#ISO 27001 Standard
Text
0 notes
Text
Benefits & Key Elements of ISO 27001 Certification
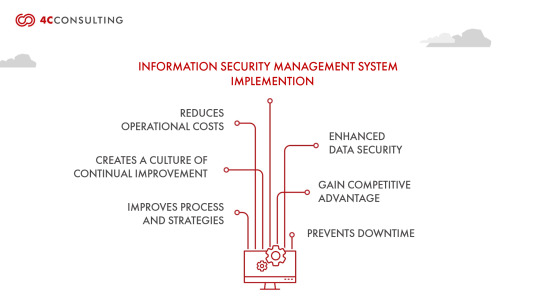
Benefits:
Risk Reduction: ISO 27001 helps identify and mitigate information security risks, reducing the likelihood of data breaches.
Improved Business Resilience: Enhanced security measures ensure business continuity in the face of cyberattacks or disasters.
Competitive Advantage: Certification sets you apart from competitors, attracting clients who prioritize security.
Global Recognition: ISO 27001 is recognized worldwide, making it easier to expand into international markets.
Key Elements:
Risk Management: A core element, risk management ensures ongoing assessment and mitigation of security threats.
Policy Development: Establishing and maintaining information security policies and procedures.
Employee Training: Ensuring that all employees understand their roles and responsibilities in maintaining security.
Incident Response: Preparing for and responding to security incidents promptly and effectively.
#ISO 27001#iso 27001 2013#iso 27001 certification#iso 27001 certification training#iso 27001 certification consultant#iso 27001 training#iso 27001 standard
0 notes
Text
How ISO 27001 Certification Can Help Improve Your Cybersecurity Strategy

ISO 27001: Achieve Better and Reliable Cybersecurity Strategy in India
If a business owner doesn't take the essential action, the future is uncertain. A company can gain great features of cybersecurity from ISO 27001 ISMS. The outstanding capabilities of ISO 27001 Certification provides a reliable cybersecurity management system.
Information Security Management System (ISMS) is the key ingredient of ISO 27001 Certification. The goals of ISO 27001 Controls are to help a company from different cybersecurity-related threats. The advantages of implementing the ISO 27001 Standards should be understood by every businessperson in India. It is an important point to boost your cybersecurity and provide better protection for sensitive information.
The most popular division inside a company is to protect its data. One with unique cybersecurity needs to follow the terms and conditions of ISO 27001 Certification. If you run a business in India, it is required to possess specific details, such as employee data, payroll information, a well-defined plan, administration data, etc.
Significant Features Available with ISO 27001 Compliance
Strong protection needs to be provided to ensure the security of any kind of data. For this, the organization will require a distinctive and solid base. Achieving the following features becomes easier when an organization in India has achieved ISO 27001 Compliance with the 2022 standards.
The following points will explain all very well:
● Decline the Rate of Risk
The approach should incorporate risk management practices including routine systems reviews and audits to guarantee data protection and rapid remedy of any flaws or vulnerabilities. When a corporation implements the ISO 27001 Standard, some data breaches can be avoided. Generally speaking, it develops several security procedures to protect any data.
● Attain Better Quality
An ISMS framework must include quality control. It is addressed by the ISO/IEC 27001 through the creation and implementation of a systematic Quality Assurance Program. The procedures, regulations, and practices should be outlined in this framework. They oversee the ITSM services' quality. To ensure that the data gathered is accurate and comprehensive, assurance should be employed.
"Quality assurance" also refers to the correctness and dependability of the technology. The term is used for data collecting and processing of the secure management of data.
● Evade Improper Security Mismanagement
A data breach is inevitable if you don't have sufficient assets and backup plans for them. A few robust business continuity plans and crisis recovery strategies are important to implement as per the ISO 27001 Standard. They will help you to build a better and more reliable cybersecurity system.
● Allocate the Finest Security Responsiveness
The ISO 27001 standard defines security responsiveness as educating and informing staff members, vendors, and other customers on the business's safety policies, procedures, and practices. This includes instructions about handling unsecured data and information properly.
● Produce Top-Class Opportunities for Employees
Better data security procedures might have some mind-blowing consequences on the market for a firm in India. The ISMS can make things better and encourage a pleasant environment among your potential employees. It shows how much your business values trustworthiness and data protection laws.
Required Strategies to Bring in ISO 27001 Certification
1. Go with the ISMS Framework
When a company decides to follow ISO 27001 Certificate criteria, the first step is the implementation of the ISMS. Better risk assessment is made possible by the framework that the ISMS creates. Each step analyzes and assesses the threats to the organization's information's dependability, accessibility, and privacy.
2. Appoint a Project Manager
Once a project manager is hired by an organization, that person will be responsible for managing and coordinating all of the activities involved in implementing ISO 27001.
3. Develop an Implementation Plan
The organization should form a plan to introduce ISO 27001 Certification. The plan includes the following factors:
● Scope of the project
● A timeline of the project
● The resources needed
● The activities to conclude
● The risks involved
4. Go for the Documentation
Every action associated with the ISO 27001 ISMS framework is organized systematically, and this includes the creation of a documentation strategy.
5. Training of Staff
The training of the workforce of an organization as per the new ISMS policies, processes, and procedures should be conducted.
6. Perform a Risk Assessment
The selected personnel will conduct risk assessments to determine and analyze the threats to the confidentiality, veracity, and accessibility of the organization's information.
7. Establish Controls
The employees in charge will make every effort to minimize any hazards. With the best risk assessment, proper controls being established, and deployment of a new one, each type of risk may be assessed.
8. Checking the Integrity of ISO 27001 ISMS
Monitoring and analyzing the efficacy of the controls regularly is the key to keeping the company safe. Maintaining the ISMS rules is crucial when everything is going smoothly.
Conclusion!
There won't be any pressure on you to keep your company's information secure. Businesses in India must exercise caution due to security issues. Use the finest ISO 27001 Certification processes and strictly adhere to improvise each cybersecurity strategy briefly.
#ISO 27001#ISO 27001 ISMS#ISO 27001 Certification#ISO 27001:2022#ISO 27001 Standard#Cybersecurity#ISO 27001 Controls#ISMS#ISO/IEC 27001
0 notes
Text

