#cyber updates
Text


#cyber y2k#cyberspace#cyber updates#futurist fashion#futuristic#fashion#contemprary#cybergoth#neo y2k#y2k#coquette#girl blogger#alternative style#nail art
128 notes
·
View notes
Text

In 2076 there a lake on city robots and cats cyber fish's
#artists on tumblr#art#blender#3d artwork#3drender#3d model#design#meow duo#cyberpunk#cyber updates#retro rides#retro#synthv
27 notes
·
View notes
Text
Cyber hit 13k!! never thought I’d see the day. I say cyber hit rather than i wrote because sometimes the narrative takes the wheel and I contribute very little from my own brain cells
2 notes
·
View notes
Text
Always hear for you


#so hot🔥🔥#twitter recovery#tumblr top 5#cyber security#hacked phone#account recovery#twitter#hacked instagram#pop team epic#hardware#cyberverse#cyberpunk#cyber updates#cyber news#cybernetics#cyber crime lawyers#instagram real followers#instagram bios#instagram#recovery#gmail#tiktok
3 notes
·
View notes
Text
Those willing to make some cash this week should Tap in. Cloned physical ATM cards💳 high & low balance available✅

#cashout#credit card#united kingdom#usa#make money fast#cyber updates#europe#finance#france#make money from home#wells fargo online transfers#tumlr#black and white#hustle#cashapp#computer#online#18+ only
2 notes
·
View notes
Photo

Investing in security software is critical to ensure your users' safety—five reasons why endpoint management software is worth considering for your business.
1 note
·
View note
Text

Be yourself because there's no one better.
#beauty#parenting#positivity#video games#health & fitness#cybersecurity#cyber updates#crytonews#crazy
2 notes
·
View notes
Text
I want to dress cyber y2k But i dont know where to find clohtes!
2 notes
·
View notes
Text
Being scammed/ hacked as a cybersecurity professional be embarrassing af💀💀
3 notes
·
View notes
Text
'eXotic Visit' Spyware Campaign Targets Android Users in India and Pakistan
Apr 10, 2024NewsroomMobile Security / Spyware
An active Android malware campaign dubbed eXotic Visit has been primarily targeting users in South Asia, particularly those in India and Pakistan, with malware distributed via dedicated websites and Google Play Store.
Slovak cybersecurity firm said the activity, ongoing since November 2021, is not linked to any known threat actor or group. It’s…

View On WordPress
#Computer security#cyber attacks#cyber news#cyber security news#cyber security news today#cyber security updates#cyber updates#data breach#hacker news#hacking news#how to hack#information security#Network security#ransomware malware#software vulnerability#the hacker news
0 notes
Text
Follow to read tips, updates related cybersecurity, data loss prevention, risk management and everything related cybersecurity awareness.
1 note
·
View note
Text
My last album cover with tony brich
C Y B O R G


#art#artists on tumblr#3d artwork#3drender#blender#design#gaming#3d model#youtube#cyberpunk#cyber updates#cyborg#music#ed meals#edm
4 notes
·
View notes
Text
Different types of cybersecurity:here is the Comprehensive list

