#data De-identification software
Text
Industry analysis provides a company with an understanding of its position relative to other companies in the industry. This can help them identify opportunities and potential threats, so they can prepare for the present and future. MRI Research helps organizations to figure out whats happening in a given industry, including demand and supply statistics, degree of competition, state of competition with other emerging industries, future prospects considering technological changes, and external factors on the industry.
0 notes
Text
Some thoughts on institutional research software management and persistent identification
Pablo de Castro, Open Access Advocacy Librarian at U Strathclyde
(with thanks to Alan Morrison, Research Data Management Officer, for the explanation on institutional workflows around research software at Strathclyde Uni)
See also this previous StrathOA blog post by Alan Morrison "Depositing, distributing & citing software and code (A Zenodo – GitHub integration)"
A webinar on "DOIs for research software" will be organised by DataCite on Wed May 24th (in two weeks at the time of writing). This forthcoming event provides a good opportunity to share some thoughts on research software and the attempts to persistently identify it. These thoughts address the way institutions may or may not be specifically supporting research software management, with some specific considerations on persistent identifiers thrown on top. These latter thoughts are driven by one of the questions immediately raised by the event title: why is it called "DOIs for software" instead of "persistent identifiers for software"?
a. On research software management and its support from institutions
1. Research software is a key part of the gradually-developing European Open Science Cloud (EOSC). Moreover, research software is also a critical element when discussing research reproducibility
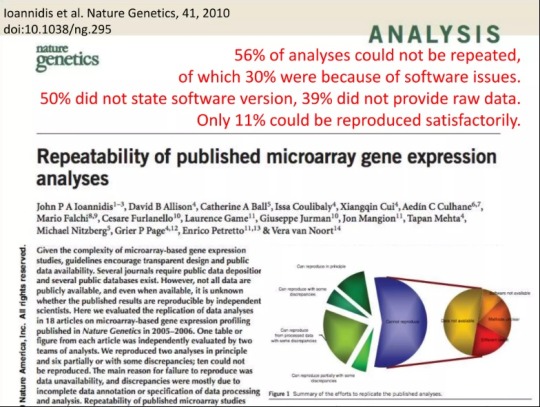
Slide from presentation “Software – a different kind of research object?” delivered by Neil Chue-Hong (Software Sustainability Institute) within the U Lancaster 3rd Data Conversation linked below (click on the image to access the full deck of slides)
2. While data repositories have also been collecting software for quite some time, this tends to be a researcher-led task. Proactive institutions are definitely able to support their academics for this specific purpose, usually within a wider conversation on Research Data Management – see for instance this inspiring 3rd Data Conversation "Software as data" held by colleagues at Lancaster University on Oct 3rd, 2017.
3. It's not that frequent however for institutions to independently address research software management as a separate area with its specific workflows and resources, but rather as part of the RDM-related work. RDM policies are quite widespread – including a recently issued RDMS policy at Strathclyde – but they tend not to include specific sections devoted to research software management.
4. When discussing general worklines like persistent identifiers for research software, the perspective of the institution is very relevant. Members of an institutional Open Research team are arguably best placed to deliver the sort of advice on Open Research implementation that would ensure that research software is always persistently identified. Critically, institutional Open Research teams are able to provide this advice in a discipline-agnostic way. This places them at the forefront of any specific dissemination activity around PIDs, not just for software but for any other entity too (including datasets but also projects or research equipment and facilities).
5. The intersection between persistent identification and institutional advocacy offers Open Research implementation teams a potential way into a more holistic support for the adequate management of the various research outputs produced by research groups, departments and schools.
b. On persistent identifiers for research software (or for any other entity in the area of "emerging PIDs" such as geosamples, conferences or research equipment and facilities)
A prominent research information management workflow modeller made the following remark during a discussion on PIDs at a recent euroCRIS event: "After extensively discussing the issue within the team, we decided not to implement a PID-issuing feature for all sorts of entities in [specific commercial CRIS solution] – which we could easily do from a technical perspective – because we could add to the confusion by enabling a mechanism to inadvertently create duplicate unique persistent identifiers for those entities".
An interesting example for this risk of duplication is provided by the VasoTracker software developed by researchers at the Universities of Strathclyde and Durham within the 'Optical Cannula' Wellcome-funded project, persistent grant ID https://doi.org/10.35802/202924 (among other acknowledged funding sources). As described on the VasoTracker website, this is a collection of open source tools for studying vascular physiology. The motivation for its development is also explained in the homepage:

This VasoTracker software not having been deposited in the system [Pure] that Strathclyde uses as a data repository, it has no DOI. The reasons why it hasn't been deposited probably come down to (i) the frequent misconception by researchers that datasets only apply to supplementary data underpinning publications and (ii) the probable wish to avoid the need to keep what has quickly become a live software package updated in several places at the same time – which may have led to choosing the website (and its associated github repository) as the default 'containers' for the code.
So would Strathclyde researchers developing code and their institutional Open Research support teams learn any new tricks at a webinar on "DOIs for research software"? Presumably yes, even if it were just on how Zenodo can help with the deposit of code, its maintenance and versioning. Plus perhaps DataCite will soon start supporting the issuing of DOIs for research software via Fabrica like it's already doing for geosamples and might one day do for research instruments and facilities.
There is however one interesting aspect regarding this VasoTracker software in line with the remark above on the risk of "inadvertently creating duplicates for unique PIDs". VasoTracker already has a PID. It's a RRID and not a DOI, granted (hence the nuanced title for the DataCite webinar?) but still a persistent identifier. How this RRID: SCR_017233 came to be assigned is not easy to tell. It's highly unlikely that this was a result of the outreach effort from the researchers involved in its development – it looks rather as if it had been automatically identified by some algorithm searching all across the Internet, including all github repositories.
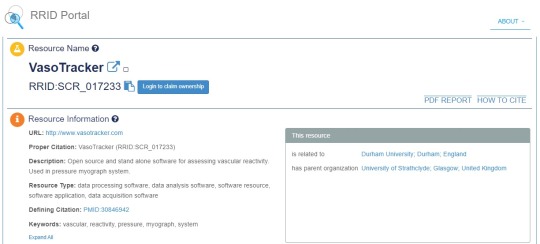
In fact, AI-driven PID cross-linking routines could quite quickly get the PID Graph displayed that we are so painstakingly building these days. The SciCrunch portal that hosts all these RRIDs is in fact able to crawl the references to a specific 'identified entity' (a software package in this case, but also a research instrument or facility or an antibody) in the published research literature (with the caveat that it needs to be available Open Access, otherwise even the super-clever modern algorithm will crash into the old-fashioned profit-driven paywalls).

The SciCrunch identification of the research publications that cite this RRID-tagged piece of software is not perfect, or not yet: the list on the RRID webpage only includes two of the seven references shown on the VasoTracker webpage (as identified by the software creators themselves). The fact that these references appear at all on the very same SciCrunch page where this RRID: SCR_017233 is described is a huge progress anyway and a hint at what we will be able to achieve in the not-so-distant future.
