#SSL Installation steps
Text
How to Play Hakuoki SSL on PC
I didn’t find a straightforward guide how to play Hakuouki SSL (modern day AU game with the shinsengumi) so, here is what I did:
I: Things to download:-
1. Download the emulator. I used Vita3k.
2. Download the english translation patch.
3. Download the game. In case the webiste is not working, here is the dropbox link for a copy of the pkg file.
II. Installation:-
1. Emulator:
The emulator should be easy to set up.
Simply follow the onscreen instructions. Make sure to download and install the files it asks you to.
2. Game
1. Click File > Install .pkg on the emulator.
2. Select the game file from step I.3. Let it complete its installation as per usual.
3. It will ask for a zRIF code which is this:
KO5ifR1dQ+d7BQDtN4TaYmRpDrLf083D0TvUP9TbMzjYB2QGHnBtR+hBCb/2qy136y9KbI85PRrjgxsAAGWlFesA
paste this in the box.
Game should be ready after this step!
3. Translation Patch
1. Extract the zip file of english patch.
2. In the folder, go to ‘HakuoGakuen.Otogelib.Hakuoki_SSL_English_Patch_v1.1\PCSG00297\data‘ and copy its contents. There should be two files- ‘GAME.cpk’ and ‘SYSTEM.cpk’
3. Now go to the game data folder location. you can do so by right clicking on the game in the homescreen on the emulator.
For me, it was here ‘C:\Users\AMY\AppData\Roaming\Vita3K\Vita3K\ux0\app\PCSG00297\data‘
4. Paste the two patch files into the data folder. Click ‘replace the files’.
Done! You should be able to play the game in english now.
Note 1: quicksaving was not working for me for some reason, so make sure to make regular manual saves!
Note 2: There are a series of mini games at the end of every route and since they use a randomiser, they are not translated. It is recommended to play Okita's route first for this reason as his games are the easiest (apparently). I have never played it past the mini games on my Saito route and my sister didn't either past the Harada route. It's not undoable ofc, we just don't have the patience for it xD
Once you finish one ending, you can skip the last mini games in other routes.
Note 3: The keyboard controls I could discern so far were:
c- enter
x- back
v- menu
arrow keys to move around the menu
q- quick save
p- emulator menu screen
#hakuoki#kazama#hakuouki#hakuoki edo blossoms#hakuoki kyoto winds#hijikata#iba#saito#okita#nagakura#todou#sanan#hakuoki SSL#hakuouki SSL#psvita#otome#game guide#harada#hakuoki SSL how to play#guide#psvita port#otome game guide#anime#is this illegal lmao
133 notes
·
View notes
Text
Get Reliable and Affordable WordPress Hosting with our Free Web Hosting Service
Are you searching for a reliable and affordable WordPress hosting provider for your business? Tired of the charges imposed by other companies? Look no further! Our free web hosting service is exactly what you need.
Create Your Own Professional Website in Minutes
With our web hosting provider, you can create your own professional website in minutes. We offer a hosting service similar to Bluehost but at a much more affordable and reliable price for your business. Start your online presence today and take advantage of the following benefits:
1. 6GB Webspace: Enjoy ample storage space for your website files, images, and data.
2. 30GB Bandwidth: Experience smooth and uninterrupted website performance with generous bandwidth allocation.
3. 10 Subdomains: Expand your website's functionalities with up to 10 subdomains.
4. 2 Addon Domains: Easily manage multiple domains under one hosting account.
5. Free .http://com.ng (http://com.ng) Domain: Stand out with a free domain name that reflects your business's Nigerian presence.
6. Free SSL Certificate: Secure your website with an SSL certificate, ensuring data encryption and visitor trust.
7. Unlimited Emails: Create professional email addresses for your business and communicate effectively with your clients.
8. Unlimited Databases: Store and manage your website's data efficiently with unlimited databases.
9. Free 1-Year Domain Name: Get a free 1-year domain name for your business, such as .http://com.ng (http://com.ng), and establish your online identity without any additional cost.
Get Started Now, No Skills Needed!
Our web hosting service is designed to be user-friendly, even for those without technical expertise. The easy-to-use interface allows you to set up your website quickly and effortlessly. Whether you're a small business owner, blogger, or aspiring entrepreneur, our free web hosting service is the perfect solution to kickstart your online journey.
Frequently Asked Questions (FAQs):
Q: Is the web hosting service really free?
A: Yes, our web hosting service is absolutely free. We believe in providing affordable solutions to help businesses thrive online.
Q: Can I use WordPress with your hosting service?
A: Yes, our hosting service is fully compatible with WordPress. You can easily install WordPress and start building your website.
Q: What if I need assistance or support?
A: We offer free 24/7 support to help you with any technical issues or questions you may have. Our team is dedicated to ensuring your website runs smoothly.
Q: Can I upgrade my hosting plan in the future?
A: Yes, if your business needs grow and you require more resources, you can easily upgrade your hosting plan to accommodate your evolving needs.
Closing Segment:
Don't let high hosting costs hold you back from establishing your online presence. Choose our free web hosting service and enjoy the reliability and affordability you deserve. Create your professional website in minutes, get a free domain name, SSL certificate, and unlimited resources. Start your business website today and take the first step towards online success. Buy now
https://wordpresshosting.free.nf
With 2k in naira currency (1.30$)
2 notes
·
View notes
Text
Unveiling Appz Review: Create Unlimited Apps
Appz Review: In this segment, you can present the Appz Reviews and make sense of why you are auditing it. You can likewise give some foundation data on the application business, like its size, development, and potential. You can likewise specify that the Appz Reviews is a cloud-based application that changes any watchword, URL, site, online business store, blog, or page into an iOS and Android PWA application in 60 seconds. You can end the presentation with a postulation explanation that sums up your central matters and assessment on the stage.
APPZ Review: Features
No-Code AI Mobile App Creator
Push Notifications
SMS Sender
Built-In Marketplace
Drag-N-Drop Templates
In-Depth Analytics
Interactive Elements
Instant Monetization
AR Integration
Payment Gateway Integration
AI App Contents Generator
eCom Integration
Access 4.9 Million Stock Library
QR Generator
SSL Encryption
Commercial License
30 Days Money Back Guarantee
Appz Works For:
Affiliate Marketers
CPA Marketers
Blog Owners
Product Creators
eCom Store Owners
Local Business Owners
Agency Owners
How Start Generating Profitable Mobile Apps?
Step 1: Login - Login to Appz Cloud-Based App (Nothing to Install)
Step 2: Select Templates - Select From Our Dozens of Templates or Start from Scratch.
Enter a “Keyword, Website, eCom Store, Blog or Even a Page”… And Appz Will Turn It Into iOS & Android PWA App.
Step 3: Publish - Publish Your New iOS/Android PWA Mobile Apps (No App Store Approval Needed).
You Can Also Start Your Mobile App Agency & Sell To Tons of Businesses On Our Built-In Marketplace
Step 4: Profits - Yup, that is it. On Average, Each App We Make Generates Money Like This
GET INSTANT ACCESS
3 notes
·
View notes
Text
How To Set Up Socks5 Proxy List in Wingate.me?
What Is Private Proxy Wingate.me?

Wingate.me is a private proxy service that delivers secure managed internet access across your entire network and all your online activities. It caters to a range of requirements, from small networks to large enterprises. Known for its high-quality private proxies, particularly in the Russian region, Wingate.me has carved a niche for itself as a powerful online platform.
Supporting for Internet hosting ensures that the WinGate Proxy Server is compatible with all browsers, SSL, FTP, streaming audio and video, DirectPlay Internet gaming, etc. Socks5 proxy list wingate.me provides clients with a safe, anonymous, and unrestricted internet browsing experience. They shield users from data collection and facilitate access to otherwise blocked websites.
Types of Private Proxy Wingate.me
It offers a variety of private proxy types, including:
1. SOCKS4 proxy
A versatile proxy for web browsing, file sharing and online gaming, known for its speed and efficiency.
