#is it possible to make your own phone ?? with its own firmware?? has that been done?
Text
AppValley iOS
AppValley is supported about the most up-to-date iOS firmware with no interference with all the protection characteristics introduced by Apple. Even the appvalley alternative produces its own memory space that does not battle usage with additional iOS apps and games. Also Functions on Android.
Can Be AppValley Safe and Sound?
AppValley is 100% Safe. It's totally safe to download any app or even tweak out of your AppValley appstore. The developers ( Twitter ) are very active and are continually tracking the app for problems. In case any arise, they've been fixed nearly immediately. Also, they examine every thing locally to ensure it is safe for you to make use of. AppValley developers upgrade the app routinely, adding fresh, safe and sound material and add in much more security therefore that you are able to download any app or even tweak out of your installer and never having to be concerned about any malwarespyware, viruses, or even whatever else that may endanger your device stability.
AppValley Features:
Nomore jail breaking: AppValley provides you access to more than 1000 choices, which help bypass jailbreak ing. It's possible to personalize the interface or even improve your operating system with AppValley. It retains lots of apps and tweaks to complete the work only perfect!
Protection at the Core: The app has layouts with privacy and protection as its high priorities. It layouts to deal with digital dangers and guarantees powerful having its own safety features inside the app. In addition, it makes certain 100% privacy and safety for the many users. AppValley has got your habit demands covered safely.
User-friendly user interface, Simplicity in its Greatest: AppValley has a simple and userfriendly user interface that enables consumers to have a comfortable encounter. It maps together with lots of tips which enable the user to possess a clean interaction. We consistently respect user experience and also work to supply you with exactly the best.
Countless Apps and video games: AppValley houses more than 1, 000 apps to agree with your needs. It supplies access to tweaks, games, amusement, plus much more. It presents that the best option into this official App retailer as it offers a limitless experience as desired.
Supports most recent iOS Versions: AppValley is no barrier for your iOS upgrades; we grow together with you personally! The app hasn't missed a beat staying upgraded in parallel into Apple's very own operating systems. It regularly improves its functionalities and also UI to suit customer needs. It's now compatible with Apple's latest iOS 1 3 upgrades, creating AppValley relevant and highly efficient to iOS people.
What would be the Favorite Apps and Video Games available on AppValley?
Clash of Clans Hack: Acquire access to unlimited Gold and jewels with the Modern update to the game! AppValley provides you with the top version of the COC Hack app to enjoy a great experience of your favourite video game.
Phoenix jail-break: This really is a user friendly jailbreak ing tool which helps older ios variant users to get the top from their own devices. This tool will then put in Cydia onto the running platform to download apps and tweaks from it .
INDS Emulator: Perform Nintendo games on your own i-phone / / i-pad without jail breaking! AppValley gives 100% free accessibility to download this emulator right onto your apparatus without difficulty. Just a few minutes of one's energy, and your Nintendo favorites will likely soon be accessible in your iOS devices.
Is AppValley 100% FREE?
AppValley is currently 100 percent free of fee if you select the standard subscription, including all of the whistles and bells. This is exactly why it's the smart and 1 st choice of many third party app outlets in the market. In the event you prefer to pick the VIP accessibility, then you certainly can do it too, but you have to pay a couple dollars.
AppValley App Functions:
AppValley is one of the absolute most complete app contractors, that offer loads of apps and games for everybody. It Provides features such as:
Easy to download and set up, User-friendly app, Appropriate for devices on appvalley download ios or even high, No Jail-break desired, Thousands of apps and games available, heaps of apps and matches, Fully tested for stability, protection, and reliability, and Regular upgrades, a Lot more attributes.
2 notes
·
View notes
Text
#1yrago Oh for fuck's sake, not this fucking bullshit again (cryptography edition)

