Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/phishing-protection/if-you-cant-trust-your-phishing-protection-company-who-can-you-trust
If You Can’t Trust Your Phishing Protection Company, Who Can You Trust?

Phishing protection is big business. There are many providers out there using advanced technologies to protect companies of all sizes. And these technologies are needed, because as research has shown, phishing protection education alone will not protect your company.
Now it has come out that one of the larger email security firms, Cofense (formerly PhishMe), is partly owned by, wait for it, a Russian oligarch.
According to an article on Reuters this month, “U.S. cybersecurity firm Cofense Inc. said on Wednesday that buyout firm Pamplona Capital Management is seeking to sell its stake in the company following a year-long probe by U.S. national security regulators.”
The article further stated that, “Pamplona bought a minority stake in Cofense, which serves major corporations, in February 2018, when the company was known as PhishMe. Pamplona’s funds [have] been partly backed by Russian billionaire Mikhail Fridman, who was on a February 2018 “oligarchs’ list” published by the U.S. Treasury Department.”
Pamplona declined to comment.
Well if you can’t trust your phishing protection provider who can you trust?
There are times when a small service provider is preferable to a larger one, like when you’re purchasing security services. Why is that? Because it’s much easier to understand who owns a small company compared to a large one. With small companies, it’s usually apparent who all the decision makers are. With larger corporations, you have to worry about management teams, board members and investors. And it only takes one to compromise the whole thing.
If you’re in the market for phishing protection services, consider a smaller service provider. One that’s been around for years with an excellent track record and superior customer service.
The Wall Street Journal first reported the news: U.S. Officials Pressure Russia-Linked Buyout Firm to Sell Stake in Cybersecurity Company (Paywall).
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/announcements/if-your-email-server-stops-accepting-emails-how-long-will-it-take-you-to-find-out
If Your Email Server Stops Accepting Emails How Long Will it Take You to Find Out?

Servers go down. And when they do it can negatively impact your business, from lost productivity to lost customers. You don’t want that to happen. Monitoring email is not as simple as checking to see if the port responds, you have to validate that the entire mail flow is functioning. So, how do you find out that your email server is down and not accepting emails or just taking too long to respond? More importantly, how long does it take for you to discover it? Minutes? Hours?
What you need is a mail flow monitoring service. One that checks your email server status every few minutes automatically without any intervention from you and alerts you if something isn’t right. Oh sure, there are monitoring tools out there, but they’re expensive, costing up to $30 per month per monitor.
What you need is a mail flow monitoring service that doesn’t cost anything. Oh sure, there are some free monitoring services out there, but they typically limit you to monitoring only one mail server.
What you need is a mail flow monitoring service that doesn’t cost anything and lets you monitor an unlimited number of email servers and also lets you:
Choose how to be alerted (email, webhook, SMS, PagerDuty or Slack)
Set up an unlimited number of notification policies
Set up different alert methods for different policies
Control how often to check your mail servers
Control the Round Trip Time (RTT) threshold
Control the Notification Delay Rate
See real-time and historical stats in an easy-to-use dashboard
Get up and running in 5 minutes
Something like that does exist and it’s MailFlowMonitoring.com. It monitors the smtp transactions and email round trip time for free, the way you want to monitor them.
Create a Free Email Monitoring Account
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/email-security/the-one-big-drawback-of-using-saas-providers-and-what-to-do-about-it
The One Big Drawback of Using SaaS Providers and What to do About it

We live in a software-as-a-service (SaaS) world. It’s great being able to pay a monthly fee and have some other companies handle your organization’s services for you. There are all kinds of companies that provide SaaS services.
There are companies that take care of
customer service (e.g., Zendesk),
marketing campaigns (e.g., SendGrid)
customer relationship management (e.g., Salesforce)
company benefits (e.g., Zenefits) and
even payroll (e.g., Workday).
And the one thing all these service providers have in common is they send out emails to your customers and employees on your behalf. Generally speaking, that’s a good thing, but it does come with a big drawback most people aren’t even aware of.
To prevent email spoofing, your company will want to use an email authentication technique called Sender Policy Framework or SPF. This protects your customers and employees by ensuring they only receive emails from service providers you approve.
Now, you don’t typically know the IP addresses of the email servers your service providers use to send out emails, and they often use more than one. But, you do know their domains (e.g., sendgrid.com, salesforce.com) and so that’s what you’ll put in your SPF record to protect your customers and employees. You only want them receiving emails from those companies’ domains. And that’s where the trouble begins.
SPF authentication only deals with IP addresses, not domains.
So, when you enter the domain of one of your service providers, you’re forcing the SPF authentication process to look up those IP addresses in the domain name system (DNS). But, the DNS has a strict limit of 10 lookups and that’s a problem.
Once the DNS lookup limit is reached, the process will no longer convert domains to IP addresses. That means either your customers/employees are getting unauthenticated emails, or worse, not getting them at all. And what makes it even worse is you’ll never know about it because SPF has no error handling capability.
One of the ways you could try to address the problem is by figuring out all of your service providers’ IP addresses and putting them in the SPF record instead of the domains to reduce the number of DNS lookups to less than ten. This technique is called “SPF flattening.” The problem with this approach is that the IP addresses used by your service providers to send out email changes all the time, and they’re not going to go out of their way to let you know about it.
To do it right, manually flattening your SPF record requires that you constantly monitor your service providers for changes in their IP addresses. What you need is a way to do that automatically, hands-off, with no intervention from you. And that’s where AutoSPF comes in.
With AutoSPF you just point your SPF record to the AutoSPF server and AutoSPF takes care of the rest. AutoSPF always returns a flattened SPF record to public DNS queries. It checks for changes in IP addresses of your service providers every couple of minutes so you don’t have to.
Adding SPF flattening with AutoSPF is fast, easy and affordable. There are no sales calls, no contracts and you’re up and running in ten minutes. And AutoSPF works with all 3rd party email service providers. What are you waiting for? Try AutoSPF risk-free for 30 days. Your customers and your employees will be glad you did.
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/phishing-protection/stop-making-hackers-job-too-easy
Stop Making Hackers’ Job Too Easy

It’s a common folklore that the greatest cyber-attacks in history are pulled off by genius hackers using clever hacking techniques to exploit a zero-day vulnerability on some obscure back-room database server. The reality is very different.
According to a recent study by security firm Centrify, “74 percent of respondents whose organizations have been breached acknowledge it involved access to a privileged account.” In other words, they got phished. How else do you think the hackers got the usernames and passwords?
Rather than spending hundreds of hours and millions of CPU cycles trying to hack into a computer network, hackers simply craft a quick phishing email and get some employee’s login credentials. Most likely an employee with access to a privileged account.