2. SOCKS5 proxy
These proxies support TCP and UDP traffic, making them ideal for online streaming, torrenting, and high-performance tasks.
3. IPv4 proxy
Stable and reliable proxy based on IPv4 protocol, compatible with most websites and services on the Internet.
4. Mix of SOCKS5 and IPv4 proxies
This option combines the advantages of both proxy types, providing flexibility for different tasks.
An Overview Of Wingate.me’s Socks5 Proxy List
Socks5 proxy list wingate.me provides an extensive list of Socks5 proxy servers, ensuring users have access to a broad range of functional and efficient proxies. The list, updated regularly, includes information such as the IP address, port number, country, and the last time the proxy was checked for functionality. This transparency empowers users to make informed decisions when selecting a proxy server.
Get 1GB Proxy Free Trial of Residential Proxies Now!
How To Set Up Wingate.me’s Socks5 Proxy?
Setting up a Socks5 proxy from Wingate.me is straightforward. After selecting a proxy from the list, users can configure their web browsers or applications to use the proxy by entering the provided IP address and port number in the relevant settings. Specific setup instructions may vary depending on the application or browser used. Here are detailed instructions:
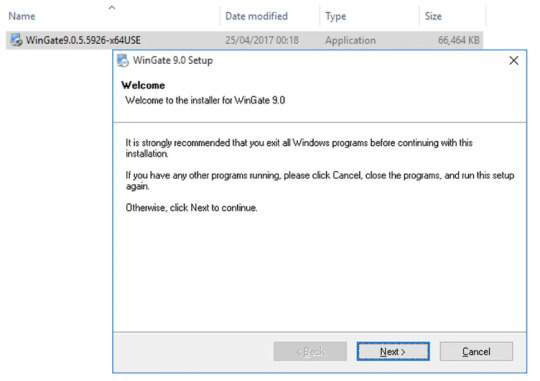
Step 1 Installing Wingate Proxy Server
After downloading the latest package of WinGate Proxy Server, double-click its ‘.exe’ package to start the installation setup wizard of WinGate proxy server. After that, you will be greeted by its welcome page to get started with the installation on your devices. Click on the “Next” button to continue.
Get 1GB Proxy Free Trial of Residential Proxies Now!
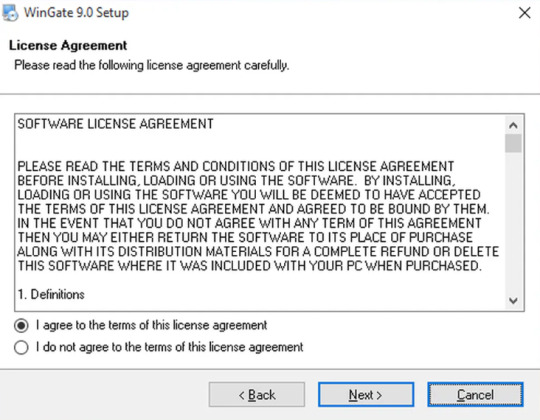
Step 2 License Agreement
You need to read and accept the license agreement before the installation and use of Wingate by choosing the right option as shown.
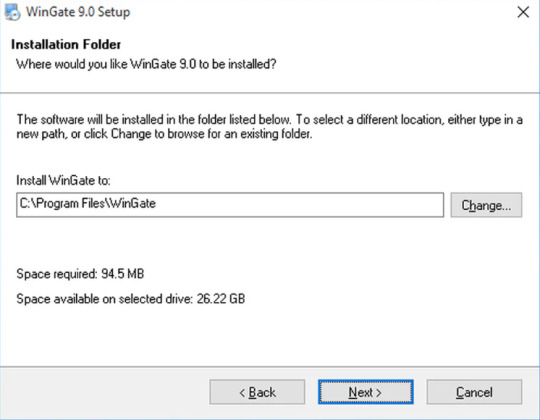
Step 3 Installation Folder
Choose the location on your system, where you like to place the WinGate installation setup.
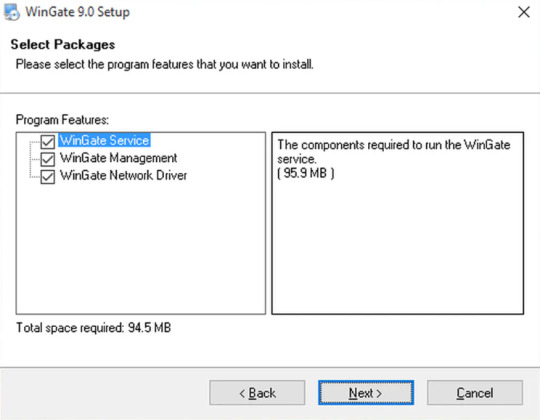
Step 4 Select Packages
You will be asked to choose the program features that you wish to install on your system.
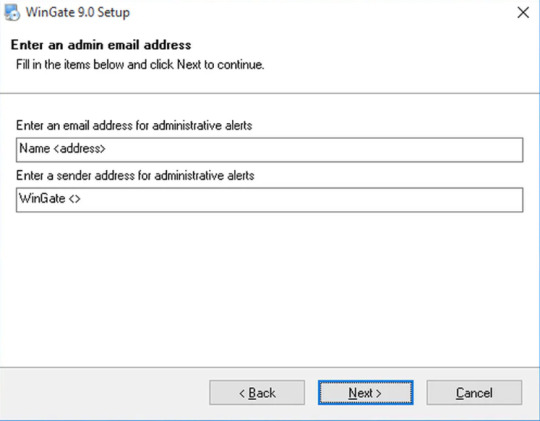
Step 5 Admin Email Address
You should provide your Administrative User Name and Email ID along with the Senders’ address for the administrative alerts.
Step 6 Ready to Install
If you click on the ‘Next’ button, your installation process will start processing files and other selecting configurations. After finishing the installation process of WinGate, click on the ‘Finish’ to exit the installer. Remember to click on the ‘Yes’ to go for system reboot and wait till it is back.

Step 7 Setting Up
After you finish the installation, you can set up Wingate.me’s Socks5 Proxy List now.
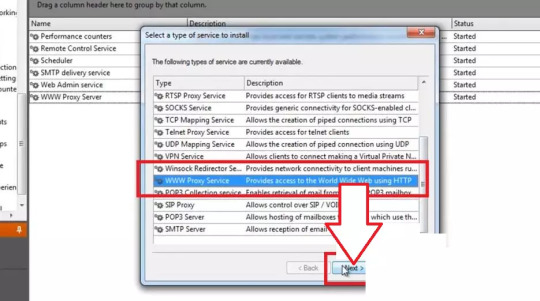
1. You will see a welcome page and a navigation menu on the left with available configuration options. Please focus on setting up the proxy. To do this, select “Services” from the navigation menu, then right-click on the empty space on the right and select Install Service.
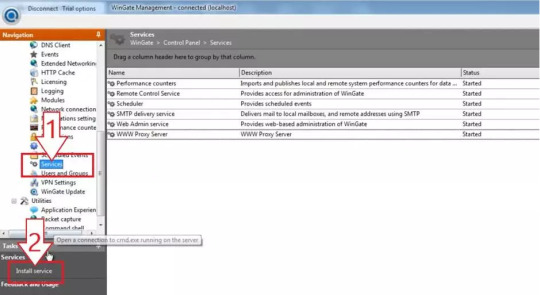
2. The service properties window will appear. Navigate to the Bindings tab. Remove all active bindings and click Add. Select “Any External Adapter” and click “OK” to save your configuration.
