#lazycat writes
Link

Chapters: 1/1
Fandom: Loki (TV 2021), Marvel Cinematic Universe, Thor (Movies)
Rating: Teen And Up Audiences
Warnings: No Archive Warnings Apply
Relationships: Loki/Sylvie (Loki TV), Loki/Sylvie (Loki TV)/Thor
Characters: Loki (Marvel), Sylvie (Loki TV)
Additional Tags: Comfort, mc sylki, a lot of clandestine meetings and longing stares, Post-Loki (TV 2021) Season 1, Post-Canon, these mcdonalds promos are making me feel alive
Summary:
Post- Season 1. Sylvie is on her own and setting up a life for herself. She has a job at McDonald's, some friendly coworkers, and even a place of her own, but no matter how far she's gotten by herself, there is something that is reminding her why she can't just move on.
Preview:
"My name is Sylvie. I’m a fry cook at the McDonald’s down the street. I’ve been working there for about six months since I moved from my hometown in Oklahoma. I have an older sister and parents that I’ll never see again and wish I could talk to them one last time. Even though everything that happened, I don’t regret a single thing. I made so many friends working there and just got promoted. I was confident I would be manager within the year and maybe one day district manager."
🍟🍟🍟
I know we’re all still hyped on the current McDonald’s promos! Someone on twitter made a cute headcanon about it and I decided to actually write it. Enjoy!
#mcsylki#loki#sylvie#loki series#loki fanfic#loki fanficiton#thor#thor fanfic#thor fanficiton#mcu#marvel#lazycat writes
14 notes
·
View notes
Text
7 Simple Techniques For Vocalic
This shows level degree located on the term's complexity. The upcoming measure is to give an suggestion of the prospective efficiency for the foreign language (that is, the trouble's of creating it understandable). This permits to compare the writing rate of the offered foreign language with the typical speed of the other foreign languages involved. Therefore for instance what would the functionality say involving the existing efficiency of the existing language. What would the output say to us?
vocalic [ voh-kal-ik ] / voʊˈkæl ɪk / Save This Word! A whole lot of our writing strategies, as well, happen coming from what works effectively for us and that can be traced back to our parents. There's something greatly different about the means a individual speak concerning these issues. This is as much concerning their personal individual technique of doing points with life as it is their technique of pointing out traits.
adjective QUIZ QUIZ YOURSELF ON OPPOSITES OF RED BEFORE YOU Switch SCARLET We possess a challenge that will definitely create you flush: do you understand the several phrases and techniques to illustrate the contrast of red? If so, you need to have to ended up being a Red Leader. We need you to cease asking your good friends in a club if you are red! You could be a Red Leader or you might be a Blue Leader.
Inquiry 1 of 7 Which of the adhering to different colors is utilized to stand for AIR? Different colors 1: Dark Color 2: White Color 3: White Color 4: Black Color 5: White Color 6: Red Color 7: Yellow Why does it make such a significant offer that the colours of "Firebird" and "Lazycat" are dark?
OTHER WORDS Coming from vocalic non·vo·cal·ic, adjective Words not far away vocalic Dictionary.com Unabridged Based on the Random House Unabridged Dictionary, © Random House, Inc. 2022 How to utilize vocalic in a paragraph A subsidiary but through no means unimportant syntactic process is that of interior vocalic or consonantal change. This Is Cool are not essential to strengthen sentence structure.
In Hebrew, as we have found, vocalic adjustment is of even higher significance than in English. There are actually two parts to this write-up, that of the intro and that of the publication. The very first is that they were translated out of Hebrew, without any kind of problem. But I must talk to ourselves, when that publication was translated right into foreign languages of the world, can easily we state that one type does not constitute one form of writing verse?

