#stayvigilant
Text
I don't know who needs to hear this but.. that was exactly their intentions. They meant to do that. Don’t be fooled.
#TrustYourInstincts#Intuition#TrueIntentions#StayWoke#StayVigilant#BeAware#NoFooling#ClearMotive#BeCautious#ProtectYourself
7 notes
·
View notes
Text
"😱💥 ALBO's Revolutionary Hack-Blocking Strategy Revealed: The Surprising Power of Turning Off Your Phone! 😱📱 Don't Miss Out on This Game-Changing Cybersecurity Tip!"
📱🚫⚡️ ALBO wants you to turn off your phone?!?!?! But why? Well, he's been communicating with the new king of cyber safety in good old down under and they've sussed out the situation. The down low key notes are that those pesky hackers want your deets and your phones have those deets. So to stop them dead in their tracks, you can use this one simple trick: just turn your phone off. 🙅♂️💥
But this advice ain't new, my fellow Tumblarians! The US of A decided way back in 2020 that the advice was lit af. 🔥🔥
The cool doctor was like, "yo, you want alarms all hours? Don't do it. Just be the cool person and prank the script kiddies with the power of no power." 😎🔌
So, fam, next time you're feeling like you're under attack from those hackers, remember Albo's advice and power down that phone. Stay safe out there! ✌️🔐✨

#PhoneSafety#CyberSecurity#TurnOffYourPhone#HackersBeware#StaySafeOnline#NoPowerNoHackers#AlbosAdvice#PrankTheScriptKiddies#StaySecure#DigitalSafety#ProtectYourDeets#USACyberSafety#PowerDown#StayVigilant#PhoneProtection#OnlinePrivacy#BeSmartBeSafe#TumblrArticle#EmojisEverywhere
5 notes
·
View notes
Text
youtube
#COVID19Scams#ArriveCanAlert#ScamAwareness#DigitalSafety#FightFraud#LinkedInCommunity#StayVigilant#ProtectYourself#KnowledgeIsPower#StaySafe#CombatExploitation#youtube#small youtuber#Youtube
0 notes
Text
Smooth Sailin' Today, Sunk Tomorrow: The Trojan Horse of Centralized Systems for Scallywags
As we sail the digital seas into the future, companies and governments seem to be buildin' more centralized data systems that connect all yer personal information in one treasure chest. Should we hand over the keys and maps to our entire lives? Let me tell ye a cautionary tale.
Imagine callin’ up a pirate pizza shop in the year 2054. Ye give the scurvy crew yer "unified identity number" and suddenly they have access to yer address, name, medical history - everything about ye! It seems convenient at first until ye realize how vulnerable ye now be.Somethin' doesn't seem right about the order? Too bad, the pizza pirates already have yer payment info. Fall ill from the stale grub? Now they can view yer medical records and sell yer data to greedy drug companies. Try to abandon ship and order elsewhere? They already control all yer details across every realm of yer digital life.
This nightmare vision could become our reality if we let companies and governments create centralized databases of all our personal booty. No more splitting up yer treasure across different locked chests and hiding maps where only ye can find them. Everything bundled together in one vulnerable pile, ripe for the pickin'.
Of course the powers that be claim centralized systems be more convenient and efficient. But what about privacy and security? Do we really want to hand over the keys to our identities and life's details to any swashbuckling sea dog who asks?
As it stands now, the terms of service we agree to already surrender quite a bit of data ownership to the ships we sail on. We lads and lasses best start examining those terms closely before we lose control of our treasures entirely. It may seem like centralized data systems are an inevitable tide in this digital era. But we still have some power to resist. We can refuse deals that require givin' up more knowledge than needed for the task at hand. Encrypt yer data, use aliases, and don't stay loyal to any one ship that wants to centralize all yer booty in their treasure room.
Most importantly, speak up! Call yer elected officials, demand stronger privacy laws, and don't let profit-hungry pirates dictate how much access we surrender. Yer identity belongs to ye, and nobody should control the keys to yer treasure chest but you! So beware the creeping control of centralized data systems. Convenience today could mean exploitation tomorrow. With vigilance and common cause, we can still chart a course toward a digital future where privacy and personal liberties are sacred treasures defended from all who would seize them as their own!
0 notes
Text