America, Canada, New Zealand, the UK and Australia are in a surveillance alliance called The Five Eyes, through which they share much of their illegally harvested surveillance data.
In a recently released Statement of Principles on Access to Evidence and Encryption, the Five Eyes powers have demanded, again, that strong cryptography be abolished and replaced with defective cryptography so that they can spy on bad guys.
They defend this by saying "Privacy is not absolute."
But of course, working crypto isn't just how we stay private from governments (though god knows all five of the Five Eyes have, in very recent times, proven themselves to be catastrophically unsuited to collect, analyze and act on all of our private and most intimate conversations). It's how we make sure that no one can break into the data from our voting machines, or push lethal fake firmware updates to our pacemakers, or steal all the money from all of the banks, or steal all of the kompromat on all 22,000,000 US military and government employees and contractors who've sought security clearance.
Also, this is bullshit.
Because it won't work.
Here's the text of my go-to post about why this is so fucking stupid. I just can't be bothered anymore. Jesus fucking christ. Seriously? Are we still fucking talking about this? Seriously? Come on, SERIOUSLY?
It’s impossible to overstate how bonkers the idea of sabotaging cryptography is to people who understand information security. If you want to secure your sensitive data either at rest – on your hard drive, in the cloud, on that phone you left on the train last week and never saw again – or on the wire, when you’re sending it to your doctor or your bank or to your work colleagues, you have to use good cryptography. Use deliberately compromised cryptography, that has a back door that only the “good guys” are supposed to have the keys to, and you have effectively no security. You might as well skywrite it as encrypt it with pre-broken, sabotaged encryption.
There are two reasons why this is so. First, there is the question of whether encryption can be made secure while still maintaining a “master key” for the authorities’ use. As lawyer/computer scientist Jonathan Mayer explained, adding the complexity of master keys to our technology will “introduce unquantifiable security risks”. It’s hard enough getting the security systems that protect our homes, finances, health and privacy to be airtight – making them airtight except when the authorities don’t want them to be is impossible.
What these leaders thinks they're saying is, "We will command all the software creators we can reach to introduce back-doors into their tools for us." There are enormous problems with this: there's no back door that only lets good guys go through it. If your Whatsapp or Google Hangouts has a deliberately introduced flaw in it, then foreign spies, criminals, crooked police (like those who fed sensitive information to the tabloids who were implicated in the hacking scandal -- and like the high-level police who secretly worked for organised crime for years), and criminals will eventually discover this vulnerability. They -- and not just the security services -- will be able to use it to intercept all of our communications. That includes things like the pictures of your kids in your bath that you send to your parents to the trade secrets you send to your co-workers.
But this is just for starters. These officials don't understand technology very well, so they doesn't actually know what they're asking for.
For this proposal to work, they will need to stop Britons, Canadians, Americans, Kiwis and Australians from installing software that comes from software creators who are out of their jurisdiction. The very best in secure communications are already free/open source projects, maintained by thousands of independent programmers around the world. They are widely available, and thanks to things like cryptographic signing, it is possible to download these packages from any server in the world (not just big ones like Github) and verify, with a very high degree of confidence, that the software you've downloaded hasn't been tampered with.
Australia is not alone here. The regime they proposes is already in place in countries like Syria, Russia, and Iran (for the record, none of these countries have had much luck with it). There are two means by which authoritarian governments have attempted to restrict the use of secure technology: by network filtering and by technology mandates.
Australian governments have already shown that they believes they can order the nation's ISPs to block access to certain websites (again, for the record, this hasn't worked very well). The next step is to order Chinese-style filtering using deep packet inspection, to try and distinguish traffic and block forbidden programs. This is a formidable technical challenge. Intrinsic to core Internet protocols like IPv4/6, TCP and UDP is the potential to "tunnel" one protocol inside another. This makes the project of figuring out whether a given packet is on the white-list or the black-list transcendentally hard, especially if you want to minimise the number of "good" sessions you accidentally blackhole.
More ambitious is a mandate over which code operating systems in the 5 Eyes nations are allowed to execute. This is very hard. We do have, in Apple's Ios platform and various games consoles, a regime where a single company uses countermeasures to ensure that only software it has blessed can run on the devices it sells to us. These companies could, indeed, be compelled (by an act of Parliament) to block secure software. Even there, you'd have to contend with the fact that other states are unlikely to follow suit, and that means that anyone who bought her Iphone in Paris or Mexico could come to the 5 Eyes countries with all their secure software intact and send messages "we cannot read."
But there is the problem of more open platforms, like GNU/Linux variants, BSD and other unixes, Mac OS X, and all the non-mobile versions of Windows. All of these operating systems are already designed to allow users to execute any code they want to run. The commercial operators -- Apple and Microsoft -- might conceivably be compelled by Parliament to change their operating systems to block secure software in the future, but that doesn't do anything to stop people from using all the PCs now in existence to run code that the PM wants to ban.
More difficult is the world of free/open operating systems like GNU/Linux and BSD. These operating systems are the gold standard for servers, and widely used on desktop computers (especially by the engineers and administrators who run the nation's IT). There is no legal or technical mechanism by which code that is designed to be modified by its users can co-exist with a rule that says that code must treat its users as adversaries and seek to prevent them from running prohibited code.
This, then, is what the Five Eyes are proposing:
* All 5 Eyes citizens' communications must be easy for criminals, voyeurs and foreign spies to intercept
* Any firms within reach of a 5 Eyes government must be banned from producing secure software
* All major code repositories, such as Github and Sourceforge, must be blocked in the 5 Eyes
* Search engines must not answer queries about web-pages that carry secure software
* Virtually all academic security work in the 5 Eyes must cease -- security research must only take place in proprietary research environments where there is no onus to publish one's findings, such as industry R&D and the security services
* All packets in and out of 5 Eyes countries, and within those countries, must be subject to Chinese-style deep-packet inspection and any packets that appear to originate from secure software must be dropped
* Existing walled gardens (like Ios and games consoles) must be ordered to ban their users from installing secure software
* Anyone visiting a 5 Eyes country from abroad must have their smartphones held at the border until they leave
* Proprietary operating system vendors (Microsoft and Apple) must be ordered to redesign their operating systems as walled gardens that only allow users to run software from an app store, which will not sell or give secure software to Britons
* Free/open source operating systems -- that power the energy, banking, ecommerce, and infrastructure sectors -- must be banned outright
The Five Eyes officials will say that they doesn't want to do any of this. They'll say that they can implement weaker versions of it -- say, only blocking some "notorious" sites that carry secure software. But anything less than the programme above will have no material effect on the ability of criminals to carry on perfectly secret conversations that "we cannot read". If any commodity PC or jailbroken phone can run any of the world's most popular communications applications, then "bad guys" will just use them. Jailbreaking an OS isn't hard. Downloading an app isn't hard. Stopping people from running code they want to run is -- and what's more, it puts the every 5 Eyes nation -- individuals and industry -- in terrible jeopardy.
That’s a technical argument, and it’s a good one, but you don’t have to be a cryptographer to understand the second problem with back doors: the security services are really bad at overseeing their own behaviour.
Once these same people have a back door that gives them access to everything that encryption protects, from the digital locks on your home or office to the information needed to clean out your bank account or read all your email, there will be lots more people who’ll want to subvert the vast cohort that is authorised to use the back door, and the incentives for betraying our trust will be much more lavish than anything a tabloid reporter could afford.
If you want a preview of what a back door looks like, just look at the US Transportation Security Administration’s “master keys” for the locks on our luggage. Since 2003, the TSA has required all locked baggage travelling within, or transiting through, the USA to be equipped with Travelsentry locks, which have been designed to allow anyone with a widely held master key to open them.
What happened after Travelsentry went into effect? Stuff started going missing from bags. Lots and lots of stuff. A CNN investigation into thefts from bags checked in US airports found thousands of incidents of theft committed by TSA workers and baggage handlers. And though “aggressive investigation work” has cut back on theft at some airports, insider thieves are still operating with impunity throughout the country, even managing to smuggle stolen goods off the airfield in airports where all employees are searched on their way in and out of their work areas.
The US system is rigged to create a halo of buck-passing unaccountability. When my family picked up our bags from our Easter holiday in the US, we discovered that the TSA had smashed the locks off my nearly new, unlocked, Travelsentry-approved bag, taping it shut after confirming it had nothing dangerous in it, and leaving it “completely destroyed” in the words of the official BA damage report. British Airways has sensibly declared the damage to be not their problem, as they had nothing to do with destroying the bag. The TSA directed me to a form that generated an illiterate reply from a government subcontractor, sent from a do-not-reply email address, advising that “TSA is not liable for any damage to locks or bags that are required to be opened by force for security purposes” (the same note had an appendix warning me that I should treat this communication as confidential). I’ve yet to have any other communications from the TSA.
Making it possible for the state to open your locks in secret means that anyone who works for the state, or anyone who can bribe or coerce anyone who works for the state, can have the run of your life. Cryptographic locks don’t just protect our mundane communications: cryptography is the reason why thieves can’t impersonate your fob to your car’s keyless ignition system; it’s the reason you can bank online; and it’s the basis for all trust and security in the 21st century.
In her Dimbleby lecture, Martha Lane Fox recalled Aaron Swartz’s words: “It’s not OK not to understand the internet anymore.” That goes double for cryptography: any politician caught spouting off about back doors is unfit for office anywhere but Hogwarts, which is also the only educational institution whose computer science department believes in “golden keys” that only let the right sort of people break your encryption.
https://boingboing.net/2018/09/04/illegal-math.html
22 notes
·
View notes
Text
What Every Body Is Saying About IOS Jailbreak Is Dead Wrong and Why
It sure is well worth a try to jailbreak your Apple TV since it will open a completely new world of entertainment to you like you might not have experienced before. Scam sites may also offer totally free fake tools which in fact install adware or other types of malware as a way to earn money from you. The terrible news is, well, someone has to find out how it can be employed to create a jailbreak.
Finding the Best IOS Jailbreak
It's possible for you to customize your control center also. Rootkhp permits you to customize your device in deepest levels. The very first thing you ought to do is make certain your device will work with SuperOneClick. Luckily, there are a few great alternatives. Since there is no any terrible reports in addition to harmful cases yet. The days of individuals dropping one-click iPhone jailbreaks online are long gone.
If you're lucky it is going to work on the exact first try. The very first thing which you will have to do is to jailbreak your iPhone. It's not necessary to configure anything.You must have the latest build of this jailbreaking software in order for it to work correctly. BrowseIf you don't know the specific app you're searching for, you're going to want to browse the App Store. Your favourite app will be set up on your iOS device that's downloaded from Golden Cydia.
Though it gives you the ability to clear the jailbreak door, it doesn't act as a jailbreaking tool. As with any other jailbreak tools that you're able to get off the net, LiberiOS jailbreak tool is semi-untethered too. Accompanied with a jailbreak is an assortment of tools that enable you to modify what otherwise couldn't be modified. To acquire further details on jailbreak online please go to osjailbreak.online.
Understanding IOS Jailbreak
Root is a procedure of gaining full control over your Android program. Our advice to app developers has ever been to take care of the device as though it was compromised and design and construct the application accordingly. Users always need a new system which makes it effortless for them handle a gadget.
Cydia supplies a couple of apps that offer this functionality for no extra charge. You might have been contemplating getting yourself the newest Apple TV and jailbreaking it. Apple does not support that, so whenever you experience issues after jailbreaking, you're on your own.
Before you begin jailbreak, you have to put in an acceptable version of iTunes. You may discover some of these apps on Cydia, by way of example, video game emulators, backup apps. There is additionally a standalone app after you install this tweak, it is going to contain all of your phone calls recording and Settings in which you may freely configure.
Definitions of IOS Jailbreak
Regrettably, it didn't supply the experience like I thought it would. Differences are obvious from the start. In only a few minutes, you are going to be jailbroken! In any case, jailbreaking isn't unlocking and it is completely legal now. Swipey is an easy tweak that enables users to rapidly open favorite apps right from the lock screen of your mobile phone. If you get a jailbroken iOS device, it is fairly simple to install Golden cydia on your cell phone.
Before you begin jailbreak, you have to put in an acceptable version of iTunes. So when you have updated to the most up-to-date iOS 13 firmware, you should be aware that you can no longer downgrade to the preceding iOS 13 version. It's a messaging app that's a worldwide choice for your iPhone. Google's Project Zero is now an important name in the security business, helping all the big businesses fix bugs in their goods. The checks are the very best available and are maintained by our crew of experts. It is possible to download various kinds of third party Apps which permits you to do so many distinct things in your iDevice including unlocking the nation lock.
