Text
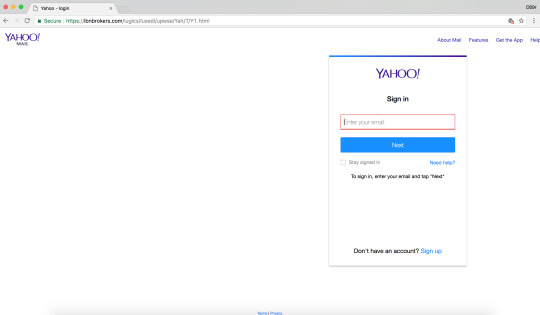
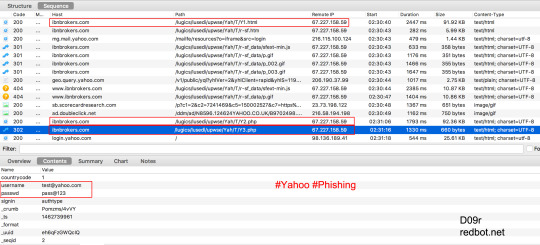
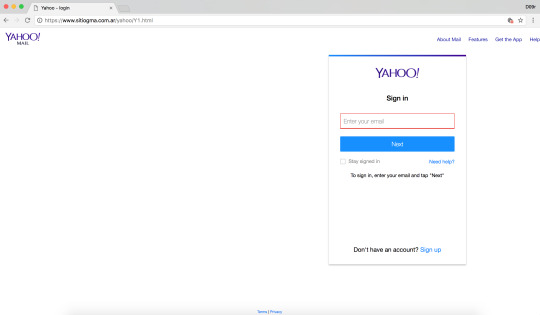
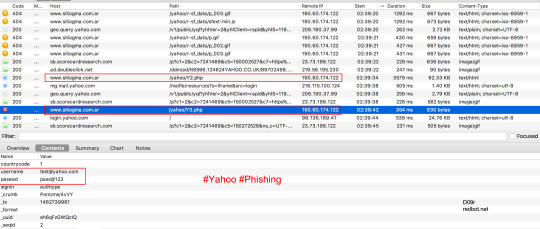
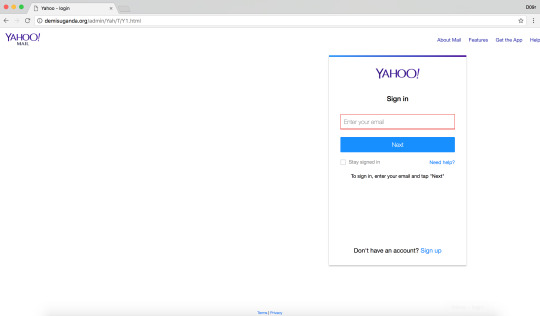
Yahoo Phishing: Y1.html 🚩 Hacked websites turned into Yahoo Phishing websites
sitiogma[.]com[.]ar/yahoo/Y1[.]html
ibnbrokers[.]com/lugics/lusedi/upwse/Yah/T/Y1[.]html
demisuganda[.]org/admin/Yah/T/Y1[.]html

0 notes
Text
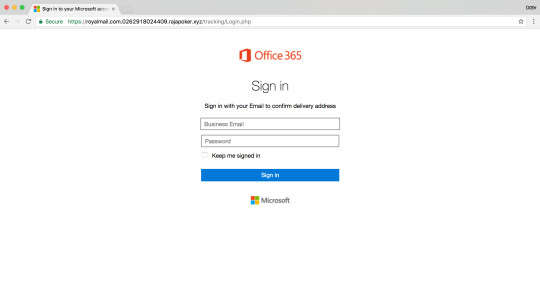
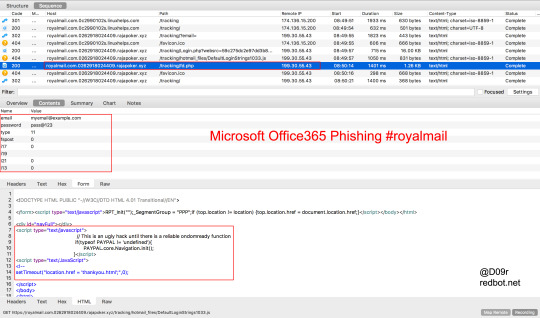
Microsoft Office365 Phishing #royalmail
royalmail.com[.]0c2990102s[.]linuxhelps[.]com/tracking
royalmail.com[.]0262918024409[.]rajapoker[.]xyz/tracking/Login[.]php

0 notes
Text
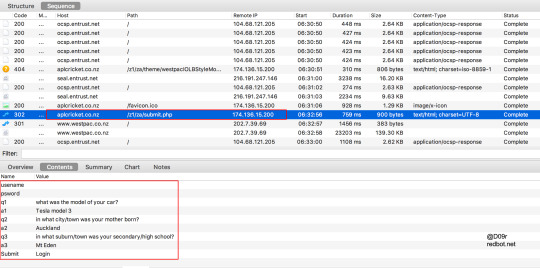
Westpac Bank Phishing attack targeting New Zealand & Australia users
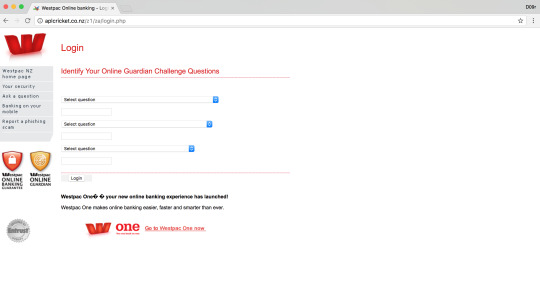
Westpac Phishing URLs
174[.]136[.]15[.]200
aplcricket[.]co[.]nz/sth/za/
aplcricket[.]co[.]nz/z1/za/index[.]htm
aplcricket[.]co[.]nz/z1/za/login[.]php
aplcricket[.]co[.]nz/zath/westpacnormal/
aplcricket[.]co[.]nz/auth/westpacnormal/
aplcricket[.]co[.]nz/sth/za/index[.]htm
aplcricket[.]co[.]nz/auth/westpacnormal/login[.]php
aplcricket[.]co[.]nz/sth/za/login[.]php
aplcricket[.]co[.]nz/zath/westpacnormal/login[.]php
aplcricket[.]co[.]nz/auth/westpacnormal/index[.]htm
1 note
·
View note
Text
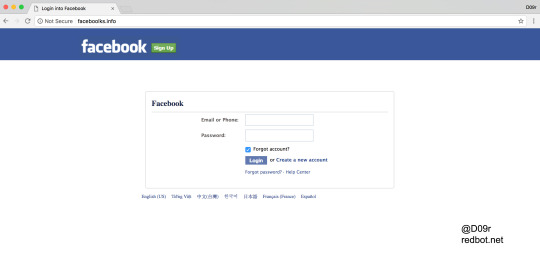