According to an article on Security Week website, “This number closely aligns with Forrester’s estimate that 80 percent of security breaches involve compromised privileged credentials. When a privileged account gets compromised, it allows the cyber-attacker to impersonate a legit employee or system and carry out malicious activity without being detected as an intruder. Once hackers compromise a privileged account, they can typically roam at will across an IT environment to exfiltrate data and cause damage.”
People and organizations are making it too darn easy on hackers.
Of course there are many technologies which can be used to try and stop compromised credentials. These include multi-factor authentication (MFA), establishing access zones, enforcing least privilege, behavior-based machine learning and risk scoring. Some of these technologies are more effective than others.
Perhaps the simplest way to prevent employees’ credentials from being compromised is to eliminate the possibility of employees getting phished. It’s not as sexy as some of those other technologies, but anti-phishing technology has been around for a while. It’s fast to deploy and doesn’t cost much. And more importantly, it works.
Whenever I read about some hack somewhere, I inevitably also read about the victims scrambling to find some super new technology to address the most recent hack. But, sometimes the solution already exists and is right in front of you.
If you want to put a stop to compromised credentials at your company, and you want to do it fast, then you are at the right place. Duocircle, with Advanced Threat Defense, is a cloud-based email security service that protects employees from malicious emails 24/7 on any device. You’ll be up and protected in ten minutes.
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/phishing-protection/top-phishing-targets-by-industry-2019-edition
Top Phishing Targets by Industry: 2019 Edition
Phishing attacks are becoming more prevalent across almost all industries worldwide. But some industries are targeted more frequently than others.
Email fraud remains one of the most common ways cybercriminals gain unauthorized access to their victims’ IT systems. Now, however, cybercriminals are beginning to expand their attacks to include more sophisticated tactics that rely on email, social media, and even victims’ mobile devices. You need more than email security to protect yourself against phishing.
We’ve compiled some of the latest statistics on industry-specific cybersecurity into a single resource for small businesses, mid-sized organizations, and enterprises. Find out where your organization stands.
Phishing Attacks by Industry
Globally, phishing attack attempts grew by 80% across all industries between 2017 and 2018. But this growth has not been uniform. According to the latest cybersecurity statistics, the top three phishing targets for 2018 were:
Pharmaceutical Manufacturers
Retail and eCommerce Companies
Government Institutions
Cybersecurity professionals have collected specific data related to each of these industries. Each one presents a unique set of advantages to cybercriminals and hackers.
1. The Pharmaceutical Industry
At first, it might seem surprising that the pharmaceutical industry would be targeted by cybercriminals, but there are good reasons for this. The success of any pharmaceutical manufacturer relies on its intellectual properties – the recipes they follow for the various drugs and compounds they create.
Cybercriminals who successfully get their hands on this kind of intellectual property can sell it on the black market for enormous sums of money.
Alternately, they can hold the manufacturer ransom and extort money out of them in exchange for keeping their trade secrets secret.
In 2018, organizations in the pharmaceutical industry reported an average of 282 cyber attack attempts per company over the course of the year. This corresponds to a 149% jump in the number of email phishing attempts compared to the same period in 2017.
2. The Retail and eCommerce Sector
Retail and ecommerce organizations are among the most targeted cyber attack victims for an obvious reason – hackers see large retail brands as wealthy and easy to fool. However, smaller retail organizations are also targeted frequently, and unlike large retail enterprises, they rarely have adequate cybersecurity solutions in place for protection from phishing attacks.
Retail accounted for almost 40% of all known cyberattacks in the second half of 2014. These attacks include everything from business email compromise attacks to user data breaches. Each type of attack has a unique scope and purpose against which retailers must protect themselves.
There is another reason why cybercriminals so frequently target retail and ecommerce organizations. Consumers who entrust their personal data to these organizations are used to receiving marketing messages from them. It’s much easier to defraud an email user who is used to reading a weekly newsletter from an ecommerce site than to impersonate the victims’ co-workers, friends, or family.
3. Government Institutions
It should come as no surprise that government institutions frequently find themselves targeted by cybercriminals. Email fraud attacks targeting government employees soared during 2018 and are unlikely to slow down any time soon.
For cybercriminals interested in sensitive data, there are few better options than government institutions. Government institutions have to collect sensitive data on citizens in order to function. The size and complexity of government mean that any government institution is likely to have multiple vulnerabilities to exploit – it’s simply not feasible to close them all.
Government and military institutions face additional challenges when securing their data against cybercrime. Instead of just facing ambitious, enterprising cybercriminals, they must also reliably protect themselves from state-sponsored espionage. Today’s spies don’t have to travel across the world like James Bond – they phish government email addresses and attempt to pilfer state secrets en masse.
Which Employees Get Targeted the Most?
Once cybersecurity teams understand hackers’ motives, they begin to see patterns in the types of individual accounts most frequently compromised. In order to establish a robust security system, they must improve the defenses of organizations’ most targeted employees.
According to the latest studies, IT and financial employees are the most common targets. In most cases, cybercriminals begin their attack by exploiting a general employee in one of these departments – typically choosing someone new and veering away from management-level employees.
Executives are the next most common targets. CEOs and CFOs make easy targets because there is usually a great deal of public information about them available online. If a cybercriminal manages to gain unauthorized access to a company’s IT system by compromising an entry-level employee account, compromising an executive-suite account is a logical next step. That’s where all the valuable data and financial information is.
Spear Phishing Disclaimer
Although the statistics above use the latest data available in the cybersecurity industry, email phishing is not simple enough to easily reduce into neat categories. All of the studies mentioned equate regular mass phishing and spear phishing – mostly because the two are difficult to distinguish from the victim’s point of view.
Mass phishing schemes simply attempt to scam the largest number of people possible. An example of this would be a cybercriminal sending off an email blast that spoofs a well-known ecommerce vendor like Paypal, attempting to get as many login credentials as possible.
Spear phishing requires research and a much more direct approach. A cybercriminal who poses as a particular employee of a particular vendor to trick a particular employee into giving up financial data is spear phishing. For the purpose of statistics, both are treated as phishing attempts, but the latter is obviously much harder to identify and protect against than the former.
In the pharmaceutical, retail, and government sectors, spear phishing is far more prevalent than in other industries. This is because successfully attacking a large-scale organization offers more value than attacking a small one. Essentially, it’s worth the cybercriminals’ time.
However, small retail businesses are disproportionately targeted because they often deal with large volumes of data yet don’t have the resources to successfully protect that data. This is why small retailers suffer greater email security risks than small businesses in many other industries.
Sources:
Phishing warning: If you work in this one industry you’re more likely to be a target
The Phishing Landscape
Phishing: Who Is Being Targeted By Phishers?
