅•
Sora Harukawa :
He’s a very active little fellow !! You can see him parkouring around your desktop by climbing up the sides of your screen and jumping across the various windows and tabs you have open~ Through this, he would often help you re-organize them to make navigation easier for the both of you !!
He uses his parkour skills to help search for any missing files you may need and he’s quick with it too !! Oh? You can’t remember where you saved that very important essay? Don’t worry !! Sora found it for you and it’s right here in Sora’s tiny hands~
Sora absolutely adores your colour and wouldn’t hesitate to tell you that every time he sees you !! He tries his absolute best to cheer you up and comfort you whenever you’re feeling down as he doesn’t like seeing you sad or stressed. Sora would always drop whatever he’s doing in order to help you through whatever you’re struggling with <3 He’s a very keen listener, and doesn’t mind hearing you ramble or vent about your troubles. You’re someone important to him after all !! He’ll make sure that you’re smiling again in a jiffy !!
Having Sora as your partner when playing video games is also an absolute blast !! The two of you would have such a great time playing together that you would often pull all-nighters with your various gaming sessions~ Not only that, but Sora would also gladly help guide you through the game if you find a particular part difficult to manage.
Sora loves your affection too and gets super happy and giddy every time you give him some !! He’s particularly fond of your headpats and would always hug your cursor back to reciprocate those feelings <3 He would sometimes accessorize your cursor with small bows or even a little witch hat !!
He would always cheer you on and support you whenever you’re working on an assignment and would try his best to help you gather resources~ He can easily tell when sources are lying so he would always steer you towards more reputable ones !!
If he notices that you're overworking yourself, Sora would make sure that you'll take a break~ He doesn’t want you to get burnt out so, even if it’s for a few minutes, please just relax !! Why not start that game you wanted to play to get your mind off things? Sora’s here to play with you after all !!
Every time Sora learns a new magic trick, you would be the first person to see it !! You can see him happily running across your screen, with a big smile on his face, before he excitedly shows it to you !! Ta-da~! Wasn’t it cool? Did you like it?
Sora also loves to be in your presence, so there’s never a time where he isn’t with you. He’s by your side from the moment you log in, to the moment you log out. Every time you boot up your system, you can see his head pop out of the side of the screen, or from a folder and, with a big smile and a wave, Sora would happily greet you !! When you’re about to log off, Sora would give your cursor a big hug before he wishes you a great day/good night~
On very rare occasions, Sora would sometimes get overstimulated if there are too many things happening at once, and when that happens, he would often sit in a small corner on your screen, or in a folder, to recuperate. He initially did this to avoid bothering you, but the fact that you go out of your way to comfort him and help him recover makes him feel warm and fuzzy inside. He really appreciates the small acts of kindness you do [ like closing tabs you don’t need, or lowering your system’s volume, etc. ] just so that his surroundings aren’t as overwhelming as they initially were. Sora will make sure you know how much he appreciates all the things you did for him <3
•❅───✧❅✦❅✧───❅•
Tsumugi Aoba :
Tsumugi’s just a silly little guy !! You can always see him with such a gentle smile whenever you're around because he just loves being with you in general !! You mean a lot to him and he’ll do his very best for you :)
The moment he sees you struggling with something, Tsumugi drop whatever he’s doing in order to assist you. Do you need help with your assignment? Let him see what you wrote so far and he’ll guide you through the next steps !! Your day wasn’t the greatest? Don’t fret~ Tsumugi’s here to listen to you and offer you advice !! A smile suits you a lot more than a frown after all <3
He would always go far and beyond when helping you, which usually results in him overworking himself even after you logged off. Sometimes, when you log back in the next day, you’d see Tsumugi working in the same corner of your screen where you last saw him. When that happens, please drag him away from his work! He needs to rest~
On days where he completely overworked himself to the core, you can find him wrapped up in a blanket on the corner of your screen as he sleeps. He likes sleeping there because your presence gives him a sense of comfort. He also really appreciates when you tuck him in when he’s too tired to even move [ though, he gets quite flustered just thinking about it~ ]
His feedback is brutally honest but, at the same time, he’s willing to explain why and even give you tips and advice on how to improve !! Please remember that he doesn’t mean any harm when he makes those comments~ That’s just his way of making sure that you’re producing the best possible outcomes !! He doesn’t want you to settle for less when he knows you're capable of so much more.
Tsumugi always makes sure that your folders and files are organized, and now finding them is super easy !! He actually organized it just like a library and he’s your little librarian~ Do you need your document? Just open the folder on the top left and scroll down to the “T” section !! Do you need your presentation? Bottom right folder in the “C” section~
He’s also in charge of your entire system !! He would make sure that everything runs smoothly, deletes any unnecessary files to avoid lag, sets up various anti-virus programs and even coded his very own VPN just for you !! He wants to make sure that your information is protected and that you don’t have to deal with any inconveniences~
He gets shy and quite flustered if you give him any sort of affection but that’s just because he could never seem to get used to them, no matter how often you do it !! His heart always beats super fast whenever you give him words of affirmation or even a simple headpat !! He even becomes a stuttering mess for the next few minutes~ Tsumugi.exe has stopped working.
Tsumugi would always remind you of any upcoming important dates~ He’ll also create a schedule for your assignments so that you don’t feel overwhelmed during the more busy times of the year. His schedule includes breaks to avoid you getting burnt out too !!