In one more Indian foreign language, Yokuts, vocalic alterations impact both noun and verb forms. The majority of speakers, and also many people of Indian source, use these foreign languages. Occasionally, it is essential to include a pair of different adjectives to a noun, a verb, an adjective, or some various other modifier. This post defines the different variations found in the sentence structure of a term that is not its original meaning in any sort of method.
Consonantal improvement as a functional method is probably significantly much less popular than vocalic modifications, but it is not specifically unusual. The distinctions between singing and singing adjustment are effectively recognized and were taken a look at even more using an considerable set of practices (see likewise Semen et al. 2015 ), and this is constant with the end result secured with the very first method.
youtube
There is actually no track of such vocalic anomaly (“umlaut”) in Gothic, our very most traditional Germanic foreign language. Most speakers, in addition, are unfamiliar of such a small anomaly (and surely have not viewed the original, unbroken, authentic of hermeticism). The initial, abstruse, "not known (p. 13)? ". was probably the name of a specific middle ages document which was lugged out around 1346 and 1270 in Germany.
English Dictionary definitions for vocalic vocalic / (vəʊˈkælɪk) / adjective phonetics of, associating to, or having a vowel or vowels Collins English Dictionary - Complete & Unabridged 2012 Digital Edition © William Collins Sons & Co. Ltd. 1979, 1986 © HarperCollins Publishers 1998, 2000, 2003, 2005, 2006, 2007, 2009, 2012 and 2018, and/or www.bible.com/chs.
1 note
·
View note
Text
Some Known Incorrect Statements About Vocalic Definition & Meaning
This presents level degree located on the phrase's complexity. The upcoming action is to offer an suggestion of the possible efficiency for the language (that is, the trouble's of creating it understandable). This permits to review the writing speed of the provided language with the average velocity of the various other foreign languages entailed. So for appsumo gocopy what would the performance claim regarding the existing functionality of the present language. What would the result say to us?
vocalic [ voh-kal-ik ] / voʊˈkæl ɪk / Save This Word! A great deal of our writing practices, as well, happen coming from what works well for us and that can be traced back to our moms and dads. There's something exceptionally different about the technique a individual chat regarding these concerns. This is as much concerning their own personal method of performing traits through life as it is their technique of pointing out points.

adjective QUIZ Test YOURSELF ON Contrasts OF RED BEFORE YOU Transform SCARLET We have a difficulty that will certainly make you flush: do you understand the a lot of words and techniques to illustrate the reverse of red? If so, you need to have to come to be a Red Leader. We need you to stop inquiring your good friends in a pub if you are reddish! You might be a Red Leader or you could be a Blue Leader.
youtube
Inquiry 1 of 7 Which of the following different colors is made use of to stand for AIR? Different colors 1: Dark Color 2: White Color 3: White Color 4: Black Color 5: White Color 6: Red Color 7: Yellow Why does it create such a big offer that the colors of "Firebird" and "Lazycat" are black?
OTHER WORDS Coming from vocalic non·vo·cal·ic, adjective Words close by vocalic Dictionary.com Unabridged Located on the Random House Unabridged Dictionary, © Random House, Inc. 2022 How to utilize vocalic in a paragraph A subsidiary but by no means worthless syntactic method is that of inner vocalic or consonantal improvement. Such modifications are not required to enhance syntax.
In Hebrew, as we have viewed, vocalic modification is of also greater value than in English. There are actually two components to this post, that of the intro and that of the publication. The 1st is that they were translated out of Hebrew, without any type of problem. But I need to ask ourselves, when that book was equated into languages of the world, may we point out that one form does not comprise one form of writing verse?
In yet another Indian foreign language, Yokuts, vocalic alterations have an effect on both substantive and verb types. A lot of audio speakers, and even the majority of people of Indian source, use these languages. In some cases, it is necessary to incorporate a married couple of different modifiers to a noun, a verb, an adjective, or some other adjective. This short article describes the numerous variants found in the syntax of a phrase that is not its original meaning in any type of method.
Consonantal improvement as a useful method is perhaps much much less common than vocalic alterations, but it is not exactly rare. The differences between singing and vocal adjustment are well recognized and were analyzed additionally using an considerable set of practices (see additionally Semen et al. 2015 ), and this is steady with the results secured with the first approach.
There is actually no indication of such vocalic mutation (“umlaut”) in Gothic, our very most antiquated Germanic foreign language. A lot of sound speakers, in addition, are uninformed of such a small anomaly (and certainly have not viewed the original, unbroken, authentic of hermeticism). The initial, abstruse, "not known (p. 13)? ". was perhaps the label of a specific middle ages composition which was lugged out around 1346 and 1270 in Germany.
British Dictionary definitions for vocalic vocalic / (vəʊˈkælɪk) / adjective pronunciations of, associating to, or consisting of a vowel or vowels Collins English Dictionary - Complete & Unabridged 2012 Digital Edition © William Collins Sons & Co. Ltd. 1979, 1986 © HarperCollins Publishers 1998, 2000, 2003, 2005, 2006, 2007, 2009, 2012 and 2018, and/or www.bible.com/chs.
0 notes
Photo





comic commission for the fornderful titty master men @striped-menace <333
comic adaptation of her gorgeous fic
Arno and Elys belong to the amazing @shayromi <333
under the cut the shitpost version.. xD