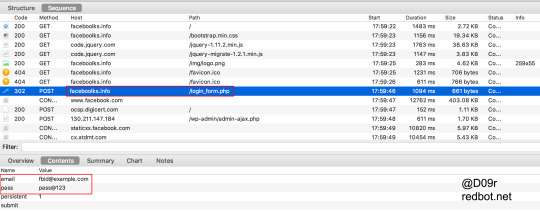
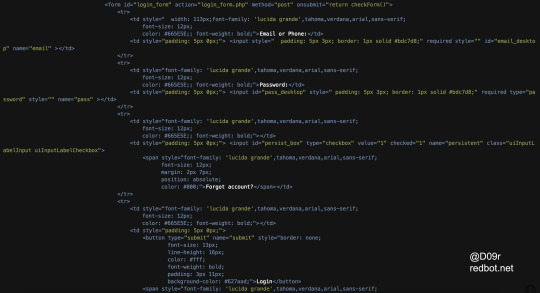
Facebook Phishing faceboolks[.]info
faceboolks[.]info - Facebook phishing
0 notes
Text
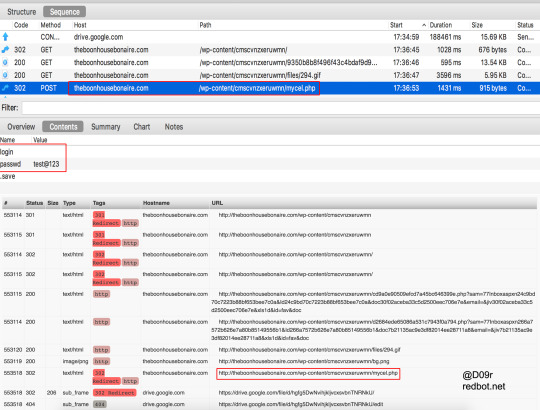
Microsoft Office Phishing

theboonhousebonaire[.]com/wp-content/cmscvnzxeruwmn/
theboonhousebonaire[.]com/wp-content/cmscvnzxeruwmn/d2684ede65086a531c7943f0a794[.]php?sam=77Inboxaspxn266a7572b626e7a80b85149556b1&Id266a7572b626e7a80b85149556b1&doc7b21135ac9e3df82014ee28711a8&email=&jiv7b21135ac9e3df82014ee28711a8&xls1d&id=fav&doc
theboonhousebonaire[.]com/wp-content/cmscvnzxeruwmn/cd9a0e90509efcd7a45bc646399e[.]php?sam=77Inboxaspxn24c9bd70c7223b88bf653bee7c0a&Id24c9bd70c7223b88bf653bee7c0a&doc30f02aceba33c5d2500eec706e7e&email=&jiv30f02aceba33c5d2500eec706e7e&xls1d&id=fav&doc
theboonhousebonaire[.]com/wp-content/cmscvnzxeruwmn/mycel[.]php
drive[.]google[.]com/file/d/hgfg5DwNvihjkljvcxsvbnTNRNkU/
0 notes
Text
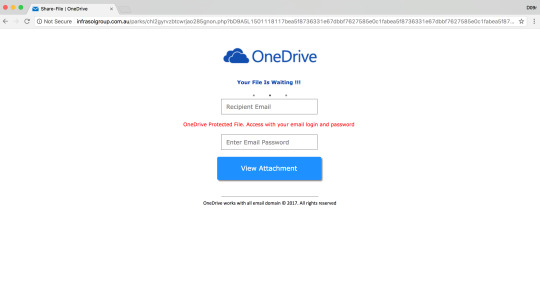
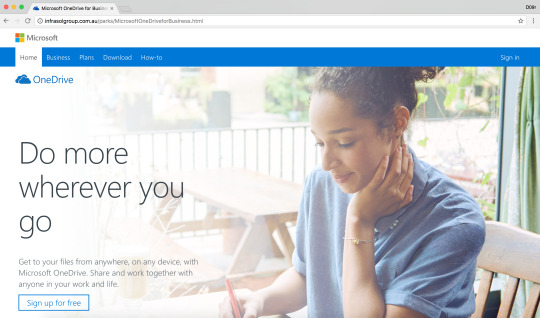
Microsoft OneDrive Phishing Attack targeting AU/NZ users

infrasolgroup[.]com[.]au/parks/index.php
infrasolgroup[.]com[.]au/parks/97436p3rt2j7jkox261yqceq.php?{redacted}
infrasolgroup[.]com[.]au/parks/changemail.php
infrasolgroup[.]com[.]au/parks/loading.php
infrasolgroup[.]com[.]au/google_analytics_auto.js
infrasolgroup[.]com[.]au/parks/abstract.simplenet.com/point2.html