Phishing Attacks On The Retail Industry
The Latest in Phishing: October 2018
Protecting People: A Quarterly Analysis Of Highly Targeted Cyber Attacks
Latest Quarterly Threat Report – Q4 2018
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/phishing-protection/microsoft-office-365-a-phishing-attack-waiting-to-happen
Microsoft Office 365: A Phishing Attack Waiting to Happen

There are a lot of benefits to using Microsoft Office 365. It contains business tools with which you’re already familiar. It’s easy to set up and offers anytime, anywhere access.
You’ll see many of these features and benefits promoted on the Office 365 website. Won’t you want to see there among the list though is that using Office 365 makes you extremely vulnerable to a phishing attack. Why is that?
There are two factors that conspire to make Office 365 users vulnerable to a phishing attack. The first is Office 365 itself. It’s really popular, and that makes it a big, juicy target for hackers. The other factor is that the phishing protection native to Office 365 just isn’t good enough.
The recent Mimecast Email Security Risk Assessment (ESRA) aggregate report collected email data over two years specifically with Microsoft Office 365. What they found is that Office 365 “misses a variety of ‘bad’ emails.” Specifically, Office 365 let in more than 33,000 impersonation attacks, as well as unwanted, potentially dangerous or malicious file attachments.
These findings were confirmed in a new study by Recorded Future. According to the study, “Eight of the top 10 most exploited vulnerabilities in 2018 were Office bugs.”
“It should come as no surprise that cybercriminals favored Microsoft Office vulnerabilities in their cyber attacks last year, given the rise in phishing attacks that included rigged Word and Excel Office file attachments.”
Now, according to an article on Credit Union Times, there’s a new Office 365 exploit. Called a NoRelationship attack, it bypasses Office 365 email attachment security which scans Office documents like Word (.docx), Excel (.xlsx), and PowerPoint (.pptx). “The attack emails include a .docx attachment containing a malicious link that leads to a credential harvesting login page.”
If you’re using Office 365 and you think you’re security worries are over, they’re just beginning. When using Office 365, it’s best to assume that you have no phishing protection and act accordingly. Fortunately, it’s easy and inexpensive to add cloud-based email security to Office 365. It comes with real-time link click protection, so even if a malicious email gets into your Office 365 inbox, you’re still protected.
Don’t be lulled into a false sense of security. Add email security to Office 365 and make all what those hackers do a waste of time.
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/phishing-protection/theres-nothing-sexy-about-sextortion
There’s Nothing Sexy About Sextortion

There was a time when hackers and email scammers used spear phishing to trick their victims into sending money. By the time someone figured what had happened, the money was gone forever. But, people are starting to get wise to that tactic. So, what do the hackers do? They evolve…all the way to blackmail.
According to an article on security training firm KnowBe4’s website, the newest spear phishing threat encountered is one that threatens the victim with a new kind of blackmail called sextortion.
Sextortion is a form of sexual exploitation that employs non-physical forms of coercion to extort money or sexual favors from the victim.
In this case, the extortion is in the form of a threat to blame you for child pornography.
According to the article, the victim receives an email that “claims the CIA will bust you for child porn unless you pay 5,000 dollars and only then your records will be deleted.” The email also contains a malicious link.
The endgame for this type of blackmail is scary to imagine. It wouldn’t be difficult for the attackers to place actual child pornography on your computer or fill your search history with fake child pornography searches. Then they could anonymously notify the FBI or law enforcement which would cause a big headache for you.
In case you’re wondering how big of a problem sextortion is, an article on security website HelpNetSecurity confirmed that “Sextortion scams make up 10 percent of all spear-phishing attacks [and] continue to increase. Employees are twice as likely to be the target of blackmail than business email compromise.”
This is just one of the findings from a new report by Barracuda titled Spear Phishing: Top Threats and Trends. The report analyzed three major types of attacks: brand impersonation, business email compromise and blackmail.
Some of the findings in the report include the following:
The majority of subject lines on sextortion emails contain some form of security alert.
Attackers often include the victim’s email address or password in the subject line.
Scammers use name-spoofing techniques to make the email appear to come from a company employee.
Even though spear phishing attacks are evolving, the tactics and techniques employed to pull them off remain the same. And that means the technology required to defend yourself against them still work. What technology is that? Cloud-based email security with Advanced Threat Defense like that offered by DuoCircle.
If you want to ensure unwanted child pornography never ends up on your computer, head on over to our phishing protection services. You’ll be up and running in 10 minutes.
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/email-security/5-ways-you-protect-your-business-from-ransomware
5 Ways You Protect Your Business From Ransomware
Cybercrime is one of the most prevalent and growing threats that organizations face today. Malware, and particularly ransomware, can cost companies millions of dollars and heavily impact user confidence. When the city of Atlanta found itself victimized by a ransomware attack, it ended up signing eight emergency contracts – and spending a total of $2.6 million – to control the damage.
Cybersecurity experts use the term ‘malware’ to describe any unauthorized software designed with malicious intent.
Ransomware is a type of malware that encrypts victims’ systems and demands payment in exchange for a decryption key.
It’s easy to think that malware, ransomware, and reputation-damaging data breaches only happen to the world’s largest organizations. Cyberattacks against household names regularly make headlines, while smaller breaches don’t.
However, the majority of cyberattack victims are in fact small and mid-sized businesses. Cybercriminals find it much easier to successfully access small businesses’ IT systems because most small organizations don’t invest in sufficient phishing protection.
There are ways small and mid-sized organizations can protect themselves from cyberattacks with the same robust infrastructure that large enterprises enjoy. Many of the industry’s most successful cybersecurity solutions can be feasibly implemented in a wide variety of business formats.
How to Protect Your Business From Ransomware and Malware
For small and mid-sized businesses, the threat environment is both active and intense. Organizations have to account for more advanced threats than ever, all while managing increasing volumes of data and third-party services.
Cybersecurity experts routinely recommend performing the following five steps to keep users’ IT infrastructure safe. Most (though not all) cyberattacks occur because organizations overlook one of these steps.
1. Implement a Next-Generation Firewall
Every Internet user should be behind a firewall. These devices prevent unauthorized traffic and can play a pivotal role in stopping ransomware and malware from taking hold on user systems.
Most traditional firewalls work by inspecting and verifying the information that data packets offer about themselves. They usually don’t perform the time-consuming task of actually inspecting every data packets’ contents.
This would be akin to having the police set up a roadblock and verify every vehicle’s license plate as it passes through. Such a process might be enough to verify a car against a stolen vehicles registry, but it wouldn’t cut down on contraband smuggling or other illegal activities.
Next-generation firewalls can inspect the contents of individual data packets and compare them to known threat signatures. Cybersecurity vendors compile these threat signatures and update their databases on a regular basis. A powerful, modern firewall can catch and quarantine suspicious data that other systems may otherwise allow through.
2. Keep Your Systems Up-to-Date
System updates can be annoying and can introduce compatibility issues with certain software licenses. Despite these difficulties, they often patch important security holes and prevent cybercriminals from taking advantage of system vulnerabilities.