The risks of duplication highlighted by the research information management colleague at the euroCRIS meeting should however be kept in mind during the process of expanding the DOI coverage. While duplication is not necessarily an issue per se, it would make sense for the different PID initiatives to enable some (reasonably simple) mechanism to map duplicate entries to each other.
#research software#research data management#persistent identifiers#PIDs#DataCite#PID graph#VasoTracker
2 notes
·
View notes
Text
BBS Limited Review

BBS Limited Review - Is this broker legitimate or a fraud?
Given the growing evidence pointing to BBS Limited's involvement in fraudulent operations, potential investors are advised to proceed with care before investing, particularly in areas prone to forex scams, cryptocurrency scams, dating scams, and CFD scams. We provide a complete study and throw light on the broker's operations and any red flags with our in-depth BBS Limited Review. Even though you should always do your research, the information at hand suggests that BBS Limited is quite likely to be a scam broker.
BBS Limited Website - www.bbslimited.co
Website Availability - NO
BBS Limited Address - 207 9 Ave SW, Calgary, Alberta, T2P 1K3, Canada
BBS Limited Warning - Ontario Securities Commission (Ontario), Autorité des marchés financiers (Quebec), and British Columbia Securities Commission (Columbia)
Domain Age -
- Domain Name: bbslimited.co
- Registry Domain ID: D2E0A4CD178004F6282EC002A3FD9B06D-GDREG
- Registrar WHOIS Server: whois.publicdomainregistry.com
- Registrar URL: publicdomainregistry.com
- Updated Date: 2024-03-07T03:19:27Z
- Creation Date: 2023-01-31T18:30:24Z
- Registry Expiry Date: 2025-01-31T18:30:24Z
Key indicators that show if BBS Limited is a scam
Several compelling reasons and disturbing data have led to the identification of BBS Limited as a probable scam. Most scam brokers lack openness in their operations, neglecting to disclose detailed information about their management team, company plan, and financial status. This lack of openness raises concerns and prevents potential investors from making sound decisions. BBS Limited, based in Calgary, Alberta, Canada, operates without financial market monitoring and is unregulated. Despite its claim of offering a simple trading platform with automatic options, the lack of a trading license raises concerns. The platform's features, including software characteristics and mobile app availability, are unknown and put potential traders in a state of uncertainty. Due to these concerns, proceed with caution while considering an involvement with BBS Limited.
Exposing the Negative BBS Limited Reviews
The number of unfavorable BBS Limited reviews on several websites is a major element in the classification of BBS Limited as a possible fraud. Reputable websites like Trustpilot, Sitejabber, Scam Bitcoin, and others are quickly examined and show a steady flow of complaints against BBS Limited. It is crucial to examine every detail carefully to determine a broker's reliability.
Taking Preventative Actions Against Unreliable Brokers like BBS Limited
Conduct Comprehensive Research
Before engaging with any broker, such as BBS Limited, safeguard your interests by conducting an extensive investigation to thwart potential scams. Ensure their legitimacy by delving into various sources, including an BBS Limitedreview. Scrutinize reviews, testimonials, and user feedback from credible outlets to gauge their trustworthiness.
Verify Regulatory Credentials
Ensure that the broker holds accreditation and operates under the oversight of a recognized financial regulatory authority in your jurisdiction. This step provides a crucial layer of oversight and protection for traders.
Prioritize Secure Payment Methods
Prioritize the use of secure payment options that offer buyer protection. It's essential not to divulge sensitive financial information to unfamiliar or untrustworthy brokers.
Beware of Unattainable Promises
Exercise caution when encountering brokers that make extravagant claims of substantial profits with minimal risk. Such promises often serve as warning signs of potential scams.
Stay Informed
Staying informed is your shield against financial fraud. By keeping up with the latest fraud trends and warning signs in the financial sector, you enhance your ability to spot potential scams and protect your investments. Vigilance and knowledge are essential in identifying red flags, particularly when dealing with brokers.
File a Complaint against BBS Limited if scammed
Seeking Justice: File Complaints against BBS Limited at Scam Bitcoin
If you suspect you have been a victim of the BBS Limited scam or any other forex scam, cryptocurrency scam, binary scam, or investment fraud, you should first know that recovery is possible from scams. Scam Bitcoin Team is a valuable resource, including the BBS Limited review, that offers assistance to victims of fraudulent schemes. Our consultation is free and we guide you through the process of recovering from financial losses.
File a Quick Complaint Here
More Scam Broker Reviews
Moreover, we offer insights through the BBS Limited review and other relevant reviews to raise awareness about potential scams.
Keep in mind that staying informed and aware is important if you want to safeguard yourself against fraud and make wise choices in trading and investing. If you believe you've been scammed, seeking help from reputable organizations like Scam Bitcoin can be crucial to recovering and preventing future incidents.
Read Scam Brokers 2024
Scam Broker Reviews
Our Social Pages
Facebook Page
Twitter
Reddit
Read the full article
0 notes
Text
SAP GRC Demo

SAP GRC Demo: A Hands-On Guide to Streamlining Compliance
Governance, Risk, and Compliance (GRC) are becoming increasingly critical for businesses in today’s complex regulatory landscape. SAP GRC offers solutions that help organizations manage compliance, reduce risk, and improve operational efficiency. A well-run SAP GRC demo is the perfect way to showcase these benefits to your stakeholders.
What is SAP GRC?
SAP GRC is a modular software platform that provides tools and features to:
Manage Risks: Identify, analyze, assess, mitigate, and monitor risks across the enterprise.
Ensure Compliance: Automate compliance assessments, implement internal controls and manage regulatory reporting requirements.
Control Access: Enforce segregation of duties (SoD), manage user authorizations, and streamline access provisioning processes.
Critical Modules in SAP GRC
A typical SAP GRC demo will usually highlight some of these essential modules:
Access Control: This is the core module for managing access, identifying SoD conflicts, and automating user provisioning and de-provisioning.
Process Control: You can design, document, and monitor business process controls with workflow-based automation.
Risk Management: Provides the framework for continuous risk identification, analysis, risk response, and real-time risk monitoring.
Preparing for an Effective SAP GRC Demo
A successful demo requires planning and preparation. Here’s what to consider:
Audience and Objectives: Tailor the demo to the specific audience (IT, business managers, executives) and focus on the pain points and goals that SAP GRC can address.
Use Cases: Select a few relevant business scenarios that showcase SAP GRC’s value proposition. Examples include automating financial controls, managing IT security risks, or streamlining compliance reporting.
Demo Script and Data: Develop a straightforward script outlining the scenario, the features being demonstrated, and their benefits. Prepare realistic sample data that mirrors the audience’s environment.
During the Demo
Keep it Engaging: Use visuals and live data, and avoid excessive technical jargon.
