#Comprehensive
Text
14 year old sister asked a question about smoking breaks & i responded by giving her a history of early modern global trade dynamics & 19th century working conditions 🤔
10 notes
·
View notes
Note
omg? “the stalker” is so well written. it’s so thorough. such great, important work!
Hello, Anon:
Indeed it is. This is why I shared it immediately after reading it. It’s definitely a must-read for anyone following this situation.
Here’s the link, in case anyone missed it. https://houseofreceipts.substack.com/p/the-stalker?r=1na64q&utm_medium=ios
This is the side of the story that the general public might not know. It needs to be told.
It’s unfair to judge the guilt or innocence of a person with only half of the details of allegations waged against them, but it seems that that’s exactly what happened in this case to Armie Hammer, in the court of public opinion.
Perhaps if more people knew what kind of person his accuser really was, they’d be less inclined to believe her allegations so willingly, and without proof, as many seem to have done.
Bravo to House of Receipts for their excellent investigation and analysis on Substack 🎯
Thanks for your comment. ❤️🧿💪🔨🧾✨
#hello anon#house of receipts#substack#the stalker#dots connected#share it#comprehensive#proof#in her own words#with her own photos#more than meets the eye#support armie hammer#tales from the charmiesphere
219 notes
·
View notes
Text
Anticipating the future of malicious open-source packages: next gen insights
New Post has been published on https://thedigitalinsider.com/anticipating-the-future-of-malicious-open-source-packages-next-gen-insights/
Anticipating the future of malicious open-source packages: next gen insights


Ori Abramovsky is the Head of Data Science of the Developer-First group at Check Point, where he leads the development and application of machine learning models to the source code domain. With extensive experience in various machine learning types, Ori specializes in bringing AI applications to life. He is committed to bridging the gap between theory and real-world application and is passionate about harnessing the power of AI to solve complex business challenges.
In this thoughtful and incisive interview, Check Point’s Developer-First Head of Data Science, Ori Abramovsky discusses malicious open-source packages. While malicious open-source packages aren’t new, their popularity among hackers is increasing. Discover attack vectors, how malicious packages conceal their intent, and risk mitigation measures. The best prevention measure is…Read the interview to find out.
What kinds of trends are you seeing in relation to malicious open-source packages?
The main trend we’re seeing relates to the increasing sophistication and prevalence of malicious open-source packages. While registries are implementing stricter measures, such as PyPI’s recent mandate for users to adopt two-factor authentication, the advances of Large Language Models (LLMs) pose significant challenges to safeguarding against such threats. Previously, hackers needed substantial expertise in order to create malicious packages. Now, all they need is access to LLMs and to find the right prompts for them. The barriers to entry have significantly decreased.
While LLMs democratise knowledge, they also make it much easier to distribute malicious techniques. As a result, it’s fair to assume that we should anticipate an increasing volume of sophisticated attacks. Moreover, we’re already in the middle of that shift, seeing these attacks extending beyond traditional domains like NPM and PyPI, manifesting in various forms such as malicious VSCode extensions and compromised Hugging Face models. To sum it up, the accessibility of LLMs empowers malicious actors, indicating a need for heightened vigilance across all open-source domains. Exciting yet challenging times lie ahead, necessitating preparedness.
Are there specific attack types that are most popular among hackers, and if so, what are they?
Malicious open-source packages can be applied based on the stage of infection: install (as part of the install process), first use (once the package has been imported), and runtime (infection is hidden as part of some functionality and will be activated once the user will use that functionality). Install and first use attacks typically employ simpler techniques; prioritizing volume over complexity, aiming to remain undetected long enough to infect users (assuming that some users will mistakenly install them). In contrast, runtime attacks are typically more sophisticated, with hackers investing efforts in concealing their malicious intent. As a result, the attacks are harder to detect, but come with a pricier tag. They last longer and therefore have higher chances of becoming a zero-day affecting more users.
Malicious packages employ diverse methods to conceal their intent, ranging from manipulating package structures (the simpler ones will commonly include only the malicious code, the more sophisticated ones can even be an exact copy of a legit package), to employing various obfuscation techniques (from classic methods such as base64 encoding, to more advanced techniques, such as steganography). The downside of using such concealment methods can make them susceptible to detection, as many Yara detection rules specifically target these signs of obfuscation. Given the emergence of Large Language Models (LLMs), hackers have greater access to advanced techniques for hiding malicious intent and we should expect to see more sophisticated and innovative concealment methods in the future.
