#Fraud
Text
How I got scammed

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security

I wuz robbed.
More specifically, I was tricked by a phone-phisher pretending to be from my bank, and he convinced me to hand over my credit-card number, then did $8,000+ worth of fraud with it before I figured out what happened. And then he tried to do it again, a week later!
Here's what happened. Over the Christmas holiday, I traveled to New Orleans. The day we landed, I hit a Chase ATM in the French Quarter for some cash, but the machine declined the transaction. Later in the day, we passed a little credit-union's ATM and I used that one instead (I bank with a one-branch credit union and generally there's no fee to use another CU's ATM).
A couple days later, I got a call from my credit union. It was a weekend, during the holiday, and the guy who called was obviously working for my little CU's after-hours fraud contractor. I'd dealt with these folks before – they service a ton of little credit unions, and generally the call quality isn't great and the staff will often make mistakes like mispronouncing my credit union's name.
That's what happened here – the guy was on a terrible VOIP line and I had to ask him to readjust his mic before I could even understand him. He mispronounced my bank's name and then asked if I'd attempted to spend $1,000 at an Apple Store in NYC that day. No, I said, and groaned inwardly. What a pain in the ass. Obviously, I'd had my ATM card skimmed – either at the Chase ATM (maybe that was why the transaction failed), or at the other credit union's ATM (it had been a very cheap looking system).
I told the guy to block my card and we started going through the tedious business of running through recent transactions, verifying my identity, and so on. It dragged on and on. These were my last hours in New Orleans, and I'd left my family at home and gone out to see some of the pre-Mardi Gras krewe celebrations and get a muffalata, and I could tell that I was going to run out of time before I finished talking to this guy.
"Look," I said, "you've got all my details, you've frozen the card. I gotta go home and meet my family and head to the airport. I'll call you back on the after-hours number once I'm through security, all right?"
He was frustrated, but that was his problem. I hung up, got my sandwich, went to the airport, and we checked in. It was total chaos: an Alaska Air 737 Max had just lost its door-plug in mid-air and every Max in every airline's fleet had been grounded, so the check in was crammed with people trying to rebook. We got through to the gate and I sat down to call the CU's after-hours line. The person on the other end told me that she could only handle lost and stolen cards, not fraud, and given that I'd already frozen the card, I should just drop by the branch on Monday to get a new card.
We flew home, and later the next day, I logged into my account and made a list of all the fraudulent transactions and printed them out, and on Monday morning, I drove to the bank to deal with all the paperwork. The folks at the CU were even more pissed than I was. The fraud that run up to more than $8,000, and if Visa refused to take it out of the merchants where the card had been used, my little credit union would have to eat the loss.
I agreed and commiserated. I also pointed out that their outsource, after-hours fraud center bore some blame here: I'd canceled the card on Saturday but most of the fraud had taken place on Sunday. Something had gone wrong.
One cool thing about banking at a tiny credit-union is that you end up talking to people who have actual authority, responsibility and agency. It turned out the the woman who was processing my fraud paperwork was a VP, and she decided to look into it. A few minutes later she came back and told me that the fraud center had no record of having called me on Saturday.
"That was the fraudster," she said.
Oh, shit. I frantically rewound my conversation, trying to figure out if this could possibly be true. I hadn't given him anything apart from some very anodyne info, like what city I live in (which is in my Wikipedia entry), my date of birth (ditto), and the last four digits of my card.
Wait a sec.
He hadn't asked for the last four digits. He'd asked for the last seven digits. At the time, I'd found that very frustrating, but now – "The first nine digits are the same for every card you issue, right?" I asked the VP.
I'd given him my entire card number.
Goddammit.
The thing is, I know a lot about fraud. I'm writing an entire series of novels about this kind of scam:
https://us.macmillan.com/books/9781250865878/thebezzle
And most summers, I go to Defcon, and I always go to the "social engineering" competitions where an audience listens as a hacker in a soundproof booth cold-calls merchants (with the owner's permission) and tries to con whoever answers the phone into giving up important information.
But I'd been conned.
Now look, I knew I could be conned. I'd been conned before, 13 years ago, by a Twitter worm that successfully phished out of my password via DM:
https://locusmag.com/2010/05/cory-doctorow-persistence-pays-parasites/
That scam had required a miracle of timing. It started the day before, when I'd reset my phone to factory defaults and reinstalled all my apps. That same day, I'd published two big online features that a lot of people were talking about. The next morning, we were late getting out of the house, so by the time my wife and I dropped the kid at daycare and went to the coffee shop, it had a long line. Rather than wait in line with me, my wife sat down to read a newspaper, and so I pulled out my phone and found a Twitter DM from a friend asking "is this you?" with a URL.
Assuming this was something to do with those articles I'd published the day before, I clicked the link and got prompted for my Twitter login again. This had been happening all day because I'd done that mobile reinstall the day before and all my stored passwords had been wiped. I entered it but the page timed out. By that time, the coffees were ready. We sat and chatted for a bit, then went our own ways.
I was on my way to the office when I checked my phone again. I had a whole string of DMs from other friends. Each one read "is this you?" and had a URL.
Oh, shit, I'd been phished.
If I hadn't reinstalled my mobile OS the day before. If I hadn't published a pair of big articles the day before. If we hadn't been late getting out the door. If we had been a little more late getting out the door (so that I'd have seen the multiple DMs, which would have tipped me off).
