#tcp headers
Text






— the tortured poets department (couple’s version) 🪿
like/reblog if you save or use.
arts credits: @cesea.art (xadenviolet), @hachandrws (ruhnlidia), @nairafeather (herongraystairs), @manaarts_ (percabeth), @artoffrostandflame (jurdan), @mahpiyaluta_ (elucien) ;))
#xadenviolet#xadenviolet headers#ruhnlidia#ruhnlidia headers#herongraystairs#herongraystairs headers#percabeth#percabeth headers#jurdan#jurdan headers#elucien#elucien headers#fourth wing header#crescent city#percy jackon and the olympians header#percy jackson headers#the cruel prince headers#the cruel prince header#the infernal devices#a court of thorns and roses#acotar headers#tcp headers#booktwt#bookstan#booktwitter#book headers#book quotes#the tortured poets department headers#the tortured poets department#ttpd header
131 notes
·
View notes
Text
cardan: *knocks on the door* are you decent?
jude: not morally, but i'm wearing pants, if that's what you're asking
#the cruel prince#incorrect the cruel prince#incorrect tfota quotes#tcp memes#tcp fanart#books#fanart#bookworm#cardan greenbriar#jude duarte#book quote#dark academia#tfota fanart#tfota memes#tcp headers#jurdan fanart#jurdan#judecardan#jude duarte headers#jude and cardan#jude headers#jude fanart#holly black#the wicked king#the queen of nothing#the folk of the air#elfhame#how the king of elfhame learned to hate stories#cardan#prince cardan
710 notes
·
View notes
Text


𓆸 ・῾ 𝆬 ‧₊˚ ✉ ・῾ 𝆬 ‧₊˚ 𔒌 ・῾ 𝆬 ‧₊˚ ✒ ‧₊˚ 🗡




the cruel prince headers ‧₊˚
#the cruel prince#tcp packs#tcp headers#jude x cardan#jude icons#jude pack#jude headers#cardan greenbriar#cardan icons#cardan packs#cardan headers#high queen of elfhame#books headers#books packs#books icons#books layouts#books moodboard
239 notes
·
View notes
Text




the cruel prince headers.
favorite or reblog if you saved, pls ♡
#booktwitter#book pack#book header#book layout#twitter layouts#girls icons#icons twitter#model icons#random girl icons#twitter packs#tcp headers#the cruel prince headers#the cruel prince#book headers#books#bookstan#book icons#icons girls#random girls icons#random girls icon#site model girls#site model icons
151 notes
·
View notes
Text




Cardan Greenbriar headers
like/reblog if saved © maddiesflame
#headers#cardan greenbriar#the folk of the air#the wicked king#the cruel prince#the queen of nothing#holly black#cardan greenbriar headers#book headers#header#cardan greenbriar header#headers cardan greenbriar#the folk of the air headers#holly black header#book header#the cruel prince header#the wicked king header#how the king of elfhame learned to hate stories#tcp#twk#tqon#htkoelths
132 notes
·
View notes
Text
HAProxy
HAProxy adalah sebuah perangkat lunak open-source yang berfungsi sebagai load balancer dan proxy server yang dirancang untuk mengelola lalu lintas jaringan pada server backend. Load balancer bertugas membagi beban lalu lintas jaringan antara beberapa server backend yang sama, sehingga dapat meningkatkan kinerja, keamanan, dan ketersediaan layanan.
HAProxy mendukung beberapa jenis protokol seperti HTTP, HTTPS, TCP, dan UDP. Selain itu, HAProxy juga mendukung beberapa mode operasi seperti mode TCP, mode HTTP, dan mode TCP/HTTP hybrid. Dalam mode operasi HTTP, HAProxy dapat melakukan manipulasi header, seperti menambahkan, menghapus, atau memodifikasi header HTTP sesuai dengan kebutuhan.
Salah satu fitur penting dari HAProxy adalah kemampuan untuk melakukan kontrol akses berbasis URL, cookie, dan ACL (Access Control List), sehingga memudahkan pengguna untuk mengelola akses ke server backend secara terpusat dan fleksibel. Selain itu, HAProxy juga dilengkapi dengan fitur keamanan seperti SSL/TLS offloading dan enkripsi, sehingga dapat meningkatkan keamanan dan privasi lalu lintas jaringan.
HAProxy sangat populer di kalangan pengembang dan administrator sistem karena mudah dikonfigurasi, skalabilitas yang tinggi, dan performa yang cepat. HAProxy juga mendukung integrasi dengan banyak perangkat lunak dan sistem, seperti Kubernetes, Docker, dan Apache.
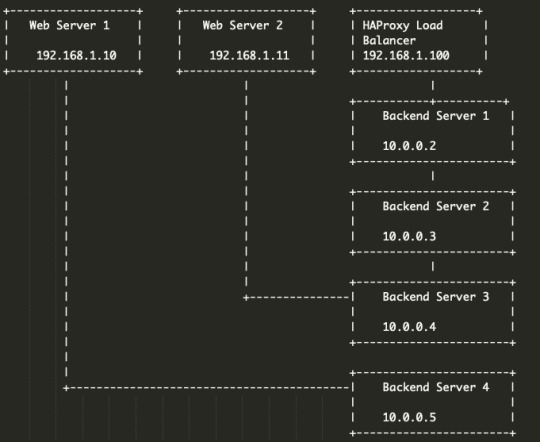
Pada topologi ini, terdapat tiga jenis perangkat utama yaitu Web Server, Backend Server, dan HAProxy Load Balancer. Web Server adalah server yang digunakan untuk menampilkan aplikasi atau website. Backend Server adalah server yang menyediakan data untuk aplikasi atau website. HAProxy Load Balancer berfungsi sebagai perangkat pengatur lalu lintas jaringan dan memastikan bahwa lalu lintas jaringan didistribusikan dengan merata ke Backend Server.
HAProxy Load Balancer memiliki alamat IP 192.168.1.100 dan berfungsi sebagai titik masuk untuk semua permintaan ke aplikasi atau website. Ketika permintaan masuk, HAProxy Load Balancer akan memeriksa setiap Backend Server untuk menentukan server mana yang tersedia dan memiliki beban kerja yang lebih ringan. Setelah memilih Backend Server yang sesuai, permintaan akan diarahkan ke Backend Server tersebut.
Setiap Backend Server berada pada jaringan yang terpisah, yaitu 10.0.0.x. Backend Server digunakan untuk menyimpan dan menyediakan data untuk aplikasi atau website. HAProxy Load Balancer memastikan bahwa beban kerja terdistribusi dengan merata ke setiap Backend Server dan menghindari overload pada satu server tertentu.
Dengan menggunakan HAProxy, administrator jaringan dapat memastikan bahwa aplikasi atau website yang diakses oleh pengguna terdistribusi dengan merata dan tidak terjadi overload pada salah satu server. Selain itu, HAProxy juga dapat diintegrasikan dengan beberapa fitur keamanan jaringan untuk meningkatkan keamanan dan kinerja jaringan.
2 notes
·
View notes
Text
what layer does vpn work on
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what layer does vpn work on
Network Layer
The network layer, also known as Layer 3 in the OSI model, serves as the backbone of communication in computer networks. It is responsible for routing data packets from the source to the destination across interconnected networks. This layer operates by using logical addresses, such as IP addresses, to identify devices and determine the best path for data transmission.
One of the primary functions of the network layer is routing, which involves selecting the most efficient path for data to travel based on factors like network congestion, distance, and cost. Routers, the devices that operate at this layer, make decisions on packet forwarding based on the destination IP address contained in each packet's header.
Another important aspect of the network layer is logical addressing. Unlike physical addresses (MAC addresses) used at the data link layer, logical addresses are assigned to devices to uniquely identify them on a network. The most commonly used logical addressing scheme is the Internet Protocol (IP), which enables communication between devices on different networks.
Additionally, the network layer provides fragmentation and reassembly services to handle data packets of varying sizes. When a packet is too large to be transmitted over a network, it is divided into smaller fragments at the sending node and reassembled at the receiving node.
Overall, the network layer plays a crucial role in ensuring reliable and efficient communication across complex networks. By facilitating routing, addressing, and packet handling, it enables devices to communicate seamlessly regardless of their physical location or network topology.
