Text
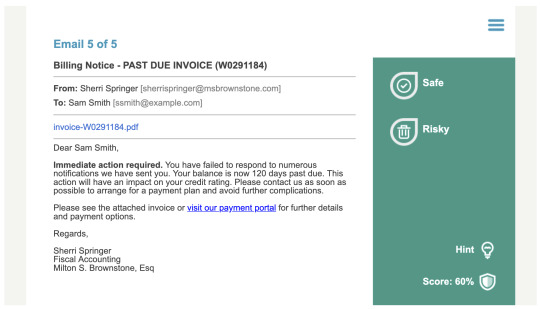
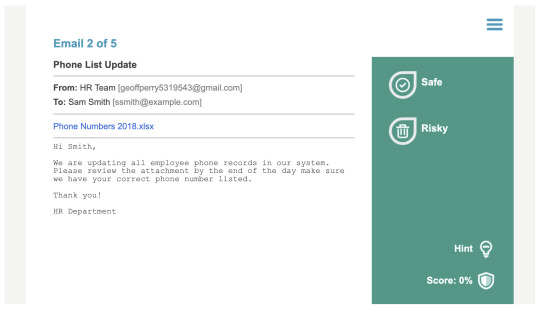
Cookies
Cookies
The question I want to ask today is.
Do I actually need to login?
For a lot of application, we don’t actually need to login at all. The whole process of login in is just to obtain some sort of cookie which is then used to identify yourself. If I can obtain that cookie, I can just skip the whole login process.
Postman and Insomnia
How do these API Testing Tools work?
I am about to test my API, website or program without login in using these tools. But these tools are not different from the browser, all they really do are send GET, POST, DELETE, PUT request without login in. Wait what!! Without logging in? Yes, so let’s say I can remember my cookies for a website, I can skip the whole process of login in and just go straight to the program.
1 note
·
View note
Text
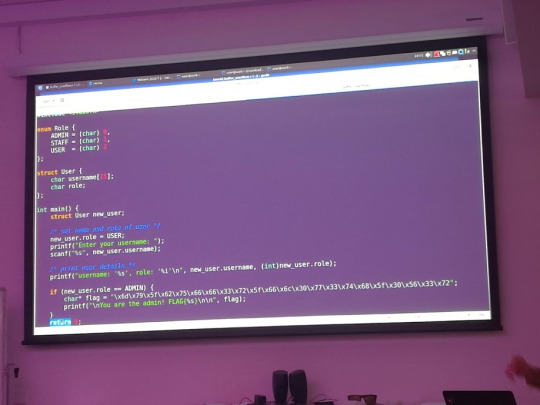
Buffer Overflows
Buffer Overflows
Let’s go from the beginning what is a buffer? Buffers are a temporary storage unit for data, a Buffer overflow is when extra data is written causing some of the data to leak out into other buffers, allowing others to corrupt, break or overwrite a program. An example of this is
// A C program to demonstrate buffer overflow #include <stdio.h> #include <string.h> #include <stdlib.h> int main(int argc, char *argv[]) { // Reserve 5 byte of buffer plus the terminating NULL. // should allocate 8 bytes = 2 double words, // To overflow, need more than 8 bytes... char buffer[5]; // If more than 8 characters input // by user, there will be access // violation, segmentation fault // a prompt how to execute the program... if (argc < 2) { printf("strcpy() NOT executed....\n"); printf("Syntax: %s <characters>\n", argv[0]); exit(0); } // copy the user input to mybuffer, without any // bound checking a secure version is srtcpy_s() strcpy(buffer, argv[1]); printf("buffer content= %s\n", buffer); // you may want to try strcpy_s() printf("strcpy() executed...\n"); return 0; }
Giving the Input
Input : 12345678 (8 bytes), the program run smoothly.
Or
Input : 123456789 (9 bytes) "Segmentation fault" message will be displayed, and the program terminates.
