Text
Cyber Security - Emotet Malware Restarts Spam Attacks After Holiday Break
https://www.prodefence.org/emotet-malware-restarts-spam-attacks-after-holiday-break/
Emotet Malware Restarts Spam Attacks After Holiday Break

After almost a three-week holiday vacation, the Emotet trojan is back and targeting the over eighty countries with malicious spam campaigns.
When Emotet sends spam campaigns the threat actors utilize various email templates that pretend to be invoices, reports, voice mails, holiday party invites, or even invites to a Greta Thunberg climate change demonstration.
These emails include malicious attachments that when opened will install the Emotet trojan.
Once installed, Emotet will use the victim’s computer to send further spam and will also download other infections such as TrickBot, which may ultimately lead to a Ryuk Ransomware infection depending on the target.
Emotet expert Joseph Roosen told BleepingComputer that on December 21st, 2019, Emotet stopped sending spam campaigns even though their command and control servers continued to run and issue updates.
At around 8:30 AM EST today, Roosen told us that Emotet began spewing forth spam campaigns again that target recipients around the world, with a strong focus on the United States.
Emotet is back from the holidays
Current Emotet campaigns being seen today include regular emails and reply-chain attacks pretending to be proof-of-delivery documents, reports, agreements, and statements.
Email security firm Cofense told BleepingComputer that they have seen spam campaigns targeting 82 countries, with a heavy targeting against the United States.
Read More…
0 notes
Text
Cyber Security - Android Trojan Steals Your Money to Fund International SMS Attacks
https://www.prodefence.org/android-trojan-steals-your-money-to-fund-international-sms-attacks/
Android Trojan Steals Your Money to Fund International SMS Attacks
An Android banking Trojan dubbed Faketoken has recently been observed by security researchers while draining its victims’ accounts to fuel offensive mass text campaigns targeting mobile devices from all over the world.
Faketoken is an Android malware strain first introduced in an F-Secure report from 2012 as a Mobile Transaction Authentication Number (mTAN) interceptor camouflaged as a mobile token generator, a Trojan that later added ransomware capabilities in December 2016.
Besides using fake logins and phishing overlay screens to steal credentials and exfiltrating mTAN numbers used by banks to validate online transactions, the malware can also generate customized phishing pages targeting over 2,200 financial apps, and can steal device information such as the IMEI and IMSI numbers, the phone number, and more.
Banking malware turned offensive mass texting tool
“Not long ago, our botnet activity monitoring system — Botnet Attack Tracking — detected that some 5,000 smartphones infected by Faketoken had started sending offensive text messages,” says Alexander Eremin, malware analyst at Kaspersky Lab. “That seemed weird.”
While the vast majority of mobile malware comes with SMS capability out of the box and it uses it for various purposes including intercepting text messages and spreading to other devices, banking malware using it to send mass texts is quite unusual.
Once it manages to infect a target’s device, Faketoken will check if their bank accounts have enough money and it will use the stolen payment cards to add credit to the victim’s mobile account.
After making sure that the funds are ready to be exhausted, Faketoken will proceed to send offensive text messages to local and international phone numbers to infect devices from all over the world on your dime.
“Faketoken’s messaging activities are charged to the infected device owners,” Eremin adds. “Before sending anything out, it confirms that the victim’s bank account has sufficient funds.
Read More…
0 notes
Text
Cyber Security - Android Trojan Steals Your Money to Fund International SMS Attacks
https://www.prodefence.org/android-trojan-steals-your-money-to-fund-international-sms-attacks/
Android Trojan Steals Your Money to Fund International SMS Attacks
An Android banking Trojan dubbed Faketoken has recently been observed by security researchers while draining its victims’ accounts to fuel offensive mass text campaigns targeting mobile devices from all over the world.
Faketoken is an Android malware strain first introduced in an F-Secure report from 2012 as a Mobile Transaction Authentication Number (mTAN) interceptor camouflaged as a mobile token generator, a Trojan that later added ransomware capabilities in December 2016.
Besides using fake logins and phishing overlay screens to steal credentials and exfiltrating mTAN numbers used by banks to validate online transactions, the malware can also generate customized phishing pages targeting over 2,200 financial apps, and can steal device information such as the IMEI and IMSI numbers, the phone number, and more.
Banking malware turned offensive mass texting tool
“Not long ago, our botnet activity monitoring system — Botnet Attack Tracking — detected that some 5,000 smartphones infected by Faketoken had started sending offensive text messages,” says Alexander Eremin, malware analyst at Kaspersky Lab. “That seemed weird.”
While the vast majority of mobile malware comes with SMS capability out of the box and it uses it for various purposes including intercepting text messages and spreading to other devices, banking malware using it to send mass texts is quite unusual.
Once it manages to infect a target’s device, Faketoken will check if their bank accounts have enough money and it will use the stolen payment cards to add credit to the victim’s mobile account.
After making sure that the funds are ready to be exhausted, Faketoken will proceed to send offensive text messages to local and international phone numbers to infect devices from all over the world on your dime.
“Faketoken’s messaging activities are charged to the infected device owners,” Eremin adds. “Before sending anything out, it confirms that the victim’s bank account has sufficient funds.
Read More…
0 notes
Text
Cyber Security - Ransomware Attackers Offer Holiday Discounts and Greetings
https://www.prodefence.org/ransomware-attackers-offer-holiday-discounts-and-greetings/
Ransomware Attackers Offer Holiday Discounts and Greetings