For example, the headline-making Petya attack exploited a Windows vulnerability that Microsoft had already fixed. The attack only affected victims who did not install Microsoft’s updates. Even after Petya, more than 50% of desktop users still do not update their system regularly.
Regardless of how annoying system updates can be, users must trust that their software vendors have their best interests in mind when releasing updates. This one step may be the single easiest way to improve protection against ransomware and malware.
3. Invest in Disaster Recovery Solutions
Even organizations with up-to-date security systems and well-trained employees may find themselves victimized by cybercriminals. In order for a security system to be truly robust, it must be multi-layered. This means that it must provide reasonable security even if its initial defenses don’t hold up.
Disaster recovery solutions play an important role in a multi-layered security environment. Being able to run an entire company off of a backup system reduces the potential damage of cyber criminals attacking the organization’s main systems.
Disaster recovery services like Datto can take much of the guesswork out of implementing this kind of solution. Instead of manually creating your own backups, a third-party service vendor can install the tools and systems you need – and then run them remotely.
4. Use a Virtual Private Network for Remote Access
Remote access is a key vulnerability for many organizations and users. Most businesses are happy to invest in high-quality on-site infrastructure that keeps their systems and users safe. However, this infrastructure does not help secure travelling employees or remote partners who wish to connect.
The best way to enable remote access to company infrastructure is by using virtual private network technology. Virtual private networks allow remote users to create secure “tunnels” to corporate systems from anywhere on the planet, potentially turning unsecured hotel lobbies into secure network access points for authorized users.
Successfully implementing a virtual private network requires using a next-generation firewall, as mentioned above. Most simple firewalls don’t know how to deal with VPN connections in a secure way. Your firewall must be able to securely identify the source of Internet traffic through the virtual network.
5. Use Real-Time Click Protection for Suspicious Email Links
Email phishing remains the number one attack vector cybercriminals use to gain unauthorized access to their victims’ systems. The vast majority of cyberattacks begin with email phishing, which allows cybercriminals to gain unauthorized access to email accounts. From there, they can begin compromising other aspects of the business with ease.
Business email compromise attacks have quadrupled since last year, and so have reported instances of cybercriminals using fake social media accounts to trick victims into phishing schemes.
Under these conditions, users must incorporate an additional line of defense in their email inboxes. Cybersecurity networks and data recovery services can only go so far on their own – it falls on individual users to verify the links they click on when receiving emails that appear to come from trustworthy sources.
Introducing Real-Time Click Protection
DuoCircle’s Real Time Click Protection allows users to protect their systems from convincing spoof emails and phishing attempts. As part of our Advanced Threat Defense suite of security tools, this solution verifies links at the moment users click on them.
Instead of instantly opening suspicious pages on users’ devices, DuoCircle opens links in a safe environment and scans them against multiple reputation databases to determine if the link is dangerous. It immediately warns users of unsafe links and quarantines any executables that they may have inadvertently triggered.
Sources:
Link Click Protection Prevents Email Phishing Attacks
What Is A Next Generation Firewall? Learn About The Differences Between Ngfw And Traditional Firewalls
The Latest in Phishing: First of 2019
VPN Beginner’s Guide
The world’s leading provider of MSP-delivered IT solutions
How Multi-Layer Security and Defense in Depth Can Protect Your Business
The Petya ransomware attack shows how many people still don’t install software updates
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/announcements/news-small-businesses-face-big-security-risks
[News] Small Businesses Face Big Security Risks

Why are small businesses at greater risk for phishing and hacking? It’s not because they make the juiciest targets. It’s because they make the easiest targets. Why is that? Because they don’t always have what it takes to defend themselves.
According to an article on SC Magazine, Smaller orgs struggle to get the security resources they need. “Small organizations often don’t have the resources to put toward cybersecurity – and the shortage of skilled talent makes their plight even more difficult,” Nathan Wenzler, senior director of cybersecurity at Moss Adams, told SC Media Executive Editor Teri Robinson.
Small companies frequently don’t have a dedicated security team because they can’t afford the large salaries to bring in skilled security officers. Yet, they have the same security threats.
As an example, a small healthcare facility called Columbia Surgical Specialists in Spokane, WA recently paid an almost $15,000 ransom to regain access to files encrypted during a ransomware attack. According to their newsletter, “[They] received notice from the people that encrypted the files just a few hours before several patients were scheduled for surgeries, and they made it clear we would not have access to patient information until we paid a fee.”
If that isn’t bad enough, Officials in Jackson County, Georgia, paid $400,000 to cyber-criminals this week to get rid of a ransomware infection and regain access to their IT systems.
Stories like this are why it’s imperative for small companies to find security solutions with the following two attributes: low cost and easy set up.
When it comes to phishing and hacking and ransomware, attackers don’t really care that you’re a small business. You still have to defend your company.
The good news for small businesses today is that almost every form of cybersecurity service is available as a SaaS (software-as-a-service) product. And that’s great for small businesses for two reasons. First, it eliminates the need for a high-salaried technical staff. There’s no hardware to buy or install. There’s no software to buy or configure. And in most cases, these security services can be deployed in as little as 10 minutes. Some services will even help companies set things up if they need the help.
The other reason SaaS security products are great for small businesses is because of their price. They’re super affordable. It’s not uncommon to find the entry levels of these service for less than fifty bucks a month. For that amount, Columbia Surgical Specialists could have purchased 27 years’ worth of protection for the ransom they paid!
Whether it’s phishing protection, spam filtering or email security, there’s an affordable SaaS solution for your small business. If you don’t know where to begin, head on over to DuoCircle and see what we have to keep your small business safe from security risks.
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/phishing-protection/why-phishing-is-a-bigger-threat-than-ever-in-2019
Why Phishing Is a Bigger Threat Than Ever in 2019
In the world of cybersecurity, it’s a well-known fact that 93% of data breaches trace their original attack vectors back to phishing. In the overwhelming majority of cases, hackers use phishing to get their foot in the door of the network they’re targeting.
Phishing is not new, nor are many of the broad strategies that cybercriminals use when phishing. However, the amount of data publicly available in today’s Internet environment brings a new level of tactical sophistication to the arena.
This is immediately apparent when surveying some of the highest profile cyberattacks in 2019. The wealth of public data available on almost anyone makes it easy for cybercriminals to conduct highly targeted phishing attacks. Additionally, the newfound ability to automate this information gathering allows bad actors to expand their operations with ease.
What We Can Learn From the Biggest Data Breaches in 2019
A quick survey of some of the biggest data breaches so far in 2019 shows that cybercriminals are getting bolder and more capable as time goes on. A veritable underground economy of black hat hackers, phishing specialists, and service providers are cooperating with an unprecedented degree of sophistication.
1. DiscountMugs.com
In the first week of January, DiscountMugs.com announced that it was successfully targeted by a professional hacking group called Magecart. The group gained access to the company’s payment processor application and skimmed credit card information from customers for four months.
