Text
Week 9 Lecture
Since I’ve basically written all my notes on tumblr, I’m gonna keep doing so:
What it means to be engineer:
- Focus on Processes (Logging and documentation)
- Testing
- Reviewing is different from testing as reviewing isn’t only done with testing. Review your code.
- Proffessionalism where we have a duty to security engineering
- Measure everything you can.
Not everything that can be measured is worth measuring.
Concept: Closing the Loop
When you actually check if your idea is right. Art of being an engineer is the art of closing the loop.
Aviation Safety Conference: Safety inspector working on oil rig and audits site. Talks about an accident where 350 alarms went off.
Rather than being reactive to the threats that occur, we need to focus on the system. Similar to being a barbarian.
System properties - Maybe the system is at fault where the working conditions result in errors occuring.
Coherence is vital in system properties.
The main reason why humans can never be closed off the loop from processes because a system can’t resolve every scenario.
Voting system is a single point of failure, technology is not properly tested and since it’s only done once every year.
Security is an End to End propety where it has to be secure all the way across.
Work to undermine limits- Romans and the Greek government tries to remove the limits that were imposed onto the system. When an individual gets into power, it starts to dismantle the power. The system must be strong enough to withstand such dismantling and must be designed to last.
Ruler of the Galaxy- If anyone wants to be the ruler off the galaxy, they can’t be the ruler of the galaxy.
Assange and Free speech-
Cars and trolly cars - We have systemic failure and thus nobody can be safe. Also addresses End to End system.
Trust with third party- Simpson episode where Homer always suggests to live under the sea as a solution.
Everything about security is about trust. Insider threats are as big as external threat or maybe even bigger.
Communication-
We are all going to communicate, without communication there’s no change. Global warming debate is a result of poor communication.
The secret to communication - Communication between individuals is about the delivery of the message towards the receiver and how the receiver perceives.
Gun license book.
New phones have a thing called face sucked in which sucks in data in the environment and send the information off.
We are all Cyborgs - Physical structure of the home is memorised. Hence the house is like an external memory.
COMP6841 Presentation:
Reverse Engineering is to disassemble malwares.
Reverse Engineering - CTF -> fun
Profit - Bug Bounties, Corporate Espionage
Malware Analysis
Interoperability - Extend the function you own
Security Audit Closed Source Software?
How to Reverse Engineer:
- Static- Read the disassembled decompiled code to determine purpose
Safe to use since it is more offline.
Using GDB is an example of Static.
Understanding x86
Generally just used to understand registers
System calls - black box
Function calls
Branching - if statements
Just read mnemonic and guess
Use regerence manual
Google
- Dynamic
Story Time-
Farmers are hacking their own tractors. In places like Ukraine and Eastern Europe the software is sold to farmers without the encryption they have in other countries like the United States
Stack
-Ainti reverse engineering abilities: Anti Re: Don’t release debug build
Remove symboles from the binary
Dump symbols
Disable asserts
0 notes
Text
MidSem Reflection
I realised that I did not make a Mid Semester Exam reflection yet. I was waiting to receive my results before making any comments about my work but I’m now making this a few weeks after the results were released.
So I performed fairly poorly in my exam. I was expecting to hopefully get a result that shows that I’m keeping up with the class but I was very unprepared for the type of exam that was given. I didn’t have enough time to look through the Exam Skeleton as I also had a major task due before the exam and wasn’t too worried about preparing extensively because the midsem replacement exists.
The questions that I encountered that I most likely got wrong were:
Houdini Case Study Application - I didn’t go to the first week’s lecture and hence the CIA term was very vague to me. However I now think the answer is Authentication and Integrity.
The lockpicking question I kept switching my answer between shimming and bumping. I put bumping at first because you were suppose to bump the pins with key but I didn’t know if it was the back side of the key or if it was something else. I also didn’t know if the key was being used to rake it or bump it and since it’s not the backside of the key, it wasn’t raking. Genuinely don’t know why I changed it to shimming. I guess the pressure kind of chipped away from my logic.
Anyways, I will be preparing extensively for the finals and make up my marks in the midsem replacement sections. Wish me luck!!!
2 notes
·
View notes
Text
Week 8 - Authentication
I absolutely love Mr Robot and this module discusses about methods in which we can attack and access Barbara’s account in E-CORP.
https://developer.okta.com/blog/2017/06/21/what-the-heck-is-oauth
OAUTH is an open standard for authorisation where it provide client applications with “secured delegated access”. It utilises Access Tokens rather than credentials for all HTTPS, API, server, and applications.
OAUTH replaces the basic credential authentication where HTTP would just request for your credentials with a pop up. OAUTH allows third party access to their server resources without sharing their credentials and can be applied to multiple applications. This would mean that only one login credential is required to access all applications given by the server and host.
For Barbara, since one login is all you need to compromise her entire account, you can brute force her 10 generated password or social engineer for both her password and 2 authentication factor and thus you are in. With social engineering, you could pretend to be IT help desk and perform remote control access to get into her network and “pretend” to log out but in reality, also access the same session and compromise her account.
