Text
Firewall Network Security the core elements towards security
The firewall network security has a modus operandi in itself and has been specifically implemented and deployed in an enterprise with an intention to keep a healthy life of the computer systems which are either a single computer or the series of workstations which are connected in the local area network (LAN) to the central server.
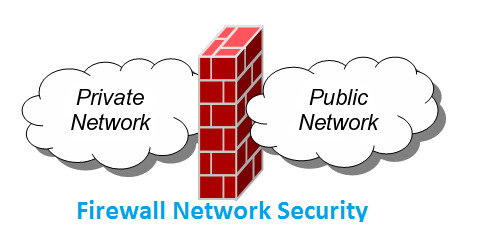
To bring forth the actual objective and the purpose of firewall network security in an enterprise has been towards the complete protection of the computer systems for a prolonged life span and it acts as blockage point thereby blocking the entry point of malicious intrusions which otherwise creates a major chaos and havoc to the crucial database which eventually a computer accommodates within itself.
For few large enterprises, the firewall network security has been a major strategic stride which ensures the three-tier security programs which protects the networks in the first place and the connected workstations in the second place.
Firewall network security over the wirelessly connected devices
With the rapid growth of technology space, there seems to an equal prevalence of malicious intrusions through wireless devices as well. There are certain malicious variants which pro-actively annexes the end point which specifically connects a series of wireless and mobile devices such as the laptops, iPads to name a few.
In this endeavor, a firewall has been the network security coverage which blocks certain end-points such as the connectivity to the third-party internet service provider (ISP) which are quite proven to bring about certain malicious intrusions to the connected devices within the premises.
Variants of firewall network security programs
In the recent past, there has been a constant innovation in the areas of network security paradigm and in this endeavor there has been a constant up-gradation over the security programs being put in practice and one such proven methodology is the unified threat management or simply put (UTM).
The UTM’s have been the evolved version of the yesteryear’s firewall network security initiatives and have been the ones which comprises of filtering component, as UTM’s have become the core component which is able to filter out certain malicious intrusions at the gateway entry point itself and hence ensuring the entire network alignment and the flow of data packets within the network systems in the premises is not affected in any malicious set-back.
If you are a business entity and you are quite apprehensive about the prevention and the total eradication of the malicious intrusions, please approach us at VRS Technologies and call us at +971 55 1683152. Please visit our official website at www.vrstechdxb.com for further endeavors.
0 notes
Text
Unified Security Management strategy for enterprise
In today’s digitized world, the most important and the pivotal component among the enterprise organization has always been towards their security concerns.
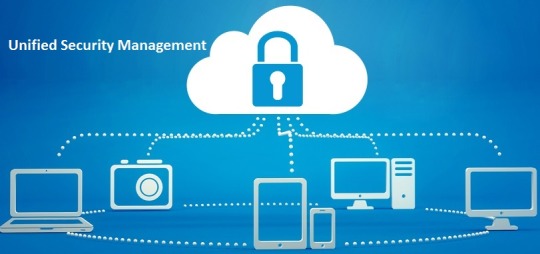
In a typical organization, the security concerns stand as the unique testimony in itself towards the safeguard of the complete ecosystem of the organization with reference to their software applications, the electronic data which encompasses the crucial documents and last but not the least the cloud computing.
The end-points which connects the entire workstations and the servers and a plethora of mobile devices which gets hooked to the network systems.
In this endeavor, the unified security management has been the integral component which completely governs the organizations towards any possible security threats which comes unnoticed.
Anecdote: As a part of the unified security management strategy, numerous security administrators are constantly involved in the implementation of multiple management consoles which strategically governs the entire network systems and seamlessly safeguard the systems over a prolonged period of time.
What could be the repercussions of the improper security managements?
As a matter of fact, the improper security management has always resulted in certain major havocs which often results in the significant loss to the crucial data, the corporate applications. These security lapses have contributed to the significant loss of revenue to the management.
VRS Technologies have been persistently been able to implement and deploy the Unified Security Management for the enterprise organizations and are able to secure the network infrastructure holistically.
If you are an enterprise organization and you are looking forward for a unified security management (USM) for your organization. Please approach us at VRS Technologies and call us at +971 55 1683152 so that our technical team dealing with security management could approach you for further endeavors. Please visit our official website at www.vrstechdxb.com for further information.
0 notes
Text
Network cabling for digital connectivity
In an organization, the network cabling in the format of structured cabling has been considered as an important component with reference to the digital connectivity across the premises seamlessly. The network cabling comprises of the category 5, 5e, 6 or 6 augmented which are primarily deployed as the three main core components in the connectivity amongst the various workstations in the local area network (LAN).