Transport Layer
The Transport Layer is a crucial component of the OSI (Open Systems Interconnection) model, responsible for ensuring reliable communication between devices across a network. Sitting above the Network Layer and below the Session Layer, it plays a vital role in data transmission, offering both connection-oriented and connectionless services.
One of the primary functions of the Transport Layer is segmentation and reassembly. It breaks down data from the upper layers into smaller, manageable units known as segments before transmitting them. Upon reaching the destination, these segments are reassembled to reconstruct the original data. This process helps optimize transmission efficiency and ensures that large datasets can be transmitted without overwhelming the network.
Another key feature of the Transport Layer is flow control. By regulating the flow of data between sender and receiver, it prevents congestion and ensures smooth communication. Flow control mechanisms such as buffering and windowing allow the sender to adjust the rate of data transmission based on the receiver's capacity, thereby preventing packet loss and network congestion.
Additionally, the Transport Layer provides error detection and correction mechanisms to ensure data integrity. Through techniques like checksums and acknowledgment mechanisms, it detects and rectifies errors that may occur during transmission, guaranteeing the accuracy and reliability of the data being communicated.
Two commonly used protocols at the Transport Layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP offers connection-oriented communication, ensuring reliable data delivery through features like acknowledgment and retransmission, making it ideal for applications requiring high reliability, such as web browsing and file transfer. On the other hand, UDP provides connectionless communication with minimal overhead, making it suitable for applications like streaming media and online gaming, where real-time transmission is critical.
In conclusion, the Transport Layer plays a pivotal role in facilitating communication between devices in a network, offering essential services such as segmentation, flow control, and error detection to ensure efficient and reliable data transmission.
Data Link Layer
The Data Link Layer is the second layer of the OSI model and is responsible for transferring data between adjacent network nodes in a network segment. It ensures that data is transmitted error-free across the physical layer and provides services such as framing, physical addressing, error detection, and flow control.
One of the key functions of the Data Link Layer is to divide the data it receives from the Network Layer into frames for transmission over the network. These frames typically include a header and a trailer, which contain control information like source and destination addresses, sequence numbers, error-checking codes, and more.
Another important aspect of the Data Link Layer is physical addressing, where devices on the same network segment are identified using MAC addresses. These addresses are used by the layer to deliver data to the correct destination within the local network.
Error detection is crucial in the Data Link Layer to ensure data integrity during transmission. Various techniques like cyclic redundancy check (CRC) are used to detect errors in data frames, allowing for retransmission if errors are found.
Flow control is also managed by the Data Link Layer to regulate the flow of data between devices to prevent congestion and ensure smooth data transmission.
Overall, the Data Link Layer plays a critical role in ensuring reliable and efficient communication between devices within a network segment, making it a fundamental component of network communication protocols.
Application Layer
The application layer is a crucial component of the OSI (Open Systems Interconnection) model, serving as the interface between the end user and the network. This layer enables communication between various applications and ensures that data is transmitted accurately and efficiently across different networks.
At the application layer, users interact directly with software applications such as web browsers, email clients, and file transfer protocols (FTP). These applications rely on specific protocols to establish communication and exchange data over the network.
One of the key functions of the application layer is to provide a platform-independent interface for applications to communicate with the underlying network. This abstraction allows developers to focus on the functionality of their applications without worrying about the underlying network infrastructure.
Another important aspect of the application layer is its support for various application-level protocols, including HTTP (Hypertext Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and FTP (File Transfer Protocol). These protocols define the rules and conventions for data exchange between different applications.
Additionally, the application layer is responsible for data formatting, encryption, and compression, ensuring that data is transmitted securely and efficiently over the network. It also manages tasks such as authentication, authorization, and session management to ensure the integrity and security of the communication process.
In summary, the application layer plays a critical role in facilitating communication between applications and networks, providing a platform for seamless data exchange while ensuring security and reliability. Its protocols and services form the backbone of modern networking applications, enabling the interconnectedness of devices and systems across the globe.
Internet Layer
The Internet Layer, also known as the Network Layer, is a crucial component of the TCP/IP protocol suite. It resides above the Link Layer and below the Transport Layer in the OSI model. This layer is responsible for the logical addressing of devices within a network and facilitating the routing of data packets from the source to the destination across different networks.
One of the key functions of the Internet Layer is to define the logical addressing scheme, such as IP addresses, which uniquely identify each device on a network. These addresses are essential for devices to communicate with each other over the internet. The Internet Layer adds a header to the data received from the Transport Layer, encapsulating it into packets known as IP packets.
Routing is another vital function of the Internet Layer. When a device sends out data packets, the Internet Layer examines the destination IP address and determines the most efficient path to deliver the packets. This process involves routers, which make decisions based on routing algorithms and tables to forward the packets towards their intended destinations.
The Internet Layer also handles fragmentation and reassembly of packets if the data to be transmitted is too large to fit in a single packet. By breaking down the data into smaller units, the Internet Layer ensures efficient transmission and reassembles the packets at the receiving end.
In conclusion, the Internet Layer plays a fundamental role in enabling communication between devices on different networks. It ensures that data packets are routed accurately and delivered to their destinations, forming the backbone of modern internet communication.
0 notes
Text
can you trust vpn services
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you trust vpn services
VPN encryption protocols
VPN encryption protocols are crucial components of virtual private networks (VPNs), ensuring the security and privacy of users' online activities. These protocols establish the framework for encrypting data as it travels between the user's device and the VPN server, protecting it from interception by malicious actors or unauthorized entities.
One of the most widely used VPN encryption protocols is OpenVPN. OpenVPN is an open-source protocol known for its robust security features and flexibility. It utilizes OpenSSL encryption libraries to encrypt data with either the OpenSSL library's default cipher algorithms or user-selected algorithms. OpenVPN supports various authentication methods and can operate over both UDP (User Datagram Protocol) and TCP (Transmission Control Protocol) connections, making it versatile and adaptable to different network configurations.
Another popular VPN encryption protocol is IPSec (Internet Protocol Security). IPSec operates at the network layer of the OSI model and can be implemented in two modes: Transport mode and Tunnel mode. In Transport mode, only the payload of the IP packet is encrypted, while in Tunnel mode, the entire IP packet, including the header, is encrypted. IPSec employs cryptographic algorithms such as AES (Advanced Encryption Standard) for encryption and HMAC (Hash-based Message Authentication Code) for authentication, providing strong security for VPN connections.
Additionally, L2TP/IPSec (Layer 2 Tunneling Protocol/Internet Protocol Security) is a commonly used protocol for VPNs, combining the features of L2TP and IPSec to establish secure tunnels for data transmission. While L2TP itself does not provide encryption, when combined with IPSec, it creates a secure encrypted connection.
In conclusion, VPN encryption protocols like OpenVPN, IPSec, and L2TP/IPSec play a crucial role in safeguarding the privacy and security of users' online communications. By encrypting data transmitted over VPN connections, these protocols help prevent unauthorized access and protect sensitive information from interception.
VPN privacy policies
VPN privacy policies are a critical aspect to consider when choosing a Virtual Private Network (VPN) service. These policies outline how the VPN provider collects, uses, and protects user data. Understanding these policies is essential for ensuring your online privacy and security.
One key aspect of VPN privacy policies is data logging. Some VPN providers may keep logs of user activity, including websites visited, files downloaded, and IP addresses used. This information can potentially be traced back to individual users and compromise their privacy. However, reputable VPN services often have strict no-logs policies, meaning they do not collect any user data whatsoever. Opting for a VPN with a no-logs policy can significantly enhance your privacy and anonymity online.
Another important consideration is data encryption. A reliable VPN will use strong encryption protocols to safeguard your internet traffic from interception by third parties, such as hackers or government agencies. Look for VPN providers that utilize advanced encryption algorithms like AES-256, which is widely regarded as highly secure.
Additionally, VPN privacy policies should clarify how the provider handles legal requests for user data. In some jurisdictions, VPN companies may be required to comply with government subpoenas or warrants, potentially compromising user privacy. Transparent policies regarding data disclosure and user notification can help users make informed decisions about their privacy risks.
Lastly, it's crucial to review a VPN provider's jurisdiction. Some countries have strict data retention laws or are part of international surveillance alliances, posing potential risks to user privacy. Choosing a VPN based in a privacy-friendly jurisdiction can help mitigate these risks.
In conclusion, carefully reviewing VPN privacy policies is essential for safeguarding your online privacy. By selecting a VPN service with a commitment to user privacy, strict no-logs policies, robust encryption, and a favorable jurisdiction, you can enjoy enhanced privacy and security while browsing the internet.