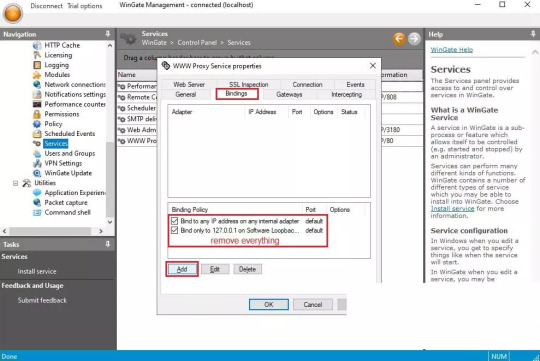
3. Now, go to the Connection tab. Check the box next to “Connect through upstream proxy.” Go to the IP Settings dashboard to configure your proxy. Note down the HTTP proxy host, proxy port, proxy username and proxy password of the private proxy you obtained from the website and import this data into WinGate.

By following these steps, you will successfully configure a private proxy using Wingate’s user-friendly interface. This ensures safe, anonymous and efficient internet browsing while protecting your online activity and data.
Get 1GB Proxy Free Trial of Residential Proxies Now!
Conclusion
Wingate.me’s Socks5 proxy list is a powerful tool for anyone seeking to navigate the digital world with anonymity, versatility, and global access. However, like any tool, it should be used responsibly and ethically. As we continue to sail through the data-driven era, tools like Wingate.me’s Socks5 proxy list will undoubtedly play a crucial role in shaping our digital experiences.
For more please read the original article which is from:
#socks5 proxy list wingate.me
#private proxy wingate.me
#buy wingate me private proxy
#proxy for email wingate.me
3 notes
·
View notes
Text
Get Your Web Hosting on Cloud Nine with BigCloudy's Year-End Deals!

In today's ever-changing digital world, establishing a strong online presence is crucial for achieving success. Whether you are an experienced entrepreneur, an aspiring blogger, or someone who wants to share their passion with the world, BigCloudy is here to support you as your dependable and affordable web hosting partner.
BigCloudy has earned a solid reputation for delivering exceptional web hosting services at affordable prices. Our unwavering dedication to providing top-notch quality and ensuring customer satisfaction has gained us the trust of a diverse range of clients, including individual bloggers and well-established businesses.
We offer a comprehensive range of web hosting solutions that are tailored to meet your specific requirements and budget. Whether you need a simple platform for your personal website or a robust environment for your high-traffic e-commerce store, BigCloudy has the ideal solution for you.
BigCloudy's Year-End WordPress Hosting Deals!
Attention all aspiring bloggers! Celebrate with joy as BigCloudy's End-of-Year Sale presents an exceptional chance to kickstart your dream blog while enjoying remarkable discounts. Experience savings of up to 99% on your initial month of WordPress hosting, starting at an unbelievably low price of only $0.01!
1. Begin Small, Aspire Big
With our affordable introductory price, you can dip your toes into the world of blogging without straining your budget. Focus on crafting exceptional content while we handle the technical aspects seamlessly.
2. Effortless Integration with WordPress
Bid farewell to complex setups. BigCloudy offers a hassle-free one-click WordPress installation and automatic updates, allowing you to concentrate on what truly matters: writing and sharing your captivating stories.
3. Impeccable Security
We prioritize the safety of both you and your visitors. Enjoy peace of mind with free SSL certificates that encrypt your website, ensuring secure communication and fostering trust with your audience.
4. A Platform for Expanding Horizons
Whether you're a novice or already boast a devoted following, BigCloudy's WordPress hosting is tailored to grow alongside your blog. Our flexible plans and reliable resources are ready to accommodate your evolving needs.
5. Beyond Hosting
BigCloudy goes above and beyond by providing a comprehensive array of tools and resources to empower your success as a blogger. From informative tutorials and guides to round-the-clock support, we're here to support you at every step of your journey.
Here's what sets BigCloudy's WordPress hosting apart:
1 WordPress Site
Build a customized online presence with 1 WordPress Site, allowing you to showcase your content and engage your audience without any limitations.
Unlimited NVMe Storage
Bid farewell to storage limitations with Unlimited NVMe Storage, enabling you to store all your essential files, images, and data with complete peace of mind.
1 Email Address
Cultivate a professional image with 1 Email Address that is directly linked to your website domain.
1 MySQL Database
Efficiently and securely manage your website's information with 1 MySQL Database, ensuring smooth operations.
FREE SSL Certificate
Enhance website security and build trust with visitors by receiving a FREE SSL Certificate.
FREE WordPress Migrations
Seamlessly transfer your existing WordPress website to BigCloudy with our FREE WordPress Migrations service.
One-Click Staging
Test new features and updates safely and easily with our convenient One-Click Staging environment.
Daily Backups / Jetbackup
Protect your valuable data with automated Daily Backups / Jetbackup, allowing for instant restoration in case of any unexpected events.
99.9% Uptime Guarantee
Enjoy exceptional reliability and minimal downtime with our 99.9% Uptime Guarantee, ensuring your website is always accessible to your visitors.
30 Days Money-Back Guarantee
Experience the BigCloudy difference risk-free with our 30 Days Money-Back Guarantee.

BigCloudy's Secure and Optimized cPanel Hosting
Are you a developer, designer, or someone who desires complete control over your online presence? Look no further than BigCloudy's robust cPanel hosting solutions! We provide you with the ability to create the website you envision, without any limitations.
Embark on your journey at a fraction of the usual cost! With prices starting at just $0.01 for the first month, BigCloudy offers professional website management that is more accessible than ever before. This limited-time offer is the perfect chance to seize control of your online space and unleash your creative potential.
Discover the exceptional benefits of BigCloudy's cPanel hosting:
1. Unmatched user-friendliness
Experience effortless navigation through cPanel, even if you have limited technical expertise. Simplify website management with just a few clicks, allowing you to focus on creating remarkable content and expanding your online presence.
2. Exceptional performance
Our servers are optimized for speed and reliability, ensuring fast-loading and flawless performance for visitors worldwide. Rest easy knowing that your website is always accessible and running smoothly.
3. Robust security
We prioritize your website's security and have implemented advanced measures to safeguard it from malware, hackers, and other online threats. Your data and your visitors' information are always protected with BigCloudy.
4. Scalability
As your online needs grow, our web hosting plans can adapt to meet your evolving requirements. Choose from a range of cPanel hosting options and seamlessly upgrade your plan as your website traffic and resource demands increase.
5. Unparalleled control
With cPanel, you have complete control over every aspect of your website. Manage files, configure settings, install applications, and much more, all through a user-friendly interface.
Here's what you'll receive with our incredible CPanel hosting offer:
1 Website
Create your unique online space and let your brand shine.
5 Subdomains
Expand your online presence with additional websites under your main domain.
50 GB Disk Storage
Store all your content, images, and data with ample space.
500 GB Bandwidth
Accommodate high traffic volumes and ensure a smooth online experience for your visitors.
1 MySQL Database
Manage your website's data efficiently with a dedicated database.
1 Email Address
Stay connected with a professional email address associated with your website.
1 Core CPU
Enjoy reliable performance and the ability to handle moderate website traffic.
1 GB RAM
Ensure smooth website functionality with ample system resources.
2,00,000 Inode Limit
Host and manage a large number of files and folders effortlessly.
Daily Backups / Jetbackup
Protect your valuable data with automated daily backups for added peace of mind.
Conclusion
BigCloudy's Year-End Deals present a unique opportunity to enhance your online visibility and propel your website to unprecedented heights. With unparalleled dependability, extraordinary functionalities, and unbelievably affordable prices that will bring tears of happiness (in terms of hosting), there is no more opportune moment to embark on your online venture or elevate your current website to new horizons.
So come aboard the BigCloudy and prepare yourself for an exceptional web hosting experience like no other! Explore our website now and seize your Year-End Deal before it slips away!
3 notes
·
View notes
Text
Enhancing Website Security with SSL Certificates: A Must for Website Design in Toronto

In today's digital age, website security is paramount. With cyber threats on the rise, ensuring the safety and integrity of your website is not an option but a necessity. For Toronto businesses investing in professional website design, the use of SSL certificates plays a crucial role in safeguarding sensitive data and instilling trust in visitors.
