#header spf
Text
DKIM, SPF And DMARC Alignment: Steps For Perfect Results
Aligning DKIM, SPF and DMARC is essential for organizations to ensure their email content is trustworthy, secure and properly authenticated. Proper alignment ensures that inbound messages are correctly authenticated and that outbound messages have a higher chance of reaching their destination inbox.
Aligning these three technologies is a complex process, but it is possible to perfect it if you have the right steps in place.
DKIM uses cryptographic signatures to verify that an email has not been tampered with and that it comes from the domain it claims to come from. SPF, on the other hand, uses a list of authorized senders for a domain to verify that an email is coming from a legitimate source.

If your DKIM and SPF records are not aligned, it could mean that your emails are not being properly authenticated and could be caught in spam filters or blocked entirely. Therefore, it is important to ensure that your DKIM and SPF records are correctly configured and aligned.
DKIM, SPF, and DMARC are three of the most commonly used authentication protocols for email security. When used together, these authentication protocols can help protect your emails from fraudsters and other malicious actors. For more comprehensive insight into DMARC alignment, please visit dmarcreport.com.
What Is Domain Alignment?
Identification alignment, also known as domain alignment, is a feature which ensures the domain name in a return email address matches that of the sending domain. It must be confirmed that your domain is available before you can execute identification alignment.
You should check for the availability of your domain name to make sure proof of domain alignment is possible.
Importance Of SPF And DKIM Alignment
DKIM and SPF provide access to different email filters. First, DKIM and SPF hinder or do not fully examine DKIM signatures. A fouled DKIM signature is primarily seen as a body hash not validating authenticates could be a result of an intermediate or receiving mail server changing something in the email.
The DKIM signature is not verifiable if it's been tampered with or changed. DKIM was created for messages that are no longer valid once they've been sent, and it was created as part of the cryptography field to demonstrate convincingly that a message has not been tampered with after it has been published.
If you do not have SPF but do have DKIM, you won't have the ability to rely on any alternate tactic if DKIM's signature is invalid. For that reason, be certain to have both SPF and DKIM alignment. Your message will be disqualified and might not get DKIM if it cannot succeed in SPF or DKIM.
If you set up SPF and DKIM alignment and have an incorrectly configured SPF alignment (or do not have SPF alignment at any all), this is almost as good as the alternative. Your emails will pass SPF and will be used for DMARC, with the exception of if your email forwards.

What Is DMARC Alignment
The sentence DMARC Identifier Alignment comes up often when people email with DMARC enabled, but what is its actual significance? It's the link between the return path domain and the FROM HEADER of an email. Since SPF and DKIM view the return path domain but not the image path domain (the FROM THE HEADER), DMARC addresses this with its alignment function.
DMARC alignment adds an additional layer of security, ensuring both domains can be reached at their SPF and DKIM return domains.
In closing, both SPF and DKIM are vital for email marketing. SPF stops spam bots from spoofing your domain, meaning that when a receiving server receives an email claiming to be from your domain, it will check your SPF records and make sure that the sending server is authorized. If your domain is misaligned with either of these, your emails will be flagged and potentially rejected.
2 notes
·
View notes
Text
DMARC Solution in India