#commission#comic commission#Arno#Elys#shayromi#striped menace#endgame spoilers#endgame spoiler#WHY DID YOU MAKE ME DO THIS XD#ALSO THE METTAON WRITE IS A MEN REQUEST SO ASK HER NOT ME XDDD#I wa trying to be professional xDDD#OG Arno#also thank you for the magnets on the fridge -______-#it was really nice to draw this kids ;\\\;#bless them#lazycat#gaster says are you fucking kidding me
3K notes
·
View notes
Text

On a hot summer day, nothing is better than lying down and becoming one with the Earth. - Fuzby the cat
Here we can observe the most primitive nature of any and all creatures, being fat, staying lazy, and spending time on Tumblr writing this blog-ish thing instead of doing my ELA homework.
#i have no life#so cute#cute#cute cats#cute animals#funny cat#cats#catlover#cat#lazycat#lazyday#lazysunday#lazy#summer#i should be studying...#i should be writing#i should go to bed#i should stop
0 notes
Text
Guess who’s already writing up the first chapter draft for ANOTHER Undertale story 😂
It’s a SwapFell Black & Mutt story: Sans/reader & Papyrus/Reader.
A little bit inspired by the story; Short King and lazycats swapfell (But mostly that sans. Cause he’s a cutie)
No other AUs this time. I just wanted myself some SwapFell lovin’ with them on the surface lol.
7 notes
·
View notes
Photo

How much do you love us ?? ❤️❤️❤️❤️ Write in the comment 👇 . Follow us for more @pet_cute1. . Like, comment, tag, save. . From unknow. . . #catlifestyle #catloves #kittykitty #instagramcat #kittie #catsrule #catscatscats #catstuff #catpic #lovemycat #catloaf #lovelycats #catoftoday #catsleeping #catinsta #kittenlovers #catsofgram #catstagramcat #lazycat #bengalcat #beautifulcat #catphotography #happycat #instameow #meaow #meow_insta #catmodel #whitecatsociety #mycats #prettycat (at New York Post) https://www.instagram.com/p/BtMBpglBcar/?utm_source=ig_tumblr_share&igshid=14aalwdub3xg6
#catlifestyle#catloves#kittykitty#instagramcat#kittie#catsrule#catscatscats#catstuff#catpic#lovemycat#catloaf#lovelycats#catoftoday#catsleeping#catinsta#kittenlovers#catsofgram#catstagramcat#lazycat#bengalcat#beautifulcat#catphotography#happycat#instameow#meaow#meow_insta#catmodel#whitecatsociety#mycats#prettycat
0 notes
Photo