As an analogy, the workstations or any other device which is connected to the network have been technically termed as network nodes or the terminal nodes. In the present context, the network cabling Dubai has undergone massive digital transitions in the past few years and in the current context have been able to accommodate the integration of both voice and data transmissions in a single cable.
Anecdote: In a broad sense, the alignment of a high-quality network cabling has always ensured that it can hold within itself the seamless data transfer rate, which actually narrow downs the significant cost and the operational time within the organization.
Network cables which essentially connect the workstation and servers in LAN
Network cabling, such as the RJ (Registered Jack ) 45 type cabling have been often considered to physically connect the servers and the rest of workstation in a local area network (LAN) so that these workstations and servers can connect with each other in order to share the data within.
Moving further, the data which is being transmitted by the workstations and servers can also accommodate the digital data (data as well as the voice). These integrated transmissions have been known have an inclusion of certain voice initiatives such as the VoIP (Voice over internet protocol)
Anecdote: The VoIP systems of voice transmissions have been quite successful in reference to the digital connectivity through a specialized device called as VoIP phones. The voice transmissions have been known to significantly reduce certain financial implications in the organization.
VRS Technologies have always been innovating itself towards enabling the companies to be digitally empowered with appropriate bandwidths to support both voice and data.
If your organization is looking forward for a network cabling services to be aligned at your premises, please approach us at VRS Technologies and call us at +971 55 1683152 so that our team can initiate with you for further endeavors. Please visit our official website at http://www.vrstechdxb.com for more details.
0 notes
Text
Arrays of backup & disaster recovery in enterprise
In the recent years, the cloud computing has been the most amazing platform for major enterprise organization to bring about more flexibility in the way things can be executed and administered. The backup and the disaster recovery has in fact been a robust application which works at its best in the cloud and the subsequent cloud-based services which persistently support the application development.

Different measures of backup and disaster recovery plan which gets executed
In a typical large enterprise organization, the backup and disaster recovery planning incorporates certain methodological approaches which persistently help an organization to constantly safeguard their database. There could be certain intrinsic planning being undertaken for the recommencement of applications, data to name a few which ardently becomes very effective before an ongoing disaster.
In a nutshell, some of the approaches have been mentioned below which takes care of the backup and disaster recovery in the cloud.
Ø The contingency approach: The contingency approach has always been a safe approach which persistently safeguards your data which is already being backed up on the cloud servers. The entire mechanisms of backup and disaster recovery are based on the process of RPO (Recovery Point Objective). The contingency plan based on RPO is based on the fact that when the data is restored till noon presumably 1 PM and the disaster has struck at 2 PM, there are fair chances that the backup is done meticulously and the data could be retrieved at any time from the cloud servers.
Ø Pilot light approach: The pilot light approach has been the approach wherein the data gets restored on the on-premise database servers and then these database servers’ makes a mirror copy of the same on the cloud servers and this replication of the database happens on a persistent basis.
As an analogy, one can understand that the database servers on the cloud are constantly activated and the database gets frequently updated in the form of the incremental backup. In the event, that the premise database server fails, the application and the data which resides on to the cloud servers are always safe and can be retrieved at any given time.
Ø Warm standby approach: The warm standby approach is the next preceding level of the above-mentioned pilot light approach.
In this approach, the application and the caching servers are being set up based on the criticalities of the business demands. The caching server constantly mirrors itself in the cloud and thereby ensures that the database is handled very safely in the cloud and is used for future retrieval process.
VRS Technologies have been successfully able to implement and deploy some of the backup and disaster recovery methods for the enterprise organization and ensuring them that the database is quite safe and are ready for any sort of unintended contingency. We constantly innovate newer and finer methods to have the backup and disaster recovery paradigms.
If you are an enterprise organization and if you are keen to explore a certain backup and disaster recovery methods at your premises, please approach us at VRS Technologies and call us at +971 55 1683152 so that our team could plan for the finest backup and disaster recovery initiatives. Please visit our official website at http://www.vrstechdxb.com for more details.
0 notes
Text
IT Disaster Recovery the major contingency plan for corporate
In today’s rapidly changing digital world, where numerous corporate across the landscape are currently emerging with newer technological space and strategizing themselves with certain innovative business models which brings about certain advanced enterprise applications which find their way towards strategically governing the certain mission critical operations. Under these situations, the IT disaster recovery becomes an ardent option which plays a vital role towards the overall strategic governance in the enterprise.