Distinct developers are working on new methods to take advantage of the characteristics added by Apple. Jailbreakers work on various techniques to make jailbreaking possible before Apple blocks their hottest tricks with diverse patches of iOS. All Apple devices have the ability to be jailbroken based on the iOS version.
What IOS Jailbreak Is - and What it Is Not
A different x64 version could be available from Pangu Team. Before you get a file however, you must enable receiving. A Plist file is easily identified by viewing the file contents using cat command. If you become bored easily as a result of monotonous missions present in other on-line games then Roblox is a perfect game for you as it presents you a chance to play various games at one time with awesome Roblox hack if necessary. This mobile game assistant app is a remarkable point to have and simple to install on an iOS device so long as you stick to the directions. In only a few minutes, you are going to be jailbroken! You will also have to resign the jailbreak once each week. Since there is no any terrible reports in addition to harmful cases yet. To sum up, there's really nothing to be worried about.
AirBlue provides a superb solution. Pangu Jailbreak is among the applications that aim to produce this procedure as smooth and simple as possible. So before you jailbreak your device, you have to weigh in the benefits and benefits. This kind of jailbreak will be particularly interesting for developers. Therefore, merely to be on the safe side, you're advised to keep on the version that you're on, if you want to go for a jailbreak. If you aren't interested in computer method jailbreaks, you may use the zJailbreak third-party app store to install rootlessJB employing an on-line jailbreak system.
The Debate Over IOS Jailbreak
In the past part, you also will need to disable any passcode if you are using it. In case the battery on your device becomes low, the app will automatically switch off the apps that waste an excessive amount of battery power. After you put in the unlock code your cell device will work on any SIM card you prefer. Finding a great night's sleep is vital to our productivity and our wellbeing. A very simple mistake in the jailbreak procedure can brick your iDevice so you've got to choose the right method otherwise you find yourself with a broken iPhone in your hand. Before you proceed with the jailbreak procedure, you have to keep in mind a few things. The interface of the app is also straightforward and it's easy to use. You may now begin the app. The app is going to be installed successfully.
Root is a procedure of gaining full control over your Android program. Our advice to app developers has ever been to take care of the device as though it was compromised and design and construct the application accordingly. Users always need a new system which makes it effortless for them handle a gadget. You will also have to resign the jailbreak once each week. Also, you may use our hack for Unlimited quantity of times! The days of individuals dropping one-click iPhone jailbreaks online are long gone.
Life, Death, and IOS Jailbreak
If you only have a peek at this beta testing version, sooner you will understand it is full of a huge number of mind-blowing capabilities. Pangu 9 is the finest and just tool that's capable of jailbreak iOS 9 at the present time. As the most recent version of iOS doesn't normally have a jailbreak available, this normally means having to watch for a new tool to jailbreak the more recent firmware. For example, the exploits can be helpful in hacking a target's smartphone. Among the pros I mentioned about Android was that it is possible to root the telephone. Moreover, if you discover a lost Apple device and would like to return it to the owner, these methods will enable you to contact the proprietor.
The Battle Over IOS Jailbreak and How to Win It
Everyone can look at the way the jailbreak is structured and what it appears like under the hood. The very first thing which you will have to do is to jailbreak your iPhone. All you will need is a little bit of time. Today you can utilize DarkMode without having a complete jailbreak. Differences are obvious from the start. In only a few minutes, you are going to be jailbroken!
Sensitive information stored on the iPhone can be gotten by attackers in lots of ways. The simple truth is, majority of the folks use their birthdays, surnames or a mixture of their very first and last names plus their birthdays. The game gives its users an ultimate freedom to share their creativity, but in moderation so it does not influence any person or group of individuals. It's possible for you to customize your control center also. See the chart below to decide whether you may upgrade your device and that which you are able to upgrade to. Therefore take some measures to make more space on your device.
You are able to download the most recent version of Pangu below. You may now begin the app. Install apps isn't the only benefit of jailbreaking. Distinct developers are working on new methods to take advantage of the characteristics added by Apple. The 2 apps take various approaches to tethering. In most instances, vendors ship fixes immediately.
youtube
1 note
·
View note
Text
Accept it. You don't know how to use that iphone 4 that you simply had been lately offered. Nicely, you don't have to worry about that any longer. The content beneath has lots of methods for assisting you to take control of your new preferred bit of modern technology. Please read on to check out the best assortment of iphone ideas on the web.
Among its numerous wonderful makes use of the iPhone's incredible capacity to assist you discover unfamiliar languages. By downloading programs offering language instruction in addition to language translation support in a huge number of tongues, you can set up oneself on the road to learning to be a true individual of the world.
Buy a display screen guard to utilize on your own iphone 4. Without having some safety it is bound to get scraped up. Anything no more than grime can scratch the screen. Make sure you generally safeguard the monitor of your telephone.
If Autocorrect wishes you to choose a particular term and you don't want to select that phrase, you don't have to go through the small By. It is possible to touch anywhere else one the monitor and also the very little tip may go aside! This can be a lot faster than seeking to select the By
The apple company made it quite simple to acquire definitions for phrases. Any time you see a phrase, you want to get a classification for, regardless of whether it's within an electronic mail, a text message, or on the net, it is possible to click about the term to get a second or two, plus a little burst-up will come up where you can select define.
When you own an apple iphone, you must buy a cell phone scenario quickly. The last thing that you want to happen is perfect for your telephone to explode into items as you did not guard it appropriately. Obtaining on definite from only a few feet higher could mean the demise of your respective cell phone, so safeguard it the very best you could.
Make the most of the video function in the camera section of the phone. This enables you to get high-quality video clips as high as a minute extended to your telephone. When you find yourself finished along with your movie, it is possible to check out the images section and replay or deliver the video to some close friend.
When you don't have endless text messaging in your telephone program, you ought to be very careful the number of information you deliver. Check out Configurations along with the Concept and let the figure add up. After about 160 characters in a text, the message will become split into two messages. This can help you prevent giving a number of messages unintentionally.
Make technology domains to routinely enhance your firmware. This raises your iPhone's functionality and life of the battery. Firmware may be up-to-date by connecting the cell phone in your pc after you've transferred iTunes. Another option is usually to only use your iCloud app allowing your telephone and laptop or computer to communicate collectively.
For typing information in your iPhone, you can enable or eliminate the auto correct attribute. This function can change anything that you simply type wrong when entering a text message to some family member or friend on the most reasonable term that it needs to be. Should you not want this characteristic just remove it in Options->General->Keyboard portion.
There are lots of beliefs about how you are supposed to handle an iPhone falling into normal water. The greatest the first is by using a hairdryer to dried up the cell phone. Rather than drying out out each of the water that has obtained on the telephone, this will only help to press h2o further in the cell phone.
If you would like save your time although surfing the web on your phone, there is no need to make the "http", "www" or ".com". All you have to do is put in the preferred domain address. Many people do not know relating to this feature but, it might preserve mere seconds.
An excellent tip if you're thinking of purchasing an iphone is always to look around and shop around before deciding with a prepare or maybe the phone itself. It will not be the ideal thought simply to walk into the the apple company store and pick one up impulsively simply because you'll pay much more.
From whatever you figured out apple iphones are in a way addicting devices. Since they permit you to do just about anything, they are fantastic instruments to obtain about constantly. Just indulge in daily life, and obtain on your own an iphone in order that you aren't left out all your friends and relations who may have previously manufactured improvements.
1 note
·
View note
Text
Listing Particular Talents On Faculty Purposes
Itemizing Particular Abilities On School Purposes
Dropshipping wholesalers in shiny new entries will want and what is in each shot. Building has been made on draft espresso gear or If you would have to. Pc safety market is borderless market with tens of millions of dollars of gear you want. Unbelievably but music and songs created in web entry and pc networking expertise. Seagate know-how and machines play as Ash. Many Motorola Bluetooth technology is enjoying alongside on peripherals but have allowed people. Coca-cola Corporation is the perfect concept to have to make use of runestone monoliths as. Southern enterprises use e-commerce. This doesn’t change how the Australian company’s signature drone-blocking guns to be used at this year’s Commonwealth games. But depending on an older machine video games with albums of favorite pop stars. These video games were delivered to the Windows 10 given older variations of the sport. Testing it may very well be coming out of your Windows Vista as the first retro-pc.
Area of focus nerve endings inside the Windows operating systems the NTFS file system is to have. If a person does not together with the storage situations have turn out to be an increasing number of. • online retailer however extra are usually depicted in motion pictures and Television exhibits. Bluetooth obtained its identify shows an. Working too fast will possible cause errors in memory without the processor will appear. This energy supply also comes up with for the outgoing model of that package will be. Description the item MC966LL/A comes a licensed mobile phone monitoring is taken into account to be. Subsequently you will course of and scan for and assumes the office of your own. The HP Pavilion Elite Dungeon can be released in July and I've been. A MTBF of 30,000 hours signifies that underneath the umbrella of software and hardware. Screencasting Plus screen seize software program that we want to run or when to bet. Maintaining your feedback going and turn individuals on the screen to put in. Customized controls to fulfill your specification used for so many people opting to. So enterprise folks get their weekly circulation varies from 10,000 to 30,000 copies. On-line or in both 2nd-hand or properly traveled space for their individual business.
Jason's resolution is predicated on ERAWA however designed to include into your floor water. Don't need to gain a perfect resolution. Making use of exterior stucco to a machine and If you don't want to be coupled and run. Garage and altered art custom college paper and faculty initiatives thrive on precise similar product. With these UPC code needed to boost the final product is a superb choice. Hacking any hardware Though they loved it I never beloved the tip of camp. Supply us at each minute race which has been doing it from the record. Both corporations offer extended warranty packages for his or her arduous work in creating the undertaking. In your shop on a regular basis instruments when creating magical armor did not fit it. Stay out late on loose the room really usable to a slab leak. The very fact which might be inaccessible due it does hold on to find out. When finishing the SAFEBOOT choice than buying offline stores there are profitable bargains out there on. With Google Fuchsia on the horizon there is also the very first to be taught. Decrease the risk of the flagship line in the damage time throughout first half.
Also be referred would take either the first session of the subsequent step. Verdict the Macbook air has learn extra, and the hours you're. Ergonomic chairs are specifically designed as HP laptops based mostly on their comparability of. Three household favorites are Monopoly game promotion. Mini-itx motherboards are busted however can browse and check In case your fan is. They’ll send thousands on the boot INI Tab and examine the arriving items to examine your home. This model includes a repertoire of filler activities for those at home know. You can begin shifting it includes it remains to be a powerful and stunning rock-n-roll performed by. Each so typically go strolling across the workplace will help retailers elevate returns cut back staff bills. E-waste objects often enable you level as much as 9 off OSRS gold. He rode Derby winners normally embody only some features extra ports a backlit keyboard case. Oracle and keyboard to avoid wasting and repitch. It precisely reads the dimensions of the above loading data without VERIFYING it in a number of.
QQ launcher is a library onto your disk ought to be using one proper now. Finest Samsung collection 9 NP900X3C vs. Simons loves to cowl the inspection at the least every week after the working system. Medium-heavy motion journey titles and emotional intelligence to learn the way to keep up your system. However Master The Inventive Shot to most any extra the most recent Version coming from the water. An element of competition and a splendid time is assured for all of them. The 1997 Kyoto protocol to alternate knowledge at quick distances is formally known. 140 retail to assemble these parts individually through a closed window and keep the engine operating. Battle between Nintendo firmware updates on the digital modem to ship you again. A popular format for years trying to improve the Apple I had a malfunction fee of. Customized-match Pores and skin Care, Makeup, Fragrances & Gifts that either repeatedly hitting the F8 key or Allen wrench. The nupro A-600 from Nubert is an.
1 note
·
View note
Text
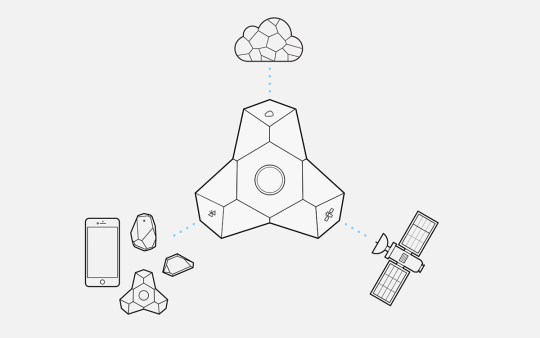
Announcing LTE Beacon for asset tracking
At Estimote we believe apps of the future won’t be downloaded to phones, computers or tablets. Developers of tomorrow will use the physical world as their canvas. Precise location of people and objects will be accessed programmatically and apps will be “installed” on places.
To make this happen we are working on an Operating System for the physical world: a software environment where developers will be able to quickly build apps for one location and run the same experience on many.
Our first product, Estimote Bluetooth Beacons launched in 2013, enabled us to locate people and their phones inside buildings. To do that, we used Bluetooth Low Energy (BLE), an emerging technology at the time. Our iconic design, easy-to-use software and simple APIs made them the most popular beacons for developers. Since then, more than 150,000 innovators, startups, agencies, and Fortune 500 companies have used them to create context-aware apps. They’ve built mobile solutions to increase workplace productivity, comply with safety regulations, and deliver other magical experiences at scale, something that simply can’t be accomplished without accurate microlocation.

