#windows os
Text




Windows Vista (2007-2009)
#queued#windows vista#windows#windowscore#webcore#aesthetic#gloss#glossy web#web 2.0 gloss#glossy aesthetic#y2k#retrofuturistic#naturecore#utopian virtual#webpunk#3d art#web#old web#old os#windows os#2007#2009#winvista#frutiger aero
63 notes
·
View notes
Text



Windows OS's As Humans
#8bityinyang#windows humans#windows humanized#windows 1#windows#windows 3.1#windows 95#windows 98#windows 2000#windows me#windows millenium edition#windows xp#windows vista#windows 7#windows 8#windows 10#windows 11#8bityinyangart#windows os
56 notes
·
View notes
Text
Exploring Kerberos and its related attacks
Introduction
In the world of cybersecurity, authentication is the linchpin upon which secure communications and data access rely. Kerberos, a network authentication protocol developed by MIT, has played a pivotal role in securing networks, particularly in Microsoft Windows environments. In this in-depth exploration of Kerberos, we'll delve into its technical intricacies, vulnerabilities, and the countermeasures that can help organizations safeguard their systems.
Understanding Kerberos: The Fundamentals
At its core, Kerberos is designed to provide secure authentication for users and services over a non-secure network, such as the internet. It operates on the principle of "need-to-know," ensuring that only authenticated users can access specific resources. To grasp its inner workings, let's break down Kerberos into its key components:
1. Authentication Server (AS)
The AS is the initial point of contact for authentication. When a user requests access to a service, the AS verifies their identity and issues a Ticket Granting Ticket (TGT) if authentication is successful.
2. Ticket Granting Server (TGS)
Once a user has a TGT, they can request access to various services without re-entering their credentials. The TGS validates the TGT and issues a service ticket for the requested resource.
3. Realm
A realm in Kerberos represents a security domain. It defines a specific set of users, services, and authentication servers that share a common Kerberos database.
4. Service Principal
A service principal represents a network service (e.g., a file server or email server) within the realm. Each service principal has a unique encryption key.
Vulnerabilities in Kerberos
While Kerberos is a robust authentication protocol, it is not immune to vulnerabilities and attacks. Understanding these vulnerabilities is crucial for securing a network environment that relies on Kerberos for authentication.
1. AS-REP Roasting
AS-REP Roasting is a common attack that exploits weak user account settings. When a user's pre-authentication is disabled, an attacker can request a TGT for that user without presenting a password. They can then brute-force the TGT offline to obtain the user's plaintext password.
2. Pass-the-Ticket Attacks
In a Pass-the-Ticket attack, an attacker steals a TGT or service ticket and uses it to impersonate a legitimate user or service. This attack can lead to unauthorized access and privilege escalation.
3. Golden Ticket Attacks
A Golden Ticket attack allows an attacker to forge TGTs, granting them unrestricted access to the domain. To execute this attack, the attacker needs to compromise the Key Distribution Center (KDC) long-term secret key.
4. Silver Ticket Attacks
Silver Ticket attacks target specific services or resources. Attackers create forged service tickets to access a particular resource without having the user's password.
Technical Aspects and Formulas
To gain a deeper understanding of Kerberos and its related attacks, let's delve into some of the technical aspects and cryptographic formulas that underpin the protocol:
1. Kerberos Authentication Flow
The Kerberos authentication process involves several steps, including ticket requests, encryption, and decryption. It relies on various cryptographic algorithms, such as DES, AES, and HMAC.
2. Ticket Granting Ticket (TGT) Structure
A TGT typically consists of a user's identity, the requested service, a timestamp, and other information encrypted with the TGS's secret key. The TGT structure can be expressed as:
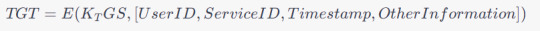
3. Encryption Keys
Kerberos relies on encryption keys generated during the authentication process. The user's password is typically used to derive these keys. The process involves key generation and hashing formulas.
Mitigating Kerberos Vulnerabilities
To protect against Kerberos-related vulnerabilities and attacks, organizations can implement several strategies and countermeasures:
1. Enforce Strong Password Policies
Strong password policies can mitigate attacks like AS-REP Roasting. Ensure that users create complex, difficult-to-guess passwords and consider enabling pre-authentication.
2. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication. This can thwart various Kerberos attacks.
3. Regularly Rotate Encryption Keys
Frequent rotation of encryption keys can limit an attacker's ability to use stolen tickets. Implement a key rotation policy and ensure it aligns with best practices.