To celebrate the holidays, ransomware operators are providing discounts or season’s greetings to entice victims into paying a ransom demand.
As ransomware operators look at their organizations as a business, it is not surprising to see them offering discounts or season’s greetings to their victims.
Such is the case with the Sodinokibi Ransomware (REvil) who MalwareHunterTeam noticed had changed their ransom note over the holidays to include a new message wishing the victims a “Merry Christmas and Happy Holidays”.
Read more…
0 notes
Text
Cyber Security - FIN7 Hackers' BIOLOAD Malware Drops Fresher Carbanak Backdoor
https://www.prodefence.org/fin7-hackers-bioload-malware-drops-fresher-carbanak-backdoor/
FIN7 Hackers' BIOLOAD Malware Drops Fresher Carbanak Backdoor

Malware researchers have uncovered a new tool used by the financially-motivated cybercriminal group known as FIN7 to load fresher builds of the Carbanak backdoor.
Dubbed BIOLOAD, the malware loader has a low detection rate and shares similarities with BOOSTWRITE, another loader recently identified to be part of FIN7’s arsenal.
Abusing legitimate Windows methods
The malware relies on a technique called binary planting that abuses a method used by Windows to search for DLLs required to load into a program. An attacker can thus increase privileges on the system or achieve persistence.
Read more…
0 notes
Text
Cyber Security - FIN7 Hackers' BIOLOAD Malware Drops Fresher Carbanak Backdoor
https://www.prodefence.org/fin7-hackers-bioload-malware-drops-fresher-carbanak-backdoor/
FIN7 Hackers' BIOLOAD Malware Drops Fresher Carbanak Backdoor

Malware researchers have uncovered a new tool used by the financially-motivated cybercriminal group known as FIN7 to load fresher builds of the Carbanak backdoor.
Dubbed BIOLOAD, the malware loader has a low detection rate and shares similarities with BOOSTWRITE, another loader recently identified to be part of FIN7’s arsenal.
Abusing legitimate Windows methods
The malware relies on a technique called binary planting that abuses a method used by Windows to search for DLLs required to load into a program. An attacker can thus increase privileges on the system or achieve persistence.
Read more…
0 notes
Text
Cyber Security - Your Company's Devices Organized and Secure
https://www.prodefence.org/your-companys-devices-organized-and-secure/
Your Company's Devices Organized and Secure

Keeping data organized and secure can be difficult – especially as your company begins to grow and incorporates more devices. Having a list of devices on the network and a way to see recorded information from each device is necessary to successfully running a business. If your business or company has a network of devices – large or small – having a dedicated software to organizing the information will save you both money and time.These programs are known as network inventory software and offer you a wide range of organizational and monitoring features. Any business in the modern-day should have some form of the program with these capabilities to help keep their business running efficiently and seamlessly. Finding the right network inventory software is where the difficult part comes in.
SNMP Management
SNMP, which stands for simple network management protocol, is essentially a standard of how one collects and organizes data. Having an SNMP tool scan your network will grant you access to information on every router, switch, network printer or other device listed all in one go. This is essentially a quick sweep through your network which gathers information for your use.This information can be about activity on a computer or location of an accessed record. Having this information can allow you to better monitor your network and keep an eye on productivity as well as shield yourself from internal hacking attempts. Having an SNMP scanner as your network discovery tool allows you to have a better grasp on your network.
Total Network Inventory
One of the best online tools for network inventory management is Total Network Inventory 4. This software has led the way for network organizations and continues to offer some of the best program features for an affordable and reasonable price. The program also incorporates SNMP scans which will allow you better access to your network of devices. This program also includes asset management tools thatgrant you easier access to files through methods of filtering and searching. Being the fourth installation of the program, TNI 4 has had time to perfect its software and offers the most up to date features.
Other great software options
Spiceworks
This is a free web solution for your network and one of the most popular programs online. This is a fantastic software to start out with as many companies tend to begin with Spiceworks. If your company is on the smaller end with a few devices on your network, having a free-web solution might be the path you’ll want to follow.
EMCO Network Inventory
Having started their company in 2007, this program has the quality that comes with their experience. This software is on the cheaper end of the spectrum, but the features are that of a higher-end program.
Solarwinds Network Inventory
This program is the best of the best, to be used by large corporations who have a need for the extreme and precise features that come with it. With Solarwinds, you have access to the industry’s best monitoring software and security programs.
Author: Adam Edmund
0 notes
Text
Cyber Security - Evil USB Cable Can Remotely Accept Commands From Hacker
https://www.prodefence.org/evil-usb-cable-can-remotely-accept-commands-from-hacker/
Evil USB Cable Can Remotely Accept Commands From Hacker