VPN user reviews
VPN user reviews play a crucial role in helping individuals make informed decisions when selecting a Virtual Private Network (VPN) service. These reviews provide valuable insights into the performance, reliability, and overall user experience of different VPN providers.
By reading VPN user reviews, potential customers can get a sense of the speed and connectivity of the service, as well as its ability to bypass geo-restrictions and provide a secure online browsing experience. Users often share their experiences with streaming services, online gaming, and torrenting to give others an idea of how well the VPN performs for various activities.
Additionally, user reviews often highlight customer support experiences, pricing plans, and the user-friendliness of the VPN applications. This information is valuable for individuals looking for a VPN that not only offers robust security features but also excellent customer service and easy-to-use interfaces.
It is important to note that while VPN user reviews can be insightful, they should be considered alongside expert reviews and recommendations from reputable sources. This comprehensive approach ensures that individuals can make well-rounded decisions when choosing a VPN service that best suits their needs.
In conclusion, VPN user reviews are a valuable resource for anyone looking to invest in a VPN service. By reading and analyzing user feedback, individuals can gain a better understanding of what to expect from a particular VPN provider and make an informed choice to enhance their online privacy and security.
VPN security audits
VPN Security Audits: Ensuring Online Privacy and Protection
In an era where digital privacy is increasingly under threat, Virtual Private Networks (VPNs) have emerged as essential tools for safeguarding online security and anonymity. However, not all VPN services are created equal, and users need assurance that the VPN they trust is truly secure. This is where VPN security audits play a crucial role.
VPN security audits involve comprehensive evaluations of a VPN provider's infrastructure, protocols, and policies to assess its security and privacy capabilities. These audits are typically conducted by independent third-party firms specializing in cybersecurity. By scrutinizing various aspects of a VPN service, including its encryption methods, data logging practices, and server infrastructure, these audits provide users with valuable insights into the reliability and trustworthiness of the VPN.
One of the primary objectives of VPN security audits is to identify any vulnerabilities or weaknesses in the VPN's security architecture. This includes assessing the strength of encryption algorithms used to protect data transmission and storage, as well as evaluating the VPN's adherence to best practices in network security.
Additionally, VPN security audits examine the provider's logging policies to determine whether they collect any personally identifiable information (PII) or browsing activity from users. A trustworthy VPN should have a strict no-logs policy, ensuring that user data remains private and anonymous at all times.
Moreover, VPN security audits evaluate the geographical distribution and security measures of the VPN's server network. This helps assess the resilience of the VPN against potential attacks or breaches and ensures that users can access a reliable and secure connection from any location.
By undergoing regular security audits, VPN providers demonstrate their commitment to transparency and accountability, reassuring users of their dedication to protecting their online privacy and security. For users seeking a reliable VPN service, looking for providers that have undergone independent security audits can provide peace of mind and confidence in their choice of protection against cyber threats.
VPN provider reputation
Maintaining a sterling reputation is paramount for VPN (Virtual Private Network) providers in today's digital landscape. With cyber threats looming large and privacy concerns at an all-time high, consumers are increasingly turning to VPN services to safeguard their online activities. However, not all VPN providers are created equal, and their reputation plays a pivotal role in attracting and retaining customers.
A VPN provider's reputation hinges on several key factors. Firstly, trustworthiness is non-negotiable. Users entrust VPNs with their sensitive data, expecting it to be shielded from prying eyes. Any breach of trust, be it through data leaks or questionable privacy policies, can irreparably tarnish a provider's reputation.
Performance is another critical aspect. A reputable VPN should offer reliable and high-speed connections, ensuring seamless browsing, streaming, and downloading experiences for users. Any downtime or sluggish performance can quickly erode trust and lead to negative reviews.
Transparency and accountability are also vital. Users appreciate VPN providers that are upfront about their logging practices, encryption standards, and data handling procedures. Any opacity or ambiguity in these areas can raise red flags and cast doubt on a provider's credibility.
Moreover, customer support plays a pivotal role in shaping a VPN provider's reputation. Prompt and knowledgeable support staff can resolve issues swiftly, enhancing user satisfaction and fostering positive word-of-mouth recommendations.
Lastly, a history of security incidents or controversies can significantly damage a VPN provider's reputation. Whether it's involvement in data scandals or allegations of collaboration with government surveillance programs, such incidents undermine trust and credibility.
In conclusion, a VPN provider's reputation is a delicate yet crucial asset in today's cybersecurity landscape. By prioritizing trustworthiness, performance, transparency, customer support, and security, VPN providers can build and maintain a solid reputation, earning the confidence of discerning users seeking privacy and protection online.
0 notes
Text
what vpn protocol should i use
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what vpn protocol should i use
OpenVPN
OpenVPN: A Secure Solution for Remote Access
In today's interconnected world, remote access to corporate networks and sensitive data is a necessity. However, ensuring the security and privacy of this access is paramount. Enter OpenVPN, a robust and open-source virtual private network (VPN) solution that offers a secure and flexible way to connect to remote networks.
OpenVPN operates on the principle of tunneling, which encapsulates data in a secure encrypted tunnel, safeguarding it from prying eyes. This encryption ensures that even if data is intercepted, it remains unreadable to unauthorized users. Additionally, OpenVPN utilizes industry-standard encryption protocols like OpenSSL to provide strong cryptographic security.
One of the key advantages of OpenVPN is its versatility. It can be deployed on various platforms, including Windows, macOS, Linux, iOS, and Android, making it accessible to a wide range of users. Moreover, OpenVPN supports both TCP and UDP protocols, allowing it to adapt to different network configurations and performance requirements.
Another notable feature of OpenVPN is its scalability. Whether you're a small business with a handful of users or a large enterprise with thousands of employees, OpenVPN can accommodate your needs. Its client-server architecture allows for easy management and administration, enabling organizations to scale their VPN infrastructure as their requirements evolve.
Furthermore, OpenVPN offers advanced security features such as multi-factor authentication (MFA), certificate-based authentication, and dynamic IP address assignment, enhancing the overall security posture of remote access solutions.
In conclusion, OpenVPN is a reliable and secure solution for remote access, offering flexibility, scalability, and advanced security features. Whether you're a business looking to provide secure remote access to your employees or an individual seeking to protect your online privacy, OpenVPN is a powerful tool that can meet your needs effectively.
IPSec
IPSec, or Internet Protocol Security, is a protocol suite designed to secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet within a communication session. It effectively protects data transferred between two devices, ensuring confidentiality, integrity, and authenticity. IPSec operates at the network layer, making it transparent to applications and higher-level protocols.
There are two main components of IPSec: Authentication Header (AH) and Encapsulating Security Payload (ESP). AH provides authentication and integrity checking, ensuring that data has not been tampered with in transit. On the other hand, ESP offers encryption to protect the confidentiality of the transmitted information.
IPSec can be implemented in two modes: Transport mode and Tunnel mode. In Transport mode, only the payload of the IP packet is encrypted and/or authenticated, while in Tunnel mode, the entire IP packet is secured. This flexibility allows IPSec to meet the diverse security requirements of different network configurations.
One of the key advantages of IPSec is its interoperability with various network devices and operating systems. It provides a standardized framework for secure communication over the Internet, making it a popular choice for virtual private network (VPN) implementations.
Overall, IPSec plays a crucial role in ensuring secure data transmission over IP networks. By leveraging encryption and authentication mechanisms, IPSec helps organizations protect their sensitive information from unauthorized access and tampering. It is a fundamental tool in the cybersecurity toolkit, enhancing the privacy and security of online communications.
L2TP/IPsec
Title: Understanding L2TP/IPsec: A Secure Tunneling Protocol for Enhanced Privacy
L2TP/IPsec, short for Layer 2 Tunneling Protocol with IP Security, is a powerful combination of two protocols that provides a secure and private means of transmitting data over the internet. Originally developed by Microsoft and Cisco, L2TP/IPsec has become a widely adopted standard for creating virtual private networks (VPNs) due to its robust security features and compatibility with various devices and operating systems.
At its core, L2TP is responsible for creating the tunnel through which data is transmitted. It does this by encapsulating the data packets within IP packets, allowing them to traverse the internet securely. However, L2TP itself does not provide any encryption, which is where IPsec comes into play.