Google And Yahoo Announce New Requirements For Bulk Email Senders
In a move to combat spam and improve email deliverability, Google and Yahoo have announced new requirements for bulk email senders. These requirements, which will take effect in February 2024, are designed to make it more difficult for spammers to send unwanted emails and to make it easier for recipients to unsubscribe from email lists.
Cast Your Eyes Upon The Three Pillars Of This Brave New World:
Authenticate Outgoing Emails
Requires set up these email authentication methods for your domain. Authenticated messages:
Help protect recipients from malicious messages, such as spoofing and phishing messages.
Help protect you and your organization from being impersonated.
Are less likely to be rejected or marked as spam by Gmail.
Set up email authentication for each of your sending domains at your domain provider. In addition to following the instructions we provide, you should also refer to your domain provider's email authentication instructions.
SPF
SPF prevents spammers from sending unauthorized messages that appear to be from your domain. Set up SPF by publishing an SPF record at your domain. The SPF record for your domain should reference all email senders for your domain. If third-party senders aren't included in your SPF record, messages from these senders are more likely to be marked as spam.
DKIM
Turn on DKIM for the domain that sends your email. Receiving servers use DKIM to verify that the domain owner actually sent the message.
DMARC
DMARC lets you tell receiving servers what to do with messages from your domain that don’t pass SPF or DKIM. Set up DMARC by publishing a DMARC record for your domain. To pass DMARC authentication, messages must be authenticated by SPF and/or DKIM. The authenticating domain must be the same domain that's in the message From: header.
Keep Spam Rates Low
Spam Rate Crackdown: Prepare for your spam score to be scrutinized under a microscope. Gmail's 0.1% threshold is your new Everest - keep your reported spam rate below it, and never, ever let it touch 0.3%. Exceed it, and your emails might as well be cast into the void.
Provide Easy Unsubscribing Option
The reign of hidden unsubscribe buttons is over! One-click emancipation for recipients is now the law. Make it prominent, make it easy, make them sing with joy as they escape your clutches (should they so desire). Remember, a frustrated unsubscribe attempt breeds nothing but spam complaints.
Get Help From A 3rd-Party DMARC Service (Recommended)
Reports can be difficult to read and interpret in raw format. We recommend using a third-party service that specializes in DMARC to receive, store, and analyze your reports:
Depending on your mail volume, it's possible to get many reports each day, up to hundreds.
Several factors determine the number of reports you get, including: how many servers you send to, how much mail you send, and the reporting options specified in your DMARC policy record.
Without a third-party service, you might need to create a dedicated Group or mailbox to receive and store the reports.
Third-party services can combine individual reports.
Jnr Management is Best DMARC Solution in India
#DMARC#dmarc solutions#DMARC solutions in India#DMARC solutions in Delhi#DMARC solutions in Mumbai#DMARC solutions in Bangalore
0 notes
Text
The Art of Deception: Exploring Email Spoofing Techniques in Cyber Attacks
In the digital age, email has become an integral part of our personal and professional lives. We rely on it for communication, information sharing, and more. However, with convenience comes vulnerability, and cybercriminals have found clever ways to exploit email systems for malicious purposes. Email spoofing is one such technique that has gained notoriety in the world of cyber attacks. In this article, we will delve into the art of deception through email spoofing techniques and the critical role digital investigation plays in countering these threats.
Understanding Email Spoofing
Email spoofing is a fraudulent activity where attackers manipulate email headers to make messages appear as though they are sent from a legitimate source when, in fact, they are not. The goal is often to deceive recipients into taking actions they wouldn't otherwise, such as clicking on malicious links, downloading infected attachments, or disclosing sensitive information. Let's explore some common email spoofing techniques:
Forged Headers: Attackers modify the "From" field in an email header to display a trusted sender's address. This gives the impression that the email is from a reputable source.
Phishing: Phishing emails typically employ email spoofing to impersonate trusted organizations, like banks or social media platforms. Victims are lured into revealing personal information or login credentials.
CEO Fraud: Attackers pose as high-ranking executives within an organization to trick employees into making unauthorized financial transactions or divulging confidential data.
Domain Spoofing: Cybercriminals forge the sender's domain to mimic a legitimate one. This makes it challenging to discern the email's authenticity.
Reply-to Attacks: Attackers set the "Reply-to" address to a different email account, diverting responses to a malicious inbox while still displaying a legitimate "From" address.
The Role of Digital Investigation
Digital investigation is crucial in combating email spoofing and other cyber threats. It involves the systematic analysis of digital devices, networks, and data to uncover evidence of cybercrimes, identify perpetrators, and prevent future incidents. When it comes to email spoofing, digital investigation serves several essential functions:
Incident Response: When an organization suspects it has fallen victim to email spoofing, digital investigation teams spring into action. They collect and analyze email headers, server logs, and other digital artifacts to confirm the attack's origin and scope.
Attribution: Digital investigators work diligently to trace the source of spoofed emails. This may involve tracking down the attacker's IP address, examining email routing paths, and uncovering the methods used to obfuscate their identity.
Evidence Collection: Investigators gather evidence that can be used in legal proceedings against cybercriminals. This includes preserving email logs, server records, and any other data that can establish the attacker's activities.
Forensic Analysis: Through forensic analysis, investigators can reconstruct the sequence of events leading up to an email spoofing incident. This process helps in understanding how the attack was executed and how to prevent future occurrences.
Countermeasures Against Email Spoofing
To defend against email spoofing, organizations should employ a multi-faceted approach:
Email Authentication Protocols: Implement email authentication protocols like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance). These protocols verify the legitimacy of incoming emails and help prevent spoofing.
Employee Training: Educate employees about email security best practices, including how to recognize suspicious emails, avoid clicking on unverified links, and report potential email spoofing incidents promptly.
Email Filtering: Employ advanced email filtering solutions that can identify and block spoofed emails before they reach employees' inboxes.
Regular Updates: Keep email systems, security software, and operating systems up-to-date to patch vulnerabilities that cybercriminals could exploit.
Digital Investigation Teams: Establish or partner with digital investigation teams that are well-equipped to respond to email spoofing incidents swiftly and effectively.
Conclusion
Email spoofing is a sophisticated form of cyber deception that can have serious consequences for individuals and organizations alike. Cybercriminals are constantly evolving their techniques, making it crucial for us to stay vigilant and invest in robust digital investigation capabilities. By implementing email authentication protocols, educating employees, and fostering a proactive approach to email security, we can mitigate the risks associated with email spoofing. In the ever-evolving landscape of cyber threats, the art of deception can be countered effectively through digital investigation, ultimately safeguarding our digital world.
So here IBRANDtech is the best digital forensics services providing agency that offers forensic chargesheet preparation, Forensic Cyber Audit, forensic cyber trail, Forensic Data Recovery and Cloning, Link detection and tracking, Spoofing email trail and Server trial, Suspect detailed profiling, Suspect Tracking and Location Detection services in all over the India. Our dedicated team of experts is committed to delivering the finest cybersecurity services tailored to your needs. We take pride in the opportunity to assist you in achieving top-notch cybersecurity solutions.
0 notes
Text
“Common Website Security Threats and How to Protect Your Business”
In today's digital age, websites have become an integral part of conducting business. They are used to attract customers, showcase products or services, and facilitate transactions. However, since people rely more on websites, there is an increase in website security concerns, which can jeopardize critical data, disrupt operations, and harm a company's brand. In this blog, we will look at some typical website security issues and offer practical solutions to secure your company. Remember that protecting your website is critical for preserving client trust and guaranteeing the success of your online presence.
1. Malware Infections:
Malware is malicious software designed to infiltrate and harm computer systems. Viruses, ransomware, and spyware are examples of common categories. Follow these procedures to safeguard your website against malware infections:
Maintain the software and plugins on your website.
Install a trustworthy security plugin or firewall to scan for and prevent harmful activity.
Using online security tools, monitor your website for vulnerabilities and malware on a regular basis.
Educate your employees on the need for safe browsing habits and the perils of downloading unfamiliar files.
2. DDoS Attacks:
Distributed Denial of Service (DDoS) attacks aim to overwhelm a website's server by flooding it with traffic, making the website inaccessible to legitimate users.
Use the following procedures to protect your company from DDoS attacks:
Use a web hosting service that includes DDoS protection.
Use rate-limiting methods to detect and prevent excessive traffic.
To disperse traffic and mitigate assaults, consider employing a Content Delivery Network (CDN).
3. SQL Injection:
SQL Injection: SQL injection is a web security flaw that allows attackers to manipulate the database of a website by injecting malicious SQL queries. To avoid SQL injection attacks, use these steps:
Use parameterized queries or prepared statements in your code to sanitize user input.
Update and patch your database management system on a regular basis.
Use a web application firewall (WAF) to detect and prevent SQL injection attempts.
4. Cross-Site Scripting (XSS) :
XSS attacks occur when malicious scripts are injected into web pages that users view, allowing attackers to steal sensitive information or take control of the website. Protect your company from XSS attacks:
Implement input validation and output encoding to prevent malicious scripts from running.
Control which scripts can run on your website by using security headers such as Content Security Policy (CSP).
Review and sanitize user-generated content, such as comments and form inputs, on a regular basis.
5. Phishing Attacks:
Phishing attacks entail deceiving people into disclosing sensitive information, such as passwords or credit card information, by impersonating a trustworthy institution. Protect your company and consumers from phishing attacks:
Teach your staff how to identify and report phishing attempts.
To prevent email spoofing, use email authentication methods such as SPF, DKIM, and DMARC.
To increase client trust, display visible security indications such as SSL certificates and trust seals on your website.
When it comes to website security, proactive measures are essential. Protect your business from these common threats and ensure the safety of your online presence. Partner with Shariwaa, a leading web security provider, to safeguard your website from cyber threats. Contact us today to learn more about our comprehensive security solutions.
#shariwaa#websitesecurity#malwareinfections#securityplugins#DDoS Attacks#webhosting#sqlinjection#cross-site scripting#securitypolicy#phishingattacks
1 note
·
View note
Text
Understanding DKIM, SPF, and DMARC: Protecting Your Email from Cyber Threats

