Text
The most effective method to Use Microsoft's Remote Desktop Connection

You're before a PC at home or at the workplace and need to get to an alternate PC to get a record, open an application, or investigate an issue. How might you arrive at that other PC? For whatever length of time that that other PC is turned on and set up for far off associations.
Through RDC, you can distantly get to numerous PCs over a similar system. You can likewise utilize it to get to PCs on various systems through the web, yet that requires some information on firewalls and port sending. So we'll concentrate on interfacing with a PC on a similar system.You can sign in and control it from a far distance utilizing Microsoft's Remote Desktop Connection highlight check here.
Distant Desktop Connection is incorporated with Windows yet in addition exists as a Windows 10 Universal application at the Microsoft Store. On the off chance that you need to access and control a PC from your cell phone, Microsoft's RDC application is accessible at Apple's App Store for iPhones and iPads and from Google Play for Android telephones and tablets.
Set Up Microsoft Remote Desktop Connection
To begin with, you or another person should genuinely sign into the distant PC (the PC you need to access from your present area). To do this, open Settings > System > Remote Desktop. Turn on the change to Enable Remote Desktop. Snap Confirm to empower the setting.
Of course, the alternatives to keep your PC conscious for associations when connected and make your PC discoverable on private systems are both empowered. To see or adjust either alternative, click the relating connect to Show settings, yet you ought to likely leave the two choices empowered now. Rather, click the connection for Advanced settings.
At the Advanced settings screen, check the case to expect PCs to utilize Network Level Authentication (NLA) to associate. NLA includes more tight security for far off associations over a similar system as clients must be confirmed before accessing the far off PC.
Accepting that you're interfacing with a PC on a similar system, you can overlook the segment for External associations. The segment for Remote Desktop port shows the default port to tune in for and acknowledge a far off association.
Snap the back bolt to come back to the past screen and look through the Remote Desktop settings. As a matter of course, any client who has a managerial record on the far off PC can get to it.
Accepting that you're utilizing a Microsoft Account to sign into Windows, and your record has regulatory rights, your smartest choice is to just utilize that record to sign in distantly. In the event that you need to allow far off access to an alternate record, click the connection at the base to Select clients that can distantly get to this PC. Snap Add and enter the client name for that account.
At long last, make note of the name of this PC as you'll require it to sign in distantly. On the off chance that you wish to change the PC name to something simpler to recall, follow these means. Close the Remote Desktop settings screen when you're done.
Associate with Remote PC
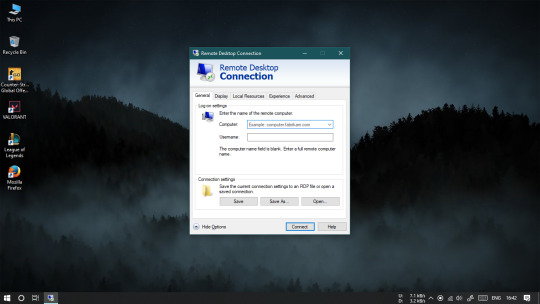
Presently suppose you need to interface with this distant PC. From the PC you wish to use to get to the distant PC, dispatch Remote Desktop Connection. To do this, click the Start button, look down the rundown, open the organizer for Windows Accessories, and select the easy route for Remote Desktop Connection. Or on the other hand click in the Search field, begin composing Remote Desktop Connection, and select the outcome.
At the RDC window, type the name of the distant PC in the Computer field. Snap the Show Options catch, and type the client name of the record you'll use to sign in. Snap Connect.
Enter your secret word at the certifications window. Check the Remember me box on the off chance that you would prefer not to enter your secret phrase each time you utilize this record. Snap OK.You may get a message saying that the personality of the distant PC can't be checked. Check the case for Don't approach me again for associations with this PC and snap Yes.
You should now interface with the distant PC so you can run applications, open and work with records, and perform different errands.
At the head of the screen is a blue association bar with different alternatives. The controls on the left half of the bar let you pin the bar and check the association speed. The controls on the correct side permit you to limit the far off window to the taskbar, change the window size, and end the distant meeting. At the point when you're done, click the Close symbol to end the association.
