Text
Formatting Strings in Java: String.format() Method
Formatting Strings in Java: String.format() Method
While System.out.println() is fine for debugging and displaying simple messages, it is not great for formatting strings. Formatted strings not only display the string content but they also show the content in a specified sequence. For instance, when displaying large integers like 100000000, you may want to include commas so that it appears as 100,000,000. Similarly with decimal numbers, you might…

View On WordPress
0 notes
Text
Understanding the Basic MLOps Principle for Data Scientists | by Daniel Izumi Katagiri | Dec, 2022
Understanding the Basic MLOps Principle for Data Scientists | by Daniel Izumi Katagiri | Dec, 2022
An introductory guide to help you put a more powerful model into production
Image by Cristiano Breuel from Wikimedia
If you are a data scientist or an aspiring one, you probably heard most ML models don’t make it to the production phase (Venture beat article). There are reasons for that, but one can argue that the current data science learning path focuses on building an ML model and improving…
View On WordPress
0 notes
Text
Linux Malware Exploits 30 Flaws To Target WordPress Websites
Linux Malware Exploits 30 Flaws To Target WordPress Websites
Heads up, WordPress admins! Researchers have warned users of a new Linux malware that targets WordPress websites with malicious JavaScript. The malware exploits 30 vulnerabilities in different WordPress themes and plugins to accomplish the goal.
Linux Malware Targeting WordPress Websites
According to Doctor Web, a new Linux malware has surfaced online, actively targeting WordPress websites.…
View On WordPress
0 notes
Text
Attackers create 130K fake accounts to abuse limited-time cloud computing resources
Attackers create 130K fake accounts to abuse limited-time cloud computing resources
A group of attackers is running a cryptomining operation that leverages the free or trial-based cloud computing resources and platforms offered by several service providers including GitHub, Heroku, and Togglebox. The operation is highly automated using CI/CD processes and involves the creation of tens of thousands of fake accounts and the use of stolen or fake credit cards to activate…
View On WordPress
0 notes
Text
Accelerate JavaScript Applications With Concurrent Pipelines | by Kartal Kaan Bozdogan | Dec, 2022
Accelerate JavaScript Applications With Concurrent Pipelines | by Kartal Kaan Bozdogan | Dec, 2022
How we achieved a 35% speedup on our application
Photo by Yoko Correia Nishimiya on Unsplash
Data pipelines, like the famous ETL pipeline, are hardly foreign to most back-end developers.
I recently found myself working with such a pipeline in my team’s Node.js backend. I was working on an endpoint taking in a number of objects, validating them, and inserting them into a database:
for (var obj of…
View On WordPress
0 notes
Text
Cops Catch Serial Child Abuser After Tech Breakthrough
Cops Catch Serial Child Abuser After Tech Breakthrough
A Pembrokeshire man has been jailed for life for a series of appalling sexual offenses against young children, after investigators used new technology to unmask him.
Global law enforcers had been trying to ascertain the identity of 50-year-old Martyn Armstrong for years after abuse material was posted to dark web pedophile site The Love Zone back in 2010.
The challenge was that the perpetrator…
View On WordPress
0 notes
Text
Pragmatic Event Sourcing. Event sourcing is an architectural… | by John Pradeep Vincent | Dec, 2022
Pragmatic Event Sourcing. Event sourcing is an architectural… | by John Pradeep Vincent | Dec, 2022
Event sourcing is an architectural pattern; it’s not a silver bullet
Photo by Mathyas on unsplash
Having successfully built multiple systems using event-sourcing patterns, I have also encountered cases where people have complicated their architecture in the name of event sourcing — an inevitable consequence of being dogmatic about patterns instead of being pragmatic.
This article aims to help…
View On WordPress
0 notes
Text
Potential Future Applications for AL and ML
Potential Future Applications for AL and ML
Artificial intelligence (AI) and machine learning (ML) have already begun to revolutionize the world of software development, and their impact is only expected to grow in the coming years. In this article, we’ll explore the current state of AI and ML in the software development industry, as well as their potential future applications.
What Are AI and ML?
First, let’s define AI and ML. AI refers…
View On WordPress
0 notes
Text
Accessibility Testing vs. Functional Testing
Accessibility Testing vs. Functional Testing
Functional testing is concerned with the functionalities that enable the software system or application to work as per the required functional specifications and business requirements. Accessibility testing is concerned with the web application’s accessibility. It ensures the disabled community can easily access a website or specific application. The UI design and usability are pondered and…
View On WordPress
0 notes
Text
Software Development Cycle Time: A Deep Dive
Software Development Cycle Time: A Deep Dive
What Is Software Development Cycle Time?
Software development cycle time refers to the period from an engineer’s first commitment to code deployment. Some teams also refer to this period as lead time. Cycle time or lead time indicates the time taken to complete a particular dev task.