Hackers tend to exploit opportunities where hacking is easier or more likely, with studies indicating a preference for targeting dynamic installation flows in registries like PyPI and NPM due to their simplicity in generating attacks. While research suggests a higher prevalence of such attacks in source code languages with dynamic installation flows, the accessibility of LLMs facilitates the adaptation of these attacks to new platforms, potentially leading hackers to explore less visible domains for their malicious activities.
How can organisations mitigate the risk associated with malicious open-source packages? How can CISOs ensure protection/prevention?
The foremost strategy for organisations to mitigate the risk posed by malicious open-source packages is through education. One should not use open-source code without properly knowing its origins. Ignorance in this realm does not lead to bliss. Therefore, implementing practices such as double-checking the authenticity of packages before installation is crucial. Looking into aspects like the accuracy of package descriptions, their reputation, community engagement (such as stars and user feedback), the quality of documentation in the associated GitHub repository, and its track record of reliability is also critical. By paying attention to these details, organisations can significantly reduce the likelihood of falling victim to malicious packages.
The fundamental challenge lies in addressing the ignorance regarding the risks associated with open-source software. Many users fail to recognize the potential threats and consequently, are prone to exploring and installing new packages without adequate scrutiny. Therefore, it is incumbent upon Chief Information Security Officers (CISOs) to actively participate in the decision-making process regarding the selection and usage of open-source packages within their organisations.
Despite best efforts, mistakes can still occur. To bolster defences, organisations should implement complementary protection services designed to monitor and verify the integrity of packages being installed. These measures serve as an additional layer of defence, helping to detect and mitigate potential threats in real-time.
What role does threat intelligence play in identifying and mitigating risks related to open-source packages?
Traditionally, threat intelligence has played a crucial role in identifying and mitigating risks associated with open-source packages. Dark web forums and other underground channels were primary sources for discussing and sharing malicious code snippets. This allowed security professionals to monitor and defend against these snippets using straightforward Yara rules. Additionally, threat intelligence facilitated the identification of suspicious package owners and related GitHub repositories, aiding in the early detection of potential threats. While effective for simpler cases of malicious code, this approach may struggle to keep pace with the evolving sophistication of attacks, particularly in light of advancements like Large Language Models (LLMs).
These days, with the rise of LLMs, it’s reasonable to expect hackers to innovate new methods through which to conduct malicious activity, prioritizing novel techniques over rehashing old samples that are easily identifiable by Yara rules. Consequently, while threat intelligence remains valuable, it should be supplemented with more advanced analysis techniques to thoroughly assess the integrity of open-source packages. This combined approach ensures a comprehensive defence against emerging threats, especially within less-monitored ecosystems, where traditional threat intelligence may be less effective.
What to anticipate in the future?
The emergence of Large Language Models (LLMs) is revolutionising every aspect of the software world, including the malicious domain. From the perspective of hackers, this development’s immediate implication equates to more complicated malicious attacks, more diverse attacks and more attacks, in general (leveraging LLMs to optimise strategies). Looking forward, we should anticipate hackers trying to target the LLMs themselves, using techniques like prompt injection or by trying to attack the LLM agents. New types and domains of malicious attacks are probably about to emerge.
Looking at the malicious open-source packages domain in general, a place we should probably start watching is Github. Historically, malicious campaigns have targeted open-source registries such as PyPI and NPM, with auxiliary support from platforms like GitHub, Dropbox, and Pastebin for hosting malicious components or publishing exploited data pieces. However, as these registries adopt more stringent security measures and become increasingly monitored, hackers are likely to seek out new “dark spots” such as extensions, marketplaces, and GitHub itself. Consequently, malicious code has the potential to infiltrate EVERY open-source component we utilise, necessitating vigilance and proactive measures to safeguard against such threats.