0 notes
Text
Week 8 - Spot the Fake
When purchasing games on game clients like Steam or even on any website that requires you to provide your age, many children can easily fake their age. For example, on Steam, for games that are age restricted, Steam would display a page which would request you for you to provide your age. If you were to put that you were under a specific age, it would refuse to give you entry. However, you could easily just refresh the page and change your age to be above the age requirement and thus you could view and download the game. There is no way to determine your age online as it would be too much of a hassle to ask users to provide documentation as this would more likely put users off and hence not register on their websites.
0 notes
Text
Challenger Disaster
The Challenger Disaster took place in January 28th 1986 in which the Challenger shuttle ship within 73 seconds of it’s take off, blew up, killing all crew members on board.
The Challenger was riddled with problems even before the day of take off where there were multiple delays due to problems with weather or exterior hatches. As space shuttles can only be launched in orbit in specific windows due to the rotation of the Earth in order to utilise the momentum of the orbit and save fuel, the delays may have caused a hasty launch.
This was evident as on the night before the launch, the temperature dropped and caused ice to form on the launch pad. However, a few hours before the launch, it was evident that the ice was melting and hence was cleared for launch.
After the initial launch of the space shuttle, it was observed that gas was leaking into the O-Ring of the space shuttle, causing large plumes of smoke to be expulsed out. This was further affected by a tremendous windshear that essentially helped disassemble the entire space shuttle and thus caused the cockpit to detach from the spaceship. There were no safety mechanisms in place in case the cockpit detached as NASA deemed as “High Reliability” and the shuttle itself was experimental by nature.
0 notes
Text
Week 8 Tutorial Reflection
So this weeks case study was called Ghost and was based on a scenario from a TV Show called Stargate. This case study discusses the idea of man in the middle attack where we have three subjects: the major, the invisible man and the alien; the invisible man is a cadet who was tasked in travelling through a portal gate that leads to an alternate dimension. However, after he returned from the Portal, he became invisible and also an alien followed through the portal gate with him. Thus the major has to find a way to retrieve the report from the invisible man through the alien. The two questions that we were given were:
1. Is the alien trust worthy
2. What information is considered urgent in this situation.
The aim is to find out about the life on the other side of the portal gate and whether or not it is “safe” on the otherside.
For the first question, we were unsure in determining how to trust the alien as we are not sure whether the alien is friendly or not. Thus we made the assumption that the alien cannot be trusted. This also posed the question on whether or not the Invisible man can be trusted and whether he is compromised. Therefore the conclusion for the first question was that the alien and the invisible man can’t be trusted too.
For the second question, we determined that certain questions like whether or not there is sentient life and if aliens are hostile. However, there were no effective ways to communicate that without having the message intercepted. Hence we couldn’t establish a solution to that issue. We had an idea where we could try to say things that only the humans would understand but if the aliens had an understanding of our history, they would also intercept the message too.
I felt like for this case study, I was less assertive with my ideasa, mainly because I was struggling to understand what the case study was asking out of me and what parts of the lecture content it was referencing to. I was also really tired due to coming off a coffee high and hence had a hard time trying to concentrate. However, I managed to still contribute to the tutorial by saying that we can’t trust the invisible man as well and also suggested that if we can authenticate the invisible man, then that’s more important than determining if the alien is hostile.
0 notes
Text
Feedback to Blogging on Tumblr , Security Everywhere on Twitter and Everything else.
So, I just wanted to provide a quick feedback to my experience on Tumblr and twitter.
I was extremely fustrated with Tumblr due to the fact that Tumblr from time to time, would “crash” where if you tried to post your blogs, it would sometime not post at all and get stuck on a sending page. This has impacted my work multiple of times where I would be writing a blog post for 3 hours and when I tried to upload my blog post, it would not upload and once I had to do it all over again because I forgot to backup my blog post on a word document. I understand that it would be my responsibility to make sure that despite Tumblr’s issues, I would always have a back up in case. However, when I’m doing CTF challenges or doing my Something Awesome project, I would keep my Tumblr blog open to constantly update it with new information everytime I made progress. Regardless, I now have worked around it but it was something that concerned me alot especially in the beginning of the term.
I also don’t like how Twitter has a word limit for each tweet you make. It meant that I would not be able to explain my Security Everywhere in depth and can only make a brief statement about it. I have worked around this by making a blog post that addressed the context of the Security Everywhere tweets but still would rather have another system to do this. Perhaps, Security Everywhere would be placed in a separate blog?
I also want to say thanks to Hayden to being a fabulous tutor. There really isn’t much feedback I can provide to him other than that he’s great and I hope the best for him.
If I had to be nit picky, I would like the course to perhaps release the slides that Richard uses in each of his lecture as it contains the weekly tasks that we have to do. This would also allow me to do some extra research at home on things that we’ve talked about and allow me to review things that I may have ignored during the lecture either from being not focused or dismissed it as something small.
5 notes
·
View notes
Text
Security Everywhere Explanations
So I discovered during my Job application development that I don’t really explain my Security Everywhere information so I will be providing the context and explanation of the posts.
June 5th: I posted a meme about Huawei controversy with their potential security threats in their phones. Australia and America’s fear of potential Chinese military spying through Huawei’s phones have spiralled to national actions where Huawei infrastructure is now banned in both the countries. These meme is just a joke about it but it was something on my Facebook newsfeed so I decided to share it.
