#SNMP
Text
BLIIoT | New Multi-Protocol PLC Gateway BL104 Converts PLC to Cloud/Server for Remote Monitoring

Introduction
With the rapid development of Industry 4.0, it is deeply recognised that real-time, reliable and secure data transmission is crucial in industrial production and life. In this context, high-performance industrial automation PLC data transmission solutions - protocol conversion gateway came into being, widely used in industrial automation systems, PLC remote monitoring and IoT application environment.
BLIIoT always insists on the core of the user's needs, and constantly expands its applications in a variety of industrial fields. Recently, we have developed a new series of BLIIoT industrial PLC protocol gateways, which not only have excellent stability and anti-interference ability, but also explore the application of industry segments, aiming to bring users a new experience of industrial automation data acquisition and conversion.
Product Description
PLC Gateway BL104 is a specially developed for PLC connect MQTT and OPC UA system and remote PLC program uploading and downloading debugging.
The downlink protocol supports PLC protocols such as Mitsubishi, Siemens, Omron, Delta, Schneider, etc. and Modbus protocol.
The uplink protocol supports Modbus RTU, Modbus TCP, MQTT and OPC UA, access to Cloud, Server, SCADA, MES, ERP and other systems.
PLC Gateway BL104 hardware interfaces include 2 or 6 RS485/RS232 serial ports, 2 network ports and 1 WiFi wireless transmission interface, which realises seamless communication between PLC and OPC UA system.
The PLC gateway BL104 has an industrial-grade design to ensure reliability in harsh environments. BL104 is suitable for industrial automation systems, PLC remote monitoring and IoT applications.The PLC gateway BL104 connects to the future of the industry and provides users with a trusted, low-cost, stable and reliable PLC to Modbus, MQTT and OPC UA solution.

By using its own patented rail-clip technology, the installation process is simplified and the utility of the gateway is ensured.
Product features
Supported protocols: Downlink protocol: Modbus RTU, Modbus TCP, Mitsubishi, Siemens, Omron, Delta, Schneider and other mainstream PLC protocols.Uplink protocol: Modbus RTU, Modbus TCP, MQTT, SNMP and OPC UA.
Hardware interface: 6*RS485/RS232 serial ports: The serial ports are independent of each other. Each serial port parameter can be set to collect different protocols. The serial port can also set the master-slave relationship independently. It can be configured as either a master station or a slave station.2*network ports: used for data collection and forwarding. The LAN port has a routing function and provides a channel for other devices to connect to the external network.1*4G or WiFi wireless transmission interface: Provides diverse communication options to adapt to different industrial environment need
Data security:Support data TSL/SSL, X.509 certificate, SNMPV1/V2, key encryption and other security gateway functions.
Remote Configuration Support: Support remote PLC programming and program uploading and downloading, saving travelling costs and improving service response speed. Support remote configuration, providing users with convenient management and monitoring methods, no longer need to visit engineers, saving maintenance costs.
Product Size: L x W x H: 30 x 83 x 110mm


Safety and Stability:
Industrial-grade design: Durable shell material meets industrial environment requirements.
Stability: Efficient communication protocol conversion ensures stable operation of the system.
Environmental adaptation:
Operating temperature range: -40~80℃, adapting to various industrial environments. Protection grade: IP30, ensuring the reliability of the equipment in harsh environments.
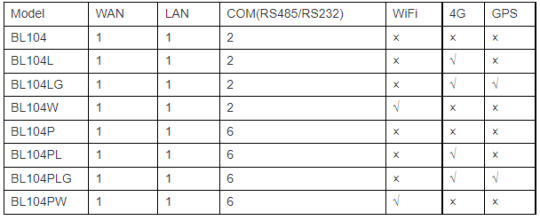
Model List
Application scenarios
Meet the needs of PLC protocol to Modbus MQTT OPC UA in industrial automation and industrial IoT scenarios.

More information about BLIIoT New PLC to Modbus MQTT OPC UA Gateway BL104: https://www.bliiot.com/industrial-iot-gateway-p00415p1.html
#PLC Gateway#Industrial Automation#IoT#Modbus#MQTT#OPC UA#SNMP#Siemens#Omron#Schneider#Delta#mitsubishi
0 notes
Text
Data Center Remote Monitoring with BLIIoT SNMP I/O Module

Data centers are at the heart of operation for any enterprise that utilises an IT infrastructure.
Real time remote data center monitoring becomes paramount when enterprises want to be the first to know about potential issues before they become bigger problems.
Factors that Influence the Monitoring of Environments
Power availability and consumption, such as generators running status and output voltage, current, frequency, water temperature, oil level, oil pressure and other parameters.
Data center environment, such as air conditioner running status, water leak, temperature and humidity, fire, etc.
What can BLIIoT SNMP I/O Module offer for data center monitoring?
Comes with digital inputs and outputs, analog inputs and outputs, RS-485 serial port, Ethernet port, the I/O module can be connected to a variety of sensors, detectors to collect data and control devices.
Support Modbus, MQTT protocols to communicate with control panel, monitoring systems, servers and cloud platforms for remote measurement and monitoring equipment status and linkage control equipment.
Support SNMP V1/V2 protocol, so users can monitoring and managing I/O modules on the network management systems.
Set power and environmental thresholds on collected data and receive alerts.
More information view:https://www.bliiot.com/ethernet-io-modules-p00258p1.html
0 notes
Text
Configuración y Monitoreo de Cámara IP Hikvision con Zabbix mediante SNMPv3
La configuración y monitoreo de una cámara IP Hikvision con Zabbix mediante SNMPv3 es importante porque permite a un administrador de red supervisar y monitorear el rendimiento y el estado de la cámara IP de manera remota. Con Zabbix, es posible configurar alertas y notificaciones para que se envíen cuando se produzca un evento determinado, como una caída de la red o un problema de rendimiento.…