infrasolgroup[.]com[.]au/parks/MicrosoftOneDriveforBusiness.html
https://www.phishtank.com/phish_detail.php?phish_id=5120084
https://www.virustotal.com/en/url/df7e1d0254bba2c6fe20442ab759c6d70077d3131209d9579f1663c32928eda5/analysis/
0 notes
Text
DriveByDownload Malware through Malvertising
Filename: HDVideoPlayer.exe
Size1.5MiB (1523688 bytes)
Type: peexe
Description: PE32 executable (GUI) Intel 80386, for MS Windows
Architecture: 32 Bit
SHA256: 183150f22c13b8baa6c720b326075bf18831b061ec07b6dca626eaa19b7c25ff
Compiler/Packer: Borland Delphi 4.0

https://www.virustotal.com/en/file/183150f22c13b8baa6c720b326075bf18831b061ec07b6dca626eaa19b7c25ff/analysis/
https://www.reverse.it/sample/183150f22c13b8baa6c720b326075bf18831b061ec07b6dca626eaa19b7c25ff
https://www.reverse.it/sample/f3680896a9780f50f72b37c67756dab6e3eace88ab14d9f300456b4dca861b51
0 notes
Text
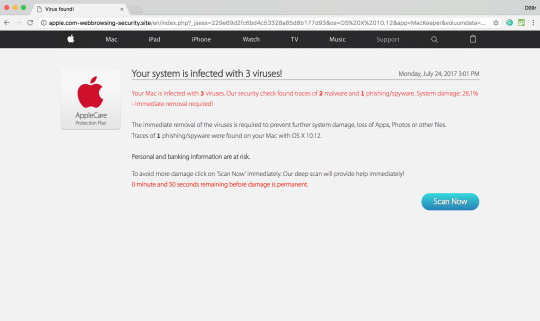
AppleCare Fake Malware Alert
apple[.]com-webbrowsing-security[.]site/en/index.php?{redacted}
69[.]90[.]132[.]23
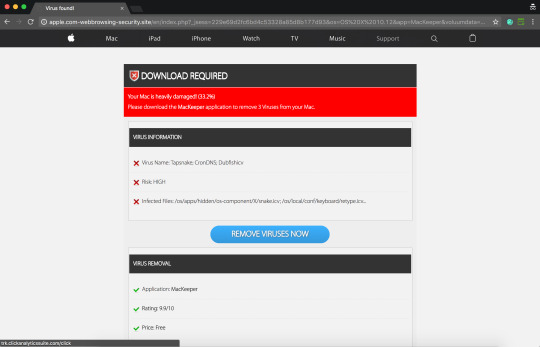
2017-07-24 apple[.]com-webbrowsing-security[.]site
2017-07-14 search apple[.]com-webbrowsing-security[.]science
2017-07-14 www[.]com-webbrowsing-security[.]science
2017-07-11 apple[.]com-webbrowsing-security[.]science
2017-07-05 www[.]com-webbrowsing-security[.]download
2017-07-01 www[.]com-webbrowsing-security[.]accountant
