#decrypt .actin files
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
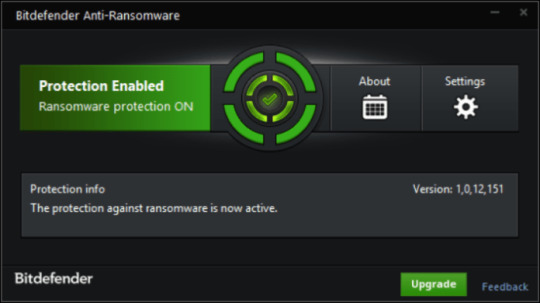
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
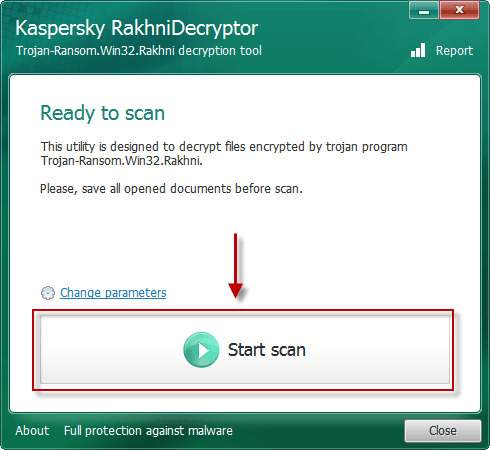
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
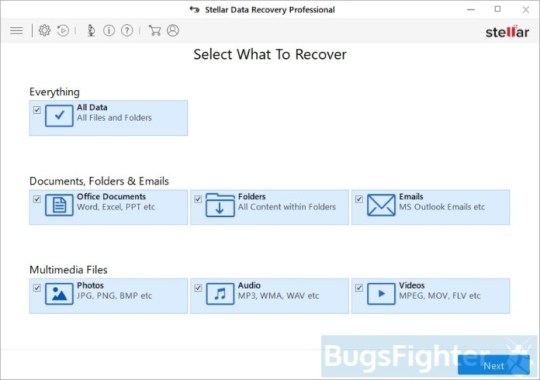
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
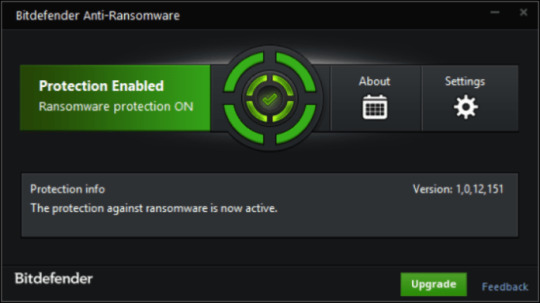
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes