#Blocks Unauthorized Scans
Text
Peace of Mind in a Pocket: My Experience with the RFID Protector
In today's digital world, protecting our personal information is paramount. With the growing prevalence of contactless payment methods, the risk of electronic pickpocketing, also known as RFID skimming, becomes a concern. That's why I decided to invest in the RFID Protector, a product designed to safeguard my contactless cards.

Discreet Protection for Everyday Transactions
The RFID Protector is a slim and lightweight sleeve that easily fits into my wallet alongside my cards. It comes in various sizes to accommodate different card types, ensuring a comfortable and discreet addition to my everyday carry. The best part is that it doesn't interfere with the functionality of my contactless cards; I can still tap and pay with ease, knowing my information is shielded.
Blocking Unwanted Scans and Ensuring Security
The core function of the RFID Protector is to block unauthorized scans. The product utilizes a special material that creates a barrier, preventing radio waves from scanners from reaching the chip embedded in my contactless cards. This effectively shields my personal and financial information from potential thieves. While I haven't personally experienced any skimming attempts, the peace of mind this product offers is invaluable.
Multiple Layers of Protection for Added Security
Some RFID Protectors simply block radio waves, but the one I use boasts additional security features. It includes a layer that physically protects the card itself from bending or breaking, a common concern with contactless cards. Additionally, some versions offer a water-resistant layer for added protection against accidental spills or splashes. These additional features make the RFID Protector a well-rounded solution for safeguarding my cards.
A Convenient and Affordable Security Solution
The RFID Protector is a convenient and affordable way to enhance the security of my contactless cards. It's easy to use, integrates seamlessly with my existing wallet setup, and offers peace of mind without breaking the bank. For anyone who uses contactless payment methods, the RFID Protector is a worthwhile investment.
A Recommended Addition to Your Wallet
Overall, the RFID Protector has become an essential part of my wallet. It offers a discreet and effective solution for safeguarding my contactless cards, providing peace of mind during everyday transactions. While remaining vigilant is always important, the RFID Protector adds an extra layer of security in today's digital age. If you're looking for a convenient and affordable way to protect your contactless cards, I highly recommend the RFID Protector.
#RFID Blocking Sleeve#pen_spark#Contactless Card Protector#Anti-Skimming Wallet Insert#Digital Security Tool#Blocks Unauthorized Scans#Protects Against Electronic Pickpocketing#Safeguards Personal Information#Enhanced Contactless Payment Security#Discreet and Lightweight Design#Multiple Sizes for Different Cards#Water-Resistant Option#Affordable Security Solution#Easy to Use and Integrate with Wallet
0 notes
Note
I'm dumb as hell, so can you explain me why JPtwt is so pressed about Manga leaks?
I mean, I have heard that those who leak spoilers earn some money out of it, so does this money come out of the Mangaka's pocket? If yes, then I'm against it. If not, then what's the big deal? I think there are many bigger issues than this to focus on.
Further, spoilers come weekly, I guess? That too, in Japanese language, so it's the same amount of time as the official release of a chapter—you getting me?
Hi there! Sorry the response is so long.
Basically, JPtwt considers leaks ("hayabare") as a crime (it is), engaging with them is something they find extremely distasteful. Not sure why the reaction is so strong, but it is. Maybe it's being protective over manga bcs it's a big industry nationally. However me being Korean, a LOT of people pirate manhwa... so... (though manhwa is generally not as big so the gripe is spoilers & not leaks.)