June 8th: At that time, there were news about ANU student and staff account information being hacked and stolen by Chinese hackers. The article discusses about the effects of such hacks and reasoning behind such cyber attacks and the impact of it to a University like ANU. This was highly relevant to the topics being discussed in Week 2 as one of our tasks was to draft a potential letter or recommendation to a recent UNSW email that attempted to raise Cyber Security Awareness. The article brought up an interesting observation where a potential outcome of the Cyber breach is that the information isn’t going to be sold to scam companies, but used by the Chinese government to track career progress of potential students that may impact Australia or China. ANU is a highly political and science driven University and holds alot of research and relationship value to China’s interest and thus leaking such information would allow the Chinese government to intervene on potential talents or projects.
June 15th: During this period of time, the Hong Kong protesting has risen over to 1 million protestors and was drawing alot of international news. The article that I read outlined China’s effort in intervening protestor’s communication through DDoSing an application called “Telegram” which was the protestor’s choice of messenger application to communicate with other protestors and organisers. Through Telegram, China was able to arrest protestors by tracking their actions throughout the riots. While this demonstrates notions of leaving digital footprints, it also poses another issue of Centralisation which we learnt in Week 3 Lectures ass all communication occurs on the Telegram application. Since all data is gathered in one place, it is also a single point of failure and if compromised, could lead to the endangerement of more rioters.
June 18th: I was recently told by my mum that her colleague/friend’s business was infected by a Wannacry virus in which they were forced to give bitcoins to the attacker in order to get their computers back.
A brief description of the WannaCry is that it is a malware where it infects all computers in the network and locks the computer up with a screen that tells the victim to send bitcoins to a certain account in order to get their computer back. The Wannacry attack works by having a worm that tunnels through all the computers and networks in order to look for a specific file that does not exist and only when the bitcoin is sent, will the worm stop tunnelling. The WannaCry attack became rampant in 2017 where major companies around the world were hit with this virus due to having computers connected to the same network, either through a local network or intranet and is usually initiated when an individual opens a suspiscious file. This bug mainly affected Window Operating systems ranging from Windows XP to Windows 10 however, individuals who had the most updated version of their OS at the time were not affected. This was because the Wannacry Virus exploits a backdoor bug that had existed in older versions of the Window operating system for more than a decade as the US Government were using this to access Russian systems through their own exploit called Eternal Blue. Microsoft eventually found the backdoor bug and fixed it in an update a month before the WannaCry virus began popping up and thus only Operating systems that were recently updated were unaffected by the WannaCry Virus.
Now the whole point of explaining that is since this is the year 2019, 2 years after the Wannacry outbreak, my mum’s friend got hit with the Wannacry attack. This meant that her operating systems weren’t updated and that was bad. Companies usually don’t update their operating systems as they may have applications or outdated systems that only work with older versions of Operating systems. As updating an operating system also meant that the company had to update their applications, it wouldn’t be cost efficient to update all their computers and would be cheaper to just use an outdated operating system to sustain their current applications. The risk assessments of Companies when using this strategy is that the likelihood of being hacked is quite low especially if they are a small company, and thus they trade security with cost efficiency. Although low probability, when they do get cyber attacked, then the impact would be huge as they are a small company.
Update your operating systems please.
June 29th: I posted about an observation I had made when I was researching about a game called Rage 2. Rage 2 is a game made by Bethesda Softwork and was released on the 14th of May and was released on the PC and purchasable on Bethesda’s game client and Steam client. Ironically, I was researching methods on ways of torrenting Rage 2 as I wanted to play the game without actually purchasing in order to try it out as I was new to the genre. However, the biggest fear I would have about games like Rage 2 is that since it is a game made by a Triple A company like Bethesda, it would be reasonable to assume that there were extensive measures in trying to keep individuals from torrenting and playing the game for free. Many companies would opt to use Denuvo to prevent individuals from torrenting the game as the game is only playable if the client they are using is able to supply the correct key. The key can only be generated by Denuvo which uses a complex cryptogaphic algorithm to generate it and hence “cracking” the key would be very difficult. Thus, trying to play the game through the Steam Client for free would take a long time as people would need to find the key first.
HOWEVER, Bethesda Softwork is very well known to be extremely slack when it comes to Quality Assurance and resolving bugs in their system and apparently this applies to their own Game Client Application. Apparently, Denuvo was never implemented to Rage 2 if you were to play the game through Bethesda’s game client. Thus the fear of not being able to “crack” the game was immediately dissolved as people were able to exploit Bethesda’s own client and thus Rage 2 was “cracked” in less than a day.
Moral of the story is that no matter how many security measures you place on your system, if there is a single point of failure, then all defence measures are done in vain if that point is breached. The single point of failure in this case is Bethesda’s Client.
July 13th: I can’t really explain about this one as it requires you to have already watched Spiderman Far from Home. However, I’ll say, Peter Parker does an oopsie and the cause of his actions resulted in a disaster occuring. However, he was the single point of failure as he was assigned a system whos User, Administrator and Owner is himself. Thus, everything that happens is a result of his actions and thus he is the single point of failure as there were no security measures that would’ve prevented his decisions or even resolved his decisions.
