Text
Organization, Policy, Requirement, and Principle
Organization
person or group of people that has its own functions with responsibilities, authorities and relationships to achieve its objectives.~ ISO 14017:2022, Environmental management — Requirements with guidance for verification and validation of water statements
group of people and facilities with an arrangement of responsibilities, authorities, and relationships~ ISO/IEC 33001:2015,…
View On WordPress
0 notes
Text
What is security?
The core concept of security is about protection. To be specific, security in discussion has to consider 1) what to protect, 2) why to protect, 3) how to protect, and 4) to what extent. Given the key points above, I define security as follows:
Security is the intended outcome of protective services considering assets, risks, and controls.~ Wentz Wu
View On WordPress
0 notes
Text
Performance
Performance
Measurable result~ ISO 14050:2020 Environmental management — Vocabulary
Carrying out or execution~ ISO/IEC 21000-5:2004 Information technology — Multimedia framework (MPEG-21) — Part 5: Rights Expression Language
Achievements of an activity, a process or an organization~ ISO 50007:2017 Energy services — Guidelines for the assessment and improvement of the energy service to…
View On WordPress
0 notes
Text
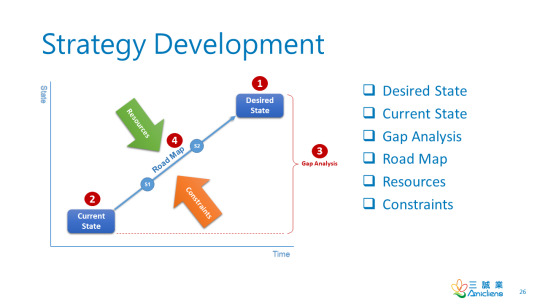
Goal, Objective, and Performance
Strategy Development
Performance is the measurable result of carrying out or executing activities to achieve an objective.
An objective refers to the result to be achieved from performing activities.
A goal is the intended outcome of achieving constituent objectives. The outcome is a good result of performance.
View On WordPress
0 notes
Text
Nmap Syntax
Nmap 7.94SVN ( https://nmap.org )Usage: nmap [Scan Type(s)] [Options] {target specification}TARGET SPECIFICATION: Can pass hostnames, IP addresses, networks, etc. Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254 -iL <inputfilename>: Input from list of hosts/networks -iR <num hosts>: Choose random targets --exclude <host1[,host2][,host3],...>: Exclude hosts/networks…
View On WordPress
0 notes
Text
Linux Basics for Hackers
Finding Stuff
locate: searching the entire file system.
whereis: searching the binaries and man page
which: searching binaries in the PATH variable
find: searching with specific pattherns

View On WordPress
0 notes
Text
Linux Shells
Source: Dan Nanni
Linux provides a variety of shells available in /etc/shells.
Bourne (/bin/sh)Developed by Stephen Bourne at Bell Labs, it was a replacement for the Thompson shell. The Bourne shell was the default shell for Version 7 Unix. It was released in 1979 in the Version 7 Unix release distributed to colleges and universities. (Wikipedia)
Bash (/bin/bash)Bash (Bourne Again Shell) is a…

View On WordPress
0 notes
Text
Get Started on CSSLP
CSSLP CBK
CSSLP Exam Outline and AIO
ISC2 Official Resources
CSSLP – Certified Secure Software Lifecycle Professional (ISC2 Official Certification Web Page)
*CSSLP Certification Exam Outline (Effective September 15, 2023)
CSSLP Study Tools and Resources
*CBK Suggested References
Recommended Resources
CSSLP Certification Exam Outline (Effective September 15, 2023)
Official (ISC)2 Guide to…

View On WordPress
0 notes
Text
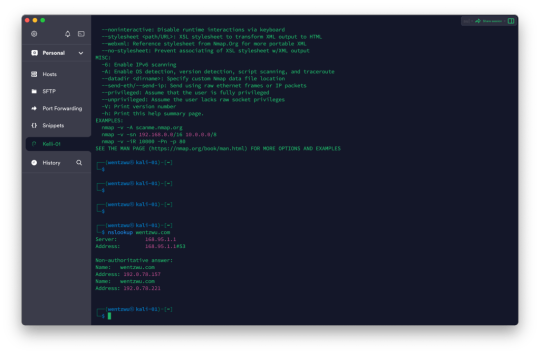
Network Mapper (Nmap)
The Network Mapper (Nmap) utility can do the following tasks:
Target Enumeration (-iL): Enumerating a target specification (simply listing targets to scan).
Host Discovery (-sn): Discovering live hosts
Port Scan: Identifying services provisioned
If none is specified, nmap will do all the above.
$ nmap 10.10.10.100/30 Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-18 06:34 PSTNmap scan…
View On WordPress
0 notes
Text
Security and Risk Management
CIA as Security Objectives
- Control
1. verification that acceptance criteria are metSource: ISO 22716:2007 (Cosmetics — Good Manufacturing Practices (GMP) — Guidelines on Good Manufacturing Practices)2. regulation of variables within specified limitsSource: ISO 11607-1:2019 (Packaging for terminally sterilized medical devices — Part 1: Requirements for materials, sterile barrier systems and…