View On WordPress
0 notes
Text
SNMP (Simple Network Management Protocol)
SNMP (Simple Network Management Protocol)
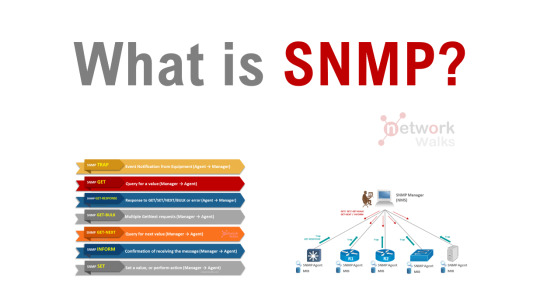
What is SNMP?
SNMP (Simple Network Management Protocol) is a Layer-7 protocol for collecting and organizing information about managed devices on IP networks and for modifying that information to change device behavior. It allows devices to communicate even if the devices are different hardware and run different software.
There are two major types of devices in SNMP, they are Managed devices which…
View On WordPress
1 note
·
View note
Text
after a certain point acronyms become an active impediment to communication
#i don't know what OCSP is#i don't know what CIRT is#i certainly don't know what SNMP is#and if somebody uses all of those in the same sentence there is a negative possibility that I will be able to figure out what they mean
1 note
·
View note
Text
ESXI SNMP Servisi Başlatılamadı. The Service Snmpd Failed to Start
ESXI SNMP Servisi Başlatılamadı.. The Service Snmpd Failed to Start Hatası ve Çözümü makalede..
Çeşitli izleme araçlarının yönetimini sağlamak ve ön izlemede bulunmak için esxi snmp servisini çalıştırmamız gerekebilir. Bunu sağlarken host ekranı üzerinden snmp servisini başlatmak istersek hata verdiğini göreceksiniz. Bu makalede esxi snmp servis başlatılamadı konusunu işleyeceğiz.
SSH Aktif Edilir
İşlem sağlayabilmemiz için ilk öncelikle host üzerinden ssh aktif edilmelidir. Bu ayarı…

View On WordPress
0 notes
Text
Synology netatalk snmp

#Synology netatalk snmp install
#Synology netatalk snmp software
#Synology netatalk snmp code
Update for SkyNAS is now available in Affected Products. Synology-SA-22:06 Netatalk (Severity: Critical). Why isn't the synology reporting via SNMP. and set the IP address and MIB as APCC but am not sure where to find the SNMP version or community. The SMART status is reporting good on both the Synology and my monitoring software.
#Synology netatalk snmp software
The issue is, the software I am using to monitor the device over SNMP says everything is A-OK. Synology has warned customers that some of its network-attached storage (NAS) appliances are exposed to attacks exploiting multiple critical Netatalk vulnerabilities. Both firms are developing patches to address the issues. Update for DSM 6.1 and DSM 5.2 are now available in Affected Products. It is being reported that it has bad sectors. Users of Synology and QNAP NAS equipment are being warned about major Netatalk vulnerabilities in their operating systems. Update for SRM 1.2 is now available in Affected Products. Update for VS960HD is now available in Affected Products. Users of Synology and QNAP network-attached storage (NAS) devices are advised to be on the lookout for patches for several critical vulnerabilities affecting Netatalk, an open-source implemention. Update for DSM 6.2 is now available in Affected Products.
#Synology netatalk snmp code
A remote unauthenticated attacker can leverage this vulnerability to achieve arbitrary code execution. This is due to lack of bounds checking on attacker controlled data. Network UPS Support - DiskStation now supports connecting to SNMP (Simple Network Management Protocol) UPS devices or network management cards, allowing your. Netatalk before 3.1.12 is vulnerable to an out of bounds write in dsi_opensess.c.If it is successful, you will see a bunch of numbers. snmpwalk -v 2c -c your-community-passphrase 192.168.1.20. CVSS3 Vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Ensure device SNMP is enabled, check community passphrase, check which snmp protocol, v1, v2c, v3 is in use, and perform a snmpwalk on it.In addition, entering Name for Controller A and Controller B, Location, and Contact helps you identify your Synology Unified. A vulnerability allows remote attackers to execute arbitrary code via a susceptible version of Synology Diskstation Manager (DSM) and Synology Router Manager (SRM). Habilitar servicio SNMP Marque Habilitar servicio SNMP y siga estos pasos. En la actualidad, se admiten los protocolos SNMPv1, SNMPv2c y SNMPv3. If you need immediate assistance, please contact Synology technical support via. To enable SNMP privacy: Tick Enable SNMP privacy. El servicio SNMP (en Panel de control > Terminal y SNMP > SNMP) que permite a los usuarios controlar Synology NAS con el software de administración de red.
#Synology netatalk snmp install
Please manually download and install version 6.1.7-15284-3. Update for DSM 6.2 is now available in Affected Products.A vulnerability allows remote attackers to execute arbitrary code via a susceptible version of Synology Diskstation Manager (DSM) and Synology Router Manager (SRM). Update for SRM 1.3 is now available in Affected Products. Update for DSM 7.0 is now available in Affected Products. In environments where AFP is still needed, setting up firewall rules to only allow trusted clients to connect over AFP (port 548) can be used as temporary mitigation. We recommend using SMB protocol instead when connecting from macOS.įor Synology systems not yet upgraded to DSM 7.1-42661-1 or newer, administrators can disable "AFP service" to mitigate this specific vulnerability. This service has been disabled by default since DSM 7.0. I was able to turn on SNMP on the main device, but I'm unclear if the other one automatically gets the same settings change (doesn't really make sense as it's located somewhere else, so the Location field needs to be set differently). We've just setup HA on our Synology devices, and are wondering how SNMP is going to work. Netatalk provides file access through AFP (Apple Filing Protocol) on DSM. It's sad that this thread has no responses. Multiple vulnerabilities allow remote attackers to obtain sensitive information and possibly execute arbitrary code via a susceptible version of Synology DiskStation Manager (DSM) and Synology Router Manager (SRM).