Distant Desktop Settings
From the arrangement screen for Remote Desktop Connection, you can change a portion of the apparatus' settings. At the General tab, check the choice to "Permit me to spare accreditations" in the event that you would prefer not to enter your client name and secret phrase each time you associate.
At the Display tab, you can change the size of the distant window and select a shading profundity.
Arrange far off sound settings and pick when to apply Windows key mixes at the Local Resources tab.
Physically modify your association speed to control the exhibition from the Experience tab.
Set the default activity for worker confirmation from the Advanced tab.
Far off Desktop App
As an option to the inherent Remote Desktop Connection device, you can utilize the Microsoft Remote Desktop application. Introduce the application from the Microsoft Store and dispatch it. To set up an association, click the Add button and select the choice for Desktop.
Type the name of the PC to which you need to interface. Snap the + catch to include your record. At the record window, include your client name and secret key. You can likewise include a record epithet in the event that you wish. Snap Save.
At the Add a work area screen, you can make a presentation name for this association. Snap Save.
Double tap the symbol for the distant PC to interface with it.At the authentication screen, check the container to not get some information about this endorsement once more. Snap Connect.You're currently associated with the distant PC. Things look somewhat better than they do from the RDC device. The magnifier symbol at the top zooms in and out, while the ellipsis symbol switches between full screen and windowed mode. Snap the ellipsis symbol and afterward select Disconnect to end the association.
Interface with Remote PC With a Mobile Device
Interface From iOS
To interface with a far off PC from an iPhone or iPad, introduce the Microsoft Remote Desktop application from the App Store and dispatch it.
Tap the + button and select the Desktop choice.
Enter the PC name. Type or pick your client account. Under Additional Options, you can make a neighborly name for the association and empower different settings. Tap Save.Tap the symbol to associate with the PC. At the Credentials screen, enter your secret key and afterward turn on the change to Store client name and secret word in the event that you would prefer not to enter them each time. Tap Done.At the verification window, turn on the switch for Don't approach me again for association with and afterward tap Accept.
You're presently associated. The first toolbar symbol zooms in and out. The subsequent one presentations sheets as an afterthought from which you can begin another association, switch among contact and mouse pointer, and end the meeting. The third one shows the console.
Interface From Android
At last, you can associate with a Windows PC from an Android telephone or tablet. Download the Microsoft Cheap RDP application from Google Play and dispatch it. Acknowledge the understanding.
Tap the + symbol to include an association and select the Desktop choice.
Tap the symbol to associate with that PC. Enter your secret key and check the container to Store client name and secret phrase on the off chance that you wish. Tap Connect.At the declaration confirmation screen, check the crate to Never approach again for associations with this PC and snap Connect.You're currently associated. The first toolbar symbol shows sheets as an afterthought from which you can begin another association, end the current association, return Home, and switch among contact and mouse pointer. The other symbol shows the console. Tap the X in the upper-left corner to detach.
0 notes
Text
RDP Security Explained

RDP on the Radar
As of late, McAfee discharged a blog identified with the wormable RDP weakness alluded to as CVE-2019-0708 or "Bluekeep." The blog features a specific weakness in RDP which was esteemed basic by Microsoft because of the way that it exploitable over a system association without verification. These traits make it especially 'wormable' – it can undoubtedly be coded to spread itself by connecting with other available arranged hosts, like the well known EternalBlue adventure of 2017. This appears to be especially significant when (at the hour of composing) 3,865,098 examples of port 3389 are appearing as open on Shodan.
Before this, RDP was at that point on our radar. Last July, McAfee ATR did a profound jump on Remote Desktop Protocol (RDP) commercial centers and portrayed the sheer straightforwardness with which cybercriminals can get access to an enormous assortment of PC frameworks, some of which are extremely delicate. One of the strategies for Cheap RDP abuse that we talked about was the manner by which it could help conveying a focused on ransomware crusade. Around then one of the most productive focused on ransomware bunches was SamSam. To increase an underlying traction on its casualties' systems, SamSam would regularly depend on pitifully secured RDP get to. From its RDP launchpad, it would continue to move horizontally through a casualty's system, effectively misusing and finding extra shortcomings, for example in an organization's Active Directory (AD).