There's a name for this in security circles: "Swiss-cheese security." Imagine multiple slices of Swiss cheese all stacked up, the holes in one slice blocked by the slice below it. All the slices move around and every now and again, a hole opens up that goes all the way through the stack. Zap!
The fraudster who tricked me out of my credit card number had Swiss cheese security on his side. Yes, he spoofed my bank's caller ID, but that wouldn't have been enough to fool me if I hadn't been on vacation, having just used a pair of dodgy ATMs, in a hurry and distracted. If the 737 Max disaster hadn't happened that day and I'd had more time at the gate, I'd have called my bank back. If my bank didn't use a slightly crappy outsource/out-of-hours fraud center that I'd already had sub-par experiences with. If, if, if.
The next Friday night, at 5:30PM, the fraudster called me back, pretending to be the bank's after-hours center. He told me my card had been compromised again. But: I hadn't removed my card from my wallet since I'd had it replaced. Also, it was half an hour after the bank closed for the long weekend, a very fraud-friendly time. And when I told him I'd call him back and asked for the after-hours fraud number, he got very threatening and warned me that because I'd now been notified about the fraud that any losses the bank suffered after I hung up the phone without completing the fraud protocol would be billed to me. I hung up on him. He called me back immediately. I hung up on him again and put my phone into do-not-disturb.
The following Tuesday, I called my bank and spoke to their head of risk-management. I went through everything I'd figured out about the fraudsters, and she told me that credit unions across America were being hit by this scam, by fraudsters who somehow knew CU customers' phone numbers and names, and which CU they banked at. This was key: my phone number is a reasonably well-kept secret. You can get it by spending money with Equifax or another nonconsensual doxing giant, but you can't just google it or get it at any of the free services. The fact that the fraudsters knew where I banked, knew my name, and had my phone number had really caused me to let down my guard.
The risk management person and I talked about how the credit union could mitigate this attack: for example, by better-training the after-hours card-loss staff to be on the alert for calls from people who had been contacted about supposed card fraud. We also went through the confusing phone-menu that had funneled me to the wrong department when I called in, and worked through alternate wording for the menu system that would be clearer (this is the best part about banking with a small CU – you can talk directly to the responsible person and have a productive discussion!). I even convinced her to buy a ticket to next summer's Defcon to attend the social engineering competitions.
There's a leak somewhere in the CU systems' supply chain. Maybe it's Zelle, or the small number of corresponding banks that CUs rely on for SWIFT transaction forwarding. Maybe it's even those after-hours fraud/card-loss centers. But all across the USA, CU customers are getting calls with spoofed caller IDs from fraudsters who know their registered phone numbers and where they bank.
I've been mulling this over for most of a month now, and one thing has really been eating at me: the way that AI is going to make this kind of problem much worse.
Not because AI is going to commit fraud, though.
One of the truest things I know about AI is: "we're nowhere near a place where bots can steal your job, we're certainly at the point where your boss can be suckered into firing you and replacing you with a bot that fails at doing your job":
https://pluralistic.net/2024/01/15/passive-income-brainworms/#four-hour-work-week
I trusted this fraudster specifically because I knew that the outsource, out-of-hours contractors my bank uses have crummy headsets, don't know how to pronounce my bank's name, and have long-ass, tedious, and pointless standardized questionnaires they run through when taking fraud reports. All of this created cover for the fraudster, whose plausibility was enhanced by the rough edges in his pitch - they didn't raise red flags.
As this kind of fraud reporting and fraud contacting is increasingly outsourced to AI, bank customers will be conditioned to dealing with semi-automated systems that make stupid mistakes, force you to repeat yourself, ask you questions they should already know the answers to, and so on. In other words, AI will groom bank customers to be phishing victims.
This is a mistake the finance sector keeps making. 15 years ago, Ben Laurie excoriated the UK banks for their "Verified By Visa" system, which validated credit card transactions by taking users to a third party site and requiring them to re-enter parts of their password there:
https://web.archive.org/web/20090331094020/http://www.links.org/?p=591
This is exactly how a phishing attack works. As Laurie pointed out, this was the banks training their customers to be phished.
I came close to getting phished again today, as it happens. I got back from Berlin on Friday and my suitcase was damaged in transit. I've been dealing with the airline, which means I've really been dealing with their third-party, outsource luggage-damage service. They have a terrible website, their emails are incoherent, and they officiously demand the same information over and over again.
This morning, I got a scam email asking me for more information to complete my damaged luggage claim. It was a terrible email, from a noreply@ email address, and it was vague, officious, and dishearteningly bureaucratic. For just a moment, my finger hovered over the phishing link, and then I looked a little closer.
On any other day, it wouldn't have had a chance. Today – right after I had my luggage wrecked, while I'm still jetlagged, and after days of dealing with my airline's terrible outsource partner – it almost worked.
So much fraud is a Swiss-cheese attack, and while companies can't close all the holes, they can stop creating new ones.
Meanwhile, I'll continue to post about it whenever I get scammed. I find the inner workings of scams to be fascinating, and it's also important to remind people that everyone is vulnerable sometimes, and scammers are willing to try endless variations until an attack lands at just the right place, at just the right time, in just the right way. If you think you can't get scammed, that makes you especially vulnerable:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
10K notes
·
View notes
Text

