#userprivacy
Text
Securing Your Mobile App: Best Practices for Data Protection

In today’s digitally connected world, mobile applications have become an integral part of our daily lives. From social media to online banking, we rely on mobile apps to access various services and manage sensitive information. However, with the increasing reliance on mobile apps, the need for robust data protection measures has become paramount. This blog will explore best practices for securing your mobile app and ensuring the protection of user data.
Encryption:
One of the fundamental steps in securing your mobile app is implementing encryption techniques. Encryption ensures that data transmitted between the app and the server is transformed into a coded form, making it unreadable to unauthorized parties. Utilize strong encryption algorithms, such as AES (Advanced Encryption Standard), to protect sensitive user information like passwords, financial details, and personal data. Additionally, consider implementing end-to-end encryption to safeguard data even if it’s intercepted during transmission.
2. Secure Authentication:
Implementing strong authentication mechanisms is vital to protect user accounts from unauthorized access. Encourage the use of complex passwords and provide guidance on creating strong passwords during the registration process. Consider implementing two-factor authentication (2FA) or biometric authentication, such as fingerprint or facial recognition, to add an extra layer of security. Regularly validate and update authentication protocols to address emerging security vulnerabilities.
3. Secure Data Storage:
Properly managing and securing data storage within your mobile app is crucial. Avoid storing sensitive information on the device unless necessary, and when required, utilize secure storage mechanisms provided by the operating system or utilize encryption techniques to protect the data. Ensure that the app’s data storage is adequately protected against unauthorized access or tampering, both locally on the device and on the server.
4. Secure Network Communication:

Mobile apps rely on network communication to exchange data with servers or APIs. It’s essential to ensure that this communication is secure. Use secure communication protocols such as HTTPS (Hypertext Transfer Protocol Secure) to encrypt data transmitted over the network. Avoid transmitting sensitive information through insecure channels, such as unsecured Wi-Fi networks, and implement certificate pinning to prevent man-in-the-middle attacks.
5. Regular Updates and Security Patches:
Keeping your mobile app up to date with the latest security patches and fixes is crucial for maintaining a secure environment. Regularly release updates to address any identified security vulnerabilities or weaknesses. Promptly address security-related issues reported by users or security researchers and provide timely patches to mitigate potential risks. Establish a process for monitoring and staying informed about the latest security practices and threats.
6. Secure Code Development:
Developing secure code is essential for building a robust mobile app. Adhere to secure coding practices and guidelines provided by the platform and framework you are using. Regularly conduct code reviews and security audits to identify and address any potential vulnerabilities. Utilize automated tools for vulnerability scanning and penetration testing to detect security flaws in your app’s codebase.
7. User Privacy and Consent:
Respect user privacy and adhere to data protection regulations such as GDPR (General Data Protection Regulation) or CCPA (California Consumer Privacy Act). Clearly communicate your app’s data collection and usage practices to users through a comprehensive privacy policy. Obtain explicit consent from users before accessing and storing their personal information. Allow users to manage their privacy settings within the app, giving them control over their data.
Securing your mobile app is not just a legal requirement but also a responsibility to protect your users’ sensitive data. By implementing strong encryption, secure authentication mechanisms, and following best practices in code development, you can create a safer environment for your users. Regular updates and a privacy-centric approach will help instill trust and confidence in your app. By prioritizing data protection, you contribute to a safer mobile app ecosystem and foster long-term user satisfaction.
Remember, data protection is an ongoing process, and staying vigilant against emerging threats and security practices is vital in this ever-evolving digital landscape.