It's upsetting in my opinion specifically because of the fact that the spoilers themselves only come out like 2 days earlier, but, this time it came out on a Friday when they were originally on Mondays (officials come out on Wednesday. But a long time ago, I heard these came out on Fridays and in Korean? Lol. I wasn't there.) Most of the people who were targeted including myself are artists. This is the source of my gripe with this callout/block list, because we never reposted the official copyrighted material in the first place, so bombarding us with blocks and possibly getting our accounts locked when there are people who rely on commissions and a platform to gain said commissions/communicate with commissioners, for instance, is a bit... odd? They could mute us instead... Yes, there are also plenty of people posting the official panels as well, and I get their frustration. But a Japanese twitter user put it well, saying something along the lines of "these users were all also forced to see leaks just like you, except they're not being [immature] about it". In my opinion if I could disengage with leaks regarding manga I would, since this was my policy up until me getting super excited about Kaiser's backstory specifically. I previously did not post about leaks on twitter. The issue is the people posting the original leaks, but they didn't even put them front and center, which I just found confusing.
I think technically since English has (online?) simurelease with Japan, it can affect sales. By how much, I'm not sure, because Twitter isn't a real good gauge of just HOW many people see the leaks (a user called Rayuga is the main one as far as I know, and their main has like 90k+ followers, so I'd imagine their reach is still above that follow count... but it also can be less, because twitter is twitter.) I apologize if this is already common knowledge because before joining twitter, I mainly got my leaks from Reddit without considering the source. Scanlations (A group called PO2? is currently scanlating Blue Lock) also probably has the same effect, which when I was in Scans, in my group we had a hard rule that an English official copy being released would warrant us to drop a series so that the author would receive fair support. So not doing that when there is an english copy, is probably damaging.
I never checked if PO2 takes donations or have a Patreon or anything like that, which from my time in scans is GENERALLY looked down upon internally within the community. If they do, this is something that I wouldn't really condone openly, specifically because it's still unauthorized redistribution. Attempting to profit off of that usually is because sometimes scan groups will pay their staff. Me, personally, I always worked for free. But if they don't, then I have nothing to say.
I don't think people who would have not bought the chapter even if that was their only option would've ever contributed to sales in the first place, right? So it depends. In conclusion, I'm sure there are losses. But it's hard to gauge by how much, so I simply listed all the possible factors for you to judge by yourself.
10 notes
·
View notes
Text
A Ghost From the Past (Part One)
Whumptober 2022: 8. Back from the Dead, 26. “Why did you save me?”
Fandom: Top Gun, Top Gun: Maverick, Bradley "Rooster" Bradshaw, f!reader
Word Count: 3337
TW: Angst, Whump, Injuries, Past Death, Grief, Hurt/Comfort, Language
Part One, Part Two

As Rooster heads out to the tarmac for another day of training, he suddenly hears shouts of disbelief and calls for help. Picking up his pace, he reaches the door to the hanger just when Phoenix steps in front of him, blocking his path. Her face is drained of all color, and her breathing is ragged as she opens and closes her mouth, trying to find the words to speak.
Rooster gently places his hands on her shoulders, “What’s wrong? Are you okay?”
Phoenix takes a deep breath before saying, “You need to stay here. Something’s happened but no one knows how and until they do, you need to stay out of the way.”
“Nat, what’s wrong? What happened?” Rooster repeats. Nothing ever shook Phoenix; she was one of the calmest, most adaptable pilots he knew. If she was this rattled, it must be something big.
Biting her lip nervously, Phoenix says, “I know it sounds impossible and if I didn’t see it with my own eyes, I never would have believed it. But someone just appeared on the tarmac.”
“What do you mean appeared? Like an unauthorized plane-”
“No,” Phoenix cuts him off. “I mean, one minute the tarmac was clear and the next she was lying in a heap on the ground. She just…. appeared.”
Rooster feels his blood run cold as he works up the courage to ask his next question. Because somehow, he knows. As impossible as it is, he already knows. “Who? Who appeared?”
With tears in her eyes, Phoenix whispers, “It’s Echo.”

Rooster stands with his arms crossed over his chest as he stares at your sleeping form through the window of your examination room. You’re fast asleep, one leg thrown across the other as you lay on your side, your right arm curled under your pillow as your left arm reaches out in front of you. Towards the side of the bed Rooster usually laid.