Cuck Edwards is more like it.
#republicans lie about everything#republican assholes#maga morons#fraud#liar#Trump caravans#Trump camps#resist#republican hypocrisy#republican family values#traitor trump#trump#crooked donald#Chuck Edwards
607 notes
·
View notes
Text
the realest thing kaz brekker ever did was take a break from breaking into a house for the purpose of tampering with his homie’s dad’s financials to bend down and give the guard dogs a good ole pet for their troubles.
#six of crows#kaz brekker#six of crows duology#leigh bardugo#crooked kindgom#kaz the dog person#kazzle dazzle#breaking and entering#fraud#soc#soc fandom#six of crows fandom#text
762 notes
·
View notes
Text

I think this might be fake. Kittens were not eligible for fishing licenses until the late 90s. Source.
1K notes
·
View notes
Text

#republican family values#sex scandal#Republican sex scandal#extra marital affairs#republican hypocrisy#republican values#one night stand#affair#Nikki Haley#Nimaratta Nikki Randhawa Haley#Republican sex obsession#fine for me not for thee#Republican fake Christian#preaching morality while being “immoral”#fraud
465 notes
·
View notes
Text

"The House voted on Friday to expel Republican Rep. George Santos of New York after a critical ethics report on his conduct that accused him of converting campaign donations for his own use. He was just the sixth member in the chamber’s history to be ousted by colleagues."
source 1
source 2
source 3
#destiel meme#destiel meme news#united states#us news#news#us politics#us congress#george santos#new york#bipartisan#way to go#mr electric kill him#now can the senate do tommy tuberville#congressman#fraud#three of the other expelled congressmen were actual confederate soldiers and the others were convicted criminals#so this is a big deal#how many major historical events do i have to live through l
539 notes
·
View notes
Text

#trump tower#trump is broke#never trump#republican assholes#traitor trump#trumps fines#trumps bail bonds#crooked donald#e jean carroll#new york#fraud
185 notes
·
View notes
Text