IPsec, or Internet Protocol Security, is a suite of protocols that ensures the confidentiality, integrity, and authenticity of data transmitted over an IP network. It achieves this by encrypting the data packets before they are sent and decrypting them upon arrival at their destination. Additionally, IPsec includes mechanisms for verifying the identity of the sender and ensuring that the data has not been tampered with during transit.
When used together, L2TP and IPsec create a highly secure VPN connection that is resistant to eavesdropping, interception, and tampering. This makes it an ideal choice for businesses and individuals who require a secure means of accessing sensitive information or communicating over public networks.
Furthermore, L2TP/IPsec is supported by most modern operating systems and devices, including Windows, macOS, iOS, and Android, making it easy to implement and use across a variety of platforms. Whether you're working remotely, accessing corporate resources, or simply browsing the web, L2TP/IPsec offers peace of mind by keeping your data safe from prying eyes.
SSTP
SSTP, which stands for Secure Socket Tunneling Protocol, is a highly secure VPN protocol that provides a secure and encrypted connection between a user's device and a remote server. Introduced by Microsoft, SSTP uses SSL 3.0 to secure the communication channel, making it an excellent choice for users who prioritize data security and privacy.
One of the key advantages of SSTP is its ability to pass through most firewalls and proxy servers effortlessly. This makes it a reliable option for users in restrictive network environments, such as workplaces or public Wi-Fi hotspots, where other VPN protocols may be blocked.
Another benefit of SSTP is its compatibility with a wide range of devices and operating systems, including Windows, Linux, macOS, iOS, and Android. This flexibility allows users to secure their internet connections across various platforms without compromising on security.
In terms of security, SSTP offers strong encryption, making it difficult for hackers or third parties to intercept user data. By creating a secure tunnel for data transmission, SSTP helps protect sensitive information such as passwords, financial details, and personal messages from potential cyber threats.
Overall, SSTP is a robust VPN protocol that combines strong security features with ease of use and compatibility. Whether you are looking to secure your online activities, access geo-restricted content, or protect your data while using public Wi-Fi, SSTP is a reliable choice that prioritizes your privacy and security.
WireGuard
WireGuard is a cutting-edge VPN (Virtual Private Network) protocol that is rapidly gaining popularity for its simplicity, speed, and security features. Unlike traditional VPN protocols, such as OpenVPN and IPsec, WireGuard is built with modern cryptographic techniques aiming to provide a faster and more secure connection.
One of the key advantages of WireGuard is its lightweight code base, making it easier to review for potential vulnerabilities and audit for security issues. This simplicity results in better performance, as WireGuard can establish connections faster than its predecessors.
Another benefit of WireGuard is its state-of-the-art encryption. It uses Noise Protocol Framework, which provides forward secrecy, ensuring that past communication cannot be decrypted even if the private key is compromised in the future. Additionally, WireGuard supports multiple cryptographic algorithms, allowing users to customize their security settings according to their needs.
In terms of usability, WireGuard is designed to be user-friendly while remaining highly efficient. Its configuration is straightforward, making it easy to set up on various platforms, including Linux, Windows, macOS, iOS, and Android.
Overall, WireGuard represents a significant advancement in the field of VPN technology. Its speed, robust security features, and user-friendly design make it a compelling choice for individuals and businesses looking to enhance their online privacy and security. It is certainly worth considering for anyone seeking a reliable and efficient VPN solution.
0 notes
Text
what is udp in vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is udp in vpn
UDP protocol explanation
UDP, or User Datagram Protocol, is a core protocol of the Internet Protocol (IP) suite. It is a connectionless protocol that operates on the transport layer, providing a way for applications to send short messages, known as datagrams, across the network. UDP is widely used for tasks that require speed and efficiency, such as audio and video streaming, online gaming, and DNS lookups.
Unlike TCP (Transmission Control Protocol), UDP does not establish a connection before sending data or guarantee the delivery of packets. This lack of overhead makes UDP faster but less reliable than TCP. Applications using UDP must handle issues like packet loss, duplication, and out-of-order delivery on their own.
UDP packets consist of a header and data payload. The header includes source and destination port numbers, packet length, and a checksum for error detection. The simplicity of UDP makes it lightweight and ideal for real-time applications where speed is crucial.
One key feature of UDP is its stateless nature, meaning each packet is handled independently. While this allows for fast communication, it also means there is no built-in mechanism for flow control or error recovery.
Overall, UDP is a valuable protocol for applications that prioritize speed and efficiency over reliability. Understanding its characteristics and limitations is essential for network administrators and developers working with real-time communication and data transfer on the Internet.
VPN communication protocols
VPN communication protocols are essential for ensuring secure and private online connections. These protocols are the set of rules that govern data transmission between a user's device and the VPN server. Understanding the different VPN communication protocols can help users make informed decisions about their online privacy and security.
One of the most common VPN protocols is OpenVPN, known for its strong security features and flexibility. It uses the OpenSSL library and supports a variety of encryption algorithms, making it a popular choice among users looking for a reliable and secure connection.
Another widely used protocol is IPSec (Internet Protocol Security), which operates at the network layer of the OSI model. IPSec provides strong security through encryption and authentication methods, making it ideal for securing communication between networks.
L2TP (Layer 2 Tunneling Protocol) is another popular VPN protocol that doesn't provide encryption on its own but is often combined with IPSec to enhance security. Its built-in support on most operating systems makes it a convenient choice for users seeking a balance between security and speed.
In contrast, PPTP (Point-to-Point Tunneling Protocol) is an older protocol known for its fast connection speeds but weaker security compared to newer protocols. While it may be suitable for streaming or bypassing geo-restrictions, it is generally not recommended for sensitive data transmission due to its vulnerabilities.
Understanding the strengths and weaknesses of different VPN communication protocols can help users choose the most suitable option based on their security and speed requirements. By selecting the right protocol, users can enjoy a safer and more private online experience.
UDP vs TCP in VPN
When it comes to Virtual Private Networks (VPNs), users often encounter the choice between User Datagram Protocol (UDP) and Transmission Control Protocol (TCP). Both protocols serve as the backbone for data transmission over networks, but they differ significantly in their approach and suitability for VPN use.
UDP, known for its speed and efficiency, operates on a connectionless basis, meaning it doesn't establish a direct connection before sending data. This characteristic makes UDP ideal for real-time applications like video streaming and online gaming, where speed is crucial. In a VPN context, UDP's lightweight nature allows for faster transmission of data packets, making it suitable for activities requiring quick response times, such as VoIP calls or video conferencing.
On the other hand, TCP is a connection-oriented protocol, ensuring reliability through features like error detection, retransmission of lost packets, and congestion control. While TCP's thoroughness adds a layer of security and robustness to data transmission, it also introduces overhead and can be slower compared to UDP. In a VPN setting, TCP is often preferred for tasks where data integrity and accuracy are paramount, such as file transfers or accessing sensitive information.
Choosing between UDP and TCP in a VPN depends on the specific requirements of the user. For activities prioritizing speed and responsiveness, UDP is the preferred option. Conversely, tasks demanding guaranteed delivery and error correction may benefit from TCP's reliability. Some VPN providers offer both protocols, allowing users to switch between them based on their needs and preferences.
Ultimately, the decision between UDP and TCP boils down to a balance between speed and reliability, with users weighing their priorities to optimize their VPN experience.
VPN encryption methods
VPN encryption methods are an essential component of ensuring secure and private online communications. When data is transmitted over the internet through a Virtual Private Network (VPN), encryption is used to protect it from unauthorized access and surveillance.
There are several encryption methods commonly used by VPN providers to safeguard user data. One of the most widely used protocols is the OpenVPN protocol, which employs the OpenSSL library and provides strong security through various cryptographic algorithms. OpenVPN is known for its flexibility and ability to work effectively across different platforms.
Another popular encryption method is the Internet Protocol Security (IPsec) protocol, which operates at the network layer to secure data transmitted over a network. IPsec can be used in tunnel mode to encrypt the entire IP packet or in transport mode to encrypt the data portion of the packet.
Transport Layer Security (TLS) is also utilized by VPN services to encrypt data during transmission. TLS is commonly used in web browsers for securing online transactions and communication, and its implementation in VPNs adds an extra layer of protection for user data.
Additionally, Secure Socket Layer (SSL) encryption is often integrated into VPN services to establish a secure connection between the user's device and the VPN server. SSL encryption helps prevent unauthorized access and eavesdropping on the data being transmitted.