Unlike many other e-commerce data breaches, hackers managed to get away with users’ full unencrypted credit card information – everything they would need to make illicit purchases using the victims’ identities.
Magecart hackers are smart enough to know that using victims’ information would tip their hand. Instead, they sell victims’ credit card information anonymously on the dark web, effectively obscuring their tracks.
2. BenefitMall
On January 7th, BenefitMall announced that it had been victimized by a data breach originating with a phishing attack that compromised an employee account. The payroll and HR service provider hasn’t revealed exactly how many records were compromised. The breach made customer names, addresses, social security numbers, birthdates, and bank account information available to hackers.
This example illustrates how dangerous a single employee’s mistake can be. Because BenefitMall is a payroll processor, hackers knew it was virtually guaranteed that sensitive customer data would be present in any employee’s email inbox.
If the company had been less prepared, a single compromised email account could easily have led to the entire company being compromised. An ambitious cybercriminal could take control of an executive account or pilfer company funds before turning on BenefitMall’s customers and partners.
3. Catawba Valley Medical Center
Approximately 20,000 patients of the Catawba Valley Medical Center in North Carolina have had their personal data exposed in a sophisticated cyberattack announced in February 2019. Hackers successfully phished three employee email accounts during the summer of 2018 and obtained the names, birthdates, social security numbers, and health records of the medical center’s patients.
This attack illustrates one of the cybercriminal industries’ highest priority targets – healthcare providers. Even providers who are compliant with HIPAA regulation can be targeted. In the case of the Catawba Valley Medical Center, the clinic had never been out of compliance with HIPAA regulation.
4. UConn Health
UConn Health recently announced that roughly 326,000 patient records were accessed by unauthorized parties at the end of 2018. The health system provider’s email accounts were compromised by phishing attacks that leaked patient names, birthdates, social security numbers, and medical data.
Healthcare providers like UConn Health are obliged to notify the U.S. Department of Health and Human Services whenever a breach affecting more than 500 people takes place. In this case, the company announced the breach and immediately offered free identity theft protection services to the patients whose social security information was compromised.
5. St. Francis Health System
One of the largest healthcare-related data breaches of 2019 to date targeted electronic health records systems partnered with St. Francis Physicians Systems. Cybercriminals targeted health record systems with public-facing portals and phished employee email accounts to gain access to patient names, addresses, birthdates, insurance information, social security numbers, and medical data.
The attack compromised 32,178 individual patient records. The clinic announced the data breach in March 2019. In this case, cybercriminals only gained access to the accounts of patients who had previously received medical services from Milestone Family Medicine, a third-party partner of St. Francis Physician Systems.
This attack showcases how compromised email accounts can allow cybercriminals to move laterally through organizations and their partners. Just like the high-profile Target hack of 2013, third-party partners often represent the easiest attack vector for cybercriminal phishing attempts.
Phishing Trends to Watch Out for in 2019
There is a clear pattern in 2019’s biggest data breaches. Cybercriminals have placed relatively small organizations – especially in the field of healthcare and e-commerce – squarely in their sights. The more sensitive information an organization is likely to have access to, the greater its risk of being targeted.
This explains why healthcare organizations are currently the most common targets of email phishing attempts. The Department of Health and Human Services maintains a publicly available “Wall of Shame” describing the very latest data breaches in the healthcare sector.
However, smaller organizations in e-commerce and finance are also being targeted. There is a clear tendency towards targeting small to mid-sized businesses that rely on third-party professional services. These organizations represent the largest and most accessible surface area for cyberattack and often do not invest in multi-layered security solutions appropriate to the threat.
Sources:
Tales of dirty deeds and unscrupulous activities.
2019 Data Breaches – The Worst Breaches, So Far
Breach Portal: Notice to the Secretary of HHS Breach of Unsecured Protected Health Information
St. Francis Physicians Services Notifies Patients of Milestone Family Medicine Data Breach
UConn Health email breach compromises data from 326,000 patients
Catawba Valley Medical Center Suffers HIPAA Email Breach
Infiltrating the Target network
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/announcements/news-if-cybersecurity-professionals-can-get-phished
[News] If Cybersecurity Professionals Can Get Phished

Defense Contractors Get Taken in by Business Email Compromise
Business email compromise (BEC) is a form of email fraud that typically involves targeting employees with access to company finances and using social engineering to trick them into making money transfers to the bank accounts of the fraudster. According to an article on security website Cyberscoop, scammers used BEC to steal more than $150,000 from two defense contractors last year.
“Business impersonation fraud is trending because it works,” said Alexander Heid, chief security officer at SecurityScorecard, which builds risk profiles on companies based on publicly accessible information. “With 1,000 target enterprises, if only 1 percent fall for the scam, that is still ten places wiring over large sums of money – and that adds up very fast.”
What makes this shocking is that defense contractors are the same companies making millions of dollars a year providing, you guessed it, cybersecurity services to government agencies and large corporations. In other words, they’re companies who should know better. It’s not surprising then that the names of the defense contractors were omitted from the article. I suppose that wouldn’t look very good, but it does prove a point. Social engineering is very hard for people to combat because, well, they’re human.
The only consistent way to combat social engineering is with technology that doesn’t fall prey to social engineering tactics.
Pros Fear Phishing Attacks
Given that even defense contractors can be taken in by phishing scams, it should come as no surprise that Very Few Professionals are Confident in Their Phishing Defense Assessments. According to research done by the IT governance organization ISACA and Terranova Security, “just 12% of security, assurance, risk and governance professionals are confident in their ability to assess the effectiveness of their phishing defenses. Additionally, only 57% of those surveyed said they carry out phishing simulations within their organizations.”
The untold story here is the reason the pros are worried is because they think the solution is to carry out more and more phishing simulation attacks. The misguided belief that if only they could somehow train their employees better, then the phishing problem would go away. But research proves that just isn’t true.
Research done on the efficacy of phishing simulation found that “with increased education and 10 or more phishing simulation campaigns, that rate could be reduced by a third from 14.2% [to 9.4%.]” Even with all the education and simulations in the world, 10% of employees are going to click on a malicious link. It’s not their fault—they’re only human. And of course, it only takes one click to infect an entire network.
I find it hard to believe that the pros don’t know there are inexpensive, easy-to-deploy, cloud-based email security solutions that can almost make phishing awareness training unnecessary. Where is the research showing before and after results of deploying this readily available technology? Nowhere.
Until the paradigm shifts the onus of email security away from users and onto technology, we’ll continue to see what we’re seeing today: companies getting phished and pros losing sleep.
