#decrypt .adame files
Text
What Your Business Needs to Know About Ransomware
What Your Business Needs to Know About Ransomware
https://nabiladam.net/what-your-business-needs-to-know-about-ransomware/?utm_source=rss&utm_medium=rss&utm_campaign=what-your-business-needs-to-know-about-ransomware
In recent years, there has been a significant increase in ransomware attacks. These attacks can affect different types of businesses, such as large corporations and small organizations. Understanding the subject of ransomware and how it can be prevented is very important for any company to protect itself from financial losses.
What Is a Ransomware Attack?
In a ransomware attack, a hacker takes over your computer system and prevents you from accessing important files. Once the ransom has been paid, the files are then released to the company. Getting ahold of your system can result in a considerable loss of money and extended downtime.
How Ransomware Operates
When a ransomware attack is performed, the hacker takes over your data and uses a unique private key to decrypt it. It’s tough to outsmart this type of attack since it can quickly destroy essential files if not dealt with properly. After getting hit by ransomware, a message will appear on your screen that informs you about the attack and the ransom that’s demanded.
While panic might set in and tempt one to give in to this demand, it is looked down upon to pay these individuals, as it will only encourage the criminals to continue these types of crimes.
People tend to pay the ransom instead of trying to unencrypt it themselves due to several reasons. They don’t want to wait for their system to recover and don’t want to risk losing their data. However, experts advise against this.
How Your Company Can Avoid Ransomware
One of the most critical steps that organizations can take to prevent ransomware attacks is to keep their systems up-to-date. This can be done through regular software updates and a robust security solution. However, there are still no easy ways to prevent this type of attack. Having a strategy in place is important to prevent it from happening, but having additional plans of action in case you end up being targeted is also essential.
Understanding Your Risk
In addition to ransomware, other threats, such as malware and phishing attacks, are also on the rise. This is why it is recommended that companies regularly monitor their operations and take the necessary steps to prevent these types of attacks. Businesses without a knowledgeable IT team can partner with a cybersecurity consultant to help them understand and lessen their risk as well as assist them in recovering from such an attack.
The post What Your Business Needs to Know About Ransomware first appeared on Nabil Adam | Technology.
0 notes
Text
Lawyer Says He’s Called the FBI on Bitboy Over Threatening Emails, Calls and Tweets - Decrypt
Lawyer Adam Moskowitz says he feels “threatened” by influencer Ben “Bitboy” Armstrong—and he’s contacted the FBI and local police because he’s concerned for his and his family’s safety.
Moskowitz told Decrypt in an interview that the threats came rolling in after his law firm filed a class action lawsuit on behalf of its clients against a number of influencers, including Armstrong, back in March.…

View On WordPress
0 notes
Text
NEW MUSE INCOMING..
Decrypting Muse File Now...
.
.
Decryption Complete
Opening File: Raging Demon.
.
.
Known as a former Shinbaori member this individual would be known as the [REDACTED] to Louvel Shinba, after his great-grandfather (Not Masamune) would [REDACTED] with a woman. Birthing the Raging Demons bloodline....However this would come to a head with his violent tendencies and even worse of all would even dare to challenge the Grandmaster of the Shinbaori himself.
This led to his exile and his end by the hands of the Adam and Sienna Khan but it would lead to his rebirth and rise to one of the Seats of Vanity claiming the Seat of Violence for a brief time.. until meeting Louvel once more and being slain by him....
He is...

“I didnt mind giving up everything! For man had to crawl on his feet in order to win!!! I’ll be the most supreme of them all!!!”
[The Seat of Violence- SHUTEN-DOUJI]
Only on Strykingback
1 note
·
View note
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
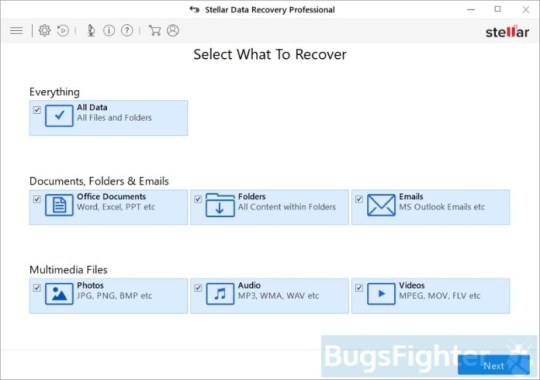
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files
What’s Phobos Ransomware
Phobos Ransomware is a virus, that encrypts consumer information using AES encryption algorithm and demands ~$3000 for decryption. Ransomware provides .phobos, .mamba, .phoenix, .actin, .actor, .blend, .adage, .acton, .com, .adame, .acute, .karlos or .Frendi extensions to encoded information and makes them inaccessible. To be able to confuse users and researchers Phobos Ransomware uses file-modification patterns and ransom notes just like very wide-spread Dharma Ransomware. Particularly after design change in January, 2019, once they began to look identically. Nevertheless, there are specific differences in file-markers and appearance. Discovered variations of Phobos Ransomware use following complicated extensions, that they append to filenames:
Show extensions
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].Frendi
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random 8-digit alphanumerical sequence.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].Frendi
.ID-random Eight-digit-alphanumerical-sequence.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-7777.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1023.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-0001.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1011.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1004.[[email protected]].phoenix
.ID-random Eight-digit-alphanumerical-sequence-1031.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1130.[[email protected]].mamba
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1104.[[email protected]].actin
.ID-random 8-digit-alphanumerical-sequence-0001.[[email protected]].phobos
.ID-random Eight-digit-alphanumerical-sequence-1148.[[email protected]].KARLOS
.ID-random Eight-digit-alphanumerical-sequence-2220.[[email protected]].actor
.ID-random Eight-digit-alphanumerical-sequence-1041.[[email protected]].phoenix
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].com
.ID-random 8-digit-alphanumerical-sequence-1022.[[email protected]].phobos
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].Acton
.ID-random 8-digit-alphanumerical-sequence-1041.[[email protected]].adage
.ID-random Eight-digit-alphanumerical-sequence-2250.[[email protected]].adage
.ID-random 8-digit-alphanumerical-sequence-1103.[[email protected]].blend
.ID-random 8-digit-alphanumerical-sequence-2275.[[email protected]].adame
Previous version of Phobos Ransomware used Phobos.hta ransom observe file. New version places two textual content information on the desktop: encrypted.txt and Knowledge.hta. Phoenix Ransomware makes use of information.txt filename for a ransom notice. Under are the contents of those information:
Phobos.hta
All of your information have been encrypted!