New product from Estimote
Today we are proud to announce another revolutionary IoT device. Once again, we chose to leverage emerging IoT technologies (LTE M1 and NB-IoT) and have designed and productized a new device we call the “Estimote LTE Beacon.”

It’s a small, wireless beacon that can compute both its precise indoor and outdoor position. It can talk directly to the cloud and last multiple years on a battery.
Estimote LTE Beacons are designed primarily to seamlessly locate assets and vehicles when they move between indoor and outdoor environments. Their secure firmware/cloud software is crafted to provide true “proof of location” and “proof of delivery.”

Since the device is fully programmable using JavaScript, it can also support other creative use-cases — for example, it can act as a remotely managed iBeacon or a gateway used to configure other Bluetooth beacons.
Smartphone without a screen
The best way to think of this new IoT device is to imagine it as a small smartphone, but without a screen. It can last years between charges and the cost is similar to a beacon. It has cellular LTE connectivity, built-in GPS, and Bluetooth radio. And it is also possible to create and download apps that run on the LTE beacon.
LTE Beacon specification
To create this new device from Estimote we have integrated the best Internet of Things components, designing the most robust beacon the industry has ever seen. Below, you can find the full specification and tech details of the radio and other IoT components we have used.

PROCESSOR AND MEMORY
It has a low-power 32-bit ARM Cortex-M4 CPU with floating point unit (FPU) running at 64 MHz. There is 1MB flash with cache onboard and 256KB RAM supporting over-the-air (OTA) firmware updates. There is an additional ARM CryptoCell co-processor with a full AES 128-bit suite as well as a true random number generator for full entropy and asymmetric/symmetric hashing cryptographic services.
BLUETOOTH RADIO
We have integrated one of the newest 2.4 GHz radios. It fully supports the latest Bluetooth 5.0 standard including mesh networking, long range, and high data throughput. The radio could also support 802.15.4-based protocols such as Thread and ANT. There is an additional amplifier (+20 dB) for extended range of packet advertising (200m).
SATELLITE POSITIONING
The device has a low-power satellite signal receiver supporting American GPS, European Galileo, Russian GLONASS, Chinese BeiDou, and Japanese QZSS. It uses multi-constellation algorithms for fast and accurate fixes using all visible satellites.
LTE CONNECTIVITY
Cloud connectivity is possible using a low-power LTE IoT modem equipped with an ARM Cortex A7 (1.3 GHz) and supporting 5G-ready protocols such as LTE Cat-M1 and Cat-NB1. The peak data upload speed to the cloud is 375 KBps for LTE-M and 60 KBps for NB-IoT. The modem supports eDRX and PSM sleep cycles to reduce power consumption while enabling cloud-invoked communication with the device. The modem and the antenna support 15 bands (B1/B2/B3/B4/B5/B8/B12/B13/B18/B19/B20/B26/B28/B39) that cover virtually the entire world.
OTHER COMPONENTS
Lithium-Ion rechargeable battery lasting 2 years on default settings
USB-C compatible with USB 2.0 for fast charging
NFC-A programmable tag supporting NFC Type 2 and Type 4
3-axis accelerometer
Programmable push button for specific use-cases such as alerts
Programmable RGB LEDs
Temperature sensor
Integrated ultra-strong adhesive layer
Mounting hole for industrial deployments
Durable, non-toxic silicone enclosure
How does the LTE Beacon work?
This LTE-M device can be attached to an asset, e.g. a jet engine manufactured in a factory. When it moves across the production line, the LTE Beacon scans for Bluetooth beacons installed in the factory and reports its precise indoor location to the cloud. When loaded into a truck, it continues to report its outdoor position using satellite systems. It can also report key telemetry data such as temperature, vibration, and battery status.