Cyber security is important for everyone in the online world. It’s not just for businesses or government entities, but for regular people too. We all have a responsibility to protect ourselves and our data from online threats.
The good news is, there are many different types of cyber security that we can use to keep ourselves safe. In this article, we will explore the different types of cyber security and how they can be used to protect us from harm.
So, whether you’re looking to protect your data or your business’s online presence, read on to learn more about the different types of cyber security and how they can help you stay safe online.
Network Security
Network security is the practice of protecting networked systems and data from unauthorized access or theft. It includes both hardware and software technologies, as well as policies and procedures implemented by an organization to protect its assets.
There are many different types of cyber security threats, including viruses, worms, Trojan horses, spyware, rootkits, botnets, phishing attacks, and denial-of-service attacks. Some of these threats are aimed at specific systems or networks, while others are designed to exploit vulnerabilities in applications or operating systems.
To effectively protect against all types of cyber security threats, organizations need to implement a comprehensive security program that includes multiple layers of defense. These defense layers can include firewalls, intrusion detection and prevention systems, encryption technologies, physical security measures, and user education and training.
Cloud Security
As more and more businesses move to the cloud, it's important to consider the security of your data. With the right security measures in place, you can rest assured that your data is safe and secure.
There are a few different types of cloud security, each with its benefits. Here are some of the most popular:
1. Identity and Access Management (IAM)
IAM is a type of security that controls who has access to your data. With IAM, you can set up different users with different levels of access. This way, you can ensure that only authorized users can access sensitive data.
2. Data Encryption
Data encryption is another way to keep your data safe. When data is encrypted, it can only be decrypted by someone with the proper key. This helps to protect your data if it falls into the wrong hands.
3. Firewalls
Firewalls are a type of security that acts as a barrier between your network and the internet. They help to block unauthorized traffic and protect your network from attacks.
4. Intrusion Detection and Prevention Systems (IDPS)
IDPS are designed to detect and prevent attacks on your network. They work by monitoring traffic and looking for suspicious activity. If an attack is detected, they can take action to prevent it from happening or minimize the damage caused.
Endpoint Security
Endpoint security is a type of cyber security that focuses on protecting the devices that are used to access corporate networks and data. These devices include laptops, desktops, smartphones, and tablets. Endpoint security solutions typically include a combination of software and hardware that work together to protect the device from malware, phishing attacks, and other threats.
The first step in implementing an endpoint security solution is to deploy antivirus and antispyware software on all of the devices that will be accessing the network. This software will help to protect the devices from malware that could be used to gain access to sensitive data or disrupt operations. The next step is to deploy a firewall on each device. This will help to block unauthorized access to the device and the corporate network. Finally, it is important to create policies and procedures for employees that outline how they should use their devices when accessing corporate data. This will help to prevent accidental data leaks or malicious attacks.
Mobile Security
It's no secret that our world is becoming increasingly mobile. We use our smartphones and tablets for everything from keeping in touch with friends and family to managing our finances and shopping online. With so much of our lives taking place on mobile devices, it's important to make sure they're secure.
Mobile security is the practice of protecting your mobile device from malicious software and attacks. This can be done in several ways, including installing security apps, using a secure VPN, and being careful about what you download and click on.
Security apps can help protect your device from malware and viruses. A VPN (virtual private network) encrypts your traffic, making it harder for hackers to intercept your data. And be cautious about what you download and click on can help prevent you from accidentally downloading malware or visiting malicious websites.
Making sure your mobile device is secure is important to protect your personal information and keep your online activities safe. By taking some simple steps, you can help ensure that your mobile device is as secure as possible.
IoT Security
The internet of things has brought us many conveniences, but it has also introduced a new level of vulnerability. As more and more devices are connected to the internet, the potential for cyberattacks increases. IoT security is a relatively new field that is constantly evolving, but there are a few key considerations that can help keep your devices safe.
