#IPsec
Text
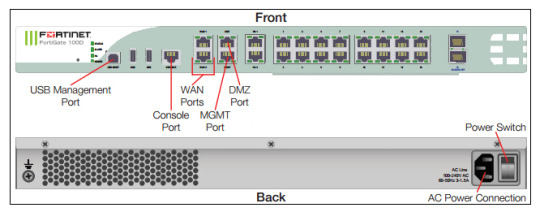
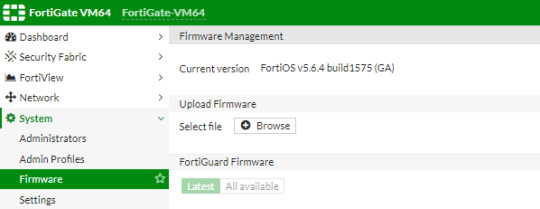
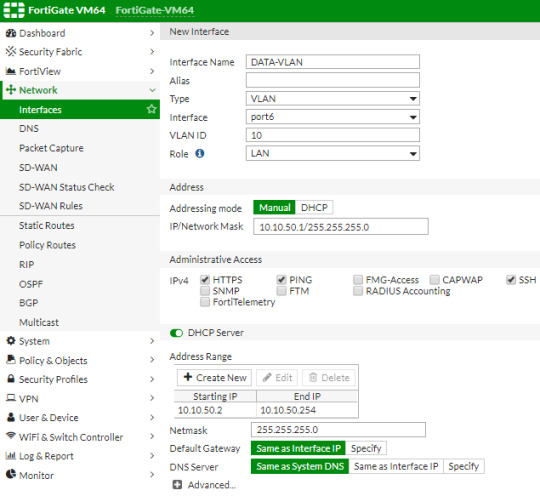
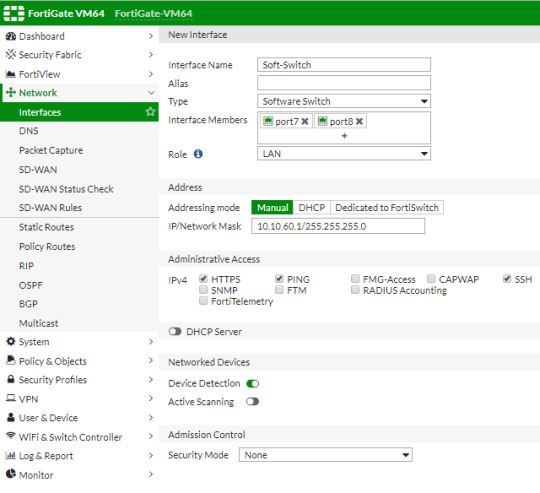
Fortify your cybersecurity arsenal with #Fortigate training. Learn to design, deploy, and manage robust security solutions. Become the guardian of your network's integrity. https://www.dclessons.com/category/courses/fortigate
#fortigate#introduction#firewall#datacenter#practicelabs#training#install#setup#routing#transparentmode#vdom#configure#network#vpn#tunneling#ipsec#tunnel#device#forticare#port#fortiexplorer#nat#mode
0 notes
Text
Mikrotik od Zera - VPN Site-to-Site IPSec IKEv2 PSK

Konfiguracja VPN IPSec IKEv2 między dwoma routerami Mikrotik.
Read the full article
0 notes
Text
Always On VPN RRAS and Stale Connections
Always On VPN administrators may be familiar with an issue that affects Windows Server Routing and Remote Access Service (RRAS) servers, where many stale VPN connections appear in the list of active connections. The issue is most prevalent when using IKEv2, either for the Always On VPN device tunnel or the user tunnel. Typically, this does not cause problems, but some administrators have reported…

View On WordPress
#Always On VPN#avopnn#device tunnel#enterprise mobility#fix#hotfix#IKEv2#IPsec#Microsoft#Mobility#routing and remote access service#RRAS#security#stale connections#update#user tunnel#VPN#Windows#Windows 10#Windows 11#Windows Server#Windows Server 2019#Windows Server 2022
0 notes
Text
Diferencias entre las Vpn PPTP, L2TP y IPSec #Tecnocompras #IA #InteligenciaArtificial
0 notes
Link
As the world becomes increasingly digital, cyber threats continue to pose significant risks to businesses. Managed Service Providers (MSPs) play a critical role in protecting their clients from these threats by choosing the right cybersecurity solutions and implementing effective cybersecurity strategies. In this blog, we will explore the importance and risks of cyber threats for MSPs and their clients, the need for choosing the right cybersecurity tools and strategies for clients, and the steps to take in implementing cybersecurity strategies for SMB clients.
#Secured Remote Services#Managed IT services for small business#Managed It Services#Managed Services Dashboard#Active Directory Domain Services#Virtual Private Networking Services#ipsec vpn security#site-to-site vpn connection
0 notes
Text