Jayden Wei became a billionaire by launching Ponzi Scheme?
Join us as we expose Jayden Wei's journey to becoming a billionaire through launching Ponzi schemes.
Follow our page for a comprehensive look at the consequences of his actions and how to steer clear of such scams and find out who is Jayden Wei.
0 notes
Text
Caught on Camera | Shocking Car Break-In Footage Revealed! 😱🚗
Buckle up for a jaw-dropping experience as we unveil raw and unfiltered footage of a shocking car break-in! In this gripping video, witness the unsettling reality of vehicle security as we share real-time footage capturing the brazen act of someone attempting to break into a car. From the nerve-wracking moment of intrusion to the unexpected twists that follow, this footage is not only a cautionary tale but also an eye-opener for all car owners. Join us as we analyze the events, discuss preventive measures, and shed light on the importance of staying vigilant in today's urban landscape. Your car's safety is our priority, and this video aims to raise awareness about the stark reality of car break-ins. Share, comment, and let's build a community focused on automotive security! 📹🚨
0 notes
Text
तीन संदिग्ध मिलने के बाद हाई अलर्ट मोड पर अयोध्या |Swadesh Live| Madhya Pradesh News In Hindi| Breaking News
#AyodhyaAlert#HighAlertMode#SuspiciousEncounter#SecurityConcerns#VigilanceInAyodhya#AlertSituation#SafetyFirst#StayVigilant#SecurityUpdate#AyodhyaIncident#CautiousCitizen#AlertnessMode#SafetyAlert#PublicSafety#SecurityResponse#CommunityAwareness#AyodhyaSecurity#WatchfulEyes#SafetyAwareness#StaySafeAyodhya
0 notes
Photo

Unveiling Tomorrow: Private Investigation Trends Shaping 2024 As we step into the realm of 2024, the world of private investigation is evolving rapidly, adapting to technological advancements, societal changes, and the ever-shifting landscape of the digital era. In this blog, we'll delve into the trends that are shaping the private investigation landscape in 2024. Cyber Sleuthing Takes Center Stage Gone are the days when private investigators relied solely on stakeouts and discreet surveillance...[...] #ReadFullArticle https://investigationhotline.org/private-investigation-trends/ We appreciate your comments, shares, and questions. If you need any assistance, please don’t hesitate to call us at (416)205-9114. Investigation Hotline. Experts-Always On Call – Private Investigator Toronto https://investigationhotline.org/
#2024Innovations#CyberSleuthing#DeepfakeDetection#DigitalDetectives#EthicalHacking#GlobalCollaboration#GlobalCollaborations#InvestigatorToolkit#PrivateInvestigation#PrivateInvestigationTrends#StayVigilant#TechAdvancements#TechTrends2024
1 note
·
View note
Text
Beware of cryptocurrency scams!

Don't fall for fraudulent schemes and lose your hard-earned money. At Regain Funds LLC, we are dedicated to protecting you from cryptocurrency scams.Our team of experts is constantly monitoring the market and can help you identify potential scams before it's too late 💰 Don't hesitate to reach out to us for assistance in recovering lost funds or preventing scam attempts.Stay informed and stay safe in the ever-evolving world of cryptocurrencies. Trust Regain Funds LLC to be your partner in fighting against cryptocurrency scams.
0 notes
Text
Your Car's Crumple Zones are like Superheroes, Absorbing the Impact during a Collision and Protecting you. But Remember, Buckle up for yourself! Safety starts with you.
#BuckleUp#SafetyFirst#CrumpleZones#StaySafe#SafetyMatters#Airbags#Seatbelts#StayProtected#SeatbeltMatters#StayVigilant#SafeDriving#MarutiSuzukiSafety#AirbagSafety#SAZArena
0 notes
Text
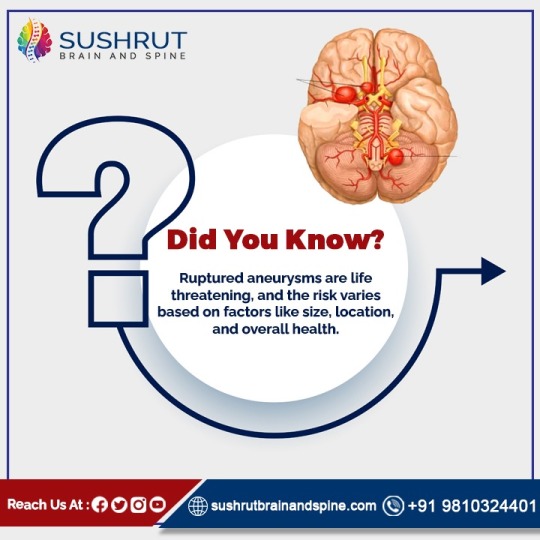
Ruptured aneurysms are no joke. Their danger level depends on factors like size, location, and your overall health. Stay informed, stay safe! ⚠🩸
🌐 Explore our website for more information and reach out for any queries or appointments! 🏥💻
Visit us at www.sushrutbrainandspine.com
📧 Email us at [email protected]
📞 Contact us at 9810324401
#AneurysmRisks#HealthMatters#AneurysmAwareness#StayVigilant#sushrutbrainandspine#aneurysmriskfactors#brainaneurysm#brainaneurysmawareness#healthfacts#didyouknowfacts#FAQ#HealthcareExperts#consultation#bookappointment
0 notes
Text
youtube
#COVID19Scams#ArriveCanAlert#ScamAwareness#DigitalSafety#FightFraud#LinkedInCommunity#StayVigilant#ProtectYourself#KnowledgeIsPower#StaySafe#CombatExploitation#youtube#small youtuber#accounting#bookkeeping#Youtube
0 notes
Text