Highlight Benefits: Focus on the business impact and value that SAP GRC can deliver, such as increased efficiency, reduced risk, and improved compliance.
Encourage Participation: Allow for questions and invite feedback from the audience.
After the Demo
Follow-up: Provide additional documentation resources and offer the opportunity to schedule more specific follow-up sessions.
Measure Success: Collect participant feedback and track potential lead conversion opportunities to evaluate the demo’s effectiveness.
Example:
Demo Scenario
Consider a demo scenario focusing on access control and SoD management. This could include:
Showcasing how SAP GRC identifies potential SoD conflicts during an access request process.
Demonstrating how risk analysis and mitigation workflows are triggered automatically based on identified risks.
Illustrating how reporting tools streamline compliance audits and provide insights into access risks.ConclusionA well-executed SAP GRC demo can be a powerful tool for demonstrating the platform’s value and building a compelling case for investment. By understanding your audience, focusing on real-world scenarios, and preparing effectively, you can showcase how SAP GRC can contribute to your organization’s risk management and compliance strategies.
youtube
You can find more information about SAP GRC in this SAP GRC Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP GRC Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on SAP GRC here – SAP GRC Blogs
You can check out our Best In Class SAP GRC Details here – SAP GRC Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
#Unogeeks #training #Unogeekstraining
0 notes
Text
Saudi Arabia Logistics Automation Market Share, Latest Trends, Industry Size, Growth & Report 2024-2032
According to IMARC Group latest report titled “Saudi Arabia Logistics Automation Market: Industry Trends, Share, Size, Growth, Opportunity and Forecast 2024-2032, offers a comprehensive analysis of the industry, which comprises insights into the logistics market size in Saudi Arabia. The report also includes competitor and regional analysis, and contemporary advancements in the market.
The market is currently witnessing strong growth in 2023. The Saudi Arabia Logistics Automation Market to exhibit moderate growth during 2024-2032.
Saudi Arabia Logistics Automation Market Overview:
Logistics automation involves the integration of technology to streamline and optimize various processes within the supply chain. Utilizing advanced software, robotics, and artificial intelligence, logistics automation enhances efficiency and accuracy in tasks such as inventory management, order processing, and transportation. Automated systems facilitate real-time tracking, reducing errors and delays, and ultimately improving overall operational productivity.
With features like warehouse automation, autonomous vehicles, and predictive analytics, logistics automation responds to the increasing demand for faster, more cost-effective, and environmentally sustainable supply chain solutions. This transformative technology not only increases the speed and reliability of logistics operations but also allows businesses to adapt to the dynamic demands of the modern market.
Request Free Sample Report: https://www.imarcgroup.com/saudi-arabia-logistics-automation-market/requestsample
Saudi Arabia Logistics Automation Market Trends:
The market in Saudi Arabia is majorly driven by the nation's commitment to technological advancement and efficient supply chain management. Furthermore, the increasing demand for e-commerce and the growth of the retail sector have amplified the need for agile and technologically advanced logistics solutions. Automated systems, including robotic warehouses and automated order fulfillment, cater to the rising volume of online transactions, ensuring timely and accurate deliveries. Besides, the geographical expanse of Saudi Arabia and its strategic location as a logistics hub in the Middle East create a necessity for sophisticated supply chain solutions.
Automation streamlines complex processes, offering a competitive edge in handling and transporting goods efficiently. Moreover, the government's commitment to infrastructure development, including smart cities and transport networks, has increased the adoption of logistics automation. Integrating technologies like IoT, AI, and robotics optimizes logistics networks, aligning with the nation's ambitions for a technologically advanced future. Additionally, the COVID-19 pandemic has underscored the importance of resilient and adaptable supply chains. The emphasis on contactless operations, increased demand for essential goods, and the need for real-time tracking have accelerated the adoption of logistics automation in Saudi Arabia.
Explore the Full Report with Charts, Table of Contents, and List of Figures: https://www.imarcgroup.com/saudi-arabia-logistics-automation-market
Saudi Arabia Logistics Automation Market Segmentation:
Component Insights:
Hardware
Mobile Robots (AGV, AMR)
Automated Storage and Retrieval Systems (AS/RS)
Automated Sorting Systems
De-palletizing/Palletizing Systems
Conveyor Systems
Automatic Identification and Data Collection (AIDC)
Order Picking
Software
Warehouse Management Systems (WMS)
Warehouse Execution Systems (WES)
Services
Value Added Services
Maintenance
Function Insights:
Warehouse and Storage Management
Transportation Management
Enterprise Size Insights:
Small and Medium-sized Enterprises
Large Enterprises
Industry Vertical Insights:
Manufacturing
Healthcare and Pharmaceuticals
Fast-Moving Consumer Goods (FMCG)
Retail and E-Commerce
3PL
Aerospace and Defense
Oil, Gas and Energy
Chemicals
Others
Regional Insights:
Northern and Central Region
Western Region
Eastern Region
Southern Region
Competitive Landscape:
The competitive landscape of the industry has also been examined along with the profiles of the key players.
Key highlights of the Report:
Market Performance (2018-2023)
Market Outlook (2024-2032)
COVID-19 Impact on the Market
Porter’s Five Forces Analysis
Strategic Recommendations
Historical, Current and Future Market Trends
Market Drivers and Success Factors
SWOT Analysis
Structure of the Market
Value Chain Analysis
Comprehensive Mapping of the Competitive Landscape
Note: If you need specific information that is not currently within the scope of the report, we can provide it to you as a part of the customization.
About Us:
IMARC Group is a leading market research company that offers management strategy and market research worldwide. We partner with clients in all sectors and regions to identify their highest-value opportunities, address their most critical challenges, and transform their businesses.
IMARC’s information products include major market, scientific, economic and technological developments for business leaders in pharmaceutical, industrial, and high technology organizations. Market forecasts and industry analysis for biotechnology, advanced materials, pharmaceuticals, food and beverage, travel and tourism, nanotechnology and novel processing methods are at the top of the company’s expertise.
Contact Us:
IMARC Group
134 N 4th St. Brooklyn, NY 11249, USA
Email: [email protected]
Tel No:(D) +91 120 433 0800
United States: +1-631-791-1145 | United Kingdom: +44-753-713-2163
0 notes
Text
Unveiling the Landscape: Navigating the World of Digital Terrain Models
In the realm of geospatial technology, the Digital Terrain Model (DTM) emerges as a powerful tool, offering a three-dimensional representation of the Earth's surface. Beyond a mere digital elevation map, a DTM intricately captures the terrain's features, fostering a deeper understanding of landscapes. Join us as we embark on a journey through the fascinating world of Digital Terrain Models, exploring their applications, creation process, and the transformative impact they have on various industries.
The Essence of Digital Terrain Models: A Digital Terrain Model is a digital representation of the topography of a geographical area. Unlike its counterpart, the Digital Surface Model (DSM), which includes both natural features and built structures, a DTM focuses solely on the bare Earth's terrain. It acts as a visual blueprint, showcasing elevation changes, slopes, and landforms with remarkable precision.