0 notes
Text
Security in Project (3/9+)
3\\ HARDEING GUIDE
Ganti password default
Hapus akun yang ngga kepake
Ganti default certificates / encryption keys
Hapus vulnerable settings (contohnya SSLv2/v3,snmp v1/v2, telnet etc.)
Gunakan secara specific product security settings
Hapus unused settings alias setting-setting yang ngga kepake
Sesuaikan subcomponents hardeningnya coba Security benchmark
Tambahkan Logs & sesuaikan NTP configuration
Perhatikan pula Connection ke external user directory (AD, ldap). Kalau disini, pakai AD jadi komputer yang diluar Domain harus dapt ijin khusus.
Terakhir, perhatikan Administration flows encryption. Bagian ini susah susah gampang. Misal nih, pake encrytion external. Harus nyesuaikan ama server juga. Apalagi kalau literaturnya dikit.

3 notes
·
View notes
Text
Centreon sysName Cross-Site Scripting Remote Code Execution Vulnerability [CVE-2023-51633]

CVE number = CVE-2023-51633
This vulnerability allows remote attackers to execute arbitrary code on affected installations of Centreon.
User interaction is required to exploit this vulnerability.
The specific flaw exists within the processing of the sysName OID in SNMP.
The issue results from the lack of proper validation of user-supplied data, which can lead to the injection of an arbitrary script.
An attacker can leverage this vulnerability to execute code in the context of the service account.
This issue is fixed in Centreon-web versions 22.10.15, 23.04.10 and 23.10.1https://github.com/centreon/centreon/pull/2464
Read the full article
0 notes
Text
BLIIoT | New PLC Gateway BL103 Developed for PLC to OPC UA Server and Remote PLC Programme Uploading and Downloading Debugging
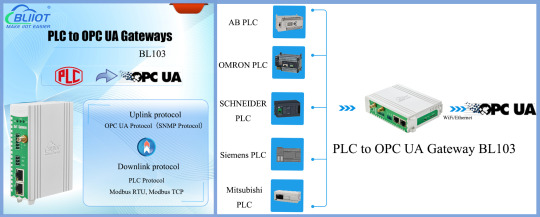
Introduction
With the rapid development of Industry 4.0, it is deeply recognised that real-time, reliable and secure data transmission is crucial in industrial production and life. In this context, high-performance industrial automation PLC data transmission solutions - protocol conversion gateway came into being, widely used in industrial automation systems, PLC remote monitoring and IoT application environment.
BLIIoT always insists on the core of the user's needs, and constantly expands its applications in a variety of industrial fields. Recently, we have developed a new series of BLIIoT industrial protocol gateways, which not only have excellent stability and anti-interference ability, but also explore the application of industry segments, aiming to bring users a new experience of industrial automation data acquisition and conversion.
Product Description
PLC to OPC UA Gateway BL103 is a specially developed for PLC connect OPC UA system and remote PLC program uploading and downloading debugging.
The downlink protocol supports PLC protocols such as Mitsubishi, Siemens, Omron, Delta, Schneider, etc. and Modbus protocol.
The uplink protocol supports OPC UA, access to SCADA, MES, ERP and other systems.
PLC to OPC UA Gateway BL103 hardware interfaces include 2 or 6 RS485/RS232 serial ports, 2 network ports and 1 WiFi wireless transmission interface, which realises seamless communication between PLC and OPC UA system.
The PLC to OPC UA gateway BL103 has an industrial-grade design to ensure reliability in harsh environments. BL103 is suitable for industrial automation systems, PLC remote monitoring and IoT applications.The PLC to OPC UA gateway BL103 connects to the future of the industry and provides users with a trusted, low-cost, stable and reliable PLC to OPC UA solution.