All your information have been encrypted as a consequence of a safety drawback together with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID within the title of your message random-code
It’s a must to pay for decryption in Bitcoins. The worth will depend on how briskly you write to us. After cost we’ll ship you the decryption device that may decrypt all of your information.
Free decryption as assure
Earlier than paying you’ll be able to ship us up to 5 information totally free decryption. The entire measurement of information have to be less than 10Mb (non archived), and information shouldn’t include worthwhile info. (databases,backups, giant excel sheets, and so forth.)
How one can get hold of Bitcoins
The simplest means to purchase bitcoins is LocalBitcoins website. It’s a must to register, click on ‘Buy bitcoins’, and choose the seller by cost technique and worth.
hxxps://localbitcoins.com/buy_bitcoins
Also yow will discover other locations to buy Bitcoins and rookies information right here:
hxxp://www.coindesk.com/info/how-can-i-buy-bitcoins/
Attention!
Don’t rename encrypted information.
Don’t try to decrypt your knowledge using third celebration software program, it might trigger permanent knowledge loss.
Decryption of your information with the help of third events might cause increased worth (they add their payment to our) or you possibly can develop into a victim of a rip-off.
encrypted.txt
All your information have been encrypted as a consequence of a security drawback together with your PC. If you wish to restore them, write us to the e-mail [email protected]
In case of no answer in 24 hours write us to theese e-mails: [email protected]
***
information.txt
!!! Your whole information are encrypted !!!
To decrypt them ship e-mail to this handle: [email protected].
If we don’t answer in 48h., ship e-mail to this tackle: [email protected]
If there isn’t any response from our mail, you’ll be able to install the Jabber shopper and write to us in help of [email protected]
After contacting the developers by way of one of many offered e-mails, they demand $3000 in BitCoins for decryption to be paid in 6 hours. Otherwise, the price of decryption will improve as much as $5000. In the intervening time automated decryptors for Phobos Ransomware don’t exist. There isn’t any proof, that malefactors ship decryptors to the victims, that’s the reason we do not advocate paying the ransom. As an alternative, attempt using directions on this web page to get well encrypted information. File-recovery software program can restore some information out of your hard-drive. If in case you have backups (Onedrive, Dropbox or other) you’ll be able to absolutely restore encrypted information. Use this tutorial to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame information in Windows 10, Home windows 8 and Home windows 7.
Phobos Ransomware (.adame extension)
Phobos-Phoenix Ransomware
Phobos Ransomware in 2019
Phobos Ransomware in 2018
How Phobos Ransomware contaminated your PC
Phobos Ransomware virus is propagated by way of spam attack with malicious e-mail attachments and by guide PC hacking. Could be distributed by hacking via an unprotected RDP configuration, fraudulent downloads, exploits, net injections, pretend updates, repackaged and contaminated installers. Virus assigns sure ID with the victims, that’s used to call those information and supposedly to send decryption key. In an effort to forestall an infection with this kind of threats in future we advocate you to use SpyHunter and BitDefender Anti-Ransomware.
Obtain Phobos Ransomware Removing Device

Obtain Removing Software
To take away Phobos Ransomware utterly, we advocate you to make use of SpyHunter 5 from EnigmaSoft Limited. It detects and removes all information, folders and registry keys of Phobos Ransomware.
How one can remove Phobos Ransomware manually
It isn’t advisable to take away Phobos Ransomware manually, for safer answer use Removing Tools as an alternative.
Phobos Ransomware information:
Phobos.hta
Knowledge.hta
encrypted.txt
ItFoV.exe
Phobos Ransomware registry keys:
no info
Find out how to decrypt and restore .phobos, .phoenix, .adage or .adame information
Use automated decryptors
Use following device from Kaspersky referred to as Rakhni Decryptor, that can decrypt .phobos, .phoenix, .adage or .adame information. Download it right here:
Obtain Kaspersky RakhniDecryptor
There isn’t any function to pay the ransom, as a result of there isn’t a assure you’ll obtain the key, but you will put your financial institution credentials at risk.
In case you are contaminated with Phobos Ransomware and eliminated it out of your pc you’ll be able to attempt to decrypt your information. Antivirus vendors and individuals create free decryptors for some crypto-lockers. To aim to decrypt them manually you can do the following:
Use Stellar Knowledge Restoration Skilled to restore .phobos, .phoenix, .adage or .adame information
Obtain Stellar Knowledge Recovery Skilled.
Click on Recuperate Knowledge button.
Choose sort of information you need to restore and click on Subsequent button.
Choose location the place you want to restore information from and click Scan button.
Preview discovered information, choose ones you’ll restore and click Recuperate.
Obtain Stellar Knowledge Restoration Professional
Utilizing Windows Earlier Variations choice:
Proper-click on contaminated file and select Properties.
Choose Previous Versions tab.
Choose specific version of the file and click Copy.
To restore the selected file and exchange the prevailing one, click on on the Restore button.
In case there isn’t a gadgets within the listing choose various technique.
Utilizing Shadow Explorer:
Download Shadow Explorer program.
Run it and you will notice display itemizing of all the drives and the dates that shadow copy was created.
Choose the drive and date that you simply need to restore from.
Proper-click on a folder identify and choose Export.
In case there are not any other dates in the record, select various technique.
In case you are utilizing Dropbox:
Login to the DropBox website and go to the folder that accommodates encrypted information.
Right-click on the encrypted file and select Earlier Variations.
Select the version of the file you want to restore and click on on the Restore button.
