Text
Hackers Hit Amateur Radio Organization American Radio Relay League ARRL

Key Points
- The American Radio Relay League (ARRL), the national association for amateur radio in the United States, has been targeted in a cyber attack that disrupted services and potentially led to a data breach.
- The non-profit organization, founded in 1914, has over 160,000 members and around 100 full-time and part-time staff.
- Services affected by the attack include the ARRL Learning Center and the Logbook of the World, a database for amateur radio contacts and tracking progress toward achievements.
- While credit card information is not stored on ARRL's systems, the organization's database contains members' personal information such as names, addresses, call signs, membership dates, and email preferences.
- ARRL has not confirmed whether the member database was accessed by the attackers, but the possibility cannot be ruled out.
Incident Response and Impact
On Thursday, May 16, the American Radio Relay League (ARRL) informed its members that it was responding to a "serious incident" involving unauthorized access to its network and headquarters systems. The cyberattack led to disruptions in several services offered by the organization, including the ARRL Learning Center and the Logbook of the World, a popular database where amateur radio enthusiasts submit electronic logs of their contacts and track their progress toward various achievements and awards.
In an update shared on Friday, the ARRL provided further details regarding the potential impact of the incident. The organization stated that its database contains personal information of members, such as names, addresses, call signs, membership dates, and email preferences. However, the ARRL clarified that it does not collect or store sensitive information like credit card details or social security numbers on its systems.
While the ARRL has not explicitly confirmed that its member database has been accessed by the attackers, the organization's statement suggests that a data breach is a possibility. The extent of the breach and the potential exposure of members' personal information remain unclear at this stage.
Investigation and Response Efforts
The ARRL has stated that it is working diligently to investigate the incident and restore affected services. However, the organization has not provided specific details about the nature of the attack or whether any ransom demands were made by the attackers.
The ARRL is expected to review and strengthen its data security measures to better protect its systems and safeguard the personal information of its members. The organization may also consider implementing additional security protocols and offering guidance to members on potential risks and preventive measures.
Read the full article
2 notes
·
View notes
Text
Malicious Actors Exploit YouTube for Phishing, Malware, and Scams

YouTube has emerged as a new battleground for cybercriminals to launch phishing attacks, distribute malware, and propagate fraudulent investment schemes, according to a report from security researchers at Avast. The report sheds light on the growing threat of malicious actors exploiting the popular video platform to target unsuspecting users.
Deepfake Videos and Cryptocurrency Scams
Researchers specifically highlighted using Lumma and RedLine malware for phishing, scam landing pages, and malicious software distribution. YouTube acts as a traffic distribution system, directing users to these malicious sites and pages, and supporting scams of varying severity.
Moreover, the report uncovered a concerning rise in deepfake videos on the platform. These realistic but fake videos mislead viewers with fabricated people or events, spreading disinformation. Avast found multiple accounts with over 50 million subscribers each that were compromised and hijacked to spread cryptocurrency scams reliant on deepfake videos. These videos feature fake comments to deceive other viewers and contain malicious links.
Exploitation Tactics on YouTube
The researchers observed five different ways YouTube can be exploited by threat actors:
- Personalized phishing emails to YouTube creators, proposing fake collaboration opportunities to gain trust before sending malicious links.
- Compromised video descriptions containing malicious links, tricking users into downloading malware.
- Hijacking YouTube channels and repurposing them to spread threats like cryptocurrency scams.
- Exploitation of software brands and legitimate-looking domains with fraudulent websites loaded with malware.
- Creating videos using social engineering techniques that guide users to allegedly helpful tools that are malware in disguise.
Protective Measures and Cybersecurity Awareness
Avast credits its scanning capabilities with protecting more than 4 million YouTube users in 2023 and approximately 500,000 users in the first quarter of this year from these threats.
Trevor Collins, a WatchGuard Network security engineer, emphasizes the importance of companies and security leaders preparing their teams and organizations for these threats. "Regular education is essential. Make people aware that there are scammers out there doing this," Collins says. "In addition, train and reassure them that it's OK to notify either their security team or other people within the company if they've gotten an unusual request — for instance, to provide login credentials, move money, or go buy a bunch of gift cards — before acting on it."
As cybercriminals continue to exploit popular platforms like YouTube, individuals and organizations must remain vigilant, prioritize cybersecurity awareness, and implement robust security measures to protect themselves from phishing, malware, and scams.
Read the full article
3 notes
·
View notes
Text
LockBit Ransomware Gang Claims Responsibility for Wichita, KS Cyberattack

The notorious LockBit ransomware gang has claimed responsibility for a devastating cyberattack on the City of Wichita, Kansas, the largest city in the state with a population of nearly 400,000. This ransomware attack has forced the City's authorities to shut down crucial IT systems used for online bill payment, including court fines, water bills, and public transportation.
Wichita, a major cultural, economic, and transportation hub in the region, and home to several aircraft factories, announced the disruptive ransomware attack last Sunday, May 5, 2024. In response, the City's IT specialists promptly shut down computers used in online services to contain the damage and stop the spread of the attack, as stated in their announcement: "This decision was not made lightly but was necessary to ensure that systems are securely vetted before returning to service."
