#cyber security updates
Text
Russia's APT28 Exploited Windows Print Spooler Flaw to Deploy 'GooseEgg' Malware
Apr 23, 2024NewsroomNational Security Agency / Threat Intelligence
The Russia-linked nation-state threat actor tracked as APT28 weaponized a security flaw in the Microsoft Windows Print Spooler component to deliver a previously unknown custom malware called GooseEgg.
The post-compromise tool, which is said to have been used since at least June 2020 and possibly as early as April 2019,…

View On WordPress
#Computer security#cyber attacks#cyber news#cyber security news#cyber security news today#cyber security updates#cyber updates#data breach#hacker news#hacking news#how to hack#information security#Network security#ransomware malware#software vulnerability#the hacker news
0 notes
Text
International hackers have launched a dedicated website for releasing information obtained from recent breaches into sensitive Israeli databases, the Israeli newspaper Haaretz reported on Tuesday.
The site has already posted thousands of documents reportedly acquired by infiltrating systems associated with the Israeli Ministry of Defense, the National Insurance, the Ministry of Justice, and the Dimona nuclear research facility, according to Haaretz.
The leaks were reportedly attributed to a newly emerging hacker group dubbed ‘NetHunt3rs’, which demanded the release of 500 Palestinian prisoners in exchange for withholding the entirety of the disclosed information.
While the Israeli Ministry of Defense acknowledged the breaches, labeling the affected websites as “non-sensitive websites,” an investigation by Haaretz reportedly revealed that the leaked materials included sensitive data from administrative portals, such as employee identification information, defense tenders, and details on Israeli military technological systems, including armored vehicles and satellite photography systems.
According to the report, another group, named ‘Tafari HaNasser’, claimed responsibility for hacking into Israel’s National Insurance Institute. It said that it possesses personal data of 8 million Israeli citizens, including bank account details and residential addresses. Although the National Insurance denied any breach, the group circulated a video purportedly showcasing access to Israeli citizens’ personal information.
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#palestinian hostages#cyber security#direct action
584 notes
·
View notes
Text
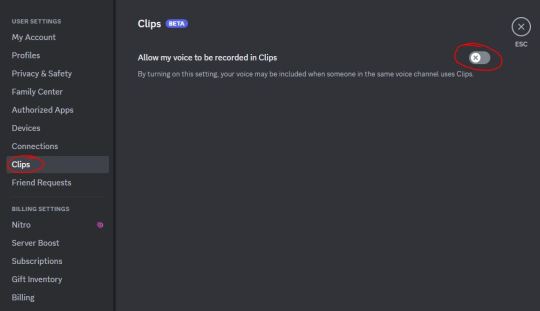
DISCORD CLIPS BULLSH*T
SO - I haven't seen anyone post about this yet, so THIS IS A PUBLIC WARNING.
A few weeks ago Discord had an unannounced feature added called Clips - which allows them to record and use aduio/voice clips, and it comes AUTOMATICALLY ENABLED!
HOW TO TURN THAT SH*T OFF!!!!!!
Under the settings section(the gear symbol), there is a new tab for Clips. Go there, and toggle off the button.
I have screenshots of where to find it on PC, I'll reblog soon with the Mobile App directions.

#Discord#Discord update#cyber security#safety#information#info#informative#helpful#useful#tips#technology
12 notes
·
View notes
Text
i feel like i never update y'all on my life
anyway i got a job at a library doing IT support hehehe
#sam rambles#listen i applied in january i just started#mONTHS I TELL YOU MONTHS#but they're paying for my certs i'm so happy#anyway i got it certified a couple of hours ago#by hours i mean yesterday#i'm working on other certs but i'm aiming to do more cyber security stuff#that's my update#and honestly one of the reasons why my fic count went up i was hella stressed LMAOO
4 notes
·
View notes
Text
Always hear for you


#so hot🔥🔥#twitter recovery#tumblr top 5#cyber security#hacked phone#account recovery#twitter#hacked instagram#pop team epic#hardware#cyberverse#cyberpunk#cyber updates#cyber news#cybernetics#cyber crime lawyers#instagram real followers#instagram bios#instagram#recovery#gmail#tiktok
3 notes
·
View notes
Text
One of my neighbors and I were just talking. He's a medical tech at a local, prestigious hospital. He didn't know what I do, so I told him, and he said, "I read that as early as 2027, no one who's working in the health care profession will be left."
On the one hand — hyperbole, of course. But on the other? Jesus. I really hope I've found something else to do with my time by then. I'm over working this gig and being expected to turn shit into gold.
#in other news#we had to do a cyber security update for our big client#and until we pass their compliance check no new work will come through#so basically i've had a month off#minutiae#text
2 notes
·
View notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Cybersecurity Report: Protecting DHS Employees from Scams Targeting Personal Devices
🔒 DHS Cybersecurity Alert! 🔒 Scammers targeting personal devices threaten national security. Our new report reveals these risks & offers robust solutions - MFA, security software, cybersecurity training & more. Safeguard yourself & critical operations!
Introduction
The digital age has ushered in an era of unprecedented connectivity and technological advancements, but it has also given rise to a new breed of threats that transcend traditional boundaries. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in both organizational systems and personal devices to gain unauthorized access, steal sensitive data, and…