Learn how to shield pc from viruses like Phobos Ransomware in future
1. Get particular anti-ransomware software
Use Bitdefender Anti-Ransomware
Well-known antivirus vendor BitDefender launched free software, that may provide help to with lively anti-ransomware safety, as further defend to your current safety. It won’t conflict with greater security purposes. In case you are looking full internet security answer think about upgrading to full version of BitDefender Web Safety 2018.
Download BitDefender Anti-Ransomware
2. Again up your information
No matter success of protection towards ransomware threats, you can save your information using easy on-line backup. Cloud providers are fairly quick and low cost these days. There’s extra sense using online backup, than creating physical drives, that may get contaminated and encrypted when related to PC or get broken from dropping or hitting. Windows 10 and eight/Eight.1 customers can find pre-installed OneDrive backup answer from Microsoft. It’s truly among the best backup providers available on the market, and has affordable pricing plans. Users of earlier versions can get acquainted with it here. Ensure that to backup and sync most essential information and folders in OneDrive.
3. Don’t open spam e-mails and shield your mailbox
Malicious attachments to spam or phishing e-mails is most popular technique of ransomware distribution. Utilizing spam filters and creating anti-spam guidelines is sweet follow. One of the world leaders in anti-spam protection is SpamFighter. It really works with numerous desktop purposes, and supplies very high degree of anti-spam protection.
Obtain SPAMFighter
four.67/5 (three)
The post How to remove Phobos Ransomware and decrypt .phobos, .phoenix, .adage or .adame files appeared first on Spouting-Tech.
#decrypt .actin files#decrypt .actor files#decrypt .acute files#decrypt .adage files#decrypt .adame files#decrypt .blend files#decrypt .com files#decrypt .frendi files#decrypt .karlos files#decrypt .mamba files#decrypt .phobos files#decrypt .phoenix files#Ransomware#recover .frendi files#recover .phobos files#remove actin ransomware#remove karlos ransomware#remove mamba ransomware#remove phobos ransomware#remove phoenix ransomware#restore .frendi files#restore .phobos files#tech#Tutorials#Viruses
0 notes
Text
The Steps of Ransomware Negotiation
The Steps of Ransomware Negotiation
https://nabiladam.net/the-steps-of-ransomware-negotiation/?utm_source=rss&utm_medium=rss&utm_campaign=the-steps-of-ransomware-negotiation
Ransomware attacks have become increasingly prevalent, targeting individuals, businesses, and government entities. When faced with a ransomware incident, victims often find themselves in the challenging position of deciding whether to negotiate with the attackers to recover their data. While cybersecurity experts generally advise against negotiating with ransomware operators, organizations may sometimes find it unavoidable.
Here are the steps involved in ransomware negotiation:
Identification and Confirmation:
The first step in ransomware negotiation is the identification and confirmation of the attack. Once a victim realizes that their systems are compromised, and files are encrypted, they need to ascertain that it is indeed a ransomware incident. Cybersecurity professionals can assist in confirming the type of ransomware and assessing the extent of the compromise.
Establishing Communication:
Ransomware operators typically provide a means of communication to facilitate negotiation. This could be through email, a dedicated website, or sometimes even through the ransomware note left on the compromised systems.
Assessment of Ransom Demand:
Upon establishing communication, the victim receives the ransom demand from the attackers. The demand usually specifies the amount of cryptocurrency (such as Bitcoin) the victim must pay in exchange for the decryption key. Cybersecurity experts may assist in assessing the reasonableness of the demand and the likelihood of obtaining a working decryption key.
Negotiation Terms and Conditions:
Negotiating the terms and conditions is a delicate process. The victim may attempt to negotiate a lower ransom amount or request proof that the attackers have a valid decryption key. It is crucial to understand the attackers’ willingness to negotiate and the terms they are willing to accept.
Payment Mechanism:
Ransom payments are almost always demanded in cryptocurrency due to its pseudo-anonymous nature. Victims are instructed on how to set up a cryptocurrency wallet and make the payment.
Verification and Decryption:
After the payment is made, victims may receive decryption keys or tools to unlock their files. However, it’s crucial to verify the legitimacy of the decryption process. Cybersecurity experts recommend creating backups of encrypted files before attempting decryption, as the process may not always be flawless, and data loss could occur.
Security Measures and Remediation:
Once the files are decrypted, and the immediate threat is mitigated, the focus shifts to strengthening cybersecurity measures to prevent future attacks.
Legal and Reporting Obligations:
Organizations that have fallen victim to a ransomware attack must consider their legal and regulatory obligations. Some jurisdictions require organizations to report such incidents to authorities, and failing to comply may result in penalties. Engaging with law enforcement can also provide valuable support in investigating the attack and potentially identifying the perpetrators.
It’s important to note that negotiating with ransomware operators is fraught with risks, and there is no guarantee paying the ransom will result in a successful data recovery. Cybersecurity experts generally advise against negotiating and recommend focusing on prevention, detection, and response strategies to mitigate the impact of ransomware attacks.
The post The Steps of Ransomware Negotiation first appeared on Nabil Adam | Technology.
1 note
·
View note
Text
@viciousvizard cont. from here (x)
Only one big brown eye was seen peering at Soifon as she chewed the inside of her cheek. Hiyori had been adamant to find out just what this secret meeting with the captains was about since Lisa was off doing another mission and therefore has delegated that task to Hiyori. Spying on captain's meetings was nothing new to be honest. In fact, it was a rite of passage. It has been a year into her appointment with Kisuke and she was waiting for this moment for him to go crying back to the other captains and saying he 'just can't handle it anymore!' -- but no such luck. Even as there was a silence and then some muffled, sympathetic laughter before the captain commander spoke.
Surprisingly, Soifon was also perched like some tiny ninja beside her as they crouched low in the ventilation shafts. Thank goodness nobody was burning fire to send heat under the ground, or they would be cooked like beatles.
"Yeah, i mean, they ain't even talkin' any more, what the hell are they doin'??" The smaller lieutenant whispered. She had already bitten her nails down to stubs in this year alone, but didn't care. She could only stare at the geta sandals that she knew belonged to Kisuke. He was tapping them in that irritating way that he did, standing beside Yoruichi's well-worn shoes.