Understanding the Significance of SSL Certificates
SSL (Secure Sockets Layer) certificates are small data files that establish an encrypted link between a web server and a browser. This encryption ensures that data exchanged between the user's browser and the website remains secure and private. SSL certificates are indicated by the "https://" and the padlock symbol in the web address, signifying a secure connection.
Why SSL Certificates Matter for Toronto Websites
Data Security: Toronto businesses, both large and small, handle sensitive information such as customer data and payment details. SSL certificates encrypt this data, preventing unauthorized access and ensuring its confidentiality.
Boosted SEO: Search engines like Google prioritize secure websites. Implementing SSL certificates can positively impact your website's search engine ranking, thereby improving your online visibility for local audiences in Toronto.
User Trust: Toronto consumers are more likely to trust and engage with secure websites. The presence of SSL certificates assures visitors that their information is protected, encouraging them to interact with your site.
Protection Against Cyberattacks: SSL certificates act as a strong deterrent against common cyber threats, including data breaches, phishing, and man-in-the-middle attacks. Toronto businesses can fortify their defences by implementing SSL.
Legal Compliance: Certain industries in Toronto, such as healthcare and finance, have specific legal requirements for data security. SSL certificates help businesses meet these compliance standards.
Obtaining SSL Certificates for Toronto Websites
Select a Reputable Provider: When choosing an SSL certificate provider, opt for a trusted, well-established company that offers different types of certificates to suit your specific needs.
Determine the Type of SSL: There are various SSL certificates available, from single domain to wildcard certificates. Your choice will depend on the complexity and scale of your website.
Install and Configure: Once you've acquired an SSL certificate, it needs to be installed and configured on your web server. This is where the expertise of a professional web design service in Toronto comes into play.
Monitor and Renew: Regularly monitor the status of your SSL certificate to ensure it remains up to date. Certificates typically require renewal every year.
In the competitive digital landscape of Toronto, website security is non-negotiable. SSL certificates are not just about encryption; they are a symbol of trust, assuring your Toronto visitors that their data is safe and secure. Incorporating SSL into your website design is a crucial step toward establishing a credible online presence. As the trusted source for website design in Toronto, we emphasize the importance of SSL certificates to fortify your online fortifications and protect both your business and your customers. Secure your future today!
At Pat's Marketing, a leading web design and web development company in Toronto, we understand the paramount importance of website security in today's digital landscape. Our experts recognize that SSL certificates are a non-negotiable asset for every website. Whether you're seeking web design services in Toronto, our team emphasizes the implementation of SSL certificates to safeguard your digital presence. We prioritize data security, user trust, and search engine optimization to ensure that your Toronto website stands out in a competitive online world. Trust Pat's Marketing to fortify your web presence with robust security measures. Contact Pat's Marketing today at 437-826-9333 to fortify your website security with SSL certificates. Your website design in Toronto deserves the utmost protection.
If you have more queries visit https://www.patsmarketing.ca/
2 notes
·
View notes
Text
How do I use WordPress for Ecommerce?
WordPress is a versatile platform that can be effectively used for e-commerce. Here's how to make the most of it:
Choose the Right E-commerce Plugin: WordPress offers several e-commerce plugins like WooCommerce, Easy Digital Downloads, and more. Choose one that suits your needs. For most, WooCommerce is a robust and user-friendly option.
Select a Hosting Provider: Opt for a reliable hosting provider that can handle your e-commerce website's traffic and security requirements. Managed WordPress hosting can be a good choice.
Install and Configure Your E-commerce Plugin: Once you've set up WordPress, install your chosen e-commerce plugin. Follow the plugin's documentation to configure it, add products, set prices, and define shipping options.
Select a Suitable Theme: Choose a WordPress theme optimized for e-commerce. Many themes are designed to work seamlessly with e-commerce plugins, ensuring a cohesive look and feel for your online store.
Customize Your Store: Customize your website to match your brand's identity. This includes adding your logo, selecting colours, and arranging elements to create an appealing and user-friendly design.
Add Products and Content: Populate your online store with products or services. Write detailed product descriptions, set prices, and include high-quality images. Ensure that your content is engaging and SEO-friendly.
Implement Payment Gateways: Integrate payment gateways that allow customers to make secure transactions. PayPal, Stripe, and Authorize .net anywhere are popular choices.
Set Up Shipping Options: Configure shipping options based on your business model. Offer choices like standard shipping, express delivery, or local pickup.
Focus on SEO: Optimize your website for search engines. Use relevant keywords, write meta descriptions, and create high-quality content to improve your site's visibility in search results.
Ensure Mobile Responsiveness: Many shoppers use mobile devices. Ensure your site is responsive and looks great on smartphones and tablets.
Implement Security Measures: Security is crucial for e-commerce. Install security plugins, use SSL certificates, and regularly update your plugins and WordPress core for protection against threats.
Test Your Site: Before launching, thoroughly test your website. Check for broken links, ensure the checkout process works flawlessly, and test the loading speed.
Launch and Market Your Store: Once you're confident everything works as expected, launch your e-commerce store. Promote it through social media, email marketing, content marketing, and other online channels.
WordPress can be a powerful platform for e-commerce when used correctly. Following these steps and staying committed to ongoing optimization can create a successful online store with WordPress.
2 notes
·
View notes
Text

Watch How We Turn TikTok Into Our Personal ATM Using ChatGPT & Make $330/Day From Short Ai Videos!
Brand New “ChatGPT + TikTok” Software Churns Out Pro-Level Short Videos 24/7 Using Ai & Plasters Them To TikTok!
ZERO Video Creation, Editing, VoiceOvers Required!
Create short videos with 1 click in any niche for any keyword using True Ai
ZERO video creation or editing required: ChatGPT does all the work
Instantly publish to TikTok or schedule for any hour
Use our “algorithm hacking” to get in front of millions of people and get virtually unlimited free traffic
Built-in affiliate campaigns: just copy/paste your link and let ProfitTok SELL for you!
AI based video creator & editor makes it all take only SECONDS
You can simply clone, cut & publish other people’s successful campaigns
COMMERCIAL LICENSE built in: sell videos to local businesses or provide video making services
Leverage the tools TikTok gives you in their fight against Instagram & Youtube
Virtually unlimited free traffic from the world’s hottest platform
Unlimited free end-to-end SSL encryption protects you, your privacy and personal data
100% Newbie Friendly
No Monthly Fees Ever – Pay once, use forever
Double Your Money Back Guarantee
24/7 support from marketing gurus
HURRY! Price Reverts To Monthly Fee In…
Get Started With This Revolutionary New Software Today!
Click Here To Grab ProfitTok
WARNING: FREE COMMERCIAL LICENSE FOR EARLY ADOPTERS ONLY…
With ProfitTok, You Are Minutes Away From Pro-Level Videos And Millions Of Visitors!
Become The World’s Next Big TikTok Star In Just 3 Simple Steps:
Login To Our ChatGPT-Powered Short Video Creation Software!
(There is NOTHING for you to download, install or configure)
Write Any Keyword Or Paste Your Affiliate Link And Watch ProfitTok Auto-Create, Edit And Publish Your Short Video Using “True Ai” Tech!
(The AI video maker does it all for you so there’s ZERO video editing required on your end)
With 1-Click Send Your Short Video To TikTok And Get Millions Of Views Using Our Next-Gen “Algorithm Hacking”!
(Leverage the tools TikTok gives you to make them compete against FB, IG, YT, get #1 rankings and visibility and use our “algorithm hacker” to get in front of millions)
Step #3
Step #2
Step #1
ProfitTok Is SO GOOD – It Gives You UNLIMITED Opportunities…
You Can Become The Next TikTok Sensation!
You Can Even SELL These Videos For $1000+ Each Using The Built-In Commercial License!
Feeling STUCK!?
Let Us Hand You The Biggest $33 BILLION Opportunity On Earth...
You’ve probably seen a LOT of video makers…
They look “easy” and “shiny” before you buy.
But they’re ill-suited for today’s world…it takes a lot of time to figure out how they work.
You need to constantly come up with new ideas for videos.