LockBit Ransomware Gang Threatens Data Leak
Earlier today, the LockBit ransomware group added Wichita to its extortion portal, threatening to publish all stolen files on the site by May 15, 2024, unless the City pays the ransom. This unusually quick listing of a ransomware victim, merely three days after the attack, is believed to be in retaliation for the recent international law enforcement operation that named and sanctioned the leader of the LockBit ransomware operation, a 31-year-old Russian national named Dmitry Yuryevich Khoroshev, who uses the online alias "LockBitSupp."
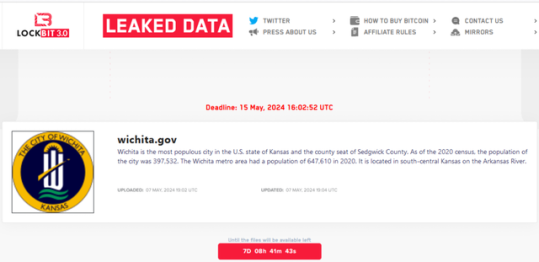
Lockbit Lists the City of Wichita as one of its victims.
Widespread Service Disruptions in Wichita
Meanwhile, Wichita continues to face significant disruptions, with the latest status update indicating that the following services remain unavailable:
- Auto payments for water bills are suspended.
- Public Wi-Fi at certain locations (Airport terminal, Advanced Learning Library, Evergreen, and Walters branches of the Library).
- The online catalog, databases, and some digital services of the Library.
- Email communications through the city network for Library staff.
- Self-service print release stations and self-check stations at the Library.
- Automated materials handler at the Advanced Learning Library.
- Most incoming phone call capability for the Library.
- Wi-Fi and phone services at neighborhood resource centers.
- Public services, including golf courses, parks, courts, and the water district, require residents to pay in cash or by check while online payment platforms are shut down.
Additionally, any Request for Bid, Proposal, or Qualifications with a due date of May 10, 2024, has been deferred until May 17, 2024, and the 'Bid Opening' scheduled for Friday, May 10, 2024, has been canceled.
Public safety services like the Wichita Fire Department (WFD) and Wichita Police Department (WPD) have resorted to using "pen and paper" reports, and the Wichita Transit buses and landfill services can only accept cash payments.
Data Theft and Potential Leak
While the City is still investigating whether data was stolen in the attack, the LockBit ransomware gang is known for stealing data before deploying their encryptors. Therefore, if a ransom is not paid, data will likely be leaked in the future on the ransomware gang's data leak site, exacerbating the already severe impact of this cyberattack on the City of Wichita.
Read the full article
2 notes
·
View notes
Text
Cybersecurity Giant Zscaler Investigates Alleged Data Breach

UPDATE - Zscaler reiterates no impact or compromise to customers, production, or corporate environments. Zscaler and an independent third-party incident response firm continue to work on forensics analysis of the quarantined test environment.
Cybersecurity powerhouse Zscaler launched an investigation on Wednesday after a notorious hacker, known as IntelBroker, announced on a popular cybercrime forum that they were "selling access to one of the largest cyber security companies". Although the hacker's post did not explicitly name the company, they later confirmed in the forum's shoutbox that the target was Zscaler.
IntelBroker has offered to sell "confidential and highly critical logs packed with credentials", including SMTP access, PAuth access, and SSL passkeys and certificates, for $20,000 in crypto. This alarming claim has raised concerns about the potential severity of the alleged breach.
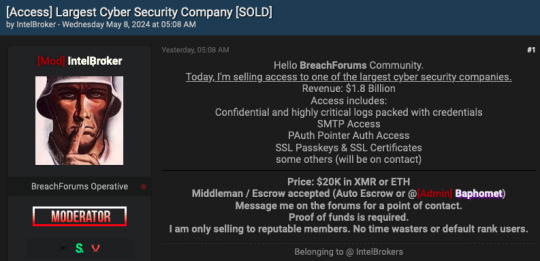
Zscaler's Initial Response and Investigation
Upon learning about the hacker's claims, Zscaler promptly announced the launch of an investigation. A few hours after the investigation commenced, the company announced that it had found no evidence of its customer and production environments being compromised.
Update on Investigation Findings
In its latest update, Zscaler confirmed that its production, customer, and corporate environments were not impacted. The company stated, "Our investigation discovered an isolated test environment on a single server (without any customer data) which was exposed to the internet. The test environment was not hosted on Zscaler infrastructure and had no connectivity to Zscaler's environments. The test environment was taken offline for forensic analysis."
IntelBroker's Recent Claims and Track Record
IntelBroker recently claimed to have stolen US State Department and other government data from the tech firm Acuity. While Acuity confirmed a breach, the company stated that only non-sensitive, old information was compromised. IntelBroker has been making claims about obtaining US government data for more than a year. In several cases, the data has been confirmed to come from third-party service providers, but in some instances, the data was allegedly obtained directly from government systems. However, some of the hacker's claims seemed false or exaggerated.
