#waf panels
Text
No, Your Web Host Won’t Do Everything for You
New Post has been published on https://thedigitalinsider.com/no-your-web-host-wont-do-everything-for-you/
No, Your Web Host Won’t Do Everything for You
A great web host is a web designer’s best friend. The better the host, the easier your life will be. And trust us. Previous bad experiences can give you a greater appreciation of what you have.
But bad things can still happen. Your website might face downtime or security issues. And technical support may not be able to fix every problem. That’s OK – nobody’s perfect.
Still, we place a lot of trust in web hosts. We trust that they have our best interests in mind. And that they have fool-proof processes in place.
That could be a mistake. Assuming that everything will be perfect can bite you. It’s then that you realize you could have done more.
Here’s a look at areas where it pays to be proactive. It could save you from a disaster.
Keep Website Backups on Hand
Any web host worth their salt should back up their servers. Some providers also offer on-demand site backups via a control panel.
It’s worth taking advantage of these services. But what if something goes wrong? What if a server outage renders your backup unreachable?
Having redundant copies of your website provides peace of mind. And it enables you to move quickly in case the worst happens.
There are several ways to accomplish this. Remote backup services will store your site in the cloud. Or you could use a WordPress backup plugin that ties in with a cloud service.
How often should you run a backup? Much depends on your website. A busy eCommerce site will need more frequent backups. However, an old-school brochure site could get by with daily or weekly snapshots.
Remember to back up the entire website. That includes files and databases. It’s helpful when you only need to restore a specific component.
Stay On Top of Your Website’s Security
Web hosts work hard to keep their servers secure. It’s a non-stop pursuit that requires investment. There’s no guarantee of perfection, however.
Every website is a target. Malicious actors will use every trick in the book to get inside a system. And they’ll wreak as much havoc as possible.
Your host will try to secure things at the server level. However, you should also fortify your website. You’ll have a better chance of avoiding a malware infection.
Again, there are several avenues to take. Installing a security plugin is a step in the right direction. And keeping your content management system (CMS) updated is another. Use strong passwords and implement two-factor authorization (2FA) when possible.
Those are the basics of website security. You can go further, though. A content delivery network (CDN) with a Web Application Firewall (WAF) blocks suspicious traffic before it reaches your site.
The bottom line: don’t take security for granted. Be proactive and make your website as secure as possible.
Optimize Your Website for Performance
Websites tend to get dragged down by bloat. Things like database calls and JavaScript libraries impact performance. Calls to third-party APIs can also kill performance. Web hosts can only do so much in this area.
The cost of your hosting plays a role. Cheap hosting will have more limitations. You’ll have access to fewer CPU cycles and less memory.
But even expensive plans can’t save a poorly built site. Features like object caching and CDNs can help. Still, resource-intensive pages will be slow to load.
A solid hosting platform and an optimized website are the ideal combination. Following best practices is still important. Doing so will allow your site to take advantage of that extra horsepower.
As such, take time to test your site’s performance. Use the information to make things as lean as possible.
Troubleshoot Website Issues Before Contacting Support
The odds are that your website will experience issues. It happens to all of us at some point.
Your first instinct may be to contact your host’s support. But it may be worth waiting in a non-emergency situation. Hastily sending an email stating that “It’s broken” won’t help.
Try to understand the problem first. Spend a few minutes troubleshooting the issue on your own. Look at your browser’s developer tools. Peruse the server’s error logs.
You might find the root cause and be able to fix the issue. That could save you from contacting technical support. And it will save everyone’s time.
If you’re still experiencing issues, then it’s OK to contact support. You can share what you found during troubleshooting. It may help them diagnose and repair the problem.
It’s worth remembering that support representatives work with a lot of people. Each has a different website configuration. And they may not instantly recognize the source of a problem. Give them as much good information as you can. That will speed up the process.
Treat Your Web Host Like a Partner
Your web host can make a difference in your site’s health. But they can’t do everything for you. Therefore, it pays to be an active participant in each item above.
Take the initiative to create backups, improve security, and optimize performance. Troubleshoot any issues before contacting support. Always take the most proactive path.
Web designers often know their sites better than anyone. That knowledge will come in handy when working with a host.
This partnership will help you get the most out of your website. That benefits everyone involved.
Related Topics
#2fa#APIs#back up#backup#backups#book#browser#cdn#Cloud#cloud service#CMS#content#control panel#cpu#Database#databases#Design#designers#Developer#direction#email#factor#Features#firewall#Freelance Business#Freelance Design#hand#Health#Hosting#how
1 note
·
View note
Text
Wie man Ninja Firewall WP Edition richtig einstellt

Im Bereich der Websicherheit ist die optimale Konfiguration und Einrichtung von Firewallsystemen entscheidend für den Schutz digitaler Daten. Dieser Artikel beschäftigt sich mit den Feinheiten der effektiven Einrichtung der Ninja Firewall WP Edition. Schritt für Schritt wird der Benutzer durch die Aktivierung der Web Application Firewall und die Aktivierung des Schutzes für die wp-login.php Datei geführt. Es werden auch Tipps zur Fehlerbehebung für mögliche Probleme gegeben, die während der Einrichtung auftreten können, um einen reibungslosen Implementierungsprozess zu gewährleisten.
Darüber hinaus werden zusätzliche Funktionen und Möglichkeiten dieser Edition erkundet, wobei die Fähigkeit zur Erkennung und Verhinderung von Brute-Force-Angriffen, zur Überwachung von unbefugtem Zugriff oder Änderungen an PHP-Dateien und zur Bereitstellung von Ereignisbenachrichtigungen für kritische Sicherheitsupdates hervorgehoben wird.
Die Anforderungen, der Installationsprozess, die FAQs, die Bewertungen und die Verfügbarkeit des Changelogs werden ebenfalls detailliert beschrieben. Dieser Artikel zielt darauf ab, den Lesern ein umfassendes Wissen über die Konfiguration verschiedener Aspekte zu vermitteln, wie z.B. das Anpassen von Sicherheitsregeln, die Konfiguration von Ereignisbenachrichtigungen, das Aktualisieren von NinjaFirewall (Pro Edition), Best Practices für die Nutzung der NinjaFirewall WP Edition unter Berücksichtigung aller Einschränkungen oder Alternativen, die mit der Verwendung der .htninja-Datei verbunden sind.
Aktivieren der vollständigen WAF
Um die volle Web Application Firewall (WAF) in Ninja Firewall zu aktivieren, sollten Benutzer die spezifische Aktivierungsmethode ihres Hosting Panels befolgen und sicherstellen, dass sie vorher ein Backup ihrer WordPress Seite machen. Benutzer mit einem benutzerdefinierten Kontrollpanel müssen die bereitgestellten Zeilen manuell in die .htaccess-Datei einfügen. Benutzer von C-Panel-Hosting hingegen sollten die Datei .user.ini im Home-Verzeichnis bearbeiten.
Nach der Aktivierung der vollständigen WAF können die Benutzer die grundlegenden Firewall-Einstellungen vornehmen. Dazu gehört die Einrichtung des Login-Schutzes, indem Sie unter Firewall-Optionen auf die Registerkarte Login-Schutz gehen und den Schutz für wp-login.php aktivieren. Außerdem sollten Benutzer eine separate ID und ein Passwort für die Firewall-Seite festlegen und den Schutz für XML-RPC aktivieren.
Ein weiterer wichtiger Aspekt ist die Konfiguration des XML-RPC-Schutzes, der sicherstellt, dass Brute-Force-Angriffe verhindert werden. Durch die Aktivierung des Brute-Force-Angriffsschutzes können Benutzer ihre Website vor mehreren fehlgeschlagenen Anmeldeversuchen schützen. Darüber hinaus ist es wichtig, die Firewall-Protokolle regelmäßig zu überwachen, da sie wertvolle Erkenntnisse über potenzielle Sicherheitsbedrohungen oder verdächtige Aktivitäten liefern.
Aktivieren des Wp-Login.Php-Schutzes
Um den Schutz für wp-login.php zu aktivieren, müssen Sie unter den Firewall-Optionen zur Registerkarte Login-Schutz navigieren. Auf dieser Registerkarte können Benutzer den Schutz für wp-login.php aktivieren und eine separate ID und ein Passwort für die Firewall-Seite festlegen. Es wird auch empfohlen, den Schutz für XML-RPC zu aktivieren.
Um die Leistung der Firewall zu optimieren, ist es wichtig, die IP-Blockierung zu konfigurieren. Dies kann durch Hinzufügen bestimmter IP-Adressen oder IP-Bereiche zur Whitelist oder Blacklist in der .htninja-Datei erfolgen. Benutzer von NinjaFirewall (Pro+ Edition) haben Zugriff auf zusätzliche Funktionen wie z.B. die Verwaltung von IP Whitelists oder Blacklists über die Menüoption Zugriffskontrolle IP Zugriffskontrolle.