"Oh look, they're all filing out. Thank fuck. My butt is sore," she complained under her breath, watching all the captains finally drift out in that annoyingly regal manner that captains did. She waited, then noticed that Kisuke and Yoruichi had yet to file out. The pair were conversing in whispers.
"... He mentioned yer name. Did ya...?" Hiyori waggled her tiny brows obnoxiously at Soifon. "I mean if ya got weird taste, I get it. But Kisuke? Reaaaally? I wake up and wanna punch him."
It wasn't that strange for Soifon to be peeping in on these Captain meetings. She was a bodyguard, so it was only natural she needed to stick by her target. That excuse didn't fair well with the Head-Captain, the decrypted looking thing that he was. So, sadly, here she was instead, eavesdropping with the 12th's Lieutenant, Sarugaki.
Fists clutched tight, and the young assassin almost growled at their stalling. The distanced pits and patters of other Captains faded as they filtered out but, these two stayed. These two...Really, they'd been chatting for hours now with the other Captains; What more could they possibly have to say, let alone to each other? And didn't they talk enough outside of these meetings? Her brows knit together, and she zeroed in, slated orbs determinedly trying get a look at and read those sough lips, all of course to no avail thanks to the ventilations tight spacing. At the mention of her name however, Soifon's face shifted, turning a visible shade of red, and she jolted upright.
Ow! Inadvertently, the sharp uprising would bang her against the ceiling of the vent. Dammit...! Why in the world did he have to say her name? Head clutched in her hands, Soifon peeked up, catching only the Lieutenant's teasing and waggled brows. The wash of red spread farther across her face and tinted her ears now.

"No!" She exclaimed, her voice a little too loud. Dropping her hands from her head, she'd clasp them about her mouth, hushing herself back to a whisper, "Wh-why would you even think I'd like an idiot like him?"
#viciousvizard#TIMELINE || Wasp waist and a pair of thin shoulders#VERSE || The bee is domesticated but not tamed
1 note
·
View note
Text
A Day In The Life of....
The grueling workload he assumed was reflected in the routines he had adopted, which were carefully recorded by Agathon Fain, who now joined Meneval in Napoleon's private office as archivist. After his coronation Napoleon no longer shared a bedroom with Josephine. He did on occasion visit her for the night, and sometimes he would ask her to come and read to him before he went to sleep. This left him free to follow his own routine, which involved rising at around two o'clock in the morning to work with his secretary, who had to be on call at all hours of the day and night. After a couple of hours work he would take a hot bath, and sometimes go to bed for an hour or two of sleep, before rising at seven to begin his toilette and dress. In Paris he always wore the blue uniform of a colonel of the grenadiers of the Guard, with white stockings and buckled shoes, or if he were going hunting, his green hunting dress, and only occasionally the 'habit habille', the former court dress which he had reintroduced but hated wearing, referring to it as 'cet accoutrement'. On campaign, he wore the green uniform of a colonel of the mounted chasseurs of the Guard, with high top-boots."
He had not moved his quarters in the Tuileries, but they had been altered. His inner study was, in the words of Fain, "but a dependency of his bedroom.", and he would work there in his dressing gown. The outer study or salon he only entered when fully dressed. Between the inner study and the bedroom was a room containing a store of maps and a large table on which they could be spread. At one end there was a partition with a hatch, behind which was a staircase and a station manned twenty-four hours a day by a garde de portefeuille who passed incoming communications through it. There were two of them, working alternate shifts, eating and sleeping at their station, entering the private study only to tidy and light the fire.
Napoleon's study was dominated by a table designed by himself, with two indentations facing each other on the long sides so he could sit at it facing his secretary with plenty of space for papers on either side. He would sit with his back to the fire, facing the door to the outer study or salon. The room had one window, opening on the gardens, in the embrasure of which stood a small writing table, at which the secretary would take dictation with his back to the room. At the other end of the room was a bookcase with a clock mounted in it, and in front of that a long mahogany table on which spreadsheets and maps could be unfolded. Beside the fire was a comfortable settee with a small round occasional table beside it.
Having dressed, Napoleon was usually back in his study by eight o'clock, ready to start work. His secretary would sit opposite him at the desk, passing him papers to sign. He would then go over to the fireplace and read the dispatches and letters piled on the table next to the settee. He would dictate replies to some, dropping them on the floor for filing, and place those which needed reflection on the table to be dealt with later. He also read various reports and letters from his correspondents, the 'friends' all over the country who kept him abreast of opinion and gossip, which he would throw into the fire after reading, and would sometime peruse a book, which also went into the fire if it displeased him. He would also look through the red morocco briefcase marked 'Gazette etrangeres', containing transcripts of letters intercepted by the cabinet noir, the postal intercept and decryption office."
Napoleon, A Life, Adam Zamoyski (pages 405-406)
#napoleon#bonaparte#Napoleon Bonaparte#Emperor Napoleon#Emperor Napoleon I#Emperor Napoleon Ier#Napoleon I#Napoleon Ier#excerpt#book excerpt#Napoleon A Life#Adam Zamoyski#A Day In The Life Of
12 notes
·
View notes
Text
7 Days: Sunday
CHAPTER I
pairing: tony stark x reader
summary: let’s face it, becoming a professional hitman wasn’t really what you thought you’d grow up to become. what happens when you start falling for your target?
a/n: took me a while to sit down and write, but i really got a good inspiration and hope that whoever finds this, likes it :)
warnings: alcohol, swearing why do ppl flag these?
feedback is appreciated!!
masterlist || series masterlist

“Are you serious?” the man asked, as you were buttoning up your shirt before taking a look at the whole outfit in the mirror.
Too formal.
“Too formal, don’t you think?” You pulled the curtain revealing the outfit to your partner.
“Are you in your sixties, divorcing your fifth husband?” He stuffed his hands in his pockets. “Anyway, about the plan, do you really think this will work?”
Rolling your eyes, you retuned to the changing booth, closing it with the curtain again. “No, I never do. But what else can I do?”