Email has become a vital communication tool, with millions of emails being sent and received every day. However, with this increased usage comes an increase in email-based threats, such as spam, phishing, and spoofing. To protect against these threats, email authentication protocols such as DKIM, SPF, and DMARC have been developed.
What is DKIM?
DomainKeys Identified Mail (DKIM) is an email authentication protocol that verifies the authenticity of an email message. DKIM works by adding a digital signature to the header of an email message that can be verified by the recipient's email server. This signature is created using a private key that is held by the sender's email server.
When an email message is received, the recipient's email server can verify the signature by retrieving the public key from the sender's DNS records. If the signature is verified, it means that the email message was not tampered with during transmission and that it did indeed originate from the domain specified in the "From" field.
What is SPF?
Sender Policy Framework (SPF) is another email authentication protocol that is used to prevent email spoofing. SPF works by allowing domain owners to specify which IP addresses are authorized to send email messages from their domain. When an email message is received, the recipient's email server can check the SPF record in the sender's DNS records to see if the IP address matches the list of authorized senders. If the IP address is not authorized, the email message can be rejected or marked as spam.
What is DMARC?
Domain-based Message Authentication, Reporting and Conformance (DMARC) is an email authentication protocol that combines the functionality of DKIM and SPF. DMARC provides a way for domain owners to specify how email messages that fail authentication checks should be handled. DMARC also provides detailed reporting on email authentication results, which can help domain owners identify and stop email-based threats.
Potential vulnerabilities if not configured or not configured properly:
If these email authentication protocols are not configured or not configured properly, email-based threats such as spam, phishing, and spoofing can bypass security measures and make it to the recipient's inbox. This can result in compromised email accounts, stolen personal information, and financial loss.
For example, if DKIM is not configured, an attacker can modify the content of an email message in transit, and the recipient's email server will not be able to detect the modification. If SPF is not configured or not configured properly, an attacker can send email messages that appear to be from a trusted domain, which can result in the recipient being tricked into revealing sensitive information.
How to mitigate these vulnerabilities:
To mitigate these vulnerabilities, it is important to properly configure and maintain DKIM, SPF, and DMARC protocols. This can be done by following these best practices:
Configure DKIM, SPF, and DMARC protocols for all email domains.
Use a separate DKIM key for each email domain and rotate keys regularly.
Specify all authorized IP addresses in SPF records.
Use a DMARC policy to specify how to handle email messages that fail authentication checks.
Monitor email authentication reports regularly to identify and stop email-based threats.
In conclusion, DKIM, SPF, and DMARC protocols are important email authentication measures that can help protect against email-based threats. It is important to properly configure and maintain these protocols to prevent potential vulnerabilities and ensure the security of email communications.
0 notes
Text
skincare