507 notes
·
View notes
Text

#abstract#frases#pink#long hair#photoshop#saúde mental#puss in boots#frasi tumblr#fraud#short hair#spotify#poem#portrait#poemas#my post#poecitas#ai#amor#frase e pensamentos#escritos de amor#amore tumblr#fanfic#gaming#history
344 notes
·
View notes
Text
Canonical enshittification
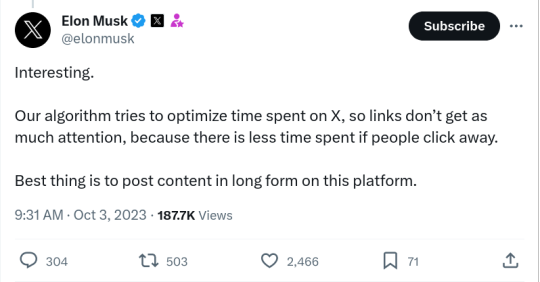
This is the Facebook playbook: you lure in publishers by promising them a traffic funnel ("post excerpts and links and we'll show them to people, including people who never asked to see them"), and then the rug-pull: "Post everything here, don't link to your own site. Become a commodity supplier to our platform. Abandon all your own ways of making money. Become entirely subject to the whims of our recommendation system."
Next will be: "We block links to other sites because they might be malicious."
Then some kind of "pivot to video."
Probably not video (though who knows?) but some other feature that a major rival has, which Twitter will attempt to defraud its captive, commodified suppliers into financing an entry into.
In case you were wondering, yes, this is canonical enshittification. Lure in business customers (publishers) by offering surpluses (algorithmic recommendation and an ensuing traffic funnel). Lock them in (by capturing their audience and blocking interop and logged-out reading).
Then rug the publishers, clawing back all the surpluses you gave them and more, draining them of all available capital and any margins they have, until they die or bite the bullet and leave.
I would also give good odds on this leading to a revivification of the "Pay us tens of thousands of dollars a month for a platinum checkmark and we'll actually show what you post to the people who asked to see it."
That will be pitched as the answer to publishers' complaints about not wanting to turn themselves into commodity Twitter inputs. It will be priced at the same (or more) as the revenues publishers expect to lose from being commodified, making it a wash.
All of this seems to me to be an "unfair and deceptive business practice" under Sec 5 of the FTC Act.
If I sign up to follow you because I want to see what you post, and Twitter shadowbans your posts unless they are formatted to maximize your dependence on Twitter, they have deceived me, and are being unfair to you.
This is *very* analogous to the Net Neutrality debate, where a platform blocks or deprioritizes the things its users ask to see, based on whether the suppliers of those things are its competitors.
I've written about how an end-to-end principle for social media could be enforced under Sec 5 of the FTCA, how it would address this kind of sleazy practice, how it would be easy to administer, and wouldn't form a barrier to entry for new market entrants:
https://pluralistic.net/2022/12/10/e2e/#the-censors-pen
7K notes
·
View notes
Text
Legal experts are stunned by many of the revelations in Friday’s 92-page New York civil fraud trial ruling fining Donald Trump and his executives $364 million, and barring him from running a business in New York for three years.
Some are pointing to portions of the actual ruling, while others are expressing shock at the magnitude of the judgment and its implications for not only the former president and his real estate empire but for the future of the nation.
“But he’s qualified to be President of the United States?” asked former Bush chief White House ethics lawyer Richard Painter, now a professor of law. Painter was responding to a news report on Friday’s ruling.
Professor of law Andrew Weissmann, a former top DOJ official for decades, made a similar observation: “NY Judge rules Trump cannot participate in business in NY for 3 years, yet Trump says he should be trusted to run the country for 4 years.”
RELATED: ‘Borders on Pathological’: Judge Decimates Trump in Fraud Ruling
238 notes
·
View notes
Photo