2 notes
·
View notes
Link
Apple's annual Worldwide Developers Conference (WWDC) is a highly anticipated event, and this year's edition promises exciting advancements for iPhone users. Rumors and leaks suggest that iOS 18, expected to be unveiled at WWDC 2024, will usher in a new era of AI-powered features designed to enhance user experience while prioritizing privacy. Let's delve deeper into the potential AI innovations Apple might introduce with iOS 18. A Glimpse into the Future: AI-Driven Enhancements for iOS 18 Two groundbreaking AI features are rumored to be making their debut in iOS 18: Apple's AI Revolution AI-Powered Browsing Assistant for Safari: Imagine having a digital assistant within Safari that anticipates your needs while browsing the web. This AI assistant could potentially offer functionalities similar to those found in browsers like Microsoft Edge, streamlining your online experience. Encrypted Visual Search: Apple's existing Visual Look Up feature in Spotlight is known for its image and text recognition capabilities. The upcoming encrypted visual search feature is expected to build upon this foundation, offering a more secure and advanced search method. Prioritizing Privacy: The Core Principle of Apple's AI Approach Apple has consistently emphasized user privacy as a core value. This commitment extends to its AI features as well. Here's what sets Apple's approach apart: Oblivious HTTP Gateway: Technical leaks suggest the use of an Oblivious HTTP gateway for these AI features. This innovative technology masks user activity by obscuring the connection between multiple requests originating from the same IP address. This cloaking mechanism provides a layer of anonymity for users, making it difficult to track their online activities. Private Relay Integration: Apple's existing Private Relay infrastructure, designed to anonymize web traffic, will be integrated with the new AI features. This further strengthens user privacy by concealing browsing data and search queries. Unmasking the Oblivious HTTP Gateway: A Technical Deep Dive (Optional) For those interested in the technical aspects, here's a deeper look at the Oblivious HTTP gateway: Preserving Privacy without Compromising Functionality: This gateway acts as an intermediary between the user's device and the websites they visit. While processing search queries or performing AI-powered tasks, the gateway prevents the website or service from recognizing the user's specific IP address. This protects user anonymity while allowing the AI features to function effectively. Balancing Innovation and Security: Implementing such a gateway presents a unique challenge. Apple needs to ensure it doesn't compromise the functionality of the AI features while maintaining a strong focus on user privacy. WWDC 2024: The Stage is Set for More Revelations With WWDC 2024 just around the corner, excitement is rising amongst tech enthusiasts. The unveiling of iOS 18 and the confirmation of these AI features are highly anticipated. Here are some key questions we hope to have answered: Compatibility Across Devices: Will these AI features be available on all iPhone models eligible for the iOS 18 update, or will they be limited to newer devices? Detailed Functionality: How will the AI-powered browsing assistant and encrypted visual search features function in real-world scenarios? Integration with Other Apple Services: Will these AI features seamlessly integrate with other Apple services like Siri and Spotlight, offering a more unified user experience? The Future of AI on iPhone: User-Centric Innovation Apple's foray into AI-powered features marks a significant step towards a more intuitive and intelligent user experience on iPhones. With a focus on privacy at its core, Apple sets itself apart by ensuring its AI advancements do not come at the cost of user data security. As we approach WWDC 2024, the potential of these features to revolutionize the way users interact with their iPhones is undeniable. FAQs: Q: What are the key AI features coming to iOS 18? A: iOS 18 will introduce an AI-driven browsing assistant for Safari and an encrypted visual search feature in Spotlight, prioritizing user privacy and enhancing functionality. Q: How does Apple prioritize user privacy in these features? A: Apple employs an Oblivious HTTP gateway to enhance user anonymity and encrypts visual search data using its Private Relay infrastructure, ensuring the security of user data. Q: When can users expect to see these AI features in iOS 18? A: The features are set to be unveiled at WWDC 2024, with further details expected to be revealed during Apple's keynote event in June.