You need to “record” content yourself (or risk a copyright claim!)
And at the end… after all this work you’d still be missing the forest for the trees!
You see – all the traffic is now going to short videos.
That’s TikTok plain and simple…they’re pulling 5 trillion views a month!
Only problem? All existing video makers are not focused on creating short videos, so you’re stuck with paying hundreds to outsource, or trying to record & edit the videos yourself…which frankly is all IMPOSSIBLE for newbies!
FACT: Short Videos Are Pulling In 5 Trillion Views A Month!
BUT No Existing Video Software Leverages ChatGPT Ai Video Creation AND TikTok…Yet!
How would you like to be able to tap into ChatGPT and “force” it to create pro-level short videos for you, auto-edit and publish them to TikTok within the next 2 minutes?
Better yet, imagine if minutes from now you could have your very own Ai video maker that enables you to finally create the traffic pulling videos you’ve always wanted…
but without any video creation required...
What if this software also came with commercial license so you can SELL videos to other people…
And It's All...
100% Done For You
100% Newbie Friendly
200% money back guarantee if it doesn’t work for you (it will!)
#tiktok#ProfitTok#how to make money online#How to make money on TikTok#domainselling#how to make money from home#how to make money on amazon#how to make money fast#how to make money with affiliate marketing
3 notes
·
View notes
Text
Fraud Prevention and Security for Ecommerce: Safeguarding Your Online Business
The rapid growth of ecommerce has revolutionized the way we shop, enabling us to browse and purchase products and services from the comfort of our homes. However, with this convenience comes the risk of fraud and security breaches that can have a devastating impact on businesses and consumers alike. To protect your online business and maintain the trust of your customers, implementing robust fraud prevention and security measures is essential.
The Importance of Fraud Prevention
Fraudulent activities in ecommerce can take various forms, such as identity theft, credit card fraud, and account takeover. The consequences can be severe, including financial loss, damage to your brand reputation, and legal liabilities. Therefore, it's crucial to prioritize fraud prevention to safeguard your business and create a secure environment for your customers.
1. Secure Payment Gateways
One of the first steps in fraud prevention is to ensure that your payment gateways are secure. Partner with reputable payment service providers that comply with industry standards and offer robust security features, such as encryption and tokenization. Implementing additional layers of authentication, such as two-factor authentication, can further enhance the security of online transactions.
2. Data Encryption
Protecting customer data is paramount in ecommerce. Utilize secure sockets layer (SSL) certificates to encrypt sensitive information transmitted between your customers' browsers and your website. This encryption makes it significantly harder for hackers to intercept and access confidential data, providing an extra layer of security.
3. Fraud Detection and Monitoring
Implement fraud detection and monitoring systems that can identify suspicious patterns and behaviors. Utilize machine learning algorithms to analyze vast amounts of data and detect anomalies that may indicate fraudulent activities. Set up alerts for unusual activities, such as multiple failed login attempts or sudden changes in purchasing patterns, to respond promptly and mitigate potential risks.
4. Strong Password Policies
Encourage your customers to create strong passwords and regularly update them. Implement password strength requirements, such as a minimum length, a mix of uppercase and lowercase letters, numbers, and special characters. Educate your customers about the importance of using unique passwords for each online account and provide tips on creating secure passwords.
5. Regular Software Updates and Patching
Keep your ecommerce platform and associated software up to date by installing the latest security patches and updates. Cybercriminals often exploit vulnerabilities in outdated software versions. Regularly monitor security advisories and subscribe to notifications from your software providers to stay informed about potential vulnerabilities and apply the necessary patches promptly.
6. PCI Compliance
If your ecommerce business handles credit card payments, it's crucial to comply with the Payment Card Industry Data Security Standard (PCI DSS). Ensure that your systems and processes adhere to the PCI DSS requirements to protect cardholder data. Conduct regular audits and vulnerability assessments to maintain compliance and minimize the risk of security breaches.
7. Educate Your Customers
Empower your customers with knowledge about online security best practices. Provide educational resources, such as blog articles or FAQs, that cover topics like recognizing phishing attempts, protecting personal information, and avoiding suspicious websites. By raising awareness, you can help your customers make informed decisions and protect themselves from fraudulent activities.
8. Ongoing Monitoring and Review
Fraud prevention is an ongoing process that requires constant monitoring and review. Regularly analyze your transaction data, review security logs, and conduct periodic risk assessments to identify potential vulnerabilities and adapt your security measures accordingly. Stay updated on the latest fraud trends and security practices to proactively respond to emerging threats.
Conclusion
As ecommerce continues to thrive, fraud prevention and security must remain top priorities for online businesses. By implementing secure payment gateways, encrypting customer data, detecting and monitoring fraud, enforcing strong passwords, staying updated with software patches, complying with PCI standards, educating customers, and maintaining ongoing vigilance, you can fortify your ecommerce business against fraudsters and build trust with your customers. Remember, protecting your business and customers from fraud is a continuous effort that requires constant adaptation to stay one step ahead of cybercriminals.
Click here to contact me on Fiverr
Source
2 notes
·
View notes
Text
How to Choose the Right Domain Name and Web Hosting for Your Business.
youtube
Are you confused about the differences between domain name and web hosting? Don't worry, we have got you covered! In this video, we will explain to you the basics of domain name & web hosting and what makes them different. Learn how to choose the best domain name and hosting service for your website and get ready to take your business to the next level!
What is a Domain Name and Web Hosting?
A domain name and web hosting are two of the most important elements of having a website. A domain name is a unique address that identifies your website, while web hosting is the service that allows your website to be visible online.
Domain services provide you with an easy way to register and manage your domain names. Web hosting services provide you with the necessary infrastructure and support to host your website on their servers. With these services, you can ensure that your website is always available and accessible to visitors around the world.
Understanding the Different Types of Domains & Hosting Companies:
The success of any website , depends on the type of domain, and hosting company you choose. Different types of domains, such as top-level domains, country code top-level domains, and generic top-level domains, can affect the search engine rankings, and visibility of your website. Similarly, the type of hosting company, you choose can also have a huge impact on your website's performance.
When it comes to hosting companies, there are two main types, shared hosting and virtual private server (VPS). Depending on the size and complexity of your website, one may be more suitable than the other. It is important to understand how each works in order to make an informed decision ,when choosing a domain registrar, or web host.
How to Choose the Right Domain Name, & Web Hosting Company for Your Business?
Choosing the right domain name, and web hosting company for your business, is an important decision. It can have a major impact ,on your website's performance, security, and scalability. It is essential to choose a reliable hosting provider, that offers the features you need at an affordable price.
When selecting a web hosting company, you should consider, the type of website hosting plans they offer, their customer support options, server uptime guarantees, and security measures. Additionally, it's important to compare different providers to ensure that, you get the best deal on cheap website hosting services. By doing so, you can ensure that your business will have access to reliable ,and secure resources for its online presence.
Finding the Best Deals on Domain, & Web Hosting Services,:
Finding the right domain ,and web hosting services can be a daunting task. With so many options available, it is hard to know which one will provide the best value for your money. Fortunately, there are ways to find the best deals on domain ,and web hosting services. You can search for cheap web host providers, compare prices between different hosting companies, and look for discounts on domains. With a little bit of research, you can make sure that you are getting the best deal ,on your domain, and hosting services.
Do-It-Yourself Guide to Setting Up a Domain ,& Web Hosting Account:
If you want to get your website up ,and running quickly, setting up a domain, and web hosting account is the first step. This guide will help you understand the process of setting up a domain ,and web hosting account, as well as how to install a WordPress site on your server. With this do-it-yourself guide, you can be sure that your website will be up and running in no time!
Getting started with a website is easier than ever before with Namecheap. Namecheap provides you with the tools and support you need to get your website up and running quickly. With Namecheap, you can register a domain name, set up hosting, purchase SSL certificates, and more in just a few clicks. Plus, their customer service team is available 24/7 to answer any questions or concerns you may have. So don't wait any longer - get started with your website by Namecheap today!