July 19th: I did this one for fun but basically, during the Week 7 tutorial, someone asked how to stop spam calls. I was getting alot too and found this solution that may help. I have received less phone calls now but I’m not sure if it’s because of the solution or if the companies have given up since I never pick up any of their phone calls.
July 21st: This was really random but one moment I was logged in on my own account in Piazza, and next moment I was in someone elses account. Apparently the account user was Natasha Wong and she went to Arizona University and she was using Piazza to do some maths course. Weird.
0 notes
Text
Week 8 Lecture Reflection
Personal Reflection:
I wasn’t sure why we had to learn the entire 3 mile island but I understand it if we look at it generally. A system that didn’t have security designed in mind will suffer the same accident as a system with the appropriate security however the latter system will take longer to break down while the former system will break down faster. Security systems can also cause misdirection as security indicators may move the focus from the actual problem to another thing that may have been indirectly affected by it. For example, having a gas detector and detecting irregularity may move the focus to valves rather than the chemical reaction that was causing the gas change.
Quick Notes:
The China Syndrome - Watch film for finals.
Root cause analysis-
1. Could be the last person who touched the system.
2. Culture
3. People lie
Something something, I’ve always been honest but you mentioned that you always have at least one piece of information that is a lie.
Human Weaknesses:
Honesty - Commander in cheat.
Experiment is university students. Got them to swear on the honour code. However, depending on where the honour code is placed, it would influence the integrity of the students. However in the end, the student integrity was all the same.
When analysing things in emergency situations, we tend to focus on one or two things.
Misdirection and limited focus - and Chekhov 1 people are bad at picking the right features for focus.
“Habit diminishes the consciouss attention with which our actions are performed” William James 1980.
Logically important vs psychologically salient- What seems logically important may not be the first thing that stands out to us as we are more likely to view something flashy and apparent before consulting our logic.
Similarity matching - Don’t have to think very much.
Frequency gambling - When you got a match, you draw upon your experience. Thus, the pattern you pick isn’t the best matching one but something that has worked for everytime.
Experiment- pendulum swing of the lead. Physics postgrads couldn’t get the location of the drop of the swing but they can theoretically calculate it well.
Devil’s computer. Everything that I don’t control is out against me.
Train algorithm experiement. Anything that Richard could control, he would try to sabotage it in the code from. The Student’s code is the only thing they can trust.
His obsession “those factors which lead to and sustain wishful thinking rather than wise thinking”
Satisficing and bounded rationality
People prefer positive statements
Overrideing tendency to verify generalisation rather than fasilfy them.
Availability heuristic - Kahneman 3.
Daniel Kahneman: The Difficulty to detect a countersign.
Confirmation bias - only look at theory that we personally might believe in. Almost like wishful thinking.
Availability heuristic is the mental shortcut of where we draw upon our most recent experience.
Cognitive strain - you thinking too hard man.
Group think syndrome - Group think is when you are in a group and how you act in a group.
Developmental phases - goed and breaked 2
1. Procedural
2. Meta-procedural
3. Conceptual
Systems
Cassandra and Apollo and hindsight and Chekhov and simplification.
Cassandra rejected Apollo and he got mad and thus cursed her where no matter what you say, no one will believe you.
Hindsight bias- Monday experts.
Everything you see might be salient and important.
- believe event has only one significant casue
- plan for fewer contingencies than occur
- ability to control outcomes - the illusion of control.
3 Mile Island.
Hindsight bias - Knowledge of outcome of pervious event increases
Perceived likelihood of that outcome
Complexity coherence coupling visibility 5
defense in depth - Theme park where the magnetic wheels have failed and safety bars has been activated but nobody notices because the machine is operating like normal despite having their back up defences activated.
Operator deskilling due to automatic safety devices
Common mode failures
latent vs active failures
Kings cross and herald for free enterprise 6
Normal accidents
1. a story(made up).
2. a story (real)
Dead battles like dead generals hold the miltiary mind in their dead group and germans no less than other people prepare for the last ware - Barbara Tuchman.
Just Culture
homework:
learn about one of Chernbyl
Bhopal
Challenger
Afternoon
3 Mile Island
Modern Reactors, nuclear engineering.
Reactor- Rods come up to speed up the reactor, Rods come down to slow down the reaction. This is because when the rod comes up, it takes the neutrons.
3 mile island text:
New technology is very complex, unit 2 has too many problems and is overworked due to the reduce in size.
Emergency system was turned off and hence caused an invisible failure.
Expected to fail 1 in 50 times but it’s rarely needed.
Light indicators could also cause issues as it might obscure certain information and cause misdirection in focus.
If you were building a system without thinking about security, you will have a “normal accident”.
Can’t stop a system failing, so we aim to make them harder to fail.
COMP6841:
Privacy does not have a definitive definition.
Imbalance of power
September 11 2001 Several airlines handed passenger records over to federal agencies. Information used for entirely different purpose than intended.
Forensics-
1. Acquisition/Imaging
- Capture an image (duplicate) of the drive
- Chain of custoddy
- Hashing
2. Analysis
- Keyword searches
- Recover deleted files
- Specialist tools are used
3. Reporting
Type of Forensics:
- Computer Forensics such as Memory Forensics, Data Forensics
- Mobile Devicie such as Phone
- Network Forensics such as Router, Switches and Packet captures
- Database Forensics and Video/Audio Foresnics movie files audio recorded on phones.