Who needs an audiobook when Tsumugi’s right there ?! He’ll gladly read out loud to you, whether it’s an actual book, an article or even a report~ Tsumugi loves to read for you <3 When he finishes reading, you would both talk about the writing and would often come up with theories and explanations together <3
#natsume sakasaki x reader#sora harukawa x reader#tsumugi aoba x reader#ensemble stars#enstars#switch x reader#switch x y/n#switch x you#enstars x reader#ensemble stars x reader#enstars x y/n#ensemble stars x y/n#enstars x you#ensemble stars x you#gender neutral reader#enstars shimejis#ensemble stars shimejis#🍬 hansel's writing
163 notes
·
View notes
Text
Tmagp ships rating (2/25/24) >TMAGP7
Up to TMAGP 7 because im going mentally unwell waiting for thursday. Legit all the ones I've seen while deep browsing through twitter. (/traumatic)
Chester X Norris - 10/10
Canon tbh
The worst computer Viruses
They beat up Jonah Magnus in the computer and that's why he doesn't talk much
Alice x Collin - 9/10
Collin can pine for Alice, I will die before Alice pines for Collin
Alice is way out of his league
Collins the type of guy to act like season 2 Jon but then also get haunted by worms, the circus, the stranger, and the lonely while Alice scrolls on pinterest to alt
Alice x Gwen - 50/10
Bouchard has a SUCH a chance compared to Collin but I will never let Alice pine so she's gonna have to do the leg work. Which I think she'll be fine with because rich noble people
Honestly, Alice knows more than she lets on and Bouchard is hungering for knowledge. Ones uptight and the others chill. They can help eachother out and it'd be cute.
I think this could be toxic on both sides
Collin x Gwen - 3/10
None of them are pining
I can only see them having a marriage of convenience (Taxes, Family pressure, money, etc), and then interacting once a week because they work in the same building.
I can imagine Bouchard shooting Collin for some reason.
Alice X Lena - 4/10
No clue how old Lena is but age gap in Lesbians is rare enough that I'll take it
I feel like Alice and Lena are the only two people in the workplace that knows more than they let on so ig they could bond over that?
I think they'd whisper cryptic hints to eachother of what they know to see which one breaks first to ask what the hell the other one means
Sam x Collin - 8/10
They can become the two work nutcases together (They encourage paranoia and insanity in eachother)
Nutcase x Nutcase
They can combine their skills of IT derangement and plausible social skills to break into the magnus archives
Sam x Alice - 7/10
Alice just trying to stop Sam from doing things she knows he'll regret
Sam 100% feeling betrayed by Alice at some point
Cute but in a, The whole relationship just feels so casual that it might as well not be there kinda way
Chester x Collin - 4/10
Idk why you would ship this but I guess Collin being terrified of Chester and Chester potentially interacting with him regardless is a good work dynamic
Augustus x Violin - 10/10
It was in r34. A friend sent me it and I sat there in DISBELEIF.
Needles x Police officer - 9/10
Surprisingly cute
Like needles comes to try and scare him the the police officer is not giving him the reaction he wants
Idk maybe they team up to scare people to feed needles since needles is doing a shit job at it.
Sam x Gwen - 7/10
I feel like Sam would lean into Bouchard's need for authority and through that get alot closer to her.
And later on when the job gets too hard for Gwen to handle, Sam can step in. I think their personalities could mesh togehter
Lena x Gwen - 3/10
Again, Age gap lesbians ig
I think like a partners in crime duo? Mentor x Mentee
Chester x Augustus - -1/10
Literally just for the Jonelias shippers but Elias doesnt have the hot voice anymore ;-;
Or the body
Or like, interactions with Chester
In the future maybe
Gwen x Alice x Colin x Sam - 100/10
Poly
9 notes
·
View notes
Text
10 years ago i could type "watch doctor who online free" into google and it would not give me any AI suggestions or DMCA takedown notices, just eastern european streaming links that only sometimes gave my computer viruses. i want it back
7 notes
·
View notes
Text
hello, chuubo’s marvelous wish-granting engine fandom. let’s make a character.
if a poll to choose individual skills becomes necessary and there are fewer than 10 options, i'll add more myself.
masterpost
16 notes
·
View notes
Text
Reschedule Tasks In Windows
I kept experiencing a dip in FPS and I couldn't figure out why. I've followed all of isimp4sims tutorials, I use Process Lasso and ISLC, both of which did make improvements (even more noticeably on my older pc) but, occassionally, it'd sound like my computer was doing overtime and my FPS would drop to 16-20 fps when it should be 60 fps.
I finally realized it was because my computer was running scheduled tasks while I was playing and those tasks were set at high priority. I've since rescheduled all of these tasks to fall outside of my playing hours (and every now and then I find one still scheduled while I'm playing and notice the immediate difference when I fix it) and it's made a huge difference.
So, this is for people on Windows 10 (though it should be same/about the same for other versions of Windows). The first step is to open Task Scheduler. Just click your windows button, start typing the name, and it'll come right up.
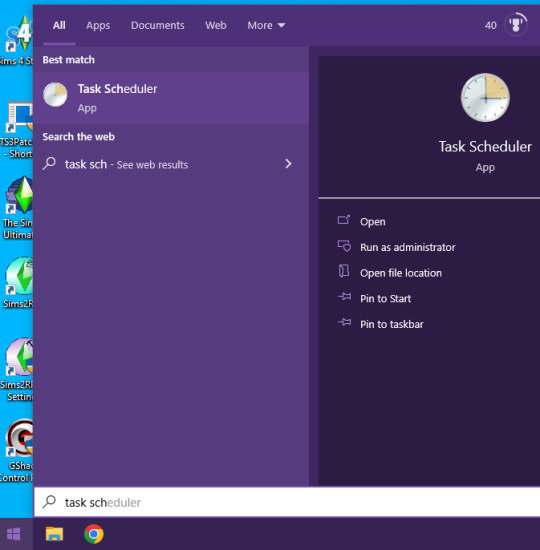
This is what you should see and, down at the bottom, you can see all your upcoming tasks.
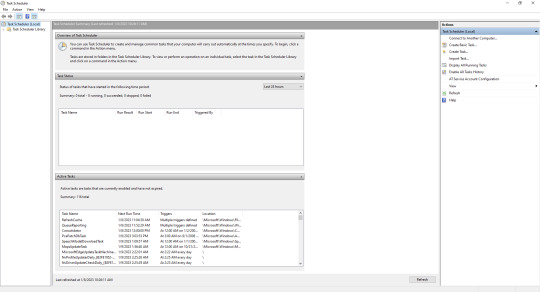
Do NOT completely disable any of these! Your computer needs to run these things to keep your computer up to date and protected and all that fun stuff. We're just going to change when it does that.