In conclusion, VPN encryption methods play a crucial role in maintaining online privacy and security. By utilizing robust encryption protocols such as OpenVPN, IPsec, TLS, and SSL, VPN users can safeguard their data against potential threats and cyberattacks.
VPN performance optimization
Title: Enhancing VPN Performance: Tips for Optimal Speed and Security
In today's interconnected digital landscape, Virtual Private Networks (VPNs) have become indispensable tools for safeguarding online privacy and security. However, while VPNs offer an added layer of protection, they can sometimes lead to a noticeable decrease in internet speed due to various factors such as server congestion, encryption protocols, and network limitations. To ensure optimal VPN performance without compromising on security, here are some effective strategies to consider:
Choose the Right Server: The proximity of the VPN server to your physical location can significantly impact connection speed. Opt for a server that is geographically closer to your location to minimize latency and maximize performance.
Select the Fastest Protocol: VPN protocols like OpenVPN, L2TP/IPsec, and IKEv2/IPsec offer different levels of encryption and speed. Experiment with different protocols to find the one that strikes the best balance between security and performance for your needs.
Utilize Split Tunneling: Split tunneling allows you to route only specific traffic through the VPN while directing the rest of your internet traffic through your regular connection. This can help alleviate congestion and improve overall speed for non-sensitive activities.
Update VPN Software: Ensure that you are using the latest version of your VPN software, as updates often include performance optimizations and bug fixes that can enhance speed and stability.
Optimize Device Settings: Adjusting settings such as MTU (Maximum Transmission Unit) size and TCP/IP parameters on your device can help improve VPN performance by optimizing data transmission efficiency.
Upgrade Your Internet Connection: A faster internet connection from your ISP can complement VPN usage, resulting in smoother and more consistent performance.
By implementing these tips, users can experience a noticeable improvement in VPN performance without compromising on the security and privacy benefits that VPNs provide. Remember that while speed is important, it should never come at the expense of security, so always prioritize a balance between the two for a seamless online experience.
0 notes
Text
does a vpn get past a strict nat type
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn get past a strict nat type
VPN NAT traversal
VPN NAT traversal refers to the ability of a Virtual Private Network (VPN) connection to securely navigate through Network Address Translation (NAT) devices. NAT devices are commonly used to map private IP addresses of devices within a local network to a single public IP address. While NAT enhances security and conserves IP addresses, it can pose challenges for VPN connections as it modifies the IP headers of packets, impacting their ability to reach the intended destination.
To overcome NAT restrictions, VPN NAT traversal techniques such as encapsulating VPN traffic within standard web traffic (HTTPS) or User Datagram Protocol (UDP) packets are used. These methods enable VPN traffic to emulate regular internet traffic, making it easier to pass through NAT devices without being detected or blocked.
Additionally, VPN protocols like Internet Key Exchange version 2 (IKEv2), Secure Socket Tunneling Protocol (SSTP), and Datagram Transport Layer Security (DTLS) are designed with NAT traversal capabilities. These protocols utilize techniques like UDP encapsulation, TCP port multiplexing, and keep-alive mechanisms to ensure successful VPN connectivity even in NAT-constrained environments.
VPN NAT traversal is crucial for establishing secure and reliable VPN connections in scenarios where NAT devices are present, such as in home networks, public Wi-Fi hotspots, and corporate environments. By utilizing innovative techniques and protocols, VPN providers can offer seamless connectivity and enhanced privacy to users, regardless of the network environment they are accessing the internet from.
VPN bypass NAT
Title: Understanding VPN Bypass NAT: How It Works and Its Benefits
VPN (Virtual Private Network) technology has become increasingly popular for securing internet connections and safeguarding online privacy. However, users often encounter challenges when trying to establish VPN connections from behind a NAT (Network Address Translation) device. NAT devices, commonly found in home routers and corporate networks, can interfere with VPN traffic, causing connectivity issues. To overcome this obstacle, VPN bypass NAT techniques have been developed.
VPN bypass NAT involves configuring the VPN client and server to encapsulate VPN traffic within standard internet protocols, such as TCP (Transmission Control Protocol) or UDP (User Datagram Protocol). By doing so, VPN traffic appears similar to regular internet traffic to NAT devices, allowing it to traverse the network without being blocked or altered.
One common method used for VPN bypass NAT is VPN over TCP or UDP port 443, which is typically reserved for HTTPS traffic. Since port 443 is commonly allowed through firewalls and NAT devices for secure web browsing, encapsulating VPN traffic within this port can often bypass restrictions.
Another approach is to utilize VPN protocols that are specifically designed to bypass NAT, such as SSTP (Secure Socket Tunneling Protocol) or IKEv2 (Internet Key Exchange version 2). These protocols employ techniques like port multiplexing and packet encapsulation to ensure VPN traffic can traverse NAT devices seamlessly.
The benefits of VPN bypass NAT are significant for users and organizations alike. By enabling VPN connections to bypass NAT, users can enjoy uninterrupted access to VPN services, even when behind restrictive network environments. This ensures secure communication and data privacy, essential for remote work, accessing geo-restricted content, and protecting sensitive information.
In conclusion, VPN bypass NAT techniques play a crucial role in ensuring seamless VPN connectivity in environments with NAT devices. By understanding how these techniques work and their benefits, users can maximize the effectiveness of VPN technology for safeguarding their online activities and data privacy.
VPN NAT type restriction
Title: Understanding VPN NAT Type Restrictions: What You Need to Know
VPN (Virtual Private Network) services are essential tools for safeguarding online privacy and security. However, users may encounter NAT (Network Address Translation) type restrictions when using VPNs, which can affect their online experience.
NAT is a process used to modify network address information in packet headers while they are in transit across a network. It allows multiple devices on a network to share a single public IP address. NAT type restrictions occur when a VPN service employs NAT to manage its network traffic, resulting in limitations for users.
One common NAT type restriction is encountered in online gaming. Many online gaming platforms require specific NAT types for optimal connectivity. When using a VPN with NAT type restrictions, gamers may experience issues such as slower connection speeds, lag, or difficulty connecting to game servers.
Another scenario where NAT type restrictions impact users is in peer-to-peer (P2P) file sharing. Some VPN providers restrict NAT types to prevent abuse or illegal activities over their networks. As a result, users may find that their ability to share files via P2P networks is limited or blocked entirely when using certain VPN services.
To avoid NAT type restrictions, users can opt for VPN providers that offer dedicated IP addresses or port forwarding capabilities. These features allow users to bypass NAT limitations and enjoy unrestricted access to online services.
In conclusion, while VPNs are powerful tools for enhancing online privacy and security, users should be aware of potential NAT type restrictions that may impact their online activities. By choosing VPN providers with suitable features and configurations, users can mitigate these restrictions and enjoy a seamless online experience.
VPN NAT firewall
A VPN NAT firewall, a combination of two powerful tools - Virtual Private Network (VPN) and Network Address Translation (NAT) firewall, serves as a robust shield against online threats while ensuring privacy and security for users.
Firstly, let's understand the role of a VPN. A VPN encrypts your internet connection, making it virtually impossible for anyone to intercept your data. It masks your IP address, replacing it with one from the VPN server, thereby enhancing your online anonymity and privacy. By encrypting your data traffic, a VPN prevents hackers, government agencies, or even your internet service provider from snooping on your online activities.
Now, let's delve into the NAT firewall aspect. Network Address Translation (NAT) firewall works by mapping multiple private IP addresses to a single public IP address. It acts as a barrier between your internal network and the internet, filtering incoming and outgoing traffic. NAT firewall adds an extra layer of security by inspecting packets of data and blocking any suspicious or unauthorized access attempts.
Combining these two technologies, a VPN NAT firewall offers comprehensive protection against various online threats such as hacking, identity theft, malware attacks, and more. It encrypts your internet traffic, hides your real IP address, and filters incoming and outgoing data packets, effectively thwarting any potential cyber threats.
Moreover, a VPN NAT firewall also allows users to bypass geo-restrictions and access region-locked content by masking their IP address with one from a different location. This feature is particularly useful for streaming enthusiasts who wish to enjoy their favorite shows or movies from anywhere in the world.
In conclusion, a VPN NAT firewall is a vital tool for safeguarding your online privacy and security in today's digital age. It offers a robust defense mechanism against cyber threats while providing users with the freedom to access the internet securely and anonymously.