Applications Across Industries: The versatility of Digital Terrain Models extends across a myriad of industries, revolutionizing the way professionals analyze and interpret geographical data. In urban planning, DTMs aid in understanding terrain variations for infrastructure development. In agriculture, they optimize land use planning by assessing slope gradients and water flow. Environmental studies benefit from DTMs by analyzing landscape changes, and in disaster management, these models assist in risk assessment and mitigation strategies.
Creating a Digital Terrain Model: The creation of a Digital Terrain Model is a meticulous process that combines cutting-edge technology and data acquisition methods. High-resolution satellite imagery, LiDAR (Light Detection and Ranging) data, and aerial surveys contribute to the creation of detailed and accurate DTMs. Advanced algorithms and software then process this data, generating a comprehensive digital representation of the Earth's surface.
Precision and Accuracy: The success of a Digital Terrain Model lies in its precision and accuracy. The data sources used, such as LiDAR, provide elevation information with high resolution, ensuring that subtle terrain features are captured. This accuracy is crucial for industries where precise elevation information is paramount, such as in civil engineering projects or environmental modeling.
Visualizing Landscape Dynamics: DTMs offer more than static elevation data; they become dynamic tools for visualizing landscape changes over time. By integrating time-series data, professionals can analyze terrain evolution, monitor erosion patterns, and assess the impact of human activities on the landscape. This dynamic visualization capability enhances decision-making processes across diverse fields.
In the dynamic realm of Geographic Information Systems (GIS), Digital Elevation Models (DEM) take center stage, revolutionizing the way we analyze and interpret terrain data. A pivotal component of GIS, DEM serves as the key to unlocking a wealth of information about the Earth's surface. In this exploration, we delve into the intricate world of DEM in GIS applications, uncovering its significance, creation process, and the transformative impact it has on spatial analysis and decision-making.
Understanding DEM in GIS: A Digital Elevation Model in GIS is a digital representation of the Earth's topography, capturing elevation data across a specified area. By utilizing elevation values organized in a grid format, DEM provides a three-dimensional visualization of the terrain. This data-rich model becomes an invaluable asset in GIS applications, enabling professionals to analyze, model, and interpret landscapes with a heightened level of precision.
Applications Across GIS Industries: The integration of DEM in GIS significantly enhances spatial analysis across various industries. In urban planning, DEM facilitates slope analysis, aiding in the identification of suitable locations for infrastructure development. Hydrologists leverage DEM to model watersheds, analyze drainage patterns, and predict flood risk. In forestry, DEM helps assess terrain ruggedness for ecological studies. The applications extend to telecommunications, transportation planning, and natural resource management.
DEM Creation Process: Creating a Digital Elevation Model involves a meticulous process of data acquisition, processing, and representation. Technologies such as LiDAR, satellite imagery, and aerial surveys contribute to the collection of elevation data. GIS software processes this data, generating a grid of elevation values that forms the basis of the DEM. The accuracy of the DEM is contingent on the quality and resolution of the input data, making data acquisition methods a critical aspect of the creation process.
Spatial Analysis and Decision-Making: The precision of DEM elevates the spatial analysis capabilities within GIS. Professionals can conduct line-of-sight analysis, viewshed analysis, and slope analysis to inform decision-making processes. In environmental management, DEM aids in assessing terrain vulnerability to natural disasters. The ability to model and simulate terrain conditions empowers decision-makers with insights that contribute to sustainable development and risk mitigation.
Interoperability and Integration: DEM seamlessly integrates with various GIS datasets, enhancing the interoperability of spatial information. This integration allows professionals to combine elevation data with other layers such as land use, hydrology, and infrastructure, creating comprehensive geospatial models. The interoperability of DEM in GIS fosters a holistic approach to spatial analysis, enabling a more nuanced understanding of the relationships between different geographical features.

For More Info:-
digital elevation model in gis
DEM in GIS
DTM
DTM in GIS
terrain modelling in gis
digital terrain model
digital elevation model in gis
digital elevation models
terrain modeling
satellite mapping
1 note
·
View note
Text
Streamlining Success: Understanding the Data Cleansing Process
In today's digital age, data has become the lifeblood of businesses, driving decisions, innovations, and strategies. However, the sheer volume of data generated daily often leads to inconsistencies, errors, and redundancies. This necessitates a crucial procedure known as data cleansing, which ensures that information remains accurate, reliable, and actionable. Let's delve into the intricacies of the data cleansing process and its significance.
Defining Data Cleansing: Data cleansing, also referred to as data scrubbing or data cleaning, is the methodical process of identifying and rectifying errors, inconsistencies, and inaccuracies within a dataset. These discrepancies can include misspellings, duplicates, incomplete records, outdated information, and formatting errors.
Importance of Data Cleansing: Clean and accurate data is vital for informed decision-making. It enhances the credibility of analytics, improves operational efficiency, and aids in generating reliable insights. Additionally, it ensures compliance with regulatory standards like GDPR, CCPA, and HIPAA, reducing risks associated with incorrect or outdated information.
Steps in the Data Cleansing Process:a. Data Assessment: Begin by assessing the existing dataset to identify issues and understand its structure and quality.b. Data Standardization: Normalize formats, remove special characters, and ensure uniformity in naming conventions to streamline data for consistency.c. De-duplication: Identify and eliminate duplicate entries to maintain data integrity and accuracy.d. Error Correction: Address misspellings, inconsistencies, and inaccuracies by leveraging algorithms or manual review to rectify errors.e. Data Validation: Validate data against predefined rules, ensuring its adherence to specified criteria and enhancing its reliability.f. Data Enrichment: Supplement existing data with additional information from reliable sources to enhance its value and completeness.
Tools and Technologies: Various software tools and technologies facilitate the data cleansing process. These tools utilize algorithms, machine learning, and artificial intelligence to automate tasks such as duplicate detection, error identification, and standardization.
Continuous Improvement: Data cleansing is an iterative process. Regularly revisiting and refining the process ensures that data remains accurate and up-to-date. Establishing protocols for ongoing data maintenance is essential for sustained data integrity.
In conclusion, data cleansing is a fundamental aspect of data management, ensuring that organizations work with accurate, reliable, and actionable information. By implementing a structured data cleansing process and utilizing appropriate tools and methodologies, businesses can unlock the full potential of their data, leading to more informed decision-making and improved operational efficiency.
For more info visit here:-
data cleansing techniques
tools for data cleaning
crm data cleaning
0 notes
Text
BCT Digital Enterprise Risk Management: Navigating Uncertainty with Confidence
In today’s fast-paced and interconnected business environment, organizations face an ever-expanding array of risks that can impact their operations, finances, and reputation. Enterprise Risk Management (ERM) is a strategic approach that organizations employ to identify, assess, and mitigate these risks, ensuring their sustainability and success. BCT Digital, a renowned provider of innovative software solutions, offers a comprehensive Enterprise Risk Management system designed to empower organizations with the tools they need to navigate uncertainty with confidence. In this article, we will explore the significance of Enterprise Risk Management in modern businesses and how BCT Digital is at the forefront of revolutionizing the way organizations manage risk.