- Steganography
Tooling:
-Encase, AUtopsy/ The Sleuth kit, FTK Imager, File, Strings, Xxd, Foremost, Binwalk, mmls
Drives and Partitioning(FAT32)
- Allocates memory in clusters
- The FAT record stores the status of each cluster (bad region, allocated, unallocated)
- 2 FAT records for backup
Where do deleted files go?
- The name of the file is changed to 0xE5[file_name].
0 notes
Text
Week 2 - Type 1 and Type 2 Errors
So I was looking through tasks that I had done for modules to prepare for the Job Application and realised I haven’t done this.
So here are some examples of Type 1 and Type 2 Errors:
Law-
Type 1 Error occurs when a Person is convieted by the jury in court despite being innocent. This is a False positive verdict and the Court system actively seeks to avoid this due to the public backlash this event may have.
Type 2 Error occurs when Person is acquitted by the jury in court despite actually committing the crime. This is a False Negative verdict and is not as concerning as a False Positive verdict.
Spies and Intelligence-
Type 1 Error occurs when the Government accuses an individual to be a Terrorist but they really aren’t. Case study: Ahmed Mohamed Clock incident.
Type 2 Error occurs when the Government dismisses an indivudal to be a terrorist but they really are.
Medicine-
Type 1 Error occurs when the Patient does not have HIV but was detected during medical testings.
Type 2 Error occurs when the Patient does have HIV but it could not be detected during the medical testing.
0 notes
Text
Week 7 - Email Phishing
So this exercise requires a walkthrough in which I am to perform social engineering to figure out facebook login and organise fake payment.
Recon:
Looking through pupplove.org-
David- [email protected]
He spends his spare time microbrewing and looking after Angela and Jessie - two gorgeous black pugs!
Sarah- Email : [email protected]
she's chasing her 3 year old James and husband David around the house! Her favourite puppy is a rescue beagle named Jasper.
So I’m browsing Sarah Jenkins facebook and I found some interesting info like

and

Also I see at the bottom the website uses wordpress so maybe we can get some admin info? Also website uses http://www.litespeedtech.com so maybe that will help too i dont know.
Also I realised that their facebook page is inactive so perhaps I need to log in manually to it.

So I don’t know how responsive this social engineering email thing is so I tested by sending a message to sarah for the facebook page. This is because I have more information about Sarah so if she questions anything I might be able to answer her better. (Or maybe it was the other way around I’m not sure).

So I’m sure this is an automated reply but holy this is like an actual response to my question. Pretty scary what technology can do nowadays.
So I got the facebook flag
COMP6441{MakeSureYouSetUpTwoFactorAuthToPreventThis!!}.
So I thought maybe what happens when you ask David as Sarah to see if it’s the same thing out of pure curiousity.

Ok so David and Sarah don’t have the same information. So let’s see what Sarah says about payment details which we need for the second goal which is to get them to transfer to me.

So I discovered that this mailing system is not as immersive as I thought as I’m guessing it works off keywords. In anycase I’ll send the same message to David as Sarah.

Uhhh I guess this is a glitch. I tried different variations of the email but it didn’t work. So I just sent him a hello message.

Uh ok, let me ask about the payments.

So I have a feeling that the word Sarah might be causing some glitch so I’ll try to do it as if I’m super familiar or something.

Ok that’s something, maybe I’ll pressure him and say it is in fact urgent.

Oh yes I did it I managed to social engineer my way into a couples bank account god I am so cool.
Anyways yeah try it out it’s pretty cool.
0 notes
Text
Week 7 - Block Cipher Modes
Confusion means that each binary digit(bit) of the cipher text should depend on several parts of the key. It obscures the relationship between the plaintext and ciphertext as it hides the relation between the ciphertext and key. If a single bit of the key is changed, most or all bits in ciphertext will also be changed.
- Caesar Cipher or One Time Pad
Diffusion means that if we change a bit of the plaintext, half of the bits in the cipher text should change. If a bit is changed in ciphertext, half of plaintext bits should be changed too. It spreads the plaintext statistics through cipher text and hides the relation between ciphertext and the plaintext.
- Utilises avalanche
Avalanche effect means that if an input is changed slightly, the output is expected to change drastically.
Substitution and Permutation Boxes transform blocks of input bits into output bits where the input bits are plaintext and keys, and output bits are the cipher text after going through rounds or layers of alternating boxes.
Feistel Ciphers works by splitting the data block into two equal pieces and applies encryption in multiple rounds. Each round implements permutation and combinations derived from the primary function or key.
A block cipher is a method of encrypting tex tin which a key and algorithm is applied to a block of data at once as a group rather t han one bit at a time. This is because identical blocks of text do not get encrypted the same way in a message and thus remove commonalities in the blocks.
Stream ciphers encrypt one at a time.
I will attempt to find what types of cipher is used just by inserting asd repeatedly in the input box.
Cipher 1: CBC since the values don’t avalanche as much compared to other block ciphers.
Cipher 2: ECB because it matches the number of text inputted but the output values are different for each block.
