Text
Heimdall is a tool aimed at getting the website admin panel using brute force with a wordlist.
Heimdall is an open-source tool designed to automate fetching from a target site's admin panel using brute force in the wordlist. Developed entirely in Python, it has simple didactic code for study and is an ideal tool for the hacking arsenal.
Examples:
1. ./heimdall.py --url www.site_target.com --wordlist 1
2. ./heimdall.py --url www.site_target.com --wordlist 2 --user-agent <USER-AGENT>
3. ./heimdall.py --url www.site_target.com --wordlist extra/wordlists/custom.txt
4. ./heimdall.py --update
#Download #Link
https://github.com/ygorsimoes/Heimdall
DISCLAIMER: Tools are being shared for educational purposes only! I'm not responsible how others choose to use them~./Ap3x
#CyberNews #HackerNews #cybersec #cybersecurity #infosec #infosecurity #informationsecurity #pentesting #IT #PoC #CVE #informationtechnology #bugbounty #RedTeam #BlueTeam #ethicalhacking #Ap3x


#cybersecurity#ethicalhacking#ceh#100 days of productivity#programming#mecha#robotics#python#illustration#studyblr
2 notes
·
View notes
Video
youtube
# 02 Fix: uTorrent access is denied ! Torrent file Downloading Error
0 notes
Video
APK Leaks - this tool scans APK files for URIs, endpoints & secrets Handy utility that quickly dumps IPs, URLs, URIs from analyzed Android app without need to search them manually during static analysis with decompilers. What are APK decompilers? Feel free to check my post from yesterday where I summarised them up including the download links. 👉 Download: https://github.com/dwisiswant0/apkleaks . . . . . #programming #hack #cybersecurity #linux #hacked #infosec #hackers #bigdata #hacking #opensource #kalilinux #ethicalhacking #csharp #github #malware #androiddeveloper #pythoncode #cyberattack #informationsecurity #pentesting #ethicalhacker #python3 #hackerman #hackerspace #bugbounty #metasploit #ceh #cybersecuritytraining #kalilinuxtools #learnhacking https://www.instagram.com/p/CMAFDsig1569w5KW6olcsygG9kYTBFPf1D6Zug0/?igshid=1ne8ri0wzrir0
#programming#hack#cybersecurity#linux#hacked#infosec#hackers#bigdata#hacking#opensource#kalilinux#ethicalhacking#csharp#github#malware#androiddeveloper#pythoncode#cyberattack#informationsecurity#pentesting#ethicalhacker#python3#hackerman#hackerspace#bugbounty#metasploit#ceh#cybersecuritytraining#kalilinuxtools#learnhacking
0 notes
Photo
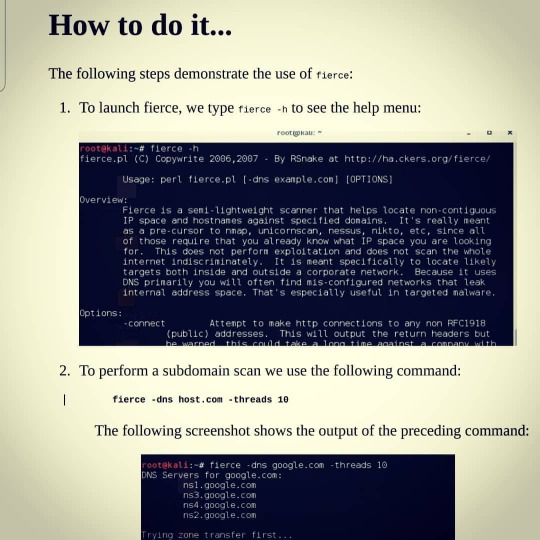
Getting a list of subdomains..... We don't always we have a situation where a client has defined a full detailed scope of what needs to be pentested. So we will use the following mentioned recipes to gather as much information as we can to perform a pentest. We will test here with Google... Example: www.google.com #tipsandtricks #cybersecurity #ceh #InsTake #it #PoC #networking https://www.instagram.com/p/CL7TAcMAhOuzpP4onz11A3PTGyoWdPDoQ_gAQA0/?igshid=18c23u35h3pt0
0 notes
Video
youtube
Learn how to bypass any applock to view any video,image& file etc..
#bypass google account#bypass#bypasslock#cyber news#cybersecurity#ethicalhacking#hackinghulk#infomation#apphacking#appbypass
0 notes
Text
🗃 How Ransomware Uses Encryption To Commit Cybercrimes? 🗳
━━━━━━━━━━━━━
Encryption is designed to protect your data, but encryption can also be used against you.
For instance, targeted ransomware is a cybercrime that can impact organizations of all sizes, including government offices. Ransomware can also target individual computer users.
How do ransomware attacks occur?
━━━━━━━━━━━━━
Attackers deploy ransomware to attempt to encrypt various devices, including computers and servers. The attackers often demand a ransom before they provide a key to decrypt the encrypted data. Ransomware attacks against government agencies can shut down services, making it hard to get a permit, obtain a marriage license, or pay a tax bill, for instance.
Targeted attacks are often aimed at large organizations, but ransomware attacks can also happen to you.
━━━━━━━━━━━━━
DoctorI.TGroup
©©©©Hacking Hulk ©©©©
CyberNews #HackerNews #cybersec #cybersecurity #infosec #infosecurity #informationsecurity #pentesting #IT #PoC #CVE #informationtechnology #bugbounty #RedTeam #BlueTeam #ethicalhacking #Ap3x #hackinghulk #ransomware #tipsandtricks

1 note
·
View note