VPN NAT blocking
VPN NAT blocking, also known as Network Address Translation blocking, occurs when a Virtual Private Network (VPN) is unable to establish a connection due to conflicts with NAT protocols. NAT is a process used by routers to modify network address information in packet headers while they are in transit, typically to allow multiple devices within a local network to share a single public IP address.
When a VPN encounters NAT blocking, it's usually because the NAT device or router is not properly configured to allow VPN traffic to pass through. This can happen for various reasons, including strict security settings or outdated firmware.
NAT blocking can manifest in different ways, such as the inability to connect to the VPN server, frequent disconnections, or slow connection speeds. It can be frustrating for users who rely on VPNs for privacy, security, and unrestricted access to online content.
To resolve VPN NAT blocking issues, several steps can be taken:
Port Forwarding: Configuring the NAT device to forward VPN traffic to the appropriate internal IP address can often resolve the issue.
VPN Passthrough: Enabling VPN passthrough on the router allows VPN traffic to bypass the NAT process.
Updating Firmware: Ensuring that routers and other network devices have the latest firmware can address compatibility issues that may cause NAT blocking.
Adjusting Firewall Settings: If a firewall is blocking VPN traffic, adjusting the settings to allow VPN connections can help.
Using a Different VPN Protocol: Switching to a VPN protocol that is less likely to be affected by NAT blocking, such as OpenVPN or IKEv2/IPSec, may provide a solution.
By understanding the causes and potential solutions for VPN NAT blocking, users can troubleshoot connectivity issues and enjoy a seamless VPN experience.
0 notes
Text






— jurdan headers. 👑
like/reblog if you save or use.
#jurdan#jurdan header#jurdan headers#the cruel prince#the cruel prince header#the cruel prince headers#the queen of nothing#tcp headers#tcp header#tcp#ttpd#the tortured poets department headers#booktwt#bookstan#booktwitter#book headers#book quotes#jude duarte header#jude duarte headers#jude duarte#cardan greenbriar header#cardan header#cardan headers#cardan greenbriar#jude x cardan#prince cardan
104 notes
·
View notes
Text
thinking about how jude duarte literally played "kiss, marry, kill" with cardan's friendgroup
#should've kissed nicasia tbh#fanart#books#bookworm#incorrect the cruel prince#the cruel prince memes#the cruel prince#jude duarte#jude fanart#jude duarte headers#jude duarte fanart#tcp#the folk of the air#tfotaedit#tfota fanart#tfota memes#tfota#jude and cardan#jude x cardan#cardan greenbriar#cardan fanart#prince cardan#book quote#holly black#fantasy books#book review#new books#booklover#jurdan#jurdan fanart
465 notes
·
View notes
Text
does a vpn block torrent
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn block torrent
VPN Torrent Blocking Mechanisms
VPN Torrent Blocking Mechanisms Explained
In the world of torrenting, VPNs (Virtual Private Networks) serve as indispensable tools for ensuring privacy, security, and anonymity. However, the cat-and-mouse game between VPNs and entities seeking to block torrent traffic is ongoing. Understanding the mechanisms behind VPN torrent blocking can help users navigate this landscape more effectively.
Deep Packet Inspection (DPI): DPI is a method used by ISPs (Internet Service Providers) and network administrators to inspect data packets as they pass through the network. By analyzing packet headers and payloads, DPI can identify and block torrent traffic, even when it's encrypted within a VPN tunnel.
Port Blocking: Torrent clients typically communicate over specific ports, such as TCP port 6881. ISPs can block these ports to prevent torrent traffic from flowing through their networks. While VPNs can help bypass port blocking by encapsulating torrent traffic within different ports, sophisticated ISPs may employ DPI to detect and block such evasion attempts.
Protocol Blocking: Some ISPs may employ protocol-specific blocking to target torrent traffic. For instance, they may identify and block the BitTorrent protocol, making it challenging for users to connect to torrent peers. VPNs can mitigate this by encrypting torrent traffic, making it indistinguishable from other types of data.
Traffic Shaping: ISPs may implement traffic shaping techniques to deprioritize or throttle torrent traffic, leading to slower download speeds. While VPNs can help mitigate the impact of traffic shaping by encrypting data, users may still experience slower speeds during peak hours or in networks with aggressive traffic management policies.
Geo-blocking: Some content providers enforce geo-blocking to restrict access to certain torrents based on the user's geographical location. VPNs can bypass geo-blocks by allowing users to connect to servers in different countries, thus appearing as if they're accessing the internet from a different location.
In conclusion, while VPNs offer valuable protection for torrent users, understanding the various blocking mechanisms employed by ISPs and other entities is crucial for maintaining reliable and secure torrenting experiences. By staying informed and employing appropriate countermeasures, users can continue to enjoy the benefits of torrenting while minimizing the risks.
VPN Encryption Impact on Torrent Access
VPN Encryption Impact on Torrent Access
When it comes to accessing and downloading torrents, using a Virtual Private Network (VPN) can have a significant impact on both security and accessibility. VPNs work by encrypting your internet connection and routing it through a remote server, masking your IP address and making your online activities virtually anonymous.
In the realm of torrenting, VPN encryption plays a crucial role in protecting your privacy and security. By hiding your real IP address, a VPN prevents your internet service provider (ISP) and other third parties from monitoring your torrenting activities. This added layer of privacy ensures that your downloading habits remain confidential and reduces the risk of legal repercussions.
Moreover, VPN encryption can also help bypass geographical restrictions and censorship that may hinder your access to certain torrent websites or content. By connecting to a VPN server in a different country, you can circumvent these restrictions and gain access to a wider range of torrents.
However, it's essential to choose a VPN provider that offers strong encryption protocols and does not keep logs of your online activities. Opting for a reputable VPN service with robust security measures will ensure that your torrenting experience remains safe and private.
In conclusion, VPN encryption has a positive impact on torrent access by enhancing security, protecting privacy, and overcoming geo-blocks. By utilizing a VPN while downloading torrents, you can enjoy a more secure and unrestricted online experience.
Torrent Traffic Obfuscation by VPNs
Torrent traffic obfuscation through Virtual Private Networks (VPNs) has become a crucial tool for internet users seeking to safeguard their online activities. With the rise in digital surveillance and monitoring, particularly regarding torrenting activities, VPNs offer a solution by encrypting internet traffic, making it indecipherable to third parties.
Torrenting, the process of downloading and sharing files through peer-to-peer networks, often involves copyrighted material, making it a prime target for monitoring by copyright enforcement agencies and internet service providers (ISPs). However, VPNs add an extra layer of security and anonymity by rerouting internet traffic through remote servers and encrypting it, thereby masking the user's IP address and location.
One of the primary benefits of using VPNs for torrenting is the ability to bypass geographical restrictions and censorship. By connecting to servers in different countries, users can access content that may be blocked or restricted in their region, enhancing their online freedom.
Moreover, VPNs help mitigate the risk of legal repercussions associated with torrenting copyrighted material. By encrypting traffic, VPNs prevent ISPs from monitoring and logging users' online activities, reducing the likelihood of receiving copyright infringement notices or facing legal action.
However, it's essential to choose a reputable VPN provider that prioritizes user privacy and does not keep logs of user activity. Additionally, users should ensure their VPN connection is secure and leak-proof to prevent any accidental exposure of their true IP address.
In conclusion, torrent traffic obfuscation through VPNs offers internet users a means to protect their privacy, bypass restrictions, and mitigate legal risks associated with torrenting. By encrypting internet traffic and masking IP addresses, VPNs empower users to torrent safely and anonymously in an increasingly monitored online landscape.
VPN Protocol Effectiveness against Torrenting
When it comes to torrenting, using a Virtual Private Network (VPN) can be a crucial tool to protect your online privacy and security. However, not all VPN protocols are equally effective in ensuring a safe and anonymous torrenting experience.
One of the most popular VPN protocols used for torrenting is OpenVPN. Known for its strong encryption and open-source nature, OpenVPN is considered highly secure and reliable for maintaining privacy while torrenting. It supports various encryption ciphers and can bypass most firewalls and network restrictions, making it a solid choice for torrent users.
Another commonly used VPN protocol is L2TP/IPsec. While it provides decent security, it may not be as fast or versatile as other protocols like OpenVPN. L2TP/IPsec can still offer a good level of protection for torrenting activities, but it may not be the most optimal choice for users looking for the highest level of security and performance.