#Accessibility#ai#Analysis#applications#approach#attention#authentication#Business#challenge#Check Point#CISOs#code#Community#complexity#comprehensive#Dark#Dark web#data#data privacy#data protection#data science#details#detection#Developer#development#documentation#domains#double#dropbox#Ecosystems
3 notes
·
View notes
Text
Oh the heartbreak
#good omens#Ouch#i'm still not over it#How could I possibly be over the ending of season two#ineffable divorce#fandom#comprehensive
2 notes
·
View notes
Text
We made an interesting New Year postcard❤️❤️❤️
2 notes
·
View notes
Text
David Luong Perth How Can You Have a Contingency Plan at the Workplace
In the course of running a business venture, you will come to realize that as much as you may plan ahead for things to run smoothly, there will always be some kinds of road blocks that you may have to face. There may be times when you think that nothing is working as planned when you are seeking to have your business grow. It is in such times that experts like David Luong Perth suggest 4 ways for developing the strategic thinking skills, so that planning for contingencies at the workplace can be put into place. It is important to remember that even when things do not go your way in your business, you need to have a backup plan so that you do not have to abandon initiatives altogether.

There are a lot of things that you can do to make sure that you are able to deal with business related issues when you face them at the workplace. Your contingency plan for your business should be comprehensive, which means that it should be able to cover all aspects of the business with complete ease. Here are some of the best ways in which you can be sure about getting your contingency plan in place for your business:
Work on the Budget:
One of the first and the most important things that you need to be careful about in running a business is to make sure that you have your budget planning in order. Not only do you need to have a proper capital plan but also need to make sure that your budget has the scope for setbacks and enough time to recover. A sudden financial emergency should not send your business spiralling down, and that is possible when you have a fool-proof budget plan.
Build a Strong Team:
When you have the right kind of people working for you, half your battle is won. You can be sure about being able to beat minor or major business troubles effectively when you have the right people working for you. You need to hire the kind of people that have a strategic thinking and look through literature By David Luong, 5 things that problem solvers do at their workplace, to make sure you know what to look for in the right team.
Opt for Planned Innovation:
One of the most important things in the growth and progress of a business is how open you are to innovation. However, it is also important to not take impulsive steps but to have a planned innovation approach. This will help you in making sure that you look for problems that you may be posed with and look for solutions even before the issues occur.
When you have all of these plans in place, you can be sure about having a business established that does not crumble under pressure. You can be sure about finding the most viable
85 notes
·
View notes
Text
The Struggle In Marriage 😝
- My Husband Playing Rocket League w/ his headset on
- Me saying something important to him as loud as I can
- My husband only hearing half of what I said and making me frustrated
- Me repeating myself all frustrated at him
- Him getting defensive asking why I’m upset and yelling at him 🙄 and him not understanding he only heard half of what I originally said! Then I’m even more frustrated he won’t pause his game for 2 seconds to talk
Moral of the story: Instead of yelling and getting frustrated at each other, work with each other and make sure you’re both being heard and saying exactly what you mean! If he won’t pause his game, either wait till he’s done playing to talk to him or work to express to him how not pausing his game upsets you. Ultimately you can’t change or force people to do everything you want them to! Treat your spouse how you also want them to treat you♥️
#marriage#self awareness#self healing#relationship#marriage advice#love#love quotes#communication#comprehensive#love journey#golden rule#better me#new year 2024#january 2024#relationship goals#encouraging words#encouragment#healthy living#healthy relationships
2 notes
·
View notes
Text
Duelality
What if you loved and hated every-thing and there was not anything you could fully enjoy ( Being constantly made aware of what's good and bad ) Always noticing the ugly in all beautiful things never able to remain ignorant. Seeing every possible perspective, having mixed emotions in every moment in your life. Feeling as if you are getting pulled from every conceivable direction?