Step by step read the given paragraph and know How can you get ISO 27001 Certification in Mexico.
.
.
.
ISOCertification #ISOCertificationinMexico #ISO27001inMexico #Mexico #ISO27001CertificationinMexico
0 notes
Text
ISO Certification in Bhubaneshwar | qfscerts
ISO Certification in Bhubaneshwar helps companies to improve their competitive advantage and win deals. If growing sales is your top priority, then achieving an ISO certification is the key to winning new business. The capital of Odisha, Bhubaneswar is scenic, lively, green, and clean, with a rich cultural life. Known for its temples, It is also known as “temple city”. Major industrial sectors in Bhubaneswar include the paper, steel, automobile, food, pharmaceutical, and electronics industries.
For More Info: https://bit.ly/3BBPJC1

0 notes
Video
Factocert is one of the leading ISO 27001 Certification providers in Ireland. We provide ISO Consultant service in Dublin, Belfast, Cork, Derry, Limerick, and other major cities. ISO 27001 certification in Ireland will Establish a good base for the safety management system in almost any organization.
For more: https://factocert.com/ireland/iso-27001-certification-in-ireland/
0 notes
Audio
While cyber-attacks and breaches are growing phenomena around the world, read this blog to learn how does cyber security help us and what we can do about it. To read more visit https://www.quality-assurance.com/blog/what-is-cyber-security-and-how-does-it-help-us.html
0 notes
Text
ISO 27001 Certification: What It Is And Why You Need It
What is ISO 27001 Certification?
ISO 27001 Certification is a globally recognized standard for Information Security Management Systems (ISMS). It provides a systematic approach for managing and protecting sensitive information within an organization. This certification ensures that an organization has implemented comprehensive security controls to safeguard its data from threats and vulnerabilities.

ISO 27001 Certification Benefits
Obtaining ISO 27001 Certification through 4C Consulting Private Limited offers numerous advantages:
Enhanced Security: ISO 27001 helps organizations strengthen their information security, reducing the risk of data breaches and cyberattacks.
Compliance: Achieving certification ensures compliance with international information security standards, potentially opening new markets for your business.
Customer Trust: Customers are more likely to trust organizations that demonstrate a commitment to protecting their data.
Improved Efficiency: The structured approach to security management improves overall business efficiency.
Competitive Advantage: ISO 27001 Certification sets your organization apart from competitors and can be a valuable marketing tool.
#iso 27001#iso 27001 2013#iso 27001 certification#iso 27001 standard#iso 27001 lead auditor#iso 27001 training#iso 27001 requirement
1 note
·
View note
Link
Niall Services provides certification, implementation & training for ISO 27001, ISMS, Information Security Management System in Ahmedabad,Gujarat, India.Contact Us: +91-99789 71691.
1 note
·
View note
Text
ISO 27000 or ISO 27001?