The IT disaster transforming itself as the pivotal contingency plan
The most challenging and one of the core components of the contingency plan for any organization in specific have been towards the disaster recovery plans for data centers.
The disaster recovery plans have always played the central role towards safeguarding the data centers as they house within themselves certain databases which are critical for any organization.
The disaster recovery plans to transforms itself as a meticulous strategy towards proper safeguarding of the IT department and caters to the small and medium scale enterprises (SME’s)
Disaster Recovery strategies
One of the most critical disaster recovery strategies that have been governed is about the safeguarding the data as a single entity.
The most pivotal contingency plans which get governed today are ensuring that the data is backed up frequently as a best practice of disaster recovery.
VRS Technologies have always been implementing the disaster recovery plans and constantly deploys the innovative methods to bring about the complete security for the organizations.
In the event that you are looking forward to the disaster recovery plans for your organization, do approach us at VRS Technologies and call us at +971 55 1683152. Please visit our official website at http://www.vrstechdxb.com for more information.
0 notes
Text
End Point Security Solutions becomes a preventive measure for clients
The endpoint security solutions in a network system often refer to network architecture where multitudes of gadgets both networked and remote are seamlessly connected and each device sits on the network endpoints of the network. These series of endpoints connectivity are constantly prone to certain security threats such as the virus, malware, ransomware, spyware to name a few.

The intricacies of endpoint security systems
In today’s scenario, the endpoint security solutions have become the major focal point of strategic debate today among the larger enterprises specifically about enabling the security systems within the networked premises.
Anecdote: The evolving technological space and the rapidly growing business mandates have constantly propelled an organization to deploy the seamless endpoint security systems in place to safeguard the entire peripherals which are being connected to the network systems.
The network endpoint architecture
As an analogy, in the recent years, it has been observed that any device such as the desktops, servers, printers and other wireless devices such as tablets, laptops and other network devices such as the routers and switches which are being seamlessly connected to the network endpoints are constantly posing threats for malware and virus.
As the threshold, of the wide range of devices increase, it becomes a major concern for the organizations to have a strategic planning to keep the robust security in place for a healthy upkeep of the entire network perimeter for a prolonged lifespan.
Efficacy of the network endpoint systems
The endpoint security solutions have been the ardent security solutions, which have been found to meticulously work under the client-server architecture which is typically connected to the local area network (LAN). In this platform, the security software happens to predominantly authenticate each terminal and hence the entire systems connected to the LAN get safeguarded without any major setback.
VRS Technologies have been in the market for a decade and we have been constantly working with numerous customers towards the strategic governance over the endpoint security concerns, we have been successfully deploying the solutions and have completely secured the corporate towards the security initiatives.
As an enterprise organization, if you are looking forward to secure enterprise with the End-point security solutions, please approach us at VRS Technologies and call us an at +971 55 1683152 so that our technical team working on the endpoint security can approach you and accomplish your mandate at the earliest. Please visit our official website at http://www.vrstechdxb.com for more comprehensive information about the endpoint security.
0 notes
Text
Instant IT support the core component to success
In the recent years, there has been a constant debate among the enterprise organization across the landscape with reference to dealing with the virus and spyware threats. The need to have an instant IT support within the organization has always been a top priority amongst the users who are prone to the virus and malware threats.