Read the full article
2 notes
·
View notes
Text
Major Healthcare Provider Ascension Hit by Ransomware Impacting Operations

A cyberattack has disrupted clinical operations at Ascension, a major healthcare nonprofit organization, forcing it to take measures to minimize the impact on patient care. According to a statement from an Ascension spokesperson, the healthcare system, which includes 140 hospitals and 40 senior living facilities across 19 states, has experienced a disruption to its clinical operations.
Ascension has recommended that its healthcare clients temporarily sever network connections to the organization as the incident is being addressed. The nonprofit detected unusual activity on some computer systems on Wednesday, prompting an investigation and notification to the appropriate authorities.
Ensuring Continuity of Patient Care
Ascension has initiated procedures to ensure that patient care delivery continues to be safe and minimally impacted during this disruption. The spokesperson stated, "We continue to assess the impact and duration of the disruption." If sensitive patient data was compromised during the cyberattack, Ascension has pledged to notify those affected.
Prevalence of Ransomware Attacks in Healthcare
The Ascension spokesperson did not immediately respond to follow-up questions on whether the incident involved ransomware, a type of malware that locks computers, allowing hackers to demand a ransom fee. Healthcare providers across the United States have suffered numerous ransomware attacks in recent years, some of which have disrupted patient care and cost healthcare providers millions, if not billions, of dollars.
In February, a ransomware attack on a subsidiary of the healthcare giant UnitedHealth Group caused billing disruptions at pharmacies across the country and threatened to put some healthcare providers out of business, highlighting the severe consequences of such attacks on the healthcare sector.
Read the full article
2 notes
·
View notes
Text
Hackers Exploiting LiteSpeed Cache Plugin Flaw to Hijack WordPress Sites

Cybercriminals are actively exploiting a high-severity vulnerability in the widely-used LiteSpeed Cache plugin for WordPress to take over websites, according to researchers at WPScan. The vulnerability, tracked as CVE-2023-40000 with a CVSS score of 8.3, is an improper input neutralization flaw that allows stored cross-site scripting (XSS) attacks.
LiteSpeed Cache for WordPress (LSCWP) is an all-in-one site acceleration plugin with over 5 million active installations. It features server-level caching and various optimization capabilities. However, the recently disclosed vulnerability enables unauthenticated attackers to escalate privileges and create rogue admin accounts named "wpsupp‑user" and "wp‑configuser" on vulnerable sites.
Once the malicious actors gain administrative access, they have complete control over the compromised WordPress website. Patchstack originally discovered the stored XSS vulnerability in February 2024, which can be triggered through specially crafted HTTP requests.
Surge in Exploitation Attempts Detected
WPScan reported a significant spike in access attempts to a malicious URL on April 2nd and April 27th, likely indicating widespread exploitation efforts. The researchers identified two prominent IP addresses involved in scanning for vulnerable sites: 94.102.51.144 with 1,232,810 requests, and 31.43.191.220 with 70,472 requests.
The vulnerability was addressed by LiteSpeed Technologies in October 2023 with the release of version 5.7.0.1. However, unpatched sites remain at risk of compromise. WPScan has provided indicators of compromise (IoCs) for these attacks, including malicious URLs like https//dnsstartservicefounds.com/service/fphp, https//apistartservicefoundscom, and https//cachecloudswiftcdncom. Additionally, users should watch out for the IP address 45.150.67.235, which has been associated with the malware campaign.
Urgent Patching Recommended
WordPress site owners and administrators are strongly advised to update their LiteSpeed Cache plugin to the latest patched version as soon as possible to mitigate the risk of exploitation and potential website takeover.
Read the full article
2 notes
·
View notes
Text
How Many Times Has the PlayStation Network Been Hacked?

Sony, the renowned multinational conglomerate, has grappled with a series of high-profile data breaches and security incidents over the years, leaving a trail of compromised user data and significant financial repercussions. From state-sponsored cyber attacks to defiant hacker groups, Sony's digital fortresses have been repeatedly breached, exposing the vulnerabilities of even the most prominent corporations in the digital age.
The Most Recent Incidents
In October 2023, Sony notified 6,791 current and former employees that their data had been compromised in a breach that occurred earlier in the year. The intrusion, which took place in late May, was part of the widespread MOVEit attacks that targeted hundreds of companies and government agencies. Sony stated that it detected the breach on June 2 and promptly addressed the situation, asserting that no customer data was implicated.
Just a month prior, in September 2023, Sony found itself investigating another alleged hack. The hacker group RansomedVC claimed to have stolen a staggering 260 GB of proprietary data from Sony's systems, including a PowerPoint presentation and source code files.
However, the credibility of this claim was challenged by another hacker, MajorNelson, who accused RansomedVC of being "scammers" attempting to gain influence. Sony affirmed that it was investigating the matter but refrained from providing further details, stating that no customer data appeared to be implicated in this incident.
The Infamous 2014 Sony Pictures Hack
One of the most notorious cyber-attacks against Sony occurred in 2014 when state-affiliated North Korean hackers, known as the "Guardians of Peace," infiltrated Sony Pictures' networks. This audacious breach resulted in the theft of a staggering 100 terabytes of data, including unreleased films, personal employee information, internal emails, salary details, and a wealth of other sensitive information.