In today’s world, everyone wants to look their best. And for that, it is essential to have healthy and beautiful skin. Skincare plays a crucial role in maintaining skin health and preventing premature aging. In this blog post, we will discuss the importance of skincare and provide readers with the necessary steps to achieve healthy and beautiful skin.
#Skin
#CareFeet care
The Importance of SkincareSkincare is not just about looking good. It’s about taking care of the body’s largest organ – the skin. Proper skincare helps to maintain the skin’s health, prevent premature aging, and protect against environmental factors such as pollution and sun damage.
Top Level Keywords
Skincare – the umbrella term for all things related to the care of the skin.
Cleansing – the process of removing dirt, oil, and impurities from the skin.
Exfoliating – the process of removing dead skin cells from the skin’s surface.
Moisturizing – the process of hydrating the skin.
Sun protection – the use of sunscreen to protect against UV rays.
Beauty – the goal of achieving healthy and beautiful skin.
Longtail Keywords
Best skincare routine for healthy skin.
How to protect skin from aging.
Importance of SPF in skincare.
Natural skincare remedies.
How to choose the right skincare products.
How to get clear skin.
Skincare for sensitive skin.
Header 1: Cleansing
Cleansing is the foundation of any good skincare routine. It helps to remove dirt, oil, and impurities from the skin, which can clog pores and cause breakouts. It is important to choose a cleanser that is appropriate for your skin type, whether it is oily, dry, or sensitive.
Steps to cleansing:
Wash your hands before cleansing.
Wet your face with lukewarm water.
Apply a small amount of cleanser to your fingertips and massage it onto your face in a circular motion.
Rinse your face with lukewarm water and pat dry with a clean towel.
Use a toner to remove any remaining impurities.
Header 2: Exfoliating
Exfoliating is the process of removing dead skin cells from the skin’s surface. This helps to reveal smoother and brighter skin, and also helps to prevent clogged pores and breakouts. It is important not to over-exfoliate, as this can damage the skin’s natural barrier.
1 note
·
View note
Text
Identity DMARC Alignment: Your Authority To Protect Your Fraudulent Email Accounts
In order to create and maintain a successful blog or website, it is important that the content you produce is aligned with your identity. Your identity is the image or persona that you project to your audience, and it should be reflected in the topics you write about, the language you use, and the overall tone of your blog.
When your identity is aligned with your content, it will be easier to connect with your audience and build a rapport. To learn more, visit here.

The Addresses Contained In An Email
There are different addresses in an email, some of which are readable by the average person, while others are meant for filtering by the present SPF and DKIM protocols. Both SPF and DKIM use their own unique set of addresses as a proof of validity for an email.
Since neither of them include the envelope-from address, SPF, and DKIM alone are unable to safeguard your domain from misuse. This is because the envelope-from address can be spoofed via spoofed domains and look-alike domains. The solution is DMARC, and more precisely, DMARC's function of guaranteeing e-mail communication identity or domain.
How Does Identity Alignment Work?
DMARC is the most obvious mail-handling protocol that works on the individual-readable address of an email. It works with SPF and DKIM to confirm all the cryptic header addresses that the DMARC policy controls. Afterwards, both SPF and DKIM take control over both individual protocols and deliver an authenticated domain. After that, matching the input from the SPF and DKIM outputs to the mail-from parameter begins.
Only when the two domains match does DMARC greenlight that email from one and a half to two times as securely, depending upon all the authentication choices. Domain names with SPF and DKIM are considered matching names. In DMARC, SPF and DKIM are considered matching domains.
Alignment Modes Of DMARC
There are strict and relaxed domain mappings. A strict mapping mode makes DMARC confirm an email only if there is a one-to-one correspondence between the domains and their corresponding flags. A relaxed linking mode maps domains in case the organizational domain is associated with the mail-from message address.
What Happens If Identities Aren’t Aligned?
If you have implemented DMARC, you're in good shape - DMARC will simply disregard any emails where the domains don't align. It won't force SPF or DKIM to overrule their 'verdicts' just because the human-readable mail-from address has been whitelisted before in the DMARC records. In this way, potential threats never reach you.
But if you haven't implemented DMARC yet, you may be in for some trouble. It's very difficult to make an email seem like it's coming from one address when its actual origin is some other address. Without DMARC in place, you're vulnerable to attack.
We highly recommend implementing DMARC as the trends show that soon, DMARC will be a mandatory email authentication tool.