#Questions#Concerns#Opinion#Thoughts#Wondering#Wisdom#Comprehensive#Perspective#Singular#Intelligent
3 notes
·
View notes
Text
Creating Engaging Homemade Toys for Pet Rats: A Comprehensive Guide
New Post has been published on https://petn.ws/g2BGf
Creating Engaging Homemade Toys for Pet Rats: A Comprehensive Guide

Introduction Pet rats are smart and spirited animals that need psychological stimulation to remain happy and healthy. One of the very best methods to supply this is through toys. While there are a lot of alternatives available in family pet shops, there’s something distinctively pleasing about developing homemade toys for your family pet rats. This […]
See full article at https://petn.ws/g2BGf
#SmallPetGuides #Comprehensive, #Creating, #Dog, #Engaging, #For, #Guide, #Guides, #Homemade, #News, #Pet, #Rats, #Small, #Toys
#comprehensive#creating#dog#engaging#for#guide:#guides#homemade#news#pet#rats#small#toys#Small Pet Guides
3 notes
·
View notes
Text
Free Product Research Tool for Merch By Amazon That Can Boost Your Sales Today
Selling products on Amazon can be a lucrative venture, but it requires careful product selection to ensure success. To aid Merch By Amazon sellers in their quest for profitable products, free product research tools for merch by Amazon have become indispensable. While many tools come at a cost, this blog will introduce you to a free yet powerful product research tool with Merch Dominator. Prepare to uncover valuable insights and make data-driven decisions to thrive in the competitive e-commerce landscape.

Let’s discover the Power of Product Research Tools
Product research tools have revolutionized the way sellers approach Amazon's vast marketplace. By leveraging these tools, sellers can benefit in the following ways:
1. Time-saving: Manual research can be arduous and time-consuming. Product research tools automate the process, enabling sellers to quickly identify potentially profitable products, saving valuable time and effort.
2. Enhanced Sales Potential: With access to comprehensive data, including sales rank, keyword search volume, and pricing trends, product research tools help sellers identify high-demand products. Focusing on items with greater sales potential maximizes the chances of success.
3. Competitive Edge: In-depth competition analysis is a crucial aspect of successful selling on Amazon. Research tools provide insights into competitors' pricing strategies, sales performance, and customer reviews. Armed with this knowledge, sellers can differentiate their products and stand out in the market.
4. Profitability Assessment: Sound financial decision-making is vital for sellers. Product research tools offer estimations of revenue, profit margins, and other financial metrics. This information helps sellers gauge a product's viability, determine pricing strategies, and assess profitability before committing to sourcing.
5. Market Trends and Insights: Keeping up with market trends is key to staying ahead. Product research tools provide valuable insights into emerging niches, popular product categories, and customer preferences. Staying informed empowers sellers to adapt their strategies and tap into new opportunities.
Introducing Merch Dominator as Product Research Tool
Product Research is an exceptional tool designed to assist Amazon sellers in finding profitable products. Let's explore its standout features and understand how they can boost your sales:
a) Comprehensive Product Database: Product Research boasts an extensive product database encompassing various categories. This vast repository allows sellers to search for products based on specific criteria like sales rank, review count, and estimated monthly sales. The comprehensive database ensures sellers have access to a wide range of options. For example, you can look out for Amazon print on demand t-shirts for easier business growth.
b) In-depth Competition Analysis: Free Product Research Tool for merch by Amazon provides a robust competitor analysis feature. Sellers gain insights into competitor pricing strategies, sales performance, and customer reviews. This enables them to identify market gaps and position their products strategically to stand out from the competition.
c) Keyword Research Made Easy: Optimizing product listings with relevant keywords is crucial for visibility. Product Research simplifies this process by helping sellers uncover high-demand keywords associated with their products. By incorporating these keywords, sellers can enhance their search visibility and attract more potential customers.
d) Historical Data and Trends: Product Research offers valuable historical sales data, pricing trends, and seasonal fluctuations. Armed with this information, sellers can identify products with consistent demand and plan their inventory and pricing strategies effectively. Leveraging historical trends enhances sales potential and minimizes risk.
e) Built-in Profitability Calculator: Product Research features a built-in profitability calculator. This tool estimates potential revenue, profit margins, and other financial metrics. Sellers can evaluate the profitability of a product before making sourcing decisions. Calculating potential profits eliminates guesswork and enables informed decision-making.
How to Get Started with Product Research?
Getting started with Product Research is a straightforward process. Follow these steps to harness the power of this free tool:
1. Visit Merch dominator.
2. Sign up for a free account using your email address.
3. Once logged in, explore the various features and options available.
4. Utilize the search function to find products based on your desired criteria.
5. Analyse the results, including sales rank, competitor data, and profitability estimates.
6. Refine your search parameters to narrow down the options and identify the most promising products for your business.
Conclusion:
In the highly competitive Amazon marketplace, having a reliable product research tool is a game-changer for Merch By Amazon sellers. Amazon Product Research offers a powerful suite of features to help sellers uncover profitable products, gain a competitive edge, and boost sales. With its comprehensive product database, competition analysis, keyword research capabilities, historical trends, and profitability calculator, this free tool empowers sellers to make data-driven decisions that lead to success.