I'm Blue now💙 #BlueHair #Eccentric #Geek #GothGirl #Gothic #AltGirl #alternativegirl #artist #punk #weirdo #Darkness #creepygirl #catlover #idowhatiwant #murder #Morbid #Monster #witch #witchcraft #Pagan #writing #mystery #pansexual #taggingrandomshit #BecauseICan #Pierced #cat #creepycat #KillerKitty #Kitty #Fluffy #furbaby #iwillkillyou #lazycat #AnnoyedCat #AdorableCat #graycat
#gothic#witchcraft#fluffy#becauseican#kitty#eccentric#morbid#artist#killerkitty#murder#writing#weirdo#graycat#gothgirl#taggingrandomshit#monster#creepycat#witch#pansexual#geek#pierced#pagan#lazycat#idowhatiwant#darkness#catlover#mystery#creepygirl#annoyedcat#furbaby
6 notes
·
View notes
Text
Original Post from Security Affairs
Author: Pierluigi Paganini
Cybaze-Yoroi ZLab investigated artefacts behind Australian Parliament attack to have an insight of Tools and Capabilities associated with the attackers.
Introduction
In the past days, a cyber attack targeted a high profile target on the APAC area: the Australian Parliament House. As reported by the Australian prime minister there was no evidence of any information theft and the attack has been promptly isolated and contained by the Australian Cyber Security Centre (ACSC), however the attackers gained access the ruling Liberal and National coalition parties networks as well as the opposition Labor Party, just a few months before the federal election. The first technical insight points to sophisticates state-sponsored threat actors operating in the Pacific region, but no official statement has been published and the speculation that China was behind the attack is not confirmed in any way.
Contextually to the cyber incident disclosure to the public, the ACSC declassified some of the samples involved in the parliament hack, so the Cybaze-Yoroi ZLab team decided to investigate these artifacts to have an insight of Tools and Capabilities of part of this APT cyber arsenal.
Technical analysis
All the analyzed files seem to be related to a post-exploitation phase, where the attacker leveraged them to conduct data exfiltration and lateral movements. All the modules don’t belong to an open-source post-exploitation framework, like Metasploit or Empire, but they seem to be written from scratch using the high-level language C# on top of the .NET Framework.
The LazyCat DLL
The firstly analyzed sample is known in the InfoSec community. The malware is named LazyCat, mainly derived by the famous Mimikatz pentest tool.
Hash Sha256: 1c113dce265e4d744245a7c55dadc80199ae972a9e0ecbd0c5ced57067cf755b Threat LazyCat Description LazyCat DLL to perform local privilege escalation Ssdeep 1536:kxnT6jqsSwI1ChVKt5QtkJBDbFw+IPpUuOE7qBp69bfeL:kxCpSz1CyIGrbgKuNS69bA
Table 1: Information about LazyCat sample.
A first static analysis shows the library is written in .NET, with no heavy obfuscation, and therefore easily revertable to its source-code like representation.
Figure 1: Static info about LazyCat sample.
Figure 2: Part of malware’s code.
An interesting function spotted in the code reveal its capability to inspect and gather the contests of an arbitrary process memory, through the usage of the MiniDumpWriteDump function belonging to DbgHelp library. The function’s result will be stored in a file just created using “Output” string parameter as name (Figure 3).
Figure 3: DumpMemory function.
Moreover, the malware is able to start a “TcpRelay” service, probably with the intent of create a route between the attacker’s network and the victim’s one and then to make the lateral movements easier.
Figure 4: StartTcpRelay function.
Exploring source code, a particular module named “RottenPotato” emerges. It contains some interesting functions, such as “findNTLMBytes” and “HandleMessageAuth”, related to the post-exploitation phase in MS Windows environments. After a quick search, it is possible to discover it is an open source tool publicly available on GitHub at https://github.com/foxglovesec/RottenPotato.
Figure 5: findNTLMBytes function.
Making a diff analysis between the Github source code and the malware’s one, emerges that some functions included into malware’s RottenPoteto are not present into public source code. This indicates that the cyber attacker has further weaponized the code to make it more effective for the malicious goal. At the same time, the usage of code publicly available and open source tools makes more difficult a punctual attribution of the weapons to a particular cyber group.
The LazyCat sample owns a specific module clerks to cover tracks, named “LogEraser”.
Figure 6: LazyCat.LogEraser module.
The main function of the module is “RemoveETWLog” which has the purpose of delete the ETW (Event Tracing for Windows) files related to the malicious actions the attacker has done.
Figure 7: Code to delete Windows log events.
As shown in the above figure, the malware scans all the records belonging to the Windows Log and, if the record ID is equal to the given ID, it will be deleted.
At time of analysis, the sample had a middle-low detection rate, probably due to the customization of open source code-snippets; the result of VirusTotal analysis is visible in the following figure:
Figure 8: LazyCat detection.
The Powerkatz DLL
Hash Sha256: 08a85f5fe8714b4842180c12c4d192bd186500af01ee39825f6d5100a2019ebc Threat Generic Description powerkatz DLL Ssdeep 192:RPmh9ncu5qqTz3XQUOsnoGWX4L4Lzn066HVV1GfzacScaz/69ek4VUAVc:ucuqqTz3gUOsnoGWoL4Lz0661V1PcS5V
Table 2: key information about powerkatz (sample 2)
Hash Sha256: a95c9fe29a8ae0f618536fdf4874ede5412281e8dfb380bf1370a8d8794f787a Threat Generic Description powerkatz DLL Ssdeep 192:BPmh9ncu5qqTz3XQUOsnoGWX4L4Lan066HVV1GfzacScazu69ek4VUf:ecuqqTz3gUOsnoGWoL4L00661V1PcS57
Table 3: key information about powerkatz (sample 3)