The Importance of Enterprise Risk Management
Enterprise Risk Management is a structured and systematic approach that helps organizations identify, assess, and mitigate risks that could impact their strategic objectives. Risks can come from various sources, including financial, operational, strategic, compliance, and reputational factors. ERM is essential for organizations to adapt to changing environments, seize opportunities, and safeguard their operations and reputation.
Key Aspects of Enterprise Risk Management:
Risk Identification: The process of identifying potential risks that could affect the achievement of an organization’s objectives.
Risk Assessment: Evaluating the likelihood and potential impact of identified risks to prioritize them based on their significance.
Risk Mitigation: Developing and implementing strategies to minimize or eliminate risks and their potential negative effects.
Monitoring and Reporting: Continuously monitoring risk factors and providing regular reporting to stakeholders to ensure transparency and accountability.
BCT Digital’s Enterprise Risk Management System
BCT Digital’s Enterprise Risk Management system is an advanced software platform designed to help organizations proactively manage and mitigate risks. It offers a wide range of features and capabilities tailored to the specific needs of businesses across various sectors.
Key Features of BCT Digital’s Enterprise Risk Management System:
Risk Assessment Tools: The solution provides a suite of risk assessment tools, allowing organizations to identify, categorize, and assess risks comprehensively.
Regulatory Compliance: Ensures that organizations remain compliant with evolving regulatory requirements, reducing the risk of penalties and reputational damage.
Risk Mitigation Strategies: Offers tools for developing and implementing risk mitigation strategies, including scenario analysis and stress testing.
Incident Reporting and Response: Facilitates the reporting of incidents and tracking of their resolution, ensuring timely and effective responses.
Data Analytics and Reporting: The solution provides advanced reporting and analytics tools to provide stakeholders with valuable insights into risk and performance.
User Access Controls: Ensures secure user access to protect data integrity and confidentiality.
The Significance of BCT Digital’s Enterprise Risk Management System
BCT Digital’s Enterprise Risk Management system is pivotal for organizations for several compelling reasons:
Enhanced Risk Management: The solution empowers organizations to proactively manage risks, from financial and operational risks to compliance and strategic risks.
Regulatory Compliance: BCT Digital’s system ensures that organizations remain up-to-date with ever-changing regulatory requirements, reducing the risk of non-compliance penalties and reputational damage.
Efficient Risk Mitigation: The solution enables organizations to develop and implement strategies for mitigating risks efficiently, reducing potential negative impacts.
Data-Driven Decision-Making: The system’s reporting and analytics tools empower organizations to make informed decisions based on real-time data and risk performance.
Time and Cost Efficiency: Automation of ERM processes reduces the time and resources required for manual tracking and reporting.
Security and Data Protection: User access controls and secure data storage protect the confidentiality and integrity of sensitive risk management data.
In the age of rapid change and evolving business environments, Enterprise Risk Management is not just a best practice; it’s a strategic necessity. BCT Digital’s Enterprise Risk Management system is more than just a technological advancement; it’s a strategic imperative for organizations aiming to thrive in a complex and risk-prone environment. It’s about proactively managing risks, ensuring regulatory compliance, and efficiently mitigating potential negative impacts. BCT Digital is leading the way in this transformative journey, enabling organizations to navigate the challenges of risk management with precision and confidence, ultimately securing a stable and prosperous future.
0 notes
Text
Fwd: Course: Online.Palaeoproteomics.Nov2-9
Begin forwarded message:
> From: [email protected]
> Subject: Course: Online.Palaeoproteomics.Nov2-9
> Date: 7 October 2023 at 06:27:58 BST
> To: [email protected]
>
>
> Dear colleagues,
>
> This course might be of interest to people on this list: "Palaeoproteomics
> and Zooarchaeology by Mass Spectrometry (ZooMS)".
>
> Instructor: Dr. Michael Buckley (University of Manchester, UK).
>
> Schedule: Online live sessions on the 2nd, 3rd, 6th, 8th, and 9th
> of November; from 13:00 to 17:00 (Madrid time zone), plus 4 hours of
> participants working on their own.
>
> Places are limited to 12 participants and will be occupied by strict
> registration order.
>
> Course overview
>
> In this course, participants will be introduced to paleoproteomic
> methods that will include various R packages including MALDIquant,
> for ZooMS MALDI peptide mass fingerprint-based species identification,
> MSFragger for sequencing, and an introduction to incorporating proteomic
> sequence data into molecular phylogeny reconstruction using MEGA.
>
> During the course, participants will first be introduced to some theory
> with illustrative examples (both from simulated data as well as some
> real datasets) and will then learn how to interpret the data as well as
> how to assess their reliability.
>
> More information and registration:
> https://ift.tt/NzoIJGv
>
> or write to [email protected]
>
> Best regards
>
> Sole
>
> -- Soledad De Esteban-Trivigno, PhD Director Transmitting Science
> https://ift.tt/Pi5Gmhb
>
> Twitter @SoleDeEsteban Orcid: https://ift.tt/sWR28Sv
>
> Under the provisions of current regulations on the protection of personal
> data, Regulation (EU) 2016/679 of 27 April 2016 (GDPR), we inform you
> that personal data and email address, collected from the data subject
> will be used by TRANSMITTING SCIENCE SL to manage communications through
> email and properly manage the professional relationship with you. The
> data are obtained based on a contractual relationship or the legitimate
> interest of the Responsible, likewise the data will be kept as long as
> there is a mutual interest for it. The data will not be communicated
> to third parties, except for legal obligations. We inform you that you
> can request detailed information on the processing as well as exercise
> your rights of access, rectification, portability and deletion of
> your data and those of limitation and opposition to its treatment by
> contacting Calle Gardenia, 2 Urb. Can Claramunt de Piera CP: 08784
> (Barcelona) or sending an email to [email protected] or
> https://ift.tt/Jv9ckjS. If you consider that the
> processing does not comply with current legislation, you can complain
> with the supervisory authority at www. aepd.es . Confidentiality. -
> The content of this communication, as well as that of all the attached
> documentation, is confidential and is addressed to the addressee. If you
> are not the recipient, we request that you indicate this to us and do not
> communicate its contents to third parties, proceeding to its destruction.
> Disclaimer of liability. - The sending of this communication does not
> imply any obligation on the part of the sender to control the absence of
> viruses, worms, Trojan horses and/or any other harmful computer program,
> and it corresponds to the recipient to have the necessary hardware
> and software tools to guarantee both the security of its information
> system and the detection and elimination of harmful computer programs.
> TRANSMITTING SCIENCE SL shall not be liable.