If you want to get more reviews of domain, and web hosting service providers ? Please check the video description below :
Thanks for watching !!
4 notes
·
View notes
Text
How to Use the AppValley App Store

AppValley is an app store with a difference. It provides a wide variety of free and paid apps, and it even offers tweaked versions of existing apps.The app also has a cool feature that makes it easy to navigate through categories.
AppValley has some features that Apple's App Store does not have. For instance, it offers an improved search engine, and it has the ability to display different language interfaces. Also, it uses a lot of SSL encryption, which is good for security.
Moreover, it includes a wide range of apps, including some that are only available in Apple's App Store. Some of these include games and hacks. In addition, it has a lot of educational material. And, it works on all iOS devices.
However, it has also received a bad rap, particularly when it comes to downloading malicious programs. This is a problem that many users have reported. Fortunately, the team at Appvalley has taken measures to rectify the situation. They've retracted some of their certificate revokes and have announced that they're adding more features to their app.
Among its other features is the fact that it uses a proxy method to run applications. Although the idea is great, this isn't always practical. As a result, it's better to use a reputable VPN instead. You can do this with the aid of PowerMyMac. After downloading the program, you can follow its steps to make sure that the Appvalley App Store is safe.
There are a number of other features and functions that the AppValley App Store has, and this list isn't exhaustive. For example, a VIP program allows you to download more games and apps at quicker speeds. Additionally, a new category was added to the app's library, allowing users to browse apps in a category-specific manner. Another feature is the ability to delete all your apps at once.
When you're ready to download the best of the best, you can either go to the AppValley website or launch the app directly from your browser. Alternatively, you can install the AppValley app on your Mac or PC.
Lastly, the AppValley App Store is a legal way to download apps. Because of this, it is safe to use. Of course, you have to be careful when using the app, especially if you're downloading from a third-party site. That's because the official App Store is one of the most secure, and a lot of the other apps in the App Store have been tainted.
The AppValley app is a useful tool that lets you find, download and play the most popular apps on the web. It also offers educational materials for those interested in improving their skills. But if you're having trouble, you can reach out to the Appvalley vip community. Moreover, the AppValley app is updated regularly.
2 notes
·
View notes
Text
what is softether vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is softether vpn
SoftEther VPN Overview
SoftEther VPN is a versatile and robust virtual private network (VPN) solution that offers a wide range of features and capabilities for both individual users and organizations. Developed by the University of Tsukuba in Japan, SoftEther VPN stands out for its flexibility, security, and performance.
One of the key advantages of SoftEther VPN is its ability to operate on multiple platforms, including Windows, macOS, Linux, and FreeBSD, as well as on mobile devices running Android and iOS. This cross-platform compatibility makes it an ideal choice for users with diverse operating system preferences.
SoftEther VPN supports various VPN protocols, including SSL VPN, L2TP/IPsec, OpenVPN, and Microsoft SSTP. This flexibility allows users to choose the protocol that best suits their needs, whether they prioritize security, speed, or compatibility.
In addition to its protocol support, SoftEther VPN offers advanced features such as high-speed throughput, low latency, and strong encryption. These features ensure that users can enjoy a secure and reliable VPN connection without sacrificing performance.
For organizations, SoftEther VPN provides powerful management tools for administering VPN servers and user accounts. Its scalability makes it suitable for small businesses as well as large enterprises, allowing them to easily expand their VPN infrastructure as their needs grow.
Furthermore, SoftEther VPN is open-source software, meaning that it is freely available for anyone to use and modify. This open approach fosters innovation and collaboration within the VPN community, leading to continuous improvements and enhancements.
Overall, SoftEther VPN offers a comprehensive solution for individuals and organizations seeking a secure, reliable, and customizable VPN solution. With its cross-platform support, advanced features, and open-source nature, SoftEther VPN stands as a compelling option in the crowded VPN market.
SoftEther VPN Features
SoftEther VPN is a powerful and versatile VPN solution with a wide range of features that make it stand out in the crowded VPN market. One of the key features of SoftEther VPN is its open-source nature, which allows for flexibility and customization based on user needs. This means that users can modify and tailor the VPN to suit their specific requirements, making it a popular choice for both individuals and businesses.
Another standout feature of SoftEther VPN is its multi-protocol support. Unlike many other VPNs that only support one or two protocols, SoftEther VPN supports multiple protocols including SSL-VPN, L2TP/IPsec, and OpenVPN. This versatility ensures that users can connect to the VPN using a range of different devices and operating systems, making it a convenient option for users with diverse tech setups.
Additionally, SoftEther VPN offers high performance and stability, thanks to its use of cutting-edge technologies. The VPN is capable of handling high traffic loads without compromising on speed or connectivity, making it ideal for users who require a reliable and fast VPN connection for activities such as streaming, gaming, or torrenting.
Furthermore, SoftEther VPN provides strong security features to protect user data and privacy. It uses industry-standard encryption protocols to ensure that data transmitted through the VPN remains secure and private, keeping sensitive information safe from prying eyes.
In conclusion, SoftEther VPN offers a comprehensive set of features that cater to the needs of both individual users and businesses. Its open-source nature, multi-protocol support, high performance, and robust security make it a top choice for those seeking a reliable and customizable VPN solution.
SoftEther VPN Installation
Title: A Step-by-Step Guide to SoftEther VPN Installation
SoftEther VPN, an open-source VPN software, offers a flexible and easy-to-use solution for creating secure VPN connections. Whether you're looking to enhance your privacy, bypass geo-restrictions, or secure your online activities, installing SoftEther VPN is a straightforward process. Here's a step-by-step guide to get you started:
Download SoftEther VPN: Begin by visiting the official SoftEther VPN website and navigating to the download section. Choose the appropriate installer based on your operating system, whether it's Windows, macOS, Linux, or FreeBSD.
Run the Installer: Once the installer is downloaded, run the executable file to start the installation process. Follow the on-screen instructions to proceed with the installation. You may be prompted to agree to the terms and conditions of the software.
Select Components: During the installation, you'll have the option to choose which components of SoftEther VPN you want to install. This includes the VPN Server, VPN Client, VPN Bridge, and more. Select the components according to your requirements and preferences.
Configure VPN Server: If you're setting up SoftEther VPN on a server, you'll need to configure it accordingly. Launch the SoftEther VPN Server Manager and follow the setup wizard to configure your VPN server settings, such as creating users, defining virtual hubs, and configuring security options.
Connect to VPN: Once the installation and configuration are complete, launch the SoftEther VPN Client on your device. Enter the IP address or hostname of the VPN server you want to connect to, along with any necessary authentication credentials. Click 'Connect' to establish a secure VPN connection.
Verify Connection: After connecting to the VPN server, verify that your internet traffic is routed through the VPN tunnel. You can check your IP address and conduct DNS leak tests to ensure your online privacy and security.
By following these steps, you can successfully install SoftEther VPN and enjoy a secure and private browsing experience. Whether you're a novice or an experienced user, SoftEther VPN provides a reliable solution for safeguarding your online activities.
SoftEther VPN Configuration
SoftEther VPN is a versatile and powerful tool for establishing secure connections over the internet. Configuring SoftEther VPN allows users to customize their virtual private network settings to suit their specific needs and preferences.
To configure SoftEther VPN, users typically start by downloading and installing the software on their desired platform, whether it's Windows, macOS, Linux, or a mobile device. Once installed, users can launch the SoftEther VPN Server Manager to begin the configuration process.
One of the key steps in configuring SoftEther VPN is setting up the Virtual Hub, which serves as the central point for managing connections and network traffic. Users can create multiple Virtual Hubs to organize and segregate different types of network traffic as needed.
Next, users can configure user authentication methods to control access to the VPN. SoftEther VPN supports various authentication methods, including user name and password, digital certificates, and RADIUS authentication, allowing users to choose the most suitable option for their security requirements.
After configuring authentication, users can define access control policies to restrict or allow specific users or groups access to the VPN network. This helps ensure that only authorized users can connect to the VPN and access resources within the network.