#AIfeatures#apple#ApplesAIRevolution#browsingassistant#encryption#iOS18#technology#userprivacy#visualsearch#WWDC2024
0 notes
Text
Meta's Plan to Fight Fake News & Make Elections Fairer
#2024USelections #artificialintelligence #civicengagement #combatingmisinformation #democraticprocess #eligiblevoters #factcheckingorganizations #increasingtransparency #machinelearning #Meta #politicaladvertising #userprivacy
#Politics#2024USelections#artificialintelligence#civicengagement#combatingmisinformation#democraticprocess#eligiblevoters#factcheckingorganizations#increasingtransparency#machinelearning#Meta#politicaladvertising#userprivacy
0 notes
Text
Facebook and Instagram : Paid Subscriptions to users in Europe
Facebook and Instagram to Offer Paid Subscriptions to Users in Europe
Facebook and Instagram are reportedly planning to offer paid subscriptions to users in Europe, in a bid to boost revenue and reduce reliance on advertising. The subscriptions would give users access to exclusive content and features, such as ad-free browsing, early access to new features, and the ability to support their…

View On WordPress
#AdFreeBrowsing#AdSupportedInternet#Advertising#DigitalMarketsAct#EuropeanRegulations#EUUsers#Facebook#GDPR#Instagram#meta#PaidSubscriptions#PersonalizedAds#SubscriptionModel#UserChoice#UserPrivacy
0 notes
Photo
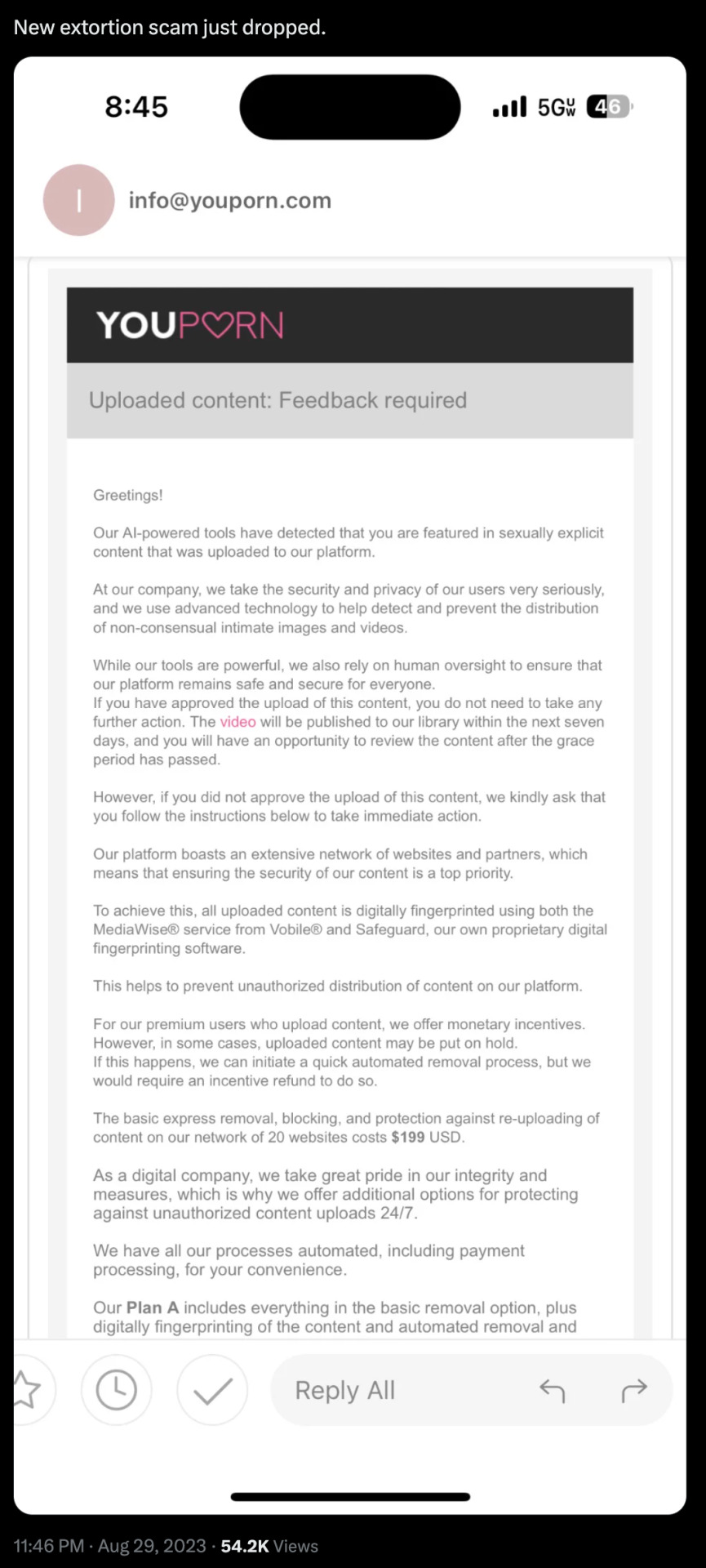
https://bit.ly/3Eoy5n5 - 📢 A new extortion scam has been identified on the platform "YouPorn." The scam involves sending notifications to individuals, claiming that their explicit content has been uploaded to the platform. #OnlineScam #YouPornAlert 🔍 The message states that YouPorn's AI-powered tools detected the individual in the uploaded content. While the platform emphasizes its commitment to user security and privacy, it also mentions the use of advanced technology to detect and prevent the distribution of non-consensual intimate images and videos. #AIDetection #UserPrivacy 🔄 If the recipient has approved the content upload, no action is required. However, if the upload was not approved, the platform provides instructions for immediate action. The content is said to be digitally fingerprinted using MediaWise® from Vobile® and Safeguard, YouPorn's proprietary software, to prevent unauthorized distribution. #DigitalFingerprint #ContentSecurity 💰 The scam's catch is the offer of a "quick automated removal process" for content that may be put on hold. This express removal, blocking, and protection against re-uploading on their network reportedly costs $199 USD. The platform also promotes additional protection options against unauthorized uploads. #ScamAlert #UnauthorizedUploads 🌐 It's crucial for users to be cautious and verify the authenticity of such messages before taking any action or making payments.