2017-06-30 www[.]com-webbrowsing-security[.]bid
2017-06-28 apple[.]com-webbrowsing-security[.]download
2017-06-26 apple[.]com-webbrowsing-security[.]bid
2017-06-24 apple[.]com-webbrowsing-security[.]accountant
2017-06-24 com-webbrowsing-security[.]accountant
https://www.virustotal.com/en/url/811767416fcec3abfd1d63ffcc004739a07f860fcf1c665ddd2758c63c4745d3/analysis/
0 notes
Text
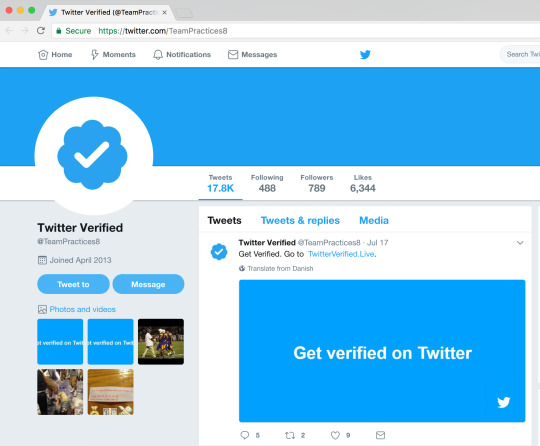
Twitter verified account Phishing tweets
A twitter verified account phishing tweets are spreading through hacked twitter accounts and using Promoted Tweets features to spreading in wide range.
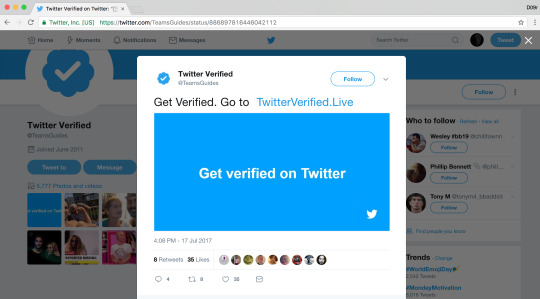
Hacked twitter accounts:
https://twitter.com/TeamsGuides
https://twitter.com/TeamsPractice9
https://twitter.com/TeamPractices40
https://twitter.com/TeamTweets40
https://twitter.com/InformTweets2
https://twitter.com/TeamTips447
Phishing tweet:
https://twitter.com/TeamsGuides/status/886897816446042112
https://twitter.com/TeamsPractice9/status/886966998193852416
https://twitter.com/TeamPractices8/status/886966197702582272
https://twitter.com/InformTweets2/status/881186864526483458
https://twitter.com/TeamTweets40/status/881119119311077377
https://twitter.com/TeamTips447/status/882061577066643456
Twitter phishing page:
http://twitterverified[.]live
https://twitterverified[.]io