Additionally, users can configure network settings such as IP address assignment, DHCP server settings, and DNS settings to customize the VPN network according to their preferences.
Once the configuration is complete, users can connect to the SoftEther VPN server using the SoftEther VPN client software or other compatible VPN clients. With proper configuration, SoftEther VPN provides a secure and reliable way to establish encrypted connections over the internet, ensuring privacy and data protection for users and their network resources.
SoftEther VPN Security
SoftEther VPN is a popular free and open-source VPN software developed by the University of Tsukuba in Japan. It is widely known for its flexibility, high performance, and strong security features, making it a preferred choice for individuals and organizations looking to ensure secure and private internet connections.
One of the key aspects that sets SoftEther VPN apart is its advanced encryption and security protocols. It supports a variety of encryption algorithms, including AES, RSA, and ECDSA, to ensure that all data passing through the VPN is protected from prying eyes. Additionally, SoftEther VPN utilizes SSL-VPN Tunneling on TCP port 443, which helps disguise VPN traffic as regular HTTPS traffic, making it harder for firewalls to detect and block.
Moreover, SoftEther VPN offers a wide range of authentication methods, such as user/password authentication, certificate authentication, and RADIUS authentication, allowing users to choose the method that best fits their security needs. This multi-layered approach to security helps to safeguard user data and ensure that only authorized users can access the VPN network.
In terms of privacy, SoftEther VPN does not keep any logs of user activity, providing users with a high level of anonymity while browsing the internet. With its built-in NAT Traversal function, SoftEther VPN can easily bypass network restrictions and firewalls, allowing users to access geo-restricted content and websites with ease.
Overall, SoftEther VPN is a reliable and secure solution for anyone looking to enhance their online privacy and security. Its robust encryption, authentication methods, and privacy features make it a top choice for individuals and organizations seeking a trustworthy VPN service.
0 notes
Text
a vpn is a network within the organization
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
a vpn is a network within the organization
VPN Encryption Protocols
VPN encryption protocols play a crucial role in safeguarding online privacy and security. These protocols dictate how data is encrypted and transmitted between your device and the VPN server, ensuring that your sensitive information remains secure from prying eyes.
One of the most widely used VPN encryption protocols is OpenVPN. Known for its open-source nature and strong security features, OpenVPN utilizes SSL/TLS protocols to create a secure tunnel for data transmission. Its flexibility and compatibility make it a popular choice among VPN providers and users alike.
Another commonly used protocol is IPSec (Internet Protocol Security), which operates at the network layer of the OSI model. IPSec can encrypt data at the IP packet level, providing a high level of security for VPN connections. It is often used in conjunction with other encryption algorithms like AES (Advanced Encryption Standard) to enhance security further.
L2TP/IPSec (Layer 2 Tunneling Protocol with IPsec) combines the best of both worlds by incorporating the tunneling capabilities of L2TP with the encryption and authentication features of IPSec. While it may not be as fast as other protocols, L2TP/IPSec is highly secure and widely supported across different platforms.
IKEv2/IPSec (Internet Key Exchange version 2 with IPsec) is another popular choice known for its stability and speed. It seamlessly handles changes in network connectivity, making it ideal for mobile devices. With strong encryption algorithms and efficient key management, IKEv2/IPSec ensures that your data remains protected at all times.
In conclusion, VPN encryption protocols play a vital role in ensuring the confidentiality and integrity of your online communications. By understanding the strengths and weaknesses of each protocol, you can choose the one that best fits your security needs. Whether it's OpenVPN, IPSec, L2TP/IPSec, or IKEv2/IPSec, implementing a robust encryption protocol is essential for maintaining your privacy in today's digital world.
Intranet VPN Configuration
Intranet VPN Configuration: A Comprehensive Guide
Setting up an Intranet VPN configuration allows businesses to securely connect remote employees to their corporate network. VPN, short for Virtual Private Network, creates an encrypted tunnel over the internet, ensuring data privacy and security.
To begin the configuration process, the first step is to select a reliable VPN protocol. Common options include PPTP, L2TP/IPSec, and OpenVPN. Each protocol comes with its own set of advantages and considerations, so it's essential to choose the one that best suits the organization's needs.
Next, configure the VPN server on the corporate network. This involves setting up authentication methods, encryption settings, and assigning IP addresses. It's crucial to ensure that the VPN server is properly configured to guarantee a secure connection.
Once the VPN server is set up, remote employees can configure their devices to connect to the corporate network. This typically involves installing VPN client software and entering the necessary connection details provided by the IT department.
Regularly updating and monitoring the Intranet VPN configuration is crucial to maintain security. IT administrators should regularly review access logs, update encryption settings, and patch any vulnerabilities to prevent potential security breaches.
In conclusion, setting up an Intranet VPN configuration is essential for organizations looking to provide secure remote access to their corporate network. By following these steps and best practices, businesses can establish a reliable and secure VPN connection for their remote employees.
VPN Tunneling Methods
VPN tunneling methods are the backbone of secure and private internet communication. These methods ensure that data transmitted between your device and the VPN server remains encrypted and inaccessible to unauthorized parties. Here are some commonly used VPN tunneling methods:
PPTP (Point-to-Point Tunneling Protocol): One of the earliest VPN tunneling protocols, PPTP offers fast connection speeds but is considered less secure compared to newer methods due to vulnerabilities in its encryption.
L2TP/IPsec (Layer 2 Tunneling Protocol with IPsec): L2TP/IPsec combines the best of both L2TP and IPsec protocols. L2TP provides the tunneling mechanism while IPsec offers strong encryption and authentication, making it a popular choice for secure VPN connections.
OpenVPN: Known for its open-source nature and versatility, OpenVPN is highly configurable and supports various encryption algorithms. It's widely used across different platforms and is known for its robust security features.
SSTP (Secure Socket Tunneling Protocol): Developed by Microsoft, SSTP utilizes SSL/TLS encryption, making it a suitable choice for Windows users. It's designed to bypass firewalls and offers good security for VPN connections.
IKEv2 (Internet Key Exchange version 2): IKEv2 is known for its stability and fast reconnection times, making it ideal for mobile devices that frequently switch between networks. It provides strong security features and is often used in combination with IPsec.
WireGuard: A relatively new addition to the VPN tunneling scene, WireGuard is praised for its simplicity, speed, and efficiency. It's designed to be lightweight yet secure, making it a promising option for VPN providers and users alike.
Each VPN tunneling method has its strengths and weaknesses, so it's essential to choose one that aligns with your security and performance requirements. Additionally, always ensure that your VPN provider implements robust encryption and follows best practices to safeguard your online privacy.
Corporate VPN Implementation
Many businesses today are turning to Corporate VPN Implementation to ensure secure and private communication within their organizations. VPN, or Virtual Private Network, is a technology that allows employees to access the company's network remotely through an encrypted connection.
One of the key benefits of implementing a corporate VPN is enhanced security. By encrypting the data transmitted between the employees and the company's network, VPNs help prevent unauthorized access and data breaches. This is especially crucial for businesses dealing with sensitive information and confidential data.
Another advantage of using a corporate VPN is improved remote access. With more employees working from various locations, having a VPN in place allows them to securely connect to the company's network from anywhere in the world. This not only boosts productivity but also ensures that employees can access the resources they need to perform their tasks effectively.
Furthermore, corporate VPN implementation can help businesses overcome geo-restrictions and censorship. By masking the users' IP addresses and routing their internet traffic through servers in different locations, VPNs enable employees to bypass regional restrictions and access online content that may be otherwise blocked.
In conclusion, Corporate VPN Implementation is an essential tool for businesses looking to enhance their cybersecurity, facilitate remote work, and enable seamless access to resources. By investing in a reliable VPN solution, companies can ensure secure communication and data transmission, ultimately fostering a more efficient and productive work environment.