One of the most important things to do when securing your IoT devices is to keep them up to date with the latest security patches. Manufacturers are constantly improving the security of their products, so it’s important to stay current. Many IoT devices also have web interfaces that can be used to manage them. Be sure to choose strong passwords and enable two-factor authentication if available.
Another consideration is the physical security of your devices. If an attacker can get physical access to a device, they may be able to bypass any software security measures you have in place. Keep devices in secure locations and consider using tamper-resistant hardware if possible.
IoT security is an ongoing process, but taking these steps can help you create a more secure environment for your connected devices.
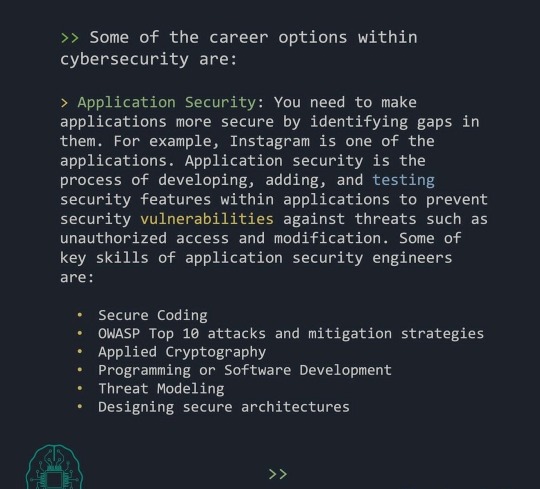
Application Security
There are many different types of cyber security, but one of the most important is application security. This type of security protects applications from attacks that could exploit vulnerabilities and allow unauthorized access to data. Application security includes features like authentication and authorization controls, data encryption, and intrusion detection and prevention.
Organizations must take steps to ensure that their applications are secure, as this is critical to protecting their data and assets. They can do this by implementing strong security measures during the development process, testing applications for vulnerabilities before they are deployed, and continuously monitoring them for signs of attack.
Zero Trust
Zero trust is a security model that requires organizations to verify the identity of users and devices before granting them access to network resources. This verification process is typically done through authentication and authorization mechanisms, such as two-factor authentication or multi-factor authentication.
Organizations that implement a zero trust security model are less likely to fall victim to data breaches and other cyber attacks because they don't rely on a single perimeter for security. Instead, they use microperimeters around individual users and devices to control access to sensitive data. This approach makes it more difficult for attackers to gain unauthorized access to sensitive information.
To implement a zero trust security model, organizations need to have strong identity management and authentication capabilities in place. They also need to be able to quickly detect and respond to security incidents.
Conclusion
There are many different types of cyber security, each with its strengths and weaknesses. No single type of security is perfect, but by understanding the different options available, you can choose the best strategy for protecting your data and keeping your business safe. Thanks for reading and be sure to stay tuned for more articles on cyber security in the future.
Note: If you aim to make a thriving career in the tech domain, Skillslash can help achieve that goal with its exclusive courses:
Advanced Data Science Course
Business Analytics program
Blockchain program
System design course (specifically IT domain)
Full Stack Developer program (specifically IT domain)
You can check out the above links individually or choose the one which best suits your career path and later get in touch with the Skillslash team for better communication.
1 note
·
View note
Text
How to protect a business from Cyber Attacks?
A business is only as strong as its weakest link. If you have a weak spot in your system, it’s only a matter of time before you get hacked. The best way to protect your business from cyber-attacks is to ensure that the people working for it are trained to protect themselves and their data from these attacks. In order to do this effectively, here are some things you should do:
Regularly back up your data.
A regular backup of your data is essential to protect against cyber attacks, as well as any natural disasters. You should make sure that you have regular backups of your data and that they're stored securely in a different location from the original data. You should also test them regularly to ensure that they work properly if needed.
Always update the software.
Finally, it's important that you keep all of your software up to date. Updates are often released on a regular basis to fix security problems and other bugs. If you're not updating regularly, you're leaving yourself vulnerable to attack.
To update software:
Update all software regularly using the methods provided by their creators (e.g., Apple Software Update, Windows Update).
Check for updates manually if the automatic download doesn't work properly or is unavailable for some reason (e.g., your computer is offline).
Train users on how to protect themselves from cyber-attacks.
As an HR professional, you have the opportunity to provide your employees with the training they need to be able to prevent cyberattacks. The most important factor in this regard is that you train your employees about what types of phishing attacks exist and how they can be detected.
You should also train them on how to avoid malware, viruses and other forms of online fraud by providing educational materials for them to read or watch online videos about these topics.
If possible, hold regular security briefings where all employees can come together and hear from experts on how best to protect themselves from cyber attacks as well as share information about emerging threats or vulnerabilities in their systems which may leave them open for attack by hackers