In summary, employers can use identity alignment to improve employee engagement and retention. Employees are more likely to be engaged and stay at their jobs if they have a sense of identity alignment.
1 note
·
View note
Text
【更改ip地址】3分鐘一鍵轉換ip地址 電腦、手機輕鬆改!
徵信社 監聽
同樣,大多數其他ESP都會提供SPF記錄以包括在客戶記錄中。 與上一段類似,如果您使用任何第三方電子郵件服務,並且希望建立完全經SPF驗證的郵件流,則必須在您的郵件中包含他們自己的SPF記錄。 DMARC是所涵蓋的三項電子郵件驗證技術中最年輕的一個,並且是專門為解決SPF和DKIM的缺點而開發的。 與另外兩個不同,它驗證消息的Header From並連結到之前由另外兩個使用者執行的檢查。 每個SSL憑證類型的名稱代表著在頒發憑證之前進行的驗證步驟。 例如,網域名稱驗證憑證是指對URL擁有者的簡單驗證,而組織驗證憑證則驗證網域名稱擁有者並對與此URL相關聯的商業組織進行身分驗證。
我們按照之前的討論,先看看 Harmony 是如何從下到上解決網路分片、交易分片和狀態分片的問題。 而另一種方案版本涉及到在方案一的基礎上,為每個分片添加額外的功能,使每一個分片更像今天的以太坊主網,允許分片儲存和執行代碼並處理交易,因為每個分片都將包含其獨特的智能合約和帳戶餘額集,跨分片通信將允許分片之間的交易。 seo 然而這種方案還在社區辯論中,因為方案一的數據可用性加上 Layer2 的協同,已經可以為以太坊提供足夠的可拓展性,因此社區還在評估版本二的經濟成本與收益價值。 應該指出的是,隨著更有效的擴展路徑的開發,以太坊的分片計劃也在不斷發展。 狀態分片是分片最大的難題,比上述的網路分片和交易分片更棘手。
隨著網際網路的發展變化和線上身分標準的日益妥協,DigiCert在 Certification Authority Browser(CA/B)Forum中發揮積極作用,宣導提高線上身分保障。 因為真實的線上身分在數位世界中應該和它在現實世界中一樣重要。 在當今的數位連線世界中,對線上身分的侵蝕將對我們渴望維護的公眾信任造成不利影響。 在Mac上打開iTunes,然後點擊“iTunes”菜單按鈕。 系統會自動查找在線提供的最新版iTunes,並在新窗口中顯示。 點擊“下載iTunes”按鈕,然後按照屏幕上的步驟使用最新版本更新iTunes。 但是,由於Mac的一些主要問題,當您同步iPhone時,您可能會認為iTunes意外退出。
雖然 Shardeum 仍在開發中,但在協議層面使用的 Shardus 技術已被證明可以實現線性擴展。 在 2021 年第第三季的更新活動中,shardus 運行在 AWS t3.medium 硬體上的 one thousand 個節點的網路被證明可以達到 5000 TPS 的跨分片交易。 聽起來更美好,但是由於某些分片的靜態特性,許多額外的節點需要加入網路才能創建新的分片。
相反,網路的每個參與者只維護與他們驗證交易的分片相對應的狀態,並且塊(Block)中所有交易的列表被分成物理塊(Chunk),每個分片一個塊。 交易分片:Harmony 的交易由單個分片處理和處理。 這使得分片能夠同時處理交易,提高了區塊鏈的總交易容量。 對於交易,用戶只需在簽名交易中指定 shard_id 字段,表示交易所屬的分片。
最簡單的原因,其實就是最便於取得國外的IP地址囉! 由以上關於電腦及手機裝置更改IP地址的方式來看,過程繁複以外,且並無法將你人在台灣上網的事實改變,進而無法存取跨境的資訊及服務來達到娛樂目的,更無法因此擺脫避免被監控審視等問題。 然而,要取得VPN其實非常簡單,只要在網路上搜尋「VPN公司」即可獲得不少資訊。
但在這篇文獻中,EAP-MD5 已經被Mishra 及 Arbaugh兩位教授證明指出它仍只是單向認證的協定,會遭受到Man-in-the-Middle及Session-Hijack攻擊,所以本校不會採用這種認證方式。 弘裕製造的布,一年產量足以繞地球8、9圈,不僅坐擁『台灣NYLON KING』的地位,還躍居大中華地區紡織標竿企業,躋身國際紡織大廠。 多年來,在全體同仁的努力下致力於提供全球最具競爭力的『全方位成本優勢』布料給全球知名品牌廠商。 台灣比菲多食品:佈局食品飲料產業,站穩市場腳步,萌芽於1998年,比菲多公司從生產大包裝果汁起家。 隨著消費者及市場變化,接續推出了成人版活菌發酵乳、好朋友系列調味乳、純萃喝咖啡等產品。 秉持創新的永續經營之道,20多年來,比菲多公司持續耕耘食品飲料市場,如今業務範圍跨足食品、化工、餐飲、宅配、物流、農場等領域,深入台灣民眾的日常生活。
1 note
·
View note
Text
電子郵件驗證最佳作法 部署 Spf、dkim 和dmarc 的絕佳方法
徵信社 感情破壞
可靠– YOKOGAWA多年來致力於測量品質,DLM5000具有低殘餘噪聲、多電壓量程和各種實時低通濾波器,能夠確保信號的真實度。 歷史記錄內存允許用戶保存和分析捕獲的全部觸發波形,確保不會丟失任何數據。
考慮到這一點,通常建議客戶將他們的預設組設定為包含其所需的ID同步設定的組,以便電腦在令牌出現問題時正確進行重新同步。 持續VDI(也通常稱為「有狀態VDI」)是一種設定,其中每個使用者的案頭可唯一自定義,並在一個會話到另一個會話「持續」。 此類虛擬部署不需要身份永續性的功能,因為這些電腦不會定期重新映像。 DKIM相對不具侵入性,因為未簽名的消息不會遭到任何拒絕。 聯絡您可能委託簽署的任何第三方,確保您的第三方支援DKIM簽署,並考慮您的選擇器管理策略。 有些組織會為不同的組織單位保留不同的鍵(選擇器)。
目前區塊鏈網路中存在兩類記賬方式,分別為 UTXO(Unspent Transaction Outputs,未使用交易輸出)模型和帳戶 / 餘額模型,前者的典型代表是 BTC,後者如 ETH。 交易分片是指關於「哪些交易要被分配到哪些分片」的規則制定,則既能夠達到並行處理的目的又能避免雙花問題的出現。 區塊鏈的帳本模型的不同會對交易分片的開發造成影響。 我們使用網站Cookie功能,透過紀錄您的偏好與瀏覽方式來為您提供最完美的網站體驗。 筆者認為,優化農夫市集營運最重要的事情,是從調查中,農民認為最不在意的人力因素。 也就是說,改善農夫市集營運的首要目標,需要至少一名專職的工作人員。
從區塊鏈1.0到3.0的定義中,或許感覺這是一種「漸進式」、「遞進式」的發展,但其實只是應用範圍的不同。 事實上,不管是1.0的加密貨幣、2.0的金融領域到3.0的各種領域,區塊鏈技術都在平行地在發展著,可以想見未來各種區塊鏈應用會越來越多、越來越完善。 區塊鏈自然在金融領域的應用上顯得最即時、最進步,讓我們將傳統銀行服務,與比特鏈區塊鏈實行情況作比較。 對於公司內的節點這條區塊鏈是去中心化的,但對於鏈外的節點則會覺得這是中心化的區塊鏈,這取決於它設計時驗證與維護是否來自足夠多的節點。 而激勵層、合約層和應用層則不是每個區塊鏈都須具備的,像是激勵層則多存在於公有區塊鏈中,因為需要藉著完善的獎勵機制,才能促進區塊鏈中的節點持續投入資源(持續記帳)在其中。 而首先記帳的節點,接著會把這個區塊傳遞給其他節點,在核實區塊內容無誤後才會放進自己的帳本,直到所有區塊鏈上的節點都有一致的交易資訊。
換一個角度切入也可以想成是,科技業漸漸佈局到以往傳統的金融業,試圖帶來一波新的衝擊性改變。 此行為利用了以下事實:最初DKIM根本沒有按照MAIL FROM或Header seo From所述驗證郵件源。 它僅驗證簽名域ID(「DKIM簽名」的「d」引數以及簽名配置檔案中的「域名」引數)是否的確承載用於對消息進行簽名的對的公鑰。
如果您立即需要憑證,這算是一種便捷的驗證方法,但這種只進行一項檢查的驗證形式是網際網路中最低標準的驗證形式,其相應的信任度也應該是最低的。 1張證書可同時包含多個驗證點,然而申請組織須建立一個單一的安全管理系統,以提供信心和保證管理系統中包括所有站點都共用且符合適用標準的要求。 如果你選用店內取貨服務,你可指定第三方代領人前往取貨。 請注意,某些特定產品與付款方式不適用第三方代領人前往店內取貨。 第三方代領人須攜帶由政府核發且附照片的身分證件與訂單編號方可取貨。 一旦你的商品完成取貨,Apple 對於第三方代領人的任何行為恕不負責。 對於任何通過電話或網路確認的訂單,Apple Store 得要求用戶提供信用卡安全密碼。
當學生下載Blockcerts Wallet之後,它會產生一組金鑰(私鑰加上公鑰),並將公鑰傳送給MIT,把它寫入數位紀錄中,再於該區塊鏈加上認證碼。 區塊鏈上並沒有記錄文憑資訊,有的只是MIT建立該紀錄的時戳,最後MIT再寄出含有公鑰的數位文憑,藉由學生手機上的私鑰來進行本人驗證。 未來也將整合能源管理、溫度空調控制,邊緣裝置掌握更多的資訊,來強化整合性與即時性的控制。 按跨策略的主機名:新的或刷新的安裝會查詢具有相同主機名的最新聯結器記錄,以便將以前的歷史資料與新註冊同步。 如果聯結器以前未安裝在此策略中,但以前在其他策略中處於活動狀態,則可以建立重複項。
有些接收者僅標籤失敗消息,或者不執行可見操作,但會向管理員報告。 在思科郵件安全裝置或雲郵件安全虛擬裝置上配置SPF驗證非常簡單。 在本檔案的其餘部分,任何對ESA的提及也將包括CES。 SPF和DKIM識別符號單獨對齊,並且需要傳遞其中的任何一個消息才能整體傳遞DMARC。 但是,有一個DMARC策略選項,傳送方可以請求生成失敗報告,即使一個對齊通過,但另一個失敗。
熟悉SPF、DKIM和DMARC的基礎知識是一個優點。 組織驗證(OV)憑證透過九項驗證檢查以進行身分驗證,並被視為中級業務憑證。 對於OV憑證,CA對網域名稱擁有權的驗證類似於DV憑證。 網域名稱驗證(DV)憑證是身分驗證程度最低的SSL憑證,即使是惡意bot也可以快速輕鬆地獲取這類憑證。 這些憑證是低成本憑證,只需要驗證公司或個人能證明他們對想要為其申請憑證的Web網域名稱的控制。 當你想要連接或同步你的iPhone時,你的Mac High Sierra體驗意外退出。
1 note
·
View note
Text
How To Create And Add An SPF Record For Email Authentication
Email authentication is a process of verifying that an email message comes from the sender that it claims to come from. This helps to prevent email spoofing, which is when someone sends an email with a fake sender address in an attempt to trick the recipient into thinking the email is from a trusted source. Please visit the duocircle.com if you'd like to learn more about how to create spf record
What Is SPF And How Does It Work?
SPF, a recommended authentication solution, incorporates three different algorithms that help you avoid email spoofing, spam, and phishing.
Identify the hostname, domain, or IP address for the server authorized to send mail to a given domain, using SPF records.
authenticate digitally signed messages, using public keys stored in DomainKeys Identified Mail (DKIM) records.
Informing email servers how to verify messages from a domain to protect it against email spoofing when using Domain-Based Message Authentication, Reporting and Conformance (DMARC).