#more free openvpn#free vpngate access to vpn servers#unblock your internet#vpn gate server list#l2tp ipsec server list
0 notes
Text

#free vpn config#openvpn access#get ovpn files#get l2tp ipsec from vpn gate#get unblocked internet#unblock your internet
0 notes
Text
Jinal Patel, Co-Founder of VPN Architects presents a talk with Greenpreneur on India's first Green Talk Show
Jinal Patel, Co-Founder of VPN Architects presents a talk with Greenpreneur on India’s first Green Talk Show
About VPN Architects:
Vipul Patel Architects (VPA) was founded in 1994, by Ar. Vipul Patel. VPA has commendably completed various projects in the field of architecture, interior designing, landscape designing, and product designing. Aesthetics and practicality are at par in all our works. The projects are an amalgamation of interesting ideas, great teamwork, and fresh creativity, since the…

View On WordPress
#architects firewall#architecture#architecture c#Architecture design#architecture diagram#architecture in flutter#architecture pattern#architecture vpn ipsec#basic architecture#greenpreneur#interior designing#Jinal Patel#landscape designing#NYIAD#product designing#talk with Greenpreneur#Vipul Patel#Vipul Patel Architects#vpa architects archdaily#vpa architects photos#VPN Architects#vpn architects enterprise#vpn architects logo#vpn network architecture#what is vpn and its advantages
0 notes
Quote
F5は、現地時間5月8日に定例のセキュリティアドバイザリを公開した。「BIG-IP」や関連モジュールなど同社製品に関する複数の脆弱性を明らかにしている。
四半期ごとに公開しているアドバイザリで、CVEベースであわせて13件の脆弱性に対処したことを明らかにしたもの。脆弱性によって対象となる製品は異なるが、同社アプライアンス「BIG-IP」や関連モジュール、VPNクライアントなどに影響がある脆弱性を解消している。
7件については、共通脆弱性評価システム「CVSSv3.1」のベーススコアが「8.0」から「7.4」のレンジにあり、重要度は4段階中、上から2番目にあたる「高(High)」としている。
「BIG-IP Next Central Manager」のAPIにおいて悪意あるSQLが実行可能となる「CVE-2024-21793」「CVE-2024-26026」を修正。
中間者攻撃によりリモートから認証を必要とすることなく「BIG-IP APM」システムとのVPN接続が確立できる「CVE-2024-28883」、仮想サーバ上で「IPsec」を稼働している場合にサービス拒否に陥る「CVE-2024-33608」などへ対処した。
のこる6件については重要度が1段階低い「中(Medium)」とレーティング。またCVE番号は採番されていないが、3件のセキュリティに関するアドバイザリをリリースした。「BIG-IP」のほか、「NGINX App Protect WAF」なども影響を受ける。
今回修正した脆弱性は以下のとおり。
CVE-2024-21793
CVE-2024-25560
CVE-2024-26026
CVE-2024-27202
CVE-2024-28132
CVE-2024-28883
CVE-2024-28889
CVE-2024-31156
CVE-2024-32049
CVE-2024-32761
CVE-2024-33604
CVE-2024-33608
CVE-2024-33612
【セキュリティ ニュース】F5がアドバイザリを公開 - 「BIG-IP」などの複数脆弱性を解消(1ページ目 / 全1ページ):Security NEXT
2 notes
·
View notes
Text
ExpressVPN-- Best VPN for IPTV in Singapore
ExpressVPN is the very best VPN for Cobra IPTV in Singapore that provides an excellent mix of safety and security and speed. With its servers in 94 countries as well as unlimited transmission capacity, you can stream networks via IPTV without inconveniences.
This costs VPN solution features the very best unblocking capability, as well as we had no issue accessing the United States collection of Netflix from abroad and other services without any proxy mistake. It additionally functions fantastic with Hulu, Amazon Prime Video, and Peacock television. You can enjoy all the content of Netflix utilizing ExpressVPN in Singapore with internationally spread out servers. ExpressVPN is likewise helpful for various other set up boxes like Magbox and so on, in fact it is the best VPN for MagBox in Singapore.
youtube
We likewise really did not deal with any constraints while accessing IPTV services like PlutoTV, Iconic Streams, Sportz TV, Beast television, and so on. We easily stream HD top quality web content with no break in transmission or significant problems.
One of the most amazing features of ExpressVPN is that it offers a service called MediaStreamer, a proxy that can bypass any type of regional constraint without the requirement for file encryption. This service can be downloaded and install on all major gadgets, consisting of Xbox, Amazon Fire TVs, routers, and also internet browsers (Chrome, Firefox, as well as Safari). It is likewise the very best VPN for streaming devices like Kodi and Roku, ExpressVPN is the most effective Stremio VPN and also ideal VPN for redbox in Singapore also.
It provides several tunneling protocols, consisting of PPTP, L2TP/IPSec, SSTP, and also OpenVPN, for optimum safety and protection from on-line dangers. Additionally, it is among the best VPN services for streaming in Singapore because of its solid unblocking capabilities.
ExpressVPN uses protection versus any type of DNS leak resulting from VPN misconfiguration. ExpressVPN Network Lock, frequently described as a web kill switch, will close down your whole internet connection in case of a VPN interference. These functions are quite useful in guaranteeing your online personal privacy as well as data defense and additionally proetcts from ISP throttling, the one of the reason it is the very best BT Broadband VPN to utilize in Singapore.
ExpressVPN rate examination information
As for ExpressVPN rate in Singapore, it is the most effective VPN for IPTV for quick streaming. You can anticipate a fast connection while streaming. It taped a download rate of 89.42 Mbps, while its upload rate reached around 84.64 Mbps on a 100 Mbps connection.
The VPN also provides a 24/7 real-time conversation support attribute. It is available night and day to answer your inquiries. If you have any, the service provider will certainly get back to you within secs. You can call them for a reimbursement or termination of your ExpressVPN membership in Singapore.
All these functions come at a rate of SGD8.85/ mo (US$ 6.67/ mo) (Get 49% Off + 3 Months Release on its 12-Month Plan), with a 30-day money-back warranty and also 5-multi logins. There is additionally 24/7 real-time conversation assistance in case you need aid.
3 notes
·
View notes
Text
she IPsec on my packet till I NAT
#i cant get wifi calling to work at home#and ive been trying for days 😭#im not even sure its a NAT issue i think it might be this phone??
3 notes
·
View notes
Text
IPsec额雌饿赐。摩擦得意思。这个vpn免费却打开了十几个软件18193382893不关闭屏幕亮度一直hai网就是没有网我就一直等很久网恢复了。电脑还连不上慢慢来。太吓人了。我没有点一个软件。后台一看100元的手机开了几十个软件。运行还快的很
3 notes
·
View notes
Text
Always On VPN Error 13868
The Internet Key Exchange version 2 (IKEv2) VPN protocol is the protocol of choice for Microsoft Always On VPN deployments where the highest levels of security and assurance are required. However, as I’ve written about in the past, often the default IKEv2 security settings are less than desirable. Before using IKEv2 VPN in a production environment the administrator will need to update these…

