#penetration testing
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
2 notes
·
View notes
Text
3 notes
·
View notes
Text

woa. must be legit LOOK at that COVER
The Hacker Playbook 2 at thrift
#software testing#penetration testing#thrift books#playbook#hacker playbook#book covers#book cover#second hand#software#reference books
3 notes
·
View notes
Text

#cybersecurity training#cybersecurity#ethicalhacking#penetration testing#cybersecuritycertifications
2 notes
·
View notes
Text
Application Penetration Testing
A Cyber Security consultancy that offers a range of services including, malware detection and prevention, website security audit and Assessment, data exfiltration detection and containment, web application penetration testing. We also offer various web-application auditing services and VAPT services.
3 notes
·
View notes
Text
How To Protect Your Facebook Account - 5 Internet Security Pointers Exposed!
The very first thing you better do prior to starting a home service is in fact set up a service. That implies obtaining either a social security or company recognition number. You're going to require to report taxes if you work in the United States and make an income of over $600, which hopefully you'll do. The last thing you want to do is run your service unlawfully.
If you have reason to believe or highly believe you have an infection, much like calling your physician's workplace, stop what you are doing. If you value the info on your system and do not want to lose it or share it with details burglars the finest thing to do is turn your system off - DO NOT restart it up until you have it in the hands of a qualified professional to get rid of the infection or corroborate its existence. Err on the side of caution.
This is the best service of all because if it do not break, you never ever need to fix it. We typically want that life was so basic that we could solve problems prior to they occur. Though not common in the physical aircraft, this is a reasonable state in the cyber-world. Possibly, not entirely however you get the concept. penetration testing website realize death and taxes are unavoidable. Death applies to your computer system as well. The hope is we will update by desire prior to we are required to update by requirement. The following are some tips to bring that dream better to truth.
Be certain that your site's navigation is basic to follow and understandable. Make it hassle-free for your visitors to find their way around your website by having the right keywords, titles and links.
A friend recommends you re-install your operating system on your computer to improve its performance. If you wish to format the drive (a step in re-installing Windows XP) you accidentally hit the wrong key, during the procedure you are asked. Congratulations, you have now cleared all of the details on your computer system. In numerous cases, the details loss is not irreparable however its repair work can be REALLY pricey and time consuming.
You require to make sure you have an excellent internet connection with a working computer. In the current times, lots of people experience web breakdown or low speed. This is because; they do notknow where to get the finest cyber security tips web connection.
Cyber Monday is one of the finest profit-making opportunities of the year if you run an online shop. But it will take more than excellent items and a website to bring in online buyers. There are a variety of essential things that online sellers like you ought to get ready for prior to Cyber Monday comes.
youtube
29. Adopt tools and strategies that permit you to measure the experience of real users throughout all websites to value the real service effect of poor performance. Look out for availability steps and your ecommerce-website speed, and tune your system accordingly.
When you obstruct a person, there will be a window appears and ask you for the reason. If they have cyber stalking or harassment, you should REPORT them. It is essential to REPORT if this is really occurring, since individuals will not stop if no one reports.
I make sure there are websites that are respectable and exceptional in offering you with different kinds of automobile funding alternative for first time vehicle buyers. Some of them will go out of their method and provide you with numerous auto loan rates from the lenders near your area. These sites generally, work like online search engine for vehicle loan for all types credit. So, it would be more useful for anyone to search for car loans online.
#website penetration testing#penetration testing#pentest#trusted website penetration testing#legit website penetration testing#find website penetration testing#website penetration testing company
2 notes
·
View notes
Text

#vulnerability assesment#penetration testing#vapt#vapt services#vapt certification#siscertifications
0 notes
Text
finding usernames/passwords for testfire.net
background: testfire.net is a "fake" website designed for pentesters to play around with. it is NOT a real bank and no one's information is actually being stolen here. this was an assignment for a class.


first we start by logging into the admin account, username: admin and password: admin. although a general SQL injection works on this site. for the inject, password is irrelevant.
other injects that work (note that's not a quotation, that's two apostrophes):
' or ''='
' or '1' = '1
or any other statement that will always be true
on the left we see we can "Edit users"


our assignment was to find username and password pairs. you'd think you could cheekily change the passwords of existing accounts or add new accounts to fulfill this requirement, but none of these options on the admin page actually work.

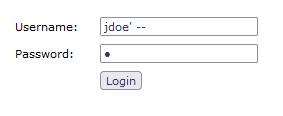
we can see the usernames of several users. since we know the username field is vulnerable to injects, we can now login to any of these without knowing the password.

this field is also vulnerable to injects. inject used:
' --
okay never mind post cancelled
i just checked the solution that my professor wanted and i shit you not its this:

these do technically work as username and password pairs. like, if you use them, you will sign in. in fact, i think you can just put anything other than a blank space for the password and it would count. but man. fuck this.
regardless, here are some actual pairs that i ended up finding. i cant quite remember how i found them, but i saw someone use "demo1234" as a password for both jdoe and jsmith, so i tested sspeed and its the same password. cant find the other ones though.
jdoe | demo1234
jsmith | demo1234
sspeed | demo1234
1 note
·
View note
Text
PEN Testing vs. Vulnerability Scanning

In safeguarding sensitive data, thwarting cyberattacks, ensuring operational continuity, adhering to regulations, preserving reputation, and nurturing customer trust, businesses steer clear of vulnerable networks. This strategy not only fosters seamless operations, mitigates financial losses from breaches, and fosters a competitive edge but also bolsters data security, curbing the risk of intellectual property theft and boosting employee productivity. Prioritizing network security showcases a dedication to customer trust, fortifies brand reputation, and secures the long-term prosperity and resilience of the business. When it comes to securing networks, business owners can opt for either PEN testing or vulnerability scanning. Discover more about PEN testing versus vulnerability scanning and their roles in fortifying your business by clicking the link below.
0 notes