Most of these email authentication protocols all use DNS records to store information about email services provided by the domain holder.
DKIM records include a public key used to sign email digitally.
DMARC records contain guidance email-receiving agencies should follow in case they receive an email that's not authenticated.
SPF records provide information on how to identify authorized domains and subdomains to send email on behalf of the given domain in the email header.
SPF and its sibling protocols are produced through the utilization of DNS to distribute the info email receiver requires to ascertain whether an email has actually been sent by the sender without the effect on deliverability.
SPF works by the email-sending agency using DNS TXT records to create rules for authenticating email sent by means of the domain name owners. Knowing how to create a DNS TXT record is a large part of the process of creating any SPF, DKIM or DMARC record.
Organizations that send e-mail for their own domain benefit from creating DNS references that can validate email.
The process for creating DNS records varies based on whether emails are sent by an email service provider, web hosting services, the internet hosting company or other third-party mail server that sends mail on behalf of a specific domain.
The process for creating the new SPF record also may be complicated depending on the email infrastructure of the domain owner.
SPF TXT records contain mail server information for a domain, an IP address, or a domain within a subdomain that can be contacted about mail for the associated domain.
Email-receiving servers check the SPF record to determine whether the email originated from an authorized IP address, domain, or subdomain and use them to decide to forward it.
SPF Record Syntax
SPF syntax defines three factors in the SPF records mechanism, qualifiers, and modifiers.
SPF has one or more specific ways in which it can determine whether a domain is allowed to send messages. A mechanism is said to be a match if some specified condition is met. Depending on the mechanism, a match resulting from a particular condition means the message would be validated.
Qualifiers can be configured to optionally be appended to executable mechanisms to specify how a receiving email server should react to listed mechanisms.
A modifier is an additional informational record that's an adjunct to a security-level registry (SPF) record but does not modify its authenticity.
How To Add An SPF Record
Once created, SPF records must be pushed out as a DNS TXT record.opacity must not be taken lightly -- publishing a DNS record affects how the domain name is used throughout the globe.
DNS TXT records can be added using the DNS service provider's website or application. Normally, the process is accomplished by choosing the Add Record option from a drop-down menu and typing in the record details.