By using its own patented rail-clip technology, the installation process is simplified and the utility of the gateway is ensured.
Product features
Supported protocols: Downlink protocol: Modbus RTU, Modbus TCP, Mitsubishi, Siemens, Omron, Delta, Schneider and other mainstream PLC protocols.Uplink protocol: OPC UA.
Hardware interface: 6*RS485/RS232 serial ports: The serial ports are independent of each other. Each serial port parameter can be set to collect different protocols. The serial port can also set the master-slave relationship independently. It can be configured as either a master station or a slave station.2*Ethernet ports: used for data collection and forwarding. The LAN port has a routing function and provides a channel for other devices to connect to the external network.1* WiFi wireless transmission interface: Provides diverse communication options to adapt to different industrial environment needs.
Data security:Support data TSL/SSL, X.509 certificate, SNMPV1/V2, key encryption and other security gateway functions.
Remote Configuration Support: Support remote PLC programming and program uploading and downloading, saving travelling costs and improving service response speed.Support remote configuration, providing users with convenient management and monitoring methods, no longer need to visit engineers, saving maintenance costs.
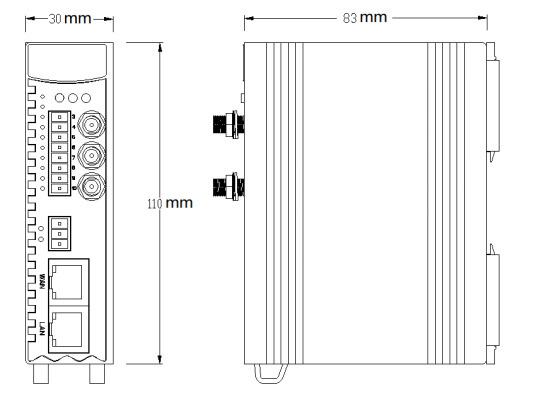
Product Size: L x W x H: 30 x 83 x 110mm
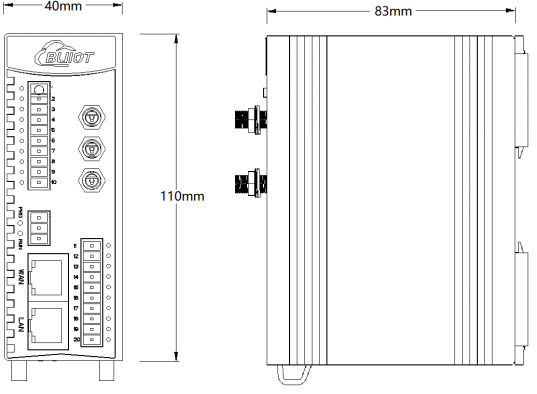
Safety and Stability:
Industrial-grade design: Durable shell material meets industrial environment requirements.
Stability: Efficient communication protocol conversion ensures stable operation of the system.
Environmental adaptation:
Operating temperature range: -40~80℃, adapting to various industrial environments. Protection grade: IP30, ensuring the reliability of the equipment in harsh environments.
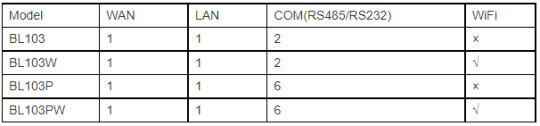
Model List
Application scenarios
Meet the needs of PLC protocol to OPC UA in industrial automation and industrial IoT scenarios.

