#also is that username in reference to... the matrix?
Text
Digital Culture - Blog 4 - Reddit & 4chan
Reddit vs. 4chan
There is one thing that makes 4chan special - anonymity. Although the idea of complete anonymity on the Internet might make you imagine a kind of hellscape, there is some hope in the form of 4chan moderators who monitor the content within each board. These moderators are also anonymous themselves. There are only a maximum of 10 web pages available in each board. There are various boards to choose from - spanning from the innocent “Animals and Nature” to the not-so-innocent “Yaoi” - Be warned before Googling!
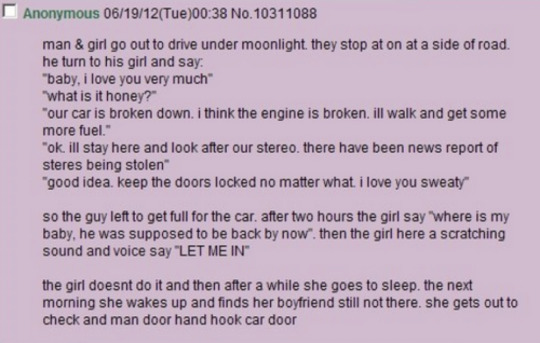
I first heard about 4chan when I was 16 from a friend at a sleepover - she showed me the “man door hand hook car door” meme and after we both laughed about it I asked her where it came from. She spoke of 4chan as if it was illegal, admittedly it did freak me out and I never used 4chan but I have enjoyed some of the memes that have come from there through other social media channels. The controversies that have been birthed from 4chan is also why I am aware of what it is - One controversy that springs to mind would be the Habbo Hotel raids.
The Habbo Hotel raids occurred on July 12th 2006 when a group in the /b/ (random) board, who called themselves “/b/lockers” joined Habbo Hotel in great numbers creating avatars of men with dark skin and an afro. The group started to form swastikas virtually and began to actually block access for other users. This raid is said to have been carried out by Anonymous as a protest again the supposed racist tendencies Habbo Hotel moderators had when banning users based on the skin colours of their avatars (Know Your Meme, 2020).
youtube
On the other hand, you have Reddit - a website that has vast “subreddits” that can be created by any user, however you do need a username to sign up so the anonymity you find with 4chan is not there. Moderators and rules exist in each subreddit, much like the boards. Similar to 4chan, there are nice subreddits like r/cats, and grim subreddits like r/Rule34 (Again, this is not for the faint-hearted). You could say there is something for everyone on Reddit, unlike 4chan. I’m fairly sure it doesn’t exist any longer, but once I did venture on a “Red Pill” subreddit. For those of you that don’t know, Red Pill is a term coined from The Matrix, basically a subreddit filled with misogynist, involuntary-celibate men. They discussed men’s rights and how to pick up and manipulate women. This kind of dangerous rhetoric is something that can be really harmful to society, and although Reddit is much more user-friendly and not anonymous, it can still encourage groups like these to grow and spew further hate.
Personally I use Reddit almost daily, mostly for pictures of cats, the Ireland and Cork subreddits and on occasion some pop culture stuff. I don’t really depend on it for my news but I feel like there is a really nice community aspect, which I don’t think is really in 4chan. The fact that there are usernames on Reddit, you can give people awards, and message people are nice aspects that connect people, unlike the cold “Anonymous” from 4chan.
-----------------------------------------
References:
C., A. (2022, October 05). Man door hand hook car door. Retrieved December 1, 2022, from https://knowyourmeme.com/memes/man-door-hand-hook-car-door
Ezvidinc. (2018, September 14). The difference between Reddit and 4chan. Retrieved December 1, 2022, from https://www.youtube.com/watch?v=MXOKItVakq0
Marche, S. (2016, April 14). Swallowing the red pill: A journey to the heart of modern misogyny. Retrieved December 1, 2022, from https://www.theguardian.com/technology/2016/apr/14/the-red-pill-reddit-modern-misogyny-manosphere-men
Pool's closed. (2017, February 11). Retrieved December 1, 2022, from https://www.youtube.com/watch?v=fp2EZbbuMa0
Pool's closed. (2022, November 06). Retrieved December 1, 2022, from https://knowyourmeme.com/memes/pools-closed
0 notes
Text
wow goooooood morning to whoever left a comment on liiiiike every chapter of my fic lol. i hope u are in a dif timezone than me (aka did not stay up all til 5am) or that u (blissfully) have no pressing engagements today and are catching some peaceful Zs
for the rest of you, i hope you also have a blissfully empty schedule ahead of you ; )
(i fucking do not)
2 notes
·
View notes
Text
Trying to explain to my dad that i agree that the pandemic has become all about money (in a way that corps just want us to keep working for them no matter how many people die bc of high profits) and not bc of the fact that they’re keeping people from taking the “miracle drug that is ivermectin”... it’s impossible.
I just had to explain that the one doctor that vouches for it was literally just some guy before the pandemic started. And he got mad saying that I’m just hating people for stating the truth that the government doesn’t want you to hear.
And i’m just.
I ended up looking at the wikipedia article of all the misinfo documented so far and I’m just stuck on how stupid people are. (specifically those ones about cocaine, veganism, and burning down 5g towers?)
Sometimes i’m glad i learned how to see if sources were valid. Why couldn’t everybody else have been taught that in school too? They need it. There’s a fine line between stupidity somebody just made up and an actual scientific peer reviewed article and it’s never labelled until you get to sources IF it has sources..
like yes. I can’t tell you the exact reason why ivermectin isn’t the cure. That’s not what i specialize in. But i can also tell you I know well enough that it’s not and well enough to listen to those who DO Specialize in it. And it’s not an opinion. From real doctors and scientists who aren’t just some guy in some town who barely knows enough to not get fired from his job. (You can get a medical degree with straight C’s ya know)
#it's an antiparisitic not antiviral#you got scabies or lice? ivermectin#you got covid? antivirals.#like why is that hard to understand#i even pulled the 'you took the polio and measles vaccines right? and didn't catch it?#and i couldn't even mention that the only reason there's boosters is bc the virus has mutated far enough to where the first one doesnt work#like. come on#i dont know whats so hard to understand about all this stuff#its becoming evident that many people never had to do research projects#also im realizing that anything that has the words 'red pill' in it is a major red flag and my dad doesn't see that either#he also doesnt realize its a reference to the matrix#bc one of his sources is a podcast/insta page that has red pill in the username#and that its not a real source its just some guy#and apparently the cdc isnt a real source to them anymore and we've hit rock bottom#jesus fuck will my mom be right about me having survivor's guilt being the only one vaxxed in the trailer park?#maybe. and i'm scared.#taks speaks#im already avoiding going to the dmv rn bc of the whole spike recently#and i just cant fathom all this shit anymore#sometimes maybe ignorance is bliss#when it's not actively harming everybody around you#*sighs* i wanna leave this shithole of a country#i don't like learning that i really am in the 25th percentile like i was told years ago after some test#its apparent and im not that smart so What The Fuck#maybe theres a reason why im the first in my family to get to 'college' even tho i burnt out before i could do it#i still got further than my dad educationally but apparently street smarts rule this#i dont want to sound narcissistic saying this#but its evident that im smarter than 75% of the country now and its sad#bc again. im really not that smart.#thanks i hate this
0 notes
Text

So when I was an egg in high school, I created a self-insert OC named Yar Kramer. I used him for a bunch of RPs, and several works of fiction, only one of which I actually completed. There were like two sprite comics and one thing I made that was literally just "sprites + dialogue and descriptions of the action", plus an unpublished and incomplete novel.
RP
The original original roleplay was on a Hitchhiker's Guide website called the H2G2, created by Douglas Adams as an attempt at realizing the eponymous Guide (which has been largely supplanted by Wikipedia). My username was originally "Adolescent White American [wronggender] Who Likes 47" (I liked the number 47 to its frequency in Star Trek); people shortened this to "Yankee Kid, likes 47" and subsequently "YK-47" and just "YK", which I backronym'd to "Yaradovich Kramer"[sic], after Yaridovich from Super Mario RPG and Cid Kramer from Final Fantasy 8. He was originally a coolkid Jedi in a red jacket, but at some point I retconned it to generic "psychic powers."
I also roleplayed him on a few RP MUDs, but I don't really remember any details there.
The "Original" Story
The novel was going to be called "Red Jacket", I think. "Yar Kramer" was a witness-protection alias, and his original name was Daniel Lancaster (hmmmm, someone's primary identity doesn't match their birth name!); he and his family had been forced to work for an evil organization called Project Robinson, which intended to create genetically-engineered espers for reasons I'm not sure about now. Project Robinson was led by an evil scientist called Dr. Krause and a computer named Mother Brain; I justified stealing the name "Mother Brain" because there were three unrelated video games which featured a character by that name (Metroid, Phantasy Star II on the Genesis, and Chrono Trigger).
The Grim Reaper was a woman who talked in underlined dialogue, and whacked people over the head with her scythe rather than actually reaping. She'd changed her form in the 1960s because she found the whole "skeleton" deal to be depressing. She had a black motorcycle with a flame pattern and the text "Pale Horse", and the souls she collected traveled in a pink sidecar which said "Binky" on the side in Comic Sans (where "Binky" is obviously a Discworld reference). When I created this in the 00's, there was totally nothing significant about a character who'd clearly changed her gender, nuh-uh.
Yar's love interest was Mackenzie Robinson, one of Project Robinson's creation. Despite the fact that the gummint had an active hand in extracting Yar's family from Project Robinson, there was some FBI/CIA spook called Agent Pinkerton who hounded Mackenzie like Inspector Javert. I know he had a classmate named Eckhart, who was this ratty-faced jerk with a heart of gold, who was inspired by one of my RL classmates.
I also found a half-written script for a comic, which gets as far as a prologue, followed by a scene which estalishes the witness protection business. Yar jokingly introduces himself Trigun-style as "Yaradovich Halvorsen Thompson-Stryfe-Gainsborough Donatello Leonard Raphael Michelangelo Farnsworth Anderson-Smith Jean-Luc Jones Solo Pepper Tibloxley Amelia Fayette-Mahoney Kierkegaard Williamtonshireworth Melora Kramer I." Wow. Let's see, "Halvorsen" and "Kierkegaard Williamtonshireworth Melora" are clearly made from whol cloth, and I'm not sure where "Jones" came from, but other than that, I can see in order ... Trigun (Thompson and Stryfe), Final Fantasy VII (Strife and Gainsborough), all four Ninja Turtles, Futurama, The Matrix, Star Trek, Star Wars, Cowboy Bebop (re-engrished "Pepelu Tivruski"), and Slayers. Again, wow.
First Reality
The "main" sprite comic, which was a sort of Final Fantasy parody made mostly in RPG Maker, and which ran from 2001 to 2004 on Keenspace. Yar Kramer was a "Neo-Samurai" (basically a ripoff of SeeD from Final Fantasy 8), fighting alongside a dude named Shigeru 'Gary' Oak (Gary Oak except as an adult, with a gunblade and dressed as Seifer Almasy, with no sign of any pokemon), and Tina Branford (Terra Branford without her tragic backstory).
The setting was incomprehensible if you didn't have detailed knowledge of Final Fantasy 6, 7, 8, and also Mega Man X; nearly every single place name was named after something from Final Fantasy except for Death Mountain, where they went to in order to get the Triforce (long story). A pink-haired goofy-and-hyperactive Celes Chere was the princess of Mysidia, and was a FF8-Sorceress; she frequently went in disguise as a thief named Fobby, and used a Reploid named Dancer as a body-double.
The main villain was named Darklumen, and his evil plan was to destroy the world by weakening the fabric of existence by leveraging sprite comic cliches, thus demonstrating that I have always been Like That. (The fact that I had a direct author avatar called the "Ultimate Guardian Force" with semi-omnipotent powers over the comic isn't even worth dwelling on, because omnipotent "author" characters are par for the course with sprite comics.)
The other party members: Kefka Palazzo, who was the court jester for Mysidia; Enerion Imusen, a half-Esper who was invented from whole cloth, who overcame his hangups about being half-esper with Tina's help before he got killed off by the bad guy; and "Rock Light" (because one of the reality-damaging sprite comic cliches was "Mega Man is present"), who was actually the Great Guardian Force Yu-Yevon in disguise for convoluted reasons.
In the ending, it's mentioned that Gary marries Princess Celes, and sort of vaguely implies that Yar ends up with Tina. (Tina made actual romantic overtures to Yar halfway through the comic, but they were interrupted by shallow comedy.)
I absolutely refused to let go of a running gag in which a male character would say something that broke the fourth wall, and at least one female character would immediately yell at him for doing so.
... I actually found some MIDI songs in the First Reality files which I personally composed. Well ... I say "composed", but the Darklumen final boss music was clearly based on the Super Smash Bros 1's Final Destination music with techno-twittering from All Your Base, one was based on a boss theme from Final Fantasy X combined with anime music, and Yar Kramer's personal themesong was chiefly based on Glyde's theme from The Misadventures of Tron Bonne.