Cipher 3: CTR
Cipher 4: CBC since values don’t avalanche as much as well and don’t seem completely random.
Cipher 5: CTR
0 notes
Text
Week 6 - 5g network
Catch up for week 6
Dear CEOs of Telstra, Vodafone and Optus,
Thank you for your cooperations towards our ban on Huawei 5g implementations and we understand the impact of this towards the effectiveness and efficiency of implementing a 5G system in Australia. However, due to Huawei policies and Chinese laws, we are unable to proceed with Huaweis involvement with our telecommunication system due to concerns on the interests of Australia’s national intelligence and security both domestic and nation.
The Chinese law is very vague on their involvement with commercial companies especially regarding terminologies like “international espionage”. Furthermore, the connection of Huawei with the Chinese Government and military is also very concerning. While we are sure that Huawei wishes the best in regards to Australia’s privacy and security, it is unfortunate that China’s regulations cannot be ignored and until then, we will continue to enforce Huawei’s 5G ban in Australia.
Yours Sincerely,
Scomo
0 notes
Text
Week 6 One time pads
Catch up for Week 6
One Time pads are secret keys that encrypt the message and once it is used, it is discarded from future uses. The secret key is infact a randomly generated key which is long enough for the entire message to be encoded. The plain text is added with the random key in order to generate a number value (the alphabet could be values of 1-26). The sum is then modulated with 26 and is then converted back to alphabet.
When a one time pad is used, Crib Dragging can be used to decode the message.
To use Crib Dragging as according to the provided blog post https://travisdazell.blogspot.com/2012/11/many-time-pad-attack-crib-drag.html:
Guess a word that might appear in one of the messages
Encode the word from step 1 to a hex string
XOR the two cipher-text messages
XOR the hex string from step 2 at each position of the XOR of the two cipher-texts (from step 3)
When the result from step 4 is readable text, we guess the English word and expand our crib search. If the result is not readable text, we try an XOR of the crib word at the next position.
So for this exercise, I will only crack the first one since it will apply to all other messages as well.
1. LpaGbbfctNiPvwdbjnPuqolhhtygWhEuafjlirfPxxl
So following the crib draggin technique, I will use a common word which is “the”.
T is number 20, H is number 8 and E is number 5. As L is the result of one time pad, we assume that T + (Some letter) % 26 = L (Number 12). Thus 12+26 - 20 = 18. We do this for the rest of the letters which is 8 and 22. Thus the resulting letters out of this are 18, 8 and 22.
Now we apply to all the other letters in which we get
- Message 1: The
- Message 2: Eve
- Message 3: Can
- Message 4: The
- Message 5: The
So for messge 2, I’m going to try the letter r for the fourth word. This will provide me new messages of the value 14.
- Message 1: Thes
- Message 2: Ever
- Message 3: Cany
- Message 4: Them
- Message 5: Thep
From first message, it looks like These so I will try the letter e next.
- Message 1: These
- Message 2: Every
- Message 3: Canyo
- Message 4: Themo
- Message 5: Thepr
From Message 3, it looks like can you so I will try u.
- Message 1: Thesec
- Message 2: Everyo
- Message 3: Canyou
- Message 4: Themos
- Message 5: Thepri
Keep doing what I’m doing and you will get these messages:
- Message 1: The Secret To Winning Eurovision Is Excellent Hair
- Message 2: Everyone Deserves A Hippopotamus When They’re Sad
- Message 3: Can You Please Help Oliver Find The Flux Capacitor
- Message 4: The Most Important Person In The World Is Me Myself
- Message 5: The Price Of Bitcoin Is Too Damn High Given The Data
0 notes
Text
Week 7 Tutorial Reflection
This week, we were told to debate over the government control and collection of our privacy and whether or not we should allow the government for more insight into our data or should reduce the amount of control the government should have over our data.
Personally, I feel indifferent about this as the government having more data and less data is dependant on how you view your privacy and whether you have anything to hide or not, thus since I don’t really have anything to hide, I don’t really care who has access to my information as long as it is not harmful such as people are more likely to scam me or what not.
I was placed into the group that was suppose to argue for more data. I felt more strongly aligned with this group as the arguments presented in this group were highly compelling. However, as we were discussing our points, we found that we found more weaknesses in our stance rather than finding more beneficial points. So we wrote them down anyways and hoped that we found a rebuttal before our adversaries bring up those points.
We wrote down these arguments:
- Allowing the government to collect more data will improve our law process especially monitoring or finding criminals or suspects. However, rather than the government collecting the data itself, the law system/legislation should be the only one that controls it so that the integrity of the data is maintained as the government cannot use criminal data for any other purpose. We would bring the idea of separation of data in case they mention that the government might use the data anyways.
- If our data was used commercially such as transport or super annuation etc (which they already do), it will improve our lifestyle as government development can be built around our convenience.
- Couldn’t think of anything more so here are some points of rebuttal: What happens during a cyber warfare, totalitarian state etc.
Then Hayden (Our tutorial guy) did a ol switcheroo and all of a sudden we had to argue for more privacy while our opponents was to argure for less privacy. Luckily, we thought of more negatives than positives for our argument so we had things to say.