Um Probleme mit dem Login-Schutz zu beheben, sollten Benutzer überprüfen, ob sie während der Aktivierung Fehler erhalten und gegebenenfalls die Seite aktualisieren. Wenn die Probleme weiterhin bestehen, wird empfohlen, den Hosting-Provider zu kontaktieren, um weitere Unterstützung zu erhalten. Das Umbenennen des Ninja Firewall Plugin-Ordners kann ebenfalls helfen, Probleme mit vergessenen Anmeldedaten zu lösen.
Um die Effektivität von NinjaFirewall (WP Edition) zu maximieren, ist es wichtig, die Anpassung der Sicherheitsregeln zu verstehen. Benutzer können Servervariablen in der .htninja Datei ändern, spezifische Anfragen basierend auf variablen Bedingungen hinzufügen oder blockieren und spezielle Rückgabewerte wie ALLOW oder BLOCK für Whitelisting oder Blacklisting von IPs verwenden.

Fehlersuche bei der vollständigen WAF-Aktivierung
Wenn während des Aktivierungsprozesses der vollständigen Web Application Firewall (WAF) ein Fehler auftritt, ist es ratsam, die Seite zu aktualisieren und gegebenenfalls den Hosting-Provider um weitere Unterstützung zu bitten. Die Fehlersuche bei der Aktivierung der vollständigen WAF umfasst mehrere Schritte:
- Überprüfen Sie, ob auf der Aktivierungsseite Fehlermeldungen oder Benachrichtigungen angezeigt werden.
- Überprüfen Sie, ob alle erforderlichen Serveranforderungen erfüllt sind, z. B. die Kompatibilität der PHP-Version und der erforderlichen Erweiterungen.
- Vergewissern Sie sich, dass es keine Konflikte mit anderen Plugins oder Themes gibt, die auf der WordPress-Website installiert sind.
- Wenn das Problem weiterhin besteht, versuchen Sie, andere Sicherheits-Plugins vorübergehend zu deaktivieren, um etwaige Konflikte zu ermitteln.
Wenn eine Fehlerbehebung des wp-login.php-Schutzes erforderlich ist, führen Sie die folgenden Schritte aus:
- Überprüfen Sie, ob der wp-login.php-Schutz auf der Registerkarte Login-Schutz unter Firewall-Optionen aktiviert ist.
- Überprüfen Sie, ob eine separate ID und ein Passwort für die Firewall-Seite festgelegt wurden.
- Stellen Sie sicher, dass der Schutz für XML-RPC ebenfalls aktiviert ist.
- Wenn beim Zugriff auf die WordPress-Anmeldeseite keine Anmeldedaten abgefragt werden, überprüfen Sie diese Einstellungen noch einmal.
Zusätzlich zur Fehlerbehebung bei Problemen mit der Aktivierung und dem Login-Schutz sind die Konfiguration der grundlegenden Firewall-Einstellungen und die Aktivierung des Schutzes vor Brute-Force-Angriffen wichtige Schritte für eine effektive Einrichtung der Ninja Firewall WP Edition.
Fehlersuche beim Wp-Login.Php Schutz
Die Fehlerbehebung des wp-login.php Schutzes umfasst mehrere Schritte, um das ordnungsgemäße Funktionieren der Sicherheitsmaßnahmen zu gewährleisten. Zunächst ist es wichtig zu prüfen, ob der Schutz für wp-login.php aktiviert ist. Dazu können Sie unter den Firewall-Optionen auf die Registerkarte Login-Schutz zugreifen und überprüfen, ob der Schutz aktiviert ist.
Als nächstes ist es wichtig, die eingestellte ID und das Passwort für die Firewall-Seite zu überprüfen. Damit wird sichergestellt, dass nur autorisierte Personen Zugriff auf die Verwaltung und Konfiguration der Firewall-Einstellungen haben.
Darüber hinaus sollte der XML-RPC-Schutz aktiviert werden, um potenzielle Brute-Force-Angriffe über dieses Protokoll zu verhindern. Dies kann ebenfalls in den Firewall-Optionen vorgenommen werden.
Darüber hinaus ist es wichtig zu bestätigen, dass beim Zugriff auf die WordPress-Anmeldeseite die Eingabe von Anmeldedaten erforderlich ist. Dadurch wird sichergestellt, dass unbefugte Benutzer keinen Zugang zu sensiblen Informationen erhalten oder bösartige Aktivitäten durchführen können.
Um die Anmeldeinformationen wirksam zu schützen, ist die Verwaltung der Firewall-Protokolle von entscheidender Bedeutung. Durch regelmäßiges Überprüfen und Analysieren der Firewall-Protokolle können verdächtige Aktivitäten oder potenzielle Sicherheitsverletzungen erkannt und umgehend behoben werden.
Schliesslich spielt die Optimierung der NinjaFirewall Leistung eine wichtige Rolle bei der Aufrechterhaltung eines effektiven Sicherheitssystems. Die regelmäßige Aktualisierung und Konfiguration der NinjaFirewall-Einstellungen gewährleistet eine optimale Leistung gegen potentielle Bedrohungen bei gleichzeitiger Minimierung falsch positiver und negativer Ergebnisse.
Zusätzliche Informationen
Der Schutz von xmlrpc.php ist entscheidend für die Sicherheit einer WordPress Webseite. Ein weit verbreiteter Irrglaube über xmlrpc.php ist die Annahme, dass es nicht wichtig ist, diese Datei zu schützen oder zu deaktivieren. Allerdings kann xmlrpc.php von Angreifern ausgenutzt werden, um Brute-Force-Angriffe und andere bösartige Aktivitäten durchzuführen.
Die Vorteile einer Firewall wie Ninja Firewall liegen in der erhöhten Sicherheit und dem Schutz vor verschiedenen Arten von Angriffen wie SQL Injection, Cross-Site Scripting (XSS) und Remote Code Execution. Vergleicht man Ninja Firewall mit anderen Sicherheitsplugins, so bietet Ninja Firewall fortschrittliche Funktionen und eine leistungsstarke Filter-Engine, die von Hackern verwendete Umgehungstechniken erkennen kann.
Um die Leistung der Firewall zu optimieren, wird empfohlen, den vollständigen Schutz der Web Application Firewall (WAF) zu aktivieren und den Schutz der wp-login.php in den Firewall-Optionen zu aktivieren. Zu den Tipps zur Fehlerbehebung bei der vollständigen WAF-Aktivierung gehören die Aktualisierung, wenn bei der Aktivierung Fehler auftreten, oder die Kontaktaufnahme mit dem Hosting-Provider zur Unterstützung. Für den wp-login.php Schutz kann das Umbenennen des Ninja Firewall Plugin Ordners helfen, Fehler bei fehlenden Dateien zu beheben.
Um die Sicherheit einer Webseite zu gewährleisten, ist es wichtig, die verschiedenen Angriffsarten zu verstehen und zu wissen, wie Ninja Firewall vor ihnen schützen kann. Mit seiner Fähigkeit, Brute-Force-Versuche zu erkennen, den Zugriff auf PHP-Dateien zu überwachen und unbefugten Zugriff zu verhindern, bietet Ninja Firewall umfassenden Schutz für WordPress-Websites.
Beschreibung und Funktionen
Die Beschreibung und Funktionen von NinjaFirewall (WP Edition) umfassen eine eigenständige Firewall, die erweiterte Sicherheitsmaßnahmen bietet, die auf WordPress-Ebene normalerweise nicht verfügbar sind. Dieses Plugin benötigt PHP 7.1, MySQLi Erweiterung und ist kompatibel mit Unix-ähnlichen Betriebssystemen wie Linux und BSD. NinjaFirewall kann jede HTTP/HTTPS-Anfrage, die an ein PHP-Skript gesendet wird, abfangen, scannen, säubern oder zurückweisen, bevor sie WordPress erreicht. NinjaFirewall schützt alle Skripte innerhalb der Blog-Installationsverzeichnisse, einschließlich der Nicht-WordPress-Skripte.
Eines der Hauptmerkmale von NinjaFirewall ist die leistungsstarke Filter-Engine, die Daten aus eingehenden HTTP-Anfragen normalisieren und transformieren kann. Es erkennt Techniken zur Umgehung der Web Application Firewall und Verschleierungstaktiken, die von Hackern verwendet werden. Das Plugin unterstützt und dekodiert auch eine große Anzahl von Kodierungen.