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/announcements/duocircle-sponsoring-open-certificate-authority-lets-encrypt-for-a-second-year
DuoCircle Sponsoring Open Certificate Authority Let’s Encrypt for a Second Year

Duocircle, a web-based email security solutions company, has chosen to sponsor Let’s Encrypt for the second year in a row. Let’s Encrypt is a service provided by the non-profit Internet Security Research Group. Let’s Encrypt gives people free digital certificates because they want to create a more secure and privacy-respecting web.
San Diego, CA – March 22, 2019 – DuoCircle is an integrated, cloud-based email security solutions company. DuoCircle is sponsoring Let’s Encrypt for the second year in a row.
Let’s Encrypt is a free, automated and open certificate authority (CA), run for the public’s benefit. It’s a service provided by the Internet Security Research Group (ISRG). Let’s Encrypt provides the digital certificates domains need in order to enable HTTPS (SSL/TLS) for their websites, for free. They do so because they want to create a more secure and privacy-respecting web.
DuoCircle is sponsoring Let’s Encrypt for a second year because the company prioritizes privacy and understands the need for encryption on the web. “We are passionate advocates for free speech and the need to make encrypted connections ubiquitous online,” said Brad Slavin, CEO of DuoCircle. ISRG, which provides Let’s Encrypt, is a non-profit organization. As such, it relies on sponsorships like those from DuoCircle to be able to offer its service for free. “It’s nice to be in the same category as world class organizations like Cisco, Facebook and Google in sponsoring such an important organization as Let’s Encrypt,” said Mr. Slavin.
Email is still the number one threat vector for malware, ransomware and business email compromise. Today’s most pressing cybersecurity challenge is reliably and accurately detecting and blocking threatening emails before they can do damage.
Forging an email is surprisingly easy. Today’s cybercriminals have no problem forging emails from reputable, well-known companies or even from executives within the corporations they seek to attack. This makes it difficult for employees to determine which emails to trust. Only a comprehensive threat detection system, that can determine the origin servers of incoming emails, can reliably verify incoming messages. Let’s Encrypt’s SSL certificates are a key component in offering this protection.
DuoCircle is not a web hosting company which benefits directly from issuing SSL certificates. However, in the enterprise IT environment, the risk of phishing and domain name forgery is high.
DuoCircle combines Let’s Encrypt certificates with their Advanced Threat Defense technology. When combined with Advanced Threat Defense, it gives users an immediate way to reliably verify safe emails. “We specifically engineered our Advanced Threat Defense system, for malware and Phish Protection, to utilize Let’s Encrypt SSL certificates for our client domains,” said Mr. Slavin.
###
About DuoCircle:
DuoCircle is a provider of inbound and outbound email security solutions including Advanced Threat Defense, phish protection, spam filtering, outbound email filtering and Smart Quarantine. Headquartered in San Diego, California, DuoCircle protects over 25,000 businesses and millions of mailboxes worldwide with business-critical messaging for complex environments. To learn more about DuoCircle’s services, visit duocircle.com
About Internet Security Research Group:
Internet Security Research Group (ISRG) is a nonprofit organization whose mission is to reduce financial, technological, and education barriers to secure communications over the Internet. Its primary project is Let’s Encrypt, a free, open and automated Certificate Authority that provides TLS/SSL certificates to over 150 million websites. Learn more at https://www.abetterinternet.org/.
Contact DuoCircle:
DuoCircle Press
+1-855-700-1386
[email protected]
https://www.duocircle.com
Contact ISRG:
[email protected]
https://www.abetterinternet.org/
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/phishing-protection/news-how-phishing-protection-can-lower-your-utility-bill
[News] How Phishing Protection can Lower Your Utility Bill

When Good Websites Turn Bad
The whole idea behind phishing awareness training is to keep you off of malicious websites. But what if the web site you want to visit, a known good website, is actually malicious? It’s more likely than you may think.
According to the Webroot 2019 Threat Report “A whopping 40 percent of malicious URLs were found on good domains. Legitimate websites are frequently compromised to host malicious content.”
You can do everything right. You can be on the lookout for misleading links in your emails. You can be trained to spot fake websites meant to scam you. And yet, you can still be had. Not because you did anything wrong, because the websites you visit and trust got compromised.
This is just one more reason why phishing awareness training alone won’t protect you from being phished. If you want to fully protect yourself, you need phishing prevention technology.
It’s Tax Season and That Can Only Mean One Thing
Phishing emails that use tax-related content to get you to let your guard down.
According to an article on security website DARKReading, “A new wave of phishing attacks aims to dupe users and steal their passwords by disguising malicious emails as tax-related notifications from the IRS. This threat lures victims with Microsoft 365 Office files claiming to be tax forms or other official documents; attackers use urgent language to convince people to open the attachment.”
The article further points out that attackers purposely use common file types like Word and Excel to put victims at ease. “Examples of this tactic include files named taxletter.doc.”
One of the more interesting items highlighted in the article is that signature-based protection systems won’t catch these emails because the attackers constantly change all the email information and “changing the characteristics of malicious emails changes their fingerprint.”
The best protection against any email with a malicious attachment is to employ a service which scans all attachments and quarantines the offending ones so there’s no chance you actually open it. No matter who claims to have sent it.
How Phishing Prevention Technology can Help Keep Your Utility Bill Down
It’s the latest craze in phishing attacks and it’s called cryptojacking. What is cryptojacking? It’s the secret use of your computer to mine cryptocurrency.
If you don’t already know it, cryptocurrencies like Bitcoin get “mined” by using a lot of computing power. The coins get mined by taxing the CPU on a computer. And stressing a CPU takes electricity—lots of it.
The miners increase their chances of mining a Bitcoin by getting as many computers as possible working in parallel. And that’s where your computer and cryptojacking come in. The attackers want to use your computer (and your electricity) to help them mine their Bitcoins.
According to an article on GlobalSign, “The techniques used to do this [cryptojacking] resemble those used in phishing attacks. A common method, for instance, is to send users a legitimate-looking email encouraging them to click a link. If a user does so, a crypto mining script is loaded onto their computer, and runs silently in the background whenever that machine is on.”
They’re no longer trying to steal your credentials or hold your computer ransom. Now, they just want to use your computer’s CPU to help them make a little money. And it can be really difficult to tell you’ve been cryptojacked once the malware is installed because it runs in the background. The only clue that you’ve been cryptojacked is slightly slower computer performance (and a slightly higher utility bill).
The good news is the cryptojacking attacks use the very same techniques as other phishing attacks. So, if you’re prepared to defend yourself against phishing attacks, you shouldn’t have to worry about encountering a shocking electrical bill. If you’re not prepared to defend yourself against phishing attacks, head on over to Phishing Protection. You’ll be up and running in 10 minutes for less than the hit to your utility bill.
0 notes
Text
New Post has been published on...
New Post has been published on https://www.duocircle.com/phishing-protection/social-engineering-is-a-growing-threat
Social Engineering Is a Growing Threat
The best cybercriminals tend to be innovative and intelligent. They constantly update their strategies and tactics to account for new developments in the cybersecurity landscape and always manage to find new vulnerabilities to exploit.