He hears Phoenix approaching, but his eyes never leave you. Before she can say anything, Rooster bluntly states, “It’s not her. It can’t be her.”
Phoenix sighs. “I know. Yet based on all the tests they’ve run, it is her. Same blood type, same fingerprints, same retinal scan. From what they can tell, that is Echo.”
“It can’t be! She’s dead!” Rooster hisses as he jabs his finger at your sleeping body. “Two years ago, I held her in my arms as she struggled to take her final breath! Whoever that is, whatever that is, it can’t be her!”
Placing her hand gently on his shoulder, Phoenix says, “I remember. But I don’t know what else to say. It’s her, Rooster. I talked to her, and it was just like talking to Echo. She knows things that only Echo would know. However she got here, that woman in there is the one we lost. Believe me, I can’t begin to comprehend how this happened, but it did. And if that’s the case…. Maybe you got a second chance.”
“Fuck you!” Rooster rips his arm away from Phoenix’s grasp. “What? You really expect me to just accept this? To say screw how it happened and just buy into the idea that she’s back? This isn’t like she just disappeared or went MIA. We had a funeral. Her ashes are still in an urn at her mother’s house. I spent every day of the last two years forcing myself to leave her in the past and now, she’s just somehow back in the present? How am I supposed to buy that?”
“Listen, I can’t even imagine what you’re feeling right now. She was my friend, and this is overwhelming. But for you….” Phoenix sighs. “She’s been asking to see you….. a lot. You’ve been cleared to talk to her but only if you feel up to it. No one expects you to do anything, but I think it would help if you spoke to her. Maybe it’ll convince you that this is what it seems. A miracle.”
She gives him a small smile before leaving him alone to think. Rooster stares at you once more. It doesn’t make any sense. It seems like something out of the fucking Twilight Zone. And yet… if there was a chance — even a fraction of a percent of a chance — that it was true and the woman asleep on that bed was you, how could he walk away without finding out the truth?
Rooster quietly eases into the room, hoping to examine you closer before you wake up. Phoenix was right. You look exactly like the woman he said goodbye to two years ago. Every single detail was the same, down to the way you murmured softly in your sleep or the small scar on your finger from where you cut it while making him a surprise dinner for his birthday. He knows every inch of your body as well as he knowa his own, and everything is exactly as it should be, but he still can’t believe it is really you.
Standing with his back against the wall across from the bed, he clears his throat. Slowly, your eyes flicker open and you roll over to see what woke you. The second your eyes meet his, both of you freeze. Your eyes…. There is no doubt that they’re your eyes; the ones that captivated him the night you met, the ones he stared deeply into as you made love, the ones he watched the light fade from as he held you–
Rooster’s eyes dart to the floor, unable to hold your gaze. Yet he hears you exclaim in breathy relief, “Rooster, thank God! I was getting so worried.”
You start to climb off the bed but he stiffens and shakes his head. Glancing at you out of the corner of his eye, he sees you slowly lower yourself back down as your lip begins to tremble. “No, Roo…. Not you too. What’s going on? Why is everyone treating me like I have the fucking plague o-or I’ve grown a second head! A few hours ago, we were making out in front of the locker rooms, while Bagman and Phoenix teased us, and now…. You can’t even look at me!”
Rooster takes a deep breath and meets your gaze once again. Keeping his voice as steady and unemotional as possible, he says, “I need you to tell me what happened. How did you get here?”
“Wh-what do you mean ‘how did I get here’? I never left!” you cry out desperately. “I was on the tarmac heading to my plane for our next exercise when all of a sudden, I felt really dizzy and I guess I collapsed. The next thing I knew, I’m waking up on the ground and people were yelling and giving me these crazy looks. Then they rushed me in here and started doing all sorts of tests on me. But I told them I’m fine! It was probably just heat stroke or nerves or some shit. Now no one will tell me what’s going on or why they won’t let me leave this room. Why I couldn’t see you until now.”