NinjaFirewall bietet einen umfassenden Schutz gegen Brute-Force-Angriffe auf wp-admin, indem es verteilte Angriffe von tausenden von verschiedenen IPs erkennt und behandelt. NinjaFirewall kann auch unbefugten Zugriff auf PHP-Dateien verhindern, indem es Administratoren in Echtzeit über jeden Zugriff auf kürzlich geänderte oder erstellte PHP-Dateien informiert.
In Bezug auf die Anmeldesicherheit ermöglicht NinjaFirewall die Konfiguration von Anmeldewarnungen für Ereignisse wie Administratoranmeldungen und Änderungen von Administratorkonten. Es bietet auch Schutz für Plugin- und Themen-Uploads und stellt sicher, dass nur autorisierte Dateien hochgeladen werden.
Um die Leistung der Firewall zu optimieren, können Benutzer verschiedene Einstellungen im Optionsmenü des Plugins konfigurieren. Darüber hinaus können Probleme mit blockierten IPs durch die Überprüfung von Serverprotokollen oder die Unterstützung durch den Hosting-Provider behoben werden.
Insgesamt ist NinjaFirewall (WP Edition) ein sehr leistungsfähiges Sicherheitsplugin für WordPress, das fortschrittliche Funktionen zum Schutz vor verschiedenen Bedrohungen bietet, mit denen Webseitenbetreiber konfrontiert werden.
Anforderungen und Installation
Die Installation des NinjaFirewall Plugins erfordert das Hochladen des ninjafirewall Ordners in das /wp-content/plugins/ Verzeichnis und die Aktivierung über das Plugins Menü in WordPress. Nach der Installation können Benutzer die Firewall-Einstellungen konfigurieren, IP-Whitelisting verwalten, Probleme bei der Aktivierung beheben, Sicherheitsregeln anpassen und NinjaFirewall aktualisieren.
Um Firewall-Einstellungen zu konfigurieren:
- Rufen Sie das NinjaFirewall Menü in WordPress auf.
- Navigieren Sie zu der Seite Firewall-Richtlinien.
- Passen Sie die Sicherheitsregeln an Ihre Bedürfnisse an.
- Aktivieren oder deaktivieren Sie verschiedene Funktionen wie den Brute-Force-Schutz und die Beschränkung des Dateiuploads.
So verwalten Sie die IP-Whitelist:
- Gehen Sie zum Menüpunkt IP Zugriffskontrolle in NinjaFirewall (Pro+ Edition).
- Setzen Sie bestimmte IP-Adressen oder Bereiche auf die Whitelist, indem Sie sie zur .htninja-Datei hinzufügen oder die Schnittstelle des Plugins nutzen.
- Blacklisting von IPs, die für den Zugriff auf Ihre Website gesperrt werden sollen.
Fehlerbehebung bei Aktivierungsproblemen:
- Wenn bei der Aktivierung ein Fehler auftritt, aktualisieren Sie die Seite und versuchen Sie es erneut.
- Wenden Sie sich bei Bedarf an Ihren Hosting-Provider, um weitere Unterstützung zu erhalten.
- Benennen Sie den Ninja Firewall Plugin-Ordner um, wenn Sie die Anmeldedaten vergessen haben, und aktivieren Sie ihn nach der Umbenennung erneut.
So passen Sie die Sicherheitsregeln an:
- Navigieren Sie zur Seite Firewall Policies in NinjaFirewall.
- Ändern Sie bestehende Regeln oder erstellen Sie eigene Regeln basierend auf spezifischen Anforderungen.
- Überprüfen und aktualisieren Sie die Sicherheitsregeln regelmäßig, wenn neue Bedrohungen auftauchen.
Um NinjaFirewall zu aktualisieren:
- Prüfen Sie regelmäßig auf Updates im WordPress Dashboard im Bereich 'Plugins'.
- Wenn ein Update verfügbar ist, klicken Sie auf 'Jetzt aktualisieren'.
- Vergewissern Sie sich vor der Aktualisierung, dass das Plugin mit der aktuellen Version von WordPress kompatibel ist.
- Testen Sie die Funktionalität der Website nach der Aktualisierung der Plugins
FAQ und Bewertungen
Die Sektion FAQ und Bewertungen bietet wertvolle Informationen über häufige Probleme bei der Fehlerbehebung, Erfahrungsberichte von Nutzern und häufig gestellte Fragen zu NinjaFirewall. Dieser Abschnitt zielt darauf ab, alle Bedenken oder Unsicherheiten zu beseitigen, die Nutzer bei der Verwendung des Plugins haben könnten.
Benutzer können Antworten auf verschiedene Fragen über die Einzigartigkeit und Leistungsfähigkeit von NinjaFirewall, seine Kompatibilität mit Nginx und Windows, sowie seine Auswirkungen auf die Geschwindigkeit der Website finden. Diese FAQs helfen den Nutzern, ein besseres Verständnis für die Fähigkeiten des Plugins zu erlangen und fundierte Entscheidungen bezüglich seiner Implementierung zu treffen.
Außerdem enthält der Abschnitt positive Bewertungen von Nutzern, die ihre Zufriedenheit mit NinjaFirewall zum Ausdruck bringen. Diese Erfahrungsberichte unterstreichen die Effektivität des Plugins beim Schutz von Webseiten vor Malware, Viren und unautorisiertem Zugriff. Durch die Darstellung realer Erfahrungen zufriedener Kunden tragen diese Bewertungen dazu bei, Vertrauen in die Zuverlässigkeit und Leistung von NinjaFirewall zu schaffen.
Zusätzlich kann dieser Abschnitt Vergleiche mit anderen auf dem Markt erhältlichen Sicherheitsplugins enthalten. Solche Vergleiche können Nutzern helfen, die Funktionen von NinjaFirewall im Vergleich zu alternativen Lösungen zu bewerten, so dass sie eine fundierte Entscheidung basierend auf ihren spezifischen Anforderungen treffen können.

Changelog und Meta
Im Changelog und Meta Abschnitt finden Benutzer detaillierte Informationen über Updates, Fehlerbehebungen und Kompatibilität der verschiedenen Versionen des NinjaFirewall Plugins. Dieser Abschnitt bietet wertvolle Einblicke in die Entwicklung des Plugins und ermöglicht es Benutzern, über alle Änderungen informiert zu bleiben, die ihre Sicherheitseinrichtung betreffen könnten. Einige wichtige Aspekte, die in diesem Abschnitt behandelt werden, sind:
- Anpassen der Sicherheitsregeln: Der Abschnitt Changelog und Meta bietet Informationen darüber, wie Benutzer die Sicherheitsregeln innerhalb des Plugins anpassen können. Dies ermöglicht es ihnen, die Firewall-Einstellungen an ihre spezifischen Bedürfnisse und Vorlieben anzupassen.
- Aktivieren des Schutzes vor Brute-Force-Angriffen: Benutzer können lernen, wie man den Schutz vor Brute-Force-Angriffen durch das NinjaFirewall-Plugin aktiviert. Diese Funktion schützt vor böswilligen Anmeldeversuchen, indem der Zugriff nach mehreren fehlgeschlagenen Anmeldeversuchen beschränkt wird.
- Einrichten des Anmeldeschutzes: Der Abschnitt Changelog und Meta bietet eine Anleitung zum Einrichten des Login-Schutzes für wp-login.php, einem wichtigen Schritt zur Sicherung von WordPress-Websites. Benutzer können diese Anweisungen befolgen, um den Schutz ihrer Website vor unbefugtem Zugriff zu verbessern.
- IP Whitelisting und Blacklisting verwalten: Das NinjaFirewall Plugin ermöglicht es Benutzern, IP Whitelisting und Blacklisting effektiv zu verwalten. Durch die Konfiguration dieser Einstellungen können Benutzer den Zugriff auf bestimmte IP-Adressen oder Bereiche kontrollieren und so die Sicherheitsmaßnahmen erhöhen.
- Konfigurieren von Ereignisbenachrichtigungen: Benutzer haben die Möglichkeit, Ereignisbenachrichtigungen innerhalb von NinjaFirewall zu konfigurieren. Diese Funktion benachrichtigt Administratoren über wichtige Ereignisse wie z.B. Administratoranmeldungen, Änderungen von Konten, Plugin/Theme Uploads, WordPress Updates und anstehende Sicherheitsupdates für Plugins/Themes. Wenn diese Benachrichtigungen aktiviert sind, können Administratoren potenzielle Sicherheitsprobleme sofort angehen.
Read the full article
0 notes
Text
Magento 2 Security: Protecting Your Store from Cyber Threats and Data Breaches
Magento 2 is a powerful e-commerce platform that creates and manages online stores. However, it is vital to emphasize the security of your Magento 2 store due to the rising incidence of cyber-attacks and data breaches.