Cycle time is often used to infer a dev team’s process speed. It measures a dev team’s efficiency and ability to…
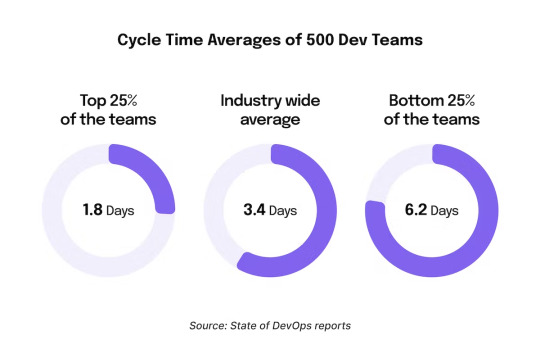
View On WordPress
0 notes
Text
Gaming: How much is too much for our children?
Gaming: How much is too much for our children?
With many children spending a little too much time playing video games, learn to spot the signs things may be spinning out of control
Across Europe, half of the population aged 6-64 plays video games, according to industry body ISFE. The number rises significantly for 6-10-year-olds (68%), and those aged 11-14 (79%) and 15-24 (72%). According to some research, teenagers may spend as many as…
View On WordPress
0 notes
Text
What Are Runbooks? And Why Are They Needed?
What Are Runbooks? And Why Are They Needed?
Runbooks are documented procedures for the maintenance and upgrades of systems. Leverage runbooks during incident response. Save your team’s invaluable time. Learn more.
Need for Runbooks
Imagine being an Ops engineer in a team just struck by tragedy. [sigh…]
Alarms start ringing, and incident response is in full force. It may sound like the situation is in control.
WRONG!
There’s panic…
View On WordPress
0 notes
Text
Want To Save Time on Estimating Projects? Consider Projections | by William Bernting | Jan, 2023
Want To Save Time on Estimating Projects? Consider Projections | by William Bernting | Jan, 2023
If you can’t get away from estimating, there’s a way to at least get away from spending time on it
Photo by Arno Senoner on Unsplash
“We know you’ve never done this before; just try to guess it anyway.”
We’ve all been there. Someone wants a few basic facts before making a business decision. Like paying for carpentry, someone thinks we can use the same principles of time estimation for product…
View On WordPress
0 notes
Text
9 Python @dataclass Best Practices To Improve the Development Process | by Bruce H. Cottman, Ph.D. | Jan, 2023
9 Python @dataclass Best Practices To Improve the Development Process | by Bruce H. Cottman, Ph.D. | Jan, 2023
An exploration of the benefits of @dataclass
Photo by Amr Taha on Unsplash
My first language was FORTRAN, which is more or less unusable for distributed computing because of global variables. I vowed back then to avoid global variables if I could.
I adopted object-oriented (LOOPS — Lisp Library) for its ability to encapsulate data states. Passing all the data encapsulated was accomplished by…
View On WordPress
0 notes
Text
High-Performant Applications in Mule 4
High-Performant Applications in Mule 4
In this blog, I would like to share a few best practices which can help in creating high-performant applications in Mule 4 from both Infrastructure and Coding perspectives.
I will start with Best Practices from an Infrastructure standpoint (we will look at only CloudHub 1.0 as a deployment option here), then I will take you through Best Practices from a Coding standpoint (achieved via API Manager…
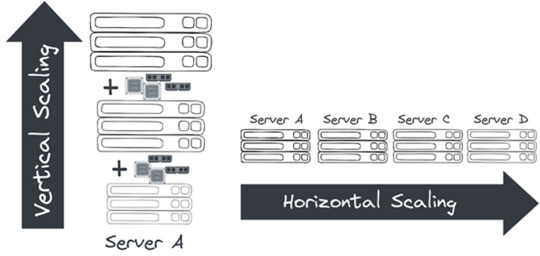
View On WordPress
0 notes
Text
RedZei Chinese Scammers Targeting Chinese Students in the U.K.
RedZei Chinese Scammers Targeting Chinese Students in the U.K.
Jan 02, 2023Ravie LakshmananOnline Scam / Cybersecurity
Chinese international students in the U.K. have been targeted by persistent Chinese-speaking scammers for over a year as part of an activity dubbed RedZei (aka RedThief).
“The RedZei fraudsters have chosen their targets carefully, researched them and realized it was a rich victim group that is ripe for exploitation,” cybersecurity…

View On WordPress
0 notes
Text
How ChatGPT Is Revolutionizing the World of Natural Language Processing
How ChatGPT Is Revolutionizing the World of Natural Language Processing
Natural language processing (NLP) has come a long way in recent years, and ChatGPT is playing a major role in its evolution. For those unfamiliar, ChatGPT is a chatbot platform that uses the power of artificial intelligence (AI) and machine learning (ML) to enable natural, human-like conversations with users. With ChatGPT, businesses and organizations can provide quick, accurate, and personalized…
View On WordPress
0 notes