“You don’t think, that the billionaire tech genius, Tony Stark, can google the specific [Y/N] [Y/L/N] before thinking about hiring her?”
“Okay, first of all, I’m not going to use my real name. Second of all-“
“Problem solved!” he answered in a mocking tone.
“Oh shut up. You bitched out as soon as you could so why don’t you just zip it and let me handle this. I’m doing it with or without you.”
“You’re going to get us both killed.”
“I won’t.”
“Yes, you will, you-“
You took your things as he spoke and threw them over your arm, heading towards the cash register. “Let’s go.”
The drive back to the motel was excruciating, as were most moments shared with your partner. He kept babbling on about how the plan is stupid and it’s never gonna work and eventually you’ll “-both end up dead or in prison. Or both if boss sends someone to kill us while we’re serving time.”
“Where’s all this positive energy coming from, I wonder.”
He rolled his eyes, adjusting in his seat. “How do we know if he traced the hack?”
“I’m guessing we’d have to actually hack first.”
You didn’t look at him, your view was focused on the side window. But you could swear his jaw was hanging open. “Relax, I’ll get it done.”
“Imma look up funeral homes while you do that.”
You rolled your eyes again, resting your forehead in your hand. The truth was, you never liked the guy, ever since you two had to start working together. Mason was always a guy without tactics. If it was up to him, you’d be wearing balaclavas on the way to bust in Stark’s home by now. In his head, that’s less suspicious than actually having a plan. Maybe it is, because other way, you show your face, but if you play it right it won’t be so obvious.
You finally reached your destination, and you rolled out of the car upstairs to the room.
After spending a good few hours trying to decrypt and break into the Stark Industries’ networks, you finally made it.
Curiosity was getting the best out of you as you scrolled through information of other candidates. Biting your lip, you added the file you’d previously completed of your alter ego and closed the laptop.
Twisting in your seat, you turned over to face Mason. “It’s done.”
———
He stomped into the living room of his house, pressing his hand over his wounded shoulder.
“Are you sure you don’t need anything, Mr Stark?”
“I’m sure, thank you.”
The woman nodded, clenching her tablet over her thighs with both hands. “Are the job interviews still on for tomorrow?”
He bit his lip, searching through his mind for anything which could associate with the following day.
“Oh, the PA meetings? Yeah, I remember, of course. Sure, they’re still on. I’m as good as new.” he said, raising his brow.
The woman nodded once again, before clenching her lips. Before she left, she let out a “I’ll leave you to it then.”
Tony turned around, facing the loneliness of his home. He rest his hand on the back of an armchair after throwing his jacket over it.
He sighed, heading towards the liquor cabinet, but got interrupted by a familiar voice.
“Mr Stark, it appears that we suffered a slight security breach.”
He sighed, pouring a drink in his glass. “Define ‘slight’, J.”
“Someone hacked into your files of tomorrow’s PA applicants. The candidate files have been edited and one has been added.”
“Which one?”
“Brooklyn Adams. Just graduated at the University of California.”
He turned around, facing the hologram screen. In front of him was a photo of a young woman. “What’s her major, computer programming?”
“No actually, anthropology.”
“Are you kidding me?” he chuckled, scratching his chin. “Tell you what J, why don’t you pull out the university’s records of recent graduates.”
“As you wish, sir.”
tags: @shannonr2003
#avengers#avengers fanfiction#iron man#iron man fanfiction#iron man imagine#iron man x reader#iron man x y/n#iron man x you#ironman#marvel#tony stark x you#tony stark#tony stark x reader#tony stark x y/n#tony stark imagine#tony stark fic#tony stark fluff#tony stark fanfiction#tony stark headcanon#iron man headcanon
14 notes
·
View notes
Photo

WELCOME TO XAVIER’S, SONG HYERIN !
… loading statistics. currently aged twenty-two, entering first semester of xavier’s in seoul, south korea. decrypting files… mutant has the following records: strength +8, durability +5, agility +6, dexterity +4, intelligence +2. currently, she is classified under tier omega.
BACKGROUND.
PART ONE: THE BEGINNING.
once upon a time, a phoenix was born, risen from the ashes of a relationship gone stale, flames lapping at the child who was too bold since birth, too brash and unforgiving for her abandoned mother to handle at such a young age. a teenage pregnancy was never a good choice, people had chided patronizingly, though hyerin’s mother’s never really cared about what people had to say in the first place, did she? her golden child, a spit in the face at all those who dared claim that her daughter was anything otherwise, even without the tell-tale father who had left the two even before she was born.
and so the phoenix grew older, still ever the charred and outspoken one, taking her classmates and everyone in between in such stride that no one could ever catch up to the girl on eternal fire. song hyerin, the child of the sole teenage parent of their small suburbia in karlsruhe, but still the sharpest of them all; stupidity seemed like such a menial option to grow under the woman who had gone through too much to raise her. in turn, hyerin vowed protection, and so came the staggered lessons of brute force — most wouldn’t dare assume such a pretty face as hers could shoot a gun or throw a punch as well as she could ace a multitude of tests at once; she’d easily prove them all wrong.
her name turns into a definition of something rare and unforgiving, blazing a trail in her way wherever she went. and so one year turns into two, and multiplies in fortitude. grade school comes and goes in a breeze, extracurriculars are what keeps her going. she picks up boxing and sharpshooting as a hobby as soon as her mother has enough to spoil her, and the two are happy, happier than they’ve ever been.