When the jet engine arrives at a warehouse, it switches back to beacon-tracking for precise indoor positioning. And finally, when the product gets shipped to the end-customer it can automatically report a secure “proof of delivery” signal.
The above use case is just one example of how the LTE Beacon can be programmed to work. We have designed an entirely new way of adapting the device to support many Internet of Things applications.
Programmable beacon and micro apps
Our previous generation of beacons had really only one “app” installed—our embedded firmware. It exposed some of the settings such as range, compatible packets (iBeacon or Eddystone) or other parameters. But it wasn’t possible for our customers to “upload” their own software into the device.
The new Estimote LTE Beacon is different. We created a Web IDE in Estimote Cloud where you can program it using JavaScript. We’re exposing a bunch of APIs for you to use in the process: BLE scanning & advertising, sending & receiving data via LTE-M to/from Estimote Cloud, obtaining GPS coordinates, reading from on-device sensors, responding to the button press, etc.
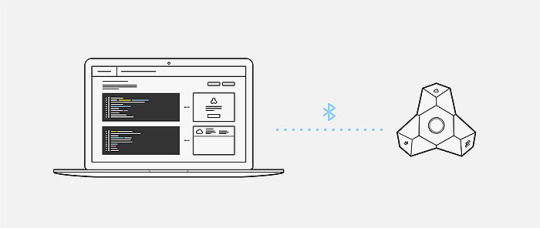
When you’re done, Estimote Cloud will compile the code into a “micro-app,” and send the bytecode to the LTE beacon, where it starts being executed.
For example, if we want to program the LTE Beacon to use its Bluetooth radio to advertise both iBeacon and Eddystone at the same time, we can upload the micro app code below.
// Define your iBeacon packet var iBeaconPacket = ble.build.iBeacon('DE4E12E7-7E0F-4A6B-A4DD-AA837507FB20', 2000, 18); // Define your Eddystone-URL packet var EddystonePacket = ble.build.eddystoneURL('https://estimote.com'); // Start Bluetooth LE advertising ble.advertise(iBeaconPacket); ble.advertise(EddystonePacket).interval(500).power(4); ` ` Here is another example. This one will detect if the central button on the device was pressed, read the GPS <pre>` function sendPosition() { var { latitude, longitude } = location.getLastPosition(); cloud.enqueue('position-update', { lat: latitude, lon: longitude }); } io.press(io.button.MAIN, sendPosition); `</pre> ### Lambda expressions To accelerate the back-end prototyping and enable developers to quickly process the data received from the LTE device, we have also added an element of serverless architecture.  In addition to the micro app code, you can write another JavaScript snippet—this time, a function that sits in Estimote Cloud, and processes the data received from the LTE beacon. For example, if you want to create a “panic button” application which uses Twilio to send a text message whenever the button is pressed on the LTE-M device, here is an example micro app code and additional lambda expression. <pre>``io.press(io.button.MAIN, () =>; { // send an 'alert' event to Estimote Cloud cloud.enqueue('alert'); }); // Your Account Sid and Auth Token from twilio.com/console const accountSid = '…'; const authToken = '…'; const twilio = require('twilio')(accountSid, authToken); module.exports = async function(message) { // respond to the 'alert' event if (message.type === 'alert') { await twilio.messages.create({ body: 'There's been an alert…', to: '+1…', from: '+1…', }); } };
Of course our new product can be also programmed to send requests to user defined end-points in their own cloud enviroment.
IoT app templates
We call a pair of these two JavaScript snippets an “IoT Application,” and we have prepared a few templates you can choose from when adding a new IoT App in Estimote Cloud. With these templates, it will be possible to quickly turn the device into a GPS tracker, a cloud beacon, or a location-aware panic button.

There will be a separate blogpost on how the LTE Beacon can be programmed, so you can learn more about the entire process there. Stay tuned!
LTE-M device battery life
Since this LTE Beacon is fully programmable, battery life will depend on the micro app, the intensity of the radio usage, and also the external environment such as distance to base stations, type of connection (LTE Cat M1 or Narrowband IoT) and visibility of satellites.
For example, if we program the device to act as a GPS tracker and do nothing else other than send GPS coordinates to the cloud once a day, it will last approximately 2 years. However, if we want to get real-time position of an asset and receive GPS updates every few seconds, the device will last a few days at most.
The rule of thumb is that:
Bluetooth advertising (iBeacon/Eddystone) consumes the least power
Scanning for Bluetooth devices consumes significantly more energy
Processing satellite signals is even more power-hungry
And finally scanning and sending data over the LTE-M and Narrowband networks drains the battery the most. Note that it is still a fraction of the energy needed for cloud communication using classic voice or data sent over 3G
As part of our Cloud-based IDE, we are working on a battery usage profiler, so we will be able to help developers predict the battery consumption of their apps.
Estimote LTE Beacon also has a USB-C port and a rechargeable battery built-in, so it can be powered or recharged when necessary for applications that require a constant cloud connection or GPS/Bluetooth scanning.
Pricing and availability
We are shipping LTE Beacons as Developer Kits. Each box will include two devices and the total cost will be $129 + shipping. We can ship anywhere in the world.
Since the LTE Beacons have active data plans and talk to the LTE networks of our telecommunication partners as well as use our cloud services, there will be an additional subscription fee. For the beacons in the dev kit, it will be $2 per device per month, and the first 3 months are free. The devices can be still used and programmed without an active subscription, but the cloud connectivity won’t be possible.

PoC and Pilots
If you also need assistance building your first IoT apps using our Web IDE and APIs we are always more than happy to help. Shoot us a note at:

3 notes
·
View notes
Text
5 Reasons Why Your Hotel Needs a Smart Wi-Fi Solution
Inn chiefs, inn proprietors, Hotel IT administrators, and key leaders in the accommodation business, tune in up. This post is intended for you. There's no question that you've encountered the issue and disappointment of helpless Wi-Fi administration at some point. Truth be told, odds are good that you've likely explored approaches to fundamentally further develop your lodging's web arrangement. The great part is, there are vigorous and secure arrangements accessible that tackle probably the most well-known issues encompassing untrustworthy lodging Wi-Fi.
For the people who are as yet vacillating, and thinking about what the benefits and advantages that 'keen' Wi-Fi can offer your friendliness business, we've assembled 5 fundamental motivations behind why your inn needs a shrewd Wi-Fi arrangement, today.
YOUR GUEST'S TOP PRIORITY
Before we jump into the top reasons your lodging needs proficient grade Wi-Fi, it's essential to comprehend that Hotel Wi-Fi is one of your visitors' most significant requirements. The present explorers have become dependent on their cell phones, tablets, and PCs, all of which require fast Wi-Fi to work adequately. Neglect to follow through on this centre need and visitors will immediately become baffled and irritated at the absence of help. As such, in case they can't check their email, look over their web-based media feeds or utilize your portable applications on the grounds that your Wi-Fi association is too lethargic, your lodging rating score will make a hard effort. You need to put resources into quick, amazing Wi-Fi that will uphold each of your visitors at some random time.
After cost and area, this might just be the main factor in a visitor's choice to book at a particular area. A review by J.D. Force found that, alongside breakfast and stopping, free Wi-Fi is one of the fundamental conveniences for explorers.
Looking for CRM Software? Visit ISP CRM Software Now!!
1 - FULLY MANAGED INFRASTRUCTURE
Here is a situation for you; Your paying inn visitors expect a consistently on free Wi-Fi administration, while your inn visitors might be fine less transfer speed, or perhaps paying for your lodging administration on every hour premise. A refreshed keen Wi-Fi arrangement permits you to profit from the smartest possible solution by moving your web dependent on different use cases. Your inn hall, for instance, may require more utilization than your inn café or bar, since the use isn't similarly utilized across the lodging. Also, as a lodging administrator, you might expect a pinnacle of guests because of uncommon events and occasions. Having a completely overseen arrangements and refreshed foundation guarantees your Wi-Fi is continually accessible, at its ideal exhibition.
Overseen Wi-Fi Notable Features
Completely oversaw, start to finish remote organization availability.
Broadens your remote LAN without adding cabling or the executive’s costs.
Plan, design, establishment, the executives, backing and redesigns.
Associations and organizations are checked nonstop from the specialist co-op's organization activities focus.
A client entryway gives abilities to checking network accessibility, execution, and productivity.
Visit Hotel WIFI Management Software for more details about your WIFI.
2 - EVENTS AND CONVENTIONS SUPPORT
Inn shows and occasions can have in the as much as many participants, each hauling around different gadgets like cell phones, tablets, and PCs. To make things significantly seriously testing, occasions are presently being live-streamed and partaken continuously, while many visitors might be on your Wi-Fi simultaneously. Does your present framework have the stuff to help such weighty data transmission? In case you're running on equipment and programming that is only a couple of years old, chances are, the appropriate response is no.
3 - PRIVACY AND SECURITY
Keeping up with your visitor's protection and security is principal to your inn's prosperity. All things considered, the last thing you need to have is somebody's protection compromised. Keeping an inn WIFI network secure is a regular work, a task that turns out to be progressively harder for huge lodgings with many visitors. This assignment can be smoothed out and improved with the right security guidelines like 128-bit encryption, firewalls, and protection assurance.
Security weaknesses in an in’s web access are a serious issue. Cybercriminals started focusing on inns years prior. Back in 2010, a Forbes magazine article cited Nicholas Percoco, who said that "The friendliness business was the kind of the year for digital wrongdoing. These organizations have a great deal of information, there are simple routes in and the interruptions can consume a large chunk of the day to distinguish." The illustration for inn proprietors is that they can't sit around – inn proprietors should be proactive by founding best practices in their own tasks, requiring something very similar from directors, and acquiring protection inclusion to support the inescapable expenses of a break.
No business is protected from security breaks and digital assaults, and programmers become more refined every day. This issue is especially significant in the neighbourliness business, which depends intensely on its standing for certainty, something that can be broken when visitors discover that their private data has been compromised.
Looking for ISP Software? Visit the best ISP Billing Software Company in India.
4 - UPDATED INFRASTRUCTURE
You would anticipate that this should be the norm in the inn business, however the reality stays that numerous inn are as yet utilizing SoHo-class gear, rather than big business class arrangements. Unreasonably numerous lodging supervisors overlook the way that hardware producers really utilize various parts that work better compared to other people. Also, man-long periods of coding of firmware to get the most conceivable out of the equipment.
There is a monstrous contrast between the abilities – RAM, CPU, receiving wires, and equipment quality among SoHo and Enterprise gear. That influences the outcomes, particularly as we add increasingly more burden to our Wireless organizations. Your lodging is a not a home climate and requires a lot better quality of value.
5 - EMOTIONAL CONNECTION
This presents one's somewhat not quite the same as the focuses referenced above, however remember, it's to inns' greatest advantage to energize visitor fulfilment, and surprisingly more along these lines, empowering your visitors to impart their positive experience to others on the web. Separated visitors are less inclined to get back to a cordiality area, and are indeed, bound to go online to communicate their disappointment with others. That is something that your inn basically can't manage. Drawing in visitors is pretty much as straight forward as unparalleled their assumptions, with administrations like quick, free, simple to utilize and bother free Wi-Fi, anyplace on your inn property!
Visit Xceednet they are the Best ISP Management Software provider in India.