View On WordPress
#13868#20227#Always On VPN#AOVPN#certificates#configuration#encryption#error#IKE#IKEv2#IPsec#IPsec policy#Microsoft#Mobility#Network Policy Ser ver#NPS#PKI#policy mismatch#RasClient#security#troubleshooting#VPN#Windows#Windows 10#Windows 11
0 notes
Text
SAN Storage Security: Protecting Your Critical Data Assets
In today's data-driven world, the integrity and security of your data storage systems are paramount. Storage Area Networks (SANs) are at the heart of many enterprise data infrastructures, enabling efficient data storage, management, and retrieval. However, with the growing sophistication of cyber threats, ensuring the security of SAN storage has never been more critical.
This blog post aims to provide IT professionals, data managers, and enterprise businesses with comprehensive insights into SAN storage security. We will explore the importance of SAN security, common threats, best practices for protecting your data assets, and the latest trends in SAN storage security.
Understanding SAN Storage Security
What is SAN?
A Storage Area Network (SAN) is a high-speed network that connects storage devices to servers. Unlike traditional network-attached storage (NAS), which connects directly to the network, SAN operates over high-speed fiber channels or Ethernet, providing block-level storage that appears as direct attached storage to the operating system. This allows for greater flexibility, performance, and scalability, making SANs ideal for enterprise environments handling large volumes of data.
The Importance of SAN Security
Given the central role SANs play in storing and managing critical data, their security is of utmost importance. Unauthorized access, data breaches, and other security incidents can have severe consequences, including data loss, regulatory fines, reputational damage, and operational disruptions. Therefore, implementing robust SAN storage security measures is crucial to safeguarding your organization's most valuable asset—its data.
Common SAN Storage Security Threats
Understanding the potential threats to SAN storage is the first step in developing a comprehensive security strategy. Here are some of the most common security threats to SAN environments:
Unauthorized Access: Without proper access controls, unauthorized users could gain access to sensitive data stored within the SAN.
Data Breaches: Hackers may target SAN storage to exfiltrate sensitive information, leading to data breaches.
Data Corruption: Malicious software or hardware failures can corrupt data stored in SANs, making it unusable.
Insider Threats: Employees or contractors with legitimate access to the SAN may intentionally or unintentionally cause harm.
Ransomware Attacks: Ransomware can encrypt data stored in SANs, rendering it inaccessible until a ransom is paid.
Network Attacks: Attacks targeting the network infrastructure of SANs can disrupt data flow and availability.
Best Practices for SAN Storage Security
To protect your SAN storage from these threats, it is essential to follow best practices tailored to the unique characteristics of SAN environments. Here are some key strategies to consider:
1. Implement Strong Access Controls
Role-Based Access Control (RBAC): Define and enforce roles and permissions to ensure that users have access only to the data and resources necessary for their job functions.
Multi-Factor Authentication (MFA): Use MFA to add an extra layer of security, requiring users to provide two or more verification factors to access the SAN.
Regular Audits: Conduct regular access audits to review and update user permissions, removing unnecessary access rights.
2. Encrypt Data at Rest and in Transit
At-Rest Encryption: Encrypt data stored within the SAN to protect it from unauthorized access, even if physical storage devices are compromised.
In-Transit Encryption: Use encryption protocols such as IPsec or SSL/TLS to secure data as it travels across the network.
3. Implement Network Segmentation
Isolate SAN Traffic: Use VLANs or dedicated network segments to isolate SAN traffic from other network traffic, reducing the attack surface.
Network Firewalls: Deploy firewalls to control and monitor traffic between different network segments, preventing unauthorized access.
4. Regularly Update and Patch Systems