Overall, I felt like I was able to convey all the information I wanted during our discussion. I felt like Hayden may have over hyped the debate because I don’t think anyone was too passionate about the topic or the debate but I found myself more talkative than usual. Probably because I felt like the opponents failed to understand what some of our points were or their rebuttal was a bit too weak for my liking and that there were better things to say as none of our arguments were perfect. In anycase it was pretty fun and I discovered that I might be more competitive as a person than I thought I was.
Here was some notes I took during the debate for rebuttal or clarification. Not all of them made it to the discussion as I may have felt it was too weak or pointless to bring up:
1. We already have ankle bracelets for criminal tracking.
2. The implementation of more security is highly expensive and may not be suitable for a country like Australia.
3. Nazi Germany is not an extreme idea since we already see radicalism in our country. If let’s say another crisis occurs, what is stopping us from voting in a particular violent party like One nation into power in which through policies of discrimination, incite another Rwandan Genocide?
4. In private space, information can be used against politicians as manipulation of data can occur more than ever. Facial Recognition can be used against us.
5. We don’t have the infrastructure to implement all these new traffic data collection.
6. Our government parties aren’t very effective with money as well as we can see in our countrys “bad spending”.
7. FBI will see me cry about Trimesters
0 notes
Text
Something Awesome Blog #5 Finale
Disclaimer:
The reason why I am ending this blog on Number 5 and at the end of Week 7 is because I’ll be completing the Job application before my tutorial on Wednesday Week 8. This is because:
- It will allow me to manage my time to do other Assignments for all my other courses and thus allow me to adapt to the Trimester changes and performing the best of my abilities for all my subjects.
- I am out of Card resources to analyse and experiment with (Further explained below under Reasoning).
I personally believe that I have accomplished what I wanted to do for the Proxmark device as I have provided a consistent blog post from the end of Week 2 to the end of Week 7 and not only that, I am also out of content to write about since I have run out of Card resources to analyse and experiment with.
Recap:
Throughout this project, I aimed to do as many cards as possible for the Proxmark device. The Proxmark kit I received had given me 5 different types of RFID cards/chips to work with. In my first blog, I discusssed about the Proxmark device and it’s usage and impact on Near-field communication (NFC) and RFID cards. In my second, third and fourth blog, I have explored the usage of 3 different types of card: Mifare Classic 13.56mH High frequency card, HID ProxCard II 125 kHz low frequency card and the EM4100 125 kHz low frequency card. For the low frequency cards, I have always mentioned cloning to a T5577 125 kHz low frequency card and always provided brief explanation of why I chose this card to clone to but I’ve never done a blog post solely about the T5577 which I will explain why I haven’t below and this will apply to other card variations.
Reasoning:
I haven’t been able to talk about other variations of the card such as the HID Iclass or Mifare Ultralights or other variations of the EM cards like EM4012 for the following reasons:
- Firstly, I usually don’t have a card that I could test out it’s functions and abilities and hence I don’t actually have a practical understanding of what the card can do. This makes it extremely difficult to explain how the card works as almost all online resources require you to have experience working with cards or the explanation is too vague.
- It is also extremely difficult to find any research topic about it as it either usually contains overlapping information with other versions of the card that I already have covered or it really isn’t explained on the internet due to the fact that it isn’t really used by anyone. Of course I can go on the company’s website which discusses about the card but it usually is very vague and tries to sell the card rather than outline it’s functions.
- Finally, the Proxmark 3 Easy kit that I had purchased for Something awesome is an “beginner friendly” research device on RFID cards and hence doesn’t contain all functions and features to clone all available RFID/NFC card in the market. Sometimes, the low frequency antenna isn’t able to detect what type of low frequency card it is so you would need to go through all reading options for each low frequency card available in the proxmark in order to identify the card.
The issue with not being able to identify the card is that it is would be extremely difficult to clone the card data to another card for example- cloning a low frequency card to the T55xx card. You could utilise “lf sim” to simulate the low frequency card but unfortunately, it is extremely basic level as it assumes that the low frequency reader only expects to output the ID of the card which can be achieved with “lf read”. This will not work with cards like EM4100 where the card is expected to return 64 bits of read only memory. However, the UID is usually only 8 bits hence the receiver would most likely not accept the simulated version of the card.
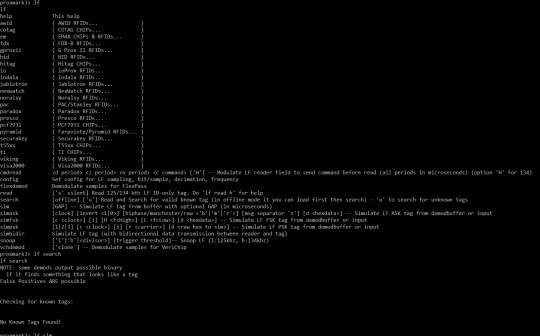
TL;DR Due to the lack of physical resource of not owning a variation of the card, lack of online content and limitations of the Proxmark device, I was not able to explore other variations of cards like Indala Proximity cards or Mifare Ultralights.
This really applied to the T5577 card as I was unable to find another T5577 card to clone since I don’t really own any T5577 cards except the one provided in the proxmark kit. Even when I tried to perhaps clone the T5577 card to the proxmark device just like how I worked around the fact that I didn’t have a blank card to copy the Mifare card to, the Proxmark device could not simulate the T5577 card as it did not have any options.
