Link
Check out my latest newsletter: Vol 2: What’s new in the digital world? https://t.co/yXazY8EzFD via @LinkedIn Please subscribe to my Linkedin Newsletter
0 notes
Text
Meeting the Needs of IoT Networks with Open RAN in 5G
https://www.unitingdigital.com/articles/2022/6/26/meeting-the-needs-of-iot-networks-with-open-ran-in-5g
0 notes
Text
IoT Device Security – How Do We Protect Ourselves from the Threats?
Recent statistics indicate that there will be 35.82 billion IoT devices installed worldwide by 2021 and 75.44 billion by 2025. However, the security challenges accompanying IoT devices are also keeping up with their rate of proliferation. Hackers use a combination of brilliantly simple ingenuous tactics to break into and exploit IoT devices. These include credential theft, exploiting insecure or out-of-date firmware, injecting malware into a device that can then be used to infect PCs and other devices on your network and more. Hackers can even eavesdrop into your personal conversations, say from hacking a Google home or Alexa device, to launch devastating social engineering scams.
The problem is further complicated by the fact that most users are not even aware of all the IoT devices that they might have in their home or workplace. While computers, phones, iPads, printers etc. are easy enough to spot and secure, many users don't register the smart speakers, smart lighting systems, thermostats, security systems and a whole list of small and big appliances littering their homes that have been rendered ‘smart’ recently. If you can't even spot all the smart devices on your network, chances are that you are not securing them properly. If they are designed well, smart technologies are often hard to detect. This is what makes effective IoT device security so challenging to implement. IT Support New Jersey can help your organization strategize and implement a comprehensive security framework for IoT devices.
IoT devices and their lack of security
Smart devices are capable of staying connected on the Internet of Things (IoT) and are designed to measure data or take inputs from surrounding environments in one form or another, process this data to turn it into actionable behavior and control the device and the surrounding environment using those inputs. The total number of IoT devices is expected to reach 125 billion in the next 10 years and the current market revenue is $212 billion worldwide. While the easy, smartphone-based access and control over all the major devices at our home and workplace affords us a degree of convenience that we could only dream of before, this convenience comes at the cost of opening ourselves up to serious threats and vulnerabilities that stem from the often-weak security posture of IoT devices.
While IoT has abundant potential and numerous applications that we are only starting to scratch into - the devices are also replete with risks that can serve as a pathway to your organization’s most valuable information. The hype around IOT devices has ensured that the industry has gone to market in a big way before taking security into account. Since IoT devices are designed to provide accessibility and connection, a single unsecured device (or even on the home network of a connected employee) can serve as a point of entry to compromise your entire network. This kind of security flaw is often exacerbated by inefficient security practices such as poor password hygiene, failure to recognize security red flags etc. This is why it's crucial for organizations to gain visibility of IoT devices as a priority and educate its workers on the risks of security vulnerability.
Effective ways to protect yourself and your employer from IoT threats
Education
Empowering employees with the right training and education on data security to recognize the risks and vulnerabilities associated with IoT can prove to be the most critical factor in strengthening your company’s security posture. Employees need to understand the threats IoT devices pose to companies, their networks, and sensitive information. You need to teach employees to recognize data security red flags, home network risks and the need to comprehensively ensure that all devices and services on their home and organization networks stay secure. A proactive approach in fostering a culture of security in your organization goes a long way in cultivating alert employees and stronger defenses.
Monitoring services
Remote users should use remote IoT device monitoring software so the services can actively monitor the network behavior and pick up on any departure from the normal. The baseline for normal behavior can be ascertained through data collection and analysis for each user profile. For sensitive data, organizations should employ alerts for access or modification of highly valuable data. In addition, endpoint monitoring tools should be deployed to monitor IoT device traffic. These are capable of isolating device-level risk through application and data security on IoT devices.
Identity and access management controls
We already spoke of the importance of gaining visibility into all devices for IoT device management. This is critical for implementing robust identity and access management controls and monitoring sensitive data flow.