YaraY
The other sprite comic, hosted on a subdirectory of First Reality's site. The name came from Yar's evil twin, Ray Remark ("Yar" and "Kramer" spelled backwards), and also from the Japanese expression "yare yare" (translated in JJBA "good grief").
It was a shallow Bob and George-esque thing with Mega Man sprites, and invovled Yar's shenanigans opposite Ray Remark; a straightlaced roommate with blue hair named Elbert Ssab (I don't know where I got "Elbert" from, but I came up with "Ssab" after noticing that "Elbert" backwards is "Treble"); a Reploid named Jive who was an orange recolor of Zero from Mega Man Zero; and a girl in a pink shirt named Kira, whose character concept began and ended with "hyperactive blonde girl." At one point, there was a comic which depicted First Reality as an actual console RPG being played by Kira; this comic was then ported directly to First Reality.
I abruptly stopped updating it in the middle of a story arc in which Jive went off with a group Maverick Hunters which inexplicably included Zio from Phantasy Star 4, who was just there to be generically evil rather than actually pursuing any of his canonical goals.
Super Adventure Yar
And finally, the "sprites plus dialogue" thing. It used whatever anime, video game, and internet characters I was interested in at any given moment, and there were inserts from several people I knew online. All of whom were basically overpowered in some respect, i.e. one of the friend-inserts was literally just a redheaded Goku in a trench coat, except his Saiyan name was "Suckarot". It was the most absurd and ridiculous of these things.
Yar was your basic inexplicably-overpowered action-shounen protagonist, and people kept going "What!? Why is he so powerful!?" (If there was going to be an explanation, I never got a chance to give it and I don't remember what it was, but I doubt there was anything reasonable.) Of course, this was also true of pretty much every protagonist.
His fighting style involved throwing energy blasts, and his signature move was named "Island King Kamehameha", because I knew the etymology of the Dragonball attack, but the kind of creative person I was at the time was that nuance, self-awareness, and "general understanding of what I was putting into my stories" were something that happened to other people.
Mayl Sakurai was impulsively violent with a squeaky-mallet.
At one point, while the protagonists were discussing a plot point which Mayl wasn't present for, she said, "What the hell are you talking about?" and then tossed an entire burger into her mouth.
Cut Man's NetNavi was FishMan.exe.
Yar bought Chii Chobits from Strong Bad, who ran an unbelievably shady second-hand electronics store; Chii's copycat tendencies extended to copying other peoples' magic and superpowers.
He also bought a generic NetNavi and expressed the intention to customize it, but all sign of NetNavis were dropped after a few episodes.
The "ageless faceless gender-neutral culturally-ambiguous adventuring person" (AFGNCAAP) from Zork/Enchanter was one of the main characters. They frequently used spells from Enchanter such as "gaspar" ("provide for your own resurrection" -- basically like a Final Fantasy "Auto-Life" spell, but AFGNCAAP was also able to use it on others), "vaxum" ("make hostile creature friendly", and every single target which it actually worked on promised to kill them after it wore off), "krebf" ("repair willful damage"), and "talcor" (healing; this seems to be something I made up myself, because I can't find any references to it in Enchanter canon).
I insisted on using "he/she" and the like instead of just the singular "they", wow I was deep in the egg in 2004. But they did say "I don't have a gender" at one point!
Magus/Janus from Chrono Trigger was trying to take over the world using robotic Sinistars. His minions were "the Terrible Trio", which consisted of Onslaught from Marvel vs. Capcom 1, Dalton from Chrono Trigger, and Dynamo from Mega Man X.
I stole the "now I'm wet and on fire!" joke from the webcomic Adventurers! during a fight between Dalton and AFGNCAAP.
Magus got a Vegeta-style "suddenly I happen to be on the same side of the heroes" redemption with the sudden arrival of, um, the Saiyans. Starting with Raditz as just a retread of Dragonball Z.
After Raditz was beaten, he sent a message to Vegeta and "Zappa", who was just Nappa but with a terrible wig and an atrocious southern accent; I have no idea what I was going for there.
The planet Arlia from Dragonball Z was populated by clones of Alia from Mega Man X5. It had the same fate as in the show, namely that Vegeta and Zappa just casually blew it up after going on a rescue-a-princess quest.
There was an "It's a gundam!" joke there.
The Goku-expy friend-insert taught Yar how to fly Hitchhiker's Guide-style ("throw yourself at the ground and miss"), and how to use bullet-time.
Mayl trained under Magus. At one point, while she was fighting a friend-insert with a sniper rifle (who'd previously stolen everyone's wallets for no apparent reason), Magus remarked that she had "hidden potential" and noted that in her hands, her squeaky mallet was just as powerful as the sniper rifle.
Vash the Stampede showed up, and the plot promptly started getting derailed as everyone around him dropped everything to try to claim his $60 billion bounty (Onslaught, to Dalton and Dynamo: "We'll split it 50-50-50!").
At one point, Vash ran off with Chii for reasons that only slightly made sense in context, and Yar chased them to a town called Las Eisley.
The three of them got into a bar fight at a "restaulant"[sic] (I thiiiink this was originally actual engrish from Trigun itself?) which completely wrecked the building.
After the bar fight, Yar called up AFGNCAAP to make repairs using the krebf spell; AFGNCAAP asked, "Was all the damage willful?" and Yar replied, "Well, I definitely proceeded in the full knowledge that massive destruction would occur." Due to the rules of sprite-comic comedy, this was enough for krebf to work.
There was a "Dear Strong Bad, how do you type with boxing gloves on?" joke.
In the middle of everything else, I started writing an episode introducing Valkyries and Loki -- which displayed a surprisingly deep knowledge of Norse mythology on 18-year-old-me's part -- but I never finished it and my files don't even have the sprites for the main Valkyrie character, who was another friend-insert.
... All of these continuities just feel amazing to me in retrospect, because this is the kind of thing that can only happen in fanfiction. Only something using existing characters, our existing associations with these characters, can possibly reach this level of ridiculousness.
Which isn't to say it's all fun and games, though. I was a particularly un-woke Rotten Egg, which meant that there was rampant sexism, and lowkey fanservice. The concept might look fun, but the execution was invariably "the worst parts of the sprite comic fandom."
#yar kramer#original character#fanfiction#trans stuff#my stuff#re: my stuff#meta#shenanigans#meta shenanigans#bob and george#violence mention#death mention#sexism mention#long post in link
14 notes
·
View notes
Text
Tag people you want to get to know better
tagged by @storiesbehold
tagging: @youarethespecial, @wiiillcw-fcrest, @dreamsofalife, @rxtroskull... and that’s all because I don’t want to be annoying. If you wanna do it, pretend I tagged you OK?
nicknames: Ditto or Raz, depending on if it’s RP or art related. I have other nicknames, but they are references to my real name
zodiac: Aquarius
height:5″ 2″, I think. I’m short af is all I know
time: Right now? It’s 9:03.
favorite band / artist: Kaiser Chiefs, The Hoosiers, The Eagles, and Styx.
song stuck in my head: Scary Love by the Neighbourhood
last movie i saw: I am in the process of watching Children of the Corn.
last thing i googled: Pixlr, which is a web based photoshop like tool..
other blogs: none that I use anymore.
do i get asks: I get a few.
why did i choose this username: It’s part of a line from Lego Movie 2. “Why would you go back into the Matrix when you know the truth?” It also fit because of how I justify playing a Rex post TLM2 when he died in the end.
following: 100 people.
average amount of sleep: I work a 9-5, so I try to get the 6-7 hours of sleep recommended for adults.
what i’m wearing (right now): PJ pants and a Nightmare Before Christmas tee.
dream job: Something in cybersecurity.
dream trip: England or LEGO HQ in Denmark. Yes, I mean that.
favorite food(s): Pizza, tater tots, chicken nuggets from Wendys, and asparagus.
play any instruments: Ocarina, a little bit of drums, I sing. I also used to play the violin and want to learn the mandolin.
eye color: Blue
hair color: Black, with blue and pink bang streaks. (like Wyldstyle bb)
languages you speak: English, some Spanish.
most iconic song: Right now, I would say either Stressed Out by Twenty-One Pilots or.. actually just that.
random fact: I have gone ghost hunting a few times. I even went to classes for it.
describe yourself as aesthetic things: I dunno... Lego, crayons, autumn, Halloween, magic, high fantasy, urban decay and exploration, time travel, sci-fi, slime, foam, bubbles... Did I do that right?
2 notes
·
View notes
Text
Fragmentation 0.8

Plot: How does one measure freedom? Are our choices truly our own, or are they part of a preset design outside of our control? We all have a question burning inside of us, though few speak it out. It is the question that drives us forward, seeking purpose in our lives. What is The Matrix?
Rating: NC-17 // NSFW
Genre: Series | The Matrix!AU | angst | sci-fi | action | drama
Pairing: N/A
Warnings: Strong language, allusions to suicide, extreme angst, graphic violence
Links: FAQ || BTS Masterlist || Admin E’s AO3 || [ REQUESTS ARE OPEN ]
Word Count: 2,138
AN: Like all of my works, there will be OCs working opposite of the boys. In this story, we have three. The first in the Fragmentation series is Mackenzie. Like Yoongi and Hoseok, she is self-substantiated. How she does will be revealed! On to Crow’s origin story for Defragmentation! All information in the universe can be found on the official Matrix Wiki so please use that as a reference guide if you ever get confused!
Tag List: @aroseforyoongi, @prisczero, @pinkpjmin, @btsaudge, @flowerwrites06, @unoriginal-username15432
© thebiasrekkers (Admin E). All rights reserved. Reposting/modifying our work is prohibited. Translations are not allowed. Plagiarism/stealing is not tolerated by any means. Legal action will be taken in instances of theft.
“Goddammit Mackenzie! I thought I told you to be home by eleven!”
A pair of green eyes glared up at the rotund looking man. His reddish complexion was barely seen from the scraggly beard covering the majority of his face. Sweat soaked through the dingy wife beater he wore, half stuffed into a pair of faded cargo pants. There were a pair of dog tags hanging from his neck - something that always piqued the green-eyed owner’s interest, but never enough to ask about them.
Mackenzie doubted he served anyone but himself, let alone the country.
Instead of answering him, she folded her arms across her chest. Normally this was the time when she escaped into her room, but he was blocking the way. He was always getting in her way.
It was his fault. Life used to be normal. This was as far from normal as a person could get. He was as far from being a real father as a person could get.
“You don’t have anything to say for yourself?”
She rolled her eyes, doing her best to ignore the stink of alcohol on his breath. Mackenzie didn’t understand why he persisted on being like this. It was the same shit on a different day. Part of her wished that he would walk outside and get hit by a bus. But she knew that that was a miracle she would never be granted.
“Answer me!”
“What do you expect when I’m closing?” Mackenzie asked, her tone flat and devoid of all emotion.
Her father’s eyes narrowed at her. She didn’t even flinch. “What did you just say to me?”
“I didn’t stutter,” came her clipped response as she let her arms fall to her side, “now move. I still have homework to do.”
Before she could take a single step, her father was advancing on her. Mackenzie mentally braced herself for what was coming. Her body was used to it, but it was always that dark corner in the back of her mind that suffered the most from all of this. So long as that part was shielded, she could handle everything else that usually followed.
The pain that exploded from the side of her head paled in comparison to the pain of her hip crashing to the floor. Her arms immediately shot up to cover the top of her head as her body curled into a ball. The flurry of kicks that collided into her caused her nerves to scream out in agony. But Mack refused to scream, instead choosing to bite the inside of her mouth. The taste of blood flooded across her tongue and she heard her teeth clacking together when the heel of her father’s boot hit the top of her head.
After what felt like hours, but were actually minutes, her father abandoned her there on the floor. Every square inch of Mack’s body throbbed from the pain. There would be bruises tomorrow. Thankfully he’d missed her face so she could still go to work and school without receiving too many curious gazes. It was none of their goddamn business anyway.
Mack waited until she heard the front door slam before picking herself up off the floor. She roughly rubbed the back of her wrist across the corner of her mouth, eyeing the blood smear and rolling her eyes. She couldn’t help but wonder if the old man would notice if she spit on the floor just to spite him. Would he even care?
Grunting, she made her way into her bedroom, locking the door after shutting it behind her. Her father would most likely be out getting drunk for the rest of the night. It meant she had the whole house to herself until he came stumbling back in at four in the morning. Mack just hoped that she’d be able to get all of her school assignments finished and have enough time to surf the internet. Something told her that she was getting closer to finding what she was looking for.
Or, rather, who she was looking for.
Speeding through her homework, Mack pulled up several browser windows once she was securely connected to the internet. Her eyes darted across the screen, her fingers flying over the keys - pausing only long enough to use her mouse to click on a few links that spiraled her into another location. Mack reached out to everyone that might have a lead and she got just a little bit closer than she did the day before.
After another hour, she was starting to get frustrated. Everything was forcing her into a dead end. Just when she thought she had a lead, it only caused her to go on a wild goose chase on the wide web. Mack roughly scratched at her head, attempting to tamp down on her slowly mounting anger.