Plugging a USB cable into your PC may seem like a harmless affair. But not if the cable has been made by a hacker.
On Sunday, the security researcher Mike Grover demonstrated the threat by creating a malicious USB cable that can receive commands from a nearby smartphone and then execute them over the PC it’s been plugged into.
His USB-to-Lightning cable looks pretty generic, but Grover actually fitted a Wi-Fi chip inside one of the sockets. Unsuspecting users will think they’ve plugged a simple cord into their PC. But in reality, the computer will actually detect the cable as a Human Interface Device akin to a mouse or keyboard.
Grover uploaded a video, showing the attack in action. In it, he plugs the cable into a MacBook. Then he uses his smartphone to remotely trigger the laptop to visit a malicious Google login webpage that can secretly collect the owner’s password.
Read more…
0 notes
Text
Cyber Security - The Needs and Solutions for the Growing E- Commerce Economy
https://www.prodefence.org/the-needs-and-solutions-for-the-growing-e-commerce-economy/
The Needs and Solutions for the Growing E- Commerce Economy

The Need for Financial Software
The growth of technology has changed the face of commerce in today’s economy. Now
from your mobile device you can order everything from a pizza to an engagement ring
and have it delivered directly to your door. All of these interactions require financial
software that ensures that the transactions are made seamlessly. Not only do these
transactions have to be made seamlessly, but both the consumer and the company
wants to make sure that each party is legitimate.
Another place where financial software needed to be improved was in the digital
banking industry. These improvements were seen in the improvement of Automatic
Teller Machines, the broadened use of mobile banking, digital banking with online
savings accounts and retirement accounts, and much more. Companies that used
financial software also needed a way to collect data better and understand what that
data meant to their users.
Financial Software Uses
As the need for financial software grew, software developers started looking for financial
software solutions. Many companies like Intellias, a software development company
based in Ukraine, have risen to the challenge of finding some of these financial software
solutions. Software development companies like Intellias have offered better financial to
their customers in many different forms.
One way companies like Intellias have helped their customers improve their financial
relations with customers is by streamlining their payments and remittances software.
This software allows its customers to be offered a range of payment processing options.
As you can imagine, you might need to use a different payment option when you are
buying your pizza with a coupon, then when you go to buy that engagement ring. These
different payment options allow your customers to find the most convenient method of
payment that suits their needs. In addition, it allows you to monitor transactions, mitigate
risks, and verify your customers that their payment has been received.
Another way software development companies like Intellias have helped their
customers improve their financial relationships with their customers in the digital
banking industry. Software development companies have found financial software
solutions that allow customers to manage their assets better by investing money,
controlling their expenses, and managing their budgets better from the comfort of their
homes or the ease of their mobile devices.
A final example of the way software development companies have helped improve
financial software solutions is the way they have helped companies collect and analyze
data. Financial services constantly try to collect data in order to produce real-time
reports that their business can use to better connect with their clients. In addition, this
data can teach their chatbots to communicate like a real person with their customers.
The data can also be used to forecast financial outcomes and avoid losses using
predictive analytics.
Importance of Financial Software
As more people rely on e-commerce for their business and shopping needs, it is more
and more important that companies focus on financial software solutions. Companies
like Intellias specialize in creating financial software and solving the problems that you
need to be solved within your business.
Author: Adam Edmond
0 notes
Text
Cyber Security - 5 use cases of image recognition that we see in our daily lives
https://www.prodefence.org/5-use-cases-of-image-recognition-that-we-see-in-our-daily-lives/
5 use cases of image recognition that we see in our daily lives