More information about BLIIoT New PLC to OPC UA Gateway BL103: https://www.bliiot.com/plc-to-opc-p00414p1.html
1 note
·
View note
Text
Thiết bị IDL-2402 Planet là thiết bị mini DSLAM ADSL 2/ 2+ với 24 cổng với một giao diện hỗ trợ link 1000Mbps Base-T thích hợp cho việc triển khai lắp đặt cho hệ thống mạng nhỏ với kết nối ADSL. Thiết bị tích hợp sẵn những cổng phân chia kênh cho những người thuê bao POTS, vì thế IDL-2402 là một thiết bị thích hợp cho những giải pháp mạng với chi phí thấp, triển khai cho nhiều khách hàng thuê bao nhưng vẫn đảm bảo chất lượng.
Hơn thế nữa, thiết bị IDL-2402 hỗ trợ khả năng khả năng quản lý từ xa nhờ các tính năng CLI, SNMP, Telnet thông qua cổng console RS-232 và giao diện quản lý Web, nhờ thế các máy trạm có thể vào giao diện web của thiết bị để quản lý, cấu hình các tính năng dễ dàng và thuận tiện khi bảo trì.
Để tăng tính bảo mật cho hệ thống mạng, IDL-2402 cũng hỗ trợ một số tính năng như QoS, VLAN, Multicast, quản lý băng thông, ưu tiên đường truyền, và ACL. Với tính năng QoS, IDL-2402 hỗ trợ rất tốt cho băng thông mạng để nhận những file video, DSL, POTS và các dịch vụ VoIP qua kết nối ADSL 2+
Mô hình ứng dụng
Giải pháp hoàn hảo cho NSP ( Netwwork Service Provider), đảm bảo về chất lượng dịch vụ
Thiết bị IDL-2402 mang đến nhiều lợi ích và hiệu quả cho các thị trường văn phòng, MTU ( Multi Tenant Unit )/ MDU ( Multi Dwelling Unit).
Đặc tính kỹ thuật
Những đặc tính chung
24 cổng ADSL/ ADSL2/ ADSL 2+, tích hợp bộ chia kênh POTS
Tốc độ truyền tải dữ liệu DMT: download với tốc độ 25 Mbps; upload với tốc độ 3 Mbps
Hỗ trợ giao diện 1000Mbps Base-T
Hỗ trợ quản lý bằng giao diện Web
Hỗ trợ quản lý thông qua giao diện RS-232 CLI, giao diện Ethernet SNMP, Telnet, SSH
Upgrade Firmware thông qua FTP
Cấu hình backup và phục hồi thông qua FTP
Hỗ trợ IPsec/ L2TP/ PPTP VPN Pass-Through
Hỗ trợ 4k địa chỉ MAC
Hỗ trợ IEEE 802.1q Tag-Based VLAN và giao thức VLAN cơ sở
Hỗ trợ khả năng chặn trên Layer 2 và Layer 3 thông qua địa chỉ MAC, IP, Port Number
Hỗ trợ danh sách quản lý truy nhập ACL thông qua địa chỉ MAC/ IP/ Port number
Hỗ trợ 802.1p, ưu tiên lưu lượng
Hỗ trợ IGMP Snooping/ proxy thông qua IGMP v1, v2 và v3
Hỗ trợ chỉ thị báo động quạt
Giám sát nhiệt độ hệ thống
Thông số kỹ thuật
Model
IDL-2402
Hardware Specification
Case
1.5U high box-type with a rack-mountable enclosure
LED Indicators
1 x SYS LED
1 x ALM LED
1 x Uplink LED
24 x ADSL LEDs
Ports
Uplink: 1 x RJ-45 (10/100/1000Base-T)
Console:RS-232 Serial Port (9600, 8, N, 1)
LINE:1 x RJ-21 Connector
PHONE:1 x RJ-21 Connector
Software Specification
Standard
Compliant with ADSL standard
- ANSI T1.413 issue 2
- G.dmt (ITU G.992.1)
- G.lite (ITU G.992.2)
- G.hs (ITU G.994.1)
Capable of ADSL2 standard
- G.dmt.bis (ITU G.992.3)
Capable of ADSL2+ standard
- G.dmt.bisplus (ITU G.992.5)
System -
- Subscriber interface with built-in POTS splitter
- Downstream DMT data rate up to 25 Mbps
- Upstream DMT data rate up to 3 Mbps (Annex M)
- Distance up to 18 kft
- 8 PVCs per xDSL port
- DHCP forward
- DHCP relay agent
- PPPoE relay
- IPSec / L2TP / PPTP VPN pass-through function
- PPPoA to PPPoE inter-working
Bridge Function -
- Supports IPv4 packet
- Supports IEEE802.1d Ethernet bridge function between trunk Ether
port and ATM VCs
- Supports static source MAC table provisioning, automatic source
MAC learning and block duplicate ones
- Supports 4K static MAC address table
- 128 MAC address per x DSL port
VLAN Function -
- IEEE 802.1q Port-based / Protocol-based VLAN
- 512 non-stacked VLAN-ID simultaneously ranging from 1 to 4095
- VLAN stacking and VLAN cross-connect
- IP Spoofing prevention
- MAC anti-Spoofing
- Port isolation functionality
- Static VLAN group and membership provisioning
Multicast Function -
- IP multicast forwarding
- Complies with RFC2684 bridged payload encapsulation mode
- Up to 256 multicast groups and 512 copies simultaneously
- Up to 48 profile-based Multicast Access Control
- Limit maximum number of IGMP groups joined per bridge port
- IGMP snooping / proxy per IGMP v1, v2, and v3
- IGMP proxy and IGMP snooping Selection
Security -
- Supports Layer-2 frame filtering based on MAC and Ether Type
- Supports Layer-3 filtering based on IP, Protocol, and Port number
- IEEE 802.1X authentication
QoS -
- Control the bandwidth occupied by broadcast, multicast, and
unknown unicast (flooding)
- Rate-limit profile binding per bridge port
- Three Color Marking (TCM) policer
- Ethernet rate limit per bridge port
- ToS (type of service) / DiffServ (differentiated services)
stripping and priority queuing
- DSCP mapping to 802.1p
- Selectable adopted priority queue mechanisms according to
Strict Priority Queue (SPQ) and Weighted Fair Queue (WFQ)
- Configurable mapping function between ATM PVC and 802.1p
priority queue
- Supports IP CoS technology
Management -
- Web based GUI management
- Local RS-232 CLI, and Ethernet SNMP / Telnet / SSH management
- Remote in-band SNMP / Telnet / SSH management
- Firmware upgradeable via FTP
- SNMP v1, v2c
Thông tin đặt hàng
IDL-2402
24-Port IP DSLAM (Annex A)
Các phụ tùng đi kèm
IDL-CBL-5
IDL 5-Meter Cable
IDL-PAN-48
IDL MDF Patch Panel
0 notes
Text
Configuración y Monitoreo de UPS APC con Zabbix mediante SNMPv3
Configuración y Monitoreo de UPS APC con Zabbix mediante SNMPv3
Para monitorizar una UPS APC con Zabbix, primero debes asegurarte de que tienes el módulo de UPS APC instalado en el servidor de Zabbix. Si no lo tienes, puedes instalarlo siguiendo las instrucciones en la documentación de Zabbix.
En el servidor Zabbix
Una vez que tienes el módulo de UPS APC instalado, necesitarás configurar un host en Zabbix para la UPS APC. Puedes hacerlo en la página de…