Guarding Our Youth: Unmasking the Dangers of Gambling Apps
#YouthProtection#DigitalAwareness#GamblingApps#Empowerment#TechSafety#GenerationZ#StayInformed#EmpoweringYouth#ChooseSmartly#DigitalEmpowerment#StayVigilant#PreventExploitation#YouthWellness#TechEducation#GuardiansOfYouth#SayNoToGambling#AwarenessCampaign#DigitalGuardians#HealthyTechHabits#EducateAndEmpower#PrioritizeSafety
0 notes
Text
🔒💡 Keeping Your Cryptocurrencies Safe: The Power of Cold Storage! 💡🔒
As the world of cryptocurrencies continues to expand, ensuring the safety of your digital assets has become more critical than ever. Cold storage, also known as offline storage, is the ultimate fortress against online threats and hacking attempts, making it the most secure way to protect your precious cryptocurrencies. Let's dive into the various methods of cold storage and their pros and cons to help you make informed decisions!
🔐 Hardware Wallets: Fortified Protection Hardware wallets stand as a fortress against cyber adversaries. These physical devices are designed explicitly for secure cryptocurrency storage. Your private keys remain safely tucked away within the hardware, and all transactions are signed securely on the device itself. It's an easy-to-use and portable option, providing you peace of mind and control over your funds.
⚖️ Pros: Top-notch security against online threats, user-friendly, and portable.
⚠️ Cons: They come with a cost, and losing the hardware wallet without a backup can lead to permanent fund loss.
📜 Paper Wallets: The Offline Scroll Printing your private keys and public addresses on paper creates the paper wallet—a venerable guardian against digital dangers. This method involves zero digital footprint, offering robust protection against online attacks.
⚖️ Pros: No digital presence, strong security against cyber threats.
⚠️ Cons: Requires careful handling and safekeeping to avoid physical damage, loss, or theft.
🧠 Brain Wallets: The Power of Memory Brain wallets are the epitome of minimalism—memorizing your private key or passphrase and storing it in your mind. As long as the passphrase is robust and unique, it can be an ultra-secure option.
⚖️ Pros: No physical storage needed, extremely secure with strong passphrases.
⚠️ Cons: Human memory is fallible; forgetting the passphrase means losing access to your funds.
🖥️ Offline Software Wallets: The Digital Guardian Some software wallets can be set up to operate offline, ensuring private keys never encounter the internet. This method adds an extra layer of protection against online threats.
⚖️ Pros: Improved security, especially for tech-savvy users.
⚠️ Cons: Setting up offline software wallets might be more complex, and a secure computer is essential during the process.
🏰 Cryptocurrency Vaults: The Custodial Defense Certain cryptocurrency exchanges and custodial services offer vault storage options. They store your funds offline in secure locations, providing added security.
⚖️ Pros: Extra layer of protection with institutional-grade security measures.
⚠️ Cons: Reliance on third-party entities, limited control over funds.
Remember, safeguarding your cryptocurrencies is paramount. Choose a cold storage method that aligns with your risk tolerance and needs, and always take responsibility for keeping your offline storage devices and recovery phrases secure. 🔒✨ #SecureYourCrypto #ColdStorageAdvantage #HardwareVsPaper #BrainWalletPower #OfflineSecurity #ProtectYourInvestment #StayVigilant #CryptoFortress #ChooseWisely
#SecureYourCrypto#ColdStorageAdvantage#HardwareVsPaper#BrainWalletPower#OfflineSecurity#ProtectYourInvestment#StayVigilant#CryptoFortress#ChooseWisely
0 notes