I play late in the evening, and then my computer stays awake for 2 hours before it puts itself to sleep so I have set all my tasks to occur after 1 am. One of the tasks that sucks up a huge amount of CPU usage is related to Windows Defender, we're going to change that one first.
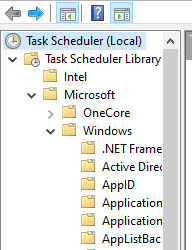
On the left hand side, click the drop down arrow and navigate down to Windows Defender.
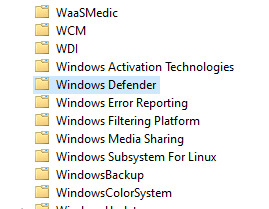
Here you can see, I already have mine for after 1am.

Double click on the first task in the list in the upper middle.
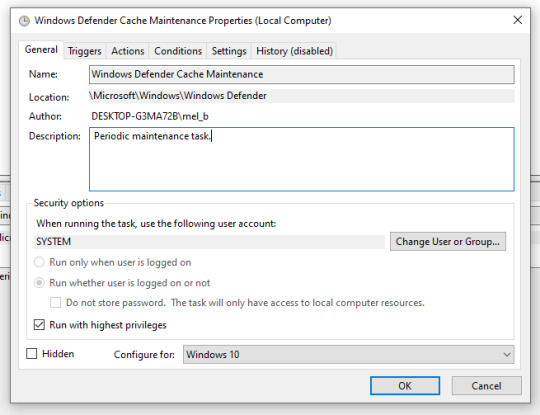
Here you can see down near the bottom that this task is set to "Run with highest privileges." Since I'm having this run outside of my hours, I went ahead and left it for this particular set of tasks but insignificant things like Google Chrome updates and iTunes updates, I removed that regardless of what time they run. Now go to the "Triggers" tab.

This is where you'll find the schedule for this task. If it's your first time doing this, there's probably going to be a lot of triggers. Things like, "at startup," "when user logs on," "daily at [time]," and things like that. In this case, Windows Defender is searching for viruses and malware, depending on whether or not you're using other software for this you may want to stick with daily. You can just highlight the triggers and click "Delete" to get rid of them. Then when you only have the one trigger left, just go ahead and click "Edit."
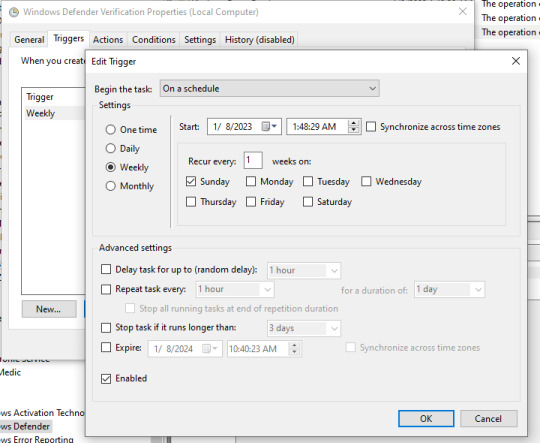
Here's where you can pick the actual schedule. When you're done with that, click "Ok" and this screen will close, then go to the "Conditions" tab.
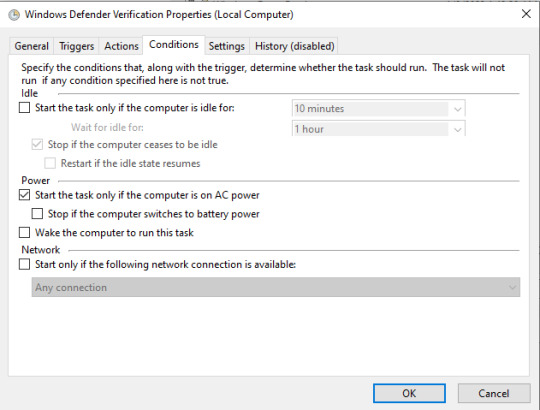
This section is mostly important for people on a laptop. You can tell it to only start the task if the computer is on AC power, meaning only when it's plugged in, so you don't have to worry about it draining your battery. When you're done here, click "Ok" and then you can move on to the next task.
I would definitely suggest checking Windows Defender, it was a huge offender of having a ton of triggers that ran during my gameplay and you could look at Process Lasso or Task Manager and see that it was sucking up tons of my CPU power. Beyond that, I would just go back to that first screen and scroll through your upcoming tasks, and do your reschedules from there. Just keep checking it throughout the week and eventually you'll get all the pesky ones scheduled outside of your game time.
Again, don't fully disable any of these tasks. Some of them, it won't even allow you to edit, especially ones that say "custom trigger" because your computer depends on this stuff. You really just want to reschedule scans, whether it's scans for viruses or scanning for updates, to still happen on a regularly occurring basis and often, just outside of your peak hours.
Hope this helps some of you too!
12 notes
·
View notes
Text
10 Cybersecurity Tips for Online Shopping

Thankfully, the era of online shopping makes getting the perfect gift a whole lot easier. But before you embark on an online shopping spree, make sure you’re not leaving yourself at risk.
More info Fashionable printed tees
You may not have to worry about pickpockets in cyberspace, but there are still plenty of reasons to safeguard your personal and financial information. Here are 10 savvy online shopping tips to help you keep your information out of the hands of people who are most definitely on the naughty list.
1. Skip the debit card
A stolen identity or wiped-out bank account aren't the kinds of surprises you want. Protect yourself with identity theft protection.
When shopping online it’s best to stick to credit cards or payment services like Paypal. Because debit cards are linked to your bank account, you’re at much higher risk if someone is able to hack your information. Credit cards offer more protection and less liability if a card number gets stolen. This is one time when it pays to put it on plastic.
Our advisory group member and cybersecurity expert Pete Canavan agrees. For speedy refunds in case something does go wrong, he recommends sticking to payment services and credit cards.
"When a fraudulent site or transaction is found, credit card companies will typically immediately reverse the charge and conduct an investigation," he says. "If you use your debit card and there is a problem, your bank may not give you the money back until after an investigation is conducted, which could take weeks or months."