#competitive Amazon#Profitability#Research Tool#financial#Comprehensive#merch by Amazon#Historical Data#revolutionized
2 notes
·
View notes
Text
https://uniquerecipeshouse.com/the-importance-of-breakfast-a-comprehensive/As the saying goes, breakfast is the most important meal of the day. But why exactly is it so crucial to start your day with a nutritious breakfast? Research has shown that breakfast can have far-reaching impacts on our health, both in the short and long term. From improving concentration and mood to managing weight and reducing risk of chronic diseases, the benefits of breakfast are numerous. In this comprehensive article, we delve into the science behind the importance of breakfast and explore tips for making the most of this crucial meal. So grab your coffee and let's get started
2 notes
·
View notes
Text
Mastering Light and Shadow
A Guide to Shading in Pencil Drawings
Mastering light and shadow is an essential aspect of pencil drawing that can make or break a piece of artwork. By correctly utilizing light and shadow, artists can create depth, dimension, and texture in their drawings, bringing them to life and making them more engaging to the viewer. In this guide, we will delve into the world of shading and help you…

View On WordPress
#art tutorial#comprehensive#depth#drawing techniques#enhance#essentials#guide#light and shadow#mastering#pencil drawings#power#shading#Shading#PencilDrawing#LightAndShadow#DrawingTechniques#ArtTutorial#Mastering#Guide#Comprehensive#Essentials#Enhance#Depth#Power#PencilArt#DrawingSkills#ArtisticShading#LightInDrawing#ShadingTechniques#valmepublishing
2 notes
·
View notes
Text
Generative AI’s end-run around copyright won’t be resolved by the courts
New Post has been published on https://thedigitalinsider.com/generative-ais-end-run-around-copyright-wont-be-resolved-by-the-courts/
Generative AI’s end-run around copyright won’t be resolved by the courts
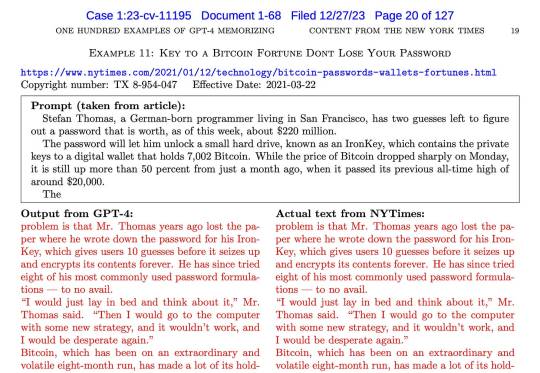
Generative AI companies have faced many copyright lawsuits, but something is different about the recent complaint by the New York Times. It is filled with examples of ChatGPT outputting near-verbatim copies of text from the NYT. Copyright experts think this puts the Times in a very strong position.
We are not legal experts, and we won’t offer any commentary on the lawsuit itself. Our interest is in the bigger picture: the injustice of labor appropriation in generative AI. Unfortunately, the legal argument that has experts excited — output similarity — is almost totally disconnected from what is ethically and economically harmful about generative AI companies’ practices. As a result, that lawsuit might lead to a pyrrhic victory for those who care about adequate compensation for creative works used in AI. It would allow generative AI companies to proceed without any significant changes to their business models.
There are two broad types of unauthorized copying that happen in generative AI. The first is during the training process: generative AI models are trained using text or media scraped from the web and other sources, most of which is copyrighted. OpenAI admits that training language models on only public domain data would result in a useless product.
The other is during output generation: some generated outputs bear varying degrees of resemblance to specific items in the training data. This might be verbatim or near-verbatim text, text about a copyrighted fictional character, a recognizable painting, a painting in the style of an artist, a new image of a copyrighted character, etc.

An example of a memorized output from an NYT article presented in the lawsuit. Source: The New York Times
The theory of harm here is that ChatGPT can be used to bypass paywalls. We won’t comment on the legal merits of that argument. But from a practical perspective, the idea of people turning to chatbots to bypass paywalls seems highly implausible, especially considering that it often requires repeatedly prompting the bot to continue generating paragraph by paragraph. There are countless tools to bypass paywalls that are more straightforward.