In today’s constantly evolving environment, we all can witness a dramatic shift in technology at
a rapid pace. It is due to such advanced technologies, we have made these advancements, a
daily part of our lives. Such is the case with image recognition as well, where this particular
application has actually changed the perspective of human beings on how we see the world.
Let’s discuss some of the use cases of image recognition that we normally see in our daily
routines.
Gaming
Image recognition has massively turned over the dynamics of the entire gaming industry where
it allows the user to opt for virtual reality options. In addition to this, it also allows them to use
their present location to act as a battlefield where they can play their games. This particular
element has massively attracted the people back towards the gaming era and as a result, we
can see a drastic shift in the gaming industry which gives a whole new experience to the
gamers.
Automobile Sector
Over the years we have heard a lot about self-driving vehicles. However, with such rapid
changes in technology, the incorporation of AI image recognition has actually made the
innovation to happen right now. In fact, not only the traditional producers of cars have
incorporated this “self – driving” element in their vehicles but also the tech giants are willing to
get involved in such creative ideas. The benefit of such execution would lead to a massive
reduction in accident rates and a proper follow of regulation with regards to the traffic situations.
Health Care
Another practical field where image recognition is doing wonders in the healthcare industry,
where such advancements are bringing new cures and treatments for the patients who weren’t
initially possible. In the health care sector, the incorporation of image recognition can be
witnessed in such a manner that microsurgical processes are being encountered by the robots,
which is actually helping the patients to cure their diseases. In fact, another use of AI in this field
can be identified by the fact that a real-time emotion can be detected by analyzing the condition
of the patient which can make the decision as to what further treatment is required.
Security Industry
Since the crime rates have been massively going up, people prefer to opt for measures that can
provide them with complete security and protection of assets and of course, their loved ones
too. In the security industry, the drones, biometric systems, facial recognition, fingerprint access,
home security cameras are some live examples that we see in our daily lives which are
incorporated with image recognition. Due to these advancements in the technological sector, be
it a camera, a smart-phone, your house, bank, office or literally anywhere – one feels safe and
protected.
Social Media
In today’s time, it’s very rare for people not to use social media platforms, which has given the
image recognition field another area to work upon. Since almost all the young generation and
now even the elderly people are actively available on social media platforms, we can clearly see
live examples of image recognition there as well. One of the biggest example is Facebook,
where it has the ability to recognize people by simply putting up a picture online and describing
who exactly is in the image, without having you to tag them manually.
Conclusion
The above practical examples of image recognition clearly make one realize how much things
have changed over the past few years and how much more is yet to come. These live scenarios
of image recognition are something that clearly shows the amount of ease and comfort that has
been added in our lives with the help of these developments.
Author: Adam Edmond
0 notes
Text
Cyber Security - How to Choose the Right Company for Your Embedded Software Project
https://www.prodefence.org/how-to-choose-the-right-company-for-your-embedded-software-project/
How to Choose the Right Company for Your Embedded Software Project

There are numerous reasons for you to opt for outsourcing embedded software
development services such as the fact that they will be able to give you a leg up on your
competition, lessen your development cycle, and assist you in creating a smarter
product. If you find that you don’t have the right skills or the proper resources to develop
embedded software and your company is in need to develop an embedded product,
outsourcing the design will be in the company’s best interest.
If you’ve been lucky enough to find the exact right embedded software development
services, management should be easy. However, on the flip side, if you choose poorly
and there are complications and issues, particularly after the product hits the market,
this can mean a huge loss to the company’s reputation along with product recall.
Companies that offer embedded software development services usually house
engineers with experience in designing embedded software. It is best if they are
capable of developing embedded programs for both larger and smaller products.
Types of Services
An embedded software development services company has the ability to offer to
predesign, design, and post-design services based upon what your particular needs
are. They can support the entirety of a project or just a small portion of the
development. The embedded development may include software coding, concept
definition, and testing programs on a low-level program on up to high-level including
interface development. Here is a list of services that a good embedded software
development service should be able to offer:
● An embedded feasibility study for the software
● Architecture and concept design for the software
● Selection of technology
● Driver development
● Package for board support
● Simulation of design
● Firmware/software development
● Debug of software
● Verification of software design
● Support and field upgrades for software
● Integration of software/hardware.
Tool And Languages
Embedded software design mandates expertise of a certain extent and complete control
over program languages as well as development tools. You can expect embedded
software development services in the market today that you work with to be
knowledgeable in the following examples:
Programming languages:
● Objective C
● Java ME
● C/C++
● Mruby
● Phyton
● Assembly
● Rust
Programming operating systems:
● iOS
● Windows
● Linux
● ThreadX
● Android
● VXWorks
● LynxOS
● QNX
● FreeRTOS
● eCos
Designing an embedded product will require your outsourced embedded software
development services company to hold specific expertise in the development process
and in your particular application area. It’s only by collaborating with the right service
provider that you will be successful in accomplishing a reliable, bug-free solution to your
company’s embedded software product needs.
First, you have to have an understanding of what it is precise that your company’s
embedded software product requirements are and have a working knowledge of what it
will entail meeting those expectations in order to be able to thoroughly and intelligently
inquire with prospective outsource partners that you may have an interest in
collaborating with. Doing your due diligence in obtaining the right fit for the company will
save from any complications or issues that could ultimately do damage to the company
in the end.
Author: Adam Edmond
0 notes
Text
Cyber Security - How to Choose the Right Company for Your Embedded Software Project
https://www.prodefence.org/how-to-choose-the-right-company-for-your-embedded-software-project/
How to Choose the Right Company for Your Embedded Software Project