Microsoft is thought to be the ideal option among domain administration vendors when it comes to creating DNS TXT records.
An IT and networking professional may use the service to add such records to the company's DNS servers, but the changes still need to be propagated beyond the internet by the internet's domain zone provider.
In summary, SPF and DKIM use helps to protect the sending of email from spoofing or alteration. Absolute minimum SPF is three and involves the use of domains, subdomains and IP addresses. SPF records essentially indicate which servers and IPs are allowed to send emails on behalf of your domain. SPF policy will allow any servers with the SPF record to send mail.
1 note
·
View note
Text
World Best Online Movie Website
You can receive a message sent by following the Failed to remember Secret key connection on the login page. To keep your old secret key, don't follow the connection in the message. This framework is additionally utilized. You can involve both SPF and DKIM in a similar message. Once more, similarly likewise with, you can check if your getting confirmed your host's area key by looking at the mail header ดูหนังออนไลน์

There is a fair opportunity no mark key was given, showing your host decided to not utilize this convention. Likewise similarly as with SPF, on the off chance that you can alter your DNS records and the mail server has a place with your space, you can set up DKIM qualifications yourself. Some how-tos exist on the off chance that you search the Web.
As a feature of the programmed overhaul wordpress places a document named .upkeep in the blog base envelope organizer that contains the administrator envelope. In the event that that document exists, will see the message momentarily inaccessible for planned upkeep. Return in a moment.
At the point when an update is delivered, notice of that delivery is shown at the top organization screens saying accessible! If it's not too much trouble, update now. Few out of every odd blog will see that message simultaneously. Your blog is modified to check for refreshes at regular intervals, however the planning of that check is absolutely arbitrary.

So in the event that your blog only checked for refreshes minutes before an update was delivered, you won't see the update message until your blog checks for refreshes after the fact. Assuming you believe your blog should check right now for refreshes, you can erase the update core choice name record in your options table. Note that modules and subjects each have their own check and update cycle.
WordPress utilizes the standard PHP mail capability, which utilizes sendmail. No record data is required. This isn't for the most part an issue in the event that you are utilizing a facilitating administration, however assuming that you are utilizing your own crate and don't have a SMTP server, the mail won't ever send.
This is the most widely recognized enemy of spam measure utilized. In the event that you are on a facilitated framework, there is a decent opportunity your host has set this up for the mail server you are utilizing. Have WordPress email you and check the message headers for proof that the message passed the SPF check.
1 note
·
View note
Text
wordpress – Amazon SES IP Fails SPF Check in DMARC
SPF is always considered of From Domain.
Header From and From Domain are 2 different things.
Header From is the part after @ in email address. In your case its ofpad.com.
But what happens is that it checks SPF from From Domain. In this case it is us-west-2
And In DMARC it also checks the mail is being sent should have same domains in Header From and From Domain. Which is different in this case.
That is the main reason of its being failed. It is known as SPF Alignment in DMARC.
0 notes
Text
Radiant defense guide