“Dammit!” She slammed her fists on her desk, rattling everything on it. “Why can’t anyone just give me a straight fucking answer?!”
Burying her face in her hands, Mack did her best to suppress a sob that she didn’t even realize was building up in the back of her throat. She was tired, in pain, and a little hungry. But most of all, she was starting to lose hope. And that was starting to hurt her more than she would care to admit aloud.
“Fuck it,” she muttered, standing up from her chair, “I’ll pick this up in the morning.”
Just as Mack turned away from her desk, the ping from her instant messenger sounded from the laptop. Pausing, she craned her neck to look at the screen. The username consisted of a series of random numbers. But what made her heart nearly drop to her stomach was what the person said.
You’ll never find Michael because you don’t know The Truth.
Mack ran back to her desk, her fingers gliding over the keyboard. She could barely hear herself typing from how loudly her heart was beating inside of her eardrums. It was the first time someone responded to her inquiries with something credible. It was the first time she could actually believe what she was seeing.
Because it was the first time someone actually mentioned her brother by name.
Who are you? How do you know that name?
The cursor on her screen blinked steadily. Mack wasn’t sure how much more she could take because she was almost positive that this was the clue she’d been searching for after all this time. It was a solid lead just because someone was able to give her a name. If they knew her brother’s name, that meant that they also had a good idea of where he was. She couldn’t afford to let this person slip from her grasp.
Who I am doesn’t matter.
How I know doesn’t matter.
What matters is...
What are you willing to do to know The Truth?
She stared at the computer dumbfounded. Was this another trick? Was this person just jerking her chain, trying to lead her into a false sense of security before sucker punching her in the face like everyone else? It would be the most logical explanation. It was the only thing that actually made sense.
Mack didn’t know why, but she felt like that wasn’t the case. Not with this person. Were they trying to lead her onto the right path after having been on the wrong one for so long?
Narrowing her eyes, she began typing again.
Anything.
The air was cold and frigid. Mack rubbed her hands together, her breath coming out in small white clouds. She peered through the metal fence as people continued to file through the city. She was isolated from the rest, sitting on a park bench and waiting. She looked at her watch, making a mental note of the time. She had five minutes left to wait.
Five minutes until she would know whether this was real or a hoax.
The sound of gravel crunching underfoot quickly brought her out of her thoughts. Mack stood up immediately, facing the direction of the noise. All she could see were the trees cloaked in shadows cast from the street lights. She couldn’t see anyone, but the crunching noise wouldn’t stop. There was a large lump forming in Mack’s throat and she couldn’t help wondering if she’d fallen into a trap.
Seconds after thinking that, a young woman dressed in gray and black appeared. She wore a long black coat with a hood just barely covering her head of thick curls. Her eyes were hidden behind a pair of sunglasses. The rest of her outfit was some sort of gray jumpsuit that almost seemed to shimmer when it hit the light just right. The legs of the suit were stuffed into a pair of shin high combat boots - the heels continuously crunching into the gravel; releasing an eerie sound.
Mack puffed out another breath of cloudy air just as the woman stopped three feet from her.
“Y-You’re early,” she managed to stammer out.
The other woman smirked, her auburn curls accentuating her mocha skin even in shadow. “If you’re early, you’re on time. If you’re on time, you’re late. You’re late, Mack.” She reached up with a gloved hand to remove the sunglasses from her face, revealing a set of dark hazel eyes. “Or should I say, Crow?”
Mack took a step back, her lips parting slightly as the woman referred to her as both her name and her alias. Her heart hammered against her ribs, causing her lungs to tighten up inside. What in the world was happening? Just how much did this woman know?
Not wanting to look like some punk, she shook her head and straightened her stance. “You have information I want and yet I don’t know anything about you.”
The woman continued to smile. “I already told you that who I am doesn’t matter. It never will matter.” She shrugged. “Not until you know The Truth.”
“What the hell is this truth you keep talking about?” Mack could feel her anger starting to grow. “What does it even mean?”
She watched the other woman reaching into her pocket to pull out a cell phone. She punched a few numbers and then pressed it up to her ear. “Unfortunately, we don’t have a whole lot of time for me to explain. You’re going to have to see it for yourself.”
Mack bit her lower lip, her eyes narrowing as she watched the woman reaching into her other pocket with her free hand. Half a second later, her heart froze as the woman trained the business end of a semi-automatic pistol at her.
“Whoa,” Mack said, raising her hands up slowly, “what in the fuck are you doing, lady?”
“You have a choice to make, Crow, and you don’t have a whole lot of time to make it, so I’ll be quick.”
Panic began to settle around Mack’s chest. “What do you mean I don’t have a lot of time?!”
“Agents are coming. They’re coming for you because you’re sloppy and desperate, which, sadly, is making me sloppy and desperate.”
When the hammer clicked back on the gun, tears sprung up in Mack’s eyes. “Please, don’t do this.”
“Shut-up,” snapped the woman, the smile now completely gone from her face, “I already told you we don’t have a lot of time. You have two choices. You let the Agents take you or I force you out of the bubble you’ve unknowingly been put in. I’m giving you five seconds starting now. Five.”
She took another step back, but the woman advanced on her. Mack didn’t know what any of it meant. What did she mean by “agents” and why did it seem like this woman was trying to help her, despite the situation looking crazy to everyone else?
“Four.”
Her heart shook in her chest, causing her to reach up and clutch at the front of her jacket. Mack didn’t want to die. She didn’t want to die without knowing the answers.
“Three.”
She still didn’t know where her brother was. She still didn’t know what The Truth was and what it had to do with her brother.
“Two.”
She wanted to live!
Mack ran up to the woman, wrestling the gun from her grasp. The woman took a step back, but the smile returned to her face. Mack pressed the barrel of the gun up to her temple as tears streamed down her cheeks. Multiple footsteps seemed to thunder through the gravel, but Mack could only see the single snowflake that began to fall from the night sky. The world disappeared into lines of green numbers before returning to normal.
She smiled.
“One.”
After the gunshot ripped through the night, Mack’s world darkened immediately. But she...she felt free, somehow.
“Welcome to the Real World.”
#bangtanarmynet#ficswithluv#btsbookclub#btswriterscollective#btspocnet#bts fanfiction#bts fanfic#bts fanfics#bts the matrix#bts the matrix au#bts the matrix!au#bts science fiction#bts science fiction au#bts science fiction!au#bts sci-fi#bts sci-fi au#bts sci-fi!au#the matrix au#the matrix!au#bts angst#bts drama#bts action#bts x angst#bts fragmentation#bts defragmentation#thebiasrekkers#bts thebiasrekkers#thebiasrekkers bts
4 notes
·
View notes
Text
How to run MySQL Enterprise Edition on Oracle Cloud Infrastructure from Marketplace ?
Deploy MySQL Enterprise Edition with OCI Market Place ApplicationIn this blog we will look into the process to deploy MySQL Enterprise Edition in to Oracle Cloud Infrastructure.In this blog we will discuss the below agenda1. Introduction about MySQL EE and OCI Market place2. Deploy MySQL EE into Oracle Cloud Infrastructure3. Accessing MySQL database from On-premises.4. Licensing/Purchase model of using MySQL EE from OCI marketplace5. ConclusionIntroductionIf you wanted to run MySQL Enterprise Edition (EE) in Oracle Cloud Compute Instance (VM) then generally what we do is first download the MySQL EE binaries from the oracle website and manually push to the Oracle Cloud Instance where, MySQL EE needed to be installed and follow the steps to get installed.Another approach is going with MySQL EE image from Oracle Cloud Marketplace.It automates this manual process to download the binaries and push to oracle cloud and then follow the step to install the MySQL binaries, it is pre-loaded package which by default install below software MySQL Server EE MySQL Enterprise Backup MySQL Shell MySQL Router MySQL Enterprise Thread poolThe MySQL Enterprise Edition Marketplace Application is an OCI compute instance, running Oracle Linux 7.7, with MySQL EE 8.0.x.The MySQL EE installation on the deployed image is similar to the RPM installation.This solutions is user-managed, meaning you are responsible for upgrades and maintenance.MySQL Enterprise Edition version 8.0 is available in OCI Marketplace. MySQL 5.7 nor 5.6 are not available in Oracle Cloud Infrastructure Marketplace. If the user needs previous versions, you need to create an OCI Compute Linux, download and install MySQL EE by themselves, similar to on-prem.What is Oracle Cloud Infrastructure Marketplace?Oracle Cloud Infrastructure Marketplace is an online store that offers solution specifically for customers of Oracle Cloud Infrastructure.you can find listings for two types of solutions from Oracle and trusted partners:1. ImageImages are templates of virtual hard drives that determine the operating system and software to run on an instance. You can deploy image listings on an Oracle Cloud Infrastructure Compute instance.2. StackStacks represent definitions of groups of Oracle Cloud Infrastructure resources that you can act on as a group.More info:- https://docs.oracle.com/en-us/iaas/Content/Marketplace/Concepts/marketoverview.htmWhat is MySQL Enterprise Edition?MySQL Enterprise Edition is a commercial product. Like MySQL Community Edition, MySQL Enterprise Edition includes MySQL Server, a fully integrated transaction-safe, ACID-compliant database with full commit, rollback, crash-recovery, and row-level locking capabilities. In addition, MySQL Enterprise Edition includes the following components designed to provide monitoring and online backup, as well as improved security and scalability, high availability.More info:- https://dev.mysql.com/doc/refman/8.0/en/mysql-enterprise.htmlDeploy MySQL EE into Oracle Cloud InfrastructurePrerequisite:- Make sure You have have create an account with Oracle Cloud. Make sure virtual cloud network(VCN) is createdhttps://docs.oracle.com/en-us/iaas/Content/GSG/Tasks/creatingnetwork.htmStep 1:- Create compute instance Step 2 : Change the shape based on the requirements(in terms of CPU , RAM )Step 03:-Configure the NetworkStep 04:- Add SSH key filesStep 05 :- Create the InstanceStep 06:- View the created InstanceStep 07:- Note down the Instance detailsInstance Public IP : 140.238.166.106Instance User Name: opcInstance Private IP: 10.0.0.92MySQL Host Name: localhostMySQL UserName: rootMySQL Port: 3306Step 08:- Let’s connect the Instance from On-premises network using PuttyMake sure putty is installed in your local machine, if not then please install by downloading from the web links:- https://www.putty.org/Enter the correct public IP address as well as .ppk file to connect , refer below screenshot .When you click on OPEN, you will see that you are connected to Oracle Cloud Infrastructure.Step 09:- Get the temporary password$sudo grep 'temporary password' /var/log/mysqld.logStep 10:- Login to MySQL DBStep 11:- Change the Password for the root user from temporary password to NEW passwordalter user root@'localhost' identified by 'MySQL8.0';Step 12:- Next is you can ready to execute the commands with MySQL Enterprise EditionThat’s it.You can also connect MySQL Server using MySQL shell utilitySo you may noticed that I have not install manually any mysql clients , libraries its dependencies , MySQL shell because it is bundled and available as pre-installed image at Oracle Cloud Marketplace.It’s easy to plug in and play with MySQL Enterprise Edition.More info available at MySQL Website:-https://dev.mysql.com/doc/refman/8.0/en/mysql-oci-marketplace.htmlLicensing ModelThis is a BYOL (bring your own license) product with there are additional fees for the infrastructure usage."Hence Price of MySQL EE OCI marketplace = Price of MySQL EE + Price of Oracle Cloud Infrastructure VM usagePrice for MySQL EE goes via MySQL Sales , you can talk with sales to get the details pricing matrix(https://www.mysql.com/about/contact/).MySQL EE licensing model is "per Server", for 2 classes: Servers with 1-4 Sockets, and Servers with 5+ Sockets. MySQL Enterprise Edition 1-4 socket server : USD5000MySQL Enterprise Edition 5+ socket server : USD10000More info :- https://www.mysql.com/products/Price of Oracle Cloud Infrastructure VM usage, it depends on kind of shape (comprises of OCPU, RAM, Storage) you are going to configured to run MySQL Enterprise Edition (EE).You can calculate using OCI cost estimator: - https://www.oracle.com/in/cloud/cost-estimator.htmlIf you are bringing your “on-premise license”, so this offering is available at no additional charge. Fees for usage of Oracle infrastructure resources, such as compute instances, are charged separately and based on the rate of usage. Learn about pricing" linked to https://www.oracle.com/cloud/compute/pricing.htmlConclusion:-MySQL Enterprise Edition include most comprehensive set of advanced features (solutions for scalability, performance, high availability, securities), management tools (unified monitoring and hot/online backup) and technical supports(24*7 support backed by MySQL engineering team)It’s easy to deploy on private cloud , public cloud and available as “Managed Service” at Oracle Cloud named as MySQL Database Service (MDS).MySQL Enterprise Edition is BYOL product and it is annual subscription product which has to be renewed annually.
https://mysqlsolutionsarchitect.blogspot.com/2021/05/how-to-run-mysql-enterprise-editionee.html
0 notes
Text
Technologies for Multi-Factor Authentication and Its Relevance
Multi-Factor Authentication (MFA) is a comprehensive authentication method that requires users to use at least two (and more) different verification factors to prove their identity to gain access to a website, mobile application, or other online resources. In this way, the attacker also has at least one more hurdle to breach before gaining access to the target's account if one element is breached or broken. At least two authentication factors are used for most Multi-Factor Authentication implementations.