For small and mid-sized organizations, the cybercriminal threat will never go away completely.
As long as there is valuable data to be illicitly gained and used, enterprising criminals will try to get their hands on it.
Technology is constantly advancing, and with it, new cybersecurity paradigms come alongside new vulnerabilities. In 2018, 83% of security professionals reported experiencing phishing attacks, up 7% from the previous year. Reports of business email compromises have soared by a factor of 70% over the same time frame.
Phishing has long been the preferred attack vector for cybercriminals. However, many are now deploying phishing strategies that rely on far more effective tactics: social engineering.
What Is Social Engineering?
Social engineering refers to a variety of tactics that people (not just cybercriminals) use to influence behavior using psychological manipulation. It leverages biases and well-known deceptive fallacies to take advantage of people in order to achieve a goal.
Social engineering tends to carry a negative connotation due to its association with deception, hacking, and cybercrime. The academic flip-side to social engineering is behavioral economics, the study of decision-making by irrational actors in inconsistent systems.
Whenever cybercriminals exploit the human element as part of a cyberattack, they are engaging in social engineering. This can mean anything from impersonating an employee on the phone to posing as a delivery driver and tailgating an employee inside an access-controlled area.
Cybercriminals have realized that these old-school spy movie tricks actually work. They work on the phone, they work on email, and they work in person.
There are a few reasons why these tactics work and why they are becoming more prevalent throughout the cybersecurity world:
Personal Data Is Easy to Find. Impersonating a close friend or relative is much easier now than it was 20 years ago. Most people prominently display their relationships on social media, along with a broad variety of other information about them.
Data Is Machine-Readable. Web crawlers can interpret your social media data and extract useful information for cybercriminals in a fraction of a second. Social engineering is not nearly as time-consuming as it used to be.
New Skills Are in Demand. In the past, cybercriminals were almost exclusively IT experts. Now, a new class of cybercriminal with competency in psychology and marketing is emerging, leading to new kinds of exploits that don’t focus exclusively on technology.
Technology Can Now Be Outsourced. Ransomware-as-a-service and similar dark web solutions make it easy for non-technical cybercriminals to deliver innovative attacks. The traditional Hollywood depiction of a caffeine-fueled cyberpunk computer hacker is no longer applicable to most cybercriminals.
What Can Small and Mid-sized Organizations Do?
Protecting against social engineering is notably more complex than protecting against an IT-based hack.
Human behavior is not reducible to a logical sequence of 1s and 0s the way business applications are, which means there is always room for an unexpected, innovative attack.
Since organizations can’t reasonably enforce phishing prevention rules that rely on controlling employees’ personal lives, they can’t prevent their employees from posting personal information on social media. The best they can do is educate their workforce about the threat of social engineering and implement solutions designed to mitigate the most serious risks.
Large enterprises and governments typically implement multi-layered approaches. These are sophisticated security strategies that successfully quarantine compromised systems and limit the damage that cybercriminals can potentially incur.
Small and mid-sized businesses have long been priced out of these kinds of security approaches. But new services like DuoCircle’s real-time Phish Protection and Advanced Threat Defense level the playing field between the world’s largest, most powerful organizations and the small businesses that cybercriminals disproportionately target.
Small businesses simply cannot afford to implement their own custom-coded application suites, so they have to use hosted solutions like Office 365 and similar products. Securing this kind of business architecture requires an appropriately scaled multi-layered security system, which includes:
Consistent Training. Training is a major part of any security strategy. However, it can’t do all the work for you. Employees need to understand the threat that social engineering poses and have access to tools and solutions for mitigating those threats.
A Next-Generation Firewall. Next-generation firewall products are inexpensive, yet several orders of magnitude more effective than run-of-the-mill firewalls. They play a critical role in preventing malicious code from executing once inside your network.
Virtual Private Networking. If your organization relies on remote or traveling employees, it must incorporate a system for extending security benefits to users outside the office using virtual private networking.
Email Security. Email phishing remains the most common attack vector that cybercriminals use to gain illicit access to company systems. Implement real-time phishing protection to prevent employees from accidentally downloading malicious software.
Domain Name Spoofing Protection. One popular social engineering tactic is impersonating trusted websites by spoofing their domain names. Even a cybersecurity expert could not tell the difference between an IDN homograph attack and the website it copies at first glance. Businesses need to deploy automated solutions for testing websites.
Phishing Prevention Best Practices: Choose Real-Time Solutions
Most phishing domains and spoof websites are only live and active for less than 36 hours. For cybercriminals, that is plenty of time to send out a highly automated, highly targeted attack and begin collecting victims’ user data. For cybersecurity professionals, it’s an extremely short window of time to catch them in the act.
In order for your organization’s multi-layered security framework to be effective against social engineering tactics, it has to offer real-time results. The clock is on from the second an employee clicks on a malicious link. If you can respond in time, you can quarantine the system and mitigate the risk effectively.
Any truly comprehensive multi-layered security system for use in today’s IT environment has to be a real-time system that protects users from innovative social engineering tactics. It must protect against email phishing and verify incoming downloads while being able to warn security professionals of suspicious events the moment it notices them.
Sources:
The Latest in Phishing: First of 2019
Nudges: Social Engineering or Sensible Policy?
How Multi-Layer Security and Defense in Depth Can Protect Your Business
Phishing Protection Service with Advanced Threat Defense – DuoCircle
Out of character: Homograph attacks explained
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/phishing-protection/phishing-in-the-news
Phishing in the News
If You Think Phishing Is Only Your Employer’s Problem Think Again
If you work for a company, you probably think about phishing attacks in a distant sort of way. In other words, phishing may be a problem, but it’s not your problem, really. It’s your employers’. Right? Wrong.
According to a recent article on the Phishing education website KnowBe4, an employer in the UK sued an employee for $250K for falling victim to a phishing scam. According to the article, “Patricia Reilly, who was working for the UK Peebles Media Group fell for a CEO Fraud Scam where the criminals sent her emails pretending Mrs. Reilly’s boss.”
She’s being sued because she should have known better. The remarkable thing is the company didn’t provide her any training on how to spot online fraud. Maybe Mrs. Reilly ought to countersue her former company for lack of proper training. Or maybe she’ll countersue them for not using inexpensive and readily-available technology to keep the darn phishing email out of her inbox in the first place.
Now Just Booking a Vacation Can Get You Hacked
If you fly, then you know that airlines send check-in links by email 24 hours before your flight. What you might not know is that some airlines send links that initiate a connection over HTTP instead of HTTPS. And that puts you at risk for being hacked.
