#DNS
Text
Beneath the Surface

Signs of a ship's passage can persist long after it's gone. The churn of its propellers and the oil leaked from its engines leave a mark on the water's surface that, in some cases, is visible even from orbit. (Image credit: A. Calado and E. Balaras)
Read the full article
#2023gofm#CFD#computational fluid dynamics#direct numerical simulation#DNS#fluid dynamics#physics#science#turbulence
129 notes
·
View notes
Text

I have now obtained enough followers on tumblr dot com that I can force you all to look at my favorite image of all time
#196#openbsd#tech support#unix#dns#boomerposting#bithc im wipe the ubi firmware in 10s and have openbsd/octeon in within an hour#reddit migration#reddit blackout
236 notes
·
View notes
Text

Louder for the people on the back, Fred!
66 notes
·
View notes
Text

Fanart of @wszczebrzyszynie ocs
I so love its characters and their story and felt really inspired to paint something
(I hope everything is drawn correctly also click for a better quality because it looks like ass in the preview!)
#i disappeared for a long time sorry#i had a lot on my head#im pretty proud of the colors and rendering on this one tho#edit: the more i look at the colors the more wrong they look on mobile#duch na strychu#oc art#oryginal character#illustration#art on tumblr#tw blood#dns#art
7 notes
·
View notes
Text
username layouts !
‹ ☁ ↳ name ! :3 ›
❛ 🤺⋮ name ! ❜
❝ ◌ name 🧸! ⸙ ˎˊ˗
🧸 ➭ name ❏ ೃ
🍡''┊name ! ˎˎˊ˗
♡❜ :// name❞
⇉ name !? ♡
< 🎸: name ❜
↳ // name ❞ 📍
🌈 --> name !
^ name! ;; ?
< name ദ
< : name ! --> ♡
🌷 name !? < ult 3
↳ // name ❞ ♡
< ♡ : name❜
♡ ❜ 🌷 name ! ❞
⇉ 🌷/ name ! ♡
: : name ! <00
'' name ! --> :3 ❞
❛ ⋮ name ! >
⇉ name︙<3
❝ name ._. ! ↺ "
: ❏ name !! >
⌗ name ! :<
⌨ name --> ❞
❛ ❏ name ¡! ꒱
< ➯ name ! <3
⇊ name ! ଓ
↺ < name > !
+ : name !
#dn ideas#simple layouts#short dn ideas#username ideas#random dn ideas#usernames#username layouts#dns#dn layouts#random layouts#<3
181 notes
·
View notes
Text
FINALLY! NEW KIRBY ART!
So for whatever reason, I've decided that Tiff (in every one of our AU's) loves axolotls. They're her favorite animal. Now in most AU's, she has a normal way to obsess over them. She'll read books on them and stuff like that.
DNS Tiff, however

Also every Tiff has a small blue axolotl plush named Wave. Meta Knight gave it to her on her birthday after Nightmare's death.
Fluffy Tiff obsesses over then randomly. She'll doodle them and talk about them endlessly.
#kirby#nintendo#hal laboratory#kirby right back at ya#digitalart#kirby au#ibispaintx#tiff#axolotls#Dawns New Star#Dawns New Star AU#DNS#DNS AU#au
13 notes
·
View notes
Note
Blockda 5 doesn’t appear to exist for iPhones. Any advice?
Use NextDNS. Per the app's description, you also need to create a (free) online account, set up adblocking on it, then connect that to your app:
You can set your configuration ID from your NextDNS account in the Settings to bring your blocking policy to your phone and get Analytics and Logs about your traffic.
If you do not have a NextDNS account yet, you can create one for free at https://nextdns.io.
I may have made other posts about it as well, search my blog for "iphone"
12 notes
·
View notes
Text
Charles must go through all the rituals against bad luck. This is incredible. 😫
15 notes
·
View notes
Text









#kpop moodboard#kpop icons#aesthetic#aesthetic kpop#kpop gg#cute kpop#kdecor#aesthetic moodboard#kpop aesthetic#kpop layouts#my gfx#dns#dont steal#give credit#messy locs
18 notes
·
View notes
Text
Yikes, thanks Tumblr
So uhhh
Custom domains are now a paid feature... by virtue of having to purchase a domain from Tumblr. And no, it's not just a fixed fee to use your own existing domain that you bought at like, Namecheap, Gandi, Porkbun or whatever...
No, Tumblr now sells domains and you can use only that for your custom blog names now. Unless you added one before and it became "Legacy Domain"...
And best of all, they don't even offer all the TLDs, so if you want a specific one, lol out of luck. I don't get what their goal was with this?
What's next? Kill entirety of "custom HTML + CSS themes"?