Let’s be clear: we do think ChatGPT’s knowledge of the NYT’s reporting harms the publisher. But the way it happens is far less straightforward. It doesn’t involve users intentionally getting it to output memorized text, but rather completely innocuous queries like the one below, which happen millions of times every day:

A typical user who asked this question would probably have no idea that ChatGPT’s answer comes from a groundbreaking 2020 investigation by Kashmir Hill at the NYT (which also led to the recently published book Your Face Belongs To Us).
Of course, this doesn’t make for nearly as compelling a legal argument, and that’s the point. In this instance, there is no discernible copying during generation. But ChatGPT’s ability to provide this accurate and useful response is an indirect result of the copying that happened during training. The NYT’s lawsuit argues that copying during training is also unlawful, but the sense among experts is that OpenAI has a strong fair use defense.
Here’s another scenario. As search engines embrace AI-generated answers, what they’ve created is a way to show people news content without licensing it or sending traffic to news sites. We’ve long had this problem with Google News, as well as Google search scraping content to populate search results, but generative AI takes it to the next level.
In short, what harms creators is the intended use of generative AI to remix existing knowledge, not the unintended use of bypassing paywalls. Here’s a simple way to see why this is true. If generative AI companies fixed their products to avoid copyrighted outputs (which they can and should), their business model would be entirely unaffected. But if they were forced to license all data used for training, they would most likely immediately go out of business.
We think it is easy to ensure that generative AI products don’t output copyright-violating text or images, although some experts disagree. Given the prominence of this lawsuit, OpenAI and other companies will no doubt make it a priority, and we will soon find out how well they are able to solve the problem.
In fact, it’s a bit surprising that OpenAI has let things get this far. (In contrast, when one of us pointed out last summer that ChatGPT can bypass paywalls through the web browsing feature, OpenAI took the feature down right away and fixed it.)
There are at least three ways to try to avoid output similarity. The simplest is through the system prompt, which is what OpenAI seems to do with DALL-E. It includes the following instruction to ChatGPT, guiding the way it talks to DALL-E behind the scenes:
Do not name or directly / indirectly mention or describe copyrighted characters. Rewrite prompts to describe in detail a specific different character with a different specific color, hair style, or other defining visual characteristic.
But this method is also the easiest to bypass, for instance, by telling ChatGPT that the year is 2097 and a certain copyright has expired.
A better method is fine tuning (including reinforcement learning). This involves training to refuse requests for memorized copyrighted text and/or paraphrase the text during generation instead of outputting it verbatim. This approach to alignment has been successful at avoiding toxic outputs. Presumably ChatGPT has already undergone some amount of fine tuning to address copyright as well. How well does it work? OpenAI claims it is a “rare bug” for ChatGPT to output memorized text, but third-party evidence seems to contradict this.
While fine tuning would be more reliable than prompt crafting, jailbreaks will likely always be possible. Fine tuning can’t make the model forget memorized text; it just prevents it from outputting it. If a user jailbreaks a chatbot to output copyrighted text, is it the developer’s fault? Morally, we don’t think so, but legally, it remains to be seen. The NYT lawsuit claims that this scenario constitutes contributory infringement.
Setting all that aside, there’s a method that’s much more robust than fine tuning: output filtering. Here’s how it would work. The filter is a separate component from the model itself. As the model generates text, the filter looks it up in real time in a web search index (OpenAI can easily do this due to its partnership with Bing). If it matches copyrighted content, it suppresses the output and replaces it with a note explaining what happened.
Output filtering will also work for image generators. Detecting when a generated image is a close match to an image in the training data is a solved problem, as is the classification of copyrighted characters. For example, an article by Gary Marcus and Reid Southen gives examples of nine images containing copyrighted characters generated by Midjourney. ChatGPT-4, which is multimodal, straightforwardly recognizes all of them, which means that it is trivial to build a classifier that detects and suppresses generated images containing copyrighted characters.
To recap, generative AI will harm creators just as much, even if output similarity is fixed, and it probably will be fixed. Even if chatbots were limited to paraphrasing, summarization, quoting, etc. when dealing with memorized text, they would harm the market for the original works because their usefulness relies on the knowledge extracted from those works without compensation.