#OnlineScam#YouPornAlert#AIDetection#UserPrivacy#DigitalFingerprint#ContentSecurity#ScamAlert#UnauthorizedUploads#StaySafeOnline#VerifyBeforeYouPay
0 notes
Text
Navigating a Cookie-Free Future: Customizing Digital Marketing Strategies
In the dynamic world of digital marketing, change is constant. Moving into the future, one of the most significant shifts facing marketers today is the move to a cookie-free environment. With growing privacy concerns and changing regulations, the era of relying on third-party cookies for tracking and targeting is coming to an end. In this blog post, we'll explore the concept of a cookie-free future, its implications for digital marketing, and strategies to adapt and thrive in this evolving environment.

The Cookie Landscape: A Brief Overview
Cookies have long been a drag on online tracking and targeting. These small pieces of data stored in users' browsers allowed marketers to gather information about user behavior, preferences, and interactions. This information, in turn, supported personalized advertising campaigns and optimized user experiences. However, growing concerns about privacy, user consent, and regulatory changes have led to a shift away from this traditional method of tracking.
The Rise of Privacy Regulations
Recent regulatory developments, particularly the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), have focused attention on user data protection and privacy rights. These regulations have ushered in a new era of digital transparency, giving users more control over their personal data. As a result, third-party cookies, often used without the user's express consent, become obsolete.
Implications for Digital Marketers
A cookie-free future presents both challenges and opportunities for digital marketers:
Data Collection and Targeting: Marketers will need to find alternative methods for collecting user data and serving targeted ads as the traditional cookie-based approach becomes less effective.
Personalization: With limitations on data tracking, achieving a personalized user experience will require innovative strategies that respect user privacy while providing relevant content.
Measurement and Analytics: Metrics using third-party cookies, such as attribution and cross-device tracking, will need to evolve to provide accurate statistics in a cookie-free environment.
User Experience: As users become more privacy conscious, brands that prioritize transparent data practices and respectful user experiences will stand out.
Strategies for adapting to a cookie-free landscape
First-Party Data: Focus on collecting and using your own first-party data, obtained through direct interactions with users on your website or in your app. This data is more reliable and ethically obtained.
Contextual Advertising: A move towards contextual advertising, where ads are displayed based on the content of a web page rather than data about individual users.
Consent Driven Marketing: Obtain user's express consent to collect and use data. Implement robust consent management systems to ensure regulatory compliance.
Advanced Technologies: Explore advanced technologies such as machine learning and artificial intelligence to create predictive models that can predict user preferences without invasive tracking.
Collaboration and Partnerships: Partner with publishers and platforms that prioritize user privacy and ethical data practices.
Embrace a Privacy Policy: Position your brand as a champion for user privacy by being transparent about your data practices and respecting user choices.
Conclusion
A future without cookies represents a key moment in the evolution of digital marketing. While change may seem challenging, it also represents a unique opportunity to build more meaningful and considerate relationships with users. By adapting your strategies to meet user expectations and privacy regulations, you can navigate this environment with confidence and continue to deliver valuable experiences to your audience. Embrace this shift and let it inspire you to innovate and discover new ways to connect and engage in a cookie-free world.