Adopt a zero-trust policy towards trusting devices
Since IoT devices can be easily rendered vulnerable, organizations should avoid automatically trusting devices connecting to the network. Trust decisions need to be examined on a case-by-case basis where factors like where the device is connecting from, and its purpose or function play a crucial role. Assessment of the device’s value versus the potential risks should also be continually monitored before trust decisions.
User permissions management
Especially with remote work still in vogue, access to data needs to be managed carefully through management of user permissions. Access should only be granted on a need-to-know basis, and the rule of least privilege applied. You also need to determine which users require access to which information and withheld permissions from the rest. If required, users can always request for access on a special case basis.
Home network policy for IoT devices
While organizations cannot prevent employees from having IoT devices on their home network, they do need to stress on the importance of managing them securely. Organizations need to specify the security requirements that IoT devices must satisfy before the device is allowed to access the organization’s network. You also need to educate your employees so they are aware of their responsibilities in ensuring security.
Add additional security through encryption
Encrypted networks are vital to ensure the security of remote access to company networks. This kind of additional security layering often improves an organization’s overall security posture. Similarly, using a virtual private network (VPN) can also help to keep the network safe (even in the case of a breach) as all connections and communications are encrypted.
ABOUT THE AUTHOR
Chris Forte is the President and CEO of Olmec Systems, which provides specialist advice and managed IT Services New Jersey, NY & GA area. Chris has been in the MSP work-space for the past 25 years. He earned his Master’s Degree from West Virginia University, graduating Magna Cum Laude. In his spare time, Chris enjoys traveling with his family. Stay connected via LinkedIn.
0 notes
Text
Uncover the Mystery of AI: How does the AI magically restore the Masking Image, Pixelated Password and Human Face
How could this be possible? Restoring a Blur or Pixelated human face to a high-resolution picture. How about restoring a mask password?
In this video, I will explain the mystery of the AI to everyone like a magician reveals a magic trick, so that everyone can understand how the magical AI algorithm is done?
How to restore the pixelated face picture or mask letters like the password using the AI algorithm?
I will also demonstrate the process of digitalization and how to create an algorithm!
In addition to restoring the original picture, the PULSE algorithm can also be used in different fields like microscope, astronomy, satellite imagery, and medical applications.
If you like our Tech News, please subscribe to show your support!
1 note
·
View note
Text
Data can be stolen without a Wi-Fi network and other unconventional hacking techniques
In this video, I will discuss a new hacking technique using unconventional mean to hack a standalone PC without any network or a Wi Fi connection. In a close area, the information can still be leaked. I will explain the science behinds the hacking techniques and how this research team did it.
Please stay tune and I will show you their demonstration video at the end.
0 notes
Link
Is today’s business ready to fire the boss?
0 notes
Text
Is today’s business ready to fire the boss?
This Microsoft’s AI Patent may fire your boss in the future!
https://www.unitingdigital.com/articles/2020/12/14/microsofts-ai-patent-may-wipe-out-the-typical-management-hierarchy
0 notes
Link
PROBLEMS OF DO-IT-YOURSELF EMAIL TEMPLATE
Many email service platforms provide an email builder that you can use to design the email's look and feel. It seems fun to do it yourself by choosing the layout and design with a template builder. However,... (Click to read more)
1 note
·
View note
Text
Do you need an Affordable Email Marketing Solution for High Volume and High Frequency email Sender with Dynamic Content
Need customized email campaign solution? Check out this article. We discussed some of the issues that we are facing in today's email marketing. Things like the actual cost, customizing your own dynamic content, etc...https://www.unitingdigital.com/articles/email-marketing-solution-for-high-volume-and-high-frequency-email-sender-with-dynamic-content
0 notes
Video
vimeo
A Complete .NET Cloud-Based Software Licensing Solution with Source Code for .NET Professionals from Uniting Digital on Vimeo.
License your software securely at affordable price today! Protect your Intellectual Property!