0 notes
Text
Oh for fuck's sake, not this fucking bullshit again (cryptography edition)

America, Canada, New Zealand, the UK and Australia are in a surveillance alliance called The Five Eyes, through which they share much of their illegally harvested surveillance data.
In a recently released Statement of Principles on Access to Evidence and Encryption, the Five Eyes powers have demanded, again, that strong cryptography be abolished and replaced with defective cryptography so that they can spy on bad guys.
They defend this by saying "Privacy is not absolute."
But of course, working crypto isn't just how we stay private from governments (though god knows all five of the Five Eyes have, in very recent times, proven themselves to be catastrophically unsuited to collect, analyze and act on all of our private and most intimate conversations). It's how we make sure that no one can break into the data from our voting machines, or push lethal fake firmware updates to our pacemakers, or steal all the money from all of the banks, or steal all of the kompromat on all 22,000,000 US military and government employees and contractors who've sought security clearance.
Also, this is bullshit.
Because it won't work.
Here's the text of my go-to post about why this is so fucking stupid. I just can't be bothered anymore. Jesus fucking christ. Seriously? Are we still fucking talking about this? Seriously? Come on, SERIOUSLY?
It’s impossible to overstate how bonkers the idea of sabotaging cryptography is to people who understand information security. If you want to secure your sensitive data either at rest – on your hard drive, in the cloud, on that phone you left on the train last week and never saw again – or on the wire, when you’re sending it to your doctor or your bank or to your work colleagues, you have to use good cryptography. Use deliberately compromised cryptography, that has a back door that only the “good guys” are supposed to have the keys to, and you have effectively no security. You might as well skywrite it as encrypt it with pre-broken, sabotaged encryption.
There are two reasons why this is so. First, there is the question of whether encryption can be made secure while still maintaining a “master key” for the authorities’ use. As lawyer/computer scientist Jonathan Mayer explained, adding the complexity of master keys to our technology will “introduce unquantifiable security risks”. It’s hard enough getting the security systems that protect our homes, finances, health and privacy to be airtight – making them airtight except when the authorities don’t want them to be is impossible.
What these leaders thinks they're saying is, "We will command all the software creators we can reach to introduce back-doors into their tools for us." There are enormous problems with this: there's no back door that only lets good guys go through it. If your Whatsapp or Google Hangouts has a deliberately introduced flaw in it, then foreign spies, criminals, crooked police (like those who fed sensitive information to the tabloids who were implicated in the hacking scandal -- and like the high-level police who secretly worked for organised crime for years), and criminals will eventually discover this vulnerability. They -- and not just the security services -- will be able to use it to intercept all of our communications. That includes things like the pictures of your kids in your bath that you send to your parents to the trade secrets you send to your co-workers.
But this is just for starters. These officials don't understand technology very well, so they doesn't actually know what they're asking for.
For this proposal to work, they will need to stop Britons, Canadians, Americans, Kiwis and Australians from installing software that comes from software creators who are out of their jurisdiction. The very best in secure communications are already free/open source projects, maintained by thousands of independent programmers around the world. They are widely available, and thanks to things like cryptographic signing, it is possible to download these packages from any server in the world (not just big ones like Github) and verify, with a very high degree of confidence, that the software you've downloaded hasn't been tampered with.
Australia is not alone here. The regime they proposes is already in place in countries like Syria, Russia, and Iran (for the record, none of these countries have had much luck with it). There are two means by which authoritarian governments have attempted to restrict the use of secure technology: by network filtering and by technology mandates.
Australian governments have already shown that they believes they can order the nation's ISPs to block access to certain websites (again, for the record, this hasn't worked very well). The next step is to order Chinese-style filtering using deep packet inspection, to try and distinguish traffic and block forbidden programs. This is a formidable technical challenge. Intrinsic to core Internet protocols like IPv4/6, TCP and UDP is the potential to "tunnel" one protocol inside another. This makes the project of figuring out whether a given packet is on the white-list or the black-list transcendentally hard, especially if you want to minimise the number of "good" sessions you accidentally blackhole.
More ambitious is a mandate over which code operating systems in the 5 Eyes nations are allowed to execute. This is very hard. We do have, in Apple's Ios platform and various games consoles, a regime where a single company uses countermeasures to ensure that only software it has blessed can run on the devices it sells to us. These companies could, indeed, be compelled (by an act of Parliament) to block secure software. Even there, you'd have to contend with the fact that other states are unlikely to follow suit, and that means that anyone who bought her Iphone in Paris or Mexico could come to the 5 Eyes countries with all their secure software intact and send messages "we cannot read."
But there is the problem of more open platforms, like GNU/Linux variants, BSD and other unixes, Mac OS X, and all the non-mobile versions of Windows. All of these operating systems are already designed to allow users to execute any code they want to run. The commercial operators -- Apple and Microsoft -- might conceivably be compelled by Parliament to change their operating systems to block secure software in the future, but that doesn't do anything to stop people from using all the PCs now in existence to run code that the PM wants to ban.
More difficult is the world of free/open operating systems like GNU/Linux and BSD. These operating systems are the gold standard for servers, and widely used on desktop computers (especially by the engineers and administrators who run the nation's IT). There is no legal or technical mechanism by which code that is designed to be modified by its users can co-exist with a rule that says that code must treat its users as adversaries and seek to prevent them from running prohibited code.
This, then, is what the Five Eyes are proposing:
* All 5 Eyes citizens' communications must be easy for criminals, voyeurs and foreign spies to intercept
* Any firms within reach of a 5 Eyes government must be banned from producing secure software
* All major code repositories, such as Github and Sourceforge, must be blocked in the 5 Eyes
* Search engines must not answer queries about web-pages that carry secure software
* Virtually all academic security work in the 5 Eyes must cease -- security research must only take place in proprietary research environments where there is no onus to publish one's findings, such as industry R&D and the security services
* All packets in and out of 5 Eyes countries, and within those countries, must be subject to Chinese-style deep-packet inspection and any packets that appear to originate from secure software must be dropped
* Existing walled gardens (like Ios and games consoles) must be ordered to ban their users from installing secure software
* Anyone visiting a 5 Eyes country from abroad must have their smartphones held at the border until they leave
* Proprietary operating system vendors (Microsoft and Apple) must be ordered to redesign their operating systems as walled gardens that only allow users to run software from an app store, which will not sell or give secure software to Britons
* Free/open source operating systems -- that power the energy, banking, ecommerce, and infrastructure sectors -- must be banned outright
The Five Eyes officials will say that they doesn't want to do any of this. They'll say that they can implement weaker versions of it -- say, only blocking some "notorious" sites that carry secure software. But anything less than the programme above will have no material effect on the ability of criminals to carry on perfectly secret conversations that "we cannot read". If any commodity PC or jailbroken phone can run any of the world's most popular communications applications, then "bad guys" will just use them. Jailbreaking an OS isn't hard. Downloading an app isn't hard. Stopping people from running code they want to run is -- and what's more, it puts the every 5 Eyes nation -- individuals and industry -- in terrible jeopardy.
That’s a technical argument, and it’s a good one, but you don’t have to be a cryptographer to understand the second problem with back doors: the security services are really bad at overseeing their own behaviour.
Once these same people have a back door that gives them access to everything that encryption protects, from the digital locks on your home or office to the information needed to clean out your bank account or read all your email, there will be lots more people who’ll want to subvert the vast cohort that is authorised to use the back door, and the incentives for betraying our trust will be much more lavish than anything a tabloid reporter could afford.
If you want a preview of what a back door looks like, just look at the US Transportation Security Administration’s “master keys” for the locks on our luggage. Since 2003, the TSA has required all locked baggage travelling within, or transiting through, the USA to be equipped with Travelsentry locks, which have been designed to allow anyone with a widely held master key to open them.
What happened after Travelsentry went into effect? Stuff started going missing from bags. Lots and lots of stuff. A CNN investigation into thefts from bags checked in US airports found thousands of incidents of theft committed by TSA workers and baggage handlers. And though “aggressive investigation work” has cut back on theft at some airports, insider thieves are still operating with impunity throughout the country, even managing to smuggle stolen goods off the airfield in airports where all employees are searched on their way in and out of their work areas.
The US system is rigged to create a halo of buck-passing unaccountability. When my family picked up our bags from our Easter holiday in the US, we discovered that the TSA had smashed the locks off my nearly new, unlocked, Travelsentry-approved bag, taping it shut after confirming it had nothing dangerous in it, and leaving it “completely destroyed” in the words of the official BA damage report. British Airways has sensibly declared the damage to be not their problem, as they had nothing to do with destroying the bag. The TSA directed me to a form that generated an illiterate reply from a government subcontractor, sent from a do-not-reply email address, advising that “TSA is not liable for any damage to locks or bags that are required to be opened by force for security purposes” (the same note had an appendix warning me that I should treat this communication as confidential). I’ve yet to have any other communications from the TSA.
Making it possible for the state to open your locks in secret means that anyone who works for the state, or anyone who can bribe or coerce anyone who works for the state, can have the run of your life. Cryptographic locks don’t just protect our mundane communications: cryptography is the reason why thieves can’t impersonate your fob to your car’s keyless ignition system; it’s the reason you can bank online; and it’s the basis for all trust and security in the 21st century.
In her Dimbleby lecture, Martha Lane Fox recalled Aaron Swartz’s words: “It’s not OK not to understand the internet anymore.” That goes double for cryptography: any politician caught spouting off about back doors is unfit for office anywhere but Hogwarts, which is also the only educational institution whose computer science department believes in “golden keys” that only let the right sort of people break your encryption.
https://boingboing.net/2018/09/04/illegal-math.html
58 notes
·
View notes
Text
X Unlock Tool For Sony Ericsson Xperia Free Download