The hackers not only purloined the data but also employed the Shamoon virus to wipe data from Sony's systems, compounding the damage. As the studio grappled with the aftermath, the hackers began leaking portions of the stolen data, including unreleased movies and confidential communications that revealed embarrassing exchanges between employees.
The attack was believed to be retaliation for the planned release of the comedy film "The Interview," which satirized North Korean leader Kim Jong-un. The hackers issued threats, warning of a "bitter fate" for those who watched the movie and ominously referencing the 9/11 terrorist attacks.
Initially, Sony capitulated and pulled the movie, but later reversed course following public pressure, including from then-President Barack Obama, and released the film in a limited theatrical and online format.
The repercussions of the 2014 hack were far-reaching. Employees filed a lawsuit against Sony, alleging economic harm due to the exposure of their personal data. The studio agreed to pay up to $8 million in compensation, fraud protection services, and legal fees. Additionally, the cost of repairing Sony's systems was estimated to be around $35 million.
Earlier Breaches and Security Incidents
Sony's history of data breaches and security incidents extends back over a decade. In 2011, the company faced a series of attacks that exposed the personal details of millions of customers.
In April of that year, hackers accessed the personal data of 77 million Sony PlayStation Network (PSN) users, including names, emails, addresses, birthdates, usernames, and passwords. The incident resulted in a several-week service outage for the PlayStation Network, causing frustration among gamers.
A month later, in May 2011, Sony announced that personal details of 25 million Sony Online Entertainment customers had been stolen, including information about PC games purchased through the system.
Additionally, in June 2011, hackers targeted several Sony Pictures-associated websites, compromising over one million user accounts and exposing music codes and coupons.
Beyond data breaches, Sony has also faced denial-of-service (DDoS) attacks and website defacements. In December 2014, a group called Lizard Squad claimed responsibility for a DDoS attack that took down the PlayStation Network, preventing up to 160 million gamers from accessing the service during the Christmas holiday season.
In August 2017, the hacker group OurMine gained access to Sony PlayStation social media accounts and claimed to have accessed the PlayStation Network database, collecting registration information. While the group positioned itself as a security firm attempting to reach PlayStation employees, its tactics were questionable.
The Road Ahead
Sony's tumultuous history of data breaches and security incidents serves as a sobering reminder of the ever-present cyber threats facing corporations and the need for robust cybersecurity measures. As technology continues to evolve, companies must remain vigilant and proactive in safeguarding their digital assets and protecting the privacy of their customers and employees.
While the financial and reputational costs of these incidents have been substantial, the lessons learned from Sony's experiences could prove invaluable in fortifying the defenses of not only Sony but also other organizations against the relentless onslaught of cybercriminals and state-sponsored actors.
As the digital landscape becomes increasingly complex, Sony's path forward must be paved with heightened security protocols, comprehensive risk assessments, and an unwavering commitment to data protection. Only by learning from the past and embracing a culture of cybersecurity can Sony and other corporations hope to navigate the treacherous waters of the digital age with confidence and resilience.
Read the full article
3 notes
·
View notes
Text
J.P. Morgan Data Breach Affects Over 451,000 Retirement Plan Participants

In a recent regulatory filing with the Office of the Maine Attorney General on April 29, J.P. Morgan Chase Bank revealed that a staggering 451,000 individuals were impacted by a vendor-provided system data breach.
According to the bank, a software issue in this system erroneously granted access to retirement plan participants' records to users who should not have had such privileges. The breach exposed sensitive personal information, including names, social security numbers, mailing addresses, payment and deduction details, as well as bank routing and account numbers for those using direct deposit.
Limited Access, but Potential for Misuse
J.P. Morgan stated that the "incorrect entitlements" were limited to three authorized system users who, as part of their job responsibilities, regularly access this type of information and are obligated to safeguard it. These three users were employed by J.P. Morgan customers or their agents.
Over the period from August 26, 2021, to February 23, 2024, these individuals downloaded a total of 12 reports containing the sensitive data of retirement plan participants.
Prompt Action and Identity Theft Protection
Upon becoming aware of the software issue on February 23, J.P. Morgan promptly corrected the users' access issue, tested it, and applied a software update to resolve the problem. A spokesperson for the bank emphasized, "There is no indication of data misuse," and clarified that the breach was not part of a cyberattack.
As a precautionary measure, J.P. Morgan is offering two years of identity theft protection services through Experian to all affected individuals. The bank has also made its call center available to address participants' questions and concerns regarding the data breach.
Read the full article
2 notes
·
View notes
Text
Russia's APT28 Cyber Espionage Group Targets Czechia, Germany Using Outlook Exploit
Czechia and Germany have exposed a long-running cyber espionage campaign conducted by the notorious Russia-linked APT28 hacking group, drawing harsh criticism from international organizations like the European Union (EU), the North Atlantic Treaty Organization (NATO), the United Kingdom, and the United States.
The Czech Republic's Ministry of Foreign Affairs revealed that certain entities within the country were targeted using a critical Microsoft Outlook vulnerability (CVE-2023-23397), allowing Russian state-sponsored hackers to escalate privileges and potentially gain unauthorized access.