According to an article on security news website Security Week, “check-in links sent to customers by several major airlines from around the world can allow hackers to obtain passengers’ personal information and possibly make changes to their booking.” The airlines found to have been doing this by security firm Wandera include Southwest in the US and KLM in the Netherlands.
According to Wandera VP of Product Michael Covington, the link itself includes a record locator, the origin of the flight and its destination, and, in some cases, the passenger’s name. Theoretically an attacker could intercept a user’s traffic and leverage these credentials to gain access to the targeted user’s online check-in page.
Once at the check-in page, the attacker might have access to other, more personal data, such as
email address,
name, gender,
passport information,
nationality,
phone number,
partial payment card information,
booking reference,
flight details (flight number, seating data), and
even the complete boarding pass.
It may even be possible in some cases for the attacker to make changes to the data provided and print the victim’s boarding pass.
Sill think you don’t need advanced phishing prevention technology?
Looking for a Hobby? How about Phishing.
Would you be surprised to learn that phishing has been around since 1996? That’s like year 2 AD in internet time. You’d think after almost a quarter of century phishing would be gone by now. In fact, just the opposite has happened.
In case you’re wonder why phishing rates continue to rise, check out this list of resources for the aspiring attacker:
Expert assistance:
Incredibly, there are actually places on the internet novices can go to learn how to phish someone. They can purchase step-by-step tutorials and templates to conduct their own phishing campaigns.
Spoofing:
Just like there is for phishing, there are resources on spoofing techniques. They include everything from how to create, compromise or find a SMTP server from which to send the spoofed emails, to how to prevent emails from ending up in spam folders or the hosting IP from ending up on blacklists.
Cloning websites:
For aspiring phishers, a website cloning or mirroring service known as XDAN CopySite makes it easy. All you need to do is enter the domain of the website they want to clone, and within seconds they have a static version of the site – enough to be convincing at first glance.
When someone tells you to try phishing for a hobby, go out and get yourself a rod and reel.
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/email-hosting/amazon-order-confirmation-trojan
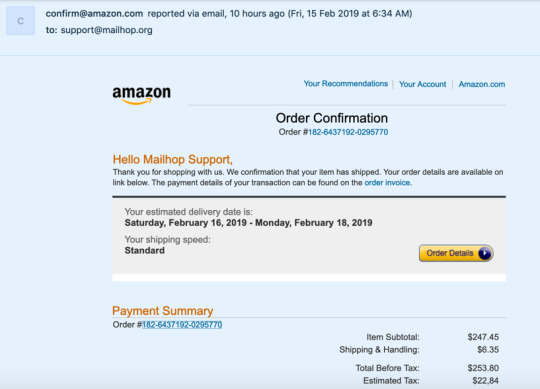
Amazon Order Confirmation Trojan

vimeo
Today we received an email to our Freshdesk support tool that that was an Amazon.com confirmation messages that contained download links to an infected Microsoft Word document.
In our office message routing configuration, all emails first flow through our Google Apps account to be spam filtered first and then delivered to our help desk software.
This is a quick video of me reviewing the message and discussing just how easy it is to be mislead by a very well crafted email messages.
0 notes
Text
New Post has been published on...

New Post has been published on https://www.duocircle.com/email-archiving/10-reasons-why-your-business-needs-a-hosted-email-archiving-solution
10 Reasons Why Your Business Needs a Hosted Email Archiving Solution
There are 3.8 billion email accounts worldwide, and 281 billion emails were sent per day in 2018. Chances are, your business has contributed a bit to that number.
After a while, the accumulated emails can get unruly, not to mention become problematic as well. To solve those problems, you should consider email archiving.
Here are 10 reasons why a hosted email archiving solution can benefit your business.
1. Better inbox management
When it comes to email, you (and your employees) may be guilty of hoarding. You never know when you’ll need that piece of information again, after all. This leads to an unsightly, cluttered inbox where nothing can be found.
By implementing mail archive software, you can finally let go of those years-old emails. They’ll go safely to rest in the archives, where you can conjure them up again should you need them.
2. Speed up your mail server
This reason goes hand-in-hand with reason #1. When everyone’s inbox is crammed with emails, it can put a strain on your mail server. The more emails there are, the slower it’ll get, to the point where it’s unworkable.
Enterprise email archiving enables everyone in your organization to clear out their inboxes and put currently irrelevant emails into the archives. This relieves the stress on your mail server and lets it work at the speed it should.
3. Excellent email recovery
How many times have you accidentally deleted the email, tried to recover it, but found it was lost in the void? This can be a fatal mistake when dealing with important clients.
You can ward off such blunders with email archiving. Anything deleted is saved in your email archiving software, which means you can recover them at any time. Any accidental deletions in your organization can then be quickly rectified.
4. Get backup of other data
Although the name sounds like they only save emails, email archiving solutions actually do so much more. Any information that could be associated with emails, such as agenda events, contact information, and more, is also archived.
5. Manage work and client information better
Much of the communication done between you, your employees, and clients are through email. Have you ever remembered that an essential piece of information was in an email chain, but couldn’t put your finger on which one it was?
It can quickly become frustrating opening hundreds of emails to find the pertinent information, only to turn up with nothing. Plus, it’s a massive waste of time. Your emails will not only be safe and sound in an email archiving solution, but it’ll also be easy to search through for precisely what you need.
6. Increase productivity
Again, when email is the primary form of communication, it can be time-consuming trying to retrieve pieces of pertinent information from your inbox. Categorizing emails can cut down on time wasted sorting through emails.
Email archiving software usually has general and granular auto-tagging features.
By streamlining email categorization with tagging, you’ll see increased productivity in your employees.
7. Relieve stress on your IT department
Your IT department should use its skills and talents on more complicated matters. But often, they get bogged down in managing your mail server, especially storage issues. When this happens, more important IT issues can fall to the wayside.
Help your IT team by implementing mail archiving solutions. This can help them focus on priorities better and keep your enterprise running smoothly.
8. Keep good records
You can do your best to run your company as well as you can, but litigations and other legal issues still may arise. Without proper records, it may be hard to defend yourself in court, leading to a lost case.
But with enterprise email archiving, you have a fighting chance. You’ll have email records dating back to years before, making e-discovery simple to carry out. Not only that but with the archiving technology, you can accumulate the relevant emails quickly without having to sift through them yourself.
9. Protect trade secrets
With cybercriminals always at large, it’s vital to take precautions in protecting your intellectual property. Any leaks and it could spell doom for your business.
When you utilize email archiving software, you’ll get added layers of protection. Should any scammers get past your initial defenses, any intellectual property in emails will be locked away in the software, out of their reach.
10. Comply with data laws
The most important item on this list:
Compliance.
Regulations for data compliance say that you must store all your data on a long-term basis. You can’t just delete it when it’s no longer relevant.
By using an email archiving solution, you’ll not only reap the benefits of the above nine points, but you’ll also ensure that your business is compliant with data laws.
0 notes