19 notes
·
View notes
Photo

kago 2021
35 notes
·
View notes
Text

Charles walks back to the paddock after his formation lap DNS | Brazilian Grand Prix | 5 November 2023
📸 Hoch Zwei
#at least the weather was nice for his little woodland adventure#really reaching here for positives#charles leclerc#brazilian gp 2023#dns
11 notes
·
View notes
Text
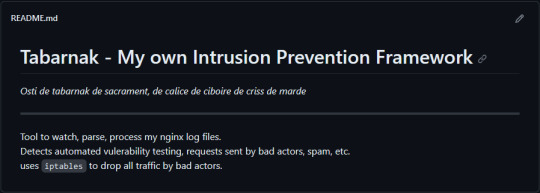
(this is a small story of how I came to write my own intrusion detection/prevention framework and why I'm really happy with that decision, don't mind me rambling)
Preface
About two weeks ago I was faced with a pretty annoying problem. Whilst I was going home by train I have noticed that my server at home had been running hot and slowed down a lot. This prompted me to check my nginx logs, the only service that is indirectly available to the public (more on that later), which made me realize that - due to poor access control - someone had been sending me hundreds of thousands of huge DNS requests to my server, most likely testing for vulnerabilities.
I added an iptables rule to drop all traffic from the aforementioned source and redirected remaining traffic to a backup NextDNS instance that I set up previously with the same overrides and custom records that my DNS had to not get any downtime for the service but also allow my server to cool down.
I stopped the DNS service on my server at home and then used the remaining train ride to think. How would I stop this from happening in the future? I pondered multiple possible solutions for this problem, whether to use fail2ban, whether to just add better access control, or to just stick with the NextDNS instance.
I ended up going with a completely different option: making a solution, that's perfectly fit for my server, myself.
My Server Structure
So, I should probably explain how I host and why only nginx is public despite me hosting a bunch of services under the hood.
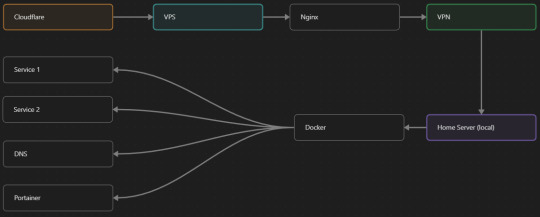
I have a public facing VPS that only allows traffic to nginx. That traffic then gets forwarded through a VPN connection to my home server so that I don't have to have any public facing ports on said home server. The VPS only really acts like the public interface for the home server with access control and logging sprinkled in throughout my configs to get more layers of security. Some Services can only be interacted with through the VPN or a local connection, such that not everything is actually forwarded - only what I need/want to be.
I actually do have fail2ban installed on both my VPS and home server, so why make another piece of software?
Tabarnak - Succeeding at Banning
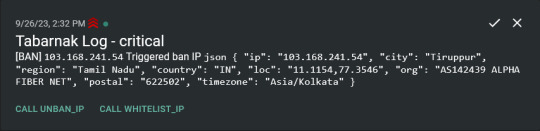
I had a few requirements for what I wanted to do:
Only allow HTTP(S) traffic through Cloudflare
Only allow DNS traffic from given sources; (location filtering, explicit white-/blacklisting);
Webhook support for logging
Should be interactive (e.g. POST /api/ban/{IP})
Detect automated vulnerability scanning
Integration with the AbuseIPDB (for checking and reporting)
As I started working on this, I realized that this would soon become more complex than I had thought at first.
Webhooks for logging
This was probably the easiest requirement to check off my list, I just wrote my own log() function that would call a webhook. Sadly, the rest wouldn't be as easy.
Allowing only Cloudflare traffic
This was still doable, I only needed to add a filter in my nginx config for my domain to only allow Cloudflare IP ranges and disallow the rest. I ended up doing something slightly different. I added a new default nginx config that would just return a 404 on every route and log access to a different file so that I could detect connection attempts that would be made without Cloudflare and handle them in Tabarnak myself.
Integration with AbuseIPDB
Also not yet the hard part, just call AbuseIPDB with the parsed IP and if the abuse confidence score is within a configured threshold, flag the IP, when that happens I receive a notification that asks me whether to whitelist or to ban the IP - I can also do nothing and let everything proceed as it normally would. If the IP gets flagged a configured amount of times, ban the IP unless it has been whitelisted by then.
Location filtering + Whitelist + Blacklist
This is where it starts to get interesting. I had to know where the request comes from due to similarities of location of all the real people that would actually connect to the DNS. I didn't want to outright ban everyone else, as there could be valid requests from other sources. So for every new IP that triggers a callback (this would only be triggered after a certain amount of either flags or requests), I now need to get the location.
I do this by just calling the ipinfo api and checking the supplied location. To not send too many requests I cache results (even though ipinfo should never be called twice for the same IP - same) and save results to a database.
I made my own class that bases from collections.UserDict which when accessed tries to find the entry in memory, if it can't it searches through the DB and returns results. This works for setting, deleting, adding and checking for records.
Flags, AbuseIPDB results, whitelist entries and blacklist entries also get stored in the DB to achieve persistent state even when I restart.
Detection of automated vulnerability scanning
For this, I went through my old nginx logs, looking to find the least amount of paths I need to block to catch the biggest amount of automated vulnerability scan requests. So I did some data science magic and wrote a route blacklist.