http://twitterverified[.]live/payment
http://twitterverified[.]live/identity
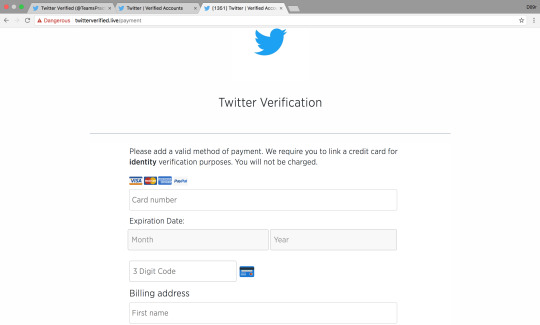
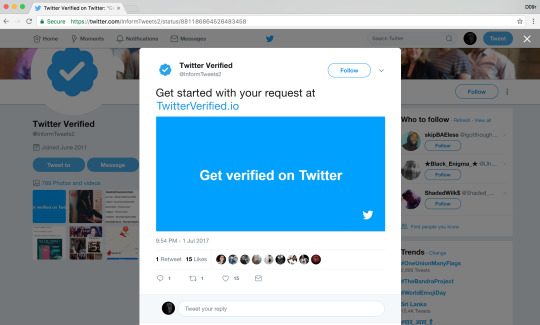
0 notes
Photo
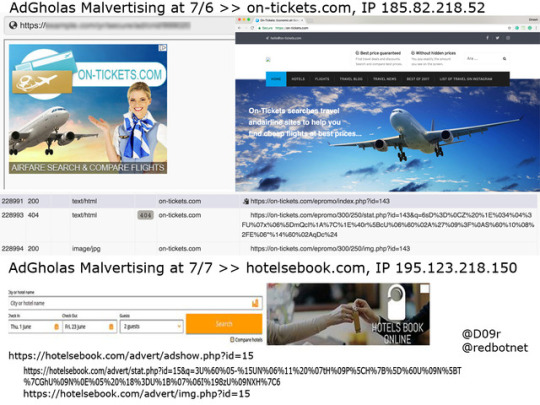
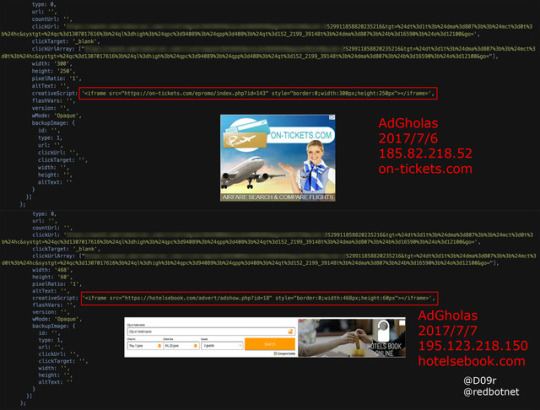
#AdGholas #malvertising shifting his home periodically.
6/29 > 5[.]34[.]180[.]73, expert-essays[.]com
7/2 > 82[.]118[.]17[.]106, jet-travels[.]com
7/6 > 185[.]82[.]218[.]52, on-tickets[.]com
7/7 > 195[.]123[.]218[.]150, hotelsebook[.]com
#D09r
0 notes
Text
AdGholas Malvertising
#AdGholas #malvertising shifting his home periodically.
6/29 > 5[.]34[.]180[.]73, expert-essays[.]com
7/2 > 82[.]118[.]17[.]106, jet-travels[.]com
7/6 > 185[.]82[.]218[.]52, on-tickets[.]com
7/7 > 195[.]123[.]218[.]150, hotelsebook[.]com
#D09r
https://d09r.tumblr.com/image/162720829673
0 notes
Text
Instagram Video Scam Message

Scammers/hackers uses various methods to do fraudulent activities. Multi-level subdomain long URLs technique is quiet popular in while because of success rate of victims is high, uses medium such as Facebook, Instagram, twitter, YouTube, and emails, chats to spreads its campaign.
In this case they using .tk domain, Dot TK is the only top level domain name registry that provides free domain names.
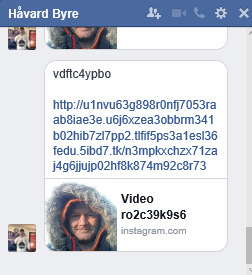
Spam message of Instagram video used in this campaign along with Phish URL.