4. Monitor and Audit Kerberos Traffic
Continuous monitoring and auditing of Kerberos traffic can help detect and respond to suspicious activities. Utilize security information and event management (SIEM) tools for this purpose.
5. Segment and Isolate Critical Systems
Isolating sensitive systems from less-trusted parts of the network can reduce the risk of lateral movement by attackers who compromise one system.
6. Patch and Update
Regularly update and patch your Kerberos implementation to mitigate known vulnerabilities and stay ahead of emerging threats.
4. Kerberos Encryption Algorithms
Kerberos employs various encryption algorithms to protect data during authentication and ticket issuance. Common cryptographic algorithms include:
DES (Data Encryption Standard): Historically used, but now considered weak due to its susceptibility to brute-force attacks.
3DES (Triple DES): An improvement over DES, it applies the DES encryption algorithm three times to enhance security.
AES (Advanced Encryption Standard): A strong symmetric encryption algorithm, widely used in modern Kerberos implementations for better security.
HMAC (Hash-based Message Authentication Code): Used for message integrity, HMAC ensures that messages have not been tampered with during transmission.
5. Key Distribution Center (KDC)
The KDC is the heart of the Kerberos authentication system. It consists of two components: the Authentication Server (AS) and the Ticket Granting Server (TGS). The AS handles initial authentication requests and issues TGTs, while the TGS validates these TGTs and issues service tickets. This separation of functions enhances security by minimizing exposure to attack vectors.
6. Salting and Nonces
To thwart replay attacks, Kerberos employs salting and nonces (random numbers). Salting involves appending a random value to a user's password before hashing, making it more resistant to dictionary attacks. Nonces are unique values generated for each authentication request to prevent replay attacks.
Now, let's delve into further Kerberos vulnerabilities and their technical aspects:
7. Ticket-Granting Ticket (TGT) Expiry Time
By default, TGTs have a relatively long expiry time, which can be exploited by attackers if they can intercept and reuse them. Administrators should consider reducing TGT lifetimes to mitigate this risk.
8. Ticket Granting Ticket Renewal
Kerberos allows TGT renewal without re-entering the password. While convenient, this feature can be abused by attackers if they manage to capture a TGT. Limiting the number of renewals or implementing MFA for renewals can help mitigate this risk.
9. Service Principal Name (SPN) Abuse
Attackers may exploit misconfigured SPNs to impersonate legitimate services. Regularly review and audit SPNs to ensure they are correctly associated with the intended services.
10. Kerberoasting
Kerberoasting is an attack where attackers target service accounts to obtain service tickets and attempt offline brute-force attacks to recover plaintext passwords. Robust password policies and regular rotation of service account passwords can help mitigate this risk.
11. Silver Ticket and Golden Ticket Attacks
To defend against Silver and Golden Ticket attacks, it's essential to implement strong password policies, limit privileges of service accounts, and monitor for suspicious behavior, such as unusual access patterns.
12. Kerberos Constrained Delegation
Kerberos Constrained Delegation allows a service to impersonate a user to access other services. Misconfigurations can lead to security vulnerabilities, so careful planning and configuration are essential.
Mitigation strategies to counter these vulnerabilities include:
13. Shorter Ticket Lifetimes
Reducing the lifespan of TGTs and service tickets limits the window of opportunity for attackers to misuse captured tickets.
14. Regular Password Changes
Frequent password changes for service accounts and users can thwart offline attacks and reduce the impact of credential compromise.
15. Least Privilege Principle
Implement the principle of least privilege for service accounts, limiting their access only to the resources they need, and monitor for unusual access patterns.
16. Logging and Monitoring
Comprehensive logging and real-time monitoring of Kerberos traffic can help identify and respond to suspicious activities, including repeated failed authentication attempts.
Kerberos Delegation: A Technical Deep Dive
1. Understanding Delegation in Kerberos
Kerberos delegation allows a service to act on behalf of a user to access other services without requiring the user to reauthenticate for each service. This capability enhances the efficiency and usability of networked applications, particularly in complex environments where multiple services need to interact on behalf of a user.
2. Types of Kerberos Delegation
Kerberos delegation can be categorized into two main types:
Constrained Delegation: This type of delegation restricts the services a service can access on behalf of a user. It allows administrators to specify which services a given service can impersonate for the user.
Unconstrained Delegation: In contrast, unconstrained delegation grants the service full delegation rights, enabling it to access any service on behalf of the user without restrictions. Unconstrained delegation poses higher security risks and is generally discouraged.
3. How Delegation Works
Here's a step-by-step breakdown of how delegation occurs within the Kerberos authentication process:
Initial Authentication: The user logs in and obtains a Ticket Granting Ticket (TGT) from the Authentication Server (AS).
Request to Access a Delegated Service: The user requests access to a service that supports delegation.
Service Ticket Request: The user's client requests a service ticket from the Ticket Granting Server (TGS) to access the delegated service. The TGS issues a service ticket for the delegated service and includes the user's TGT encrypted with the service's secret key.
Service Access: The user presents the service ticket to the delegated service. The service decrypts the ticket using its secret key and obtains the user's TGT.
Secondary Authentication: The delegated service can then use the user's TGT to authenticate to other services on behalf of the user without the user's direct involvement. This secondary authentication occurs transparently to the user.
4. Delegation and Impersonation
Kerberos delegation can be seen as a form of impersonation. The delegated service effectively impersonates the user to access other services. This impersonation is secure because the delegated service needs to present both the user's TGT and the service ticket for the delegated service, proving it has the user's explicit permission.
5. Delegation in Multi-Tier Applications
Kerberos delegation is particularly useful in multi-tier applications, where multiple services are involved in processing a user's request. It allows a front-end service to securely delegate authentication to a back-end service on behalf of the user.
6. Protocol Extensions for Delegation
Kerberos extensions, such as Service-for-User (S4U) extensions, enable a service to request service tickets on behalf of a user without needing the user's TGT. These extensions are valuable for cases where the delegated service cannot obtain the user's TGT directly.
7. Benefits of Kerberos Delegation
Efficiency: Delegation eliminates the need for the user to repeatedly authenticate to access multiple services, improving the user experience.
Security: Delegation is secure because it relies on Kerberos authentication and requires proper configuration to work effectively.
Scalability: Delegation is well-suited for complex environments with multiple services and tiers, enhancing scalability.
In this comprehensive exploration of Kerberos, we've covered a wide array of topics, from the fundamentals of its authentication process to advanced concepts like delegation.
Kerberos, as a network authentication protocol, forms the backbone of secure communication within organizations. Its core principles include the use of tickets, encryption, and a trusted third-party Authentication Server (AS) to ensure secure client-service interactions.
Security is a paramount concern in Kerberos. The protocol employs encryption, timestamps, and mutual authentication to guarantee that only authorized users gain access to network resources. Understanding these security mechanisms is vital for maintaining robust network security.
Despite its robustness, Kerberos is not impervious to vulnerabilities. Attacks like AS-REP Roasting, Pass-the-Ticket, Golden Ticket, and Silver Ticket attacks can compromise security. Organizations must be aware of these vulnerabilities to take appropriate countermeasures.
Implementing best practices is essential for securing Kerberos-based authentication systems. These practices include enforcing strong password policies, regular key rotation, continuous monitoring, and employee training.
Delving into advanced Kerberos concepts, we explored delegation – both constrained and unconstrained. Delegation allows services to act on behalf of users, enhancing usability and efficiency in complex, multi-tiered applications. Understanding delegation and its security implications is crucial in such scenarios.
Advanced Kerberos concepts introduce additional security considerations. These include implementing fine-grained access controls, monitoring for unusual activities, and regularly analyzing logs to detect and respond to security incidents.
So to conclude, Kerberos stands as a foundational authentication protocol that plays a pivotal role in securing networked environments. It offers robust security mechanisms and advanced features like delegation to enhance usability. Staying informed about Kerberos' complexities, vulnerabilities, and best practices is essential to maintain a strong security posture in the ever-evolving landscape of cybersecurity.
12 notes
·
View notes
Text