In November 2018, the FBI and the Justice division arraigned two Iranian men for creating and spreading the SamSam ransomware blackmailing clinics, districts and open foundations, causing over $30 million in misfortunes. Shockingly, this didn't prevent different cybercriminals from utilizing comparable strategies, methods and methodology (TTPs).
The sheer number of weak frameworks in the wild make it a "target" rich condition for cybercriminals.
In the start of 2019 we devoted a few online journals to the Ryuk ransomware family that has been utilizing RDP as an underlying section vector. Despite the fact that RDP abuse has been around for a long time, it appears to have increased an expanded notoriety among hoodlums concentrated on focused ransomware.
Ongoing insights demonstrated that RDP is the most prevailing assault vector, being utilized in 63.5% of unveiled focused on ransomware battles in Q1 of 2019.
Making sure about RDP
Given the desperate conditions featured above it is astute to address if remotely open RDP is an outright need for any association. It is additionally savvy to consider how to all the more likely secure RDP on the off chance that you are totally dependent on it. The uplifting news is there are a few simple advances that help an association to all the more likely secure RDP get to.
Suggestions are extra to standard frameworks cleanliness which ought to be completed for all frameworks (despite the fact that it turns out to be progressively significant for Internet associated has, for example, staying up with the latest, and we deliberately keep away from 'security through lack of definition' things, for example, changing the RDP port number.
Try not to permit RDP associations over the open Internet
To be extremely clear… RDP ought to never be available to the Internet. The web is ceaselessly being examined for open port 3389 (the default RDP port). Indeed, even with an intricate secret phrase strategy and multifaceted validation you can be defenseless against refusal of administration and client account lockout. An a lot more secure option is to utilize a Virtual Private Network (VPN). A VPN will permit a far off client to safely get to their corporate system without presenting their PC to the whole Internet. The association is commonly scrambled, giving validation to both customer and worker, ideally utilizing a double factor, while making a safe passage to the corporate system. As you just approach the system you will at present need to RDP to the PC yet can do so more safely without presenting it to the web.
Utilize Complex Passwords
A regularly utilized elective abbreviation for RDP is "Extremely Dumb Passwords." That short expression typifies the main weakness of RDP frameworks, essentially by filtering the web for frameworks that acknowledge RDP associations and propelling an animal power assault with well known apparatuses, for example, ForcerX, NLBrute, Hydra or RDP Forcer to obtain entrance.
The following are the best 15 passwords utilized on helpless RDP frameworks. We manufactured this rundown dependent on data on powerless passwords shared by an agreeable Law Enforcement Agency from brought down Forex RDP shops. What is most stunning is the way that there is such an enormous number of helpless RDP frameworks didn't have a secret word.
Use Multi-Factor Authentication
Notwithstanding a mind boggling secret key, it is best practice use multifaceted verification. Indeed, even with incredible consideration and perseverance, a username and secret word can in any case be undermined. In the event that real accreditations have been undermined, multifaceted confirmation includes an extra layer of insurance by requiring the client to give a security token, for example a code got by warning or a biometric check. Even better, a FIDO based validation gadget can give an additional factor which isn't helpless against ridiculing assaults, likewise to other one-time-secret word (OTP) components. This expands the trouble for an unapproved individual to access the processing gadget.
Utilize a RDP Gateway
Ongoing forms of Windows Server give a RDP door worker. This gives one outer interface to numerous interior RDP endpoints, accordingly rearranging administration, including a large number of the things laid out in the accompanying suggestions. These involve logging, TLS declarations, verification to the end gadget without really presenting it to the Internet, approval to inner host and client limitations, and so forth.
A high number of fizzled logon endeavors is a solid sign of a beast power assault. Constraining the quantity of logon endeavors per client can forestall such assaults. A fizzled logon endeavor is logged under Windows Event ID 4625. A RDP logon falls under logon type 10, RemoteInteractive. The record lockout limit can be determined in the nearby gathering strategy under security settings: Account Policies.