Germany Accuses APT28 of Targeting Social Democratic Party
Similarly, Germany's Federal Government attributed the APT28 threat actor, also known as Fancy Bear, Pawn Storm, and Sofacy, to a cyber attack aimed at the Executive Committee of the Social Democratic Party, exploiting the same Outlook flaw over a "relatively long period" to compromise numerous email accounts.
The targeted industries spanned logistics, armaments, air and space, IT services, foundations, and associations located in Germany, Ukraine, and other European regions. Germany also implicated APT28 in the 2015 cyber attack on the German federal parliament (Bundestag).
Widespread Condemnation of Russia's Malicious Cyber Activities
NATO stated that Russia's hybrid actions "constitute a threat to Allied security," while the Council of the European Union condemned Russia's "continuous pattern of irresponsible behavior in cyberspace."
The UK government described the recent APT28 activity, including targeting the German Social Democratic Party, as "the latest in a known pattern of behavior by the Russian Intelligence Services to undermine democratic processes across the globe."
The US Department of State acknowledged APT28's history of engaging in "malicious, nefarious, destabilizing and disruptive behavior," and reiterated its commitment to upholding a "rules-based international order, including in cyberspace."
Disruption of APT28's Criminal Proxy Botnet
Earlier in February, a coordinated law enforcement action disrupted a botnet comprising hundreds of SOHO routers in the US and Germany believed to have been used by APT28 to conceal their malicious activities, such as exploiting CVE-2023-23397 against targets of interest.
Cybersecurity researchers warn that Russian state-sponsored cyber threats, including data theft, destructive attacks, DDoS campaigns, and influence operations, pose severe risks to upcoming elections in regions like the US, UK, and EU, with multiple hacking groups like APT28, APT44 (Sandworm), COLDRIVER, and KillNet expected to be active.
Securing Critical Infrastructure from Pro-Russia Hacktivist Attacks
Government agencies from Canada, the UK, and the US have released a joint fact sheet to help critical infrastructure organizations secure against pro-Russia hacktivist attacks targeting industrial control systems (ICS) and operational technology (OT) systems since 2022, often exploiting publicly exposed internet connections and default passwords.
The recommendations include hardening human-machine interfaces, limiting internet exposure of OT systems, using strong and unique passwords, and implementing multi-factor authentication for all access to the OT network.
Read the full article
2 notes
·
View notes
Text
CISA Catalogs GitLab Vulnerability (CVE-2023-7028) Enabling Account Hijacking

The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical improper access control vulnerability affecting GitLab Community and Enterprise Editions to its Known Exploited Vulnerabilities (KEV) catalog, citing the risk of account takeovers.
GitLab Account Takeover Flaw Tracked as CVE-2023-7028
The high-severity vulnerability, assigned CVE-2023-7028 with a CVSS score of 10.0, enables attackers to hijack accounts without user interaction by exploiting an account password reset email verification bypass.
GitLab's advisory warns that the following versions are impacted:
- 16.1 before 16.1.6
- 16.2 before 16.2.9
- 16.3 before 16.3.7
- 16.4 before 16.4.5
- 16.5 before 16.5.6
- 16.6 before 16.6.4
- 16.7 before 16.7.2
Patches Available, Agencies Ordered to Remediate by May 22
GitLab has released security updates 16.7.2, 16.5.6, and 16.6.4 to address the flaw, with backported patches for 16.1.6, 16.2.9, and 16.3.7. Self-hosted users are urged to review logs for exploitation attempts targeting the /users/password path with multiple email addresses.
Per BOD 22-01, CISA has mandated federal agencies remediate this vulnerability by May 22, 2024, to mitigate the significant risk of known exploits. Private organizations are also strongly recommended to review the KEV catalog and patch their GitLab instances promptly.
Widespread Exposure Persists Despite Available Fixes
Despite the availability of patches, researchers at ShadowServer report thousands of vulnerable GitLab instances remain unpatched, predominantly in the United States, Germany, and Russia, highlighting the urgent need for prompt remediation of this account hijacking vulnerability.
Read the full article
2 notes
·
View notes
Text
Massive Malware Campaigns Infiltrate Docker Hub, Deploying Millions of Malicious Containers

JFrog's security research team has uncovered three large-scale malware campaigns infiltrating Docker Hub, a platform facilitating Docker image development, collaboration, and distribution. These campaigns have deployed millions of malicious "imageless" containers, exploiting Docker Hub's community features.
Docker Hub hosts a staggering 12.5 million repositories, but according to JFrog, approximately 25% serve no useful functionality. Instead, they act as vehicles for spam, pirated content promotion, and malware dissemination, posing a significant threat to unsuspecting users.
Exploiting Community Features: Malicious Documentation Pages
The attack on Docker Hub exploited its community features, allowing users to publish repositories with only documentation pages, devoid of actual container images. Disguised as legitimate content, these documentation pages lead users to phishing and malware-hosting websites, putting their systems at risk.
Three Major Malware Campaigns Identified
Through an analysis of Docker Hub image creation patterns over the past five years, the research team identified over four million imageless repositories, constituting 37% of all public repositories. Further investigation revealed three main malware campaigns:
- Downloader Campaign: Offers pirated content and game cheats as bait.
- eBook Phishing Campaign: Lures users with free eBook downloads to steal credit card information.