In this post, we'll discuss how to safeguard your Magento 2 online business against hacking and other forms of cybercrime. Customers will feel more comfortable shopping with you online if you take these precautions to protect their personal information.

Understanding the Importance of Magento 2 Security
Cyber threats and data breaches can severely affect your Magento 2 store. They can result in the loss or compromise of customer data, financial loss, damage to your reputation, and legal implications.
Understanding the potential impact of these threats is crucial for prioritizing security measures. Inadequate security measures can leave your Magento 2 store vulnerable to attacks and less competitive.
These may include unauthorized access to customer information, credit card fraud, website defacement, or malicious code injection. The consequences can be devastating, leading to customer distrust, loss of revenue, and potential legal ramifications.
Implementing Strong Magento 2 Access Controls
· Use Secure Usernames and Passwords
Make sure that all users and administrators have secure and different passwords. Passwords should be long and difficult to crack, featuring a mix of uppercase and lowercase letters, numbers, and symbols.
Password rotation regulations should be enforced, and simple passwords like birthdates, names or addresses should be discouraged. Choose the format of your password wisely so that no one can crack it easily.
· Enable Two-Factor Authentication
Two-factor authentication can be enabled to further strengthen the security of administrator accounts. Two-factor authentication necessitates a login, password, and a separate piece of information, such as a one-time code texted to a mobile device.
· Limit Admin Panel Access
Only authorized users should be given access to the admin panel. Limit who can access what depending on their specific job duties. Set up a reliable user management system to monitor who has access to what.
· Regularly Review and Update User Permissions
Ensure users can only access the necessary resources by regularly reviewing and updating their permissions. Users who no longer need administrative access should have their rights revoked.
Keeping Your Magento 2 Installation Up to Date
Stay updated with the latest security patches and updates released by Magento. These updates often address vulnerabilities and security weaknesses. Regularly check for new releases and apply them promptly to protect your store.
Subscribe to security advisories and newsletters provided by Magento to stay informed about security releases. These updates will inform you of potential vulnerabilities and provide instructions on addressing them.
Ensure all installed extensions and themes are current. Developers often release updates that include security enhancements. Regularly review and update these components to minimize vulnerabilities.
Implement regular malware scanning using reliable security tools or services. Scanning can detect and identify any malicious code or vulnerabilities in your store. Consider implementing a web application firewall (WAF) to protect against common web-based attacks.
A WAF can help detect and block suspicious requests and protect your store from known attack vectors. Regularly audit your codebase to identify potential security vulnerabilities. Engage professional developers or security experts to conduct thorough code reviews.
Securing Your Magento 2 Server Environment
Choose a Secure Hosting Provider: Select a reputable hosting provider that prioritizes security and offers robust server protection. Look for features like firewalls, intrusion detection systems, and regular security audits.
Enable Firewalls and Intrusion Detection Systems: Enable firewalls at the server level to filter incoming and outgoing traffic. Additionally, consider implementing intrusion detection systems (IDS) to monitor and detect suspicious activities in real time.
Implement Secure File Permissions: Set appropriate file and directory permissions to restrict unauthorized access to critical files. Follow Magento's recommendations for file approvals to ensure a secure configuration.
Enable SSL/TLS Encryption: Enable encryption for secure communication between your store and customers. Obtain an SSL certificate and configure your store to use HTTPS to encrypt sensitive data, such as login credentials and payment information.
Securing Payment Processing, Data Backup and Disaster Recovery
· Implement Secure Payment Gateways
Process your customers' financial transactions using safe and reliable gateways. Verify that the payment processor uses secure protocols and meets all applicable regulations. Check twice while making any payments.
· Use Tokenization and Encryption for Sensitive Data
Protect private information, such as customers' credit card numbers, using tokenization and encryption. Tokenization is the process of exchanging personally identifiable information for randomly generated identifiers.
· Comply with Payment Card Industry Data Security Standard Requirements
Your store must follow PCI DSS (Payment Card Industry Data Security Standard) guidelines to accept credit cards. As a standard for protecting customers' credit card information, PCI DSS is essential for any online retailer.
· Regularly Back up Your Magento 2 Store
Ensure your Magento 2 store and database are regularly and automatically backed up. To guarantee data recovery during a breach or system failure, backups should be stored in safe locations, preferably off site or on the cloud.
· Test Data Restoration Procedures
To ensure backups can be restored effectively, it is important to verify your data restoration operations regularly. Your backup strategy's validity and efficiency can only be guaranteed through consistent testing.
· Have a Disaster Recovery Plan in Place
Create a thorough recovery strategy that details what to do during a data breach or other catastrophic event. Don't forget to outline how you'll be in touch with key players and what you'll do in an emergency.
Educating and Training Your Staff
Train your employees to follow best practices and teach them the value of security. Among these are strong passwords, the ability to spot phishing efforts, and the early reporting of security breaches.
Provide courses that instruct employees on how to recognize and counteract security risks. Spotting suspicious behavior, filing reports, and following all necessary security measures. To quickly identify and address security incidents, implement real-time monitoring.
The data from these instruments may shed light on intrusion attempts, suspicious behavior, and other forms of potentially malicious activity. Create a successful plan outlining what to do during a security breach.
Manage the situation, conduct an investigation, and start the recovery process. Monitor audit and log files for any signs of questionable behavior. Examine data to discover any indications of hacking, unauthorized access, or other system flaws.
Conclusion
Keeping your Magento 2 store safe from hackers and data breaches is crucial to protecting your clients' information and preserving their trust. The security of your Magento 2 store can be greatly improved by implementing the methods described in this article.
From secure server environments and payment processing to strict access controls, taking every precaution to protect your data is important. Remember that maintaining security is an ongoing task that demands awareness, consistent upgrades, and constant monitoring.
Remember to stay vigilant, keep up with security updates, and regularly review and improve your security measures to adapt to evolving threats. With a comprehensive security strategy, you can confidently run your Magento 2 store and provide a safe shopping environment.
Protecting your customers' personal information and avoiding hacks are two benefits of making Magento 2 security a top priority for your online store. So, avoid wasting your time and start safeguarding your Magento 2 store with Webiators Technologies.
Original Source : https://store.webiators.com/blog/post/magento-2-security-protecting-your-store-from-cyber-threats-and-data-breaches
0 notes
Text
ELIMINATE DECEPTIVE SITE AHEAD AND OTHER WARNINGS ON YOUR WEBSITE

When you’re browsing the internet and see a warning on the website you’re visiting, it’s likely that you’ll see something like “dangerous site ahead” or “deceptive site ahead.” The majority of these warnings are based on a third-party tool called Phishtank and are generated when someone alerts their service to an offending website. When this happens, the site will be flagged with a warning saying that it’s either deceptive or dangerous. This article will walk you through how to remove these warnings from your website and prevent them from reappearing in the future.
What Are Deceptive Site Ahead And Other Warnings?
When you see a warning in your browser that says “Deceptive site ahead” or “Danger: Malicious site ahead,” it means that Google Safe Browsing has detected that the website you’re visiting may be trying to trick you into doing something dangerous, like installing malware.
These warnings are shown for sites that host malicious or deceptive content, such as phishing scams, viruses, and other unwanted software. If you see this warning, it’s best to leave the site immediately.
To protect yourself from deceptive and malicious sites, make sure you have an antivirus program installed on your computer and keep it up-to-date. You should also use a strong password for all of your online accounts.
How To Fix Deceptive Site Ahead And Other Warnings On Your Website
If you’re seeing the “Deceptive site ahead” or “Danger: Malicious File” warnings in Google Chrome when visiting your own website, it’s likely that your site has been hacked. These warnings are displayed in an attempt to protect users from phishing attacks, malware, and other online threats.
Fortunately, there are a few steps you can take to fix these warnings and secure your website:
Identify the source of the issue. Deceptive site ahead warnings are usually caused by malicious code injected into your website. This can be done by examining your website’s source code for any suspicious code or files.
Remove any malicious code or files from your website. Once you’ve identified the source of the issue, you’ll need to remove any malicious code or files from your website. This can be done using a FTP client or through your hosting control panel.
Remove any malicious code or files from your website. Once you’ve identified the source of the issue, you’ll need to remove any malicious code or files from your website. This can be done using a FTP client or through your hosting control panel.
Remove any malicious code or files from your website. Once you’ve identified the source of the issue, you’ll need to remove any malicious code or files from your website. This can be done using a FTP client or through your hosting control panel.
Remove any malicious code or files from your website. Once you’ve identified the source of the issue, you’ll need to remove any malicious code or files from your website. This can be done using a FTP client or through your hosting control panel.