View On WordPress
0 notes
Text
what port for vpn
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
what port for vpn
Protocolos de Rede
Um protocolo de rede é um conjunto de regras que definem como os dispositivos em uma rede se comunicam uns com os outros. Essas regras incluem a forma como os dados são formatados, transmitidos, recebidos e controlados. Os protocolos de rede são essenciais para garantir que a comunicação entre os dispositivos em uma rede seja eficiente e segura.
Existem diversos protocolos de rede que são amplamente utilizados em diferentes tipos de redes, como a Internet. Alguns dos protocolos mais comuns incluem o TCP/IP, UDP, SNMP, HTTP, FTP e SMTP. Cada um desses protocolos desempenha um papel específico na comunicação de dados em uma rede.
O protocolo TCP/IP, por exemplo, é fundamental para a comunicação na Internet e divide-se em camadas para garantir uma transmissão de dados confiável. O protocolo UDP, por sua vez, é utilizado para aplicações em que a velocidade é mais importante do que a integridade dos dados, como em transmissões ao vivo.
Além disso, os protocolos de rede também permitem a comunicação entre dispositivos de diferentes fabricantes, facilitando a interoperabilidade entre eles. Essa padronização é essencial para o funcionamento harmonioso das redes modernas.
Em resumo, os protocolos de rede desempenham um papel crucial na garantia da comunicação eficiente e segura entre os dispositivos em uma rede. Sem essas regras bem definidas, a comunicação entre os dispositivos seria caótica e ineficaz. Por isso, é fundamental compreender e utilizar os protocolos de rede adequados para cada situação.
Segurança da Rede
A segurança da rede é um aspecto fundamental em meio à crescente digitalização de nossas vidas. Com a expansão do uso da internet, torna-se ainda mais importante proteger os dados e informações que trafegam pela rede. A segurança da rede diz respeito às medidas e práticas adotadas para garantir a integridade, confidencialidade e disponibilidade dos dados.
Uma das formas mais comuns de garantir a segurança da rede é através do uso de firewalls, que atuam como uma barreira de proteção, monitorando e controlando o tráfego de informações. Além disso, a utilização de criptografia é essencial para proteger os dados em trânsito, evitando que sejam interceptados por terceiros mal intencionados.
Outra prática importante para garantir a segurança da rede é a atualização constante dos softwares e sistemas utilizados, uma vez que as vulnerabilidades em programas desatualizados podem ser exploradas por cibercriminosos. Além disso, a implementação de políticas de segurança, como o uso de senhas fortes e a autenticação em duas etapas, contribui para fortalecer a proteção da rede.
Em um cenário cada vez mais propenso a ataques cibernéticos, investir em segurança da rede se torna essencial para empresas e usuários individuais. Ao adotar boas práticas e estar sempre atento às ameaças, é possível manter a integridade e a privacidade dos dados que circulam pela rede, garantindo uma experiência mais segura e tranquila no ambiente digital.
Configuração de VPN
A configuração de VPN, ou Rede Privada Virtual, é fundamental para garantir a segurança e privacidade dos dados transmitidos pela internet. Uma VPN cria uma conexão criptografada entre o dispositivo do usuário e um servidor remoto, tornando praticamente impossível para terceiros interceptarem as informações transmitidas.
Existem várias formas de configurar uma VPN, sendo a mais comum o uso de aplicativos ou softwares dedicados. Essas ferramentas facilitam o processo, geralmente exigindo apenas que o usuário selecione um servidor e clique em conectar. No entanto, também é possível configurar manualmente uma VPN em dispositivos e sistemas operacionais compatíveis.
Para configurar manualmente uma VPN, o usuário geralmente precisará inserir informações como endereço do servidor, tipo de protocolo de segurança e credenciais de acesso. Apesar de ser um processo um pouco mais técnico, a configuração manual oferece maior controle sobre as configurações de segurança e privacidade da conexão.
Além da segurança, as VPNs também são amplamente utilizadas para contornar restrições geográficas, permitindo acessar conteúdos bloqueados em determinadas regiões. No entanto, é importante ressaltar que o uso de VPN para atividades ilegais pode resultar em consequências legais.
Em resumo, a configuração de uma VPN é uma medida essencial para proteger a privacidade e a segurança online. Seja por meio de aplicativos intuitivos ou configuração manual, utilizar uma VPN garante que os dados transmitidos pela internet permaneçam seguros e privados.
Portas de Acesso
As "Portas de Acesso" são um elemento fundamental em qualquer construção, permitindo entrar e sair de um espaço de forma segura e eficiente. Estas portas desempenham um papel crucial na segurança de uma casa, empresa ou qualquer outro edifício, tornando-se um elemento essencial do seu design.
Além da sua função prática, as portas de acesso também desempenham um papel estético importante, contribuindo para a primeira impressão que alguém tem de um espaço. Com uma ampla variedade de estilos, materiais e acabamentos disponíveis, as portas podem complementar o design interior e exterior de qualquer edifício, acrescentando personalidade e estilo.
No que diz respeito à segurança, as portas de acesso modernas vêm frequentemente equipadas com fechaduras avançadas e sistemas de segurança, garantindo a proteção dos ocupantes e dos bens no interior do edifício. Adicionalmente, as portas corta-fogo são essenciais em edifícios comerciais e industriais, protegendo vidas e propriedades em caso de emergência.
Para além do seu papel prático e estético, as portas de acesso podem também contribuir para a eficiência energética de um edifício, oferecendo isolamento térmico e acústico quando devidamente instaladas.
Em conclusão, as portas de acesso são muito mais do que simples elementos funcionais de um edifício. Elas desempenham um papel crucial na segurança, no design e no conforto dos ocupantes, sendo essenciais para qualquer construção moderna e bem concebida.
Criptografia de Dados
A criptografia de dados é uma técnica utilizada para proteger informações sensíveis e garantir a segurança na comunicação e armazenamento de dados. Essa prática consiste em codificar as informações de forma que apenas pessoas autorizadas consigam acessá-las, garantindo privacidade e confidencialidade.
Existem diferentes tipos de algoritmos de criptografia, como a criptografia simétrica e assimétrica. Na criptografia simétrica, uma mesma chave é usada tanto para criptografar quanto para descriptografar os dados, enquanto na criptografia assimétrica são utilizadas chaves diferentes: uma pública, para criptografar, e outra privada, para descriptografar.