Where you have to report? - Obviously, its Dot TK
Report Abuse to Dot TK, http://www.dot.tk/en/report_abuse.html
Why not Facebook? - Fb used as a medium to spread this campaign
My friend's account is sending out spam, https://www.facebook.com/help/205730929485170
Reference: http://answers.microsoft.com/en-us/protect/forum/protect_defender-protect_scanning/facebook-virus-instagram-video/9d668818-4722-42cf-a665-dc77c8d8dead
#facebook#malware#phishing#scammers#scam#phishing scam#phishing email#virus#report malware#d09r#facebook abuse#online abuse#hackers#spam#instagram#facebook messenger#instagram video#scam video#phish#microsoft#facebook virus
0 notes
Text
How to Remove @virus = HR
Follow below steps to remove @virus = HR in Windows;
Navigate to C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup and delete system.bat (shift+del - requires Administrator privilege)
Reboot the Windows
Now, delete (shift+del) its remnants on desktop, user directories, system drive, windows drive, and root of each partition & drives
Reference: http://answers.microsoft.com/en-us/protect/forum/protect_other-protect_scanning/cant-remove-virushr/3faa84c8-9dbf-4bb3-b4dd-2bc08f339d81
0 notes
Text
Paytm Fake Offer Scam
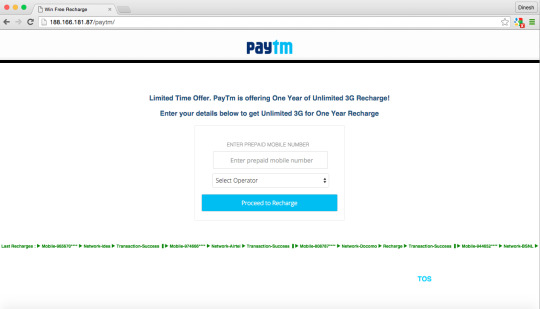
Paytm Promotional Offer WhatsApp message, its a Fake Offer; in order to do fraudulent and force user to do survey or install affiliate app or watch videos with pre-roll/mid-roll ads and last but not least drop a malware to your device.
What is a Scam?
A Scam or trick is an attempt to defraud a person or entity and involving fraudulent activities. Scammer is a person who perpetrates a scam. There are so many online frauds in that Tech Support Scam is widely known online scam beyond the boundaries of countries.
For example, many tech support scam which defraud the Microsoft name and involved fraudulent activities of dialing Cold-Call to users for online tech support paid services.
Paytm Offer WhatsApp message
You may received the following fake offer invite from your friend or unknown recipient in WhatsApp.
"http://paytm.xy4.co || Hey Friends, Paytm is offering 1 Year of Unlimited 3G Recharge as Promotional Offer! Do not pay for 3G in 2016. Get Unlimited 3G Data for 1 year for free! NOTE: Offer Valid only till Tomorrow!"
Infection Flow:
hxxp://paytm.xy4.co/
hxxp://188.166.181.87/paytm/
hxxp://188.166.181.87/paytm/invite.html
hxxp://188.166.181.87/3g/survey.html
hxxps://motifiles.com/script_include.php?id=424450{redacted}
Paytm Scam Investigation
You may received the message in WhatsApp from your friend or unknown recipient states "Paytm is offering 1 Year of Unlimited 3G as Promotional Offer!" with phishing URL hxxp://paytm.xy4.co/ (subdomain is widely used trick nowadays by Phishers/Hackers to get more numbers of victims/fishes), look at first sight seems Paytm website address and users will click in it.
Xy4.co Whois Record
Created on 2015-11-29 - Expires on 2016-11-28 - Updated on 2015-11-29
IP Address: 50.63.202.9 with 135,794 other sites hosted on this server
Website Title: Internet Free WhatsApp Activation!
Registrant Organization: Domains By Proxy, LLC
Registrant Email: [email protected]
As of DomainTools archive, xy4.co domain is registered for one year with private registration through Domains By Proxy, LLC. Additionally, we got an information about HTML title element value of last captured Whois record as "Internet Free WhatsApp Activation!". WhatsApp Activation or WhatsApp Voice Call scam is on-wild another popular scam. These information makes domain xy4.co as Suspicious!
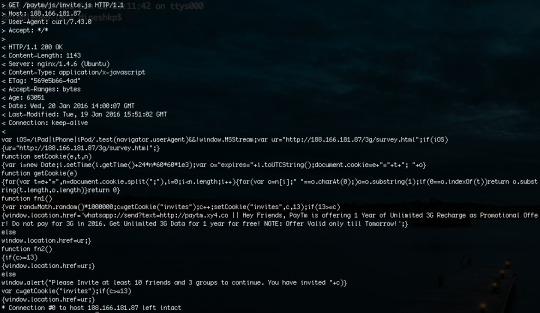
When click on the URL hxxp://paytm.xy4.co/, HTTP 303 found and redirect to actual phish page hxxp://188.166.181.87/paytm/. The URL redirection is known method of using in malware or phish attack in order to avoid the domain name or IP address be blacklisted by anti-virus/ anti-malware products.
Paytm phish page contains form with fields mobile number and operators listbox. From the information of operators list clears this Paytm attack targets India users.
Behind the scene/ behind-the-page, we see hxxp://188.166.181.87/paytm/index.html page have only form with conditional on-click to invite.html page, in-line javascript for browsers cookies and hidden histats counter in-line javascript.