Secure your website with a web application firewall (WAF). A WAF will help to protect your website from future attacks by blocking malicious traffic before it reaches your site. There are many different WAFs available, so be sure to choose one that’s right for your specific needs.
Keep your CMS and plugins up-to-date. Outdated software is one of the most common causes of hacked websites. Be sure to keep your content management system (CMS) and plugins up-to-date to help prevent vulnerabilities that could be exploited
When To Expect This Issue
When you see a warning that says “Deceptive site ahead,” it means that Google has detected that the site you’re trying to visit may be trying to trick you into providing personal information (like your password or credit card numbers). This can happen when someone creates a fake login page that looks like a legitimate website, or when a site is infected with malware.
To protect yourself from these types of attacks, it’s important to keep your browser and operating system up to date, and to only enter personal information on websites that you trust. If you see a warning like this, it’s best to go back to the previous page or choose a different result.
Why Is This Happening?
There are a few reasons that you might be seeing the “deceptive site ahead” warning on your website. It could be that your site has been flagged by Google as being potentially malicious, or it could be that you’re using an outdated security protocol like SSL 3.0.
If your site has been flagged by Google, it’s important to take steps to fix the issue so that visitors don’t get scared away. The best way to do this is to submit a request to Google for a review of your site. You can also try to improve your site’s security by upgrading to a newer security protocol like TLS 1.2.
If you’re using an outdated security protocol like SSL 3.0, it’s time to upgrade to a newer and more secure protocol like TLS 1.2. This will help to keep your visitors safe and will also make sure that you don’t get any more warnings from Google in the future.
Conclusion
If you’re seeing warnings like “Deceptive Site Ahead” or “This site may be hacked” when visiting your website, it’s important to take action to fix the problem. Not only are these warnings off-putting to your visitors, they can also lead to a loss of traffic and customers.
Luckily, there are a few things you can do to eliminate these warnings and get your website back up and running smoothly. By following the tips in this article, you can quickly and easily get rid of these pesky warnings for good.
0 notes
Video
youtube
Birds trapped in buildings are amongst the trickiest rescues we get and, when we were called out to rescue a bird from an office roof space, we expected a long day!
This pigeon had managed to find it's way into the space above an office in Leatherhead and was proving very difficult to find. It took the combined efforts of Simon, Ed and Connor to get him to safety!
#new#rescue#video#YouTube#bird#pigeon#stuck#trapped#roof#roofing#space#panel#Leatherhead#office#business#Simon#Cowell#WAF#wildlifeaid#wildlifesos#wild#animal#wildlife#aid#sos#release#rehab#rehabilitation#thin#weak
15 notes
·
View notes
Text
"Go on, turn it on den," said Bignutz to his trusty helper Fuggit.
The greasy Grot shuffled across the cluttered workshop and with some difficulty pushed up a large iron lever labelled 'onn'. The large wheeled machine started to rattle and shake as a large capacitor began to power up, a loud electric whine making everyone's teeth rattle. The glowy gubbins began to glow on cue.
Boss Nailz glowered at the machine as if it had just mortally offended him by calling him a humie or a Grot or something equally offensive.
"What is it?" He asked.
"A gun Boss" said Bignutz as if it was obvious "a naffin big gun, juss like ya wanted."
Nailz just stared at him.
"On wheels," added Bignutz in case that helped.
"An wotz dat colour?" Added Nailz accusingly, "dat's not an Orky colour."
Bignutz looked up at the violently shaking field gun who's barrel bitz now glowed an unexpected orange colour.
"Well, it's a bit like red, an a bit like yella. I'm gonna call it redella." Decided Bignutz after some consideration.
Still glowering like a starved hoggsquig, Boss Nailz took a couple of steps closer to the gun. "So woz it actually do den?"
Gesturing to Fuggit, Mek Nailz took a couple of steps away from the machine. Fuggit lowered his welding mask, pulled up his thick rubber gloves as far as they would go and stepped up to the big red button on the rusty control panel.
"Go on den," Bignutz waffed his hand at Fuggit.
Standing as far away as his long arms would allow, Fuggit reached forwards and mashed the button with the palm of his greasy glove.
The gun wobbled for a second, juddered for two then suddenly stopped.
"Well..." began Boss Nailz before the gun spat an Ork sized ball of redellow energy, smashing through the contents of the workshop and obliterating the opposite wall I a shower of scrap and gubbinz.
Moments passed.
"Maybe we should of dragged it outside boss," said Fuggit.
"Maybe." Agreed Bignutz.
"Build more o' dem." Coughed Nailz.
2 notes
·
View notes
Text
High 5 Free MP3 Converters For Mac
Wv to MP3,MP2,WMA , WAV, OGG, APE, AAC(utilized by iTunes),FLAC(lossless compression),MP4,M4A, MPC(MusePack),AC3,TTA,ofr(OptimFROG),SPX(Speex),Ra(Actual audio), and wv(WavePack). Complete Audio converter is a versatile software that's able to converting even the rarest codecs corresponding to OPUS to MP3. Some of the output audio formats it help consists of MP3, WMA, WAV, FLAC, MP4, MPC, OPUS, and over 20 extra formats. Along with that, it may also rip audio from CDs and convert YouTube movies to the varied output codecs it helps. Total has been on-line for over 10 years and is being utilized by tens of millions of users.
Audio Converter additionally supports video to audio conversion. For instance, you need to use this app to transform MKV, WMV, M4V, AVI, MOV, MPEG or MP4 video file to MP3 file. Click on "Convert" to convert WV files to FLAC format; alternatively, click on "Convert to One" to convert all information in record and combine to a single one FLAC file. CUETools makes use of output path templates similar to foobar2000 title formatting syntax.
Numerous predefined conversion profiles. Risk to save your own settings to an INI file. The program converts conversion from MP3 to MPC, APE, WV, FLAC, OGG, WMA, AIFF, and WAV. Slower changing pace than desktop FLAC converters particularly when converting a big or multiple recordsdata. An audio file converter is one kind of file converter that (shock!) is used to convert one sort of audio file (like an MP3 , WAV , WMA , etc.) into one other kind of audio file.
To trim WV, you just want to move the sliders to specify start and end time, then hit OKAY; to separate WV, simply enter the value you want, click OK. If you want to merge several WV recordsdata, you solely need to tick the box before Merge all recordsdata, all the WV information might be merger after conversion. Click on "Add" button to load your video information.
Be aware: When installing the Freemake Audio Converter, be certain that to uncheck what you do not need as the Freemake installer will try to install different applications not related to the converter. As might be seen from the diagram, the panel lets you set the anticipated quantity and output format of the audio, and to customize the pattern fee, Bit fee and channels the audio will comprise.
Since 1994, Zone 8 Recording has been serving the audio wants of northern West Virginia with high quality music and vocal recordings. By way of the years we have labored arduous to keep the overhead low and go the financial savings alongside to shoppers. Zone 8's objective has at all times been to achieve the skilled quality sound of a major label CD at a fraction of the fee. Prior to now sixteen years, we have had the chance to file every conceivable style of music, and work with musicians of all age teams and skill ranges. Ask any of our shoppers they usually'll let you know, the recording environment here is super-relaxed and we'll work carefully with you to get one of the best recordings attainable. No project is simply too massive or small.
Freemake is a characteristic-rich and extremely straightforward to use audio converter that helps a number of input and output audio file formats. With Freemake, you may mix multiple files into one large audio file. This software additionally permits you to adjust the output quality before file conversion starts. Input formats supported embrace MP3, vanmoloney868.pen.io WMA, WAV, OGG, M4R, M4A, FLAC, AC3, AMR, and AAC. Output formats supported include MP3, WMA, WAV, OGG, M4A, FLAC, and AAC.

WAV to FLAC Converter affords you a simple and quick choice to convert wv audio to mp3 WAV to FLAC audio with prime quality. Audio Transcoder is a complicated WAV to FLAC Converter and Audio CD Ripper with support of assorted properly-favored audio codecs and encoders. MP3 is the preferred audio file type based totally on MPEG-1 Layer III compression. Its lossy algorithm was developed in 1991. MP3 codes the sound almost with the identical top quality, as CD (sixteen-bit stereo), offering compression in dimension 1 to 10 from the distinctive WAF or AIFF tracks.Unlimited video downloading and changing to MP3. CUERipper is an utility for extracting digital audio from CDs, an open source different to EAC. It has rather a lot fewer configuration options, so is somewhat easier to make use of, and is included in CUETools package deal. It helps MusicBrainz and freeDB metadata databases, AccurateRip and CTDB. - Online e-e book device, convert between various e-ebook codecs on-line.To hurry up the conversion course of or with a purpose to save computer sources it is attainable to set the Free WavPack to MP3 Converter process thread priority. I'm positive you've got solved your problem of extracting the audio from video files, but whereas I used to be looking for the solution to my downside, I found the information on a converter that does just what you want (I think).