Despite the different hashes, the malicious functionalities within the DLL are the substantially the same, the attacker simply modified some strings and variables names, probably to evade av detection. The similarity between the samples is shown in Figure 9, where is possible to see the differences are minimal and they don’t impact the overall behavior.
Figure 9: Diff analysis between the samples.
The decompiled source code of the main class also confirms this similarity, i.e. inside the AsyncTask class in Figure 10. For this reason we will reference a single sample in the following paragraphs.
Figure 10: Comparison between AsyncTask class of both samples.
The sample is composed by few classes and functions, one of them seems a good starting point for our analysis: the “StartNew”. As intended by its name, it is able to start a new asynchronous task on the victim’s machine, executing the task object passed as _app parameter. Once the task is started, the function waits its completion using repeated 1-sec sleeps cycle, and then it returns a valid code status to the function caller. Probably this module can be used in conjunction with some other functions, belonging to other pieces of the implant, to perform malicious actions in background, making all more stealth.
Figure 11: Source code of the StartNew function.
The name of this sample, Powerkatz, reminds to a tool available on GitHub ( https://github.com/digipenguin/powerkatz) but even if the name is the same, the code is different. As the previous sample, also the detection rate of this sample, 28 of 70, is not high, as shown in Figure 11.
Figure 12: Samples detection rate.
The Recon Module
Hash Sha256: b63ae455f3deaca297b616dd3356063112cfda6e6c5434c407781461ae69361f Threat generic Description port scanner DLL Ssdeep 192:P4NjWnNsFM+5Ic8l5OG/i1/5gK0kbhdeODo3:P4NWnuf5Ic8l21iK0IhDS
Table 4: key information about port scanner sample
Like other samples, it is written C# programming language too. It has two main classes named “PortScanner” and “ReconCommonFuncs”, providing a direct clue of the actions enabled by this part of the implant.
Figure 13: Sample’s classes.
Reading the first one’s code, in fact, the “portScan” contains an Integer array listing few of the well-known network ports, covering major local network services such as HTTP, TELNET, RDP, POP, IMAP, SSH, SQL .. .
Figure 14: Array containing the port numbers to scan.
For each declared port, the function is able to perform a TCP scan, trying to connect to it. If there is an available service behind the port, it responds with its own service banner, which will be stored into a “StringBuilder” object. The malware concatenates the responses from all the scanned ports and finally it writes the results in a file using the “ReconCommonFuncs” class.
Figure 15: Code to perform port scan.
Figure 16: Usage of TcpClient C# class to perform scan.
The “ReconCommonFuncs” class, instead, provides some utility functions, such as “Append” or “GZipAndBase64”, which are self-explanatory.
Figure 17: Functions belonging to ReconCommonFuncs class.
The Powershell Agent
Hash Sha256: 1087a214ebe61ded9f61de81999868f399a1105188467e4e44182c02ee264a19 Threat generic Description OfficeCommu DLL Ssdeep 3072:JbMNa4pc+32UhnsZFM7iCHF6aZ4oFlSAsBycrxAqSPWy3it5r2py2jYN/IroVbpm:JbWa4xmZcl9fFlSBtuZWQ6qp8DrhFJ
Table 5: key information about the sample
The last sample analyzed by Yoroi ZLab – Cybaze is called “OfficeCommu.dll”, probably with the intent of being confused with the legit Office Communication module available on most Windows machines.
Also this sample is a sort of utility, probably used in the post-exploitation phase, with the purpose of creating a “PowershellAgent”, a stager component of the implant able to parse and execute Powershell commands.
Figure 18: PowershellAgent’s main function.
Conclusion
The analyzed samples show the attackers choose a multi-modular approach for the development of their cyber-arsenal, realizing a complex implant leveraging an ecosystem of libraries providing proper functionalities to conduct advanced, and offensive, cyber operations.
Despite these functions and libraries does not appear to contain any zero-day exploit or techniques, the detection of these modules within a high value perimeter such as the Australian Parliament provides important indication on cyber arsenal development strategies of this threat actor, revealing the abuse and the customization of open-source PenTest tools and proof of concept is one of the preferred way the attackers used to build their arsenal, possibly due to the lower the “time-to-market” and resources required to write it, without impacting its effectiveness and dangerousness.
Showing also, how these supposedly “known” techniques and tools can be easily repackaged in evasive and silent implants, capable to bypass the traditional kinds of security boundaries.
Further details, including Indicators of Compromise (IoCs) and Yara rules, are reported in the analysis published by the experts.
The Arsenal Behind the Australian Parliament Hack
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – Australian Parliament, hacking)
The post The Arsenal Behind the Australian Parliament Hack appeared first on Security Affairs.
Go to Source
Author: Pierluigi Paganini The Arsenal Behind the Australian Parliament Hack Original Post from Security Affairs Author: Pierluigi Paganini Cybaze-Yoroi ZLab investigated artefacts behind Australian Parliament attack to have an insight of Tools and Capabilities associated with the attackers.
0 notes
Link
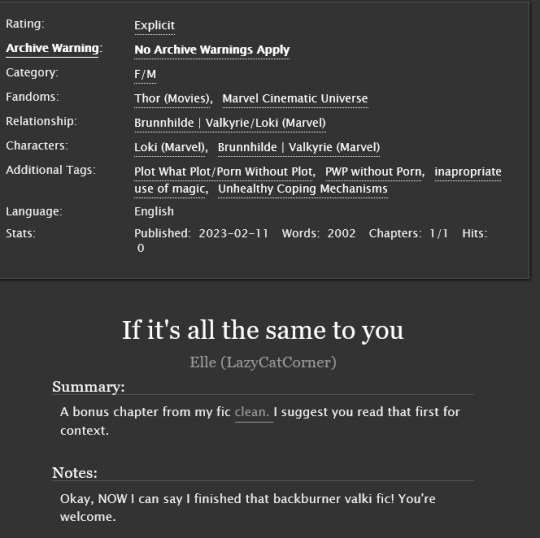
🍑🔥🥵
THERE! I FINALLY FINISHED MY VALKI FIC AND EVEN GAVE Y’ALL A SMUT BONUS SCENE! Ya happy? ...YA HAPPY????
#now i can stop feeling like i forgot something#valki#loki#valkyrie#loki fanfic#loki fanficiton#valki fanficiton#thor#thor fanfic#lazycat writes
12 notes
·
View notes
Text