A romance scammer conned my mom. I went to Nigeria to find him.
“The Romance Scammer on My Sofa,” issue no. 140 from The Atavist Magazine, is now available:
In Nigeria, Yahoo boys are online fraudsters. Their nickname comes from the email service Yahoo, which became popular in Nigeria in the 2000s, and they are descendants of the infamous 419 scammers, who, first with letters, and later in emails, promised to help strangers get rich for a nominal advance fee. (The number is a reference to a section of the Nigerian criminal code pertaining to fraud.) Biggy is a particular kind of Yahoo boy: a romance scammer who pretends to be other people online to seduce foreigners into trusting him and giving him money.
Biggy’s game is all about intimacy. He invests time in building what seems like a real relationship with his victims. He flatters them, tells them jokes, asks intimate questions. “The most important thing about being a Yahoo boy is keeping the conversation alive,” Biggy told me. “Dating is all about patience. It takes a long time before a client starts trusting you.”
Yahoo boys, I was learning, love euphemisms.
Biggy estimated that over his ten years—and counting—as a romance scammer, he’d lined his pockets with $30,000 from people he conned. People yearning for love. People like my mother.
775 notes
·
View notes
Text
Wow! 👏👏👏 JDEadonWriter on X, put this amazing post out today. Check this out!
Are Meghan Markle's kids FAKE? 🤔
Megnant
1 Size: Bump drastically altering in size, even in a single day 😯
2 Slip: Bump slipped down to her knees in Birkenhead, UK 😯
3 Wobble: Bump wobbled side-to-side as she crossed the street. 😯
4 Clutching: Supporting her bump with her hands overly often. 🤔
5 Popping: audibly popped in a video, and wafted her clothes😯
6 Shape: Bump unnaturally shaped on Netflix🤔
7 Straps: Moonbump straps outlines visible under clothing in several photos. And something snapped, impacting the clothing fabric (video of H&M in London)😯
8 Biology: An absence of swelling of ankles, and other subtle biological (non)signs.🤔
9 Holding: Carrying a (doll?) infant on her bump, instead of on her hip.🤔
10 Squats: Squatting, effortlessly, with her knees together in videos and photos. In heels.😯
Births
11 Announcements: Royal official birth announcements are indirect. One states they are delighted "by the news of the" (not by the actual) birth.🤔
12 Coverup? A medic who certified a birth closed down her practice shortly afterwards.😯
13 Certificates: Questions linger over the birth certificates signatures, etc.🤔
14 Leak: An official Royal twitter account tweet indicated that Meghan’s kids are fake, before being taken down. An innocent prank?😁
15 Recovery: Epidural (ouch!) birth in a bath description anomalies and arriving home too soon afterwards to be quite plausible.🤔
16 Born Of Body?: Meghan allegedly told a friend she was infertile, when at college, and there was a reported alleged hysterectomy before the births.
17 Silence: Meghan is silent on her claimed births, despite always flashing her bump; having a "Capacity for over sharing"; boasting about being a “Mom”, and always talking about herself (apparently) on her feminist podcast. 🤔
Rented Infants
18 Archie Model: The real parents of the infant predominantly shown in Archie photos are identified. 💥
19 Lilibet Model: Parents of the infant shown in Lilibet photos are identified.💥
20 Loan: Mother of “Lilibet” commented on Insta that she does not "loan" her daughter to Meghan any longer.😯
21 Shape-Shifting: Different infants used in photos of both Archie and Lilibet.😯
22 Photoshopping: A litany of incompetently-photoshopped “family” photos. (A huge topic in itself).🤔
Dolls
23 Reborn Doll: Seemingly cradling a doll (a product called Darren) in official photo of Archie 🪆
24 Party Doll: Meghan seemingly cradled a similar doll when gate-crashing a polo match party, begetting astonished looks.😯
25 Bumpy Ride: Meghan seemed to be lugging an inanimate doll on top of her bump through some woods in Canada. Whilst grinning at a hired pap.🪆
26 Twisted: In one photograph, Archie's head is twisted more than 90 degrees 🪆
27 Carrying: A high % of photographs show them carrying the “kids” 🪆
28 Backs-Turned: A high % of Photos are of kids facing away from the camera 🤔
Other Oddities
29 Website: A startling absence of updates of Royal website on Meghan’s offspring.🤔
30 Bishop: Los Angeles christening cleric was not the official Bishop the Harkles claimed he was.🤔
31 Implausible Platitudes: Claiming Archie’s first word was “Crocodile”, and that he demands a Leica camera for his birthday. As tots do...🤔
32 Merch: An uncharacteristic unwillingness to merchandise their kids, for $$$ or PR.🤔
33 Invisible: The Harkles are never seen with their kids. There are hints of "home schooling" (will they ever be allowed out?)😯
34 Family Holidays: Weirdly, the Harkles never take their kids on holiday, and, if they pretend they did, they incompetently photoshop them into pap snaps on Insta.🤔
35 Everything Else: All the stuff I overlooked in this hastily speed-typed list.🤔
🤔🤔🤔
Why does it matter? 🤔
Because rich Prince Harry wants we skint, long-suffering tax payers, to pay for his security expenses; he’s a traitor, and, well, it’s fraud, isn’t it? 💥
Feel free to leave evidence I missed out in the comments. 👍
#MeghanMarkleIsAGrifter
#MeghanMarkleExposed
#WhereAreTheKids
#sussexbabyscam
#fraud#move along meghan#meghan markle lies#meghan and harry#megxit#youtube#lilibet#spare me#fucking grifters#grifters gonna grift#worldwide privacy tour
151 notes
·
View notes
Text
"It's a complete joke. Fraud is now on the government balance sheets. They're cooking the books." 🤔
#pay attention#educate yourselves#educate yourself#knowledge is power#reeducate yourself#reeducate yourselves#think about it#think for yourselves#think for yourself#do your homework#do some research#do your own research#ask yourself questions#question everything#everything is collapsing#government corruption#cooking the books#fraud
143 notes
·
View notes
Text

"Judge Arthur Engoron, ruling in a civil lawsuit brought by New York Attorney General Letitia James, found that the former president and his company deceived banks, insurers and others by massively overvaluing his assets and exaggerating his net worth on paperwork used in making deals and securing financing."
source 1
source 2
source 3
#destiel meme#destiel meme news#united states#us news#news#HE'S GUILTY YOUR HONOR#donald trump#trump#fuck trump#trump arrest#trump fraud#fraud#tax fraud#ahahaha#eat it trump
447 notes
·
View notes