1 note
·
View note
Text
To Audio Converter For Mac
Utilizing Mac OS X's powerful built-in media encoding tools, giant AIFF audio recordsdata may be quickly and easily transformed to compressed top quality M4A audio, ready to be used on in iTunes or an iPod, iPhone, or elsewhere. Universal audio converter. Extract and convert audio tracks from audio and video recordsdata to MP3, AAC, AC3, WMA, OGG, FLAC, M4A, WV, AIFF, WAV and other formats. Zamzar is likely one of the hottest on-line AIFF to MP3 converter, which is able to deal with greater than 1,200 formats. It is the ultimate media converter, including video codecs, audio codecs, music information, eBook, photos and CAD information.
At last, you'll be able to click on "Convert" button to begin to convert AIFF to MP3 with this AIFF to MP3 Converter. While you get the MP3 recordsdata, you may switch the files to any devices to enjoy the music or audio file. button on the program interface, and then there might be a pop up window which allows you to set output path and output audio format. Output format as MP3, FLAC, WAV & AAC can be found to decide on.
Step 3: Now you'll be able to click on the "Rip Music" option and choose the "RIP Settings" option. Click on "Format" menu after which choose "MP3" format after which click on on "Apply" adopted by "OK". Hit Convert" button to launch the conversion. Our MP3s are encoded at 320 Kbps CBR (Fixed Bit Price) using a LAME encoder. 320 kbps is the very best doable bit price setting a LAME encoded mp3 file can have, and this larger bit price usually leads to superior sound high quality as well as a more in-depth illustration of the unique sound.
After importing source file, go to format panel to pick MP3 as output format. To enter the format panel, click the button on the left facet of the massive green Convert button and click Change" in the course of the followed drop-down menu. There are 4 sections within the format selecting panel. Go to Format part and select MP3 in Common Audio.
An audio file converter is one sort of file converter that (shock!) is used to convert one sort of audio file (like an MP3 , WAV , WMA , and so on.) into one other kind of audio file. In the event you simply want to convert your AIFF music to file withaac extension, you select General Audio > AAC - Superior Audio Coding (.aac) from the panel; otherwise you want to get the AIFF right into a format that adopts AAC to encode observe, in that case, decide M4A - MPEG-four Audio (.m4a) from the listing.
Speed will not be an vital consideration if it's essential to convert just some recordsdata. Nevertheless, a fast converter software program may prevent hours when you have loads of recordsdata to convert, or end up changing information often. Sluggish conversion speed is the biggest draw back when utilizing free online music file converter aiff to mp3 converter software program.
MP3 is the most popular audio file type primarily based on MPEG-1 Layer III compression. Its lossy algorithm was developed in 1991. MP3 codes the sound nearly with the same high quality, as CD (16-bit stereo), offering compression in size 1 to 10 from the unique WAF or AIFF tracks. The standard of MP3 critically will depend on the bitrate. It may be 128 - 256 kbps. Larger bitrates are also supported, however they severely increase the file dimension. It is supported by all trendy laborious- and software gamers.
in case you are converting it is not going to make your recordsdata sound higher. It can also convert MP3 to AIFF or convert betwwen AIFF, MP3, WAV, FLAC, free online music file converter aiff to mp3 M4A, AAC, WMA, etc. Here the primary setting is the encoder. By default, it's the LAME MP3 Encoder, which you need to use to transform other audio codecs into MP3 format. Nonetheless, if you want to convert an audio file to FLAC, OGG, WAV or BONK, simply choose the suitable encoder.It is a subtle difference, however as soon as you know it is there, it's somewhat annoying that MP3 became the ubiquitous format, rather than one of many others. AAC and Ogg Vorbis information weigh in simply barely bigger than MP3s, albeit a negligible quantity. Most software program helps Ogg (see chart), however the whole lot supports AAC, so chances are you'll want to consider it over MP3 when you convert music down from lossless formats.The WAV and AIFF audio codecs are very related in performance and these days are most likely unwell fitted to most internet audio. Nonetheless, these formats remain the standard for top-quality uncompressed audio earlier than it gets converted to be used on the Web. The Waveform Audio File Format (.wav) was originally developed as the usual audio format for the Microsoft Home windows operating system, however it is now supported on the Macintosh as effectively. WAV files can support arbitrary sampling charges and bit depths, though 8 kHz and eleven.025 kHz at eight or sixteen bits are commonest for Web use.
1 note
·
View note
Text
Is Hostinger a Good Web Host?
Hostinger is one of the reliable and trustworthy companies of Hosting. The company provides excellent resources for web hosting at a very low cost. Hostinger focuses on shared Hosting and Scalable VPS Hosting in 39 countries with more than 29 million customers. The company provides 99.99% uptime promise with fastest loading speed. It not only deals with hosting but also provides domains, website builder, emails and many more web related services at an affordable cost It is the one-stop for those who want to make their website from a single company. The company also offers Hostinger Coupon Code to reduce the actual cost of its customers. By using this coupon code you will get a huge discount on its web hosting services.

Overview of Hostinger Features
Daily Backup
Cloud Linux
Custom hPanel
Cloudflare integration
Access Manager
SSD Drive
Intercom
HTTP/2
Real-time reactive server monitoring
Memcached
Intelligent WAF
Let's Encrypt integration
Nginx micro cache
Pros and Cons of Hostinger
Pros
Good Value for money
Quality site manager as similar to Cpanel
There is no limitation to website builder
You can give other secure access to your website
Cons
No phone Support
Suitable for those who have the richest technical knowledge of hosting resources
Technical Details
Features- The company provides Unlimited Bandwidth, Disk Space, Sites, Free Domain, and Wordpress Hosting.
Platform- Linux based hosting provider.
Scripting and Language- Java and PHP
Control panel- Cpanel
Easy Installs- Drupal, Joomla, Magento, Wordpress, SSL
Server location- USA, UK, Singapore
Databases- PHPMyAdmin, MySQL
Support- Live Chats, Knowledgebase, Tickets
Conclusion
It is very important to select the right web hosting service for your website. Hostinger is one of the largest web hosting provider. Make sure that you will choose a web hosting provider which will suit your website needs and requirements.
1 note
·
View note
Text
In 10 Minutes, I'll Give You The Truth About Linux Reseller Web Hosting Plans
As a result, there's a sizable volume of all sorts of computer software and scripts available for site owners to put in on Linux servers. By using a bunch, you could just upload all you'll want to the server plus your buyers can then connect there to be aware of your web site. very first thing you should to be aware of about is servers.
for anyone who is arranging for an E-commerce Internet site for obtaining and advertising objective, then SSL Certification is amazingly necessary. there are numerous things that are necessary to be thought of by a internet hosting assistance supplier that wishes to acquire into the top 1. Apart from that, you bought to possess to consider the best and wonderful internet hosting services provider as again this can be critical together with the visibility of your web site is depended to the exact same.
How To Make More reseller hosting By Doing Less
If your company is very little and you do not need then that's a unique watch. The absolute primary source for starting up any enterprise is a good Perspective. If you're able to passionately present excellent company on your consumers, you'll achieve any Market.
Server protection may be preserved by providing minimum privileges to produce sure that no-one accesses your web site for mischievous applications. the pc program is accessed through the net. if you are web hosting applications, WAF before (or as a component of) your Internet server is a crucial technologies you ought to examine.
published here
there are numerous Indian internet hosting providers to pick from. VPS internet hosting is cost efficient As well as aspect loaded so people today obtain it more beautiful when put next to dedicated servers As well as Shared web hosting alternatives.
You should be farsighted and select a host which has scalable web hosting designs. a web host is dependable in earning your website seen around the world wide web, so It is really only suitable that you choose to opt for a web hosting firm that can offer you essentially the most Gains. If it involves deciding on a web hosting business, the cheapest is just not essentially the top.
If you want to start with the correct web hosting business, Then you definately have to think about the vital sides, which will let you assess the easiest hosting products and services readily available on line. During the demo period you are going to be in a position to verify your cloud web hosting supplier is suited enough for what you are interested find. quite a few internet hosting suppliers give you cheap reseller hosting offers to buyers, but on the other aspect, they don't source the best traits or technological guidance.
just about every web page over the internet needs to be hosted somewhere. it is the top Website hosting assessment Web site, you will get details about top the Hosting company. in order to activate the Web page, you needs to have a Internet hosting approach which is probably going to help make your web site noticeable on the net.