View On WordPress
#access controls#antivirus#awareness campaigns#best practices#collaboration#cyber resilience#cybersecurity#cybersecurity training#data backup#data protection#DHS#firewall#government#impersonation#incident response#insider threats#malware#multi-factor authentication#national security#password management#personal device security#phishing#physical security#public outreach#risk assessment#scams#social engineering#software updates#threat intelligence#VPN
0 notes
Text
How should you secure your home wireless network for teleworking
How should you secure your home wireless network for teleworking #100daysofhomelab #HomeWiFiSecurity #TeleworkingTips #NetworkSecurity #VPNUse #WiFiPasswords #SecureConnections #CyberAttacksPrevention #RemoteWork #DeviceUpdates #MACAddressFiltering
Even though companies are starting to tighten down on who can work remotely and where hybrid work happens, it is still being leveraged like never before. Workers are at least working remotely part of the time, which means that sensitive information and data are subject to the security of the network the workers connect to. It often means the security of their home wireless network. Let’s consider…

View On WordPress
#Cyber Attacks Prevention#Device Updates#Home Wi-Fi Security#MAC Address Filtering#network security#remote work#Secure Connections#Teleworking Tips#VPN Use#Wi-Fi Passwords
0 notes
Text
youtube
0 notes
Text
'eXotic Visit' Spyware Campaign Targets Android Users in India and Pakistan
Apr 10, 2024NewsroomMobile Security / Spyware
An active Android malware campaign dubbed eXotic Visit has been primarily targeting users in South Asia, particularly those in India and Pakistan, with malware distributed via dedicated websites and Google Play Store.
Slovak cybersecurity firm said the activity, ongoing since November 2021, is not linked to any known threat actor or group. It’s…

View On WordPress
#Computer security#cyber attacks#cyber news#cyber security news#cyber security news today#cyber security updates#cyber updates#data breach#hacker news#hacking news#how to hack#information security#Network security#ransomware malware#software vulnerability#the hacker news
0 notes
Text