( karlsruhe continues to be kind to them — so far. )
PART TWO: INTERLUDE.
there’s a call from home. not the home hyerin has grown to know, karlsruhe with its german speaking inhabitants and large and spaced grandeur, but where her roots show. seoul, south korea, where her mother ( and presumed father ) was born, the heart of hustle and bustle, bumping shoulders and other korean people who actually might look a bit like her. it’s not the language she’s worried about, no; such a thing is the least of her worries when her mother was so keen and adamant on teaching her ever since she was young. it’s the environ she’s afraid of, with its smog-filled cities and harsh glares. but then again, a sixteen-year-old hyerin can’t do much when it’s her mother than answers and accepts the call of a new start, and who is she to regret anything as of now?
touchdown in seoul, and no one is there to warmly greet the duo ( as expected ). life starts in the most mundane of ways, with her mother starting her new job at the new company, hyerin at her new school. turns out the star student is less of a star here, which bothers her none; hyerin simply tries much, much harder. but of course, her looks stay as stellar as always — a bright smile here and a coy wink there, and she’s finding her way around campus much easier, learns all the gossip, but it’s one flitted rumor that changes her life.
they speak of a boy who can play with fire without getting his fingers ( or anything else, for that matter ) burned about halfway into the school year, and hyerin is all ears. of course it’s a baseless rumor, she thinks, but perhaps it would be interesting enough to see someone being so steadfast as to actually incinerate his fingers off, what a sight to see!
hours after school does the incident happen, and she remembers the event like clockwork. a high five, that’s all it took — ten minutes before he was supposed to douse himself in lighter fluid and step into a fucking bonfire — for the boy to do just that: step into a bonfire in lighter fluid, but he stays burning, despite those high and mighty words that he wouldn’t.
and he screams. chaos ensues, though lucky for him, there’s still enough time to extinguish him ( who would have known what would have happened if not for emergency precautions, what a mess ) as he continues to screech for bloody murder. and as soon as it’s all over, he wheels on her with murder in his eyes, and hyerin has no idea what she’s done. it’s too late to even think however, because the next thing she knows, there’s a rough hand gripping against her throat, darkness coating her visage.
( she stays gone for a while, a long while. )
PART THREE: ROOTS.
she wakes up to unfamiliarity, discord in her thoughts. her expectations of stark white walls and a steady iv drip at a hospital environment are replaced with an oddly discolored wallpaper and a soft bed, nothing familiar other than a dull headache pinging steadily into her temples. her mother is the first person she seeks, another woman — unfamiliar at best — looming by her bedside is who she finds instead.
and so the unknown one explains the extent of hyerin powers — ‘powers’ said in the absolute lightest term — powers rather as in, what is not. negation is what she supposedly has; the nullification of others’, which explains the fire situation and the lack of extinguishment so well, the fact that she almost killed someone is the only thing that is left to simmer in her mind. and it’s no surprise she had no idea she had such an ability; surrounded by a bunch of humans that had none at all were useless to her, but what is to become of her now?
the newest freak show, that’s what she’s been dumbed down to. and now, lo and behold: said freak show placed in an academy with a bunch of other freaks — or was it ‘mutants’ that they called themselves? — who absolutely hated the very ability that had her grouped in the same stupid category that they were all in. the one girl who would take away whatever it was that made them special, a recipe for hate brewing in all their veins, curse her uselessness, a feeling that’s never been felt by song hyerin before.
and so ends the phoenix’s reign, simmered into nothing but a pile of hateful ash at the bottom of everything, missing only one person from her life.
( she’ll escape from here soon enough anyways, she swears on it. )
MUTATION.
power negation is the strata of power that is fully able to nullify those abilities of others, usually for an extended amount of time. the user is able to cancel out the powers of those around themselves, making them unable to utilize their powers so long as they are under the user’s effect.
hyerin’s ability, as she has newly manifested her powers, has the potential to be a complete hazard to those others currently attending the academy who require their powers to properly function. she has virtually little to no control over her abilities, meaning that a simple graze has enough power to completely nullify a person’s ability for a duration from five minutes to almost five hours, depending on her current mood and health. the nullification can be activated through simple touch, or any form of skin-to-skin contact, though it is usually propelled from her hands or arms.
she is virtually immune to all, if not most powers that require close proximities or any sort of possession if the wielder is to be in her vicinity. her power is completely based on emotions; even without skin-to-skin contact, if feeling highly on-end and agitated, she may unknowingly create a negation barrier that may effect everyone around her for an extended duration of time in a ten-foot maximum radius around her. a calmer and more sober mood only limits her powers to those who have been in actual physical contact with her, as is the usual case when she is alone or in personal quarantine.
even the slightest spike in temper or mood may be a potential danger to those around her, especially because she has no idea on how her powers work just yet. her radius is still small and limited, but as small as they are, may drain her on more than one occasion; oversleeping (in a rather comatose state) is not uncommon, as is the occasional bloody nose and splitting migraines that recur more often than not. the more stressors that are inflicted on her body, the weaker she and her power become, and due to that very reason, proper contact with many people at once is not highly recommended.
STRENGTHS.
barrier negation: unconsciously, the user has a force field around them in which superpowers are canceled in its vicinity. in hyerin’s case, it is uncontrollable and happens when in high-stress situations, which may either be both beneficial and detrimental in her experience.
because her ability is something that does not enhance her physically, she holds her strength in being able to fight and hold her ground in hand-to-hand combat rather than having to rely on special abilities like others may expect.
if another person is under the control of a power such as transmutation, she may able to negate the physical form they are afflicted by.
WEAKNESSES.
constantly active, and uncontrollable in hyerin’s case. this accounts for constant fatigue, as any sort of use of her powers is rather debilitating to her physical health due to its unknown levels of control, and therefore power.
hyerin has a very limited range of her negation field, where touch is the most effective and long-lasting. the field that she emits is weaker around the edges, and anyone in her field will know and feel the dampening, effectively rendering her ability useless when people can recharge outside of her station.
unlike power erasure, effects are mostly temporary at most. she has never been known to be rid of a person’s powers for longer than thirty minutes at a time when taking into account the initial contact. later, with more practice and intellect into the ability itself, the time may increase to longer hours, but at the expense of her physical health.
if a person’s power is attributed to their physical qualities, hyerin virtually has no power against them. she cannot simply make one’s cellular biology deplete, so if someone is enhanced with some sort of physiology she cannot just make the attributes disappear off a person’s body.
some powers may not be negated, such as negation immunity and power anchoring, as well as those abilities that have been acquired or copied (i.e. if someone had ‘stolen’ the ability of fire manipulation, she cannot dampen the effects of fire manipulation, but only prevent the person from thieving against an ability again).
power negation only has the ability to negate those powers past “normal” abilities. it is ineffective against those who do not use supernatural abilities in combat, or are naturally physically gifted.
