#EmailSecurity
Text
Spear phishing is a targeted attempt to steal sensitive information, such as login credentials or financial information, from specific individuals by posing as a trusted organization. In this blog post, we will look into what spear phishing is, how it works, and most importantly, how you can protect yourself and your organization from falling victim to such attacks. Stay vigilant, stay informed, and prioritize cybersecurity to protect your digital assets from spear phishing and other cyber threats.
#CyberSecurity#SpearPhishing#PhishingPrevention#CyberAwareness#InfoSec#EmailSecurity#MFA#DataProtection#CyberThreats#StaySafeOnline#infosectrain#learntorise
1 note
·
View note
Text
9 Best Practices for Email Marketing Security

Email marketing is a powerful tool for businesses to engage with customers, but it also presents security risks. Cybercriminals often target email campaigns to steal sensitive information or spread malware. To safeguard your email marketing efforts, it's crucial to follow best practices that enhance security and protect both your business and your recipients. Here are nine best practices for email marketing security:
1. Use Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA), adds an extra layer of security. This ensures that only authorized users can access your email marketing platform, significantly reducing the risk of unauthorized access.
2. Regularly Update and Patch Software
Ensure that your email marketing software and all related systems are regularly updated and patched. Cybercriminals often exploit vulnerabilities in outdated software to gain access to sensitive information. Keeping your systems up-to-date mitigates this risk.
3. Encrypt Sensitive Data
Encryption is crucial for protecting sensitive information transmitted via email. Use Secure Sockets Layer (SSL) or Transport Layer Security (TLS) to encrypt data in transit. Additionally, consider encrypting sensitive data stored within your email marketing platform.
4. Monitor and Audit Email Activity
Regularly monitoring and auditing email activity can help detect suspicious behavior early. Implement logging and tracking mechanisms to keep an eye on email campaigns, login attempts, and any changes to account settings.
5. Educate Your Team
Human error is a significant factor in many security breaches. Educate your team on email security best practices, phishing scams, and the importance of using strong passwords. Regular training sessions can help keep security top of mind.
6. Implement SPF, DKIM, and DMARC
Implement Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC) to protect your domain from being used in email spoofing attacks. These protocols verify that your emails are coming from authorized servers, reducing the risk of phishing attacks.
7. Use a Secure Email Gateway
A secure email gateway can help filter out malicious emails before they reach your inbox. These gateways scan incoming and outgoing emails for malware, phishing attempts, and other security threats, providing an additional layer of protection.
8. Regularly Back Up Data
Regular backups ensure that you can recover your data in the event of a security breach or system failure. Ensure that backups are stored securely and are tested regularly to confirm their integrity and effectiveness.
9. Be Cautious with Third-Party Integrations
Third-party integrations can enhance the functionality of your email marketing platform, but they can also introduce security risks. Only integrate with trusted third-party services and regularly review their security practices. Ensure that they comply with relevant data protection regulations.
Conclusion
Securing your email marketing efforts is vital to protecting your business and your customers. By following these nine best practices, you can significantly reduce the risk of security breaches and ensure that your email marketing campaigns run smoothly and safely. Implementing these measures will not only enhance security but also build trust with your audience, leading to more successful email marketing outcomes.
0 notes
Text
https://roadrunnermailsupport.com/spectrum-email-customer-service/
1 note
·
View note
Text
Cyber Threats Q1 2024 revealed: Cat-Phishing, Living Off the Land, Fake Invoices