For logging purposes, it is ideal to log both fizzled and effective logons. Moreover, it is essential to take note of that "particular security layer for RDP associations" should be empowered. Else, you will be not able to tell that the logon endeavor came over RDP or see the source IP address. A correlation is demonstrated as follows.
Utilize a Firewall to limit get to
Firewall rules can be made to limit Remote Desktop get to so just a particular IP address or a scope of IP locations can get to a given gadget. This can be accomplished by basically opening "Windows Firewall with Advanced Security," tapping on Inbound Rules and looking down to the RDP rule. A screen shot can be seen underneath.
Empower Restricted Admin Mode
When interfacing with a distant machine by means of RDP, certifications are put away on that machine and might be retrievable by different clients of the frameworks (for example malevolent assailants). Microsoft has included limited administrator mode which educates the RDP worker not to store certifications of clients who sign in. In the background, the worker currently utilizes 'organize' login instead of 'intelligent' and in this way utilizes hashes or Kerberos tickets as opposed to passwords for confirmation. Evaluation of the upsides and downsides of this alternative are suggested before empowering in your condition. On the negative side, the utilization of system login uncovered the chance of accreditation reuse (pass the hash) assaults against the RDP worker. Pass the hash is likely conceivable at any rate, inside, through other uncovered ports so may not altogether increment presentation there, however while including this choice to Internet workers, where different ports are likely (and ought to be!) limited, pass the hash is then reached out to the Internet. Given the advantages and disadvantages, dodging interior heightening of benefit is regularly organized and in this way limited administrator mode is empowered.
Encryption
There are four degrees of encryption bolstered by standard RDP: Low, Client Compatible, High, and FIPS Compliant. This is designed on the Remote Desktop worker. This can be additionally enhanced by utilizing Enhanced RDP Security. At the point when Enhanced RDP security is utilized, encryption and worker verification are executed by outer security conventions, for example TLS or CredSSP. One of the key advantages of Enhanced RDP Security is that it empowers the utilization of Network Level Authentication (NLA) when utilizing CredSSP as the outside security convention.
Empower Network Level Authentication (NLA)
To diminish the measure of at first required worker assets, and along these lines alleviate against forswearing of administration assaults, arrange level validation (NLA) can be utilized. Inside this mode, solid verification happens before the far off work area association is built up, utilizing the Credential Security Support Provider (CredSSP) either through TLS or Kerberos. NLA can likewise assist with securing against man-in-the-center assaults, where qualifications are captured. Be that as it may, know that NLA over NTLM doesn't give solid validation and ought to be handicapped for NLA over TLS (with substantial declarations).
Confine clients who can logon utilizing RDP
All chairmen can utilize RDP of course. Far off access ought to be constrained to just the records that require it. On the off chance that all chairmen needn't bother with distant access you ought to consider expelling the Administrator account from the RDP get to gathering. You would then be able to include the particular clients which expect access to the "Far off Desktop Users" gathering. See here for more data on overseeing clients in your RDS assortment.
End
When attempting to run an effective IT association, having far off access to certain PC frameworks may be basic. Sadly, when not actualized effectively, the apparatuses that make distant access conceivable likewise free your frameworks up to undesirable visitors. Over the most recent couple of years there have been dreadfully numerous instances of
0 notes
Text
What is RDP? Also, how to utilize it?
We take a top to bottom look a the MS's Remote Desktop Protocol (RDP) and how to utilize it. We additionally incorporate recommend the most hearty option RDP devices.
The Windows Remote Desktop Connection instrument enables clients to associate with a far off Windows PC or worker over the web or on a nearby system, giving them full access to the devices and programming introduced on it. This is made conceivable by Microsoft's own Remote Desktop Protocol (or RDP for short).
All Windows PCs and workers can utilize RDP to interface with another Windows gadget, yet just certain forms of Windows permit RDP associations. This restrictive convention equals the open-source Virtual Network Computing (VNC) convention usually utilized on Linux and different stages.
What is RDP?
The Remote Desktop Protocol permits far off clients to see and use Windows on a gadget in another area. Key peripherals like your console and mouse are imparted to the far off machine, permitting you to utilize and control it as though you were sat directly before it.