A criptografia de dados é amplamente utilizada em transações online, como compras em lojas virtuais e serviços bancários pela internet, garantindo a segurança das informações dos usuários. Além disso, é fundamental em ambientes corporativos, protegendo dados confidenciais e estratégicos de empresas contra acessos não autorizados.
Para garantir a eficácia da criptografia de dados, é importante utilizar algoritmos robustos e manter as chaves de segurança protegidas. Além disso, é fundamental estar sempre atento às atualizações e tendências na área de segurança da informação, a fim de se adaptar a novas ameaças e vulnerabilidades.
Em resumo, a criptografia de dados desempenha um papel fundamental na proteção da privacidade e na segurança das informações no ambiente digital, sendo uma ferramenta essencial para garantir a integridade e confidencialidade dos dados em diferentes contextos.
0 notes
Text
Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Dumps Questions
The NSE6_FNC-7.2, also known as the Fortinet NSE 6 - FortiNAC 7.2 exam, plays a key role as one of the elective exams for achieving the esteemed FCP in Network Security certification. If your goal is to successfully pass this NSE6_FNC-7.2 exam, then look no further than Certspots as your primary resource. Certspots is undoubtedly the best choice for you, offering up-to-date Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Dumps Questions. These are not just any questions; these are meticulously updated materials that will significantly increase your chances of achieving a high score in your Fortinet NSE6_FNC-7.2 exam right at the first attempt! Utilizing these Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Dumps Questions will also assist you in gauging your current preparation level. This is invaluable as it provides an opportunity for you to assess and subsequently enhance your preparation strategy for the final Fortinet NSE6_FNC-7.2 exam, ensuring that you are fully prepared when the time comes.
youtube
Fortinet NSE 6 - FortiNAC 7.2 (NSE6_FNC-7.2) Exam Description
To achieve the esteemed FCP in Network Security certification, a key requirement is to successfully pass the core examination along with one optional elective exam. It's important to note that these examinations should not be spaced more than two years apart. NSE6_FNC-7.2, also known as the Fortinet NSE 6 - FortiNAC 7.2, is one such elective exam that aligns with the FCP in Network Security certification.
The Fortinet NSE 6 - FortiNAC 7.2 exam is a comprehensive evaluation of your understanding and level of proficiency with FortiNAC devices. The examination is designed to test your applied knowledge of configuring, operating, and administering FortiNAC on a day-to-day basis. The examination's structure includes a variety of operational scenarios, configuration extracts, and troubleshooting captures to fully assess your ability to manage FortiNAC devices.
The Fortinet NSE 6 - FortiNAC 7.2 exam is specifically designed for network and security professionals who are responsible for the configuration and administration of FortiNAC within a network security infrastructure. Its purpose is to ensure that these professionals have the necessary knowledge and skills to effectively manage and secure their network environments using FortiNAC.
Studying Fortinet NSE6_FNC-7.2 Exam Topics
Successful candidates have applied knowledge and skills in the following areas and tasks:
Concepts and design
Explain access control
Explain information gathering and network visibility techniques
Explain isolation networks and the configuration wizard
Deployment and provisioning
Configure security automation
Configure access control on FortiNAC
Configure and monitor HA
Model and organize infrastructure devices
Explain and configure logical networks
Explain and configure MDM integration
Configure FortiNAC security policies
Network visibility and monitoring
Guests and contractors
Use logging options available on FortiNAC
Explain and configure device profiling
Options for rogue classification
Monitor network devices and device status
Troubleshoot endpoint connectivity and classification
Integration
Integrate with third-party devices using Syslog and SNMP trap input
Configure and use FortiNAC Control Manager
Configure and use group and tag information for network devices
Configure FortiGate VPN integration with FortiNAC
Preparation Tips To Pass The NSE6_FNC-7.2 Fortinet NSE 6 - FortiNAC 7.2 Exam
To excel in the NSE6_FNC-7.2 Fortinet NSE 6 - FortiNAC 7.2 Exam, it's crucial to adopt a methodical approach to your studies. Here are some tips:
Understand the Exam Objectives: Familiarize yourself with all the exam objectives and the topics they cover. Use them as a guide for your study plan.
Use the Available Study Materials: Fortinet provides various study materials, such as manuals, guides, and tutorials, which you can utilize to understand the exam concepts better.
Practice with Real Equipment: If possible, get hands-on practice with real FortiNAC equipment. This will enhance your understanding of the practical aspects of the exam.
Take Practice Exams: Regularly taking practice exams will help you assess your progress and identify areas of weakness. Remember, understanding why an answer is correct is just as important as getting it right.
Join Study Groups: Participating in study groups or forums can provide valuable insights from others who are preparing for the same exam.
Conclusion
In conclusion, this article provides comprehensive information about the Fortinet NSE 6 - FortiNAC 7.2 (NSE6_FNC-7.2) exam. It details the importance of the exam in achieving FCP in Network Security certification, the various topics covered in the exam, and effective methods to prepare for it. Utilizing the Fortinet NSE 6 - FortiNAC 7.2 NSE6_FNC-7.2 Dumps Questions, coupled with practical training and diligent study, can significantly increase one's chances of passing the exam on the first attempt. The value of this certification cannot be overstated in today's competitive job market, making this a worthwhile endeavor for any network and security professional.
0 notes
Text
Forza introduce en Chile una nueva serie de PDUs medibles para la protección de Data Center y Edge
La empresa fabricante anuncia el lanzamiento y disponibilidad de la nueva serie de PDUs diseñada para gestión avanzada de energía y monitoreo en tiempo real del consumo eléctrico, la cual se adapta a una amplia gama de espacios, incluyendo seguridad, telecomunicaciones, centros de datos y equipos al borde.