3 notes
·
View notes
Text
Jeff Bezos Phone Hack: What You Need to Know Now
New Post has been published on https://www.politicoscope.com/jeff-bezos-phone-hack-what-you-need-to-know-now/
Jeff Bezos Phone Hack: What You Need to Know Now

U.N. human rights experts are asking Washington to investigate a suspected Saudi hack that may have siphoned data from the personal smartphone of Jeff Bezos, Amazon founder and owner of The Washington Post. But the forensic evidence they cite comes from an incomplete study of Bezos’s phone, raising multiple questions.
Here’s a quick guide to what’s known, and what remains unknown, about their findings.
WHAT HAPPENED TO BEZOS’ PHONE?
According to a report overseen by a former longtime FBI agent and top cybersecurity official in the Obama administration, evidence on the phone suggests it was infected by spyware in May 2018 via a WhatsApp message from the account of Saudi Crown Prince Mohammed bin Salman. That message included a video file that the firm’s investigators say likely contained malware.
Bezos’ personal security adviser had been advised in February 2019 to have the phone examined by an intelligence official who has not been named. Bezos went public with the suspected hack shortly thereafter, saying the National Enquirer tabloid had threatened to publish his private messages and photos.
ARE THE FORENSIC FINDINGS CONCLUSIVE?
Not at all. Outside security researchers highlighted several issues with the forensics report, which was overseen by Anthony Ferrante, who is senior managing director of FTI Consulting’s cybersecurity operations and had worked on the National Security Council under President Barack Obama.
For instance, the FTI report, dated November and obtained Wednesday by the Vice News site Motherboard, said researchers didn’t find any malware on the phone, nor any evidence that Bezos’ phone had surreptitiously communicated with known spyware command servers.
Further, an examination of the crucial root file system — where top-flight hackers often hide their malware — was still pending when the report was written. IPhone security expert Will Strafach, CEO of Guardian Firewall, said that if the FTI investigators didn’t look at the root file system, they didn’t do a thorough forensic exam.
“I think the U.N. intentions are good but the details really matter here and the public reporting falls short of any real firm smoking gun,” said Strafach.
Other security experts questioned the FTI team’s forensic chops, wondering on Twitter and in blog posts why it was unable to decrypt the software that would have delivered the malware payload along with the video file.
Alex Stamos of Stanford University tweeted: “The funny thing is that it looks like FTI potentially has the murder weapon sitting right there, they just haven’t figured out how to test it.”
FTI’s Ferrante did not response to emails and text messages seeking comment. The company said in a statement that all FTI’s work for clients is confidential and that FTI does not “comment on, confirm or deny client engagements.” Facebook said the outfit did not reach out to WhatsApp to request assistance with its probe.
COULD HACKERS HAVE ERASED ALL EVIDENCE OF INTRUSION?
Absolutely, said Strafach. Elite hackers plant malware that erases itself after surreptitiously sending sensitive data to command servers.
“It scoops up everything they want and removes itself so there’s no trace, no evidence,” he said. “Anyone who knows what they are doing are going to cover up their tracks.”
Sophisticated mobile spyware — such as a package called Pegasus, made by the Israeli hacker-for-hire company NSO Group — is designed to bypass detection and mask its activity. Saudi Arabia is reported to have used Pegasus against dissidents and human rights activists within weeks of the suspected Bezos hack.
On Wednesday, NSO Group “unequivocally” denied that its technology was used in the Bezos hack.
WHY IS THE UNITED NATIONS INVOLVED?
One of the two U.N. officials seeking answers in the case, Agnes Callamard. focuses on extrajudicial killings and has already investigated the Saudi government’s role in the October 2018 murder in Turkey of Saudi critic and Washington Post columnist Jamal Khashoggi.
The other, David Kaye, is the U.N. point person on free expression. He focuses on the growing and lawless use of malicious spyware to monitor and intimidate human-rights defenders and journalists.
Both are independent experts in the U.N.’s human rights arm, not employees of the international organization.
Kaye said via text message that he received the FTI report in November.
ARE OTHER PUBLIC FIGURES AT RISK?
It’s difficult to say at the moment. Prince Mohammed has attended gatherings with numerous U.S. entertainers, technology executives and sports-team owners. A senior administration official, speaking on condition of anonymity to discuss internal matters, said Jared Kushner, a White House aide and son-in-law to President Donald Trump, has communicated with the crown prince via WhatsApp.
WHY ISN’T THE U.S. GOVERNMENT MORE INVOLVED?
A top U.S. Justice Department official, Adam S. Hickey, would not say whether federal investigators were looking into the allegations. Trump has been reluctant to condemn the Saudi prince over the Khashoggi killing and often expresses satisfaction with his government’s purchases of U.S. weapons.

Jeff Bezos and Prince Mohammed bin Salman
ap
0 notes
Photo

New Post has been published on https://magzoso.com/tech/jeff-bezos-phone-hack-what-we-know-and-dont-2/
Jeff Bezos Phone Hack: What We Know, and Don't


UN human rights experts are asking Washington to investigate a suspected Saudi hack that may have siphoned data from the personal smartphone of Jeff Bezos, Amazon founder and owner of The Washington Post. But the forensic evidence they cite comes from an incomplete study of Bezos’s phone, raising multiple questions.
Here’s a quick guide to what’s known, and what remains unknown, about their findings.
What happened to Bezos’ phone?
According to a cybersecurity firm run by a former Obama administration official, evidence on the phone suggests it was infected by spyware in May 2018 via a WhatsApp message from the account of Saudi Crown Prince Mohammed bin Salman. That message included a video file that the firm’s investigators say likely contained malware.
Bezos’ personal security adviser had been advised in February 2019 to have the phone examined by an intelligence official who has not been named. Bezos went public with the suspected hack shortly thereafter, saying the National Enquirer tabloid had threatened to publish his private messages and photos.
Are the forensic finding conclusive?