The buffer could be overflow by the users input. In these cases, the program did not check the size of the buffer before compiling. Good explanation here:
The vulnerability exists because the buffer could be overflowed if the user input (argv[1]) bigger than 8 bytes. Why 8 bytes? For 32-bit (4 bytes) system, we must fill up a double word (32 bits) memory. Character (char) size is 1 byte, so if we request buffer with 5 bytes, the system will allocate 2 double words (8 bytes). That is why when you input more than 8 bytes; the mybuffer will be over flowed Similar standard functions that are technically less vulnerable, such as strncpy(), strncat(), and memcpy(), do exist. But the problem with these functions is that it is the programmer responsibility to assert the size of the buffer, not the compiler. Every C/C++ coder or programmer must know the buffer overflow problem before they do the coding. A lot of bugs generated, in most cases can be exploited as a result of buffer overflow.
1 note
·
View note
Text
Job Application Letter
Job Application Letter
Dear GITZon,
I am writing in response to the advertisement posted for the job opportunity at Gitzon. As an experienced Engineer with expert knowledge in many areas.
I offer a strong aptitude for learning new technologies and a proven track record of meeting aggressive goals. My most notable skills include:
Analytical Ability
Time Management
Skills
Community/Professionalism
'Something Awesome' Project
Thank you for your time and consideration.
Hope to hear from you soon!
Sincerely,
Andy
z5113471
1 note
·
View note
Text
Something Awesome
Something Awesome
My assignment was about Capture the Flag (CTFs) and a Break In project which focused on recon analysis. In which my HD criteria was to complete 2 CTF challenges and perform in-depth recon and attempt to break in.
My tutor approved this after questioning a few issues regarding permission on whether I was allowed to be conducting analysis and breaking in at work.
Completion
I blogged my progress as to what I have completed throughout the weeks.
Initial Idea
Marking Criteria
week 3 general update
week 3-4 update
week 4 Recon analysis
week 5 Social Engineering ideas
Week 6 Pre-Card stealing
Week 6 Card Stealing Reflection
Week 6-7 More Experiments
Week 7 Card Stealing Review
Week 7 Pre-Texting
Week 7 Interesting Event
Week 7-8 Breaking In
Sneaking co-workers
Ways to get access
Fire Alarm
Last bits of recon
Phishing
Logging
Week 2-8 Natas 0-10
Week 8 Other options
Week 7-8 More Natas
Week 7-8 Ever more Natas
XXS Games
Bandit
Office
Lunch
End
Reflect
Presentation
As part of my submission I post a YouTube video example my Something Awesome and also presented it in class.
Something Awesome Submission
Video submission
1 note
·
View note
Text
Community and Professionalism
Community and Professionalism
Communities
Tumblr
I decide to use a public blogging platform for others to be able to access and learn from my work. I also build a community where I would like and comment on others work and they would on mine. I share all my knowledge I learnt and even post them in the forms of notes


Slack
I join the security community and many different security related channels. Also have my tutor on slack.


Class Participation
I rearrange my whole work schedule to attend the tutorial which started at 5 and participated in the discussion and conversation with the rest of the class. Helping to form a solution, viewpoint or answer to the question.
Lecture notes and activities
Week 1 Week 1: Lecture Exercise Life expectancy of a computer Shredding Analysis Dumpster Driving
Working with others
I participated in group studying activities at university and also privately. In which I either helped other students or they help me. We also created a Facebook group chat to help each other. Teamwork


Data handling
My whole Something Awesome topic and many of my blogs reference the company in which I worked at. This means that I would have to handle the data in which I post very carefully.
I always thought twice about post images and/or video which contain work environment, which is why there are only videos and pictures toward the end of the semester. I also emailed my tutor regarding the lack of images explaining that their maybe sensitive data and would prefer not to publicly post it. Refer to email subjected Re: COMP6[84]41: Summary of Week 6 & 7 Tutorials. Even for this blog post the images used above have been approved and I decide to not include an image of the email but rather give you the subject heading of the email.
My question to you is, can you name the company I work for?
Security Everywhere
I developed security eyes and started to see security issues in everyday life. I blog about issues and topics related to security which provide evidence of my effectiveness and time management skills.
Hong Kong Protest
Opal building/Mascot Tower
Huawei
Cathay Attack
Google Maps
Examples
Smart Phone Infection
NSW transport Kiosk
Something Awesome
When conducting my CTF and XXS I post explanation and answer for anyone that wanted to try.