There are numerous reasons for you to opt for outsourcing embedded software
development services such as the fact that they will be able to give you a leg up on your
competition, lessen your development cycle, and assist you in creating a smarter
product. If you find that you don’t have the right skills or the proper resources to develop
embedded software and your company is in need to develop an embedded product,
outsourcing the design will be in the company’s best interest.
If you’ve been lucky enough to find the exact right embedded software development
services, management should be easy. However, on the flip side, if you choose poorly
and there are complications and issues, particularly after the product hits the market,
this can mean a huge loss to the company’s reputation along with product recall.
Companies that offer embedded software development services usually house
engineers with experience in designing embedded software. It is best if they are
capable of developing embedded programs for both larger and smaller products.
Types of Services
An embedded software development services company has the ability to offer to
predesign, design, and post-design services based upon what your particular needs
are. They can support the entirety of a project or just a small portion of the
development. The embedded development may include software coding, concept
definition, and testing programs on a low-level program on up to high-level including
interface development. Here is a list of services that a good embedded software
development service should be able to offer:
● An embedded feasibility study for the software
● Architecture and concept design for the software
● Selection of technology
● Driver development
● Package for board support
● Simulation of design
● Firmware/software development
● Debug of software
● Verification of software design
● Support and field upgrades for software
● Integration of software/hardware.
Tool And Languages
Embedded software design mandates expertise of a certain extent and complete control
over program languages as well as development tools. You can expect embedded
software development services in the market today that you work with to be
knowledgeable in the following examples:
Programming languages:
● Objective C
● Java ME
● C/C++
● Mruby
● Phyton
● Assembly
● Rust
Programming operating systems:
● iOS
● Windows
● Linux
● ThreadX
● Android
● VXWorks
● LynxOS
● QNX
● FreeRTOS
● eCos
Designing an embedded product will require your outsourced embedded software
development services company to hold specific expertise in the development process
and in your particular application area. It’s only by collaborating with the right service
provider that you will be successful in accomplishing a reliable, bug-free solution to your
company’s embedded software product needs.
First, you have to have an understanding of what it is precise that your company’s
embedded software product requirements are and have a working knowledge of what it
will entail meeting those expectations in order to be able to thoroughly and intelligently
inquire with prospective outsource partners that you may have an interest in
collaborating with. Doing your due diligence in obtaining the right fit for the company will
save from any complications or issues that could ultimately do damage to the company
in the end.
Author: Adam Edmond
0 notes
Text
Cyber Security - 9 Ways to Improve Your Cybersecurity Incident Response Plan
https://www.prodefence.org/9-ways-to-improve-your-cybersecurity-incident-response-plan/
9 Ways to Improve Your Cybersecurity Incident Response Plan