View On WordPress
0 notes
Text
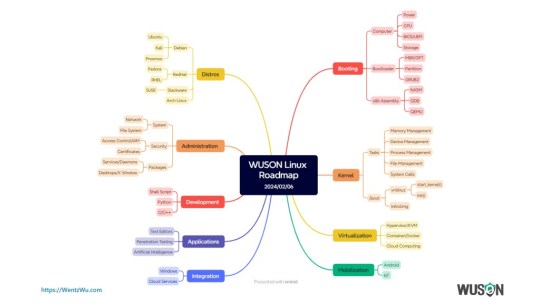
WUSON Linux Roadmap
References
Booting
Bare Bones
x86 Assembly/X86 Architecture
NASM – The Netwide Assembler
Writing An Operating System – The Boot Process (Part 1)
Welcome to QEMU’s documentation!
Kali-Meta
Debian Packages
The Linux Kernel
What are .S files?
Kernel subsystem documentation
Beginning x64 Assembly Programming: From Novice to AVX Professional (book)
View On WordPress
0 notes
Text
CISSP Exam Changes Effective April 15, 2024
New CISSP Exam Outline
Please Note: Effective April 15, 2024, the CISSP exam will be based on a refreshed exam outline. Please refer to the CISSP Exam Outline and our FAQs for more information.
Source: CISSP Certification Exam Outline Summary
New CISSP Exam Languages Availability
Effective 15 April 2024, the following exams will only be delivered in the listed languages: CC – English, Chinese,…
View On WordPress
0 notes
Text
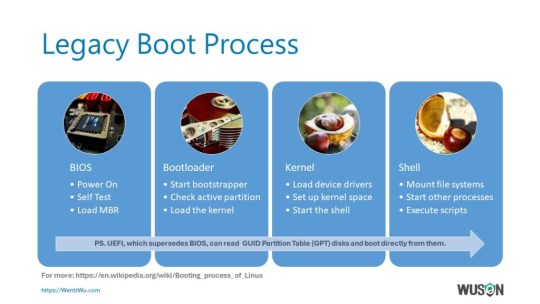
How Computers Boot Up
General Legacy Boot Process
CPU jumps to the reset vector when the power is turned on.
CPU executes the BIOS code to start the Power On Self Test (POST).
BIOS loads the Master Boot Record (MBR) and executes the bootstrapper code.
The bootstrapper determines the active partition and loads the OS boot sectors.
Continue reading How Computers Boot Up
View On WordPress
0 notes
Text
The Evolvement of Linux
Unix was developed by Ken Thompson at Bell Laboratories, a division of AT&T, in 1969.
Linus Torvalds was born in a Swedish-speaking family in Helsinki, Finland, in 1969.
C programming language was created by Dennis Ritchie in 1970.
Unix 7th edition was released in January 1979.
3BSD (Berkeley Software Distribution), the first full distribution of BSD, was released in December 1979.
System…

View On WordPress
0 notes
Text
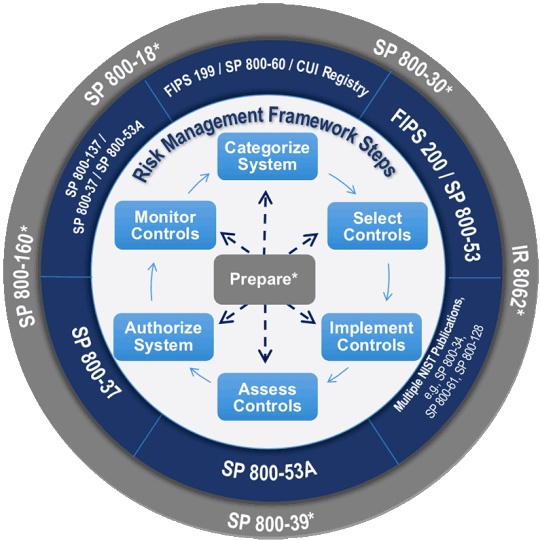
ISC2 CGRC Exam Highlights
NIST RMF (Source: NIST)
With 20 study hours or so, I passed the ISC2 CGRC (formerly known as CAP) exam today (Jan 9, 2024). As a CISSP, I was reluctant to pursue the entry-level exam CC and US government-specific CGRC/CAP because CISSP covers job practices well enough. However, as a CISSP instructor, I must wear the same shoes to prove to my students that CC is a fantastic starter and a…
View On WordPress
0 notes
Text
Common Business Terminologies
Source: THEIIO
A business is an entity with the capability of performing various functions that add value by transforming incoming things into outgoing results to deliver products and services. A business function comprises one or more processes, which can be broken down into minor activities and tasks. Activities can be assigned to the role level and tasks at the individual level.
Source:…

View On WordPress
0 notes
Text
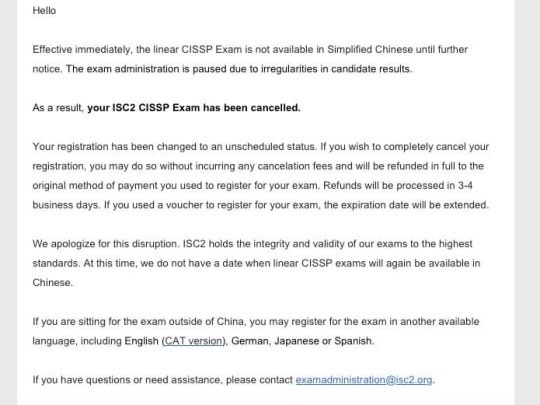
The problem of the CISSP Exam in Simplified Chinese
View On WordPress
0 notes