Types of Technologies for Multi-Factor Authentication
Hardware Tokens: Small, simple-to-use hardware devices that are brought with them by users to authorize access to a network service. Supporting a strong one-time password (OTP) authentication, these hardware tokens provide the Multi-Factor Authentication possession factor, thus allowing enhanced protection for banks and application providers who need a single computer to protect multiple applications.
Soft Tokens: A single-use login PIN is created by software or app-based tokens. These tokens are also used for Multi-Factor Authentication, in which the possession factor is given by the device, in this case, a smartphone.
SMS Text-Message: SMS-Text Message provides the user with one-time authentication passwords. The password is sent to the user's mobile device via an SMS-text message.
Push Notification: Push notifications provide the authentication code or one-time password on the mobile device of the user via a push notification. The notification appears on the device's lock screen rather than as an SMS message.
Visual Cryptogram: Visual Cryptogram MFA solutions use a particular visual challenge found in a colored dot matrix graphical cryptogram. On their mobile computer, the consumer uses the camera to photograph the cryptogram and decode the transaction information inside.
Mobile Authentication: Mobile authentication refers to the process of verifying a user or verifying the device itself through their phone, enabling users to log in to secure locations and access services with improved protection from anywhere.
Biometric Authentication: This includes leveraging a fingerprint scan or facial recognition to authenticate users accurately and safely, even on mobile devices, as well as behavioral authentication that offers an invisible protective layer that continuously authenticates end-users by the specific ways they communicate through a keystroke, swipe pattern, and mouse movements with their computer or mobile device.
Why Is Multi-Factor Authentication Needed?
Methods of authentication that rely on more than one factor are more challenging to compromise than methods with a single factor. Therefore, Multi-Factor Authentication strategies correctly developed and implemented are more effective and a better deterrent for cybercriminals than obsolete single-factor username/password user authentication, which is more challenging to protect against security breaches, compromising data security. Such data breaches may potentially result in significant loss of missing/stolen data, identity theft, and phishing attacks, etc., to the customer or organization.
Before they can be authenticated, Multi-Factor Authentication allows users to prove their identities using two or more verification methods. In this way, the attacker still has at least one more barrier to breach before breaking into the target if one element is compromised.
When accessing any confidential data, multiple-factor authentication can be used. For instance:
You use MFA by getting something you know (the PIN) and something you have (the ATM Card) when you access your bank account at an ATM.
You use Multi-Factor Authentication when you visit your Facebook, Google, or Microsoft account from a new location or device, by getting something you know (the password) and something you have (your mobile phone that receives the notification you must accept before logging in).
Good Multi-Factor Authentication (MFA) enables you to be secured and offers the ability to do so easily while accessing a service provider's features and functions.
0 notes
Text
300+ TOP SELENIUM Interview Questions and Answers
Selenium Interview Questions for freshers and experienced :-
1. What is Automation Testing?
Automation testing or Test Automation is a process of automating the manual process to test the application/system under test. Automation testing involves use to a separate testing tool which lets you create test scripts which can be executed repeatedly and doesn’t require any manual intervention.
2. What are the benefits of Automation Testing?
Benefits of Automation testing are:
Supports execution of repeated test cases
Aids in testing a large test matrix
Enables parallel execution
Encourages unattended execution
Improves accuracy thereby reducing human generated errors
Saves time and money
3. Why should Selenium be selected as a test tool?
Selenium
is free and open source
have a large user base and helping communities
have cross Browser compatibility (Firefox, chrome, Internet Explorer, Safari etc.)
have great platform compatibility (Windows, Mac OS, Linux etc.)
supports multiple programming languages (Java, C#, Ruby, Python, Pearl etc.)
has fresh and regular repository developments
supports distributed testing
4. what is Selenium and what is composed of?
Selenium is a suite of tools for automated web testing. It is composed of
Selenium IDE (Integrated Development Environment) : It is a tool for recording and playing back. It is a firefox plugin
WebDriver and RC: It provide the APIs for a variety of languages like Java, .NET, PHP, etc. With most of the browsers Webdriver and RC works.
Grid: With the help of Grid you can distribute tests on multiple machines so that test can be run parallel which helps in cutting down the time required for running in browser test suites
5. What do we mean by Selenium 1 and Selenium 2?
Selenium RC and WebDriver, in a combination are popularly known as Selenium 2. Selenium RC alone is also referred as Selenium 1.
6. Which is the latest Selenium tool?
WebDriver
7. What are the testing types that can be supported by Selenium?
Selenium supports the following types of testing:
Functional Testing
Regression Testing
8. Why should Selenium be selected as a test tool?
Selenium
is free and open source
have a large user base and helping communities
have cross Browser compatibility (Firefox, chrome, Internet Explorer, Safari etc.)
have great platform compatibility (Windows, Mac OS, Linux etc.)
supports multiple programming languages (Java, C#, Ruby, Python, Pearl etc.)
has fresh and regular repository developments
supports distributed testing
9. What are the different types of waits available in WebDriver?
There are two types of waits available in WebDriver:
1.Implicit Wait
2.Explicit Wait
Implicit Wait: Implicit waits are used to provide a default waiting time (say 30 seconds) between each consecutive test step/command across the entire test script. Thus, subsequent test step would only execute when the 30 seconds have elapsed after executing the previous test step/command.
Explicit Wait: Explicit waits are used to halt the execution till the time a particular condition is met or the maximum time has elapsed. Unlike Implicit waits, explicit waits are applied for a particular instance only.
10. What are the limitations of Selenium?
Following are the limitations of Selenium:
Selenium supports testing of only web based applications
Mobile applications cannot be tested using Selenium
Captcha and Bar code readers cannot be tested using Selenium
Reports can only be generated using third party tools like TestNG or Junit.
As Selenium is a free tool, thus there is no ready vendor support though the user can find numerous helping communities.
User is expected to possess prior programming language knowledge.

SELENIUM Interview Questions
11. When should I use Selenium IDE?
Selenium IDE is the simplest and easiest of all the tools within the Selenium Package. Its record and playback feature makes it exceptionally easy to learn with minimal acquaintances to any programming language. Selenium IDE is an ideal tool for a naïve user.
12. How do I launch the browser using WebDriver?
The following syntax can be used to launch Browser:
WebDriver driver = new FirefoxDriver();
WebDriver driver = new ChromeDriver();
WebDriver driver = new InternetExplorerDriver();
13. What is Selenese?
Selenese is the language which is used to write test scripts in Selenium IDE.
14. When should I use Selenium Grid?
Selenium Grid can be used to execute same or different test scripts on multiple platforms and browsers concurrently so as to achieve distributed test execution, testing under different environments and saving execution time remarkably.
15. What is Selenium? What are the different Selenium components?
Selenium is one of the most popular automated testing suites. Selenium is designed in a way to support and encourage automation testing of functional aspects of web based applications and a wide range of browsers and platforms. Due to its existence in the open source community, it has become one of the most accepted tools among the testing professionals.
Selenium is not just a single tool or a utility, rather a package of several testing tools and for the same reason it is referred to as a Suite. Each of these tools is designed to cater different testing and test environment requirements.
The suite package constitutes of the following sets of tools:
Selenium Integrated Development Environment (IDE) – Selenium IDE is a record and playback tool. It is distributed as a Firefox Plugin.
Selenium Remote Control (RC) – Selenium RC is a server that allows user to create test scripts in a desired programming language. It also allows executing test scripts within the large spectrum of browsers.
Selenium WebDriver – WebDriver is a different tool altogether that has various advantages over Selenium RC. WebDriver directly communicates with the web browser and uses its native compatibility to automate.
Selenium Grid – Selenium Grid is used to distribute your test execution on multiple platforms and environments concurrently.
16. What is an Xpath?
Xpath is used to locate a web element based on its XML path. XML stands for Extensible Markup Language and is used to store, organize and transport arbitrary data. It stores data in a key-value pair which is very much similar to HTML tags. Both being markup languages and since they fall under the same umbrella, Xpath can be used to locate HTML elements.
The fundamental behind locating elements using Xpath is the traversing between various elements across the entire page and thus enabling a user to find an element with the reference of another element.
17. How to type in a textbox using Selenium?
User can use sendKeys(“String to be entered”) to enter the string in the textbox.
Syntax:
WebElement username = drv.findElement(By.id(“Email”));
// entering username
username.sendKeys(“sth”);
18. How can you find if an element in displayed on the screen?
WebDriver facilitates the user with the following methods to check the visibility of the web elements. These web elements can be buttons, drop boxes, checkboxes, radio buttons, labels etc.
1.isDisplayed()
2.isSelected()
3.isEnabled()
Syntax:
isDisplayed():
boolean buttonPresence = driver.findElement(By.id(“gbqfba”)).isDisplayed();
isSelected():
boolean buttonSelected =driver.findElement(By.id(“gbqfba”)).isDisplayed();
isEnabled():
boolean searchIconEnabled = driver.findElement(By.id(“gbqfb”)).isEnabled();
19. Can you explain the phase of Automation Testing LifeCycle?
Outline the potential benefits and test tool proposal
Test tool evaluation and selection
Steps necessary to outline automated testing to the project
Identifies the test procedure standards, defines the tests, defines development standard
Test plans are executed
This is done throughout the life-cycle
20. What are the different types of locators in Selenium?
Locator can be termed as an address that identifies a web element uniquely within the webpage. Thus, to identify web elements accurately and precisely we have different types of locators in Selenium:
ID
ClassName
Name
TagName
LinkText
PartialLinkText
Xpath
CSS Selector
DOM
21. What are the different types of Drivers available in WebDriver?
The different drivers available in WebDriver are:
FirefoxDriver
InternetExplorerDriver
ChromeDriver
SafariDriver
OperaDriver
AndroidDriver
IPhoneDriver
HtmlUnitDriver
22. What is difference between assert and verify commands?
Assert:
Assert command checks whether the given condition is true or false. Let’s say we assert whether the given element is present on the web page or not. If the condition is true then the program control will execute the next test step but if the condition is false, the execution would stop and no further test would be executed.
Verify:
Verify command also checks whether the given condition is true or false. Irrespective of the condition being true or false, the program execution doesn’t halts i.e. any failure during verification would not stop the execution and all the test steps would be executed.
23. What are the steps to run automation using selenium?
The very basic steps are:
Record the test steps using selenium-IDE.
Modify the script according to the testing needs. Add validation points, Java Scripts, Time-out etc.
Run the test.
View the result after test run complete analyze.
24. What are the capabilities of Selenium IDE?
Selenium IDE (Integrated Development Environment) works similar to commercial tools like QTP, Silk Test and Test Partner etc.
The below points describes well about Selenium IDE.
Selenium IDE is a Firefox add-on.
Selenium IDE can support recording the clicks, typing, and other actions to make a test cases.
Using Selenium IDE, a tester can play back the test cases in the Firefox browser.
Selenium IDE supports exporting the test cases and suites to Selenium RC.
Debugging of the test cases with step-by-step can be done.
Breakpoint insertion is possible.
Page abstraction functionality is supported by Selenium IDE.
Selenium IDE can supports an extensibility capability allowing the use of add-ons or user extensions that expand the functionality of Selenium IDE
25. How to find more than one web element in the list?
At times, we may come across elements of same type like multiple hyperlinks, images etc arranged in an ordered or unordered list. Thus, it makes absolute sense to deal with such elements by a single piece of code and this can be done using WebElement List.
Sample Code
// Storing the list
List elementList = driver.findElements(By.xpath("//div//ul//li"));
// Fetching the size of the list
int listSize = elementList.size();
for (int i=0; i {
// Clicking on each service provider link
serviceProviderLinks.get(i).click();
// Navigating back to the previous page that stores link to service providers
driver.navigate().back();
}
26. What is the difference between driver.close() and driver.quit command?
close(): WebDriver’s close() method closes the web browser window that the user is currently working on or we can also say the window that is being currently accessed by the WebDriver. The command neither requires any parameter nor does is return any value.
quit(): Unlike close() method, quit() method closes down all the windows that the program has opened. Same as close() method, the command neither requires any parameter nor does is return any value.
27. How can we get a text of a web element?
Get command is used to retrieve the inner text of the specified web element. The command doesn’t require any parameter but returns a string value. It is also one of the extensively used commands for verification of messages, labels, errors etc displayed on the web pages.
Syntax:
String Text = driver.findElement(By.id(“Text”)).getText();
What is the difference between “/” and “//” in Xpath?
Single Slash “/” –
Single slash is used to create Xpath with absolute path i.e. the xpath would be created to start selection from the document node/start node.
Double Slash “//” –
Double slash is used to create Xpath with relative path i.e. the xpath would be created to start selection from anywhere within the document.
How to select value in a dropdown?
Value in the drop down can be selected using WebDriver’s Select class.