Virus and malware have always proven to be the most vulnerable component for organizations
In fact, virus and spyware’s have been the vital components which have found to be the most vulnerable entity which completely hampers the computer’s health. In fact, the impact has been more felt in an enterprise organization where the entire workstations and servers are connected across through a local area network (LAN)
Viruses such as the Trojan horse and few such malicious malware software are responsible for the destructions to the database in specific. These software’s are deliberately designed with a profound intention to cause loss of data, system slowdown, applications become a problem to open up to name a few.
Initiatives were taken towards the instant support
Towards this initiative, the technical vendors across, have been constantly been implementing the instant IT support wing, which constantly involves itself towards the offering the prolonged IT support towards the problem resolution.
VRS Technologies have always been able to assist numerous companies across towards the instant IT support the initiative and have been able to deploy these support endeavors to companies and making them the trouble-free zone.
In the event that you are looking forward to the Instant IT support, do approach us at VRS Technologies and call us at +971 55 1683152 so that our technical team could do the needful. Please do visit our official website at http://www.vrstechdxb.com for more information.
0 notes
Text
Endpoint Security-Effective Solution for Security Breaches
Corporate network security is very essential for if the network is not secured, it is just giving way to threats or attacks. The endpoints like servers, laptops, desktops and other network devices of remotely working employees give ways for threats to enter the network. It is highly important to restrict or control the foreign threats from intruding into the corporate network to steal or handle the personal data. With multi-layered nature of the endpoint security, the corporate network can be at safety from potential cyber threats or attacks.
What is endpoint security?
To be elaborate, the endpoint security is an effective and efficient security for the corporate networks. With a centralized approach, the endpoint devices are secured from potential threats so the entire corporate network is protected. With anti-virus, firewalls and other software put together, the endpoints can be monitored for the network security.
Why is endpoint security matter for the corporate security?
Most of the employees work on the go or from a remote environment. So there are chances of security breaches, which would result in the data theft or loss through an unauthentic source accessing to the corporate network. Spam, malware, spyware, virus and many such security threats are a cause of concern compelling the need of the security. With so much of a risk at the endpoints, the corporate cannot afford to compromise on network falling into risk and hence is necessitated by this comprehensive method.
Why is endpoint security comprehensive and more effective?
This kind of security is known to be more effective in comparison to the centralized security since it is a more definable security solution needed by the organization today.
Rather than the centralized approach which attempts to secure the network and its systems through one single source, offering the security at each endpoint is more effective. Each endpoint device is responsible for its own security. With multi-layer security like anti-virus, firewalls, anti-spam, the security is more effective and comprehensive.
VRS Technologies is an IT company based out of Dubai and UAE, offering professional IT services. We have the best of our efforts to provide the appropriate endpoint security solutions for your corporate network.
0 notes
Text
Why is Anti-Spam Protection necessary for the Computers?
The words ‘spam’ or ‘viruses’ are often thrown around terms. As often as they are heard, so is their aftermath. Spam is one of the common risks a computer is prone today. Spam mails are sent in a make-believe fashion that you are tricked into opening the mail trusting in its legitimacy only to realize at the end it is not. The spam containing virus spreads further, aiming at more victims. Even if you are knowledgeable, your computer might be a victim which may be without your knowledge. A viable option would ever be a realization by installing an anti-spam protection software tool to give no way to any virus issues for the computer.
Why do you need an anti-spam protection?
When spam contenders are able to trick a few recipients, the spam is spread to the other users. As a fateful result, computers are infected by viruses. To filter the spam, anti-spam software is essential so it can protect the computers from virus guised within the spam mails. This security tool identifies the unauthorized emails and blocks them from entering the system through content filtering and allows authentic mails to the computer.
The anti-virus software works on protecting the computer from a virus attack induced by the spam mails. Hence, an anti-spam along with anti-virus software helps the computers to be safe from the consequences arising out of a spam mail.
VRS Technologies in Dubai is an IT company providing IT services for corporates across various spectrums and as part of our services; we offer protection for your computers against spam, virus with our updated anti-spam and anti-virus tools.

0 notes
Text
Computer AMC Services For Optimal Performance of the Systems
Computers are part and participle of every enterprise. In every business compartment, a row full of computers gets the employee group busy the whole day, for there is a heap full of work to be accomplished. So long as the computers are up all the time, the scheduled work can go as per the revised plan. Or there can be shackles in the business owing to downtime issues. Is there anything of the kind making your path thorny from being productive and attaining a successful business? Computer AMC services in Dubai from VRS Technologies will do the best to push such obstacles away.

What can computer AMC services do?
As evident it is, a computer is a set of components and none can predict when there can be a trouble with it. Technology adds up to another host of chances for trouble. Any downtime can end up in the loss of the company’s valued time. With fixed schedules and work to progress, it is hardly possible to keep the work unmoving. Ultimately, this could end up in the loss of productivity.
Hence, there is a need to fix the issue in time for which there must be someone to monitor and handle all that is necessary for the computers to be running optimally.
If you are trying to fix things through other sources, you will have to invest time and a heap full of money in getting it done, especially for multiple issues. Employing an in-house manual team can be expensive too. Outsourcing for computer AMC services can be a better choice with real-time benefits for the company.
If the computers are running well without any complaints, it is a real boon for the company having an unobstructed business.
VRS Technologies in Dubai is an AMC company providing services to nurture your computers under the annual maintenance contract. We monitor and administer the needs of your computers round the clock so they are up all the time.
Just leave it to us and your duty is done; we will take care of any rigid computer related trouble. As part of the AMC, we offer data recovery and backup, defragmentation, spyware solutions and many more along with round the clock customer service support. We perform regular checkups, services, and maintenance so there are zero chances for the computer to show up a complaint or cause a downtime.
0 notes
Link
If you looking for Annual maintenance contract Pivotal Component resolving services in Dubai. Choose VRS Technologies to resolve the major bottleneck issues.
If you looking for Annual maintenance contract Pivotal Component resolving services in Dubai. Choose VRS Technologies to resolve the major bottleneck issues.
1 note
·
View note
Link
If You Searching Right Network Cabling Installation Sevices in Dubai. Choose VRS Technologies benefits for your business. Reach us Call +971 55 1683152.
0 notes
Text
Is anti-virus protection a must for the computer?
Before figuring out the importance of anti-virus, it is worth looking into what virus is capable of. The virus, software is hidden with a malicious code, is to infect computers. The code embeds on your computer program and once the virus is able to activate itself, it spreads itself to other programs in the computer. This gives way to the external sources that sent the virus to access your data by administrating the virus. Anti-virus protection is highly essential to save the files from being infected by the virus or for a timely detection in case of virus attack.