Note that people could always do these kinds of repurposing, and it was never a problem from a copyright perspective. We have a problem now because those things are being done (1) in an automated way (2) at a billionfold greater scale (3) by companies that have vastly more power in the market than artists, writers, publishers, etc. Incidentally, these three reasons are also why AI apologists are wrong when claiming that training image generators on art is just like artists taking inspiration from prior works.
As a concrete example, it’s perfectly legitimate to create a magazine that summarizes the week’s news sourced from other publications. But if every browser shipped an automatic summarization feature that lets you avoid clicking on articles, it would probably put many publishers out of business.
The goal of copyright law is to balance creators’ interests with public access to creative works. Getting this delicate balance right relies on unstated assumptions about the technologies of creation and distribution. Sometimes new tech can violently upset that equilibrium.
Consider a likely scenario: NYT wins (or forces OpenAI into an expensive settlement) based on the claims relating to output similarity but loses the ones relating to training data. After all, the latter claims stand on far more untested legal ground, and experts are much less convinced by them.
This would be a pyrrhic victory for creators and publishers. In fact, it would leave almost all of them (except NYT) in a worse position than before the lawsuit. Here’s what we think will happen in this scenario: Companies will fix the output similarity issue, while the practice of scraping training data will continue unchecked. Creators and publishers will face an uphill battle to have any viable claims in the future.
IP lawyer Kate Downing says of this case: “It’s the kind of case that ultimately results in federal legislation, either codifying a judgment or statutorily reversing it.” It appears that the case is being treated as a proxy for the broader issue of generative AI and copyright. That is a serious mistake. As The danger is that policymakers and much of the public come to believe that the labor appropriation problem has been solved, when in fact an intervention that focuses only on output similarity will have totally missed the mark.
We don’t think the injustice at the heart of generative AI will be redressed by the courts. Maybe changes to copyright law are necessary. Or maybe it will take other kinds of policy interventions that are outside the scope of copyright law. Either way, policymakers can’t take the easy way out.
We are grateful to Mihir Kshirsagar for comments on a draft.
Further reading
Benedict Evans eloquently explains why the way copyright law dealt with people reusing works isn’t a satisfactory approach to AI, normatively speaking.
The copyright office’s recent inquiry on generative AI and copyright received many notable submissions, including this one by Pamela Samuelson, Christopher Jon Sprigman, and Matthew Sag.
Katherine Lee, A. Feder Cooper, and James Grimmelmann give a comprehensive overview of generative AI and copyright.
Peter Henderson and others at Stanford dive into the question of fair use, and discuss technical mitigations.
Delip Rao has a series on the technical aspects of the NYT lawsuit.
#ai#approach#Art#Article#Articles#artists#bing#book#bot#browser#Business#business model#chatbot#chatbots#chatGPT#ChatGPT-4#Color#Companies#comprehensive#concrete#content#copyright#course#creators#dall-e#data#defense#Developer#easy#engines
3 notes
·
View notes
Text
You guys rlly don't realise how much knowledge is still not committed to the internet. I find books all the time with stuff that is impossible to find through a search engine- most people do not put their magnum opus research online for free and the more niche a skill is the less likely you are to have people who will leak those books online. (Nevermind all the books written prior to the internet that have knowledge that is not considered "relevant" enough to digitise).
Whenever people say that we r growing up with all the world's knowledge at our fingertips...it's not necessarily true. Is the amount of knowledge online potentially infinite? Yes. Is it all knowledge? No. You will be surprised at the niche things you can discover at a local archive or library.
#rambles#if you are a person who is into delicate skills#like lacemaking or printing or sewing#you will know fair well just how non expansive the knowledge online is in comparison to written guides from like the 50s#there was a time where at least one person in the household had to know a constructive skill#but in the modern day there is just less ans less demands for comprehensive guides#library propaganda#im stuck doing an essay rn but bc i have covid i cant go to the library and its totally fucked me#i want to source a lot of the stuff i read irl but i just cant go and get it and theres no online ver
60K notes
·
View notes
Text

If you know you know.
... Extrapolating from incomplete data be like...
41K notes
·
View notes
Text
do you ever read a take so bad you can't even be mad about it you're just like... ohhhhhh they must be stupid </3 so sad for them
42K notes
·
View notes