Syntax:
SelectByValue:
Select selectByValue = new Select(driver.findElement(By.id(“SelectID_One”)));
selectByValue.selectByValue(“greenvalue”);
selectByVisibleText:
Select selectByVisibleText = new Select (driver.findElement(By.id(“SelectID_Two”)));
selectByVisibleText.selectByVisibleText(“Lime”);
selectByIndex:
Select selectByIndex = new Select(driver.findElement(By.id(“SelectID_Three”)));
selectByIndex.selectByIndex(2);
28. What are the different types of navigation commands?
Following are the navigation commands:
navigate().back() – The above command requires no parameters and takes back the user to the previous webpage in the web browser’s history.
Sample code:
driver.navigate().back();
navigate().forward() –
This command lets the user to navigate to the next web page with reference to the browser’s history.
Sample code:
driver.navigate().forward();
navigate().refresh() –
This command lets the user to refresh the current web page there by reloading all the web elements.
Sample code:
driver.navigate().refresh();
navigate().to() –
This command lets the user to launch a new web browser window and navigate to the specified URL.
Sample code:
driver.navigate().to(“https://google.com”);
29. How to get title?
driver.getTitle();~To Print: System.out.println( driver.getTitle());
30. Can Selenium handle windows based pop up?
Selenium is an automation testing tool which supports only web application testing. Therefore, windows pop up cannot be handled using Selenium.
31. Can WebDriver test Mobile applications?
WebDriver cannot test Mobile applications. WebDriver is a web based testing tool, therefore applications on the mobile browsers can be tested.
32. How can we handle web based pop up?
WebDriver offers the users with a very efficient way to handle these pop ups using Alert interface. There are the four methods that we would be using along with the Alert interface.
• void dismiss() – The accept() method clicks on the “Cancel” button as soon as the pop up window appears.
• void accept() – The accept() method clicks on the “Ok” button as soon as the pop up window appears.
• String getText() – The getText() method returns the text displayed on the alert box.
• void sendKeys(String stringToSend) – The sendKeys() method enters the specified string pattern into the alert box.
Syntax:
// accepting javascript alert
Alert alert = driver.switchTo().alert();
alert.accept();
33. How can we handle windows based pop up?
Selenium is an automation testing tool which supports only web application testing, that means, it doesn’t support testing of windows based applications. However Selenium alone can’t help the situation but along with some third party intervention, this problem can be overcome. There are several third party tools available for handling window based pop ups along with the selenium like AutoIT, Robot class etc.
34. How to click on a hyper link using linkText?
driver.findElement(By.linkText(“Google”)).click();
The command finds the element using link text and then click on that element and thus the user would be re-directed to the corresponding page.
The above mentioned link can also be accessed by using the following command.
driver.findElement(By.partialLinkText(“Goo”)).click();
The above command find the element based on the substring of the link provided in the parenthesis and thus partialLinkText() finds the web element with the specified substring and then clicks on it.
35. How to assert title of the web page?
//verify the title of the web page
assertTrue(“The title of the window is incorrect.”,driver.getTitle().equals(“Title of the page”));
36. What is a framework?
Framework is a constructive blend of various guidelines, coding standards, concepts, processes, practices, project hierarchies, modularity, reporting mechanism, test data injections etc. to pillar automation testing.
37. How to handle frame in WebDriver?
An inline frame acronym as iframe is used to insert another document with in the current HTML document or simply a web page into a web page by enabling nesting.
Select iframe by id
driver.switchTo().frame(“ID of the frame“);
Locating iframe using tagName
driver.switchTo().frame(driver.findElements(By.tagName(“iframe”).get(0));
Locating iframe using index
frame(index)
driver.switchTo().frame(0);
frame(Name of Frame)
driver.switchTo().frame(“name of the frame”);
38. When do we use findElement() and findElements()?
findElement(): findElement() is used to find the first element in the current web page matching to the specified locator value. Take a note that only first matching element would be fetched.
Syntax:
WebElement element =
driver.findElements(By.xpath(“//div//ul//li”));
findElements():
findElements() is used to find all the elements in the current web page matching to the specified locator value. Take a note that all the matching elements would be fetched and stored in the list of WebElements.
Syntax:
List elementList =
driver.findElements(By.xpath(“//div//ul//li”));
39. What are the advantages of Automation framework?
Advantage of Test Automation framework
Reusability of code
Maximum coverage
Recovery scenario
Low cost maintenance
Minimal manual intervention
Easy Reporting
40. How can I read test data from excels?
Test data can efficiently be read from excel using JXL or POI API. See detailed tutorial here.
41. Explain how Selenium Grid works?
Selenium Grid sent the tests to the hub. These tests are redirected to Selenium Webdriver, which launch the browser and run the test. With entire test suite, it allows for running tests in parallel.
42. How to mouse hover on a web element using WebDriver?
WebDriver offers a wide range of interaction utilities that the user can exploit to automate mouse and keyboard events. Action Interface is one such utility which simulates the single user interactions.
Thus, In the following scenario, we have used Action Interface to mouse hover on a drop down which then opens a list of options.
Sample Code:
// Instantiating Action Interface
Actions actions=new Actions(driver);
// howering on the dropdown
actions.moveToElement(driver.findElement(By.id("id of the dropdown"))).perform();
// Clicking on one of the items in the list options
WebElement subLinkOption=driver.findElement(By.id("id of the sub link"));
subLinkOption.click();
43. Can captcha be automated?
No, captcha and bar code reader cannot be automated.
44. Explain what is assertion in Selenium and what are the types of assertion?
Assertion is used as a verification point. It verifies that the state of the application conforms to what is expected. The types of assertion are “assert” , “verify” and “waifFor”..
45. While using click command can you use screen coordinate?
To click on specific part of element, you would need to use clickAT command. ClickAt command accepts element locator and x, y co-ordinates as arguments-
clickAt (locator, cordString)
46. What are the advantages of Selenium?
It supports C#, PHP, Java, Perl, Phython
It supports different OS like Windows, Linux and Mac OS
It has got powerful methods to locate elements (Xpath, DOM , CSS)
It has highly developer community supported by Google
47. How to retrieve css properties of an element?
The values of the css properties can be retrieved using a get() method:
Syntax:
driver.findElement(By.id(“id“)).getCssValue(“name of css attribute”);
driver.findElement(By.id(“id“)).getCssValue(“font-size”);
How to capture screen shot in WebDriver?
import org.junit.After;
import org.junit.Before;
import org.junit.Test;
import java.io.File;
import java.io.IOException;
import org.apache.commons.io.FileUtils;
import org.openqa.selenium.OutputType;
import org.openqa.selenium.TakesScreenshot;
import org.openqa.selenium.WebDriver;
import org.openqa.selenium.firefox.FirefoxDriver;
public class CaptureScreenshot {
WebDriver driver;
@Before
public void setUp() throws Exception {
driver = new FirefoxDriver();
driver.get("https://google.com");
}
@After
public void tearDown() throws Exception {
driver.quit();
}
@Test
public void test() throws IOException {
// Code to capture the screenshot
File scrFile = ((TakesScreenshot)driver).getScreenshotAs(OutputType.FILE);
// Code to copy the screenshot in the desired location
FileUtils.copyFile(scrFile, new File("C:\\CaptureScreenshot\\google.jpg"));
}
}
48. What is the difference between type keys and type commands ?
TypeKeys() will trigger JavaScript event in most of the cases whereas .type() won’t. Type key populates the value attribute using JavaScript whereas .typekeys() emulates like actual user typing
49. What is the difference between setSpeed() and sleep() methods?
:Both will delay the speed of execution.
Thread.sleep () : It will stop the current (java) thread for the specified period of time. Its done only once
• It takes a single argument in integer format
Ex: thread.sleep(2000)- It will wait for 2 seconds
• It waits only once at the command given at sleep
SetSpeed () : For specific amount of time it will stop the execution for every selenium command.
• It takes a single argument in integer format
Ex: selenium.setSpeed(“2000”)- It will wait for 2 seconds
• Runs each command after setSpeed delay by the number of milliseconds mentioned in set Speed
This command is useful for demonstration purpose or if you are using a slow web application
What is same origin policy? How you can avoid same origin policy?
The “Same Origin Policy” is introduced for security reason, and it ensures that content of your site will never be accessible by a script from another site. As per the policy, any code loaded within the browser can only operate within that website’s domain.
To avoid “Same Origin Policy” proxy injection method is used, in proxy injection mode the Selenium Server acts as a client configured HTTP proxy , which sits between the browser and application under test and then masks the AUT under a fictional URL
50. What is Object Repository? How can we create Object Repository in Selenium?
Object Repository is a term used to refer to the collection of web elements belonging to Application Under Test (AUT) along with their locator values. Thus, whenever the element is required within the script, the locator value can be populated from the Object Repository. Object Repository is used to store locators in a centralized location instead of hard coding them within the scripts.
In Selenium, objects can be stored in an excel sheet which can be populated inside the script whenever required.
What is Selenium and what is composed of?
Selenium is a suite of tools for automated web testing. It is composed of
Selenium IDE (Integrated Development Environment) : It is a tool for recording and playing back. It is a firefox plugin
WebDriver and RC: It provide the APIs for a variety of languages like Java, .NET, PHP, etc. With most of the browsers Webdriver and RC works.
Grid: With the help of Grid you can distribute tests on multiple machines so that test can be run parallel which helps in cutting down the time required for running in browser test suites
51. What is Selenium 2.0 ?
Web testing tools Selenium RC and WebDriver are consolidated in single tool in Selenium 2.0
52. Mention what is the use of X-path?
X-Path is used to find the WebElement in web pages. It is also useful in identifying the dynamic elements.
53. List out the technical challenges with Selenium?
Technical challenges with Selenium are
Selenium supports only web based applications
It does not support the Bitmap comparison
For any reporting related capabilities have to depend on third party tools
No vendor support for tool compared to commercial tools like HP UFT
As there is no object repository concept in Selenium, maintainability of objects becomes difficult
53. List out the test types that are supported by Selenium?
For web based application testing selenium can be used
The test types can be supported are
a) Functional
b) Regression
For post release validation with continuous integration automation tool could be used
a) Jenkins
b) Hudson
c) Quick Build
d) CruiseCont
54. What is heightened privileges browsers?
The purpose of heightened privileges is similar to Proxy Injection, allows websites to do something that are not commonly permitted. The key difference is that the browsers are launced in a special mode called heightened privileges. By using these browser mode, Selenium core can open the AUT directly and also read/write its content without passing the whole AUT through the Selenium RC server
55. Why testers should opt for Selenium and not QTP?
Selenium is more popular than QTP as
Selenium is an open source whereas QTP is a commercial tool
Selenium is used specially for testing web based applications while QTP can be used for testing client server application also
Selenium supports Firefox, IE, Opera, Safari on operating systems like Windows, Mac, linux etc. however QTP is limited to Internet Explorer on Windows.
Selenium supports many programming languages like Ruby, Perl, Python whereas QTP supports only VB script
56. What are the four parameter you have to pass in Selenium?
Four parameters that you have to pass in Selenium are
Host
Port Number
Browser
URL
57. How you can use “submit” a form using Selenium ?
You can use “submit” method on element to submit form-
element.submit () ;
Alternatively you can use click method on the element which does form submission
Selenium IDE captures 3 options?
Command, Target, Value
58. Mention what is the difference between Implicit wait and Explicit wait?
Implicit Wait:Sets a timeout for all successive Web Element searches. For the specified amount of time it will try looking for element again and again before throwing a NoSuchElementException. It waits for elements to show up.
Explicit Wait : It is a one-timer, used for a particular search./p>
59. What is Object Repository ?
An object repository is an essential entity in any UI automations which allows a tester to store all object that will be used in the scripts in one or more centralized locations rather than scattered all over the test scripts.
60. Explain how to assert text of webpage using selenium 2.0 ?
WebElement el = driver.findElement(By.id(“ElementID”))
//get test from element and stored in text variable
String text = el.getText();
//assert text from expected
Assert.assertEquals(“Element Text”, text);
61. Can we use Selenium grid for performance testing?
Yes. But not as effectively as a dedicated performance testing tool like Loadrunner.
62. Can Selenium test an application on Android browser?
Selenium can handle Android browser.
63. Which browsers does WebDriver support?
The existing drivers are the ChromeDriver, InternetExplorerDriver, FirefoxDriver, OperaDriver and HtmlUnitDriver. For more information about each of these, including their relative strengths and weaknesses, please follow the links to the relevant pages. There is also support for mobile testing via the AndroidDriver, OperaMobileDriver and IPhoneDriver
64. What tests can selenium do?
Selenium could do functional, regression, and load of web based applications.p>
65. Which attribute you should consider throughout the script in frame for “if no frame Id as well as no frame name”?
You can use…..driver.findElements(By.xpath(“//iframe”))….
This will return list of frames.
You will ned to switch to each and every frame and search for locator which we want.
Then break the loop
66. How do I execute Javascript directly?
We believe that most of the time there is a requirement to execute Javascript there is a failing in the tool being used: it hasn’t emitted the correct events, has not interacted with a page correctly, or has failed to react when an XmlHttpRequest returns. We would rather fix WebDriver to work consistently and correctly than rely on testers working out which Javascript method to call.