Once you provided the mobile numbers and claim 3G offer will take you to hxxp://188.166.181.87/paytm/invite.html page and force to share invitation of this offer to your WhatsApp friends or WhatsApp groups in order to claim recharge offer.

Click on invite dialog share a coded message as following with link back here;
"hxxp://paytm.xy4.co || Hey Friends, Paytm is offering 1 Year of Unlimited 3G Recharge as Promotional Offer! Do not pay for 3G in 2016. Get Unlimited 3G Data for 1 year for free! NOTE: Offer Valid only till Tomorrow!"
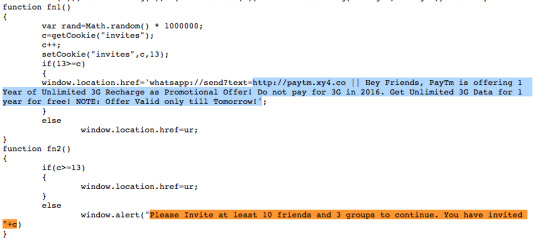
The invite.html page have external javascript file located at "./js/invite.js". The invite.js script have conditional check of user-agent to met mobile devices either iPhone/iPad/Android and pass to survey page hxxp://188.166.181.87/3g/survey.html or else looping on survey page.
The survey.html page loads successfully if user visiting this URL in mobile devices. Here is the main core part of game, the intension behind this Paytm scam now reveals. Survey page have 3 listed offer such as,
Download and install app (probably affiliate link app or malicious app)
Watch Videos (probably pre-roll/mid-roll ads)
Win Brand New Samsung Galaxy S6 Edge! (probably collects personal identity information and force to do another paid survey)
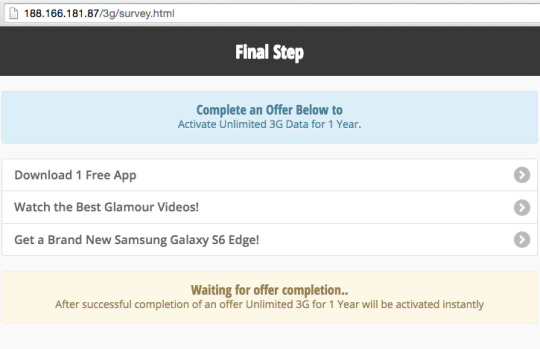
Whatever option you chosen from above lists and completes also won't get any offer as claimed earlier. You may comes to known at end, it's fake offer and a scam.
But, scammers gets $$$.
Here, is the source code of survey.html page.
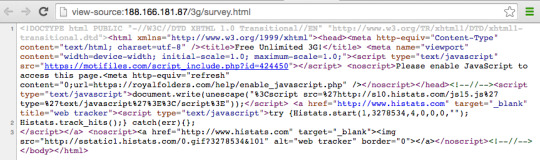
Domain motifiles.com provides those surveys, affiliate app randomly depends on users geo-location, browser cookies.
Motifiles.com Whois Record
Created on 2015-12-09 - Expires on 2016-12-09 - Updated on 2015-12-15
IP Address: 104.25.214.28 with 26 other sites hosted on this server
Registrant Organization: WHOISGUARD, INC.
Tips
Be aware of scam, and online fraudulent.
Don't share any URLs/information to friends either through email or messengers unless you're sure about its legitimation and trusted source of information.
Read news to get up-to-date information about online frauds, malware.