Cat-phishing, using a popular Microsoft file transfer tool to become a network parasite, and bogus invoicing were among the notable techniques cybercriminals deployed in Q1 2024, per @HP Wolf Security Report.
https://tinyurl.com/mpjd96xp
#cybersecurity#threats#phishing#malware#infosec#cybercrime#hacking#emailsecurity#netsec#dataprotection#ransomware#antivirus#cyberthreats#phishingattacks#scams#catphishing#asyncrat#bits#filehijacking#redirectattacks#fakeinvoices#securityawareness#threatintelligence#emailgateways#browsersecurity#mobilemalware
0 notes
Link
https://bit.ly/3SSDF86 - 🔍 Guardio Labs unveils "SubdoMailing" — a widespread subdomain hijacking campaign compromising over 8,000 domains, including MSN, VMware, and eBay. Millions of malicious emails circulate daily, exploiting trust and stolen resources. #SubdoMailing #CyberSecurity 📉 Guardio's email protection systems detect unusual patterns, leading to the discovery of thousands of hijacked subdomains. The operation involves complex DNS manipulations, facilitating the dispatch of spam and phishing emails under reputable brands. #EmailSecurity #DNSManipulation 📧 Examining a deceptive email reveals clever tactics, including image-based content to bypass spam filters. SPF, DKIM, and DMARC authentication are manipulated, allowing scam emails to reach users' inboxes. #EmailScam #CyberAttack 💻 Analysis uncovers the resurrection of abandoned domains, enabling subdomain hijacking for malicious activities. Actors manipulate SPF records, creating a web of authorized senders to evade detection. #DomainSecurity #SPFManipulation 🛡 Guardio identifies a coordinated campaign by threat actor "ResurrecAds," exploiting compromised domains for mass email dissemination. The operation spans diverse tactics, including SPF authentication injection and SMTP server hosting. #ThreatActor #CyberCrime 🔎 Tracking indicators of compromise reveals the extensive infrastructure behind "SubdoMailing," spanning hosts, SMTP servers, and IP addresses. The operation's scale and sophistication underscore the need for collaborative defense efforts. #CyberDefense #ThreatAnalysis 🔒 Guardio launches a "SubdoMailing" checker tool to empower domain owners in reclaiming control over compromised assets. The tool provides insights into abuse detection and prevention strategies. #CyberAwareness #SecurityTool 📢 Join Guardio in raising awareness about the "SubdoMailing" threat and utilizing the checker tool to fortify domain security. Together, we can mitigate the impact of malicious email campaigns and safeguard digital landscapes.
#SubdoMailing#CyberSecurity#EmailSecurity#DNSManipulation#EmailScam#CyberAttack#DomainSecurity#SPFManipulation#ThreatActor#CyberCrime#CyberDefense#ThreatAnalysis#CyberAwareness#SecurityTool#DomainProtection#ebay#dmarc#stolenresources#domain#emails#cybersecurity#operation#brands#emailsecurity
0 notes
Text
Smart Email Solutions
📧✨ Discover Smart Email Solutions with Century Solutions Group! ✨📧
Tired of inbox clutter? 📥 Need a secure & efficient email system? Look no further! We offer top-notch Email Security Services to streamline your communication and boost productivity. 🔒💼
Our Managed IT Solutions ensure seamless email management, advanced security, and easy collaboration. Say goodbye to spam and hello to a smooth emailing experience! 😃🚀
🔗 Learn more: https://centurygroup.net/managed-it-solutions/email-solutions/
#EmailSecurity #Productivity #ManagedIT #CenturyGroup
1 note
·
View note
Text
Unleash your campaign strategies and content strategy with B2BInDemand Email marketing

Unleash your campaign strategies and content strategy with B2BInDemand Email marketing
1. AI-Powered Personalization: Elevate customer experiences with AI-driven content tailored to individual preferences.
2. Interactive Emails: Engage audiences like never before with interactive elements, boosting click-through rates and conversions.
3. Privacy-First Strategies: Embrace evolving privacy regulations by prioritizing transparent, consent-driven communications.
4. Omni-Channel Integration: Seamlessly integrate email marketing with other channels for a cohesive customer journey.
5. Sustainability Initiatives: Embrace eco-friendly practices by optimizing email delivery and reducing carbon footprints.
6. Hyper-Personalization: Harness advanced segmentation techniques to deliver hyper-targeted content based on user behavior, demographics, and preferences.
7. Visual Storytelling: Utilize compelling visuals, videos, and GIFs to convey your brand story and captivate audiences, enhancing engagement and brand recall.
8. Automation and Workflow Optimization: Streamline your email marketing processes with automated workflows, from welcome sequences to post-purchase follow-ups, saving time and maximizing efficiency.
Stay ahead of the curve and revolutionize your email marketing strategy in 2024!
Get in touch with us:
https://lnkd.in/d4DSZgEA
Follow Us:
Instagram: https://lnkd.in/dmpTZrbX
Twitter: https://lnkd.in/dGZE7pq2
Linkedin: https://lnkd.in/dyfVd2uv
contact us:
1 (302) 966 9297
www.b2bindemand.com
[email protected]
#emailmarketing#trends2024#emailcampaigns#emailsecurity#emails#emailmarketingtips#emailmarketingstrategy#b2bindemand
1 note
·
View note
Text