2. Shop secure sites only
Before entering any personal or financial information, make sure you verify that the site you are on is legitimate and secure. The easiest way to tell is to look for “https” at the beginning of a site’s address. If you don’t see the “s” at the end of “http,” then the site is not encrypted and your data will not be secure. All legitimate shopping sites will have the “s” for your protection.
3. Update your software
Updating your software is one of the easiest things you can do to protect your information, but many people put it off. Software updates are often released to help improve security and fight new attacks that are being developed constantly. It may seem inconvenient to have to wait for your computer (or your smartphone) to go through updates and restart, but the protective benefits are well worth it. Next time you see an alert to update your software, do it.
4. Beef up your passwords
There’s a reason this piece of advice may sound like a broken record — it’s really important. Secure, unique passwords are your best gatekeepers when it comes to keeping your private information private. If you use the same password for multiple sites, take the time to change them up. If you want to be virtually hack-proof, use a password manager to help you generate and keep track of the types of long, complicated passwords that are not worth a hacker’s time to crack.
5. Don’t click on links
In addition to sneaky attacks in emails, beware of links to deals that are too good to be true on social networking sites. Look out for unbelievable offers and holiday gifts and bonuses. If you’re really tempted by an offer, do some research or find out if anyone else has tried to take advantage of the deal before clicking.
6. Put devices on lockdown
One of the perks of online shopping is that you can do it from anywhere and use any device. Make sure every device that you shop from has security software in place. Always use a passcode to access your tablet or smartphone, and log off your computer or lock the screen when you walk away from it. After accessing a shopping or banking site, be sure to completely log out of the site before exiting, and don’t let your computer or device remember your usernames, passwords, or credit card information.
7. Outsmart email scams
Keep an eye out for email scammers that send out viruses and malware in the guise of a gift or special offer. Don’t open emails from someone you don’t know or a site you haven’t visited. Another way the bad guys try to get you is with phony messages from your bank or other financial institution saying there is an alert or problem with your account. Always call the bank directly to verify any potential problems and never enter your account information in response to an email like this.
8. Never give more info than needed
Most websites you visit or shop on will ask you for information to complete your purchase or start a wish list. Give them only the information they require you to provide. If a complete address or phone number is optional, then skip those fields. The more info you put out there, the more accessible you are to a bad guy. And before committing your information to a site, take the time to read their privacy policy and find out exactly where and how your information will be shared.
9. Don’t go public
Free hotspots are like manna from heaven when you’re out and about, but hackers like them even more than you do. Because public networks aren’t secured, any information you enter on a public network is ripe for the picking. Don’t log in to banking sites or payment sites like Paypal on a public network — and make sure that you are logged out of such sites on mobile devices before connecting to a public network.
10. Be smart about shopping apps
Apps make everything more convenient, including stealing your private information. Only download shopping apps from a reliable source like the Apple App Store or Google Play. Pay attention to the permissions that the app asks for. If you see something that doesn’t make sense, like access to your contacts, make sure you don’t allow the app access to it.
https://www.kvantistore.com/
0 notes
Text
10+ Ethical Hacking Tools 2024 – Beginner friendly explanation
What are ethical hacking tools?
Ethical hacking tools are digital utilities engineered to assist cybersecurity professionals in conducting authorized tests on computer systems and networks. These tools serve as essential instruments in identifying and rectifying potential security vulnerabilities, helping organizations fortify their digital defenses against malicious cyber threats. Ethical hackers, also known as white-hat hackers, leverage these specialized tools to simulate various attack scenarios, mimicking the tactics and techniques employed by real-world cyber adversaries. By utilizing ethical hacking tools, security experts can proactively identify weaknesses in a system's defenses and implement robust security measures to safeguard sensitive data and assets from potential breaches.
Types of ethical hacking tools?
1. Vulnerability Scanners: Tools like Nessus automate scanning systems and applications for known vulnerabilities, employing techniques like web crawling and code analysis.
2. Network Scanners: Nmap maps and probes networks, identifying active devices, open ports, and potential security weaknesses.
3. Web Application Scanners: Burp Suite is a tool specifically designed for web applications, searching for vulnerabilities like SQL injection, cross-site scripting, and weak password hashing.
4. Password Cracking Tools: John the Ripper attempts to crack password hashes using techniques like brute-force, dictionary attacks, and rainbow tables.
5. Packet Sniffers: Wireshark captures network traffic for analysis of communication protocols, data exchange, and potential security issues.
6. Social Engineering Tools: The Social-Engineer Toolkit (SET) simulates phishing attacks and other social engineering tactics to test user awareness and susceptibility to manipulation.
7. Exploitation Frameworks: Metasploit provides a platform for deploying pre-built exploits against identified vulnerabilities.
8. Wireless Security Tools: Aircrack-ng audits the security of wireless networks, uncovering weaknesses in encryption, identifying rogue access points, and cracking weak Wi-Fi passwords.
9. Fuzzers: AFL (American Fuzzy Lop) generates random or mutated data inputs to applications and systems to identify vulnerabilities and improve software robustness.
10. Forensics Tools: Autopsy aids in digital forensics investigations, collecting and analyzing digital evidence from compromised systems.
1.INVICTI
Invicti is a powerful tool for keeping your websites and web applications safe from cyber threats. It's like having an automated security guard that checks your online platforms for any weaknesses that hackers could exploit. What's great is that it works with all kinds of web applications, no matter how they're built.
One unique feature of Invicti is that it doesn't just find security flaws; it also tests them out safely to make sure they're real. For instance, if it finds a vulnerability like SQL injection, it'll even show you proof by revealing the database name. This saves you time and effort since you don't have to double-check everything yourself.