It doesn't just end there. Since I know the routes of valid requests that I would be receiving (which are all mentioned in my nginx configs), I could just parse that and match the requested route against that. To achieve this I wrote some really simple regular expressions to extract all location blocks from an nginx config alongside whether that location is absolute (preceded by an =) or relative. After I get the locations I can test the requested route against the valid routes and get back whether the request was made to a valid URL (I can't just look for 404 return codes here, because there are some pages that actually do return a 404 and can return a 404 on purpose).
I also parse the request method from the logs and match the received method against the HTTP standard request methods (which are all methods that services on my server use). That way I can easily catch requests like:
XX.YYY.ZZZ.AA - - [25/Sep/2023:14:52:43 +0200] "145.ll|'|'|SGFjS2VkX0Q0OTkwNjI3|'|'|WIN-JNAPIER0859|'|'|JNapier|'|'|19-02-01|'|'||'|'|Win 7 Professional SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|AA==|'|'|112.inf|'|'|SGFjS2VkDQoxOTIuMTY4LjkyLjIyMjo1NTUyDQpEZXNrdG9wDQpjbGllbnRhLmV4ZQ0KRmFsc2UNCkZhbHNlDQpUcnVlDQpGYWxzZQ==12.act|'|'|AA==" 400 150 "-" "-"
I probably over complicated this - by a lot - but I can't go back in time to change what I did.
Interactivity
As I showed and mentioned earlier, I can manually white-/blacklist an IP. This forced me to add threads to my previously single-threaded program. Since I was too stubborn to use websockets (I have a distaste for websockets), I opted for probably the worst option I could've taken. It works like this:
I have a main thread, which does all the log parsing, processing and handling and a side thread which watches a FIFO-file that is created on startup. I can append commands to the FIFO-file which are mapped to the functions they are supposed to call. When the FIFO reader detects a new line, it looks through the map, gets the function and executes it on the supplied IP.
Doing all of this manually would be way too tedious, so I made an API endpoint on my home server that would append the commands to the file on the VPS. That also means, that I had to secure that API endpoint so that I couldn't just be spammed with random requests.
Now that I could interact with Tabarnak through an API, I needed to make this user friendly - even I don't like to curl and sign my requests manually. So I integrated logging to my self-hosted instance of https://ntfy.sh and added action buttons that would send the request for me.
All of this just because I refused to use sockets.
First successes and why I'm happy about this
After not too long, the bans were starting to happen. The traffic to my server decreased and I can finally breathe again.
I may have over complicated this, but I don't mind. This was a really fun experience to write something new and learn more about log parsing and processing.
Tabarnak probably won't last forever and I could replace it with solutions that are way easier to deploy and way more general. But what matters is, that I liked doing it. It was a really fun project - which is why I'm writing this - and I'm glad that I ended up doing this.
Of course I could have just used fail2ban but I never would've been able to write all of the extras that I ended up making (I don't want to take the explanation ad absurdum so just imagine that I added cool stuff) and I never would've learned what I actually did.
So whenever you are faced with a dumb problem and could write something yourself, I think you should at least try. This was a really fun experience and it might be for you as well.
Post Scriptum
First of all, apologies for the English - I'm not a native speaker so I'm sorry if some parts were incorrect or anything like that.
Secondly, I'm sure that there are simpler ways to accomplish what I did here, however this was more about the experience of creating something myself rather than using some pre-made tool that does everything I want to (maybe even better?).
Third, if you actually read until here, thanks for reading - hope it wasn't too boring - have a nice day :)
8 notes
·
View notes
Text
Some thoughts about the voice acting in BG3. Note that these are all complaints on a very high level, the voice work is pretty fantastic overall. Also note that my knowledge about voice acting is superficial at best.
Lae'zel and Vlaakith are the only (?) githyanki you meet who talk Like That TM? All the other githyanki you meet seem to speak fairly normal, to the point where it is distracting.
I forgot his name but the comedian's son at the Elfsong has uh. Some questionable casting. He sounds like an old man.
I love and adore Abigail Thorne, but man, idk what went wrong, something is off about her voice work for Nocturne. Microphone quality? Insufficient mixing? Insufficient direction? Lack of experience in VA work specifically?
Same with JK Simmons as Kethric Thorm. It sounds Hella fucking off, and the guy is a legendary voice actor, so what went wrong there??
Very frequent cases of different voice lines in the same dialogue being at different volumes. Some lines are so quiet they are barely audible.
My biggest gripe: The PC voices being so unemotive. One of the key features in the series and related games is that the PC voices tend to have a lot of character. Rather than having a bunch of different pitch voices that don't have any personality to them, having a bunch of voice sets that give the PC more personality is something that I truly miss. Sad.
8 notes
·
View notes
Text
😔

seriously don't let this happen
9 notes
·
View notes
Text
Sleepy child. Meta prefers it when she's quiet, she's usually loud and full of energy. Poor orb.

"What do you mean this doesn't count as a hat??"
#Kirby#Kirby right back at ya#Kirby au#au#tiff#Meta Knight#digitalart#ibispaintx#nintendo#hal laboratory#Best to just let her sleep#Dawn's new Star AU#Dawns new Star#DNS#DNS Au
21 notes
·
View notes