Do you need a proper licensing system to protect your software product? UD’s Complete .Net Cloud-Based Software Licensing Solution is 100% .NET solution build with the latest .NET technology. With full source code enclosed, you can easily integrate with your desktop, UWP, mobile-device, or web applications. Secure and Affordable!
unitingdigital.com/articles/a-complete-net-cloud-based-software-licensing-solution-with-source-code-for-net-professionals
Bonus: SendOwl Connector
#licensing #licensingsystem #.NET
0 notes
Video
Do you need a licensing solution for your app development?
License your software securely at affordable price today! Protect your Intellectual Property! Check this out!
https://www.unitingdigital.com/articles/a-complete-net-cloud-based-software-licensing-solution-with-source-code-for-net-professionals
0 notes
Text
A Complete .NET Cloud-Based Software Licensing Solution with Source Code for .NET Professionals
Secure and Affordable! You own the source code! .NET Software Licensing Solution (No Monthly Fee!)
Bonus: SendOwl Connector
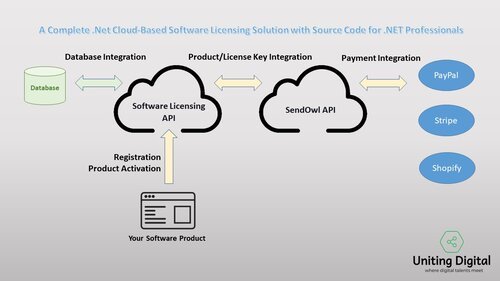
You should focus your energy on making your software product, and not have to worry about licensing and protecting your software product or spending a lot of money before launching your product!
Uniting Digital (UD) .NET Cloud-Based Software Licensing Solution is complete and incredibly flexible. It includes source code, and you can quickly integrate into your project, and fit in with your use-cases and scenarios.
Why licensing your software?

0 notes
Video
vimeo
What Video Thunder can do for you - Video Automation Software - Create Video Series from Uniting Digital on Vimeo.
Today, creating animation videos have become a popular way of making explainer or YouTube videos.
Suppose you have experience in making one of these fun animation videos. In that case, you probably spend a lot of time to perfect the scenes by moving objects and characters around from timeline to timeline. No matter how fast you can do for a video project. You can never reuse the efforts that you put in because the next project will be different.
Have you ever thought of what if you can reuse animation clips that you have been worked so hard on to create unlimited new content?
Video Thunder can help you create a video series show.
You can also use it for repetitive video sequences like the weather forecast, headlines, product promotion, or a quick vlog by merging a series of scenes with voiceover.
video-thunder.com
#videoautomation #software #videothunder #animationseries
0 notes
Video
vimeo
What Video Thunder can do for you - Video Automation Software - Create Video Series from Uniting Digital on Vimeo.
Today, creating animation videos have become a popular way of making explainer or YouTube videos.
Suppose you have experience in making one of these fun animation videos. In that case, you probably spend a lot of time to perfect the scenes by moving objects and characters around from timeline to timeline. No matter how fast you can do for a video project. You can never reuse the efforts that you put in because the next project will be different.
Have you ever thought of what if you can reuse animation clips that you have been worked so hard on to create unlimited new content?
Video Thunder can help you create a video series show.
You can also use it for repetitive video sequences like the weather forecast, headlines, product promotion, or a quick vlog by merging a series of scenes with voiceover.
#videoautomation #software #videothunder #animationseries
0 notes
Photo

Check out our newest product that helps you supercharge your video creation workflow and acts as a complement to your existing video editors. https://www.unitingdigital.com/video-thunder
0 notes
Video
vimeo
A Super easy-to-use automated video creation software from Uniting Digital on Vimeo.
Video Thunder is so much more than just software. It gives you a workflow that allows you to easily follow and help to automate and turbocharge your video production.
0 notes
Video
vimeo
VT_Project_01pprenderfs_1598840514437 from Uniting Digital on Vimeo.
0 notes