- Website Campaign: Characterized by randomly generated repositories with benign descriptions.
Each campaign employed distinct tactics to evade detection, such as URL shorteners and open redirect bugs. The payloads of these campaigns, predominantly Trojans, communicated with command-and-control (C2) servers to download additional malware and execute persistent tasks on infected systems.
Call for Enhanced Moderation and Community Involvement
These findings highlight the need for enhanced moderation on Docker Hub and greater community involvement in detecting and mitigating malicious activity. Andrey Polkovnichenko, security researcher at JFrog, warned, "The most concerning aspect of these three campaigns is that there is not a lot that users can do to protect themselves at the outset other than exercising caution."
Polkovnichenko added, "These threat actors are highly motivated and are hiding behind the credibility of the Docker Hub name to lure victims. As Murphy's Law suggests, if malware developers can exploit something, it inevitably will be, so we expect that these campaigns can be found in more repositories than just Docker Hub."
Read the full article
2 notes
·
View notes
Text
R Programming Language Exploit (CVE-2024-27322) Allows Arbitrary Code Execution
CVE-2024-27322 RDS Flaw Exposes R Packages to Supply Chain Attacks
A severe security vulnerability in the R programming language has been disclosed, which could be exploited by malicious actors to create a malicious RDS (R Data Serialization) file that results in arbitrary code execution when loaded and referenced.
The flaw, identified as CVE-2024-27322, "involves the use of promise objects and lazy evaluation in R," according to a report from AI application security company HiddenLayer.
RDS: The R Programming Language's Pickle Equivalent
RDS, similar to pickle in Python, is a format used to serialize and save the state of data structures or objects in R, an open-source programming language widely used in statistical computing, data visualization, and machine learning.
The serialization process – serialize() or saveRDS() – and deserialization – unserialize() and readRDS() – is also leveraged when saving and loading R packages.
Root Cause: Arbitrary Code Execution on Deserialization
The root cause behind CVE-2024-27322 is that it could lead to arbitrary code execution when deserializing untrusted data, thus leaving users exposed to supply chain attacks through specially crafted R packages.
An attacker seeking to exploit this vulnerability could leverage R packages' use of the RDS format to save and load data, causing automatic code execution when the package is decompressed and deserialized.
Supply Chain Attack Vector via R Package Repositories
"R packages are vulnerable to this exploit and can, therefore, be used as part of a supply chain attack via package repositories," security researchers Kasimir Schulz and Kieran Evans warned. "For an attacker to take over an R package, all they need to do is overwrite the RDX file with the maliciously crafted file, and when the package is loaded, it will automatically execute the code."
https://www.youtube.com/watch?v=33Ybpw99ehc
Patch Released in R Version 4.4.0
The security defect has been addressed in R version 4.4.0 released on April 24, 2024, following responsible disclosure.
HiddenLayer elaborated, "An attacker can exploit this by crafting a file in RDS format that contains a promise instruction setting the value to unbound_value and the expression to contain arbitrary code. Due to lazy evaluation, the expression will only be evaluated and run when the symbol associated with the RDS file is accessed."
"Therefore if this is simply an RDS file, when a user assigns it a symbol (variable) to work with it, the arbitrary code will be executed when the user references that symbol. If the object is compiled within an R package, the package can be added to an R repository such as CRAN. The expression will be evaluated and the arbitrary code run when a user loads that package."
Read the full article
2 notes
·
View notes
Text
Cisco Exposes State-Sponsored Hackers Exploiting Cisco Firewall Zero-Days CVE-2024-20359

Cisco has uncovered a sophisticated state-backed hacking group exploiting two previously unknown vulnerabilities in Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls since November 2023. The malicious cyber espionage campaign, dubbed "ArcaneDoor," has successfully infiltrated government networks worldwide, compromising crucial security infrastructure.
Weaponizing Zero-Day Exploits for Cyber Espionage
The threat actors, identified as UAT4356 by Cisco Talos and STORM-1849 by Microsoft, leveraged two zero-day vulnerabilities—CVE-2024-20353 (denial of service) and CVE-2024-20359 (persistent local code execution)—to breach Cisco firewalls. These previously undisclosed security flaws allowed cybercriminals to deploy sophisticated malware implants, granting them persistent access and remote control over compromised devices.
One implant, dubbed "Line Dancer," is an in-memory shellcode loader capable of executing arbitrary payloads, disabling logging mechanisms, and exfiltrating captured network traffic. The second implant, a persistent backdoor named "Line Runner," incorporates multiple defense evasion techniques to evade detection while enabling the attackers to execute arbitrary Lua code on the hacked systems.
Hallmarks of State-Sponsored Cyber Threats
Cisco's analysis reveals that the threat actor's bespoke tooling, espionage focus, and in-depth knowledge of targeted devices are hallmarks of a sophisticated state-sponsored actor. The malicious actors exploited their access to exfiltrate device configurations, control logging services, and modify authentication mechanisms for lateral movement within compromised environments.
Urgent Call for Mitigation and Enhanced Security
In response to this severe cyber threat, Cisco has released security updates to address the two zero-day vulnerabilities and strongly recommends that customers promptly upgrade their ASA and FTD devices to the latest patched software versions. Administrators are also urged to monitor system logs for suspicious activity, implement strong multi-factor authentication, and ensure devices are securely configured and logged to a centralized location.