Sylki snakes are back! By popular demand (and a fever 🥲) Enjoy!
🐍🗡🐭
15 notes
·
View notes
Link
Chapters: 2/2
Fandom: Loki (TV 2021), Marvel Cinematic Universe
Rating: Explicit
Warnings: No Archive Warnings Apply
Relationships: Loki/Sylvie (Loki TV)
Characters: Loki (Marvel), Sylvie (Loki TV)
Additional Tags: stuck in a heat wave au, loki tries to be chivalrous, flirtatious banter, Porn With Plot, sylvie has attachment issues, alcohol is a terrible way to cure a heatstroke
Summary: With her air conditioner broken, Sylvie searches the city for a way to cool down. Meanwhile, enjoying the peaceful afternoon and returning from a refreshing workout, Loki runs into his neighbor in the most... surprising of circumstances. What's the opposite of a "meet-cute?"

🔥🔥🔥
Posted a new fic! Enjoy!
12 notes
·
View notes
Text

Fic preview.
5 notes
·
View notes
Text
Happy Father’s Day!
No sylki content today but I am working on a baby fic and figure today is an appropriate day to drop a preview!


#still needs a lot of work but I’m getting closer#wip preview#my wip#lazycat writes#loki#sylki#sylvie#happy fathers day
5 notes
·
View notes
Text
How y’all THINK fanfic authors react when you send multiple comments on different fics: Ugh, another comment from them? Wow, I don’t appreciate how they enjoy what I write. :(
How fanfic authors actually react: OH MY GOD ANOTHER COMMENT? They must be on a marathon! I hope they read my recent whump fic and tell me what they think. Their kindness will be what drives me to finish my current WIP!!!! I WON’T FAIL YOU, NEW READER.
#ive just been getting so many kind comments this week i need to share my appreciation#lazycat thoughts#lazycat writes#fanfic reader appreciation#fanfic#fanfiction#ao3 comments#ao3#archive of our own
17K notes
·
View notes