Internal Network Security
Internal network security is a critical aspect of maintaining the confidentiality, integrity, and availability of data within an organization's network. It involves implementing various measures to prevent unauthorized access, misuse, modification, or denial of network resources and data by individuals or malware within the organization.
One key component of internal network security is access control. This involves defining and enforcing policies that determine who can access what resources within the network. By implementing mechanisms such as user authentication, role-based access control, and encryption, organizations can ensure that only authorized users have access to sensitive data and systems.
Another important aspect is network monitoring and logging. By using intrusion detection systems (IDS) and security information and event management (SIEM) tools, organizations can detect and respond to suspicious activities or security incidents in real-time. Logging network activities also helps in forensic analysis and compliance with regulations.
Regular software patching and updates are essential to mitigate vulnerabilities that could be exploited by attackers to gain unauthorized access to the network. By staying up to date with security patches, organizations can prevent known security flaws from being exploited.
Employee awareness and training play a crucial role in internal network security. By educating employees about security best practices, such as avoiding phishing emails, using strong passwords, and reporting suspicious activities, organizations can reduce the risk of insider threats and human errors that could compromise network security.
In conclusion, internal network security is an ongoing process that requires a combination of technical controls, policies, and user awareness to protect an organization's valuable assets from cyber threats. By implementing a holistic approach to internal network security, organizations can establish a robust defense against potential security breaches.
0 notes
Text
what is sophos ssl vpn client
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is sophos ssl vpn client
Sophos SSL VPN Client features
Sophos SSL VPN Client is a powerful tool that provides secure remote access to your network resources. With a range of useful features, this client ensures that your data remains protected while allowing you to connect from anywhere in the world.
One of the key features of the Sophos SSL VPN Client is its user-friendly interface. The client is easy to install and configure, making it simple for even non-technical users to set up secure connections. Once installed, users can quickly connect to the VPN with just a few clicks, ensuring a seamless user experience.
Another important feature of the Sophos SSL VPN Client is its robust encryption capabilities. The client uses strong encryption protocols to secure data in transit, protecting it from potential cyber threats and ensuring the confidentiality of sensitive information.
Furthermore, the Sophos SSL VPN Client offers reliable connectivity, allowing users to access network resources without interruptions. Whether you are working from a coffee shop or traveling abroad, you can rely on the Sophos SSL VPN Client to maintain a stable connection to your organization's network.
Overall, the Sophos SSL VPN Client is a versatile solution for remote access, offering a range of features designed to enhance security and convenience. By utilizing this client, organizations can ensure that their employees have secure access to network resources from any location, all while maintaining the confidentiality of their data.
Sophos SSL VPN Client setup guide
Setting up the Sophos SSL VPN Client is a relatively straightforward process that allows users to securely connect to their company's network from remote locations. This guide will walk you through the necessary steps to configure the SSL VPN Client on your device.
To begin the setup process, you will first need to download the SSL VPN Client software from the Sophos website. Make sure to choose the correct version for your operating system, whether it is Windows, macOS, Linux, or even mobile platforms.
Once the software is downloaded, proceed with the installation by following the on-screen instructions. You may need administrative privileges on your device to complete the installation.
After the installation is complete, launch the Sophos SSL VPN Client and enter the connection details provided by your network administrator. This typically includes the server address, port number, and your login credentials.
Once you have entered the necessary information, you can save the connection profile for easy access in the future. Simply click on the "Save" button to store the configuration.
Now, you can connect to the VPN by selecting the saved profile and clicking on the "Connect" button. The SSL VPN Client will establish a secure connection to your company's network, allowing you to access resources and services as if you were physically in the office.
In conclusion, setting up the Sophos SSL VPN Client is a simple process that helps ensure secure remote access to your company network. By following the steps outlined in this guide, you can quickly and easily configure the VPN Client on your device and stay connected wherever you are.
Benefits of using Sophos SSL VPN Client
Sophos SSL VPN Client offers a secure and reliable solution for remote access to corporate networks. By utilizing the Sophos SSL VPN Client, users can benefit from enhanced data encryption, ensuring that sensitive information remains protected during transmission. This level of security helps to prevent unauthorized access and potential data breaches.
One of the key advantages of using Sophos SSL VPN Client is its ease of use. The client provides a simple and intuitive interface, making it easy for even novice users to establish a secure connection to the company network. This streamlines the remote access process and allows employees to quickly and securely access the resources they need to stay productive.
Furthermore, Sophos SSL VPN Client offers compatibility with a wide range of devices, including desktops, laptops, and mobile devices. This flexibility enables users to connect to the corporate network from virtually anywhere, whether they are working from home, on the go, or in a remote location. This convenience promotes remote work capabilities and enhances overall productivity.
In addition to its security features and user-friendly interface, Sophos SSL VPN Client also provides reliable performance. The client offers stable and high-speed connections, ensuring that users can access network resources without experiencing delays or disruptions. This reliability is essential for maintaining seamless business operations and supporting critical workflows.
Overall, the benefits of using Sophos SSL VPN Client include enhanced security, ease of use, device compatibility, and reliable performance. By leveraging this solution, businesses can empower their remote workforce, protect sensitive data, and maintain a high level of connectivity and productivity.
Sophos SSL VPN Client comparison
When it comes to choosing the right SSL VPN Client for your network, Sophos offers a reliable and feature-rich solution that caters to various business needs. To make an informed decision, let's compare the Sophos SSL VPN Client with other options in the market.
One of the key advantages of the Sophos SSL VPN Client is its user-friendly interface, making it easy for administrators to set up and manage VPN connections. The client supports multi-platform compatibility, allowing users to connect securely from different devices and operating systems.
In terms of security features, the Sophos SSL VPN Client offers robust encryption protocols to ensure data privacy and integrity during transit. It also provides advanced authentication mechanisms to prevent unauthorized access to the network.
When comparing performance, the Sophos SSL VPN Client stands out for its efficient connection speeds and stable performance even under heavy network traffic. This ensures a seamless remote access experience for employees working from various locations.
Another notable aspect of the Sophos SSL VPN Client is its scalability, making it suitable for small businesses to large enterprises. With flexible licensing options and centralized management capabilities, Sophos caters to organizations of all sizes.
In conclusion, the Sophos SSL VPN Client emerges as a top contender in the market due to its user-friendly interface, robust security features, high performance, and scalability. By choosing Sophos, businesses can establish a secure and reliable VPN connection to support their remote workforce effectively.
Troubleshooting Sophos SSL VPN Client issues
Troubleshooting Sophos SSL VPN Client Issues
Sophos SSL VPN Client offers a secure and seamless way for users to access corporate networks remotely. However, like any software, it may encounter issues that can disrupt connectivity and productivity. Here are some common problems users may face and steps to troubleshoot them:
Connection Failures: If the VPN client fails to establish a connection, first ensure that the server is operational and reachable. Check network settings, including firewalls and routers, to ensure they're not blocking VPN traffic. Verify that the client configuration matches the server settings, including IP addresses, ports, and authentication methods.
Authentication Errors: Users may encounter authentication errors if their credentials are incorrect or expired. Double-check usernames and passwords, and ensure that users have the necessary permissions to connect. If using two-factor authentication, ensure that tokens or codes are entered correctly.
Slow Performance: Slow VPN performance can result from various factors, including network congestion, server overload, or insufficient bandwidth. Troubleshoot by testing network speeds without the VPN, and consider upgrading network infrastructure if necessary. Additionally, optimize VPN settings for performance, such as enabling compression or adjusting encryption levels.
Disconnects or Drops: VPN connections may drop unexpectedly due to network instability or configuration issues. Update the VPN client software to the latest version, as vendors often release patches to address connectivity issues. Check for interference from other applications or background processes that may disrupt the VPN connection.
Error Messages: Pay attention to error messages displayed by the VPN client, as they often provide clues to the underlying issue. Search online forums or vendor documentation for solutions specific to the error message received.
By following these troubleshooting steps, users can resolve common Sophos SSL VPN Client issues and maintain secure and reliable remote access to corporate networks.
0 notes