Forza Power Technologies, empresa fabricante de soluciones de energía confiable, anuncia el lanzamiento de su última serie de Unidades de Distribución de Energía (PDU) medibles, diseñadas para brindar la máxima calidad, confiabilidad y rendimiento en la distribución eléctrica para equipos críticos en gabinetes y racks.

"La nueva serie de PDUs de Forza es una respuesta directa a la creciente necesidad de protección y monitoreo avanzado en entornos de Data Center y Edge. Con soluciones disponibles en 220V, tanto horizontales como verticales, estas PDUs se adaptan perfectamente a una amplia gama de espacios, incluyendo seguridad, telecomunicaciones, centros de datos y equipos al borde", anunció Marianela Suco, Territory Manager para Cono Sur de Forza Power Technologies. Y añadió: "Lo que distingue a nuestras PDUs es su capacidad para proporcionar una gestión avanzada de energía junto con un monitoreo en tiempo real del consumo eléctrico. Equipadas con una pantalla digital, las PDUs para racks con medidor ofrecen una visión detallada del consumo de energía, lo que permite a los administradores de centros de datos evitar sobrecargas y optimizar la eficiencia energética".

Además, las PDUs Forza están diseñadas con indicador LED de sobretensiones que proporciona una alerta instantánea en caso de fluctuaciones peligrosas en el suministro eléctrico.
"Nuestra nueva serie de PDUs representa el compromiso continuo de Forza con la innovación y la excelencia en el campo de la gestión de energía", dijo Marianela Suco. "Estamos encantados de ofrecer a nuestros clientes soluciones de última generación que no solo garantizan la protección de sus equipos críticos, sino que también proporcionan herramientas poderosas para optimizar la eficiencia energética y mejorar la capacidad de respuesta del borde y centro de datos".

Características de la nueva Serie de PDUs medibles de Forza
MPN: FPD-1012M1U
PDU Medible 4000W, 10 Tomas, 1U, 220V Empresariales
Capacidad: 4000W
Voltaje: 220V
Tipo de entrada: C20
Tipo de salida: 10 (8 x IEC C13 /2 x IEC C19)
Indicador visual: LCD
Garantía: 2 años
MPN: FDP-3012M0US
PDU Medible 7200W, 30 Tomas, SNMP, 0U, Empresariales
Capacidad: 7200W
Voltaje: 220V
Tipo de entrada: L6-30P
Tipo de salida: 30 (24 x IEC C13 /6 x IEC C19)
Indicador visual: LCD
Software de gestión: Watch Power
Garantía: 2 años
0 notes
Text
What are the Major Applications and the Future Trends in the Market for Alarm Monitoring?
The Alarm Monitoring Market was valued at USD 42.88 billion in 2017 and is expected to reach USD 59.83 billion by 2023, at a CAGR of 5.5% during the forecast period.
ADT (US), Moni (US), Honeywell (US), Securitas (Sweden), UTC (US), Schneider (France), Johnson Controls (US), Vivint (US), Vector Security (US), and Bosch (Germany) are some of the major companies dominating the alarm monitoring market.
Download PDF Brochure:
https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=110120052
Alarm monitoring is a service wherein alarm systems installed in buildings, equipment, or vehicles are professionally monitored by a central monitoring station (CMS). The alarm systems are monitored in lieu of a monthly recurring charge. The CMS alerts security agencies or the property owner incase an alarm is triggered. Alarm monitoring is carried out to detect intrusion, fire, glass break, or rising carbon monoxide levels inside a premise.
The objectives of the report includes forecast of the Alarm Monitoring market size in terms of Offering (Systems Hardware, Services), Input Signal (Discrete, Protocol), Communication Technology (Wired, Cellular, IP), Application (Building, Equipment, Vehicle Alarm Monitoring), and Geography.
The alarm monitoring market by protocol input signal to grow at the highest CAGR during 2017–2023
Protocol inputs are electrical signals, which are formatted into a formal code that represents more complex information than that in case of discrete or analog signals. There are different types of protocols for transmitting telecom alarm data. The most widely used telemetry protocols are open standards such as SNMP, TL1, ASCII, and TBOS. The alarm monitoring market by protocol input signal is expected to grow at the highest CAGR during the forecast period.
The alarm monitoring market by cellular wireless network communication technology to grow at the highest rate during forecast period.
Among all the communications technology of alarm monitoring market, cellular wireless network expected to grow with the highest CAGR during forecast period. Cellular wireless network is increasingly being used for connectivity between control panels and alarm monitoring centers. It is mostly used as a backup system for connectivity incase primary lines go down. With the increasing reliability of cellular networks, the market for cellular wireless network-based alarm monitoring is expected to grow.
North America to hold a major share of the alarm monitoring market in 2016
North America is expected to dominate the alarm monitoring market during the forecast period. North America is in the forefront in the evolution and development of alarm monitoring technology as this region is home to some of the largest multinational corporations in the world. Most leading players operating in the global alarm monitoring market are based in this region. Increased R&D in the field of remote monitoring, home automation systems, and Internet of Things, in terms of new and improved technologies, is a major factor driving market growth in North America.
0 notes