>
> Links: ------
> https://ift.tt/Yy5exAH
>
> Soledad De Esteban-Trivigno
0 notes
Text
Cloud-based Salesforce Implementation Services: Benefits

Salesforce CRM can increase employee and customer loyalty in a significant way. Salesforce can be confusing, expensive, and time-consuming for associations that lack the necessary knowledge.
Services for Salesforce Implementation
It is possible to achieve rapid revenue growth by using Salesforce Implementation Services.
We are bringing to you some important information regarding this particular Salesforce sector. This blog has been divided into different categories to make it easier for you. We will cover the following sections:
Six essential conditions for implementing Salesforce Services
Each setup requires a few essential components. Even if a single brick is missing, the configuration will collapse. Below are the six building blocks of Implementation.
Clear-Cut Strategy
The Salesforce Implementation team will work closely with you to evaluate your business practices and systems in order to recommend the best course of action.
Cloud Configuration and Setup
Salesforce’s biggest selling point is its cloud-based platform. If your Salesforce implementation firm needs to take this into consideration, then you are still alive. To automate business processes, you need to create email templates that are ready to use, a simple workflow and approval procedures.
Customization
Some technologies are only suitable for certain people. You would benefit from bespoke programming if you used your Salesforce system to its full potential.
Transfer of Information
After your plan has been created, your cloud configuration is complete, and your source code is customized, it’s time for you to move your data. Data migration is a critical part of the Implementation for Salesforce. The data migration process includes the following: extraction, cleaning and de-duplication of data, standardization, validation and importation into the Salesforce system.
The Integration of Technology
Next, we have the integration supporting block. Integration allows you to streamline your entire business from the software running on the hardware that you already own, all the way down to the hardware.
Technical Assistance
Maintenance and improvement are essential for a successful Salesforce setup. To achieve this, dependable Salesforce support is essential.
Why do you need services for Salesforce Implementation Services?
Change is the only constant, as the old saying goes. Salesforce is one of the most sophisticated, reliable and accessible cloud-based CRM platforms that the IT industry has ever seen. All of these factors show that this will remain the same.
Salesforce.com, and the Force.com Platform update on a quarterly release schedule — yes, I said “triannual releases” — beating out all other CRM tools and systems on the market. This is the primary reason for using Salesforce implementation services.
These enhancements are made three times a year, so you can rest assured that your system and personnel will be operating at the best level possible. Salesforce Implementation Services are necessary to keep pace with the system’s rapid evolution.
Implementation services for Salesforce: Benefits
You can enjoy the following benefits by using Salesforce Implementation Services.
Faster and more effective business operations
Salesforce automates mundane tasks like client identification, follow-up and meeting scheduling. The time it takes to move from a mustering of estimates to a real proposal, quotation, and finally to completing orders is significantly reduced.
Employee satisfaction at work increases
Many CRM systems offer their users the ability to set and track goals. A CRM program such as Salesforce makes use of excellent graphics to show the story of the sales funnel. Salesforce users can use these incredible capabilities to identify where they need more decisive effort, select the percentage of goals that have already been achieved, and estimate future results.
Improved Lead Management
Once your Salesforce system is established, it will allow you to convert leads automatically. Salesforce programs typically collect leads via outbound calls, website visits by users, and other marketing initiatives. Then, they inform sales reps about new leads that have been added to the pipeline.
Improved Business Functionality
Salesforce deployment is more efficient in terms of return on investments thanks to its excellent integration and functionality system. Salesforce CRM, once successfully implemented, offers centralized data about customers, multiple reports, statistical options and the ability to run it on any browser, desktop or tablet device.
Components of a top-notch Salesforce service provider
There are several things you should consider when choosing a Salesforce Implementation Services provider. You should be on the lookout for:
Reliability
Search the AppExchange or Salesforce.com platform for reviews of the agency.
Experience
Find out if the company has experience in managing your business.
Cost-effectiveness
It is important to determine whether you are able to pay the compensation the agency has estimated. Be sure that the budget is within reach before executing, as results can take some time to manifest even after implementation.
Flexibility
Be sure that the company you choose can meet your scheduling and work needs. Be sure that they will also listen to your suggestions.
Cloud Analogy offers Salesforce Implementation services
The years have passed. Cloud Analogy— IT Solutions and Salesforce Consulting Companies is the best Salesforce implementation. They provide fantastic Salesforce Consulting services around the globe. Cloud Analogy offers Salesforce Implementation Services.
Strategic Salesforce Implementation Plan
A well-structured project will help you achieve a greater return on your investment.
Your current Salesforce setup will be upgraded by reengineering initiatives that have been cleverly organized.
You can be sure that they will provide the most customized solutions for your business.
Affordable Salesforce Implementation Services
Conclusion
Proper Salesforce implementation is essential to achieve your goals for using the Salesforce CRM system. You know what to expect when you hire Salesforce Implementation Services. You know the fundamentals of a successful execution.
0 notes
Text
The Logistics Automation Software Market is Segmented by warehouse automation market (by component (hardware (Mobile Robots (AGV, AMR), automated storage and retrieval systems (AS/RS), automated sorting systems, de-palletizing/palletizing systems, conveyor systems, automatic identification and data collection (AIDC), order picking), software, and services), by end-user industry (food and beverage, post and parcel, groceries, general merchandise, apparel, manufacturing), by geography (North America, Europe, Asia Pacific, Latin America, Middle East, and Africa), and transportation automation market).
Download Free Sample Report - Logistics Automation Software Market
0 notes
Text
What Is Data Destruction? And What Are The Importance And Methods Of Data Destruction?

Data destruction refers to the process of permanently removing or erasing data from storage devices such as hard drives, solid-state drives, memory cards, and other media. The goal of data destruction is to ensure that sensitive or confidential information cannot be recovered or accessed by unauthorized individuals, even after the storage device has been discarded, sold, or repurposed. Data destruction is a critical practice for maintaining privacy, security, and compliance with regulations.
Importance Of Data Destruction:
Protection of Sensitive Information: Data destruction prevents unauthorized access to sensitive or confidential information, such as personal identification details, financial records, medical history, and trade secrets. This safeguards individuals and organizations from potential breaches and data leaks.
Prevention of Data Breaches: Improper disposal of storage devices without proper data destruction can lead to data breaches, where cybercriminals or malicious actors retrieve and exploit discarded data. This can result in financial losses, reputation damage, and legal consequences.
Compliance with Regulations: Many industries and regions have regulations that require organizations to ensure the proper disposal of data-containing devices. Failure to comply with these regulations can result in fines and legal penalties.
Risk Mitigation: Data destruction reduces the risk of data falling into the wrong hands, minimizing the potential for identity theft, fraud, and corporate espionage.
Environmental Responsibility: Proper data destruction involves securely disposing of electronic devices. This helps prevent electronic waste (e-waste) from accumulating and polluting the environment, as well as promotes responsible recycling practices.