Week 2-8 Natas 0-10
Week 7-8 More Natas
Week 7-8 Ever more Natas
XXS Games
Bandit
Recon analysis and experiments where done in teams with others in which we had to work together, or I had to rework a solution when given feedback.
Reviewed Phishing Email
Pre-texting experiment + Review
1 note
·
View note
Text
Skills
Skills
Module Activities
I was able to complete the security modules each week, in which I cover in more details in the Analytical Skills section.
Cryptograms
For preparation for the final and mid semester exams, I solved many ciphers, whether it is on the Cryptogram website, app or others that are offered online.
Crypto
NSA Crypto App
Week 1 - Crypto Website
Something Awesome
My something awesome assignment led me to practice different Capture the flag games, XXS games and recon challenges. Which allowed to practice both technical programming abilities when practicing CTFS and XXS games.
Week 2-8 Natas 0-10
Week 7-8 More Natas
Week 7-8 Ever more Natas
XXS Games
Bandit
And allowed to the practice physical skills as well, in the form of experiments. This include many data analysis, social engineering and research skills
Week 6 Pre-Card stealing
Week 6 Card Stealing Reflection
Week 6-7 More Experiments
Week 7 Card Stealing Review
Week 7 Pre-Texting
Week 7-8 Breaking In
Sneaking co-workers
Phishing
Logging
Submission links here for more information
Something Awesome Submission
Video submission
Extra
I also did some extra reason into other topic such as phishing emails and plan to do a quick lightning talk on it.
Emails
Lighting Talk on Phishing
Some other skills I did research on will be listed below.
How to steal a penguin
Vulnerabilities
Threat Modelling
Hashing Gone Wrong
Co-Incidence Index
Dumpster Driving
Co-Incidence Index
Type I & Type II Errors
Crypto Processors
Locks picking, raking and bumping
SQL Injections
Threat Modelling
Other topics that interested me
Buffer Overflows
Cookies
1 note
·
View note
Text
Time Management
Time Management
Frequency of post
One of the biggest indicators of time management is the frequency of that individual posts. Not only but whether that individual is able to complete the weekly modules and activities that come with it. Similar to other students if we check the archive we notice that I post an average of 34 blogs a month meaning that I have around 8 blogs per week.
I was able to take and complete this course to a high standard while balancing a full-time work role which is already a great indication of time management.
Weekly Modules - Homework and Exercise
I was able to complete homework and exercise activities to a high standard.
Week 1: Lecture Exercise
Life Expectancy of a computer
Shredding Analysis
Dumpster Driving
Co-Incidence Index
Cipher Intro
Type I & Type II Errors
NSA Crypto App
How to steal a penguin
Low Probably High Impact
ATM attacks and defence
Crypto Processors
Locks picking, raking and bumping
Human Weakness and Moral Hazards
Hashing Gone Wrong
Passwords - Grandparents Letter
Vulnerabilities
Vulnerabilities - 2nd attempt
OWASP Top 10
Threat Modelling
5G in Australia
Case Studies - Tutorial Labs
Attending case studies and have pre-laboratory or reflections after is also a good proof of time management. Especially in a situation like mine where I have work between 9-5, meaning that I have to organise some alternatives to attend the tutorial which starts at 5. With bad time management I would not be able to attend the tutorial. I had to attend work half to an hour early so I could leave early to attend the tutorial.
Week 1 - Deepwater Horizon Oil Spill
Pre-Tutorial/Lab 2 - Houdini
Post Lab - Houdini
Post-Lab - Airplane Doors
Week 4 - Assets
Week 5 - Driving Cars
Week 6 - Safer - Pre-Lab Week 7 - Snoop
Something Awesome
My Something Awesome project was not one that could be easily finish in 1-2 weeks, as it took extensive recon analysis and many different experiments. I decide to blog and work it in a little each week. But sadly, it was hard to manage a full-time work and part-time studies, in which the fact that I was able to complete the assignment is proof of good time management. In which some of the blogs I will link below.
week 3 general update
week 3-4 update
week 4 Recon analysis
week 5 Social Engineering ideas
Week 6 Pre-Card stealing
Week 6 Card Stealing Reflection
Week 6-7 More Experiments
Week 7 Card Stealing Review
Week 7 Pre-Texting
Week 7 Interesting Event
Week 7-8 Breaking In
Week 2-8 Natas 0-10
Week 8 Other options
Week 7-8 More Natas
Week 7-8 Ever more Natas
Something Awesome Submission
Since I am working full-time, I do not have much time to spend on university during weekdays. So, I decided to finish and submit my something awesome a few days in advice. This was before the tutor even told us how we would submit our something awesome videos.