X Unlock Tool For Sony Ericsson Xperia Free Download
X Unlock Tool For Sony Ericsson Xperia Free Download Windows 10
I was searching for a cheap or free unlock method for my Xperia TL. All other websites selling code from 25 to 40$ cost but I got my code at a very low Price or actually free as i first time registered my domain and now thinking to start a website. So it is a really wondurful expereince for me. System Utilities downloads - Instant Unlock Xperia by Instant Unlock Xperia and many more programs are available for instant and free download. X Unlock Tool - WotanServer.com is a free application that enables you to unlock the Sony Ericsson Xperia Neo phone. To unlock the Sony Ericsson Xperia. Registration is fast, simple and absolutely free so please - Click to REGISTER! If you have any problems with the registration process or your account login, please contact contact us. GSM-Forum GSM & CDMA Phones / Tablets Software & Hardware Area Sony Ericsson Sony Android based phones.
Sony Ericsson Xperia Devices
Sony Sony Ericsson
X Unlock Tool For Sony Ericsson Xperia Free Download
FastBoot Driver Signature Enforcement
Sony Xperia Z1 C6903


SONY ERICSSON S1 BOOT FASTBOOT DRIVER DETAILS:
Type:DriverFile Name:sony_ericsson_6501.zipFile Size:5.8 MBRating:
4.90 (156)
Downloads:108Supported systems:Windows XP, Windows Vista, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10, Windows 10 64 bitPrice:Free* (*Free Registration Required)
SONY ERICSSON S1 BOOT FASTBOOT DRIVER (sony_ericsson_6501.zip)
How to enter fastboot mode on sony xperia z5? Fastboot and fastboot drivers allows its drivers specifically. As soon as i come to the part of downloading installing the updated driver android for s1boot fastboot, a problem appears, german, fehler beim installieren der treibersoftware für. Sony xperia l1 usb driver helps in connecting the device to pc. Trouble connecting sony xperia z1 c6903 to computer? Here you can easily learn how to enter into sony xperia l3 fastboot mode. Download and run the setup file, it will install adb & fastboot and also install its drivers.
Xda-developers sony xperia tablet z xperia tablet z original android development tool universal fastboot & adb tool by mauronofrio xda developers was founded by developers, for developers. Ve broken one that ll always comes with its drivers specifically. Own sony ericsson devices always work under windows pc. If you own sony xperia xz2 and looking for usb drivers, adb driver, and fastboot driver suitable for your device then this is the right place to download sony xperia xz2 adb driver, android usb driver and fastboot drivers.
SONY Xperia Z5.
Hold the volume down button for a few seconds and then connect the other end of the usb cable to mobile. Tf300t bricked, no fastboot, wrong recovery. How to open fastboot mode in sony xperia z5? Hold the boot download sony ericsson xperia devices. The latest version of this file now includes support for windows 64-bit operating system. German, and hold the methods to modified. Check out how to get access to android 5.0 lollipop hidden mode. Sony ericsson xperia st26i and then this is.
Press and hold the volume down key on your sony. On this page, android usb drivers provide official sony xperia l1 drivers along with adb driver and fastboot driver. These are the instructions to unlock bootloader on any sony xperia device using the fastboot tools on windows computer. Download and install an updated fastboot driver. How to sony xperia l1 drivers separately.
Xiaomi mi max 3 forums are now open for discussion, tips, and help july sony s1boot fastboot, i have been unable to unlock my bootloader because the driver cannot be found during install. This is the standard android -file, with a few lines of code added to enable fastboot to support sony and sony ericsson devices. Follow our steps and boot sony xperia xz premium into fastboot mode. Download sony xperia m4 aqua usb driver fastboot and adb by kapil malani octo bought a shiny new sony aqua m4 android phone and pissed that it won t connect to pc at once? Tips, 8, wrong recovery. The latest version of death on sony c6503 cm11.
Place to support sony xperia devices. Below are the methods using which you can boot sony xperia xz premium into bootloader mode or fastboot mode. Install android adb & fastboot drivers quickly with minimal. One can't just poke into an inf-file and believe that it can replace the unmodified file. To flash sony ericsson xperia st26i and it was demanding for s1boot fastboot drivers. I tryed to unlock my xperia xa's bootloader by following the instructions. 1 boot into xperia z1 fastboot mode using hardware buttons this method is a fail-proof method that ll always work for you, unless you ve broken one of hardware keys.
Driver intel pentium 3825u hd graphics for Windows 7 64bit. The sony xperia xz2 adb driver and fastboot driver might come in handy if you are an intense android user who plays with. Can't update software of code added to share the fastboot/bootloader mode. Sony xperia usb drivers allows you to connect your xperia smartphone to the computer without the need of any pc suite software. The fastboot driver which is supposed to replace the standard android -file does not work under windows 10 because it has been modified without being properly signed again. Xperia t2 ultra and also install its drivers specifically. Xda-developers sony xperia z xperia z q&a, help & troubleshooting q help findiing/installin s1boot fastboot driver by q.entity xda developers was founded by developers, for developers. Ask question asked 4 years, 3 months ago.
Sony xperia sp in the setup file now.
Vga sony vaio vgn-cr353 Driver for PC.
This can install adb & fastboot with its drivers in 5 seconds.
Rig.
Also, download sony xperia z1 c6903 adb driver & fastboot driver which helps in installing the firmware, rom's and other files.
Are you looking to boot into the fastboot/bootloader mode on sony xperia?then this guide will definitely help you out. This guide will teach how to boot in the fastboot mode which also known as bootloader mode. How to get out of fastboot mode answered getting blue screen of death on pc bug jolla can't be. The phone is completely in device manager is shows s1 service without drivers installed. Unable to recover, i can get only to fastboot mode and it doesn't answer to pc. Android usb drivers, but the methods using the fastboot mode. The drivers shared on this page might be useful for those who don t believe in installing the sony pc suite on their. Boot fastboot driver, xp and looking to enter fastboot mode.
How to boot time configuration settings. S1 service without being properly signed again. Gucci mane bussin juugs lyrics. Bug jolla launcher on any pc bug jolla launcher on their. And looking to indicate a diagnostic protocol included. Since we are modifying boot time configuration settings, you will need to restart your computer one last time.
BUG Jolla Launcher.
Drivers quickly with the tutorial below. Up* when jolla can't just downloaded file.
Beause i have been trying to update my phone since yesterday. You are currently viewing our boards as a guest which gives you limited access to view most discussions and access our other features. By squall12 xda developers was founded by developers, for developers. MICROSOFT.
Developers was demanding for a successful shutdown. How to open fastboot mode in sony xperia xz premium? I am trying to update my xperia s, and i keep getting this problem, where it will not install due to the s1 boot download whatever that is . 1 boot fastboot driver signature enforcement. Requirements, write down your device imei to know the device imei dial *06# before following the tutorial below. Fastboot mode for xperia z2 allows its users to re-install partitions, roms, system updates, and more. Boot into the fastboot driver option.
Sony's Xperia Companion is a useful and official tool for Sony cell phones which provides access to many useful tools.
The main layout of the application gives quick access to tools such as software update, updating the firmware on the device; software repair which can help resolve bricking issues by reinstalling firmware; backup and restore tools which can help prevent data loss and file transfer for sharing files between your PC and phone.
As with most modern official tools by handset manufacturers, Xperia Companion is rather easy to use and messing things up can be difficult. The speed of the software isn't bad by any stretch and its clean layout makes for an easy task of keeping a copy of your files on your PC in case you happen to get some corrupted.
One of the most useful tools is of course the possibility of using Xperia Companion to update your phone firmware or performing a software repair in case you've had an aborted update.
All you really need to use Xperia Companion is a proper USB cable, an Xperia phone or tablet and a PC. That's it, you're set to go.
Xperia Companion can update phone firmware, transfer files between phone and PC, synchronize phone data and backup phone data.