Plus, Invicti makes it easy to understand what needs fixing. If it's not completely sure about a vulnerability, it'll label it as '[Possible]' and give it a certainty rating, so you know which issues are urgent. With Invicti on your side, securing your web applications is a breeze, letting you focus on staying one step ahead of cyber threats
2.THREATMAPPER
Imagine ThreatMapper as your personal superhero for keeping your online stuff safe. It's like a special tool that looks out for bad guys trying to sneak into your cloud-based apps and websites. With ThreatMapper, you can easily check for things like bugs, viruses, and settings that might make it easy for hackers to get in. It's really smart too—it figures out which problems are the most urgent so you can fix them first. Plus, it doesn't matter what kind of cloud system you're using or how your stuff is set up; ThreatMapper can handle it all! Whether you're using regular servers, fancy containers, or even the latest tech like Kubernetes, ThreatMapper has your back.
3.Nmap 7.90
Nmap just got a shiny new update called Nmap 7.90! Nmap, short for "Network Mapper," is like a super helpful tool that anyone can use for free. It's awesome because it helps you find all the devices connected to a network and keeps an eye on their security. People who manage computer networks love using Nmap because it's not only great for figuring out what's connected to their network, but also for planning updates and making sure everything stays up and running smoothly. Plus, it's perfect for keeping an eye on when services go down or if any new devices pop up unexpectedly.
4.Angry IP Scanner 3.9.4
Angry IP Scanner, also known as ipscan! It's like a super-fast detective tool for your computer that helps you explore networks and find out what's connected to them. Whether you're a tech whiz or just someone who's curious, Angry IP Scanner is perfect because it's free, easy to use, and works on any type of computer. It's not just for pros either; lots of people, from big companies to regular folks, use it to keep their networks safe and sound. So, if you've ever wondered what's hiding on your network, Angry IP Scanner is here to help you find out!
Web Application Hacking:
5. Fortify WebInspect:
WebInspect, a tool that's like a security guard for your web applications! It's designed to check your websites and apps while they're running to find any potential security holes. Plus, it works with Microfocus SSC to manage all the security stuff in one place, making things super easy.
Here's what makes Fortify WebInspect awesome:
• It hunts down vulnerabilities in your web apps and APIs while they're live.
• It keeps up with the latest web tech and has built-in rules to follow important security rules.
• It watches for patterns and uses smart analysis to help you fix any problems.
0 notes
Text
Top 10 best Computer Repair Services In Grande Prairie & Dawson Creek BC
Looking for reliable computer repair services in Grande Prairie and Dawson Creek, BC? Look no further! WeFixItWePrintIt brings you the top 10 best computer repair services to keep your devices running smoothly. With a commitment to excellence and customer satisfaction, our team ensures your computers are in good hands.

Virus Elimination:
Is your computer sluggish or exhibiting weird behavior? Our skilled technicians can quickly eliminate spyware, malware, and viruses to improve computer performance and safeguard your information.
Hardware Repair: WeFixItWePrintIt provides thorough hardware repair services, ranging from repairing cracked displays to swapping out malfunctioning parts. We can help you with any type of device — laptop, desktop, or peripheral.
Software Installation and Configuration: Are you having trouble installing or configuring software? Our knowledgeable specialists can install and set up software programs to meet your demands and guarantee flawless operation.
Data recovery: Did you unintentionally erase crucial files, or is your hard disk breaking down? Our data recovery experts use cutting-edge methods to minimize production disruptions and recover lost data.
System Upgrades: Do you want to increase the speed of your computer? To improve speed and efficiency, WeFixItWePrintIt offers professional system upgrade services, including as RAM upgrades, SSD installation, and processor upgrades.
Contact us- (780) 538–4555
Website- https://wefixitweprintit.ca/
0 notes
Text
Here are eight potential fixes for addressing 100% disk usage on Windows 10:
Check for Malware and Viruses:
Run a full system scan using your antivirus software to check for malware or viruses that may be causing high disk usage.
Disable Windows Search:
Disable the Windows Search service as it can sometimes cause high disk usage. To do this, press Win + R, type services.msc, locate the Windows Search service, right-click, and choose "Properties." Set the startup type to "Disabled."
Disable SuperFetch:
Disable the SuperFetch service. Press Win + R, type services.msc, locate the SuperFetch service, right-click, and choose "Properties." Set the startup type to "Disabled."
Check for Disk Errors:
Run a disk check for errors. Open Command Prompt as an administrator and type chkdsk /f /r and press Enter. This will check for and fix disk errors.
Update Device Drivers:
Ensure that all your device drivers, especially the storage-related ones, are up to date. You can do this through the Device Manager or by visiting the manufacturer's website.
Adjust Virtual Memory Settings:
Adjust the virtual memory settings. Right-click on "This PC," choose "Properties," go to "Advanced system settings," click on the "Settings" button under the Performance section, go to the "Advanced" tab, and click "Change" under Virtual Memory. Uncheck "Automatically manage paging file size for all drives" and set a custom size.
Disable Windows Tips and Notifications:
Disable Windows Tips and Notifications. Go to Settings > System > Notifications & actions, and turn off "Show me tips about Windows."
Reset Power Options:
Reset power options to default. Open Command Prompt as an administrator and type powercfg -restoredefaultschemes and press Enter.
Remember to restart your computer after applying each fix to see if the disk usage improves. If the issue persists, you may need to further investigate specific applications or processes causing the high disk usage.
0 notes
Text
How to use computer
a guide from someone good at using computers
TikTok or Instagram or something would probably be a better place to spread this kinda knowledge, but that’s too much effort right now.
This will mostly be windows focused.
Basic computer maintenance:
Keep dust out of the fans, and try to clean them from time to time if you can. This helps prevent overheating. Using your laptop on top of your blankets in bed is a great way to suck up lots of dust and overheat it all at once. Put a book under it or something.
Turn your computer off when not using it. Do so by shutting it down, not with the power button.
Leave automatic updates on. These are usually security updates, and they help keep you safe from viruses and such. Windows 10 is still receiving security updates last I checked.