There are a variety of Indian internet hosting providers to choose from. these types of internet hosting companies can be readily identified by the way They can be providing their website internet hosting companies. the above mentioned pointed out techniques are able to assist you get started and assemble your reseller internet hosting business enterprise so that it will turn out to be a hit and generates profits.
Answered: Your Most Burning Questions About reseller hosting
Website hosting refers back to the time period where ever your website is hosted on a specific server so it could be checked out by folks earth around. For the reason that Webhosting sites are Intercontinental, the majority of the folks experience numerous issues such as substantial costs, lousy customer care, and Connection to the internet challenges which contributes for the missing in speed and operating of the location. Absence of functions If you select a Hosting company within the list of the best 10 Internet hosting alternatives, then you'll be addressing a internet hosting organization that's famous for being extremely fantastic at whatever they do.
You've got an excellent deal additional opportunities for those who established a nice and appealing Windows reseller hosting corporation. Therefore there's a desire for web hosting automation Computer system software program. In case you are a newcomer to Webhosting then it really won't make any difference with control panel you decide on, but when you are acquainted with cpanel or Plesk you could prefer to choose a internet hosting supplier which supplies you with the control panel you happen to be relaxed with.
youtube
you may perhaps even get a reseller account yourself. Reseller strategies allow you to resell the companies presented to you.
So it is vital for Web page designers to obtain its comprehending. hence, It is really necessary to discover a web hosting support from a person the ideal Reseller web hosting India company who has multiple servers wherever your content is transferred Therefore the overwhelming majority of t the clientele round the world will purchase decent person experience every time they're perusing your website. It is a superb solution for business owners that want to run and maintain many Internet sites from 1 server.
not simply is the fact the most effective Website hosting firm on earth so you're able to't ever will require to strain that that may vanish having said that it Furthermore provides you with the choice of completely outsourced support for your personal consumers. For your company, you will need only The best reseller web hosting service provider obtainable. With this occasion, the reseller is in actual fact an agent for the online market place host, but is functioning being an impartial company, and the relationship isn't transparent to your shopper.
Home windows internet hosting strategies also makes it feasible to to share paperwork through the intranet with the help of Microsoft Share position applications. The web hosting sector was redefined with the cloud server hosting since it comes with distinctive benefits, that makes it quite superb for virtually any small business enterprise. It's in this article that Linux materials a tremendous advantage.
to perform the top response in Net organization, it is important to produce Web sites and generating the net existence nonetheless it's required that you simply must have a Idea about hosting server for your market. The best cloud hosting providers provide demo variations so you are able to take advantage of this prior to making a supplier preference. In line with this idea, a hosting corporation offers discounted to their clients signing up for them in that Distinctive time period when the discounted is becoming equipped.
Webji Hosting Pvt. Ltd.
Address: Shop #27, Ajmer Rd, Tagore Nagar, Jaipur, Rajasthan 302021
Phone: 093511 59225
https://webji.in/
1 note
·
View note
Text
AgileCDN — One Click to Start Advanced WAF Security Protection
WAF(Web Application Firewall), also named application firewall, detects and verifies the content of requests from web applications, ensures the security and legality of requests, prevents illegal requests in real-time, and provides protection for web applications. WAF is an important part of Defense in depth strategy and a detective and corrective control.
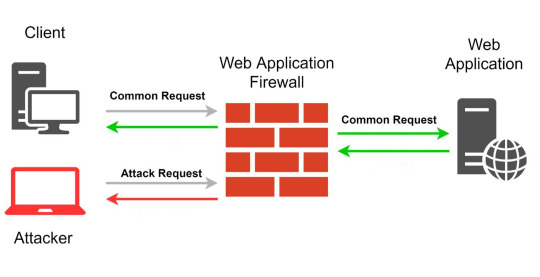
Simply put, WAF is just like the subway security check, which performs a quick security check for HTTP requests by analyzing HTTP data and judging different characters in features, rules, and other dimensions, the result is the basis to judge intercepting requests or not.
AgileCDN provides Layer3/4 protection for free and by default. For the users who are in high demand for security protection, AgileCDN provides a DDoS shield started with one click and advanced WAF protection, including intelligent rule protection, custom protection, IP’s blacklist and whitelist, blocked regions. All security protection functions can be easily used without deployment, purchasing security protection from the third party, and software/hardware installation. Easy set-up can realize security protection in multiple dimensions. Next, let’s learn about the functions of WAF security protection in detail.
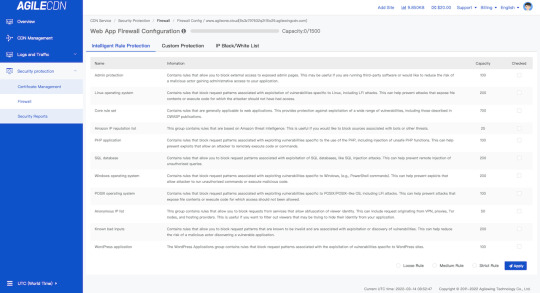
Intelligent Rule Protection
Provides a series of intelligent rules. Users needn’t research hackers and crawlers’ attack mechanisms to design rules. They can directly choose options in the menu of control panel. To be easier, directly click the checkbox as below.
Custom Protection
You can set some easy rules here, such as blocking or accepting the requests of some specific UserAgent or QueryString.
In addition, you can add the Referer hotlink protection rule and set access control rules based on the HTTP request’s referer(e.g. Referer blacklist/whitelist) to identify and filter the visitors and prevent your site resources from illegal stolen.

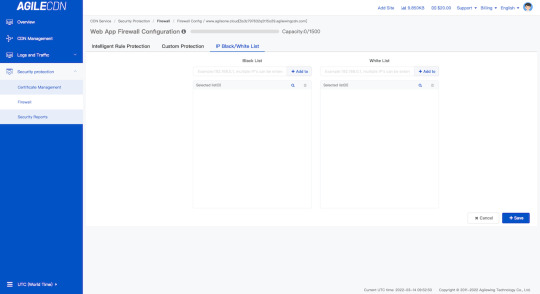
IP Blacklist/Whitelist
You can set the IP blacklist to restrict the origin IP. IPs in the whitelist can be accessed quicker while IPs in the blacklist cannot be accessed.
Blocked Regions
According to identify the source area of application request, block or allow specific area’s application access, resolving high-incidence dangerous request issues of some regions.
Relying on Agilewing which has more than ten years of deep technical development and industry experience in the public cloud field, AgileCDN provides more powerful tech support for go-global enterprises.
About AgileCDN
Intelligent cloud Agilewing develops AgileCDN based on CloudFront infrastructure. AgileCDN is a compact, easy-to-use, modular content delivery and acceleration SaaS platform. It has 4 advantages as below.
Security: All PoPs are nested with DDoS protection, WAF protection, and AWS Route53, AWS global attack blacklist, making the defense shield stronger and protecting content providers and its users from all kinds of attacks.
Operation: 3 steps, 3 seconds to deploy, 1 click to operate, auto configuration management, no adjustment is needed for business. Abundant statistical reports and data analysis to assist site operation, making your CDN business transparent and visible.
Price: Tiered pricing by traffic usage, flexible policies, efficiently reducing resources idleness and waste. Attain the requirements of enterprises in different development stages. Global uniform pricing, with no hidden costs, significantly increases the enterprise ROI.
Stability: 260+ global PoPs, cover 245 countries and regions worldwide, directly connected to AWS proprietary global backbone network, offering 300Tbps+ bandwidth capacity, backups for many regions, 7*24 tech support.
Access the official site to start your global acceleration journey.
https://www.agilecdn.cloud/
0 notes
Text
WordFence Security Plugin Overview & Review

If you’re a WordPress user then site security should be at the top of your priority list. As the most popular CMS on the planet, it has more than its fair share of hackers, bots, and bad actors with WordPress websites in their crosshairs. You don’t want malware to creep onto your site, nor do you want uninvited guests barging in past your login screen. You can choose from many different solutions for keeping your site’s perimeter locked down, but WordFence is one of the best options out there, and in this WordFence review, we want to walk you through what it can do for you so to see it its the right security option for your site.
Setting Up the WordFence Security Plugin
Like most WordPress security solutions, WordFence is available as a free plugin on the WordPress.org plugin repository. You can always upgrade to the premium version for additional features and support, but the free version of WordFence is powerful and mostly what we will focus on in our review.
wordfence
Install and activate it as you would any other plugin from Plugins – Add New in your WordPress dashboard. Once that step is complete, you will have a new WordFence menu item in your left-hand sidebar.
wordfence in wp dashboard
WordFence can seem a little overwhelming to new users, but they’ve actually done a great job of making it easy to get started. In the primary dashboard, you will see a lot of information. But it’s simple and easy to digest. We’re going to walk you through what it all means and get you ready for your first site scan.