From the get-go of establishing your digital space, even with well-documented employee training, there's a risk that someone on the team might unintentionally click or download harmful software from the 🤿backend waters. The bait? Often disguised as emails, robust email security is the ultimate fishing rod for safeguarding your environment.
It's not just about securing your emails; it's about becoming a savvy angler, identifying false positives swimming in the currents, and skilfully redirecting them to the correct inbox, ensuring smooth sailing for your business activities.
Whether it's 💰 monetary values, your reputation, 🌐email login details, or sensitive codes like OTP, you must avoid falling victim to phishing scams.
⚓ Stay sharp | Don’t Get Phished 🎣
Connect with us, and let’s discuss your current cyber plan.
#emailsecurity#phishingprotection#phishingawareness#linkedin#cyberattack#cybercrime#cyberaware#cyber
0 notes
Text

The Need of secure e-mail service
.
.
.
.
for more information and tutorial
https://bit.ly/47giFx3
check the above link
#cybersecurity#emailsecurity#sslstripping#mitbattck#computerscience#arpspoofing#emailhacking#sessionhacking#mitmattck#computerengineering#javatpoint
1 note
·
View note
Text
🛡️ Unlocking Email Power: Master Email Authentication Now! 🌟
Dive into the world of email security with our latest guide! Discover how SPF, DKIM, and DMARC protocols can supercharge your email deliverability, boost sender reputation, and shield you against cyber threats. 🚀🔒
✨ Learn how to:
Implement SPF to prevent spam and phishing.
Use DKIM for a digital seal of authenticity.
Master DMARC for robust email protection.
👉 Stay ahead with cutting-edge strategies like AI, blockchain, and interactive security. Transform your email game now!
Check it out here 👇 https://metadatamarketer.com/email-authentication-for-better-deliverability
#EmailSecurity#DigitalMarketing#EmailDeliverability#Cybersecurity#TechInnovation#EmailAuthentication#SPF#DKIM#DMARC#MarketingStrategy
1 note
·
View note
Text
Email Security Exploration: Guide to DMARC Reports and Beyond
In the vast landscape of digital communication, fortifying your email security is no longer a choice but a necessity. Join us on an expedition through the intricate realm of DMARC (Domain-based Message Authentication, Reporting, and Conformance) reports – the guardian of your domain's sanctity against phishing and cyber threats. 🌐📧🛡️
Navigating the DMARC Citadel
Embark on a journey into the heart of DMARC, a formidable fortress shielding your domain from the rising tide of phishing scams and cybercrimes. Understand the pivotal role DMARC plays in ensuring your emails are not just messages but trusted emissaries from your domain. 🏰📬
DMARC: Sentinel of Email Authenticity
Delve into the significance of authenticating emails in the digital age. Explore how DMARC acts as a vigilant sentinel, protecting users from phishing attacks, fostering trust with customers, and boosting email deliverability. Uncover the power of genuine communication. 🔒📩
Deciphering the Code: Inside DMARC Reports
Unlock the mysteries concealed within DMARC reports, presented in the enigmatic XML format. From metadata to policy application, become fluent in interpreting the wealth of information these reports offer. Equip yourself with the skills to monitor and optimize your email ecosystem. 🕵️♂️📊
Strategies for Email Deliverability Mastery
Your emails deserve the spotlight, not the shadows of spam folders. Learn the art of leveraging DMARC policies to maximize email deliverability. Safeguard your sender reputation, engage with your audience, and witness the success of your email campaigns soar to new heights. 📈📧
DMARC in Marketing Alchemy
Witness the transformation of DMARC from a security protocol into a potent catalyst for marketing success. Elevate your email open rates, enhance your sender reputation, and craft marketing strategies that resonate with your audience. Unleash the alchemy of DMARC in your marketing endeavors. 🚀📈
Crafting the Invincible DMARC Policy
Forge an impregnable DMARC policy that not only shields your domain against cyber threats but also optimizes email delivery. Navigate the delicate balance between security and accessibility, gradually enforcing policies to secure your domain's reputation. ⚖️🔒
Ready to elevate your email security, authenticity, and deliverability? 🚀 Embark on this comprehensive guide, and let DMARC be your beacon in the ever-evolving digital landscape. ����📧🌐
🎁 To view the full review in detail: Click here!
🎊 To learn About The Power of other software, themes, or plugins: Click here!
✨ To hire any of us as a Video Editor, Audio Engineer, Shopify Expert, YouTube Manager, or Content Writer: Click here!🌐🔐🚀
#DMARC#EmailSecurity#DigitalFrontier#DMARCreports#CyberGuardian#EmailDeliverability#MarketingAlchemy
0 notes
Text
Experts Advise Caution Before Scanning QR Codes