Evidence of this can be found in my email with my tutor. Subject marked Re: COMP6[84]41: Summary of Week 6 & 7 Tutorials
Job Application
I was able to submit this application before the due date.
Exam
Attending the exam and making it 2 hours in advance in case there was traffic.
1 note
·
View note
Text
Analytical Ability
Analytical Ability
Case Studies - Tutorial and Labs
Every week I try to blog about the case study, whether it is a prelab, post lab or just a reflection. In these blogs I include knowledge learnt in the lectures or self-learnt and then I apply that knowledge, normally in the form of brainstorming with other class members. This usually results in a great discussion where I either verify that my point is valid or end up opening to other points of view.
Week 1 - Deepwater Horizon Oil Spill
Pre-Tutorial/Lab 2 - Houdini
Post Lab - Houdini
Post-Lab - Airplane Doors
Week 4 - Assets
Week 5 - Driving Cars
Week 6 - Safer - Pre-Lab Week 7 - Snoop
Security Everywhere
Whenever possible, I try to blog about security everywhere. These posts apply my knowledge I have learnt from the course into the real world and help my analyse security problems and solution.
Hong Kong Protest
Opal building/Mascot Tower
Huawei
Cathay Attack
Google Maps
Examples
Smart Phone Infection
NSW transport Kiosk
Something Awesome
I decide to regularly blog about my Something Awesome where I analysis different workplace security problems and practice recon experiment which we cover in class and others which I researched myself and CTF answers and analysis.
week 3 general update
week 3-4 update
week 4 Recon analysis
week 5 Social Engineering ideas
Week 6 Pre-Card stealing
Week 6 Card Stealing Reflection
Week 6-7 More Experiments
Week 7 Card Stealing Review
Week 7 Pre-Texting
Week 7 Interesting Event
Week 7-8 Breaking In
Sneaking co-workers
Ways to get access
Fire Alarm
Last bits of recon
Phishing
Logging
Week 2-8 Natas 0-10
Week 8 Other options
Week 7-8 More Natas
Week 7-8 Ever more Natas
XXS Games
Bandit
Homework & Exercise
The homework and exercise include details of course material and many examples of knowledge.
Week 1: Lecture Exercise
Life Expectancy of a computer
Shredding Analysis
Dumpster Driving
Co-Incidence Index
Cipher Intro
Type I & Type II Errors
NSA Crypto App
How to steal a penguin
Low Probably High Impact
ATM attacks and defence
Crypto Processors
Locks picking, raking and bumping
Human Weakness and Moral Hazards
Hashing Gone Wrong
Passwords - Grandparents Letter
Vulnerabilities
Vulnerabilities - 2nd attempt
OWASP Top 10
Threat Modelling
5G in Australia
Topics related
Buffer Overflows
Cookies
Reflection
I tried to regularly blog and revisit topics, exercises and task in which I have completed and community of how it changed my views.
My Situation
Something Awesome Reflection
Something Awesome - break in
Something Awesome Card Stealing Reflection
1 note
·
View note
Text
Security Everywhere - Google Maps
Security Everywhere - Google Maps
Well well well, google that looks a lot like JavaScript. I wonder what I could do with this information. Also, I do enjoy the function name. Good job on that.

1 note
·
View note
Text
Security Everywhere - NSW transport Kiosk
Security Everywhere - NSW transport Kiosk

Well well well Look what we have here. So, the kiosks for NSW transport which show us the train times are actually just windows machines. Wonder what we can do with this information
1 note
·
View note
Text
Security Everywhere - Smart Phone Infection
Security Everywhere - Smart Phone Infection
[9 News Report] (https://www.9news.com.au/technology/agent-smith-malware-australian-android-users-may-have-downloaded-new-form-of-mobile-virus-news-update/9cd458ed-c41b-49bc-b7fc-d820a54b6ee3?fbclid=IwAR02N8zEjFBI0ResRK9lC7sZWCyt60fUHQkOeA10fl48KreTO7NrWGvhz44)
Recently 25 million smartphones have found to be hack by a malware by the name "Agent Smith" Worldwide. Seems as though we have no clue how much information was stolen.