We also realise that there will be times when this is a limitation. As a result, for those browsers that support it, you can execute Javascript by casting the WebDriver instance to a JavascriptExecutor. In Java, this looks like:
WebDriver driver; // Assigned elsewhere
JavascriptExecutor js = (JavascriptExecutor) driver;
js.executeScript(“return document.title”);
Other language bindings will follow a similar approach. Take a look at the UsingJavascript page for more information.
67. My XPath finds elements in one browser, but not in others. Why is this?
The short answer is that each supported browser handles XPath slightly differently, and you’re probably running into one of these differences. The long answer is on the XpathInWebDriver page..
68. Explain what is the difference between find elements () and find element () ?
find element ():
It finds the first element within the current page using the given “locating mechanism”. It returns a single WebElement
findElements () :
Using the given “locating mechanism” find all the elements within the current page. It returns a list of web elements.
Explain what are the JUnits annotation linked with Selenium?
The JUnits annotation linked with Selenium are
@Before public void method() –
It will perform the method () before each test, this method can prepare the test
@Test public void method() –
Annotations @Test identifies that this method is a test method environment
@After public void method()-
To execute a method before this annotation is used, test method must start with test@Before
69. What is Selenium IDE?
Selenium IDE is an integrated development environment for Selenium tests. It is implemented as a Firefox extension, and has a recording feature, which will keep account of user actions as they are performed and store them as a reusable script to play back. Selenium-IDE also offers full editing of test cases for more precision and control.
70. Why is my Javascript execution always returning null?
ou need to return from your javascript snippet to return a value, so:
js.executeScript(“document.title”);
will return null, but:
js.executeScript(“return document.title”);
will return the title of the document.
71. What is WebDriver?
WebDriver is a tool for writing automated tests of websites. It aims to mimic the behaviour of a real user, and as such interacts with the HTML of the application
72. Can Selenium test a application on iPhone’s Mobile Safari browser?
Selenium can handle Mobile Safari browser. There is experimental Selenium IPhone Driver for running tests on Mobile with Safari on the iPhone and iPad and iPod Touch.
73. What are the disadvantages of Selenium?
Disadvantages of Selenium:
Limitation in terms of browser support (It runs only in Mozilla).Scripts written using Selenium IDE can be used for other browsers only if it is used with Selenium RC or Selenium Core.
We can’t run recorded script if it is converted to Java, C#, Ruby etc.
Not allowed to write manual scripts like conditions and Loops for Data Driven Testing
There is no option to verify images
74. Explain what is Datadriven framework and Keyword driven?
Datadriven framework:
In this framework, the test data is separated and kept outside the Test Scripts, while test case logic resides in Test Scripts. Test data is read from the external files ( Excel Files) and are loaded into the variables inside the Test Script. Variables are used for both for input values and for verification values.
Keyworddriven framework:
The keyword driven frameworks requires the development of data tables and keywords, independent of the test automation. In a keyword driven test, the functionality of the application under test is documented in a table as well as step by step instructions for each test.
76. What are the features of TestNG and list some of the functionality in TestNG which makes it more effective?
TestNG is a testing framework based on JUnit and NUnit to simplify a broad range of testing needs, from unit testing to integration testing. And the functionality which makes it efficient testing framework are
Support for annotations
Support for data-driven testing
Flexible test configuration
Ability to re-execute failed test cases
77. Explain how you can login into any site if it’s showing any authentication popup for password and username?
Pass the username and password with url
Syntax- http://username:password@url
ex- http://creyate:[email protected]
78. What is the selenium’s recording language?
Selenium’s recording language is “HTML”.
79. What does it mean to be “developer focused”?
We believe that within a software application’s development team, the people who are best placed to build the tools that everyone else can use are the developers. Although it should be easy to use WebDriver directly, it should also be easy to use it as a building block for more sophisticated tools. Because of this, WebDriver has a small API that’s easy to explore by hitting the “autocomplete” button in your favorite IDE, and aims to work consistently no matter which browser implementation you use.
80. What are the steps to run automation using selenium?
The very basic steps are:
Record the test steps using selenium-IDE.
Modify the script according to the testing needs. Add validation points, Java Scripts, Time-out etc.
81. Why to use TestNG with Selenium RC ?
If you want full automation against different server and client platforms, You need a way to invoke the tests from a command line process, reports that tells you what happened and flexibility in how you create your test suites. TestNG gives that flexibility.
82. How you can capture server side log Selenium Server?
To capture server side log in Selenium Server, you can use command
java –jar .jar –log selenium.log
83. Other than the default port 4444 how you can run Selenium Server?
You can run Selenium server on java-jar selenium-server.jar-port other than its default port
84. How Selenium grid hub keeps in touch with RC slave machine?
At predefined time selenium grid hub keeps polling all RC slaves to make sure it is available for testing. The deciding parameter is called “remoteControlPollingIntervalSeconds” and is defined in “grid_configuration.yml”file
85. Using Selenium how can you handle network latency ?
To handle network latency you can use driver.manage.pageloadingtime for network latency
86. To enter values onto text boxes what is the command that can be used?
To enter values onto text boxes we can use command sendkeys()
87. How do you identify an object using selenium?
To identify an object using Selenium you can use
isElementPresent(String locator)
isElementPresent takes a locator as the argument and if found returns a Boolean
88. In Selenium what are Breakpoints and Startpoints?
Breakpoints: When you implement a breakpoint in your code, the execution will stop right there. This helps you to verify that your code is working as expected.
StartpointsStartpoint indicates the point from where the execution should begin. Startpoint can be used when you want to run the testscript from the middle of the code or a breakpoint.
89. Mention why to choose Python over Java in Selenium?
Few points that favor Python over Java to use with Selenium is,
Java programs tend to run slower compared to Python programs.
Java uses traditional braces to start and ends blocks, while Python uses indentation.
Java employs static typing, while Python is dynamically typed.
Python is simpler and more compact compared to Java.
90. Mention what are the challenges in Handling Ajax Call in Selenium Webdriver?
The challenges faced in Handling Ajax Call in Selenium Webdriver are
Using "pause" command for handling Ajax call is not completely reliable. Long pause time makes the test unacceptably slow and increases the testing time. Instead, "waitforcondition" will be more helpful in testing Ajax applications.
It is difficult to assess the risk associated with particular Ajax applications
Given full freedom to developers to modify Ajax application makes the testing process challenging
Creating automated test request may be difficult for testing tools as such AJAX application often use different encoding or serialization technique to submit POST data.
91. Mention what is IntelliJ?
Intellij is an IDE that helps you to write better and faster code for Selenium. Intellij can be used in the option to Java bean and Eclipse.
92. Mention in what ways you can customize TestNG report?
You can customize TestNG report in two ways,
Using ITestListener Interface
Using IReporter Interface
93. To generate pdf reports mention what Java API is required?
To generate pdf reports, you need Java API IText.
94. What is Listeners in Selenium WebDriver?
In Selenium WebDriver, Listeners "listen" to the event defined in the selenium script and behave accordingly. It allows customizing TestNG reports or logs. There are two main listeners i.e. WebDriver Listeners and TestNG Listeners.
95. What are the types of Listeners in TestNG?
The types of Listeners in TestNG are,
IAnnotationTransformer
IAnnotationTransformer2
IConfigurable
IConfigurationListener
IExecutionListener
IHookable
IInvokedMethodListener
IInvokedMethodListener2
IMethodInterceptor
IReporter
ISuiteListener
ITestListener
96. What is desired capability? How is it useful in terms of Selenium?
The desired capability is a series of key/value pairs that stores the browser properties like browser name, browser version, the path of the browser driver in the system, etc. to determine the behavior of the browser at run time.
For Selenium,
It can be used to configure the driver instance of Selenium WebDriver.
When you want to run the test cases on a different browser with different operating systems and versions.
97. For Database Testing in Selenium Webdriver what API is required?
For Database Testing in Selenium Webdriver, you need JDBC (Java Database Connectivity) API. It allows you to execute SQL statements.
98. Mention when to use AutoIT?
Selenium is designed to automate web-based applications on different browsers. But to handle window GUI and non-HTML popups in the application you need AutoIT.
99. Why do you need Session Handling while working with Selenium?
While working with Selenium, you need Session Handling. This is because, during test execution, the Selenium WebDriver has to interact with the browser all the time to execute given commands. At the time of execution, it is also possible that, before current execution completes, someone else starts execution of another script, in the same machine and in the same type of browser. So to avoid such situation you need Session Handling.
100. What are the advantages of Using Git Hub For Selenium?
The advantages of Using Git Hub for Selenium are
Multiple people when they work on the same project they can update project details and inform other team members simultaneously.
Jenkins can help you to build the project from the remote repository regularly. This helps you to keep track of failed builds.
SELENIUM Questions and Answers pdf Download
Read the full article
0 notes
Note
For the PD2 Ask meme -- 8, 13, 26, 27?
Hoh, shit. I didn’t think I’d get any requests from this. Okay, so…
Day 8 - Which heister is your least favorite?
Well, I have two at a tie. Houston and Sydney. I don’t like Houston, ‘cause he was forced on us Payday: The Heist fans back before Hoxton was brought back. I actually switched to playing Dallas after a while, until the Brit was reinstated. Emma can confirm, ‘cause she met me after I had already made the switch. And I don’t like Sydney, because I find her annoying. My mother is a junior high teacher, and some of her more irritating students are like Sydney. Very ‘lol, random’ and thinking that they’re hot shit. Plus, I’m disappointed with what OVERKILL did with her character. She could’ve been soooooo much more interesting, but they went with ‘preteen going into goth without knowing what it really is’ shtick, rather than anything with more substance. I dig her design, though. Always had a thing for mohawks and tattoos.
Day 13: Favorite personal incident that happened during a game?
Okay, so, I’m gonna preface this with admitting that I am a dick. A big one. I was playing Shadow Raid DW by myself and talking to Emma on Discord - this was before the Mayhem and One Down update - and she was like, “I’ll join you in a minute.” and I was all like, “Cool beans.” I go into the sewer when she drops in, ‘cause she’s Iron Manned out at max armor and all set for loud, the goober, and I tell her to put them on the zip line while I open the last of the crates. So, she’s moving the bags I have down there when I find three - count ‘em - THREE artifacts. And, hoh, I just start laughin’ in my head. Then the helicopter comes with ANOTHER artifact. I pile the bags up in a certain way so she won’t grab the lighter stuff, and get the last artifact when she starts complaining about how slow she’s moving with the artifacts. I switch outa bag of coke with the last artifact, so she’ll grab it. She picks it up and starts losing her mind. “FOUR FUCKING ARTIFACTS?!” Then I told her that I made it so she’d pick up and move all four in a row, and she goes into meltdown mode, and I was laughing so hard. She changed her Steam username to ‘4 FUCKING ARTIFACTS’ when we started on a different map and kept yelling at me for the rest of the day. She also kept seeing the number 4. It was beautiful~ I have evidence. Full picture.

Day 26: If you could suggest a new heister, what would they be like?
Well, that’s a tough one. ‘Cause we have the mother hen (Dallas), cool older bro (Chains), workaholic (Houston), asshole (Hoxton), nervous wreck (Wolf), Ted 2: the Tryhard Matrix Edition (Wick), corrupt cop gave up donuts for weights (Dragan), your annoyed and very drunk aunt is ruining your family barbecue (Bonnie), Flippy the army bear got lost in the ‘80s (Jacket), you see Ivan… (Sokol), insert Leprechaun in Hood joke here (Clover), dingoes ate my sense of humor (Sydney), Flightplan dubbed in Japanese (Jiro), Pilz-E meets Surrogates (Jimmy), Surfin’ USA (Bodhi), my self-references just remind you that my acting was better in these cooler things (Rust), saluda a mi pequeño amigo (Scarface), and I wear Hawaiian shirts so you won’t see all the margarita stains (Sangres).
That’s a lot of disparate personality traits, most of them one-note as you can tell from my sarcastic labeling. Kinda like how all the traits of the kids in the Breakfast Club would make one person if put together.
So… I dunno. Maybe someone who’s new to heisting? Like maybe a really quiet or even shy character, since everyone else is pretty loud and cocksure. There’s also those who get quieter the angrier they get, and they’re actually a lot more terrifying than the screamers, ya know? Or maybe someone who’s actually mentally unstable - I’m looking at you, Wolf. Jacket, you’re underutilized. And don’t make me fucking laugh, Sydney. Really, I just want a character that’s well written for fucking once. ‘Cause, yeah, the Crew can be rather funny and all that, and that’s great, but when OVERKILL gets down to characterization on the ‘Reasons Why They Are Here’ and ‘Why You Should Like Them’ parts, they fall flatter’n a pancake on the Waffle House’s kitchen floor and they still serve it to us.
Day 27: What’s your favorite in-game quote? Who says it?
*Heavily snorts some cocaine.* “Good job, yeah? Good job. Now we party, you fuckers!” - obviously Jimmy, that precious idiot~
Also, “Wollllfeeeee, you gotta help meeee!” yelled by Hoxton will always be my favorite Payday: The Heist quote. It’s adorable.