Incident response plan (IRP) is a document called to “detect, respond to, and limit
consequences of malicious cyber attacks”, according to NIST definition. Ideally, a
comprehensive IRP fully protects an organization from insider threats. In real life, the
document needs constant improvements and reviews.
In this article, we discuss 9 ways to make sure your IRP is up to date. These tips help to
improve your procedures and stay focused when you face an attack.
Appoint specific employees responsible for IRP implementation
Every official document designates those responsible for its implementation. But
often it’s not specific enough. For example, a cybersecurity incident response plan
may refer to a particular department or team.
Shared responsibility isn’t that effective when you need your response team to act
fast and efficient. It’s best to appoint a specific person or job title. Such accuracy will
save time during insider attack mitigation.
Keep an eye on compliance recommendations
Following cybersecurity standards and regulations is a must. Fines for non-complying
with GDPR, for example, can reach $20 million or 4% of annual turnover.
NIST, HIPAA, NISPOM, and other standards consist of mandatory requirements and
recommendations too. The easiest way to ensure compliance is to implement only
“must” rules. But you should take a closer look at recommendations as well. They are
based on cybersecurity best practices and can make your security incident response
plan more reliable.
Analyze all insider-related incidents
To defeat an enemy, you must know them. You have two major information sources:
● Known incidents. A thorough study of insider threat cases will save you from
making the same mistakes. Analyze reasons and threat sources relevant to
your industry using materials from the media, expert interviews, and reports
on the subject.
● Incidents inside your company. Incident investigations help to improve your
IRP. If you detect a suspicious pattern of actions, look at it closely. It may
indicate an upcoming attack, or show how you can make cybersecurity
policies more comfortable for employees.
Establish procedures for continuous identification of critical resources
Defining which resources you need to protect is the first step of creating IRP. The
trick is to keep updating this list after the plan is implemented. As time goes by, the
organization’s environment grows, incorporates new services and types of sensitive
data. IRP should reflect those changes.
In order to detect sensitive data, you can employ a data loss prevention (DLP)
system. Such solutions constantly scan a protected perimeter for files with classified
information and detect a possible leakage.
Monitor as much as you can
Thorough monitoring of both regular and privileged users is essential not only for
timely threat detection but for cybersecurity incident response. Records of user
screen activity allow for pinpointing the cause and scope of an attack. Even better, if
you record audio input and output, or use UEBA to establish a baseline of employee
behavior and detect suspicious changes.
This information will help you determine potential losses and mitigating actions.
Ensure reliable external and internal communications
Time is one of the key factors of insider threat cost. When you detect an insider
attack, it’s important to clearly communicate a course of actions inside your response
team. It’s also important to create a clear external communication strategy.
For this reason, you should include a PR representative and a lawyer to your incident
response team. Also, include emergency contacts to your IRP in case responsible
specialists are unavailable.
Fine-tune alerting system
A timely alert on suspicious activity is vital for attack detection and prevention. Any
insider threat software provides you with alerting functionality. It’s important to
personalize this system according to your business processes.
Otherwise, you’ll end up with a lot of false-positive alerts that distract the security
team. Also, security officers turn a blind eye on constant messages about minor
security rules violations. In order to avoid it, employ tools that can automatically react
to minor incidents (e.g. block a session or a user).
Work out a recovery strategy
No matter how well you are prepared to detect an insider threat, there’s always a
possibility to miss it. For such a scenario, your cyberattack response plan should
include a recovery strategy.
This is a set of actions aimed to:
● Establish a regular back up procedure
● Restore damaged or lost data and resources
● Perform an incident review
● Form long-term communication strategies for clients, partners, investors,
business owners, and press
● Conduct incident investigation
Conduct red team and blue team training
An effective training is the best way to ensure that your response team will react
properly if a breach occurs. Red team versus blue team is a classic cybersecurity
practice that allows you to find out weaknesses in your security system, and rehearse
action in case of attack.
During this training, incident response specialists are divided into two teams. The red
team has to steal sensitive data in any way, and the blue team has to prevent or
mitigate the attack.
You can also use other tactics and frameworks to train your cybersecurity team.
Conclusion
An incident response plan is often required by obligatory standards but it can be so much
more than a simple formality. Creating a clear scheme of incident response steps will save
your company a lot of time and resources when a data breach is detected.
In order to stay effective, this document needs to be constantly updated and reviewed. Pay
attention to security best practices, new approaches, expert recommendations, new tools to
be able to detect an insider attack in time and respond to it.
Author: Adam Edmond
0 notes
Text
Cyber Security - 9 Ways to Improve Your Cybersecurity Incident Response Plan
https://www.prodefence.org/9-ways-to-improve-your-cybersecurity-incident-response-plan/
9 Ways to Improve Your Cybersecurity Incident Response Plan