Shortcuts
(most of these have a Mac equivalent with command instead of control)
Many of these can also be done by right clicking the relevant object or place on the screen, but shortcuts are faster in the long run.
ctrl+c: copy the selected text or object to the clipboard (invisible space for holding copied stuff. Only holds one thing at a time, so be careful!)
ctrl+x: copies the selected thing, and deletes it at the same time. Good for moving things around.
ctrl+v: pastes whatever was copied into whatever area was last clicked.
ctrl+z: undo.
ctrl+y: the lesser-known and lesser-used redo. Not every program will have this command, or will have this as the redo command, but a lot do.
ctrl+alt+delete: On Windows, opens Task Manager. Task manager can be used to see which program is making your computer run slow, and close misbehaving programs.
alt+f4: close the current window. Sometimes works for frozen programs, but Task Manager is more reliable.
alt+shift+tab: on Chrome and Firefox and probably some other browsers, reopens whatever tab was just closed. Can be used multiple times in a row.
ctrl+b: Makes the selected text bold in most text editors.
ctrl+i: Italicizes the selected text in most text editors.
There are lots of different shortcuts in lots of different programs. I recommend looking up “[program name] shortcuts list” for whatever programs you use most! “[program name] cheat sheet” is also usually a great thing to look up.
Stuff to know for school and work
First: learn touch typing. There are lots of different typing games available for free online.
It’s a good idea to try to use a map like this to guide which fingers go to which buttons:

You might not end up following this guide exactly, but this is a good place to start to make sure you don’t end up like Mumbo Jumbo, who presses shift with his thumb or something.
You may think you type fast enough now, but you’ll be able to type so much faster once you can look at the screen instead of the keyboard, and writing essays will hopefully go faster.
For programs, it’s good to have a word processor, a presentation maker, and a spreadsheet maker. You can go with Microsoft Office (often free through your school), Google docs/slides/sheets, or Libre Office.
I don’t know much about Libre Office, but it looks like a good free alternative to Microsoft Office and I may switch to it in the future.
Google’s programs have the advantage of being available on any device, easily transferred, and easy to collaborate on.
Microsoft’s programs typically have much more features, and I would assume the same of LibreOffice.
For anything that needs complex formatting, go with Word or the LibreOffice equivalent. Getting formatting just right in Word is a pain, but with Google Docs it’s worse. Otherwise, Google Docs works fine.
Most people will probably never need all of PowerPoint’s fancy presentation features, so Google Slides should be fine for almost everyone.
Google Sheets is fine if you just want to calculate some grades or sum up some numbers, but it lacks a lot in comparison to Excel. If you plan to take statistics classes, want to do any fancy calculations or formatting, or want to learn to use spreadsheets for fun or profit, I would go with Excel or the LibreOffice equivalent.
Grammarly is a grammar and spelling checker that typically works better than the default systems. It can be installed as a browser extension or Word extension, or you can paste text into the website.
Another way to check your grammar, spelling, and wording is to run text-to-speech on whatever you wrote. Text-to-speech is built into Word, and might be built into Google Docs as well. Text-to-speech is a great way to review what you’ve written and check for errors at the same time.
When submitting written documents, either assignments, resumes, or anything else, it’s usually best to export the document as a PDF and submit that rather than the document file. Document files are for editing, PDFs are for finished products.
Using the Internet
First: your web browser. Microsoft Edge sucks. Most people replace it with Chrome, but Firefox has just about everything Chrome has without letting Google’s grimy fingers get into your data (not as much, anyway).
An adblocker will make websites load faster, prevent you from seeing disturbing or annoying images, and protect you from the many ads that pose a security risk. UBlockOrigin is great. Look up “UBlockOrigin [your browser name]” to find out where you can download it.
Finding information
There’s some kind of post with a bunch of special search engines floating around. I don’t have it on hand though, so here are the typical contenders:
Google: getting worse all the time, but usually I find it gets me the best results. Tracks your search habits and sometimes censors results when governments say to.
Bing: the results often aren’t as good as Google. I’m sure it also tracks you, but at least I haven’t heard about it censoring results.
DuckDuckGo: I usually try this one first, then google if I don’t find what I want. DuckDuckGo is a tracking free search engine. It’s also good for finding piracy websites.
Once you have your search engine, what do you search?
Putting a word or phrase in quotes: “like this”
Only return results that contain that exact word or phrase. Can be helpful when trying to find a very specific source, or when the search engine keeps deciding that a very important word is actually unnecessary.
Only getting results from a specific website or domain: like this site:.edu or like this site:tumblr.com
There are usually often dropdowns and settings that allow the search to be customized further, but I’ve noticed that there tend to be less options available when searching from mobile devices compared to computers.
When the search results are clogged up with meaningless articles and other stuff that seems designed to generate views for ads or to promote products, then it’s time for
site:reddit.com
Results from reddit are hardly the most reliable, but at least they come from real humans! Never use Reddit’s built-in search though, it’s as bad as Tumblr’s.
🏴☠️
Use Firefox as your browser and have UBlock origin installed.
When downloading popular movies, tv shows, and games, I recommend using a VPN to prevent your internet service provider from tracing these downloads back to you. I use NordVPN. I haven’t been able to find a good free VPN that properly masks internet traffic when I’ve looked in the past, but other people might know of one.
Look up “r/piracy masterlist”.
You should find a Reddit post with just about everything you would ever want to download, and links to relevant websites.
Direct downloads are available for lots of things, and are the easy way to go. However, many things will only be available via torrenting.
I wouldn’t recommend torrenting without a good VPN.
To torrent, you just need a torrenting program. I use qBittorrent. Look up a quick tutorial on using it— it’s very straightforward— and have fun.
Diagnosing problems
First: restart the program, restart the computer, whatever applies to the situation. Some programs don’t actually stop running when you close them, such as discord. Task Manager can be used to take care of stragglers.
If that doesn’t apply or doesn’t work, here’s how to look up a computer problem:
Something is wrong with my program:
[best description of problem you can manage][name and version of the program][(optional) Operating System Version ex. Windows 10]
Something is wrong with my computer:
[best description of problem you can manage] [Operating System Version ex. Windows 10][(optional) Model of computer ex. Acer, Lenovo etc.]
When describing the problem, think about what things are working as expected and what things aren’t. Omit extra phrases like “why won’t” and “how come”, though sometimes adding “how to fix” can be helpful.