If your business deals with sensitive information, you must gain and maintain your clients' trust. The ISO 27001 security standards come into play here.
You can instantly discover why information security is more crucial than ever by opening any news app. Every 39 seconds, a new cyberattack is launched, and each one costs businesses.
If your business deals with sensitive information, you must gain and maintain your clients' trust. The ISO 27000 security standards come into play here.
Several sets of rules make up the ISO 27000 family of standards, which all work toward certifying a company's information security procedures. The primary worldwide standard is ISO 27001, whereas the other standards offer information security best practices that independent auditors and certification bodies can use to vouch for your internal information security procedures.
One of the finest ways to demonstrate to potential customers that you can be trusted to protect their data is with an ISO 27001 Certificate. This handbook contains all the information you need to know regarding audit procedures and what information you must record.
Is ISO/IEC 27000 a thing?
The International Organization for Standardization (ISO) and the International Electrotechnical Commission jointly publish the ISO 27000 set of standards to assist businesses in strengthening their information security management frameworks (ISMS).
The goal of this ISMS is to reduce risk in relation to the three components of information security—people, procedures, and technology.
There are 46 distinct standards in the ISO/IEC 27000-series, including ISO 27001.
Its foundation is ISO 27001, which describes the conditions for putting an ISMS into place. The sole ISO 27000 series standard that businesses can be inspected and certified against is ISO IEC 27001:2013.
Even while not all ISO standards will apply to your business, it's still beneficial to gain a general understanding of ISO 27000 and its guiding ideals, such as the specifications for creating an ISMS.
An ISMS
Let's define an ISMS in greater depth since it is essential to the ISO 27000 standard.
The full collection of procedures a company employs to deal with safe data is referred to as an information security management system. Information assets should be shielded from unwanted access to proactively identify and mitigate risk, and ensure data availability by ISMS.
An ISMS is typically thought of in terms of hardware and software. The concept is larger under ISO 27000 and includes procedures, rules, plans, and culture.
What do ISO 27000 standards entail?
There are 12 distinct standards on the list of ISO 27000 standards. If you need a certificate, the only set that is required is ISO 27001. However, having some familiarity with the others can help you choose which ones apply to you.
ISO/IEC 27001
The security procedures required to protect client data appropriately are described in ISO 27000. These principles are met in the actual by ISO 27001 Certification. Businesses execute the requirements defined in ISO 27000 standards and use an ISO 27001 audit to confirm the efficiency of their ISMS.
The requirements for creating an ISMS that complies with ISO 27001 are listed. The ISMS needs to:
Accurate documentation
With the backing of top leadership
Capable of foreseeing and reducing dangers
Provided with everything necessary for it to operate
Regularly updated and evaluated
An organization may employ one of the 114 specific ISO 27001 controls listed in Annex A to comply with these standards.
Also, Check -->> How long does it take to get ISO 27001 Certified?
How do I become certified for ISO 27000?
In theory, you don't.
Just to clear up any misunderstanding, ISO 27000 certification does not exist. The ISO 27001 standard specifies how to certify a company as adhering to any of ISO 27000's requirements.
Now that is out of the way, how can you become certified for ISO 27001?
By thoroughly comprehending ISO 27000 requirements, you can begin the ISO 27001 certification procedure. Study ISO 27017 and ISO 27018, for instance, if you keep a portion of your infrastructure on the cloud. Study ISO 27701, etc., if your consumers are in the EU.
Make sure your ISMS is up to standard as your next action. Here, ISO 27003 will be useful. It's time for the risk assessment if your documented ISMS complies (at least on paper) with all pertinent controls in each area of ISO 27000.
As you develop your risk assessment procedure, use ISO 27005's guidelines as a guide. It will highlight the areas where your ISMS falls short of compliance and highlight which unabated hazards pose the greatest danger of negative outcomes.
Information security is essential in the ever-evolving cybersecurity world, which is why ISO 27000 has such a strict set of guidelines.
A compliance platform can make the certification process for ISO 27001 more transparent and efficient. Make a demo appointment right away for knowledgeable explanations.
#ISO 27001#iso 27001 certification#iso 27001 certification in india#ISO 27001 Standard#ISO 27001 ISMS#information security#ISO 27000#Information Security Management System
0 notes
Text
What is iso 27001 - Iso 27001 Compliance, Standards & Requirements | 4C Consulting