Securely store and dispose of confidential data.
The most important thing to do is to not keep sensitive or confidential data on a computer or mobile device. This includes not saving any information, like email messages or attachments, that contains personal information such as social security numbers or credit card numbers in the cloud.
Data stored on hard drives can be easily stolen if someone breaks into your business premises or steals your laptop from your home office.
Don’t also keep sensitive information on servers where employees have access to it as well as hackers who can gain access through malware installed on employee machines that allows them direct access to network drives (if they’re connected).
The same applies to e-mail servers, which often contain passwords and other sensitive information about customers and suppliers that could be used maliciously by cyber criminals if they were compromised by an attack like ransomware (which encrypts files until paid a ransom).
Finally, don’t use cloud storage services that don't have good security measures because if there's ever an infiltration into their data centres, then all your stored data will be at risk too!
Always have 2-factor authentication enabled.
2-Factor Authentication (2FA) is a security measure that requires users to provide two pieces of information - something they know, like a password or PIN, and something they have, such as a phone with an authentication app. By requiring both factors, you can be sure that you’re authenticating the right person.
While 2FA isn’t perfect — if someone steals your phone or tablet, they could access your accounts — it represents an improvement over basic single-factor authentication (SSO). If you use SSO alone and lose the device storing your login credentials, there will be no way to access them again without resetting them on every account individually.
With 2FA enabled on each account at all times, losing your device won't prevent access as long as you have another form of authentication in place (like SMS/phone call or email).
It's important for businesses to ensure that at least one of their employees has two-step verification enabled so there's always some level of protection against attacks designed solely around stealing passwords from unsuspecting users' social media accounts."
Keep employees up-to-date on security policies.
Employees should be kept up-to-date on security policies.
Make sure that employees are aware of the latest security threats by updating them regularly.
Keep your employees informed about the nature of cyber attacks and their effects on a business’s reputation, finances and operations.
You can do a lot to make sure your business is protected from cyber attacks
There are a number of things you can do to reduce the risk of a cyber attack. The first step is to make sure that your technology is up-to-date and protected by the latest security updates. If you're using an old operating system, it may be vulnerable to known exploits.
Another important step is to have a process in place for dealing with an incident when it does occur. This should include steps such as notifying your customers and what information about them needs to be released publicly, as well as how you handle any lost revenue or reputational damage caused by the event.
Finally, it's important that you build resilience into your business so that if there is a major breach (or several smaller ones), your organization can recover quickly without losing too much ground in its market share or customer base.
Hire a Cyber Security or Ethical Hacking Expert
One of the best ways to protect your organization is to hire a cybersecurity expert. This person can help you create a plan for mitigating and responding to incidents and monitor your network for any signs of compromise.
Moreover, this person can give you a better understanding of how to manage your system's security, including the use of firewalls, anti-virus software, and other tools. In addition to this type of professional advice, you can also hire an ethical hacker. This person will try to break into your system in order to find vulnerabilities that could be exploited by cybercriminals.
Additionally, it's important for them to understand the importance of keeping their own devices secure.
Conclusion
We hope this blog post has given you some helpful ideas on how to protect your business from cyber-attacks. Remember that staying up-to-date on security policies can help keep employees aware of what they should be doing in order to reduce their risk and keep data safe, but it’s also important for businesses to take advantage of cloud storage solutions like Google Drive or Dropbox so users don't store sensitive files locally where they could be stolen if an employee loses their device or isn't sure how the best practice would apply in this situation (e.g., whether or not they should have 2-factor authentication enabled).
1 note
·
View note
Text
Buy High Balance clone cards (physical/virtual cards)
Achetez des cartes clones High Balance (cartes physiques / virtuelles)
#credit card#united kingdom#cashout#usa#make money from home#money#cyber updates#update#france#finance
2 notes
·
View notes
Text
Hmmm.... I enjoy getting lit responsibly

#lit#neo#storytelling#art journal#faustoguio#cyber updates#series#music video#techno#ambient#fausto guio
0 notes