Firmware and Software Updates: Keep SAN hardware and software up to date with the latest security patches and updates to protect against known vulnerabilities.
Automated Patch Management: Use automated tools to ensure timely and consistent application of patches across all SAN components.
5. Monitor and Detect Anomalies
Intrusion Detection Systems (IDS): Implement IDS to monitor SAN traffic for suspicious activity and potential security breaches.
Log Management: Collect and analyze logs from SAN devices and related infrastructure to identify and respond to security incidents.
6. Backup and Disaster Recovery
Regular Backups: Perform regular backups of critical data stored in the SAN to ensure data can be recovered in the event of corruption or loss.
Disaster Recovery Plan: Develop and test a disaster recovery plan that includes SAN storage to quickly restore operations after a security incident.
Emerging Trends in SAN Storage Security
As technology evolves, so do the methods and tools for securing SAN environments. Here are some emerging trends shaping the future of SAN storage security:
1. Artificial Intelligence and Machine Learning
AI and ML are increasingly being used to enhance SAN security by identifying patterns and anomalies that may indicate a security threat. These technologies can automate threat detection and response, improving the overall security posture of SAN environments.
2. Zero Trust Security Model
The Zero Trust Security Model advocates for strict verification of every user and device attempting to access resources within the network. Applying Zero Trust principles to SAN environments can significantly reduce the risk of unauthorized access and data breaches.
3. Blockchain for Data Integrity
Blockchain technology offers a decentralized and tamper-proof method for verifying the integrity of data stored in SANs. By recording transactions and changes in an immutable ledger, blockchain can provide enhanced security and transparency.
4. Quantum Cryptography
While still in its early stages, quantum cryptography promises to revolutionize data encryption by leveraging the principles of quantum mechanics. This technology could provide unparalleled security for data stored in SANs, making it virtually impossible for attackers to crack encryption keys.
Conclusion
SAN storage security is a critical aspect of protecting your organization's data assets. By understanding common threats and implementing best practices such as strong access controls, encryption, network segmentation, regular updates, monitoring, and robust backup strategies, you can significantly enhance the security of your SAN environment.
Stay ahead of emerging trends like AI, Zero Trust, blockchain, and quantum cryptography to ensure your SAN storage remains secure against evolving threats. By prioritizing SAN storage solution security, your organization can confidently manage and protect its critical data assets, maintaining trust with clients, partners, and stakeholders.
For more insights and tips on data storage and security, follow us on LinkedIn and visit our website. Secure your data, secure your future.
0 notes
Text

#get openvpn access for free#vpn for secure internet access#vpngate keys for openvpn#vpn servers#50 vpn servers#l2tp ipsec vpns for free
0 notes
Text
Vpn Packages Online
Safe Net VPN is a one of the best VPN Provider in 2023. VPN constructs a secure tunnel using different protocols between your computer and your desired destination on the internet.
Vpn Packages Online
About Company :- We have optimised streaming servers around the globe. Allowing you to get the most from your existing streaming subscriptions. Blazing fast speeds and avoid censorship.
A VPN is a much more sophisticated tool as compared to a proxy. A VPN not only facilitates you to cope with censorship concerns but it also takes care of your security. VPN constructs a secure tunnel using different protocols (IKEv2 IPsec, OpenVPN, SSTP, SoftEther, WireGuard) between your computer and your desired destination on the internet. That’s not it, A VPN also uses high level encryption to encrypt all the traffic passing through its servers.
Click Here For More Info - https://safenetvpn.com/
Social Media Links :- https://www.instagram.com/safenetvpn/
0 notes