Alternatively, SSTP and IKEv2 are other VPN protocols that can be effective for torrenting. SSTP is known for its ability to bypass censorship and provide strong security through its integration with SSL/TLS encryption. On the other hand, IKEv2 is praised for its speed and stability, making it a suitable option for users who prioritize performance when torrenting.
In conclusion, the effectiveness of a VPN protocol against torrenting largely depends on the user's specific needs and priorities. While OpenVPN is often recommended for its overall security and flexibility, other protocols like L2TP/IPsec, SSTP, and IKEv2 can also provide reliable protection for torrent users. It's important to choose a VPN protocol that best suits your requirements for privacy, speed, and security while torrenting.
VPN Logging Policies and Torrent Monitoring
VPN Logging Policies and Torrent Monitoring
When it comes to using a Virtual Private Network (VPN) for torrenting, understanding the logging policies of VPN providers is crucial. VPN logging policies determine what kind of user data is recorded and stored by the VPN service. If a VPN provider keeps logs of your online activities, it can potentially compromise your privacy, especially when torrenting.
Ideally, you should look for VPN providers that have a strict no-logs policy. This means that they do not monitor, record, or store any information about your online activities while using their VPN service. By opting for a VPN with a no-logs policy, you can have peace of mind knowing that your torrenting activities are not being tracked or monitored.
On the other hand, some VPN providers may keep connection logs or metadata that could potentially be used to trace your online activities back to you. These logs may include timestamps, IP addresses, and the amount of data transferred. While this information may not directly link you to specific torrent downloads, it can still pose a risk to your privacy if accessed by third parties.
Moreover, some ISPs and copyright enforcement agencies actively monitor torrent traffic to identify users who are downloading copyrighted content illegally. By using a VPN with robust encryption and a strict no-logs policy, you can mask your IP address and encrypt your internet traffic, making it harder for anyone to monitor your torrenting activities.
In conclusion, choosing a VPN provider with a transparent no-logs policy is essential for protecting your privacy while torrenting. By understanding VPN logging policies and opting for a service that prioritizes user anonymity, you can enjoy a secure and private torrenting experience without the risk of being monitored or tracked.
0 notes
Text
do you need nat for vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you need nat for vpn
NAT Explained for VPN
NAT, or Network Address Translation, plays a crucial role in understanding how VPNs, or Virtual Private Networks, work. To break it down simply, NAT is a process that allows multiple devices within a local network to share a single public IP address. This enables devices on a local network to access the internet while appearing as though they all originate from a single IP address, providing an added layer of security by masking individual device identities.
When it comes to VPNs, NAT can have important implications. VPNs create a secure and encrypted connection over a public network, like the internet, by routing traffic through a server, effectively masking the user's IP address and encrypting data for enhanced privacy and security. However, NAT can sometimes interfere with the functionality of a VPN by altering IP headers and making it harder for VPN traffic to pass through without being detected.
To overcome NAT-related challenges, VPN providers often employ techniques like NAT traversal, which helps VPN traffic pass through NAT routers smoothly by encapsulating VPN data within standard internet traffic. Additionally, VPN protocols like UDP, which is less likely to be blocked by NAT devices compared to TCP, can also enhance compatibility.
Understanding how NAT works and its impact on VPN connections is essential for ensuring a smooth and secure browsing experience. By employing appropriate techniques and protocols, users can enjoy the benefits of both NAT and VPN technologies without compromising on security or performance.
VPN without NAT Pros and Cons
When it comes to utilizing a Virtual Private Network (VPN) without Network Address Translation (NAT), there are distinct advantages and disadvantages to consider.
VPN without NAT, also known as "NAT exemption," offers enhanced security and privacy for users. By bypassing NAT, the original IP addresses of devices remain intact, making it harder for hackers to trace the connection back to the source. This heightened anonymity is especially beneficial for individuals or businesses looking to safeguard sensitive data and communications.
Furthermore, VPN without NAT can help overcome certain restrictions imposed by NAT, such as limitations on certain applications or services that require direct peer-to-peer connections. By preserving the original IP addresses, users can enjoy unrestricted access to online content and improved network performance.
On the flip side, there are some drawbacks to using a VPN without NAT. One of the main concerns is the potential risk of exposing the actual IP addresses of devices to external threats. Without the protective shield of NAT, devices may become more vulnerable to cyber attacks and unauthorized access.
Additionally, setting up a VPN without NAT can be more complex and demanding compared to traditional VPN configurations. Users may encounter difficulties in ensuring compatibility with existing network infrastructure and resolving connectivity issues.
In conclusion, VPN without NAT offers enhanced security and circumvents certain NAT limitations, but users should weigh these benefits against the potential risks and complexities involved in its implementation. Ultimately, the decision to use VPN without NAT should be based on individual security needs and technical capabilities.
NAT vs No-NAT VPN Comparison
When it comes to choosing a VPN (Virtual Private Network) service, understanding the difference between NAT (Network Address Translation) and No-NAT configurations is crucial. These two options offer distinct features and functionalities, catering to different user needs and preferences.
NAT VPN, also known as NAT-T (NAT Traversal), employs Network Address Translation to route traffic through the VPN server. In this configuration, the VPN server assigns a new IP address to the user's device, masking its original IP address. This method enhances security and privacy by obfuscating the user's identity and location. However, NAT VPNs may encounter compatibility issues with certain applications or services that rely on direct peer-to-peer connections.
On the other hand, a No-NAT VPN, as the name suggests, does not utilize Network Address Translation. Instead, it allows the user's device to maintain its original IP address while encrypting the traffic passing through the VPN tunnel. This configuration offers advantages such as improved compatibility with peer-to-peer applications and services that require direct IP connectivity. However, it may provide less anonymity compared to NAT VPNs since the user's original IP address remains visible.
In terms of performance, NAT VPNs may experience slightly slower speeds due to the additional overhead of address translation. No-NAT VPNs, on the other hand, can offer faster speeds since they do not involve this extra step.
Ultimately, the choice between NAT and No-NAT VPN depends on individual priorities. Users seeking enhanced privacy and anonymity may prefer NAT VPNs, while those prioritizing compatibility and speed might opt for No-NAT configurations. It's essential to evaluate the specific needs and requirements before selecting the appropriate VPN service.
NAT Bypass in VPN Networks
NAT (Network Address Translation) is a fundamental component of modern networking that allows multiple devices within a network to share a single public IP address. This technology poses challenges for VPN (Virtual Private Network) networks as it can hinder the establishment of direct connections between devices. However, with the advent of NAT bypass solutions, this issue can be effectively overcome.
NAT bypass in VPN networks refers to the mechanisms that enable VPN traffic to circumvent the NAT process, ensuring seamless communication between devices. By implementing NAT bypass techniques, VPN networks can maintain the confidentiality and integrity of data while optimizing connection speeds and reliability.
One common method of NAT bypass involves using specialized protocols such as NAT Traversal (NAT-T) or UDP encapsulation. These protocols encapsulate VPN traffic within UDP packets that can traverse NAT devices without modification, thus preserving end-to-end connectivity.
Additionally, VPN providers may deploy relay servers to facilitate communication between devices behind NAT barriers. These servers act as intermediaries that relay encrypted data between clients, allowing them to establish direct connections despite NAT restrictions.
Overall, NAT bypass plays a crucial role in enhancing the performance and usability of VPN networks. By leveraging innovative technologies and strategies, organizations can ensure secure and efficient communication across distributed environments, without being limited by the constraints of NAT.
NAT Traversal for VPN Configuration
Title: Understanding NAT Traversal for VPN Configuration
NAT traversal, or Network Address Translation traversal, plays a crucial role in configuring Virtual Private Networks (VPNs) across networks utilizing NAT devices. NAT, a technique used to modify network address information in packet headers while in transit, poses a challenge for VPN connections, primarily because it alters the IP addresses and ports in the packet headers, making it difficult for VPN protocols to establish connections.
In essence, NAT traversal enables VPN traffic to bypass NAT devices, ensuring seamless communication between VPN endpoints. This is particularly essential in scenarios where VPN endpoints are located behind NAT devices, such as routers or firewalls commonly found in home or corporate networks.
There are several techniques employed for NAT traversal in VPN configurations:
VPN Protocols with NAT Traversal Support: Some VPN protocols, such as IPSec (Internet Protocol Security) and L2TP/IPSec (Layer 2 Tunneling Protocol over IPSec), incorporate NAT traversal mechanisms into their design. These protocols use techniques like UDP encapsulation and NAT-Traversal (NAT-T) to traverse NAT devices successfully.