Incident response plan (IRP) is a document called to “detect, respond to, and limit
consequences of malicious cyber attacks”, according to NIST definition. Ideally, a
comprehensive IRP fully protects an organization from insider threats. In real life, the
document needs constant improvements and reviews.
In this article, we discuss 9 ways to make sure your IRP is up to date. These tips help to
improve your procedures and stay focused when you face an attack.
Appoint specific employees responsible for IRP implementation
Every official document designates those responsible for its implementation. But
often it’s not specific enough. For example, a cybersecurity incident response plan
may refer to a particular department or team.
Shared responsibility isn’t that effective when you need your response team to act
fast and efficient. It’s best to appoint a specific person or job title. Such accuracy will
save time during insider attack mitigation.
Keep an eye on compliance recommendations
Following cybersecurity standards and regulations is a must. Fines for non-complying
with GDPR, for example, can reach $20 million or 4% of annual turnover.
NIST, HIPAA, NISPOM, and other standards consist of mandatory requirements and
recommendations too. The easiest way to ensure compliance is to implement only
“must” rules. But you should take a closer look at recommendations as well. They are
based on cybersecurity best practices and can make your security incident response
plan more reliable.
Analyze all insider-related incidents
To defeat an enemy, you must know them. You have two major information sources:
● Known incidents. A thorough study of insider threat cases will save you from
making the same mistakes. Analyze reasons and threat sources relevant to
your industry using materials from the media, expert interviews, and reports
on the subject.
● Incidents inside your company. Incident investigations help to improve your
IRP. If you detect a suspicious pattern of actions, look at it closely. It may
indicate an upcoming attack, or show how you can make cybersecurity
policies more comfortable for employees.
Establish procedures for continuous identification of critical resources
Defining which resources you need to protect is the first step of creating IRP. The
trick is to keep updating this list after the plan is implemented. As time goes by, the
organization’s environment grows, incorporates new services and types of sensitive
data. IRP should reflect those changes.
In order to detect sensitive data, you can employ a data loss prevention (DLP)
system. Such solutions constantly scan a protected perimeter for files with classified
information and detect a possible leakage.
Monitor as much as you can
Thorough monitoring of both regular and privileged users is essential not only for
timely threat detection but for cybersecurity incident response. Records of user
screen activity allow for pinpointing the cause and scope of an attack. Even better, if
you record audio input and output, or use UEBA to establish a baseline of employee
behavior and detect suspicious changes.
This information will help you determine potential losses and mitigating actions.
Ensure reliable external and internal communications
Time is one of the key factors of insider threat cost. When you detect an insider
attack, it’s important to clearly communicate a course of actions inside your response
team. It’s also important to create a clear external communication strategy.
For this reason, you should include a PR representative and a lawyer to your incident
response team. Also, include emergency contacts to your IRP in case responsible
specialists are unavailable.
Fine-tune alerting system
A timely alert on suspicious activity is vital for attack detection and prevention. Any
insider threat software provides you with alerting functionality. It’s important to
personalize this system according to your business processes.
Otherwise, you’ll end up with a lot of false-positive alerts that distract the security
team. Also, security officers turn a blind eye on constant messages about minor
security rules violations. In order to avoid it, employ tools that can automatically react
to minor incidents (e.g. block a session or a user).
Work out a recovery strategy
No matter how well you are prepared to detect an insider threat, there’s always a
possibility to miss it. For such a scenario, your cyberattack response plan should
include a recovery strategy.
This is a set of actions aimed to:
● Establish a regular back up procedure
● Restore damaged or lost data and resources
● Perform an incident review
● Form long-term communication strategies for clients, partners, investors,
business owners, and press
● Conduct incident investigation
Conduct red team and blue team training
An effective training is the best way to ensure that your response team will react
properly if a breach occurs. Red team versus blue team is a classic cybersecurity
practice that allows you to find out weaknesses in your security system, and rehearse
action in case of attack.
During this training, incident response specialists are divided into two teams. The red
team has to steal sensitive data in any way, and the blue team has to prevent or
mitigate the attack.
You can also use other tactics and frameworks to train your cybersecurity team.
Conclusion
An incident response plan is often required by obligatory standards but it can be so much
more than a simple formality. Creating a clear scheme of incident response steps will save
your company a lot of time and resources when a data breach is detected.
In order to stay effective, this document needs to be constantly updated and reviewed. Pay
attention to security best practices, new approaches, expert recommendations, new tools to
be able to detect an insider attack in time and respond to it.
Author: Adam Edmond
0 notes
Text
Cyber Security - Fresh Ursnif (GOZI/ ISFB) campaign
https://www.prodefence.org/fresh-ursnif-gozi-isfb-campaign/
Fresh Ursnif (GOZI/ ISFB) campaign