#CookielessFuture#PrivacyFirst#DigitalMarketingShift#AdaptAndThrive#DataPrivacy#UserExperience#FirstPartyData#ContextualAdvertising#ConsentDrivenMarketing#EthicalDataPractices#PersonalizationStrategies#InnovativeMarketing#UserPrivacy#MarketingRegulations#DigitalTransformation#UserConsent#DataCompliance#TransparentMarketing#BrandTrust#MarketingInnovation
0 notes
Video
#LibraryPrivacy
#PatronConfidentiality
#LibraryConfidentiality
#PrivacyRights
#DataPrivacy
#ConfidentialityAgreement
#LibraryEthics
#UserPrivacy
#ConfidentialityPolicy
#PrivacyProtection
#LibraryRecords
#InformationPrivacy
#IntellectualFreedom
#PrivacyAwareness
#LibrarySecurity
0 notes
Text

📵 #WhatsAppUpdate: In a move to boost user privacy, WhatsApp has rolled out a new feature preventing Android users from taking screenshots of profile pictures.
This safety measure is automatic and cannot be altered. "Your privacy, our priority!" Says Whatsapp in their statement.
#UserPrivacy #Android #NoMoreScreenshots #SafetyFirst #TechNews #WhatsApp
0 notes
Text
Facebook's Historic Dividend Payout Boosts Stock Prices: A Win for Shareholders and the Future
#cashreserves #CEO #competition #consistentprofits #corebusiness #dividendpayment #dividendpayout #Ecommerce #facebook #financialstrategy #futureperformance #Inc. #industryexperts #longtermgrowthprospects #MarkZuckerberg #MetaPlatforms #misinformation #onlinebanking #publiclytradedcompany #regulatoryscrutiny #Resilience #Stockprices #tangiblereturns #userprivacy #valuetoshareholders #virtualreality
#Business#cashreserves#CEO#competition#consistentprofits#corebusiness#dividendpayment#dividendpayout#Ecommerce#facebook#financialstrategy#futureperformance#Inc.#industryexperts#longtermgrowthprospects#MarkZuckerberg#MetaPlatforms#misinformation#onlinebanking#publiclytradedcompany#regulatoryscrutiny#Resilience#Stockprices#tangiblereturns#userprivacy#valuetoshareholders#virtualreality
0 notes
Link
The Pros And Cons Of VPN Use For Different Tasks
1 note
·
View note
Link
The adult entertainment industry is embroiled in a battle over online age verification. This article explores the recent developments in Texas, where a new law mandating age verification for pornographic websites has led to Pornhub pulling out of the state entirely. Texas Law Requires Age Verification for Adult Websites Texas House Bill 1181, enacted in September 2024, requires websites offering sexually explicit content to verify the age of their users before granting access. This verification can be achieved through digital identification or a commercial age verification system. Proponents of the legislation argue that it's necessary to protect minors from accessing harmful content online. However, the law has sparked significant controversy, raising concerns about its effectiveness and potential violation of free speech rights. Pornhub Departs Texas Market, Citing Ineffectiveness of Age Verification Law In response to the new law, Pornhub, one of the world's most popular adult websites, has opted to exit the Texas market entirely. The company's homepage now displays a message to users in Texas explaining their decision. Pornhub argues that the age-verification requirement is not only an infringement on adult users' right to access protected speech but also a flawed solution. They claim that similar laws in other states have simply driven users away from legitimate, age-verified platforms towards unverified websites with potentially weaker safety measures. The company proposes an alternative approach – implementing age verification at the device level. This would allow for access control based on pre-existing verification settings on users' devices, eliminating the need for individual verification on each website. Texas Law Faces Legal Challenges and Criticism The Texas age-verification law has been met with legal opposition from the Free Speech Coalition, an adult-industry advocacy group. The organization, along with other plaintiffs, challenged the law in court, arguing that the age verification requirement is unconstitutional. Critics of the law raise several concerns: Free Speech Concerns: They argue that the law creates an unnecessary barrier to accessing protected content for adults. Ineffectiveness: Opponents claim the law simply pushes users towards unverified websites, potentially exposing them to greater risks. User Privacy: Concerns exist regarding the collection and storage of user data required for age verification. Financial Impact: The law could potentially harm the revenue streams of adult content creators and publishers. The recent court decision upholding the legislation has drawn criticism from the Free Speech Coalition, who likened the situation to the canary in the coal mine – a warning sign for the potential stifling of free speech