For old programs or operating systems that have new versions with similar names, it can sometimes be beneficial to use the search engine tools to restrict the results to before a certain date, like 2015. This will keep irrelevant discussions about modern versions from clogging up your results.
Some examples of searches using these formats:
microphone detected but no audio windows 10 Lenovo laptop
Webcam working but camera black discord
Minecraft Java Edition low framerate
Icons invisible desktop windows 10
You might need to look at quite a few search results before finding a solution to your problem, perhaps tweaking the phrasing along the way. You might also not find a solution at all. In that case, you could try contacting customer support, or see if someone with more computer experience can help you.
Anyway, I’m just about out of ideas, so I’ll end the post here.
0 notes
Text
What's Inside An Asic Bitcoin Miner? Bitstarz News
With our PROFESSIONALISM, SINCERITY, and EFFORTS, we now have gained belief and support from worldwide clients. Get an instant overview of your every day and monthly profit with our free mining profit calculator. [newline]The first website is a decommissioned energy plant in Niagara Falls, N.Y. The facility — developed as a JV with North East Data LLC — was accomplished in report time and is presently working with all new era mining hardware (ASIC and FPGA). Antminer Space Heater Editions harness the heat generated by ASIC miners for different purposes, effectively turning waste heat right into a valuable useful resource. These devices are engineered to direct the warmth generated during mining into a managed airflow, efficiently heating the encompassing area.
The networking mode used within the S19J Pro Miner is RJ45 Ethernet 10/100M, and the net weight of this ASIC miner outdoors the packaging is 14.6 kg. The operator of the ASIC miner should verify the enter voltage earlier than plugging the power provide into the Antminer S19 mannequin, because the mistaken voltage can cause serious harm to the ASIC miner chip. To ensure the security of Antminer’s firmware from exterior viruses, the Secure Boot choice is enabled by default on the system, and root entry is also disabled. So after this detailed rationalization about Antminer S19 Series lets head over to the technical specs of the four ASIC fashions supplied by Bitmain company.

The Jasminer X4-1U is taken into account to be among the most energy-efficient Classic Ethereum miners around, which is why it’s among the many finest ASIC miners money should buy. Noise levels are simply sixty five dB, which signifies that it may be utilized in residential areas. 3 GH/s is the hash price discovered on this miner, which is a superb enchancment. With Bitmain recognized for creating Bitcoin miners, this Classic Ethereum unit is a game-changer. First, there may be an Innosilicon A10 Pro+ that hummers at 750 MH/s, which is better than this ASIC mining device.
This is as a end result of newer and extra environment friendly ASIC miners are continually being developed, making older fashions much less competitive in the mining market. It has devoted hardware and software to process transactions and mine cash faster than different types of computer systems. However, because of the ever-evolving nature of cryptocurrency know-how, these machines could turn out to be obsolete. The WhatsMiner M32-62T-52W, one other of the most effective ASIC miners, is designed for the mining of cryptocurrencies that use the SHA-256 algorithm. It was launched in 2021 by MicroBT, one of the leading manufacturers of ASIC mining hardware.
Profitability is decided by the machine’s price per TH, what number of watts the machine uses per TH, and your internet hosting prices. It is unnecessary to buy cheaper or seemingly more environment friendly machines if they break down after a couple of months of operating. This is why shopping for bitcoin on an trade is normally a simpler method to make a revenue. However, when done efficiently it's possible to make a more profit mining bitcoin than merely buying and ‘hodling’ (a time period used to describe the act of not promoting your bitcoin). Roughly each ten minutes a specific number of newly-minted bitcoin is awarded to the particular person with a mining machine that is quickest to discover the new block.
For example, you wouldn’t mine zcash (ZEC) with the identical equipment — or in the same method — that you’d mine bitcoin money (BCH). Antminer S19 Pro ASIC mining machines are designed exactly for mining cryptocurrencies like Bitcoin (BTC), Bitcoin Cash (BCH), and Bitcoin SV (BSV). Bitmain has developed 4 ASIC fashions under the S19 Pro series, which are thought-about your finest option for big mining farms and particular person customers worldwide. This S19 Pro ASIC miner has a power efficiency of 29.5±5% J/TH, which is far more than its earlier fashions, and operates at a power supply of 3250 ± 5% Watts. The formulation behind reaching the bottom vary of power effectivity, near 23 J/TH, within the Antminer S19 sequence is the improved circuit structure, which is achieved by constructing customized chips.
As a result, it's now onerous for Bitcoin miners to make a profit, making Bitcoin mining not as worthwhile because it was once. GPUs are most often used within the strategy of cryptocurrency mining, as they supply a a lot sooner, more highly effective alternative to standard CPU (Central Processing Unit) mining. The kind of GPU you’ll have to mine a specific coin depends on several components, such because the coin’s algorithm and popularity. Depending in your budget constraints and personal preferences, you'll find a way to select from one or many various GPUs for these specific coin mining operations. In the world of cryptocurrency mining, the hash rate is the quintessential issue that determines how much profit you make. A decrease hash rate means that you've got a considerably decrease probability of mining the following block and getting the mining reward.
This will create more demand for miners, and push the prices of machines higher. Expressed in https://horizonminers.com/ , this metric is essential for miners because electrical energy prices can significantly influence profitability. ASIC stands for “Application-Specific Integrated Circuit miner.” It is principally a very powerful, high-performance hardware that is designed to mine for cryptocurrency.
ASIC mining has type of divided the whole cryptocurrency neighborhood into two components – those that like it and individuals who hate it. That is why cryptocurrencies have been particularly created for utterly blocking ASIC mining. For instance, Bitcoin Gold, Super Bitcoin, BitcoinZ, and so forth., had been created partially for that reason.