ISO 27001 Information Security Standard Compliance: Understanding Its Importance And Process
What is ISO 27001
Being a part of ISO 27000 standards family, ISO 27001 is an information security standard that provides a framework which enables modern organizations to secure their information and data as well as manage risks. Risk Management, being one of the significant parts of the standard, is essential for an organization to identify the strengths and potential risks that can be posed with regards to their information security.
The standard is also a structured process that leads the organizations to identify, establish, implement, operate, monitor, maintain and improve their ISMS. It encompasses all the legal, physical and technical aspects involved in the risk management process of any organization.
Confidential information such as intellectual properties, employee and client information must be kept secured. However, it is challenging to keep it secure all the time, especially when organizations are technology-reliant and therefore, technological and other security measures can be breached.
Despite all the challenges, a sole IT department in an organization is not enough for data integrity and security, especially if the organization is spread across the globe with multiple organizations. An ISMS framework can help in streamlining data security measures to keep confidential information secure in the company.
ISO 27000 Family of Standards
ISO 27001 is a part of ISO 27000 family of Information Security Management Systems (ISMS), which contains a series of standards that focus on managing the risks related to information asset of the company. The purpose is to keep the information assets that are either crucial or confidential for the company including financial data, intellectual property, client and employee details as well as other classified information safe and secured.
ISO 27001 Requirements
ISO 27001 can be applicable to all organizations irrespective of their size and industry. It provides a comprehensive approach to security of information needing protection spanning from digital information, physical documents, physical assets (computers and networks) to the knowledge of individual employees. It also covers competence development of staff, technical protection against computer fraud, information security metrics, incident management as well as requirements common to all management system standards such as internal audit, management review and continuous improvement.
General requirements
Define scope of your ISMS as per your organizational needs
Prepare comprehensive documentation
Prepare clarified management policies
Demonstrate control on risk assessment and management
Documental requirements
Documented statements of the ISMS policy and objectives
Elaborate the scope of the ISMS
Procedures and controls in support of the ISMS
A description of the risk assessment methodology
The risk assessment report
The risk treatment plan
Business continuity plan
What are the ISO 27001 standards
Before beginning the implementation process, it is necessary for the management and stakeholders to get acquainted with all the sections of the standard. Following are the 12 sections of ISO 27001:
Introduction – identification of the objective of managing risks and define information security
Scope – understand and prepare for requirements for an ISMS
Normative References – explains the relationship between ISO 27000 and 27001 standards.
Terms and Definitions – covers the complex terminology that is used within the standard, also the reintroduction of ISO 27000 standard as applicable.
Context of the Organization – defines the role of stakeholders and their responsibilities in the creation and maintenance of the ISMS
Leadership – describes the responsibilities and commitments of leaders within an organization with regards to ISMS policies and procedures.
Planning – provides an outline of risk management planning across the organization.
Support – describes ways to raise awareness about information security and assign responsibilities within the organization and staff members/employees.
Operation – provides insights into risk management and document creation to meet the audit standards
Performance Evaluation – provides guidelines on the performance monitoring and measurement of the ISMS
Improvement – explains the ISMS must be continually updated and improved as per the audits and rules.
Reference Control Objectives and Controls – provides an an next on the individual elements of the audit.
#What is iso 27001#iso 27001 Requirements#ISO 27000 Standards#ISO 27001 Standards#Iso 27001 Compliance
2 notes
·
View notes
Text
A Brief Guide on ISO 27001 Standard
ISO 27001 Standard
Since organisations and industries cannot hide data away from peeping eyes like one would do in a personal diary, there are simple measures to enable organisations gain such ease in accessing information. The ISO 27001.Hence, many organizations now, are making use of the ISO 27001 Trainingto protect data and to manage cybersecurity risks. This blog will help you understand…

View On WordPress
#What are the 14 domains of ISO 27001?#What are the key requirements of ISO 27001?#What does the ISO 27001 standard focus on?#What is the ISO 27001 code?
0 notes