Suddenly, you pause. Scooting to the end of the bed and leaning in closer, you say, “Roo, what happened? When did you get these scars?” You reach out to touch his face but Rooster jerks away just before your fingers brush his skin.
You collapse back onto the bed once more. “Okay, what the fuck is going on? You seem too repulsed to even let me touch you, yet hours ago you…” The first tears begin to stream down your face and you cry, “I don’t know what’s happening! Everything’s slightly off and no one will tell me why. Like, those scars are old– old enough to have plenty of time to heal. Yet, they weren’t there this morning. And this is the same Top Gun from before but I don’t recognize half the staff or officers. Did I hit my head when I passed out on the tarmac? Did I lose time or am I forgetting things or-or….. I don’t know. But Roo, I’m scared, and I need you right now, so please… just, whatever it is, please tell me what the fuck is going on.”
It takes everything in him for Rooster not to give in, crawl onto the bed, and gather you into his arms. There was nothing he hated more in the world than seeing you cry, yet he still can’t buy into the idea that this was really you. If he allowed himself to believe that and it turned out this was all a lie or a trick…. He wouldn’t survive that.
So, he remains with his back pressed firmly against the wall as he says, “We don’t know what happened or what’s going on. We don’t even know for sure who or what you are.”
You look as if he had just slapped you. “What I am? Rooster, what the hell does that mean?”
“The Top Gun cadet known as Echo died two years ago during a training exercise.” Your eyes grow wide and you shake your head but Rooster continues. “One of the fuel lines in her plane was damaged and her plane crashed.”
“Tha-that’s not possible,” you whisper. “You’re wrong.”
Rooster’s jaw tightens. “I was the first one to the wreckage. She wasn’t able to eject so I had to pull her out of what was left of her plane just for her to die in my arms minutes later. So don’t tell me I’m wrong.”
“But it can’t be… I’m Echo. Just ask me anything. Something about my childhood? How I got the callsign Echo? The day we meet at the Naval Academy? Our first kiss? The first time you told me you loved me? I can tell you anything you want to know. Do you want to search my body for something out of place? Examine every last inch of me? It’s not anything you haven’t seen hundreds of times before. If what you are saying is true, I don’t know how it happened or how it’s even possible. But I do know who I am. I’m the same girl you fell in love with years ago. Who has loved you back for just as long. Who’s begging you to believe me now. I’m Echo.”
Rooster stares at you long and hard for a moment before shaking his head. “No, it can’t be true. You are not my Echo.” Pushing himself off the wall, he walks towards the door.
But just as he wraps his hand around the door handle, your voice calls out from behind him. “Do you remember our conversation right before we walked out onto the tarmac? Because I do. For me, it only happened a few hours ago, so I remember every word.”
Without turning around, Rooster says, “Don’t.”
“You pulled me aside and reminded me that you loved me and as soon as Top Gun was over, you wanted us to start looking for rings.”
“Stop it!”
“And I said that was the stupidest proposal I had ever heard, but nothing would make me happier. Then you kissed me-“
“I said stop!”
“- and told me you would spend the rest of our lives making up for it…. Starting with that night.”
“That’s enough!” Rooster roars as he whirls around to face you, though you didn’t as much as flinch. Your eyes stare unblinkingly into his even as he towers over you, glaring and panting heavily.
Softly, you whisper, “I guess we never got that night, did we?”
He stares at you for another minute before backing out of the room. Rooster never takes his eyes from your heartbroken face until he is out the door and it closes, giving him a barrier between you. Only then does he allow himself to collapse against the wall, breathing heavily as he tries to process what you just said.
Rooster had never told anyone about the conversation he had with you just before he watched you climb into your plane for the last time. He had kept that moment, that promise buried deep down inside himself for the past two years, along with the dreams for the future that went with it. You had agreed to be his wife and when he watched you take your last breath, he hadn’t lost his girlfriend but his fiance. And no one knew. No one except you.