Not at all. Outside security researchers highlighted several issues with the forensics report by FTI Consulting, run by former Obama administration National Security Council cybersecurity official Anthony Ferrante.
For instance, the FTI report, dated November and obtained Wednesday by the Vice News site Motherboard, said researchers didn’t find any malware on the phone, nor any evidence that Bezos’ phone had surreptitiously communicated with known spyware command servers.
Further, an examination of the crucial root file system — where top-flight hackers often hide their malware — was still pending when the report was written. iPhone security expert Will Strafach, CEO of Guardian Firewall, said that if the FTI investigators didn’t look at the root file system, they didn’t do a thorough forensic exam.
“I think the UN intentions are good but the details really matter here and the public reporting falls short of any real firm smoking gun,” said Strafach.
Other security experts questioned the FTI team’s forensic chops, wondering on Twitter and in blog posts why it was unable to decrypt the software that would have delivered the malware payload along with the video file.
Alex Stamos of Stanford University tweeted: “The funny thing is that it looks like FTI potentially has the murder weapon sitting right there, they just haven’t figured out how to test it.”
Ferrante of FTI did not respond to emails and text messages seeking comment.
Could hackers have erased all evidence of intrusion?
Absolutely, said Strafach. Elite hackers plant malware that erases itself after surreptitiously sending sensitive data to command servers.
“It scoops up everything they want and removes itself so there’s no trace, no evidence,” he said. “Anyone who knows what they are doing are going to cover up their tracks.”
Sophisticated mobile spyware — such as a package called Pegasus, made by the Israeli hacker-for-hire company NSO Group — is designed to bypass detection and mask its activity. Saudi Arabia i s reported to have used Pegasus against dissidents and human rights activists within weeks of the suspected Bezos hack.
On Wednesday, NSO Group “unequivocally” denied that its technology was used in the Bezos hack.
Why is the United Nations involved?
One of the two U.N. officials seeking answers in the case, Agnes Callamard. focuses on extrajudicial killings and has already investigated the Saudi government’s role in the October 2018 murder in Turkey of Saudi critic and Washington Post columnist Jamal Khashoggi.
The other, David Kaye, is the U.N. point person on free expression. He focuses on the growing and lawless use of malicious spyware to monitor and intimidate human-rights defenders and journalists.
Both are independent experts in the UN’s human rights arm, not employees of the international organization.
Are other public figures at risk?
It’s difficult to say at the moment. Prince Mohammed has attended gatherings with numerous U.S. entertainers, technology executives and sports-team owners. A senior administration official, speaking on condition of anonymity to discuss internal matters, said Jared Kushner, a White House aide and son-in-law to President Donald Trump, has communicated with the crown prince via WhatsApp.
Why isn’t the US government more involved?
A top US Justice Department official, Adam S. Hickey, would not say whether federal investigators were looking into the allegations. Trump has been reluctant to condemn the Saudi prince over the Khashoggi killing and often expresses satisfaction with his government’s purchases of US weapons.
0 notes
Text
Windows 10 Security Flaw Found by US NSA, Microsoft Issues Fix
The US National Security Agency (NSA) has discovered a major security flaw in Microsoft's Windows 10 operating system that could let hackers intercept seemingly secure communications.

But rather than exploit the flaw for its own intelligence needs, the NSA tipped off Microsoft so that it can fix the system for everyone.
Microsoft released a free software patch to fix the flaw Tuesday and credited the intelligence agency for discovering it. The company said it has not seen any evidence that hackers have used the technique.
Amit Yoran, CEO of security firm Tenable, said it is “exceptionally rare if not unprecedented” for the US government to share its discovery of such a critical vulnerability with a company.
Yoran, who was a founding director of the Department of Homeland Security's computer emergency readiness team, urged all organizations to prioritize patching their systems quickly.
An advisory sent by the NSA on Tuesday said “the consequences of not patching the vulnerability are severe and widespread.”
Microsoft said an attacker could exploit the vulnerability by spoofing a code-signing certificate so it looked like a file came from a trusted source.
"The user would have no way of knowing the file was malicious, because the digital signature would appear to be from a trusted provider," the company said.
If successfully exploited, attackers would have been able to conduct "man-in-the-middle attacks" and decrypt confidential information they intercept on user connections, the company said.
“The biggest risk is to secure communications,” said Adam Meyers, vice president of intelligence for security firm CrowdStrike.
Some computers will get the fix automatically, if they have the automatic update option turned on. Others can get it manually by going to Windows Update in the computer's settings.
Microsoft typically releases security and other updates once a month and waited until Tuesday to disclose the flaw and the NSA's involvement. Microsoft and the NSA both declined to say when the agency privately notified the company.
The agency shared the vulnerability with Microsoft “quickly and responsibly,” Neal Ziring, technical director of the NSA's cybersecurity directorate, said in a blog post Tuesday.
Priscilla Moriuchi, who retired from the NSA in 2017 after running its East Asia and Pacific operations, said this is a good example of the “constructive role” that the NSA can play in improving global information security. Moriuchi, now an analyst at the US cybersecurity firm Recorded Future, said it's likely a reflection of changes made in 2017 to how the US determines whether to disclose a major vulnerability or exploit it for intelligence purposes.
The revamping of what's known as the “Vulnerability Equities Process” put more emphasis on disclosing vulnerabilities whenever possible to protect core internet systems and the U.S. economy and general public.
Those changes happened after a mysterious group calling itself the “Shadow Brokers” released a trove of high-level hacking tools stolen from the NSA, forcing companies including Microsoft to repair their systems. The U.S. believes that North Korea and Russia were able to capitalize on those stolen hacking tools to unleash devastating global cyberattacks.
Welcom to batteriestore.co.uk!We are a manufacturer representative and wholesaler that specializes in Laptop Batteries and Laptop AC Adapters . We have tested Batteries from virtually every manufacturer on the market. Our commitment is to provide our customers with the price/performance available on the market.
Please read the product details carefully to ensure that the brand, model and compatibility of the laptop battery you purchased meets your needs. If you need help, please contact us. Email: [email protected].
0 notes