#Rest of my dream figures arrived ;u ;#THEYRE ALL SO CUTE#os-tan#me-tan#XP-tan#2k-tan#95-tan#windows OS#Microsoft#retro computer#mine
15 notes
·
View notes
Text




#windows os#windows os tan#os tan#trouble windows#inut tan#inu t tan#anime figures#anime figure#inucore#dogcore#kawaiicore#animecore#webcore#old web#internetcore#moecore#old anime#old internet#bug posts#web find#cutecore#2000s core#2000score#2000s internet#2000s web#2000s#puppycore#kemono#kemonomimi#kawaii anime
43 notes
·
View notes
Note
*magic* baldi teloports into a (appropriately) old windows os


#windows 95#windows95#windows os#os#bbieal:3#bbieal baldi#bbieal#baldis basics#baldi au#baldi art#baldi fanart#baldimore#baldi ask blog
7 notes
·
View notes
Text


#fringe - the Dell notebook by Olivia, Symb_OS? No, Windows😀
#fringe#fringefox#olivia dunham#anna torv#series#fantasy#tvedit#fringeedit#tv shows#tvandfilm#operatingsystem#windows os
9 notes
·
View notes
Text
If Microsoft ever made a Windows Peter Platter OS system collaboration with Sid and Marty Krofft (fanmade)


(credits to Sid and Marty Krofft for making The Bugaloos and its character peter platter)
#the bugaloos#peter platter#the bugaloos tv show#i love peter platter#sid and marty krofft#70s tv show#old tv show#windows#microsoft#microsoft windows#fanmade#Windows Peter Platter#Fanmade Windows codename#windows os#Peter Platter OS#bugaloos tv show#the bugaloos peter platter#peter platter the bugaloos#bugaloos#Based off of windows xp#windows xp#Fake windows os
2 notes
·
View notes
Text
Hey, Linux Community, do you have any linux distro recommendations for a window user with no coding experience? Thinking of changing as my laptop gets older and slower, and I honestly don't know where to start.
3 notes
·
View notes
Text
Microsoft Windows in a Nutshell
(Treat this like you would Vegetable Justice and don't take it seriously or get offended, even if I pick at your favorite OS here.)
1.0: Yikes that's bright, good thing this is the first one AND you can change how bright it is?
2.0: Well, at least- hey, wait a minute...
3.0: It's too bad you got forgotten as soon as your ".1" version came out.
MultiMedia Extensions: Actually, it was you who was the first one with a startup sound.
3.1: YIPPEE! Dododo do~
N.T 3.1: For the extra nerdy nerds... And business people, apparently?
95: Now we're cooking! ... And it celebrated being shut down?
N.T 4: Huh, it took you until about 1996 to be as easy to use as your home counterpart?
98: Good thing Microsoft realized you needed a quick fix, so you got a 2nd edition.
ME: 2000's evil twin.. Make that "Incompetent" twin.
2000: A forgotten legend...?
Whistler: ... You know, that watercolor theme is kinda cute.
XP: Don't mind people comparing you to a Fisher Price toy... You are AWESOME!
Longhorn: Man, if only we got that Samsung the- er, beautiful original theme~
Vista: ... At least you look nice? They could've specified on the specs.
7: Vista but with less complaints from everybody.
8(.1): But my computer can't even become a tablet!
10: You're okay, but I don't need the junk you occasionally want me to set up.
11: NO, YOU ARE NOT MAC OS!
12: You better not try and shove A.I down my throat-
0 notes
Text
I know I'm late to the party, but why did Microsoft do windows 11 like this? I only now have to interact with it because work had to update for security reasons.
Like, it's a small gripe, and I've spent a grand total of like an hour with it. So, maybe there's a way to get it back. But one of the things I liked was the ability to right click and hit D to quickly delete a file without having to move the mouse more finely to actually select delete.
Also stop grouping my files. Found a tutorial online to unset that as the default, but it didn't work, and I think it has to do with it being a work computer.
1 note
·
View note
Photo

Microsoft Windows Ugly Sweater For 2023 Is Hardly Ugly; It’s Nostalgic
So nostalgic! 🥰
Follow us for more Tech Culture and Lifestyle Stuff.
0 notes
Text


Some redesigns and an alternate design for some of the humanized Windows OS's that I made.
Alt Text:
3.1 Alternate Design
Windows 7 Redesign
Windows Humanized: XP Redesign
Human! Windows 11 Redesign
ID: Human Windows XP's updated design has ear-length wavy grass-green hair, a round face, vertical oval black eyes, big round glasses, round eyebrows, a button nose, a cute open smile, and light pinkish skin. They're wearing a white short-sleeved button up with rolled up sleeves, a cerulean vest with grass-green buttons, grass-green long pants, and blue loafers. Their updated design as depicted here is now plus-sized.
Human Windows 11’s updated design has ear-length cerulean hair, round cerulean eyes, thick long straight eyebrows, pale orangey pinkish skin, silver cuff earrings, a tall triangular nose, and a closed smile. They are taller than Human XP and are wearing a bluish off-white long-sleeve jacket with shoulder pads, bluish off-white long pants and loafers, and a cerulean button-up with ruffles on the chest.
Human Windows 3.1’s alternate design has a yellow high-top hairdo, emerald-green colored contacts in their round eyes, a rectangular face, a flatter nose, a smile showing only their teeth, and dark brown skin. They're wearing a dark blue button up, a red bowtie, and a bright teal suit with the mid-to-late 1990's version of the MS Windows logo on the left lapel of their jacket and loafers.
Human Windows 7's updated design has ear-length gold-yellow wavy hair with an ahoge and hexagonal highlights, light pinkish skin, blue gradient eyes, a small button nose, round blue sunglasses, and a closed smile. They're wearing a blue T-shirt with an aurora pattern on it under a now-green short-sleeve button up with a bubble pattern, long blue-to-yellow gradient pants, and red converse-style sneakers with daisies where the stars would be. End ID.
#8bityinyang#windows#windows humanized#windows 3.1#windows xp#windows 7#windows 11#windows os#8bityinyangart
9 notes
·
View notes
Text
0 notes
Text

fixing away
#my art#OC#Utau#utauloid#android#cute#os-tan#windows OS#ibm#retro#retro computer#tinkering#drawing#doodle#please do not steal
19 notes
·
View notes
Text
How to remove the activate windows watermark without the product key
Estimated reading time: 2 minutes
In this article, I am going to share how you can remove the activate windows watermark without the product key. This is not illegal as we are not using any product key generator or anything. However, we are just disabling the watermark. Using the steps I share below you should be able to remove the activate windows watermark without the product key. And use…

View On WordPress
0 notes