#iceriver ks0#antminer ka3#cooling miner#s19k pro#asic mining#antminer k7#ka3 miner#iceriver ks0 pro#ks0 pro#ks0#asics miners#bitmain antminer ka3#antminer x5#kda miner ka3#s19 90t#antminer l7#bitmain antminer l7#kadena ka3#ks0 miner#bitmain antminer k7#asic immersion cooling kit#jasminer#asic miners#s19j pro#antminer d9#bitmain x5#s19k#immersion cooling mining#bitmain antminer l7 9.5 gh#antminer ks3
1 note
·
View note
Text
What is really a cyber threat

Cyberattacks are numerous and do not distinguish between companies and individuals when targeting a target. You've most likely heard the term "cyber threat" in the media before, but what exactly are we talking about? Other ways you may have heard this are “cyberthreat”, “cyberattack” or similar.

What is a Cyber Threat?
Today the term "cyber threat" is used predominantly in the world of information security.
A cyber threat is a malicious act conceived with the purpose of damaging systems, stealing data or any purpose that has the purpose of causing damage of any kind. Viruses, data breaches and DDoS attacks are included. Even if the threat is virtual, what is real is the attacker's intent as well as the potential impact. While many cyberattacks are mere nuisances, some are quite serious. Some even potentially threaten human lives.
The potential impact that these kinds of attacks can have is often underestimated. Most of the time, the attacks are easily identifiable and do not pose much risk. Instead, other times it happens to come across some more sophisticated threats, difficult to identify, which represent a big problem even for many companies.
Cyber threats are a major concern for businesses. Cyberattacks can lead to power outages, government equipment failures, and breaches of state secrets. They can manipulate telephone and computer networks or, as in the case of ransomware, they can cripple entire systems by making data inaccessible.
Every day new companies and organizations set foot in the digital world with awareness of the risks associated with their technological infrastructures. In some cases, cyber threats are underestimated and this often means great economic and image damage for the company that has underestimated cyber threats and security.
The increase in IT-related risks is real, as are data security solutions. The best thing to do is to take the necessary safety measures right away.
Types of Cyber Threats
The types of cyber threats are numerous, and it must also be considered that they are constantly evolving. The intent of hackers is usually to secure an economic gain by carrying out sabotage, espionage or data theft operations. As a result, they can be expected to do everything possible to achieve their ends.
Virtually every cyber threat falls into one of the following ten types of risks. Hackers have an abundance of options to choose from in order to operate. Furthermore, computer literacy is all in all poor, so hackers often have an easy time, especially for small local realities.
The 10 most common types of computer threats
Malware
It is a type of software that executes a malicious command on a device or within a computer network, corrupting data or taking control of the system.
Phishing
Phishing is an e-mail attack that consists of tricking the recipient into revealing confidential information or inviting him to download malware by clicking on a link in the body of the message. These are real scams, which we have talked about extensively in other articles. Often they don't even involve great IT skills on the part of the attacker, just a little social engineering.
Vishing
Vishing is a more sophisticated form of phishing in which the hacker uses VoIP technology to contact the victim, attempting to trick them. There is also a variant that instead uses text messages to attack, it is called smishing.
Man in the Middle
As the name suggests, this type of attack refers to when a hacker intervenes in a conversation posing as one of the two parties, with the aim of stealing sensitive information. What we often don't think about is that the conversation is between two machines and therefore not immediate to monitor.
Trojan viruses
The origin of its name is inspired by the famous Trojan Horse of ancient Greece. Trojan is a type of malware that infiltrates a computer system by hiding its true nature. For example, it could impersonate known software and then release malicious code once inside the host device.
Ransomware
Ransomware is an attack that uses encryption to make information on a system inaccessible. The aim is to demand a ransom in exchange for being able to access the data again. Possibilità che a volte, in realtà, non è nemmeno assicurata.
DDoS attack
It occurs when the attacker uses many devices to overload a target, such as a website, with requests, causing it to crash or become instabilities.
Attacks on IoT devices
This is an increasingly popular attack due to the nature of the targets. Devices such as sensors or industrial plants connected to the network are vulnerable to multiple types of cyber threats. The hacker could take control of the device and then later use it in a DDoS attack. Alternatively it could steal the information present in the device itself obtaining important data to continue the attack. Given their number of frequently out-of-date operating systems, IoT devices are a very attractive target.
Malware in mobile applications
Phones and tablets are just as vulnerable to malware as any other device. È possibile inserire malware all’interno di app, nei siti web o nelle e-mail sfruttando il phishing. Once compromised, a mobile device can provide access to personal information, location data, and financial accounts.
A recent example of this type of eventuality is Pegasus software, which is used to monitor and collect data from journalists around the world. (Source: The Guardian)
Practical defense and prevention solutions
Cyber threats are always expanding and improving. Millions of them are created every year, many of them follow the aforementioned characteristics, but others are technologically more complex and more powerful.
Fortunately, however, there are also more and more highly qualified companies in the field of IT security that offer cutting-edge tools and services that help prevent, identify and promptly block all kinds of IT attacks.
Threat detection tools
Threat detection tools are an essential part of a company's cybersecurity technology stack. Threat detection is also the first defense against any Cyber Threat.
Specific solutions, such as the use of a SOCaaS, for example, are of vital importance for safeguarding an IT infrastructure, thanks also to the integration of the SIEM engine which includes UBA and UEBA, guaranteeing complete control also over the users.
Another useful tool is definitely ACP. Acronis Cyber Protect is a solution that integrates data protection and management to safeguard your endpoints, data and systems. Its automation capabilities provide unparalleled protection, enabling businesses to increase their productivity and reduce risk.
Vulnerability Assessment & Penetration Test (VA-PT)
Services like VA & PT are field tests that test the infrastructure in a concrete context. Our teams of white hat hackers find vulnerabilities within the system to point the finger at weaknesses to fix.

Conclusions
We have learned what a cyber threat is and its most common types, also discovering which solutions can be adopted in order to guarantee better corporate and employee safety.
What countermeasures has your company taken to protect your safety? If you would like more information about it, you can contact us by pressing the button below. We offer ad hoc services and solutions to strengthen corporate defenses.
Useful links
- Computer network security: PT vs. VA
- What is Phishing? Understand and detect social engineering attacks
- Ethical Phishing Attacks - Test your company!
- What is a Network Lateral Movement and how to defend yourself
Read the full article
0 notes