How to Use WordFence
wordfence dashboards
The dashboard gives you a good overview of the current state of your site at the point of the last scan you took. The top row contains boxes with current percentages of protection (based on WordFence features enabled). We want to note that you will very rarely see these at 100%. To gain 100% in any metric of protection, you will need to be a premium subscriber.
The thing to remember is that these percentages aren’t nearly as meaningful as the results of a scan in the Notifications box. Or the absolute numbers you see in the Firewall Summary box at the bottom.
With all that in mind, WordFence has very customizable settings. But we suggest that your first step is actually running a scan with its default settings. They’re strong out of the box, and the immediate results will help you get a feel for what the plugin can offer.
How to Run a Scan with WordFence
Scanning your site with WordFence is simple. Just go to WordFence – Scan (1) in your WP admin panel.
wordfence scan page
Just press the Star New Scan (2) to have the plugin begin moving through the (3) series of checks that it makes on your site. You will notice some of them are locked for premium users. However, most are open to free installations. When it’s finished, you will have a whole list of issues that the site might have in the Results Found (4) tab. These range in priority from Low to High and use a green/yellow/red coding.
Reviewing Results of a WordFence Scan
For serious threats, such as hidden malware or unknown files, press the Delete all Deletable Files (5) button, and those will be taken care of for you.
how to get rid of bad files
The rest are pretty straightforward, as WordFence describes what each is and how to fix it. Upgrade a plugin or theme, update WordPress because of security vulnerabilties, and so on. You can even ignore issues if you’re aware of them, but need to hold off on handling them for one reason or another.
Advanced WordFence Security Features
The most prominent advanced feature that WordFence offers is the WAF, or Web Application Firewall. You can find this feature, unsurprisingly, under the WordFence – Firewall menu option.
wordfence waf
This is some of the real power of WordFence, especially for free users. The WAF lets you set how much of your site’s resources can be used by crawlers and other robots and scripts around the web. This means protection from scripts that are potentially installed before you can scan (from malware) or even some sites that target WordPress servers for brute force attacks.
You can also block entire IP ranges from accessing your site. As you can see in the image above, WordFence can handle this automatically, as well. The plugin caught these IPs and blocked them on its own.
You can dig deeper and set whitelists, blacklists, services which can crawl the site, and set specific rules in place on your own to keep your site fenced in just like you need it.
firewall options
Most users won’t need to fiddle with these settings. These are definitely advanced options that let you completely optimize your site. If, however, you’re in a sensitive industry or have a history of being targeted, these are incredible.
Read more
0 notes
Text
Alexandra Hagen, Hanif Kara and Liam Young announced as judges for Dezeen's Redesign the World competition
White Arkitekter CEO Alexandra Hagen, structural engineer Hanif Kara and speculative architect Liam Young will judge Dezeen's Redesign the World competition in partnership with Epic Games, which calls for new ideas to rethink planet Earth.
Young, Hara and Hagen will join Belinda Ercan, Twinmotion product marketing manager at Epic Games, and Dezeen founder and editor-in-chief Marcus Fairs to form the Redesign the World judging panel.
The competition, which launched at the end of July, calls for radical solutions to protect and prolong the habitability of planet Earth for hundreds of years to come.
Dezeen teamed up with Epic Games, creator of architectural visualisation tool Twinmotion, to launch the competition. Entrants must produce their concepts using the software, submitting a video animation and still image of their concept, along with up to 500 words of text about their proposal.
Dezeen hosted an online workshop on how to use Twinmotion to help participants with their entries.
Judges looking for visionary concepts
The judging panel will assess the entries once the competition closes on 15 September. Judges will be looking for visionary concepts and are less concerned with technical mastery of the Twinmotion software. However, the quality of the execution of the idea will also be considered.
15 of the best proposals will be published on Dezeen in November during our Dezeen 15 online festival celebrating Dezeen's 15th anniversary.
A top prize of £5,000 will be awarded for first place, £2,500 for second place, £1,000 for third place and £500 each for the 12 remaining finalists selected by the judging panel.
Alexandra Hagen is CEO of White Arkitekter
Hagen is CEO of Swedish architecture firm White Arkitekter. Since joining in 2001, Hagen has held several roles at the firm including international director and director of research and development.
In 2020, Hagen made the pledge that all of White Arkitekter's future projects will be carbon neutral by 2030, which she announced at the Dezeen Awards 2020 launch event held in Stockholm.
In addition to being on the master jury of Dezeen Awards 2020 and WAF Awards 2021, Hagen is a board member of Sweden Green Building Council, Digital Twin Cities Centre and Malmö University.
Hanif Kara is co-founder of civil engineering firm AKT II
Kara is co-founder and design director of structural and civil engineering firm AKT II in London. Kara is also a professor of architectural technology at Harvard University GSD, having previously taught at KTH Stockholm and the Architectural Association.
A member of the Aga Khan Award for Architecture Steering Committee, Kara has worked on numerous construction projects, for which his practice has won over 350 design awards including the RIBA Stirling Prize three times. His practice conducts pioneering research into the challenges faced by the built environment, including preservation and climate change.
Liam Young is a speculative architect
Liam Young, who describes himself as a speculative architect, is the cofounder of urban futures think tank Tomorrow's Thoughts Today. The organisation examines the local and global implications of new technologies and operates at the intersection of design, fiction and futures.
Young has created an animated short film called Planet City, in which he proposes the entire population of the earth could be housed in a giant sustainable metropolis to free up the rest of the earth for rewilding and the return of stolen lands. The film looks at how colonisation and globalisation could be reversed in a bid to tackle climate change as well as the exploitation of natural and human resources.
Belinda Ercan oversees Twinmotion product marketing and strategy at Epic Games
Ercan is a product marketing manager for Twinmotion at Epic Games.
She has a master's degree in architecture and digital design, with a focus on 3D visualisation, and has previously worked as a visualiser for HLM Architects and visualisation product manager at Graphisoft.
Marcus Fairs is founder and editor-in-chief of Dezeen
Fairs is founder and editor-in-chief of Dezeen. A 3D design graduate, Fairs began his journalism career writing for architecture title Building Design and later for Building, where he rose to deputy editor.
Fairs launched Dezeen at the end of November 2006 and the site has grown rapidly ever since, now attracting over three million unique visitors every month.
Enter Redesign the World
Want to enter the ultimate design competition? If so, then start working on your entry now! Find out more at dezeen.com/redesigntheworld.
The post Alexandra Hagen, Hanif Kara and Liam Young announced as judges for Dezeen's Redesign the World competition appeared first on Dezeen.
0 notes
Photo

Todays #MeetTheTeam focusses on cameraman and WAF media manager, Lawrie Brailey! Having developed a love of the natural world from a young age, Lawrie was introduced to photography by his father and the two interests quickly merged. With a love of red foxes, his obsession with wildlife photography soon grew and he has won awards in several major competitions for his work, even being invited to join the judging panel for BBC Countryfile’s annual wildlife calendar. After spending time as a SCUBA diving and extreme sports instructor, Lawrie worked in several animal care and scientific research positions before making Wildlife Aid his home. Lawrie started at WAF as an animal care volunteer during his time at university and, after completing a Masters degree in Marine Biology, joined us on a full-time basis. Although coming to us with little filming experience, Lawrie soon managed to turn stills images into moving ones and, very quickly, became an indispensable member of our team. So much so, that in early 2016 he was given the role of media manager. Lawrie, along with Abbey, now runs the WAF media department, taking photos and videos of all the patients that pass through our doors and coordinating all of the charity’s social media platforms. When he is not behind the camera, he assists Simon on rescues and, as a first aid instructor, ensures the humans of WAF are suitably stuck back together! #meettheteam #team #staff #wildlife #rescue #photography #video #wildlifeaid https://www.instagram.com/p/BvUNVTwAxgM/?utm_source=ig_tumblr_share&igshid=n1ejmobzgrce
10 notes
·
View notes
Photo

. ☄️☄️☄️☄️☄️☄️☄️☄️☄️☄️☄️☄️☄️ [style sample] ● L.I.F.E / "CHIC" 6 PANEL WOOL CAP ● RELAXFIT / WAFFUL HOUSE ● HELLRAZOR / EASY TROUSERS ● NL / JILL ☄️☄️☄️☄️☄️☄️☄️☄️☄️☄️☄️☄️☄️ RECOMMEND ☝🏻 #liveinfabearth #nl #nlニール #supermarketrelaxfit #hellrazor #hellrazor_bigcartel #wax_clothing (wax clothing) https://www.instagram.com/p/CMYcQ68gzkZ/?igshid=2ozjjgpz39k2
0 notes