Reputation Management: Safeguarding sensitive data through proper data destruction enhances an organization's reputation and builds trust with customers, partners, and stakeholders.
Preventing Data Resale: When selling or disposing of used devices, data destruction ensures that any personal or confidential information is permanently removed, preventing its potential use by subsequent owners.
Methods of Data Destruction:
Physical Destruction:
Shredding: Using specialized equipment to physically shred storage media into small pieces, making data recovery impossible.
Crushing: Applying significant force to crush storage devices, rendering data unreadable.
Disintegration: Breaking storage devices into tiny particles through mechanical processes.
Data Overwriting:
Standard Overwrite: Using software to overwrite data on storage devices with random or predefined patterns multiple times.
DoD 5220.22-M Method: Following the U.S. Department of Defense standard for data destruction, involving multiple passes of data overwrites.
NIST SP 800-88 Guidelines: Following the National Institute of Standards and Technology's recommended guidelines for secure data sanitization.
Degaussing:
This method uses a powerful magnetic field to erase data from magnetic storage devices such as hard drives. It renders the data unreadable and unrecoverable.
Magnetic Field: Using a degausser to expose storage devices to a powerful magnetic field, erasing the data by demagnetizing the storage media.
Secure Erase Software:
Specialized software can securely erase data by overwriting it with random patterns, making it nearly impossible to recover.
Specialized Tools: Utilizing software designed for secure data erasure, often with verification processes to ensure effectiveness.
Cryptographic Erasure:
Cryptographic erasure involves encrypting the data on the storage device using strong encryption algorithms. To destroy the data, the encryption keys are securely deleted or destroyed, making the data inaccessible and effectively destroyed. Cryptographic erasure is often used in cloud storage and remote data-wiping scenarios
Digital Data Destruction:
Digital data destruction involves the erasure or overwriting of data stored electronically. This method is typically applied to magnetic media, such as hard drives. Secure erasure techniques ensure that the data is permanently removed, making it virtually impossible to recover.
3R Technology
8002 S 208th St E105, Kent, WA 98032, United States
(206) 582-7100
0 notes
Text
Compliance Third-Party Solutions The Risk Management Solutions

The majority of industries are now focusing on the use of third party risk reduction. It's no longer just about meeting regulatory compliance requirements or keeping data secure - it's about protecting your customers and preserving the company's reputation.
The manual process and the disconnected procedures make it hard to oversee vendors over the entire life-cycle of relationships and even as standards for regulatory compliance alter. The use of a TPRM solution could aid.
The identification of risks from third parties
You probably use a variety of third-party vendors, which put your business at risk. Risks from third parties can involve cybersecurity, operational and legal risks, or even reputational. These can be vendors, suppliers, agencies, contractors, and infrastructure companies, for example. To find out extra information on anti-fraud system, you've to check out app de ponto eletrônico site.
Implementing efficient solutions for third party management will help your organization keep these partners from introducing unacceptably high risks. They must be incorporated into an enterprise risk framework, or in a separate manner, focusing only on one specific part of the business.
As the third-party risk landscape becomes more complex and complex, it is essential that you have a robust system of record to manage this risk. A system of record can help streamline and automate the process of conducting due diligence, assessments as well as monitoring. This includes the ability to carry out identification verification, risk analysis, adverse media review, and identification of supply chains without difficulty. It can help save both time and money as well as cut down on the the manual work that is required by every department.
Conducting Due Diligence
The process of due diligence involves evaluating a third-party to see if they are suitable for the task at being performed. This is often done before onboarding new suppliers and continues all through the duration of their existence.
Third-party risk management solutions automate the process of collecting and analyzing information from partners in business, service providers, and other third parties. The specialized TPRM software helps manage relationships, enables real-time tracking, compliance and risk assessments and problems, as well as monitoring of all third party relations.
The management of third-party risks could encompass any of a variety of risks, including security financial, operational, legal and social obligation. Data breaches caused from a company that has access to information about customers could result in a negative impression on your brand's reputation, and even fines or penalties. All of these risks should be analyzed by risk management programmers and should be reduced to a level that is acceptable.
Review of Third Party Performance
It is essential to continuously assess the risk of engaging with third party. This may include a more frequently-reviewed review procedure (typically using data feeds for cybersecurity rating) or monitoring the how they perform over time (using visual reports or dashboards as well as business intelligence).
It's crucial to know the various risks third entities can bring to your business. Understanding these particular risks can help you create standards to evaluate vendors, which will make it easier to onboard and control these vendors.
Conducting due diligence on other parties is more than a business best practice; it's a regulated obligation. The company is protected from liability if a third party causes a breach of security.
Monitoring the Performance of Third Party Partners
Due to breaches of personal data and interruptions to the process of supply, the regulators have increased the pressure on businesses to implement Third-party Risk (TPRM). However, whether your business is on the path to an official third-party risk management plan or has one in place, you will require methods, tools and content to ease the burden, expand the program and improve your understanding of the efficiency of the suppliers you work with.
Reducing time-consuming tasks by using an integrated method of storing and organizing information about suppliers including contracts, agreements and policies. Automate reassessments with pre-defined due dates as well as alerts and risk scores to ensure that your suppliers are keeping pace with your internal requirements.
0 notes
Text
Data De-identification or Pseudonymity Software market Unidentified Segments – The Biggest Opportunity Of 2023
Latest business intelligence report released on Global Data De-identification or Pseudonymity Software Market, covers different industry elements and growth inclinations that helps in predicting market forecast. The report allows complete assessment of current and future scenario scaling top to bottom investigation about the market size, % share of key and emerging segment, major development, and technological advancements. Also, the statistical survey elaborates detailed commentary on changing market dynamics that includes market growth drivers, roadblocks and challenges, future opportunities, and influencing trends to better understand Data De-identification or Pseudonymity Software market outlook.
List of Key Players Profiled in the study includes market overview, business strategies, financials, Development activities, Market Share and SWOT analysis are:
IBM (United States)
Thales Group (France)
TokenEx (United States)
KI DESIGN (United States)
Anonos (United States)
Aircloak European Union
AvePoint (United States)
Very Good Security (United States)
Dataguise (United States)
SecuPi (United States)
The most common technique to de-identify data in a dataset is through pseudonymization. Data De-identification and Pseudonymity software replace personal identifying data in datasets with artificial identifiers or pseudonyms. Companies choose to de-identify or pseudonymize their data to reduce their risk of holding personally identifiable information and comply with privacy and data protection laws such as the CCPA and GDPR. Data De-identification and Pseudonymity software allows companies to use realistic, but not personally identifiable datasets. This protects the anonymity of data subjects whose personal identifying data, such as names, dates of birth, and other identifiers, are in the dataset. Data De-identification and Pseudonymity solutions help companies derive value from datasets without compromising the privacy of the data subjects in a given dataset. Data masking is often used as a way companies maintain sensitive data, but prevent misuse of data by employees or insider threats.