Quick Response codes can be very convenient for traveling to websites, downloading apps, and viewing menus at restaurants, which is why they’ve become a vehicle for bad actors to steal credentials, infect mobile devices, and invade corporate systems. https://jpmellojr.blogspot.com/2023/12/experts-advise-caution-before-scanning.html
#QRcodePhishing#Zimperium#MobileSecurity#QRcodeAttacks#Quishing#emailSecurity#QRcodeBestPractices#QRcodeSecurity
0 notes
Text

Best-in-Class Email Services
Experience Email Perfection with Magtec
#Email#emailservices#emailcontent#emailsecurity#emailmarketing#emailmarketingsolutions#emailmanagement#magtec#uaebusiness#dubai2023
1 note
·
View note
Link
https://bit.ly/3RnKL4Q - 🛠️ Mosint: A New Open-Source Email OSINT Tool: Developed by Alp Keskin, Mosint is designed for efficient email investigations. It stands out for its speed, pulling data asynchronously from multiple services. This tool is ideal for security tests involving leaked email addresses. #Mosint #EmailOSINT #CyberSecurityTool 📧 Features of Mosint: The tool offers fast email scanning, is lightweight on resources, and features email verification, social media checks, data breach analysis, and more. It outputs results to a JSON file, simplifying data management for security researchers. #EmailSecurity #DataBreachAnalysis 🌐 Future Enhancements: Keskin plans to integrate more services into Mosint and may develop a Mosint API service. This indicates ongoing improvements to the tool's capabilities in email security and data analysis. Mosint is currently available for free on GitHub. #CyberSecurityInnovation #OpenSourceTools 🔍 Other Noteworthy Open-Source Tools: In addition to Mosint, there are several open-source tools worth considering for various cybersecurity needs: ➡️ Vigil: LLM security scanner ➡️ AWS Kill Switch: Incident response tool ➡️ PolarDNS: DNS server for security evaluations ➡️ k0smotron: Kubernetes cluster management ➡️ Kubescape 3.0: Kubernetes security enhancement ➡️ Logging Made Easy: Log management solution from CISA ➡️ GOAD: Practice environment for Active Directory attacks ➡️ Wazuh: XDR and SIEM system ➡️ Yeti: Threat intelligence repository ➡️ BinDiff: Binary file comparison tool ➡️ LLM Guard: Toolkit for securing Large Language Models ➡️ Velociraptor: Digital forensics and incident response tool These tools demonstrate the diverse range of open-source solutions available for enhancing cybersecurity and digital forensics.
#Mosint#EmailOSINT#CyberSecurityTool#EmailSecurity#DataBreachAnalysis#CyberSecurityInnovation#OpenSourceTools#OpenSourceCybersecurity#DigitalForensics#IncidentResponse
0 notes
Text
Email Cyber threat
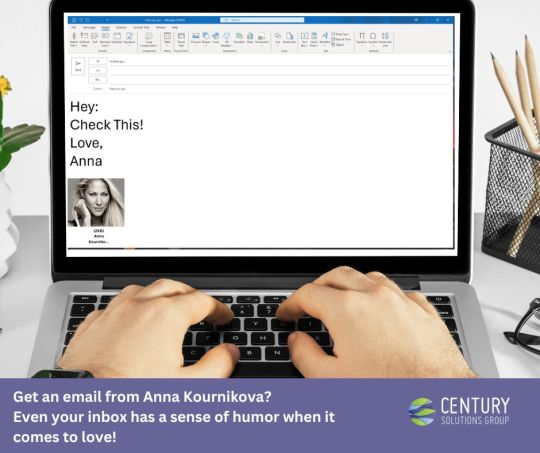
On February 12th, 2001, Emails with a new virus took advantage of Microsoft Corp.'s Outlook software, and circulated among users, preying upon people's attraction to tennis star and model Anna Kournikova. At Century Solutions Group, we've got the perfect Valentine's Day remedy: a dose of Patch Love and a sprinkle of SOC and SIEM magic! 💖🔐 🚨🤖 Say goodbye to cyber heartbreaks with our SOC and SIEM dream team! Like the perfect couple, they work in harmony, detecting threats and swooping in to save the day. This Valentine's Day, don't let your data be a victim of a bad romance. Choose Century Solutions Group – because nothing says "I love you" like a secure, cyber-hug from us! 🌐🛡️ #SecureWithCentury #HappyValentinesDay 🚀💝 Contact us https://okt.to/B5WefR
1 note
·
View note