The Citizen Lab says it informed officials that suspected Pegasus spyware was discovered in 2020 and 2021, with the Downing Street incident linked to operators in the UAE.
Pegasus is sold by NSO Group to governments to carry out surveillance through infecting phones with malicious software.
The Israeli-based company has denied the allegations, saying they are false and could not have taken place.
The Citizen Lab, which tracks electronic surveillance, said in 2020 and 2021 it notified the UK government that networks belonging to both 10 Downing Street and the Foreign and Commonwealth Office were suspected to have been infected using Pegasus spyware.
Pegasus allows governments to take control of people's phones, extract data and carry out surveillance.
NSO Group has always defended its use, saying it is only sold to selected governments for legitimate law enforcement and intelligence purposes, such as against criminals or terrorists.
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#great britain#cyber security
293 notes
·
View notes
Text
DCxDP Fanfic idea: Wrong Number
Bruce prides himself in keeping all of his networks secured. If he didn't make it himself, he had the funds and connections to get him the best working on his systems.
He had backup plans in case the systems were ever hacked, of course, but he had yet to encounter a cyber attack that wasn't beaten away by his firewalls or his team.
Babs and Tim were far more feral when booting out unwanted guests. The level of protection was also transferred to his other systems that weren't Batman-related, just to make sure the connection between Bruce and Batman was never made.
That's why he never really checks his personal phone's caller ID, not the one he gave out as Brucie Wayne, but the one Bruce used for his real life without any masks- civilian or vigilante. The only ones who had the number- and the access- were his children and Alfred.
Not even the Justice League- those who were aware of his identity- knew of this number.
Bruce is in the middle of typing up a report for the next Wayne Board meeting when his personal phone rings. He figures it's Dick giving him a call to update him on his drive home or maybe Jason, as his son was planning on going to college.
"Go for Papa Bruce," He says, knowing his kids hate his phone greeting and doing it deliberately to spite them.
There is a long pause where he can't help but smirk thinking his child is either rolling their eyes or cringing too hard to properly speak. Eventually, a voice cracks over the speaker.
"Hello. I'm selling cookies to raise money for my own star. Would like to buy a box from me?" says a boy, not one he has taken in. The voice is young maybe not even double digits yet. Bruce is alarmed.
"Who are you?! How did you get this number?" He demands, yanking his phone to his face and seeing, with a chill, a phone number out of state.
His system had been compromised. By a child. By accident.
"My name is Danny!" The boy chirps. "I sell cookies. Like the Girl Scouts, but I'm a boy, and I don't scout."
"That's rather fantastic, lad. What kind of cookies are you selling?" Bruce asks to keep the boy on the line while sending an email blast to the others. It's a string of numbers that are code for compromise so they all know to close any communication channel until it's safe to get back on.
"Chocolate chip. Mint Slim. Oatmeal and peanut butter. I made them myself!"
Right. Bruce hooks up his phone, tracing the call. The signal bounces off the call, swinging up to a salute and falling back down to earth. In seconds he has the boy's location. It pings in a small town right outside of Star City.
He sends Barry a private message. His friend is already on the way to the location. He'll get the boy in a few seconds.
"How much for a box of chocolate chips? Those are my favorite." Bruce tells the boy, voice whimsical as his Brucie persona demands.
In an unsure tone, the boy pauses, then whispers, "I don't know. No one ever let me get this far."
"How about twenty for a box of dozen? I'll buy five boxes for each of my kids that live at him," Bruce tells him, and the boy gasps.
"That could buy me one whole night in a hotel!"
Bruce's insides freeze. What did he mean-
"Hey! No! Let go!" Danny suddenly screams. Bruce's heart launches- he hates it when kids get hurt, especially those that sound like Danny- until Barry's voice comes over the speaker.
"I got him, Mr. Wayne. Thank you for alerting the Justice League Hotline." That's code for This is not a threat to you Batman and Bruce allows himself to relax just a little.
"Narc!" The boy shouts, outraged, before the call drops. Barry is likely taking over the situation, which means Bruce can leave it in his capable hands.
After reassuring his kids that he is fine and that they are all safe, he suits up and meets the Flash in the Watch Tower. There, he learns that Danny is only seven years old and has been living on the streets for a while.
The boy had been surviving by baking some cookies to sell on the side of the street- where did he bake them? The boy would not say- until he got the bright idea to try to sell through phone calls like he had seen on TV.
He punched in random numbers at the community center phone and gave his pitch about a star, thinking people would be more willing to buy from him if he had an excellent reason.
Barry had left him with CPS, but he looked devastated about that. It turned out that Danny was a meta and had likely been kicked out of his home once it was found out based on what he said of his parents.
Bruce felt he should assure Barry that Danny was fine and look into his placement to help settle his more sensitive teammate's nerves.
He was unhappy that Danny was not in a good placement; there were far too many reports from a concerned neighbor to make him think it was a safe place. Given the fact that placement had a lot of meta kids that "fell through the cracks," Bruce worried he had just stumbled across a trafficking ring.
He would sick Barry and Jason on them. Just to ensure they wouldn't see the light of day again.
Still, that did not fix his mistake with Danny, the little cookie seller.
Bruce hacked into the system to move Danny. He thought about where he would move the young child but ultimately had him in Wayne Manor.
Just until he could confirm that he would be safe. He certainly didn't think about the adorable little boy who called him with his heart in his hand and got sent to a terrible place for three weeks because of Bruce.
Danny arrived at Wayne Manor with a happy little bounce and a chipper outlook on life than Bruce was expecting. "If it isn't Mr. Narc!"
God, he going to adopt the boy, isn't he?
(Danny has been thrown into a different universe, aged down to a child. He survived by overshadowing people into letting him spend the night baking cookies.
He was thrown into a somewhat typical home, but the nosy neighbor down the street took far too much notice of his overshadowing, and now he was being moved again.
Maybe he can terrorize Mr. Narc now instead? )
#dcxdpdabbles#dc x dp crossover#Danny de-age#Dimension travel#Crack#Basically He overshaowed people and everyone lost their minds about it#Barry will fight Bruce for Danny#Danny will make it his life goal to be Bruce's life hell
2K notes
·
View notes
Video
youtube
Cybersecurity Threats Mailchimp discloses breach and How to be SafeCybersecurity Threats: MailChimp Discloses New Data Breach Read out blog at; https://ecomhardy.com/cybersecurity-threats-mailchimp-discloses-new-data-breach-in-2021/ It 19s no secret that cyber threats are becoming increasingly prevalent in today 19s digital age. In fact, a recent study conducted by NortonLifeLock found that a staggering 4 in 5 small business owners have experienced a cyber attack. One company that has recently fallen victim to these threats is MailChimp, a leading email marketing platform. On January 18th, 2023, MailChimp announced that they had suffered a data breach after several of their employees fell victim to a phishing attack. The attackers were able to gain access to sensitive information, including customer data and account information. While the company has stated that the majority of affected accounts have been secured, it 19s important for all MailChimp users to take steps to protect their information. To start, users should update their passwords and enable two-factor authentication (2FA). Additionally, users should be on the lookout for suspicious activity on their accounts, such as unwanted email sends or unauthorized changes to their account settings. It 19s also worth noting that this is not the first time MailChimp has suffered a data breach. In 2017, the company experienced a similar incident in which a hacker was able to gain access to customer data. This highlights the importance of staying vigilant and taking proactive steps to protect your information, regardless of the company or platform in question. In addition to protecting your own information, it 19s important to stay informed about the latest cybersecurity threats and best practices for staying safe online. This includes staying up to date on software and security updates, avoiding suspicious emails and links, and being cautious when sharing personal information online. Conclusion The MailChimp data breach serves as a reminder that cyber threats are a very real and pressing issue. It 19s essential for individuals and businesses alike to take steps to protect their information and stay informed about the latest threats and best practices for staying safe online. By taking these precautions, we can work towards a safer and more secure digital world.
#woocommerce#ecomhardy#mailchimp#data breach#cybersecurity#phishing attack#information security#email marketing platform#customer data#account information#two-factor authentication#nortonlifelock#protecting personal information online#latest cybersecurity threats#importance of two-factor authentication#small business cyber attacks#keeping software and security updates current#avoiding suspicious emails and links#cyber security
0 notes
Text
Follow to read tips, updates related cybersecurity, data loss prevention, risk management and everything related cybersecurity awareness.
1 note
·
View note
Text
Eset cyber security pro 6.x with updated modules