Key Market Trends: Increasing Demand from various Enterprise
Growing Demand from Government Sector
Opportunities: Technological Advancement associated with Data De-identification or Pseudonymity Software
Rising Demand from the various Developing Countries
Market Growth Drivers: Increasing Adoption from Smart City Projects
High Adoption due to increasing security Threats
The Global Data De-identification or Pseudonymity Software Market segments and Market Data Break Down by Application (Individual, Enterprise (SME's, Large Enterprise), Others), Deployment Mode (Cloud, On Premise), Technology (Encryption, Tokenisation, Anonymization, Pseudonymisation), Price (Subscription-Based (Annual, Monthly), One Time License), End User (BFSI, IT and telecom, Government and defense, Healthcare, Other)
Presented By
AMA Research & Media LLP
0 notes
Text
Best XBRL Software in India for XBRL Filing Developed by IND-AS Taxonomy Developer
Introduction
XBRL (eXtensible Business Reporting Language) has revolutionized the way companies prepare and file financial reports. In India, where XBRL filing is mandatory for certain organizations, having the right software can make a significant difference in streamlining the process and ensuring compliance. In this article, we will explore the best XBRL software in India for XBRL filing, specifically developed by IND-AS Taxonomy Developer.
What is XBRL?
XBRL is a standardized language for communicating financial and business data electronically. It enables companies to present their financial statements and reports in a structured format, making it easier for regulators, investors, and other stakeholders to analyze and compare the data.
Importance of XBRL
XBRL offers several advantages over traditional reporting methods. It enhances data accuracy, facilitates data analysis and comparison, improves data accessibility, and reduces the time and cost associated with manual data entry and processing. XBRL also promotes transparency and standardization in financial reporting, making it an essential tool for regulatory compliance.
XBRL Filing in India
In India, the Ministry of Corporate Affairs (MCA) mandates certain companies to file their financial statements in XBRL format. This requirement applies to companies falling under the specified thresholds based on their turnover, paid-up capital, or outstanding loans. Failure to comply with XBRL filing requirements can result in penalties and other legal consequences.
Challenges of XBRL
While XBRL offers numerous benefits, its implementation can pose challenges for organizations. Some common challenges include complex taxonomy mapping, data validation errors, software compatibility issues, and the need for continuous updates to accommodate changing regulations.
Benefits of XBRL
Despite the challenges, the benefits of XBRL outweigh the complexities involved. XBRL improves data accuracy, ensures consistency in reporting, facilitates data analysis and trend identification, simplifies regulatory compliance, and enhances decision-making by providing reliable and timely information.
Features of the Best XBRL Software
The best XBRL software offers a comprehensive set of features to simplify the XBRL filing process. Some key features to look for include:
1. Intuitive User Interface: The software should have a user-friendly interface that enables easy navigation and quick access to essential functions.
2. Taxonomy Mapping: It should provide a seamless taxonomy mapping process, allowing users to map their financial data accurately.
3. Data Validation: The software should include robust validation checks to identify errors and inconsistencies in the XBRL documents.
4. Automated Tagging: It should offer automated tagging capabilities to assign XBRL tags to the relevant financial data.
5. Version Control: Version control features to ensure proper management of XBRL filings, allowing users to track changes and maintain a clear audit trail.
6. Collaboration: The software should facilitate collaboration among multiple stakeholders involved in the XBRL filing process, ensuring smooth coordination and efficient workflow.
7. Data Security: Data security is crucial when handling sensitive financial information. The software should provide robust security measures to protect data from unauthorized access or breaches.
IND-AS Taxonomy
IND-AS Taxonomy is the XBRL taxonomy specifically designed for Indian Accounting Standards (IND-AS). It ensures that XBRL filings comply with the prescribed reporting requirements in India. IND-AS Taxonomy Developer is a leading provider of XBRL software and solutions in India.
Why Choose IND-AS Taxonomy Developer?
There are several reasons why IND-AS Taxonomy Developer stands out as the preferred choice for XBRL software in India:
1. Expertise in Indian Reporting Standards: IND-AS Taxonomy Developer specializes in XBRL solutions tailored to meet the unique reporting requirements of Indian companies.
2. Robust Software: Their XBRL software offers a comprehensive set of features, enabling seamless XBRL filings and ensuring compliance with regulatory standards.
3. Continuous Updates: IND-AS Taxonomy Developer stays updated with the latest regulatory changes and releases timely updates to their software, ensuring users can adapt to new reporting requirements effortlessly.
4. Customer Support: They provide excellent customer support, assisting users in addressing any queries or issues related to XBRL filings.
Key Features of the Best XBRL Software
When evaluating XBRL software options in India, consider the following key features:
1. Accuracy and Reliability: The software should ensure accurate mapping, tagging, and validation of financial data to minimize errors.
2. Ease of Use: Look for user-friendly software that simplifies the XBRL filing process, even for non-technical users.
3. Integration Capabilities: The software should integrate seamlessly with existing accounting systems, allowing easy data import and export.
4. Compliance with Regulatory Standards: Ensure the software adheres to the prescribed reporting standards and keeps up with regulatory changes.>
5. Data Security and Privacy: Choose software that prioritizes data security and provides robust measures to protect sensitive financial information.
Pricing and Plans
XBRL software providers offer various pricing models, including subscription-based plans and one-time license fees. It's essential to evaluate the pricing structure and choose a solution that aligns with your organization's requirements and budget.
Customer Reviews
Before making a final decision, it's helpful to explore customer reviews and testimonials of the XBRL software providers. Real user feedback can provide valuable insights into the software's performance, ease of use, customer support, and overall satisfaction.
Conclusion
In conclusion, selecting the best XBRL software in India is crucial for organizations required to file financial statements in XBRL format. IND-AS Taxonomy Developer, with its expertise in Indian reporting standards, robust software features, continuous updates, and excellent customer support, emerges as a top choice. However, it's essential to evaluate other providers as well to ensure the software aligns with your specific needs.
FAQs
1. Q: What is XBRL filing?
A: XBRL filing refers to the process of submitting financial statements and reports in the XBRL format, which enables standardized and structured data communication.
2. Q: Who needs to file XBRL in India?
A: Certain companies in India, based on turnover, paid-up capital, or outstanding loans, are required to file their financial statements in XBRL format as per the regulations of the Ministry of Corporate Affairs.
3. Q: How does XBRL software help with compliance?
A: XBRL software simplifies the mapping, tagging, and validation of financial data, ensuring compliance with regulatory standards and reducing the chances of errors.
4. Q: Can XBRL software integrate with existing accounting systems?
A: Yes, many XBRL software solutions offer integration capabilities, allowing seamless data import and export between the software and existing accounting systems.
5. Q: Is data security a concern when using XBRL software?
A: Yes, data security is a crucial aspect of XBRL software. Reputable providers prioritize data security and implement measures to protect sensitive financial information.
1 note
·
View note