Paytm Scam Investigation Video
youtube
#paytm#scam#scammers#scamming#online#frauds#whatsapp#phishing#phishing scam#phishing attack#phish#phishtank#phishing email#javascript#user-agent#online-scam#online-fraud#domaintools#virustotal#malware#survey#affiliate-apps#fraudulent#cookies#browsers#whatsapp-groups
0 notes
Text
WhatsApp Phishing Attack
hxxp://starcheats.biz/WhatsApp/
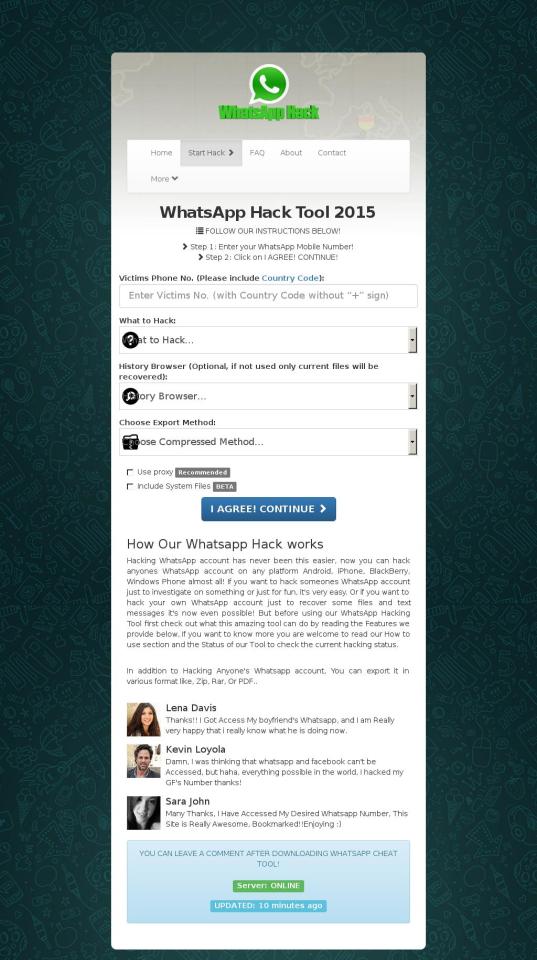
Attackers on starcheats.biz may trick you into doing something dangerous like installing software or revealing your personal information (for example, passwords, phone numbers, or credit cards).
Whois Lookup:
Created on 2015-04-30 - Expires on 2016-04-29 - Updated on 2015-07-01
IP Address: 104.24.120.55 - 52 other sites hosted on this server
Observed subdomains:
instagram.starcheats.biz
wifi.starcheats.biz
clashofclans.starcheats.biz
boombeach.starcheats.biz
Reference:
https://www.phishtank.com/phish_detail.php?phish_id=3713880
https://www.google.com/transparencyreport/safebrowsing/diagnostic/index.html#url=starcheats.biz
#Whatsapp#phishing#phishing attack#malware#scammers#hackers#hacking#phishtank#phishing email#phishing scam#password#instagram
0 notes
Text
Malvertising Campaign targeting Germany Popular Publishers Website
Jérôme Segura, a Senior Security Researcher at Malwarebytes published a blog post about a large Malvertising campaign is currently targeting Germany popular publishers Websites.
According to post, the following Publishers were affected on this Malvertising Campaign.
Affected Publishers
ebay.de
t-online.de
arcor.de
swp.de
fischkopf.de
donaukurier.de
The Malicious Ads which calls through following Bogus Advertising Network and leads to Malicious website hosted Angler Exploit Kit or Neutrino Exploit Kit.
deutschlandauto.xyz
deutschewelle.pw
According to DomainTools, both a domains Whois information are identical.
Registrant Name: Rocko Mantas
Registrant Organization: Best Media ltd
Registrant Street: legian str 12
Registrant City: Paris
Registrant State/Province: Loire-Atlantique
Registrant Postal Code: 12151
Registrant Country: FR
Registrant Phone: +33.142928900
Registrant Email: [email protected]
Currently, both a domains does’t resolve any IP address. Also, 80.86.89.179 doesn’t resolve any domains currently. Earlier, both a domains resolves on IP address 80.86.89.179
The following domains resolved on the IP address 80.86.89.179,
2015-10-19 deutsch-uni.pw
2015-10-18 deutschlandauto.xyz
2015-10-17 deutschewelle.pw
2015-10-17 hookersbase.top
2015-10-17 pornclub.space
2015-10-16 pornclub.asia
2015-10-15 bestmilf.pw
2015-10-15 bigass.pw
2015-10-13 analitycs.xyz
2015-10-13 datingbase.xyz
2015-10-13 geeforce.download
2015-10-13 pornoclub.xyz
2015-10-13 soft-hub.download
2015-10-12 free-soft.download
2015-10-11 freesoft.asia
2015-09-27 extranet.pw
[email protected] email used on Browlock Malvertising Campaign at doublepimp network, Youporn and some adult Websites.
Additionally, domains deutschlandauto.xyz and deutschewelle.pw were registered on 2015-10-17.
When do a keyword search “Best Media ltd”, founded a Facebook page for "Best Media ltd". The Facebook page is newly created in recent days, currently the page have "0" likes, also no information about company in the page.
https://www.facebook.com/pages/best-media-ltd/163548686998614
Reverse Whois of Best Media Ltd, results 132 domains associated with it.
For more information about Kampagnen Malvertising Campaign.
#malvertising#malvertising attack#malware#advertising#virustotal#malwarebytes#D09r#youporn#malicious ad#fake advertiser#ebay#ad network#domains
0 notes