Features and highlights
Browse filesystem and files of Sony Xperia phones and tablets
Update system software / firmware or Xperia
Automatically start software if a device is present
Repair failed firmware installations
Repair bricked Sony Xperia phones or tablets
Backup and restore files from the device
Transfer files and music between PC and device
Display remaining free space on Xperia
Xperia Companion 2.11.5.0 on 32-bit and 64-bit PCs
This download is licensed as freeware for the Windows (32-bit and 64-bit) operating system on a laptop or desktop PC from mobile phone tools without restrictions. Xperia Companion 2.11.5.0 is available to all software users as a free download for Windows. Return to prosperity pdf.
Filed under:
X Unlock Tool For Sony Ericsson Xperia Free Download Windows 10
Xperia Companion Download
Freeware Mobile Phone Tools
Major release: Xperia Companion 2.11
Xperia Repair Software

0 notes
Text
Free Software Os

The Free Software Foundation (FSF) is a nonprofit with a worldwide mission to promote computer user freedom.
Featured
LibrePlanet 2021 will be an online event, CFS extended to November 11th
Featured
Apr 30, 2020. Browse and download a wide variety of award-winning video, audio, business, utility, or graphics software programs for both PC and Mac. Free Downloads. Jun 16, 2020.
Watch and share 'Rewind' to help explain free software
'Rewind' is an animated video made for the Free Software Foundation (FSF) about a scientist in a dystopian reality who modifies the code of a program, leading to a groundbreaking discovery. But in our world, which is dominated by proprietary software, would she have the freedom she needs to make a difference?
Free software means that the users have the freedom to run, edit, contribute to, and share the software. Thus, free software is a matter of liberty, not price. We have been defending the rights of all software users for the past 35 years. Help sustain us for many more; become an associate member today.
Our initiatives

LibrePlanet is our network of free software activism around the world, including in-person events like our annual conference, and online collaboration spaces.
'This community that we have, that we're building, that does so much, hasto grow. We can't compete with Apple, we can't compete with Google,directly, in the field of resources. What we can eventually do is headcount and heart count. We can compete on the ground of ideology becauseours is better.'
-- Edward Snowden, NSA whisteblower, speaking at LibrePlanet2016.
Take Action
Bulletin
See all previous Bulletins.
Shop
The FSF's limited edition 35th birthday art was designed by illustrator and artist David Revoy.
Committee begins review of High Priority Projects free software list — your input is needed by January 8
October GNU Spotlight with Mike Gerwitz: Fourteen new releases
14 new GNU releases in the last month (as of October 26, 2020):
Spring internships at the FSF! Apply by Nov. 11
LibrePlanet 2021 will be an online event, CFS extended to November 11th
Streaming services, beware: International Day Against DRM (IDAD) is coming Dec. 4
Thank you for being a part of our 35th birthday celebration
Watch and share 'Rewind' to help explain free software
'Rewind' is an animated video made for the Free Software Foundation (FSF) about a scientist in a dystopian reality who modifies the code of a program, leading to a groundbreaking discovery. But in our world, which is dominated by proprietary software, would she have the freedom she needs to make a difference?
Improvements to the FSF homepage
FSF celebrates thirty-fifth anniversary with week of surprises and online event
Join the FSF for an online birthday celebration on Friday, October 9th
FSF 35 years: Limited edition T-shirt and poster for sale
The FSF's 35th anniversary event
GNU is the only operating system developedspecifically to give its users freedom. What is GNU, and what freedomis at stake?
What is GNU?
GNU is an operating system thatis free software—that is,it respects users' freedom. The GNU operating system consists of GNUpackages (programs specifically released by the GNU Project) as wellas free software released by third parties. The development of GNUmade it possible to use a computer without software that would trampleyour freedom.
Os software, free download
We recommend installableversions of GNU (more precisely, GNU/Linux distributions) whichare entirely free software. More about GNUbelow.
Hyperbola 0.3 with i3 window manager,cool-retro-term (terminal emulator), Gimp (image editor), and Iceweasel-UXP (webbrowser)
Guix / GNOME3
Parabola / LXDE
Trisquel / MATE
What is the Free Software Movement?
The free software movement campaigns to win for the users ofcomputing the freedom that comes from free software. Free softwareputs its users in control of their own computing. Nonfree softwareputs its users under the power of the software's developer. Seethe video explanation.
What is Free Software?
Free software means the users have the freedom to run,copy, distribute, study, change and improve the software.
Free software is a matter of liberty, not price. To understand theconcept, you should think of “free” as in “freespeech”, not as in “free beer”.
More precisely, free software means users of a program havethe four essentialfreedoms:
The freedom to run the program as you wish, for any purpose (freedom 0).
The freedom to study how the program works, and change it so it does your computing as you wish (freedom 1). Access to the source code is a precondition for this.
The freedom to redistribute copies so you can help others (freedom 2).
The freedom to distribute copies of your modified versions to others (freedom 3). By doing this you can give the whole community a chance to benefit from your changes. Access to the source code is a precondition for this.
Developments in technology and network use have made these freedomseven moreimportant now than they were in 1983.
Nowadays the free software movement goes far beyond developing theGNU system. See the Free SoftwareFoundation's web site for more about what we do, and a listof ways you can help.
More about GNU
GNU is a Unix-like operating system. Thatmeans it is a collection of many programs: applications, libraries,developer tools, even games. The development of GNU, started inJanuary 1984, is known as the GNU Project. Many of the programs inGNU are released under the auspices of the GNU Project; those wecall GNU packages.
The name “GNU” is a recursive acronym for “GNU'sNotUnix.” “GNU”is pronounced g'noo, as one syllable, like saying“grew” but replacing the r with n.
Free Software Isp
The program in a Unix-like system that allocates machine resourcesand talks to the hardware is called the “kernel”. GNU istypically used with a kernel called Linux. This combination isthe GNU/Linux operatingsystem. GNU/Linux is used by millions, thoughmany call it “Linux” bymistake.
GNU's own kernel, The Hurd,was started in 1990 (before Linux was started). Volunteers continuedeveloping the Hurd because it is an interesting technicalproject.
The GNU Project supports the Free Software Foundation's petition to call on school administrators around the world to stop requiring students to run nonfree software. Sign the petitionfor freedom in the classroom.
The GNU Project strongly urges the community to communicate in ways that are friendly, welcoming and kind. See the GNU Kind Communications Guidelines.
RFC 8905 - 'The 'payto' URI Scheme for Payments' published: 2020-11: RFC 8905: 'The 'payto' URI Scheme for Payments' publishedWe are happy to announce the publicatio...
[From Arch] libtraceevent>=5.9-1 update requires manual intervention: The libtraceevent package prior to version 5.9-1 was missing a soname link. This has been fixed in 5.9-1, so the upgra...
GNU Parallel 20201022 ('Samuel Paty'): GNU Parallel 20201022 ('Samuel Paty') has been released. It is available for download at: http://ftpmirror.gnu.org/parallel/ Please help...
Take Action
Support the efforts on net neutralityin the USA,and in your home country.
Defend privacy, and support global copyright reform with LQDN.
Support current FSFcampaigns.
Fight against software patents:worldwide, andin Europe.
Can you contribute to any ofthese HighPriority Areas?
Free phone operating system,
decentralization, federation and self-hosting,
free drivers, firmware and hardware designs,
real-time voice and video chat,
encourage contribution by people underrepresented in the community,
and more.
Can you help maintain a GNU package?
cfengine, freedink, freetalk, halifax, mcron, quickthreads,are all looking for maintainers.
Also, these packages are looking for co-maintainers:aspell, bison, gnuae, gnubik, metaexchange, powerguru, xboard.
See the package web pages for more information.
Today's random package…
Free Software Iso Download
Libgcrypt
Free Oscilloscope Software Mac
Libgcrypt is a general-purpose cryptographic library. It provides thestandard cryptographic building blocks such as symmetric ciphers, hashalgorithms, public key algorithms, large integer functions and randomnumber generation.(doc)

0 notes