For RDP associations with work, you need two parts—a RDP worker and a RDP customer. A regular RDP worker is the Windows PC or worker you're associating with and will control. The customer is a PC or cell phone with a RDP customer application introduced, from which you control the worker. Microsoft offers its own customer for Windows, macOS, Android, and iOS, with different outsider choices accessible for Linux and different stages.
RDP is a Windows-just convention, and you can just set up distant associations utilizing RDP with Windows PCs and Windows Server establishments that help it. Not all forms of Windows do—Windows 10 Home, for example, must be utilized as a customer to associate with different Windows Remote Desktops, not the reverse way around.
You can just build up a solitary association with Windows PCs that have far off work area empowered. To associate numerous clients without a moment's delay, you'll need a Windows worker with the Remote Desktop Services (RDS) part introduced and empowered.
In the event that you need to set up RDP associations with a protected undertaking system from a far off area, you'll additionally require the Remote Desktop Gateway administration introduced and designed on a reasonable Windows Server establishment. This additionally offers expanded security, swapping the requirement for an inner virtual private network (VPN).
Step by step instructions to empower Remote Desktop associations on Windows
To utilize RDP to associate with another Windows PC or worker, you'll first need to empower it on the far off worker or PC. Fortunately, designing Windows to empower Remote Desktop is a genuinely direct procedure.
To empower Remote Desktop on Windows PCs:
Open the Windows Settings menu. To do this, click the Start button, at that point press the Settings symbol. From here, press System > Remote Desktop.
Press the Enable Remote Desktop slider to move it to the On position. The slider will turn blue when Remote Desktop has been empowered.
Of course, the Microsoft account you use to sign in will be the record you use to associate with your PC distantly. To permit extra clients to interface, press Select clients that can distantly get to this PC. In the Remote Desktop Users window, press Add and quest for the client account.
To take into account RDP associations over the web, you'll ordinarily need to permit approaching and active associations with TCP/UDP port 3389 on your system, except if port sending is essentially.
Tips for building up secure Windows Remote Desktop associations
Any sort of distant work area arrangement opens a gap that can possibly be abused. RDP is the same, and the RDP (port 3389) is notable and routinely checked for abuses. In the event that you intend to utilize Windows Remote Desktop over the web, you need a methodology set up to make sure about it.
Undertaking clients can utilize Remote Desktop Gateways to help give a protected method to interface with a RDP worker, however standard Windows clients don't have this extravagance. Rather, you'll have to utilize some good judgment answers for build up secure RDP associations. A few hints for building up a safe RDP association include:
1.Try not to permit open RDP associations over the web. On the off chance that you have to utilize Windows Remote Desktop over the web, set up your own virtual private system (VPN) or utilize a RD Gateway to make a protected passage to your nearby system first. Permitting an open RDP association over the web is incredibly hazardous, so don't leave it to risk.
2.Empower Network Level Authentication (NLA). This ought to be empowered as a matter of course in Windows 10, Windows Server 2012, and more current, yet in case you're utilizing more established variants of Windows, you should empower this—it guarantees that an association can possibly happen when it is appropriately verified and a privilege username and secret phrase is given.
3.Confine RDP associations with non-overseers. You should just permit non-director client records to distantly interface with Windows PCs. Standard client accounts can't change settings, introduce programming, and have restricted access to records. This should confine the harm that any potential rebel association could make.
4.Breaking point secret word endeavors. You should restrict the quantity of off base passwords on a record before it is bolted out, which should confine any harm from a disavowal of administration assault.
5.Utilize perplexing, secure passwords. Utilizing secure passwords is a word of wisdom for any circumstance, yet particularly for Windows Remote Desktop associations. Try not to utilize a similar secret phrase for various records, and utilize a blend of letters, numbers, and images.
6.Set RDP for most extreme encryption. As a matter of course, RDP associations will consistently attempt to utilize the most noteworthy conceivable degree of encryption. To guarantee that the most elevated level of encryption is constantly utilized, notwithstanding, you can set the default encryption level utilizing the Group Policy Editor (Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security > Set customer association encryption level > Enabled > High Level).
1 note
·
View note