As state-sponsored cyber threats continue to escalate, organizations must prioritize proactive security measures, regular patching, and robust incident response strategies to safeguard critical infrastructure and sensitive data. Complacency in the face of such advanced cyber espionage campaigns can devastate national security and organizational resilience.
Read the full article
2 notes
·
View notes
Text
Russian Hackers Likely Behind Muleshoe, Texas Town's Water System Attack

The cybersecurity firm, Mandiant, revealed on Wednesday that Russian hackers were likely responsible for the water tank overflow incident that occurred in Muleshoe, Texas, back in January. The incident, which saw a torrent of water spewing from the town's water tank, was initially contained within an hour. Still, it has raised serious concerns about the vulnerability of critical infrastructure systems to cyber attacks.
Sandworm: A Formidable Russian Hacking Group
Mandiant, owned by tech giant Google, attributed the attack to Sandworm, a Russian hacking group known for its dynamic and operationally mature capabilities. According to the report, Sandworm is actively engaged in the full spectrum of espionage, attack, and influence operations, making it a formidable threat actor.
Security experts believe Sandworm is likely connected to the Russian spy agency, GRU. Unlike most state-backed threat groups that specialize in specific areas, Sandworm stands out for its ability to unify various capabilities into a comprehensive package.
Cyber Army of Russia Reborn Claims Responsibility
A group calling itself the Cyber Army of Russia Reborn, which Mandiant has linked to Sandworm, has claimed credit for the Muleshoe attack. They posted a video on Telegram showing their manipulation of the town's water system, demonstrating how they overpowered it and reset the controls, as reported by The Washington Post.
If validated, this would mark the first attack on a public American infrastructure system by this group, according to the Post. US officials have previously blamed Iran for a separate attack on water systems in Pennsylvania last November.
Muleshoe's Water Tank Overflow and Sandworm's History
Ramon Sanchez, Muleshoe's city manager, confirmed to CNN that the city's water tank overflowed for approximately 30 to 35 minutes during the incident. Authorities have previously blamed Sandworm, which has operated under different names over the years, for various attacks worldwide, including on Ukraine's power grid and the 2018 Olympic Games in South Korea.
In 2020, the US Department of Justice charged six members of the group with crimes related to their attacks, with one member allegedly involved in disrupting the 2016 US presidential elections. The Justice Department also accused the men of creating the NotPetya virus, which caused $10 billion in damage to computers worldwide, shutting down the power grid in Ukraine, and taking down the computer systems of a chain of Western Pennsylvania hospitals.
Read the full article
0 notes
Text
UnitedHealth Confirms Ransomware Attack Led to Massive Theft Was Larger Than Expected

The healthcare industry giant UnitedHealth Group acknowledged that a ransomware attack on its subsidiary, Change Healthcare, earlier this year resulted in a massive theft of private medical data belonging to millions of Americans. The healthcare data breach has raised serious concerns about cybersecurity and the protection of sensitive personal information.
According to UnitedHealth's statement on Monday, a notorious ransomware gang successfully infiltrated Change Healthcare's systems and stole files containing personal data and protected health information that may "cover a substantial proportion of people in America." The extent of the data breach is still being investigated, and UnitedHealth warned that the review process is "likely to take several months" before affected individuals can be notified.
Change Healthcare: A Central Hub for Medical Data Processing
Change Healthcare plays a critical role in the healthcare ecosystem, processing insurance claims, billing, and other administrative tasks for hundreds of thousands of hospitals, pharmacies, and medical practices across the United States. As a result, the company has access to a vast trove of health information on approximately half of all Americans, making the data breach particularly alarming.
Ransom Paid to Protect Patient Data
In a bold move to safeguard the stolen data, UnitedHealth confirmed that it paid a ransom to the cybercriminals responsible for the attack. Tyler Mason, a UnitedHealth spokesperson, stated, "A ransom was paid as part of the company's commitment to do all it could to protect patient data from disclosure." However, the company did not disclose the exact amount paid.
While UnitedHealth has not yet seen evidence of doctors' charts or complete medical histories being stolen, the investigation is still ongoing. The healthcare data breach has raised concerns about the potential misuse of sensitive personal information, including medical records and financial data.
Amidst the fallout from the massive healthcare data breach, UnitedHealth's CEO Andrew Witty, who pocketed a staggering $21 million in total compensation for the full year of 2022, is scheduled to face questioning from House lawmakers on May 1st. Witty's multi-million dollar pay package is likely to come under scrutiny, given the company's failure to adequately protect the sensitive medical data of millions of Americans entrusted to its care.