Some Russian campaign running over leaked email spreads different kind of malware. Today on Yahoo mail has come some fresh Ursnif with 0 detections. |
The domain used for my email was inactive and there was no file for download, but I found it somewhere else.
In the pictures below will find the research steps:
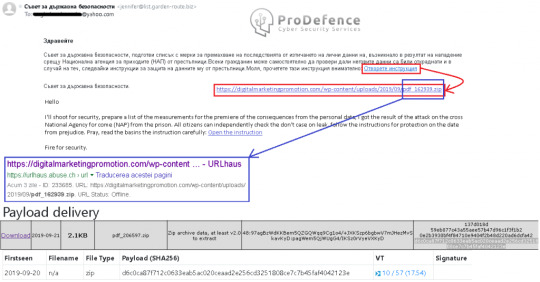
Was easy to find a sample of malware using the SHA256 (d6c0ca87f712c0633eab5ac020ceaad2e256cd3251808ce7c7b45faf4042123e) on Google.
The .zip file is detected and this may be an advantage for the users IF they are using the Antivirus that have on his database this sample… but this is another discussion…
At this moment the VirusTotal says 18/57.. so is going to be better in a few hours.
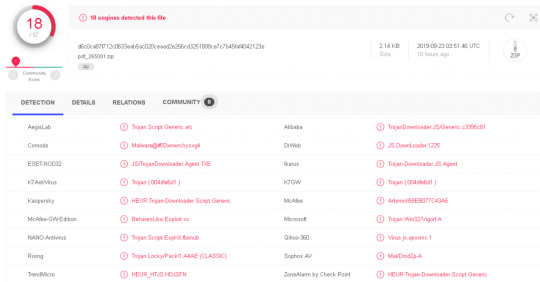
Now.. extracting them one by one we have a good encrypted malware named Ursnif (GOZI/ ISFB). This malware is trying to steal baking credentials from his victims and the hacker may have access to the system.
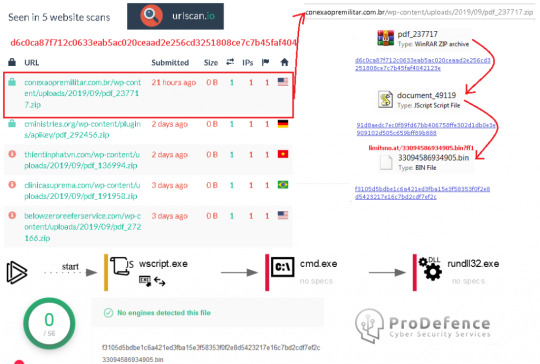
I will not explain the whole process at this time but how-to that you may find on some recent post I’ve made:
https://www.prodefence.org/malware-analysis-gozi-ifsb-bank-trojan-aka-ursnif/
Useful links:
Urlscan with samples
VirusTotal .zip
VirusTotal .js
VirusTotal .bin
0 notes
Text
Cyber Security - Just an update of our work in cyber security field.
https://www.prodefence.org/just-an-update-of-our-work-in-cyber-security-field/
Just an update of our work in cyber security field.
The time is not our friend and that’s why we prefer just to edit the pictures with the results of some analysis.
#malwareanalysis
#cybersecurity
#prodefence
#securityresearch
#mobilebotnet
0 notes
Text
Cyber Security - Hack the Zone Conference and Challenges 2019
https://www.prodefence.org/hack-the-zone-conference-and-challenges-2019/
Hack the Zone Conference and Challenges 2019

Real dynamic challenges, one unique event in Europe – Hack the Zone Conference and Challenges Unique not just in Romania, but also in Europe, Hack the Zone Conference and Challenges wishes to reunite all Ethical Hacking passionate.

If you are interested or know someone who might be interested in taking part in a fun event with real Capture the flag challenges, then keep reading.. What is Hack the Zone Conference and Challenges? The event takes place in October and is divided in 2 stages: 1. The Challenges: start date 12-13th of October, the challenges require the participants to travel to different geolocations in Bucharest2. The Conference: 17-18th of October at Crystal Palace Ballrooms, 198A Calea Rahovei, District5 It’s no coincidence that the event takes place in October, October has been declared as the Cyber Security Month by the European Union.HTZ event aims to build a community of Ethical Hackers in Romania and also to raise awareness on the latest threats in the cybersecurity industry. HTZ “Experiment how it feels to be part of a RED TEAM!” HTZ

Challenges are especially designed to help participants to prove and improve their skills by being part of a RED TEAM. The quests have different levels of difficulty and only one participant will be the winner.The winner will take home 3000 euro and uncover other fun surprises at the Conference. The Challenges will test your creativity and analytic thinking!Furthermore the challenges will also test your knowledge of: pen-testing, scripting, social engineering, crypto and many more.Only few will pass the majority of the challenges, while faced with a real simulation of a cybersecurity attack. Follow the guidelines carefully and get to know instructions in order to reach the final stage.If 2 participants get to final stage, the one with the best timing will win.For more information on the guidelines and instructions go to hackthezone.comHack the Zone Conference – talking about the hottest topics in cybersecurity at the moment As previously mentioned, the 2nd part of the event is the Conference which reunites speakers across the IT industry and debates different security topics focusing on latest threats, prevention and resolution. During the 2 days Conference, the participants can meet and network with different companies representatives, take part in different activities on site and also explore career opportunities. On the last day of the Conference the HTZ team will announce the winner, but before that, we will reveal the step by step walkthrough. Tickets to the event can be purchased on iabilet.ro and eventbrite.com, for more information around the event please visit hackthezone.com.
0 notes