#RADIANT DEFENSE GUIDE HOW TO#
#RADIANT DEFENSE GUIDE SKIN#
#RADIANT DEFENSE GUIDE ANDROID#
Please contact with any inquiry or feedback. "Radiant Defense is an engrossing strategy game with lovely spacey visuals and just enough quirky touches to set it apart from the crowd. Get this game and start fending off the brilliantly bright waves of invaders that come your way." With an SPF of 30, it also touts pretty decent protection against UVA/UVB rays. The lightweight, oil-free formulation provides three forms of defense: environmental, barrier and photo defense.
#RADIANT DEFENSE GUIDE SKIN#
"Radiant Defense is still a tower defense game, but it's a really good one. Radiant Defense is a new skin tint that protects your skin against the sun and other stressors while improving your complexion over time. size S M L position L C R U D change title 1 title 2 caption delete. size S M L position L C R U D change Credit Delete. Paragraph Header 4 Header 3 Header 2 Quote Link Img Table. If you like this kind of game, you really should download it immediately." Think youre an expert in Radiant Defense Why not start up this guide to help duders just getting into this Game. "Radiant Defense is one of the best interpretations of the genre we’ve witnessed in an age. "It's refreshing to find a game that respects your intelligence, money, and time. Build your space fortress any way you wish, set up wide variety of weapons and traps and let the invasions begin IN-APP PURCHASES Radiant Defense is free to play without any ads, supported only by.
#RADIANT DEFENSE GUIDE ANDROID#
"Radiant Defense Is One Of The Best Tower Defense Games On Android Right Now" MILLIONS OF ALIENS WILL DIE Radiant Defense is a tower defense game set in a vibrant universe invaded by countless alien hordes. There are no consumable microtransactions! See more ideas about rodan and fields, radiant, oil free. Do you have Radiant Defense app problems We have instructions to fix the not working issue, loading problems or the common black screen / white screen. Each in-app purchase greatly enhances your tactical options. Dermacosmetics Made for all skin types so it's non-acnegenic, non-comedogenic and breathable. Radiant Defense is free to play without any ads, supported only by in-app purchases. Radiant Defense is a defense game set in a vibrant universe invaded by countless alien hordes.
#RADIANT DEFENSE GUIDE HOW TO#
Please note that a D-pad remote is not supported. Radiant Defense Strategy Guide Read more on how to build a strong economy and get the maximum out of your deadly arsenal. Use a game controller for the best experience when playing on TV. ★ Online hall of fame - your scores can only grow ★ 9 upgradable weapons to kill the aliens with style ★ More than 400 waves of aliens across 15 missions
★ Build your own route for incoming waves of enemies! MILLIONS OF ALIENS WILL DIE
Radiant Defense is a tower defense game set in a vibrant universe invaded by countless alien.
★ Tower Defense set in the Radiant Universe Radiant Defense is a tower defense game set in a vibrant universe invaded by countless alien hordes.īuild your space fortress any way you wish, set up wide variety of weapons and traps and let the invasions begin!

0 notes
Text
Yet another mail merge

#Yet another mail merge full
In that case, we won’t be able to record a read, unless the recipient explicitly ask Gmail to display all images from your email. In most email services, like Gmail, people can disable the display of images by default.If you go to your “Sent Mail” folder in Gmail and open the email you sent, it will be counted as read.If you have multiple recipients in the same row of your Sheet (or people added as cc or bcc), it creates only one email and you’ll be able to check if this email has been opened but not who (among the recipients) has opened it.You can then click on the menu “Check if emails have been opened” to check if our system have recorded opening of some of your emails. When the recipient opens the message, the tracking image is referenced and recorded by our system. YAMM embeds a tiny, invisible tracking image (a single-pixel gif, sometimes called a web beacon) within the content of each message. For each email opened, in the column “Merge status”, the status will change from “EMAIL_SENT” to “EMAIL_OPENED” and a note in the cell will tell you how many times the email was opened and when was the last time it was opened (note that we are keeping the receipts in our database for only 4 days). Once you have activated email tracking and sent emails, you’ll see a new entry in YAMM menu.Ĭlick on this menu to check if your emails have been opened. You can begin to write your template in your Sheet and copy / past it in Gmail, all formatting (colors, margins.) will be kept!Ĭopy/past in Gmail to create your template: as your mail templates are standard drafts in Gmail. But YAMM makes it especially easy to use an alias, add cc, bcc, attachments, inline images. There are multiple add-ons available to send emails upon form submissions. If it doesn’t exist yet, add a column named ‘Merge status’ in your Sheet and add a 0 for all rows that should be skipped. S imply add a new marker as subject of your draft / template. Simply add ‘cc’ as the header for a column in your spreadsheet and the cc recipients will be retrieved from this column (you can add several comma separated email addresses).Īnd you can do the same for Bcc recipients.
#Yet another mail merge full
That why, if you’ve used the tool yesterday, you might need to wait a few hours more to get your full quota today. The quota of emails you can send is refreshed at the end of a 24-hour window the exact time of this refresh, however, varies between users. If you are a Google Apps for Work, Education or Government customer and this 1 00 recipients / day limit is not enough for you, you can subscribe to one of our paid plans and get much more quota (those paid plans are not for users). You can send emails to 1 00 recipients every 24 hours. The app freezes without any error messageįrequently asked questions How many emails can I send each day? The add-on is not working as expected, what can I do about it? Issue with inline images (since 04/15/14) - Fixed The “Send from” field (alias picker) isn’t working How to add a clickable image / button with a specific link for each recipient?Īvoid being blacklisted by spam filters with SPF I want to add different links / URL for each recipient Is it possible to add a different attachment for each recipient ? How Bounce messages / Failure for Delivery status are handled ? Here’s a tip: start writing your email body in a Sheet I want to send emails only to some people listed in my Sheet (I want to filter rows) How to pull the subject line from a column in the spreadsheet? How to pull the cc or bcc recipients from a column in the spreadsheet? Ī video tutorial is availabl e here: Short link to this documentation: YAMM is a mail merge for Gmail / Google Apps first featured on the Google Apps Developer blog.

0 notes
Text
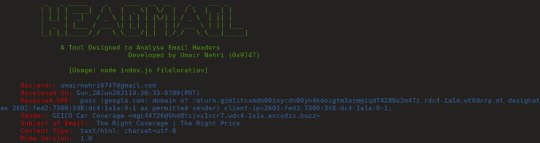
[Media] HeadMail
HeadMail
HeadMail is an cross-platform tool developed using Nodejs which can help investigators and researchers to analyse email headers to filter out relevant data which can be considered useful during digital investigations.
Filtered:
▫️ Delivered-To
▫️ From
▫️ Date & Time
▫️ Subject
▫️ Received-SPF
▫️ Content-Type
▫️ Message-ID
▫️ Mime-Version
▫️ X-Mailer
https://github.com/umair9747/headmail
t.me/hackgit
0 notes