online. The Rise of VPNs as Users Seek Workarounds In the wake of Pornhub's exit, Google Trends data suggests a significant rise in searches for Virtual Private Networks (VPNs) across Texas. Users are likely exploring VPNs as a potential workaround to access blocked content. However, it's important to note that using VPNs to bypass age verification laws might be illegal in Texas. Additionally, VPNs can have security risks and may not always provide reliable access to restricted content. The Future of Online Age Verification: Balancing User Privacy and Safety The Texas law represents a contentious issue in the online regulation landscape. Finding a balance between protecting minors, safeguarding user privacy, and upholding free speech rights remains a complex challenge. Here are some key questions to consider: Can effective age-verification systems be implemented without infringing on user rights? How can we ensure user privacy is protected when implementing age verification measures? Are there alternative solutions that could better safeguard children online without hindering adult access to legal content? The debate surrounding the Texas law is likely to continue, with potential implications for online age verification practices nationwide. FAQs Q: Why did Pornhub leave Texas? A: Pornhub exited the Texas market in response to a new law requiring age verification for adult websites. The company believes the law is ineffective and infringes on adult users' rights. Q: Is the Texas age-verification law constitutional? A: The law was recently upheld by a federal appeals court. However, the Free Speech Coalition is challenging its constitutionality in court. Q: Are VPNs a safe and legal way to bypass age verification in Texas? A: Using a VPN to bypass age verification might be illegal in Texas. Additionally, VPNs can have security risks and may not always be reliable for accessing restricted content.
#adultcontentregulation#constitutionalrights#digitalrights#freespeech#internetfreedom.#Legalchallenges#onlinecensorship#onlineprivacy#Pornhub#PornhubExitsTexasMarket#Texasageverificationlaw#userprivacy#VPNs
1 note
·
View note
Text
Meta's Plan to Fight Fake News & Make Elections Fairer
#2024USelections #artificialintelligence #civicengagement #combatingmisinformation #democraticprocess #eligiblevoters #factcheckingorganizations #increasingtransparency #machinelearning #Meta #politicaladvertising #userprivacy
#Politics#2024USelections#artificialintelligence#civicengagement#combatingmisinformation#democraticprocess#eligiblevoters#factcheckingorganizations#increasingtransparency#machinelearning#Meta#politicaladvertising#userprivacy
0 notes
Link
The updated privacy policy of WhatsApp can be seen as a move to ensure its seamless expansion into retail entity. In the longer run — it’s obvious that WhatsApp is integrating greater into Facebook group so that Facebook, WhatsApp and Instagram all become part of one package.
0 notes
Link
https://bit.ly/3CfP9KQ - 📰 The #SafetyDetectives cybersecurity team reports hackers on a Telegram channel allegedly exposed admin credentials of i2VPN, a freemium VPN service, including user and data center information. #Cybersecurity #DataBreach 📱 The hackers shared the VPN service’s dashboard URL, admin's credentials, and screenshots of the backend of the dashboard. i2VPN, available on Google Play and the App Store, has been downloaded over 500,000 times. Each download could correlate to a user account potentially impacted by this breach. #VPN #CyberAttack 👥 User data such as IDs, account names, registered email addresses, and premium subscription details, including payment methods and expiry dates, were allegedly exposed. This data could be used by hackers for fraud or spying activities. #UserPrivacy #OnlineSafety 📍 The breach was posted on an Arabic-speaking Telegram channel, potentially exposing the accounts of over 500,000 users. Cyberattackers could use this information for phishing attempts or to find a backdoor into users' browsing activities. #Phishing #InfoSec 🔒 If you suspect your account was affected, consider whether to continue using the service, review accounts accessed while using the VPN, and scan your device for sensitive files to enhance security. #CyberHygiene #DataProtection 🔔 Telegram, offering encryption and anonymity, is often used by hackers to communicate and post data breaches. By monitoring these channels, we can inform those potentially affected to act quickly. Always stay alert for unusual activity. Your digital well-being is in your hands.
#SafetyDetectives#Cybersecurity#DataBreach#VPN#CyberAttack#UserPrivacy#OnlineSafety#Phishing#InfoSec#CyberHygiene#DataProtection#StaySafeOnline#DigitalWellBeing
0 notes
Link
Is Google Incognito Really Private? Find Out How Protected You Are
0 notes