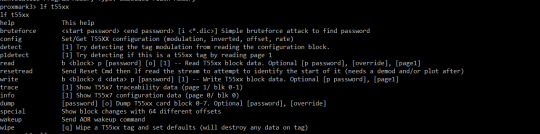
(There were no options to simulate a t55xx card as it only contained methods to retrieve data from the card).
Results:
However, despite these setbacks, there were several things that I have learnt in regards to RFID and NFC cards that we use everyday.
I discovered that no matter how many security measures you place into the card’s hardware and software, there always will be a method to bypass that. You could tell the Mifare card to reject a write if it is a card that is a different version or model however to prevent being copied to Chinese Magic Cards however, individuals could get an exact same model and version of the card and copy it to that instead. Or, if the card is set to read only to prevent any alteration of data, the read data could be copied to make a similar card with the exact same permissions.
That’s why I think that nowadays, it’s a good thing that card technology like opal cards or debit cards do not only rely on the card hardware security as they also require online confirmations. For example, the opal card requires you to register your card with your bank account online such that only 1 version of the card is in use unless specified otherwise. Since a cloned copy of a card would have a different card ID from the original card, even if the unique ID is the same, it will not work for the cloned copy.
In our case studies, the exploits all existed within the card security and not else where, especially for low frequency cards as they do not contain any security mechanisms since the only thing they contain is read only memory in regards to card type, ID and permissions. Low frequency cards only do simple things and thus should only be used for simple day to day tasks such as access to parking in a parking lot or guest passes. It should not store things like money details or used as authentication methods to access highly confidential buildings or rooms.
However, while the Proxmark does indicate a scary reality of cards being easily cloned and copied without being stolen, the likelihood is relatively small for something large scaled like transport cards. Although there has been cases, countries have now adapted more complicated security measures for cards and eventually will be cardless. While this would resolve many issues regarding card and access safety, it will bring in a whole new realm of possibilities since everything will most likely be digital and thus other methods can be used to steal cards.
Reflection:
There are things that I could definitely have done better, especially with how I structure my blog posts. My blog posts are pretty long due to the tutorial I place at the end of each blog so maybe instead of putting the tutorial and blog in the same location, I could have them separated. This would also give me an opportunity to talk about other cards that I may not have been able to clone but still could be relevant due to the similarities it has with current subject. However, since my something awesome blog posts are already really long, I was afraid that it wouldn’t really add anything except more words and also kind of goes outside of my original proposal.
Another thing is I wish I could’ve purchased a more advanced Proxmark 3. Most tutorials on how to clone cards through proxmark all use a more updated version of the Proxmark like proxmark 4. Proxmark 3 Easy kit was way too simple for somethings I tried to do and also didn’t really provide a huge variety of blank cards to experiment with so it really limited my ability from exploring more RFID/NFC cards. I realised that I only really know what to talk about if I manage to successfully clone a card and hence making a blog post about a card and making a tutorial was really something that came together rather than done separately as a bonus.
CONCLUSION:
Overall, I had a great time working with the Proxmark 3 Easy kit, hoped that somethings had worked such as the keyfobs as that would’ve been interesting to talk about. Hopefully in the future, I will also be working with interesting technology and devices (for research purposes) and has definitely inspired me to do more of my own projects like using an Arduino Uno to be a Rubby ducky usb except it’s not a usb it’s more of an external harddrive.

0 notes
Text
Lightning Talk Dirty Cow
I did a Lightning Call on Dirty Cow CVE Exploit. Find link here:
https://www.youtube.com/watch?v=SBPfjC8wbVc&t=3s
I did this talk because I wanted to always analyse a vulnerability and wanted to do this talk when the Lectures start discussing about exploits and vulnerability. Dirty Cow is an interesting CVE, along with Heart Bleed and Wanna Cry however Wanna cry was a bit too much to talk about due to its extensive history and Heart bleed was a bit too complex to explain.
Research Comments:
I began researching about Dirty Cow after the lecture explaining CVEs and exploit tools like Kali and Nmap. I was also inspired after completing a Week 5 module in which required us to discuss about an OWASP Top ten Vulnerability. Since I was researching Security Mismanagement, the idea of not updating your operating system made me wonder if there have been any exploits that have existed for a long time. Thus I found Dirty COW which existed since 2007 and was finally found and patched out in 2016. When researching about Dirty COW, I stumbled upon a video https://www.youtube.com/watch?v=kEsshExn7aE which basically gave me all the essential information about Dirty Cow and its history. However, the person goes into too much detail about certain aspects about the Dirty Cow and hence I only had to extract certain information such as:
- Using /proc/self/mem to write to virtual memory
- Called dirty because dirty bit is the manipulation or corruption of bit data.
- Bug caused by parallel threads causing an overlap in commands.
I then used https://www.cs.toronto.edu/~arnold/427/18s/427_18S/indepth/dirty-cow/index.html and the demo they provided to understand the concept of Dirty Cow visually. This greatly helped since during the lightning talk, I ended up drawing the process rather than use the powerpoint.
0 notes