11 notes
·
View notes
Text
Yeerk Pool chatroom usernames
If you read Chapter 4 of “The Tree of Life” you’ll note there’s some interesting usernames in the Yeerk Pool chat log. I put a lot of thought into the usernames, so if you didn’t catch the references, here they are.
AkdorsWorstNightmare: Akdor 1154 was the Yeerk who led the uprising against the Andalites on the homeworld, kicking off the war.
SeerowsHeir: This Yeerk took their cue from Prince Seerow, who gave the Yeerks advanced technology.
TheSageintheWeeds: The mysterious mentor figure in the Yeerk epic of the same name. (Dæmorphing canon, not book canon.)
Janath: Janath 492 was a Yeerk elder who appeared in The Hork-Bajir Chronicles.
Madra: After the moon of the Yeerk homeworld.
Bandit: After the Andalite Bandits.
Visser3Gashad: From Visser, a gashad is an order from the Council of Thirteen to kill a Yeerk on sight.
FilshigTraitor: Filshig is a Yeerk swear word.
HackersVeleek: Veleek means pet in Yeerkish.
Grr’rnrHerder: In “A Place to Stand” I established that grr’rnr is what the Gedd call the weird headless beings we saw in the Time Matrix dimension version of the Yeerk homeworld in TAC. The Gedd keep them as herd animals. (This is also a bit of a Star Wars joke.)
GenerationFreedom: Yeerks measure time in terms of generations and cycles.
FightingEveryRane: “rane” is the Yeerkish word for the three-day feeding cycle. Stole this word from the excellent fic 167 Rane of Aniss.
Margoth: The main character in the Yeerk epic The Sage in the Weeds (Dæmorphing canon, not book canon)
VanarxHunter: The Vanarx or Yeerkbane is a predator of Yeerks.
19 notes
·
View notes
Text
cMATRIX - Chain Matrix Business Platform (Help and Support Tools)
Our Chain Matrix Business Platform is for Multi-levels Business, it’s perfect for Networking businesses that want to administrate their users and give the opportunity to each user to have a virtual wallet. You can also have a referral & 1:3 Pair Bonus system and each user can earn commissions. Every multi-level business needs to have more control over each user and the only way to be able to do this is with Our system which will allow you to Full Dynamic Controlable Networking Business Without any coding knowledge within five minutes….
User Features:
☵ Responsive User Interface.
☵ Total Deposit History.
☵ Total Earning History.
☵ Total Profit History.
☵ Activity Logs.
☵ Easy to Use System.
☵ Easy To contact.
☵ Easy Signup & Signin.
☵ Support Perfect Money.
☵ Support PayPal.
☵ Support Master Card (Stripe).
☵ Support Bitcoin.
☵ SEO Friendly URL.
☵ Secure User Dashboard.
☵ Referal System.
☵ Automated Add Fund System.
☵ Fund Add Report.
☵ Easy to Purchase Prize Bond.
☵ Referer Manager.
☵ Refer History.
☵ Refer User History.
☵ Manage Withdraw.
☵ Unique Templates.
☵ Email Notification.
☵ SMS Notification.
☵ And More…
Admin Features:
☵ Total USER Management.
☵ Block / Unblock Facility.
☵ Payment Method Management.
☵ Dynamic Admin Panel.
☵ 100% Secure Login.
☵ 1:3 Network Management.
☵ Referer List.
☵ Premium Member Management.
☵ Network Commision Management.
☵ WithDraw Method Management.
☵ Activity Logs Management.
☵ Total Withdraw History.
☵ General Setup.
☵ Testimonial Management.
☵ Menu Management.
☵ Slider Management.
☵ Web-Page & Content Management.
☵ Deposit History.
☵ Charge & Commision Management.
☵ Footer Management.
☵ Email Notification Management.
☵ SMS Notification Management.
☵ NewsLetter Management.
☵ Full Website SETUP.
☵ Manage Testimonial.
☵ Manage SITE Color.
☵ And More….....
Demo Access
Frontend: http://ift.tt/2EZEl4Q
Admin Access: http://ift.tt/2Eb8mxs
Admin Login: Username: admin || Password: admin
Support Facility:
Please send us your product presale query, after sales developer support request, customization project and any other queries to our dedicated support: [email protected]
from CodeCanyon new items http://ift.tt/2Eb7zwp
via IFTTT https://goo.gl/zxKHwc
0 notes
Photo




Can a “corporeal cyberfeminism” be couched in a yearning for an existence beyond mortal flesh? This question comes up again and again in the work of Gabrielle Drew, also known by her Instagram username babydreamgirl. Though she has roots as an artist with a dynamic in-person performance practice, Gabby lays out the circuitry for her overarching thematic matrix through her online presence on Instagram.
Spaces like Instagram blur the lines between the real and unreal through their ability to foster “feminist potentialities of disembodied and dislocated online interaction” (Brophy, 137). The caption for the first image above (top left) reads, “Trying on some new avatars”. Another (bottom left) says, “No ghost just the shell”- a reference to the popular anime Ghost in the Shell, which explores the nature of consciousness, identity, and human/machine connection through the eyes of a cyborg law enforcement officer. In many of her posts, Drew takes on multiple identities and (dis)embodiments as her feed expands and develops, making “real” the potentiality afforded to her through the social media space. Similarly, she begins to blur the line between her physical self and an imagined self by using apps like FaceTune to heavily alter and edit her features until she achieves what she calls a “haunted doll” look. Is the Uncanny Valley a feminist domain? Just as in the VNS Matrix Collective’s writings and theories, artists like Drew make room for the liminal and the abject to flourish and garner a wide audience through the power of the internet. The nonhuman becomes just as real, aspirational, and thought-provoking as anything else through its very presence as an (online) aesthetic project.
Furthermore, much of Drew’s work draws upon her trans womanhood (and all the potentialities she sees within that embodiment). In “Glitch the Cis-tem”, Andrea Abi-Karam writes, “I’m working towards glitching the gender mainframe until it freezes forever.” Drew’s work carries a similar examination/excavation of gender, though done in a way that seeks to usurp hegemonic gender relations in order to center the needs, feelings, and experiences of trans women and femmes. She interrogates trans women’s complicate roles in sex work with layered and edited video collages, glamorous and foreboding photos, and livestreams through the Instagram Live feature. These nuanced and multidisciplinary mediums hold a mirror to the livelihoods of other trans femmes, who must navigate their own (dis)embodiment in the face of erasure, sexual assault, and rampant violence.
Yet while tethered to very visceral (real?) experiences, there is also an infinite sense of place, a kind of neither-here-nor-there (corpo)reality, in Drew’s work. Her physical being is not limited by its own mortality or endangerment-through-embodiment. There is no space she doesn’t occupy, as noted by her tongue-in-cheek Instagram bio: NY-LA-MIAMI-Reykjavik (hacked at 230k).
The ways in which Brophy writes about the “intra-agency of body and medium” can be directly observed in the ways emerging transfeminine and gender non-conforming creatives utilize platforms like Instagram and Tumblr (138). Here, Drew and others in (and beyond) her creative circle “terraform” the online space to make “safer, softer home[s]” for themselves and each other. This creation of a “liberating territory of one’s own” is a (hyper)real and powerful cyberfeminist praxis (Daniels, 105).

- Blythe
@wst394cyberfeminisms
1 note
·
View note
Text
Confluence 6.13 Release Notes
We're excited to present Confluence 6.13.
Highlights
Run Confluence with AdoptOpenJDK 8
Supporting your GDPR efforts
PDF export improvements
Moving to the Cloud has never been easier
End of year Enterprise release roundup
Resolved issues
Get ready to upgrade
Get the latest version
Read the upgrade notes for important info about this release and see the full list of issues resolved.
Thanks for your feedback
More than 130 votes satisfied!
Run Confluence with AdoptOpenJDK 8
Oracle will stop providing public updates for Oracle JDK 8 in January. This means that only Oracle customers with a paid subscription or support contract will be eligible for updates.
In order to provide you with another option, we now support running Confluence 6.13 with AdoptOpenJDK 8. AdoptOpenJDK is free to use, and provides regular maintenance and security updates. Paid support for AdoptOpenJDK is also available from organisations such as IBM.
We'll continue to support running Confluence with Oracle JDK / JRE 8, and also plan to introduce support for Java 11 in a future release.
Supporting your GDPR efforts
General Data Protection Regulation (GDPR) compliance is front of mind for most organisations right now, and we know many of you are keen to adopt best practices, even if you aren't subject to the EU regulation.
In this release we've added the ability to permanently delete a user account and anonymise much of the personally identifiable information associated with it. There are some limitations, but we think this will be a useful tool for many organisations.
Delete accounts, wherever they're managed
Deleting a user account is very straight forward. If Confluence can write to the directory they're stored in, all you need to do is head to User Management, look up the user and click Delete.
If Confluence can't write to the directory, or if they're present in several directories, it's a two-step process. Remove them from all external directories, then head to the new Unsynced from Directory tab in User Management, and delete them from there.
When you delete an account, Confluence will:
remove their account, profile picture (avatar), and personal information
replace their full name and username with an anonymised alias
reindex any content they've contributed to or been mentioned on, so their name doesn't appear in search results.
What happens to people's content after they're deleted?
Deleting a user account does not remove any pages, comments, or other Confluence content. We also don't delete their personal space, as this may contain content owned by your organization.
This means that there will be some additional work to do after their account has been deleted to remove their personal space, and locate any references to the person in free text, or stored by third party apps or Synchrony in the database.
How deleted accounts appear to other people in your site
When an account is deleted, the full name is replaced with an alias like 'user-12345' in places including the dashboard, page history, @mentions, and macros. The username is replaced by a user key (a unique string of characters).
The alias stays the same throughout the site. This means that people can see that pages and comments were made by the same person, but not the identity of that person.
Delete vs disable an account
In most cases, when someone leaves your organisation or no longer needs access to Confluence, the existing process to disable a user is adequate. Their name remains attached to their content, and you can easily re-enable their account if they return.
PDF export improvements
If you regularly need to create PDFs of your content, you'll be pleased to know that we've resolved a bunch of PDF export bugs, and made several visual improvements to our PDFs. Some highlights:
Tables better match their Confluence counterparts, no longer filling the whole width, or forcing the columns to be equal width.
Headings have been refreshed, with more consistent sizing.
Ugly ducklings like the recently worked on, status, and tip macros now display more consistently.
Each Confluence page starts on a new PDF page, making your documents easier to read.
Long words and strings now wrap correctly.
We've kept the styling of the PDF plain and simple, giving you the perfect blank canvas to add your own style and flair, via the PDF stylesheet.
Moving to the Cloud has never been easier
The Cloud Migration Assistant for Confluence is now bundled with Confluence 6.13. If your team is currently considering a move to Atlassian Cloud, the Migration Assistant will make your day.
Migrate spaces at your own pace
Use the Migration Assistant to analyse the amount of content in your current site, and make plans to move spaces to your new cloud site.
It's up to you which spaces to migrate, and when. For example you may choose to migrate a few spaces relating to a particular project first, or migrate the spaces belonging to teams in a particular location, to limit disruption to these teams during their working hours.
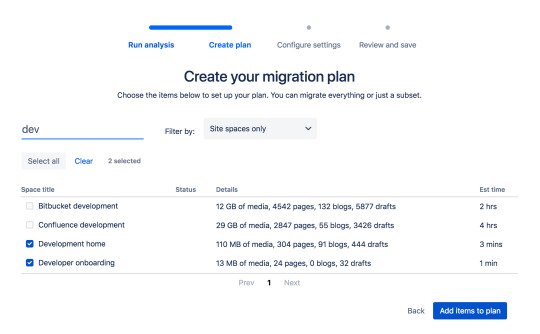
You're in control. You choose which spaces to migrate, when to run the plan, and can monitor the migration progress in real time. While one space's data is being uploaded, the next space's data is being exported from your database.
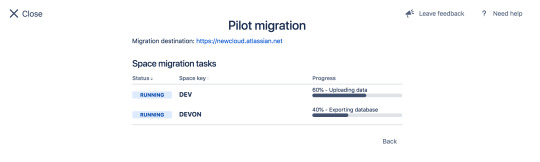
Securely transfer your data
We take your security seriously. There's no need to make changes to your firewall to allow incoming traffic. Just allow outgoing traffic from your Server site to our migrations.atlassian.com service and your new cloud site, and you'll be off and running.
Good to know
The Migration Assistant only transfers spaces. It doesn't migrate your users. We recommend populating your new cloud site with users first, so people are seamlessly reunited with their content.
Curious? Head to Cloud Migration for everything you need to decide, plan and migrate your Confluence Server site.
End of year Enterprise release roundup
It's been 12 months since Confluence 6.6 was designated our first Enterprise release so let's look at how it compares to standard releases this year.

We made a new 6.6.x bug fix version available about every 4 - 6 weeks, and backported many important stability and performance fixes from later releases.