#Eset cyber security pro 6.x with updated modules for mac os#
#Eset cyber security pro 6.x with updated modules for mac#
Your product will update automatically after installation and activation. How do I update ESET Cyber Security/ESET Cyber Security Pro?.See What operating systems are ESET products compatible with? (Home Users). You can select your preferred language from the drop-down menu of available languages on the download page. The latest version is available in English, French, French-Canadian, Spanish and several others.
#Eset cyber security pro 6.x with updated modules for mac#
What languages are available for Mac Home Edition?.The latest version of ESET Cyber Security: When was ESET Cyber Security/ESET Cyber Security Pro released?.Click here to learn more about Mac security products from ESET.
#Eset cyber security pro 6.x with updated modules for mac os#
ESET Endpoint Antivirus for OS X and ESET Endpoint Security OS X have replaced ESET NOD32 Antivirus 4 Business Edition for Mac OS X.
Is there a Mac ESET product for business users?.
For more information, visit the following ESET Threat Blog article: Straight facts about Mac malware, threats and responses Home users and business users that share files and/or email between Mac and other platforms such as Windows or Linux can potentially spread threats without knowing or being affected themselves. Why do I need an antivirus product for it?
Mac OS X is a very secure operating system.
The new products bring improvements to existing feature sets along with new functionality, improved user experience and redesigned interface.
What's new in ESET Cyber Security/ESET Cyber Security Pro ?.
Advanced heuristic technology recognizes and removes new threats. ESET Cyber Security/ESET Cyber Security Pro protects you and your network from emerging and cross-platform (such as, Windows, Linux, Mac) threats without system slowdowns. It brings the protection of ESET NOD32 Antivirus that Microsoft Windows users have trusted in and depended on for 25 years.
What is ESET Cyber Security/ESET Cyber Security Pro?ĮSET Cyber Security/ESET Cyber Security Pro are security solutions for Mac home users.
You can also contact your local distributor or reseller to purchase the product. The products are available for purchase at.
Where can I purchase and download ESET Cyber Security/ESET Cyber Security Pro?.
Free 30-day Trial of ESET Cyber Security.
Free 30-day Trial of ESET Cyber Security Pro.
Visit the Trial Download page for more information and to download the product: Yes, you can try ESET Cyber Security/ESET Cyber Security Pro free for 30 days.
Is there a trial version of ESET Cyber Security/ESET Cyber Security Pro?.
Download, install and activate ESET Cyber Security or ESET Cyber Security Pro.
How do I install ESET Cyber Security/ESET Cyber Security Pro?įor step-by-step installation instructions, see one of the following ESET Knowledgebase articles:.

0 notes