VPN Passthrough: Many NAT devices come with VPN passthrough features, which allow VPN traffic to pass through the NAT device without interference. However, this method may not always be reliable, especially for complex VPN configurations or stringent security requirements.
Port Forwarding: Another approach involves configuring port forwarding rules on the NAT device to redirect VPN traffic to the appropriate VPN endpoint. While effective, this method requires manual configuration and may pose security risks if not implemented carefully.
Third-Party NAT Traversal Solutions: In some cases, third-party NAT traversal solutions, such as STUN (Session Traversal Utilities for NAT) or TURN (Traversal Using Relays around NAT), may be employed to facilitate VPN communication across NAT devices.
By understanding and implementing NAT traversal techniques, organizations can ensure smooth and secure VPN connectivity, even in complex network environments with NAT devices. Proper configuration and adherence to best practices are essential to maintain the confidentiality, integrity, and availability of VPN communications.
0 notes
Text
don't detect my vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
don't detect my vpn
VPN detection prevention
Title: Protect Your Privacy: Effective VPN Detection Prevention Techniques
In an era where online privacy is increasingly threatened, Virtual Private Networks (VPNs) have become a popular tool for safeguarding digital anonymity. However, as VPN usage rises, so does the sophistication of methods to detect and block VPN traffic. To maintain privacy and circumvent detection, users must employ effective prevention techniques.
One approach to prevent VPN detection is by utilizing obfuscation techniques. These methods disguise VPN traffic to make it appear like regular internet traffic, thereby evading detection by network administrators or censorship systems. Obfuscation can involve encrypting VPN metadata, disguising packet headers, or even mimicking known protocols such as HTTPS.
Another strategy is to use specialized VPN protocols designed to bypass detection measures. Protocols like OpenVPN with Transmission Control Protocol (TCP) port 443, commonly used for secure web browsing (HTTPS), can make VPN traffic appear indistinguishable from regular HTTPS traffic. Similarly, protocols like WireGuard or Shadowsocks offer stealth capabilities, making VPN detection more challenging.
Furthermore, choosing VPN providers that offer a wide range of servers and regularly update their IP addresses can help prevent detection. By constantly shifting IP addresses and using servers located in multiple countries, users can avoid being flagged by detection systems that target specific IP ranges associated with VPNs.
Moreover, employing additional layers of security such as multi-hop VPN connections or integrating VPNs with Tor (The Onion Router) can enhance privacy and make VPN detection even more difficult.
In conclusion, while VPNs are powerful tools for preserving online privacy, their effectiveness can be compromised by detection methods employed by ISPs, governments, or other entities. By implementing obfuscation techniques, utilizing specialized protocols, choosing reputable VPN providers, and adding extra layers of security, users can effectively prevent VPN detection and safeguard their digital privacy.
VPN proxy evasion techniques
VPN proxy evasion techniques are utilized by individuals seeking to bypass restrictions and access restricted content online. These techniques are employed to mask the real IP address of the user and make it appear as if they are accessing the internet from a different location.
One common evasion technique is the use of virtual private networks, or VPNs. VPNs encrypt the user's internet connection and route it through a remote server, effectively hiding their IP address and location. By using a VPN, users can access geo-blocked content and surf the web anonymously.
Another popular technique is the use of proxy servers. Proxies act as intermediaries between the user and the internet, masking the user's IP address and providing access to restricted content. Users can choose from different types of proxies, such as HTTP proxies, SOCKS proxies, and transparent proxies, depending on their specific needs.
DNS tunneling is another evasion technique that can be used to bypass VPN blocks and censorship. By redirecting DNS queries through encrypted tunnels, users can circumvent restrictions and access blocked websites. This technique is often used in combination with VPNs to enhance privacy and security.
Overall, VPN proxy evasion techniques are valuable tools for individuals seeking to protect their online privacy and access restricted content. However, it is essential to use these techniques responsibly and abide by local laws and regulations regarding internet usage.
Bypass VPN detection methods
Bypassing VPN detection methods has become increasingly important as more online platforms crack down on VPN usage. Whether you're trying to access geo-blocked content, maintain privacy, or circumvent censorship, understanding how to evade VPN detection is crucial. Here are several effective techniques to bypass VPN detection:
Obfuscation: Many VPN services offer obfuscation features that disguise VPN traffic as regular HTTPS traffic. By encrypting VPN data to mimic standard web traffic, it becomes harder for detection systems to identify and block VPN usage.
Protocol Switching: Some VPN providers offer multiple protocols for connection, such as OpenVPN, IKEv2, or SSTP. Switching between protocols can help evade detection since different protocols use different methods of encapsulating and encrypting data.
Port Selection: VPN traffic typically operates on specific ports. Changing the port used by your VPN connection can help avoid detection, as some detection systems target known VPN ports for blocking or throttling.
Stealth Mode: Certain VPNs offer a stealth or camouflage mode designed specifically to bypass VPN detection. This mode disguises VPN traffic to make it appear as regular internet traffic, making it harder for detection systems to identify and block.
Split Tunneling: Split tunneling allows users to route only specific traffic through the VPN while letting other traffic go directly to the internet. By selectively routing traffic, users can bypass detection on platforms that block VPN connections.
DNS Encryption: Encrypting DNS queries helps prevent DNS leakage, which can reveal VPN usage to detection systems. Using a VPN that offers DNS encryption ensures that all DNS requests are routed through the VPN tunnel.
In conclusion, while VPN detection methods continue to evolve, there are various strategies available to bypass them effectively. By utilizing obfuscation, protocol switching, port selection, stealth mode, split tunneling, and DNS encryption, users can maintain their privacy and access restricted content without interference.
Conceal VPN usage
Using a VPN, or Virtual Private Network, can offer users increased privacy, security, and anonymity while browsing the internet. However, there may be situations where one needs to conceal their VPN usage for various reasons.
One common reason for concealing VPN usage is to bypass restrictions imposed by networks or governments. In some countries, certain websites or online services may be blocked or restricted, and using a VPN can help users access these sites. By concealing VPN usage, users can avoid detection and potential repercussions for bypassing such restrictions.
Another reason to conceal VPN usage is to prevent targeted advertising or tracking. Some internet service providers and websites collect data on users’ online activities to deliver targeted ads or monitor behavior. By using a VPN and concealing its usage, users can make it more difficult for third parties to track their online movements and serve intrusive ads.
Furthermore, concealing VPN usage may be necessary for individuals who value their online privacy and wish to keep their browsing habits confidential. Whether it’s for personal reasons or professional privacy, hiding VPN usage can provide an added layer of protection against potential breaches of sensitive information.
In conclusion, while using a VPN can enhance online security and privacy, there are instances where concealing VPN usage becomes necessary. Whether it's to bypass restrictions, avoid tracking, or safeguard personal data, being able to conceal VPN usage can empower users to navigate the digital world with increased control and anonymity.
VPN obfuscation strategies
VPN obfuscation strategies are techniques used to make VPN traffic appear as normal internet traffic, thus helping users bypass censorship and restrictions in highly regulated environments. These strategies enhance privacy, security, and anonymity by preventing third parties from detecting and blocking VPN usage.
One common obfuscation strategy is using obfuscated servers that hide VPN traffic by making it look like regular HTTPS traffic. By disguising VPN packets within encrypted HTTPS connections, it becomes challenging for network administrators to distinguish VPN traffic from standard web traffic.
Another effective obfuscation method involves the use of stealth VPN protocols such as SSTP (Secure Socket Tunneling Protocol) or OpenVPN with obfuscation features. These protocols make VPN traffic less detectable by camouflaging it to appear like normal internet traffic, thus evading deep packet inspection (DPI) used by some firewalls to block VPNs.
DNS tunneling is another obfuscation technique where DNS requests are used to encode VPN traffic. By sending data through DNS servers, users can circumvent filtering mechanisms and access blocked content without triggering alarms.
Furthermore, utilizing a combination of obfuscation techniques like XOR cipher encryption, steganography, and traffic obfuscation with the use of Tor over VPN can bolster the effectiveness of VPN obfuscation strategies, making it even more challenging for adversaries to detect and block VPN traffic.
In conclusion, VPN obfuscation strategies play a vital role in maintaining online privacy and freedom of access. By implementing these advanced techniques, users can enjoy a secure and unrestricted browsing experience while keeping their online activities private and protected from prying eyes.
0 notes