Although most of you go for the latest and greatest Confluence version, many of our biggest customers chose the Enterprise release this year. In fact more Data Center customers chose to run Confluence 6.6 than any other version.
Organizations choose the Enterprise release for different reasons. For some, its the chance schedule regular minor version upgrades throughout the year, and for others it's the ability to react quickly to a serious issue or vulnerability, without the overhead of upgrading to a new feature version.
Confluence 6.13 will be our next Enterprise release line
We'll give 6.13 the Enterprise release stamp of approval early in the new year, so start planning your upgrade now. Keep an eye on this page for the announcement.
Whether you choose an Enterprise release or a standard release, always remember to grab the most recent bug fix version to make sure your Confluence is the best it can be.
See you next year!
Issues in Release
For full details of bugs fixed and suggestions resolved, head to Jira.
Suggestion: PDF export to cater for better heading formatting
Fixed: Log spams "mIMPORT Base URL is unknown" WARN messages when a mail notification is sent
Fixed: Edit in App does not work when Confluence is integrated with Crowd SSO
Fixed: Deadlock in Spring Framework 4.2.5 used by Confluence
Fixed: Valid drafts are being removed as a stale draft when we restart Collaborative Editing
Fixed: Loading the "Reorder Pages" space tool page for very large spaces as a non-admin user causes CPU spike
Fixed: Slow page loading with too many attachment versions
Fixed: Profile Avatars (Profile pictures) appears too large in PDF export
Fixed: PDF export of status macro and emoticons will not render background color.
Fixed: Each column has same width in a wide table regardless of the contents on exported PDF
Fixed: Extremely slow PDF export in Confluence 5.10.x while running behind a proxy
Fixed: Export PDF Unable to Export Special Icon to PDF
Fixed: Export to PDF, Centered Images are not included in .pdf file
Fixed: Word and PDF Export: Info, Note, Warning and Tip macros are not included in the exported document
Fixed: Default connection string for SQL Server uses database parameter instead of DatabaseName
Fixed: When profile language is in Dutch workbox notifications are undefined
Fixed: Table cut off on PDF Export
Fixed: Jira Macro is not rendered correctly when page is exported to PDF
Fixed: Broken tables in PDF export file on a page with layouts
Fixed: PDF / Word export with lettered nested list is converted to numbered nested list
Fixed: Export a page in PDF makes profile picture macro too large
Fixed: PDF export of status macro will not render background properly if context path is set.
Fixed: Export to PDF failed because of certain corrupted PNG
Fixed: PDF Export - Emoticons Are not Rendered When Placed inside Table Cells
Fixed: Long word in a table is resulting to right part of the table cutoff on PDF Export
Fixed: Failed export to PDF due to "BMP version 5 not implemented yet."
Fixed: Incomplete Link on the PDF Export in Instance with Particular URL
Fixed: Unable to do Space/Page PDF Export with Large Dimension Image Attached in a Page
Fixed: Cell background colors do not print out
Fixed: pdf export fails to retrieve image if the image on the page is a web image and url contains "download/attachments"
Get ready to upgrade
Before you upgrade, check out the Upgrade Notes for important changes in this release, then follow the usual upgrade instructions to upgrade your site.
Been a while since your last upgrade? Check out our upgrade matrix for a bird's-eye view of the most important changes since Confluence 6.0.
Don't forget to renew your software maintenance. Renew now
Credits
Our wonderful customers...
You play an important role in making Confluence better. Thanks to everyone who participated in interviews with us, made suggestions, voted, and reported bugs !
Source
0 notes
Text
Matrix Plan MLM Software | Matrix MLM Software | Matrix MLM
Multilevel Marketing business is growing every day, in that Matrix Plan MLM Software is the most important and profitable plan in the Multi Level Marketing business. This plan works on the principle of structural width and depth. This plan is very simple to understand and more safe to use. This Matrix Script Plan is also referred Forced matrix plan of Ladder Plan, where the user can grow his team within limited number of downline member and motivates to hire more members in the downline. The user need to login with the valid username and password for this matrix script. The user needs to register using sponsor id, nominee details, and personal details. The user can see the profile dashboard with visual statistics of purchase value and details, payout calculation, direct and indirect bonus amount, genealogy structure and more.
The main features of our Matrix MLM are membership plans, direct and indirect bonus, product management, reward management, company and member management, secure login process, powerful and user-friendly admin dashboard, purchase management, social sharing and many others. The customization of the matrix MLM plan is possible according to the client requirements and business needs. The benefits of our Matrix MLM Software are web based applications, secure code, accuracy and consistency, user-friendly interface, downline/upline report, payment statement, secure e-wallet, member management and more.
The compensation and bonus plan enhance the user and business more active. Our Matrix MLM Software has different types of attractive bonus model such as sponsor bonus, level bonus, matching bonus, position bonus and, forced matrix bonus. The main advantages of our matrix script are entire matrix MLM script is controlled by the admin and he has ability to change the contact us, about us, pages and payment details. We are the leading MLM software company and we are providing different types of readymade MLM Software to the clients with the best price and high features. We provide 1-year technical support, 6 month free updates of the source code and brand free website. After purchasing our Matrix MLM, the site will be live within 24 hours.
For more details about Matrix Plan MLM Software:
Call us to reach:
(IND) – (+91) 9841300660
(USA) – (+1) 858 633 0515
(UK) – (+44) 203 290 5530
To know more: https://www.phpscriptsmall.com/product/mlm-forced-matrix/
0 notes
Text
New Post has been published on Bestnewsmag
New Post has been published on https://bestnewsmag.com/heres-how-to-use-saved-searches-on-twitter-for-ios/
Here’s How to Use Saved Searches on Twitter for iOS
Whilst the Android model of Twitter’s cellular software allows users to save searches for clean get right of entry to in a while, the iOS version currently does now not. But, this doesn’t mean that iOS customers can’t use the stored searches function in the iOS Twitter app.
To apply this feature on iOS, you want to first store each search While the use of Twitter on the internet. This can allow you to get entry to the stored searches afterward inside the app. Our manual will display you ways this is finished.
Step 1: On Twitter’s internet site, search for the topic you’d want to shop through the hunting menu within the top proper corner of the display.
Step 2: Click the 3 vertical dots near the top proper nook of the hunt results page.
Step 3: Click on “save this search” to keep the search in your account.
After you’ve saved a seek to your account, you may get entry to it within the Twitter cellular app on iOS. Right here’s how.
Twitter 101: Basic Tips
If you own an enterprise, the chances are very good that you have profiles on at least some social media channels. Twitter may be very probably one of those. You can consider handling all your social media channels to be challenging but once you have got mounted a rhythm, it should get easier.
handling Twitter as easily as possible
The numerous social media channels have some differences which you want to study and use accurately. Fb works otherwise from LinkedIn, which matches differently from Twitter. Because of the one’s differences a few of the social media channels, it is very important so that it will learn how to navigate one of kind social media platforms and having a deep understanding of them in my view will make all the difference in your achievement.
The fact is that the more you apprehend about the social media channels, the extra effective your interactions along with your target audience contributors might be and the greater effectively you’ll be capable of doing your activity. After all, you need to interact other human beings in the most successful manner possible and you need the connection which you percentage with the ones humans to be enduring, stable, and together useful.
In case you are highly new to Twitter (or have sincerely no longer engaged on Twitter as an awful lot as you may have wanted to do), here are a few simple suggestions to help you to get the maximum out of it on your particular business.
Earlier than you can sincerely proceed, you’ll need to have a primary information of the phrases that Twitter makes use of most usually. So, right here is the Twitter one zero one word list.
Tweet: A tweet is a message on Twitter. Tweets are precise from other social media posts in that you have a problem with one hundred forty characters, which includes spaces. That still includes any snapshots and any hyperlinks. You’re probably most secure In case you restrict your text to among a hundred and fifteen and 120 characters (without areas) so you go away some characters for the pix and hyperlinks. If you cross over your man or woman limit, the textual content will be truncated, that you definitely do now not want to occur.
Retweet: If someone retweets a tweet, That means the tweet is shared with that individual’s followers, which gives your tweet much wider exposure than it had Earlier than. There are distinct approaches wherein someone can efficiently retweet. One is manual. If the person is going to do it that manner, she or he would kind “RT” Before the username and the content that is being retweeted will follow. For a long term, the handiest manner that someone should retweet was manual. But, there’s now a 2d way wherein a person can retweet, and this is by way of sending an internet retweet. In that case, the man or woman could hit the “retweet button” and the complete tweet could visit the recipient of the retweet. The “retweeter’s” name and avatar could additionally be included. between the two techniques of retweeting, the second is easier, much less time-consuming, and greater police.
Feed: The feed is the supply of the updates that you receive on Twitter. Your feed will tell you what content material is being up to date and it’s going to also will let you understand who’s retweeting the content.
Cope with: The Take care of is the name of your account (as an example, @johnsmith). You need to try to be as steady as possible in terms of your Cope with so that other human beings can engage with you as easily as viable.
Mention: A Mention is while you Point out some other character’s Handle in a social media put up. That creates the perception that the people whose Take care of are being referred to is influential is some manner. It reasons different people to pay attention.
Hashtag: This is a “#” followed by a keyword or keyphrase. As is always the case, you ought to be aware of the keywords/keyphrases you select for maximum effect.
Direct message: That is a personal message through Twitter to one in all your Twitter fans. it’s far vital to take into account that an instantaneous message can simplest be despatched to someone who’s following you on Twitter already.
Quote tweet: This is a manner to allow a Twitter consumer to include remarks within the tweet.
Now for the suggestions and hints
Use keywords and key terms wisely: key phrases paintings the identical manner on Twitter as they do on all other social media channels. The extra unique the keyword/keyphrase, the simpler it is going to be for the opposite individual to find you. After all, you need to connect to the other individual so that you can begin to develop a courting collectively.
Focus on the perfect influencers: Influencers are extraordinarily critical for the achievement of your enterprise. Your influencers come up with brought credibility and they create a lot to the desk for your benefit in addition to for the gain of your target market individuals. You need to Attention on resonance, reach, and relevance whilst thinking about which influencers are suitable for your business.
Make top use of hashtags: Hashtags are instrumental in getting different people to take note of you. They help you to solidify your dating with your target market.
Give credit score wherein credit is due: In case you examine something on Twitter that is worthy of being shared and being mentioned, you have to no longer hesitate to accomplish that. Anybody likes to be mentioned. Giving credit is going a very lengthy manner for little or no attempt.
Be prepared: Twitter is one social media channel that makes it clean with a view to automating (agenda) your tweets. If you could try this, you’ll have less strain than when you have to do the whole thing manually.
Speak approximately how important engagement is for Every person: when you have a desire to prevail with your social media interactions, engagement have to manifest. Engagement does such a lot of tremendous things, together with strengthening your credibility, boosting your enterprise’ reputation, and positioning you as an expert in your niche.
Entire your Twitter profile: This might be the, in reality, the first factor which you must do. Earlier than the opposite man or woman will do not forget to interact with you, he or she will most possibly take a look at out your profile. it is extraordinarily essential that you not simplest have an Entire profile however that you additionally make it interesting for different human beings to read. A dry profile may not reduce it.
Introduce a photo element: The reality is that many human beings are visible and; consequently, they reply higher to graphics than to words. It has been confirmed that tweets that include pix do higher than tweets with words by myself.
Preserve consistency: Your dedication and consistency are important for your fulfillment on Twitter. Your followers will stay up for seeing your tweets on the identical days and at the same time every week. Your frequency is much less crucial than your dedication to the regularity of your posts.
pick best over amount: if you have a huge range of fans however you haven’t any idea who most of these followers are, what price does the number hold? probably not a lot. it’s miles greater powerful to have a smaller number of pinnacle-pleasant connections.
Conclusion
Twitter can be an exceptionally powerful social media channel that will let you interact people in a way this is very effective for your business. it’s far vital so as to learn about what Twitter has to provide so that you can leverage it within the exceptional way possible to your commercial enterprise. Twitter can assist your enterprise in a number of approaches and build solid relationships is one of the main ways. you may need to embody Twitter so you can determine how to use it maximum efficiently to your precise commercial enterprise.
Michael Cohn is the founder and Leader Generation Officer (CTO) of CompuKol Communications. He has over 25 years of enjoying in IT and net technologies. Mr. Cohn spent a great quantity of time at a first-rate telecommunications enterprise, wherein his fundamental Awareness changed into on initiating and leading synergy efforts across all commercial enterprise gadgets via dramatically enhancing performance, online collaboration, and the business enterprise’s Intranet talents, which improved profits in business productiveness. He additionally reduced company journey and travel charges with the aid of introducing and imposing various collaboration technology.
His expertise consists of enterprise evaluation; project management; management of global go-matrix teams; structures engineering and evaluation, structure, prototyping, and integration; Technology evaluation and evaluation; systems improvement; performance evaluation; and control of off-shore improvement.
Mr. Cohn earned a Grasp’s diploma in mission management from George Washington College in Washington, DC; and a Grasp’s degree in computer technology and a Bachelor of technological know-how degree in electrical engineering from Fairleigh Dickinson College in Teaneck, NJ.
0 notes