How did this happen?
The malware disguised itself as a google replated application and exploited Android vulnerabilities, automatically replace different apps. Everyone needs to check their phone NOW
Oh, and for all your apple users, yes this actually affects you to. So, I would hurry and check your stuff
1 note
·
View note
Text
Week 7
Snoop
Tutorial Question
*Should the government or government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them? *
So, I didn't get to choose which group to be in and very sadly I was put in the group I was AGAINST and had to fight for something I didn't believe in.
Why should the government have more data
Safety - World PEACE
So, we argued that with more data the government could easily crack down on Terrorism and be able to easily stop Crime e.g. Child abuse.
Convenience
We argue that a lot of slow processors would be a lot more efficient e.g. transport, checks (e.g. Centrelink checks and background checks)
Also, I personally think that there could me so many different industry and job opportunities if the government did have more data.
BUT
Obviously, no one really think they should privacy is a real issue, the more power you give the more responsibility and looking at history we are not good with responsibility
2 notes
·
View notes
Text
Week 5 - Driving Cars
Pre-Lab
List of attacks
- Insider attack
- Ransomware attacks on infrastructure
- DoS attacks
- Sabotaging power and other services
- GPS jamming
- Drone/device hijacking
- Backdooring application
- Surveillance
Assets
Data - confidential information
Power supply
Infrastructure
Ranking
Insider attack
Background checks on programmers
Keep critical people anonymous
Create backdoors
Recommendations
- Educating/hiring
- Production of ransomware/virus/malware
- Power supply support
- Infrastructure support - energy, financial, manufacturing, transport, communication and health systems
- Financial preparation
- Resource preparation
- Global relationships
- Local relationships
- Pre-planning for attacks (making procedures) - incident response
- Risk assessments
Other
-
Recommendations
???
For anyone that wanted the C code
1 note
·
View note
Text
Week 4 Lab Case Study
Hardware
- Locker to store device/computer overnight
- Computer/devices is attached to computer vault/stand which is locked to the desk

Security Pass
- Personalised security passes to access different areas
- To enter work space room / lift security to access level (different passes)
- For server rooms/other static devices
CCTV
- CCTV to be able to contently monitor work space and its surroundings
Learning
- Mandatory security module that employees must pass
Site construction
- Glass in the building
What would be important to protect
- Intellectual property, data, protect
- Design of facility
- Technology used in production
- Employees
- Insider attack
- Keys and swipe cards
Not physical sec but extras
- Reputation
1 note
·
View note
Text
5G in Australia
5G in Australia
write a letter to US President Donald Trump explaining why you have chosen to allow them to build the network and why you do not think it is a concern.
Dear President Donald Trump,
I have deep concern about Huawei 5G roll out network. I think that in our current situation we should let Huawei help The United States roll out its 5G network. Overall it will improve the US quality of life but this does not mean we should approach without caution.
I refer to the bottom advantages and disadvantages
1. Advantages
2. Improved quality of life
3. Overall cheaper cost
4. Increase competition for local business
Disadvantages
1. If we are to allow Huawei to roll out this network we must impose necessary regulation and rules they must follow.
Overall, the advantages out way the disadvantages and therefore, either way United States will be in a beneficially state.
write a letter to the CEOs of Telstra, Vodafone and Optus, explaining the importance of the ban, and why the 3 x increased cost to them and their customers is work paying
To whom this may concern,
The Unite States have deep concerns regarding the Huawei 5G network, we will not be continuing business and as of today we highly recommend all Unites States business to stop trading with Huawei.
It may seem as if this is a huge setback, but if we give China the potential to produce a backdoor in our network, the United States and therefore all United State business will be at a huge advantages.
The US is also planning to roll out our own 5G network, which may not be completed as fast, but reduced the potential of national security.
For further information please join our conference call
1 note
·
View note