Read the full article
0 notes
Text
Akira Ransomware Breaches Over 250 Global Entities, Rakes in $42 Million
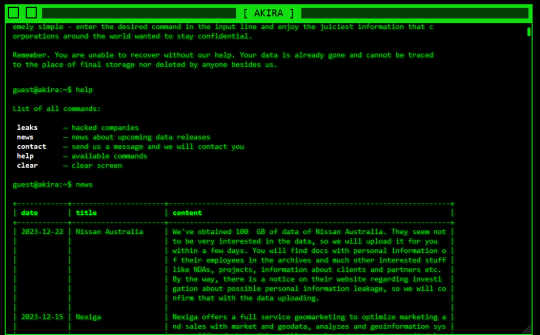
A joint cybersecurity advisory issued by CISA, FBI, Europol, and the Dutch NCSC-NL has uncovered the staggering scale of the Akira ransomware campaign. Since early 2023, the nefarious Akira operators have compromised more than 250 organizations worldwide, extorting a whopping $42 million in ransom payments.
Akira's Prolific Targeting Across Industries
The Akira ransomware group has been actively infiltrating entities across diverse sectors, including education, finance, and real estate. Staying true to the double extortion playbook, the threat actors exfiltrate sensitive data before encrypting the victims' systems, amplifying the pressure for a ransom payment.
Early Akira versions, coded in C++, appended the .akira extension to encrypted files. However, from August 2023 onward, certain attacks deployed Megazord, a Rust-based variant that encrypts data with the .powerranges extension. Investigations reveal the perpetrators interchangeably using both Akira and Megazord, including the updated Akira_v2.
Initial Access and Privilege Escalation
The cybercriminals exploit various entry points, such as unprotected VPNs, Cisco vulnerabilities (CVE-2020-3259 and CVE-2023-20269), RDP exposures, spear phishing, and stolen credentials. Post-compromise, they create rogue domain accounts, like itadm, to elevate privileges, leveraging techniques like Kerberoasting and credential scraping with Mimikatz and LaZagne.
Disabling Security Controls and Lateral Movement
To evade detection and facilitate lateral movement, Akira operators disable security software using tools like PowerTool to terminate antivirus processes and exploit vulnerabilities. They employ various tools for reconnaissance, data exfiltration (FileZilla, WinRAR, WinSCP, RClone), and C2 communication (AnyDesk, Cloudflare Tunnel, RustDesk, Ngrok).
Sophisticated Encryption
The advisory highlights Akira's "sophisticated hybrid encryption scheme" combining ChaCha20 stream cipher with RSA public-key cryptography for efficient and secure encryption tailored to file types and sizes.
As the Akira ransomware campaign continues to wreak havoc, the joint advisory provides crucial indicators of compromise (IoCs) to help organizations bolster their defenses against this formidable threat.
Read the full article
2 notes
·
View notes
Text
Stealthy RedLine Malware Variant Leverages Lua Bytecode for Advanced Attacks

McAfee Uncovers Sophisticated Information Stealer Exploiting GitHub Repositories
Cybersecurity researchers at McAfee Labs have uncovered a new and sophisticated variant of the notorious RedLine Stealer malware that employs Lua bytecode for enhanced stealth and evasion capabilities. This advanced information-stealing malware targets gamers by masquerading as game cheats, distributed through ZIP archives hosted on official Microsoft repositories on GitHub.
First documented in March 2020, RedLine Stealer is a prevalent off-the-shelf malware strain capable of harvesting sensitive data from cryptocurrency wallets, VPN software, web browsers, and more. Over the years, various threat actors have co-opted this malware into their attack chains, making it a widespread threat across multiple continents.
Abusing Trust in GitHub Repositories
The latest infection sequence identified by McAfee abuses GitHub by uploading malware-laden payloads in the form of ZIP archives to two of Microsoft's official repositories: the C++ Standard Library (STL) and vcpkg. This technique exploits the trust associated with these repositories, allowing threat actors to distribute malware more effectively. The ZIP files, disguised as game cheats named "Cheat.Lab.2.7.2.zip" and "Cheater.Pro.1.6.0.zip", are no longer available for download from the Microsoft repositories.
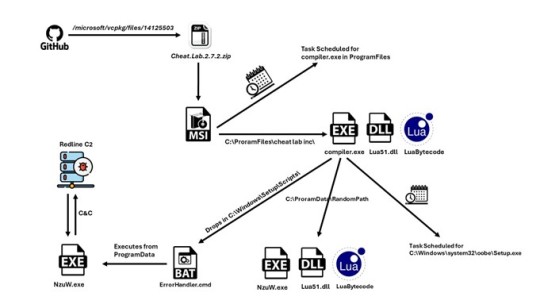
Stealthy Execution and Persistence
The ZIP archives contain an MSI installer that runs the malicious Lua bytecode, providing a stealthy execution method by avoiding easily recognizable scripts. The installer also sets up persistence on the host using a scheduled task and drops a CMD file to run the malware under a different name, enhancing evasion capabilities.
Once executed, the malware functions as a backdoor, communicating with a command-and-control (C2) server over HTTP, which has been previously associated with RedLine Stealer. It can carry out tasks fetched from the C2 server, such as taking screenshots, and exfiltrate the results back to the server, compromising sensitive information.
This campaign highlights the evolving tactics employed by threat actors, including the abuse of trusted repositories and the use of stealthy execution methods like Lua bytecode. As the threat landscape continues to evolve, organizations and individuals must remain vigilant and implement robust security measures, including regular software updates, employee awareness training, and the deployment of advanced security solutions.
Read the full article
0 notes