How anti-virus protection safeguards the PC?
Internet security software is required for safeguarding the PCs with complete protection. There is not one or two but multiple numbers of viruses existing today that anti-virus protection software is required for a tactful detection of the virus and provide latest updates regarding the same.
If you are smart enough, is anti-virus not required?
There is a misconception that only those users who are irresponsible and less cautious are prone to virus issues. This is no way true and even those who are careful are vulnerable to the virus since the rise in virus-related crimes is alarmingly rising.
It is not when you download suspicious files or go to unauthentic websites that virus enters your PCs. It is worth remembering the fact that there are security flaws that are incentives for the virus attackers.
Even when the old virus issues are rectified, there is no guarantee if a new one would not arise. Also, from lawful sites, the virus might gain the facility to enter the PCs through illegitimate sources of advertising. There is a need for a constant protection since computer insecurity due to lack of forethought should not be a concern in the future.
Is antivirus the ultimate protection?
Anti-virus protection is the least way you can protect your PC but with advanced malware erupting today, anti-virus software can only offer to detect in time the virus infections for preventing the spreading of virus and avoiding further damage to the system’s files. But, anti-virus protection should not be the only layer of protection for the PC. You have to be watchful likewise to be additionally safe.
In spite of having antivirus software installed on your PC for the protection against virus, you still have to watch out downloading and running files on your computer. At the same time, defending the system from a virus is the other way of being cautious and be a step ahead to those trying to gain control over your PC and its financial information and sensitive data.
Contact VRS Technologies at +971 55 1683152 for anti-virus software protection or the entire complex threats your computer encounters. Refer to www.vrstechdxb.com for a clear insight of our antivirus and other security software
�^<��!
0 notes
Link
Network Cabling Services for scalable business
0 notes
Video
youtube
Backup and Disaster Recovery from VRS Technologies in Dubai.
0 notes
Text
How an enterprise benefits by adopting the structured cabling solutions
Irrespective of whether the enterprise is IT based or not, depends on telecommunications i.e. data, voice or video communications. The overall business revolves round the flow of data and the cabling tells how well it is exchanged between the network and its devices. Also, how these network systems communicate with one another to transmit data is the core of a productive business. The better the communication, the higher is the ROI. As you invest, so you reap out of it. Whenever the enterprise needs to set up a data centre, it is worth having forethought before arriving at the apt cabling solution for connecting the hardware. The structured cabling solutions are proven to be reliable for organizing the network of the enterprise.
How structured cabling solutions are an advantage for the enterprise
The needs of communications have taken a steep rise; the cabling system should be able to comprehend the same by adapting the needs constantly and reaching potentiality. Any amount of data demands will be met for the communications to take place on a larger scale, enabling higher returns on investment.
When there is a requirement for the future expansion of the enterprise, the structured cabling offers to cut down the costs of it. At the same time, it is also easy to make modifications in the hardware the data center equips, as the architecture of the structured cable systems permits the same.
Whenever the data center is necessitated by a shift, the organized structured cabling enables it without having to invest much time.
What can be the possible result of not adopting the structured cabling?
The structured cabling system is highly organized and there is no other cabling system offering the same arrangement. The traditional cabling is messy and disorganized that it gives more chances to downtime issues and possible errors, hindering productivity.
The traditional cabling cannot adapt to the ever-growing changes and communication needs unlike the structured cabling which in contrast offers adaptability, flexibility and less downtime.
VRS Technologies is a specialist in Dubai, UAE, offering tailor-made structured cabling solutions for your network communication systems. With our skilled technicians, we come up with well-planned strategies for designing the network infrastructure with our structured cabling solutions, cutting down the cost of the overall infrastructure. We are specialized in planning the cabling installation for any kind of environment to benefit your business.
Contact VRS Technologies at +971 55 1683152 [L7] to organize your infrastructure smart with the structured cabling solutions we have to offer. For a clear insight of our solutions and services, go to our website www.vrstechdxb.com.

0 notes
Video
youtube
How Does Anti Spam Protection Secure a Business?
http://www.vrstechdxb.com/antispam-and-endpoint-security.html
0 notes