The next week is a whirlwind of activity. Not only is the team busy preparing for their upcoming mission, but they are also preoccupied with the mystery surrounding you. Hangman, Phoenix, and Coyote had all been with you and Rooster at Top Gun when you died. Hangman had even been the one to find Rooster cradling your dead body next to the wreckage of your plane. They all quickly buy into the story that the woman who appeared on the tarmac was the same one they had lost two years ago, but Rooster still refuses to accept it.
After a few days, the Navy reluctantly agrees to allow you back into a plane. After all, you had been the best of the best, practically guaranteed the top spot in your graduating class before your death. And with the mission coming up, they need someone with your talents. Seeing you in the sky erases any lingering doubt in people’s minds that this wasn’t the same Echo as before. The precision and skill are impeccable, with a flair only you can possess. Yet still, Rooster refuses to believe.
So far, he has done his best to avoid you, but your paths have crossed more than a few times over the last week. At first, you try talking to him or get him to believe your story. But after a few days of him ignoring you, you gave up. Yet, seeing you interact with Phoenix, Hangman, and Coyote, laughing and joking as if nothing had ever happened, it is agony for Rooster. But it did make his resolve slip just a little. Could it be true? He still didn’t believe it was really you but what if….?
There is a long discussion on if you should be allowed on the mission or not. After all, you are still legally dead and are no longer active in the military. However, as you point out, that is why you are perfect for the mission: if you don’t make it back, then it’s like nothing changes. So, you are chosen to fly cover behind Dagger 1 – 4, to Rooster’s dismay. He is already nervous enough about this mission and having you along just makes it worse.
However, the mission is completed perfectly. The squad manages to destroy the target just as instructed and they make it out of the valley safely. But the real trouble starts as soon as they fly out of Coffin Corner and into the path of the SAMs. Soon the sky is full of missiles and everyone is desperately trying to stay out of their way.
Rooster shoots off round after round of flares until he presses the button and nothing happens. “Shit! I’m out of flares!” He tries a barrel roll and a few other evasive tactics but nothing is slowing the missiles on his tail. “I can’t shake ‘em, they’re on me!”
Suddenly, his coms come to life. “It’s okay, Roo. I’ll give them another target.”
Panic seizes his heart as he cries desperately, “What? No, Echo, don’t!”
But your reply is oddly calm and resigned. “It’s okay, Rooster. After all….I’m already dead.”
Before he can say anything else, he watches in horror as your plane explodes in a ball of flames. “NO!”
But then Rooster notices a parachute open far below him. You got out this time! And as he turns his plane around, he swears to himself that he’s not going to lose you again.
Mav and the other Daggers all scream at him to continue on and head back to the ship, but he just turns the coms off. He doesn’t care what this will mean for him or his career. Right now, there is only one thing on his mind.

As soon as Rooster touches down, he is tearing through the woods screaming your name. He doesn’t think about the enemies in the area. All he cares about is finding you before it’s too late.
“Echo! Echo, where are you?” There is no response. Just the still quiet of the snowy forest. He screams again, “Goddamn it, Echo! Please! Answer me!”
“Rooster….” The sound is weak and pained, but it’s yours.
Scrambling towards the direction of your voice, he finally spots you propped against a tree with one hand pressed to your stomach. He is by your side in seconds, carefully removing your helmet and holding your face in his hand. “Are you okay? Why the hell did you do that? After everything I put you through for this last week, you still risked your life to save mine. Why?”
“Because I love you, you idiot. I always have.” You smile at him but it quickly turns into a grimace of pain.
“Here, let me see.” Rooster begins unzipping your flight suit and lifting up the shirt you are wearing underneath to examine the area under your hand.
You groan softly as he jostles you. “I don’t think there’s anything to see. A piece of debris hit me on the way down. I’m sure it’s just a bruise but it hurts like a motherfucker.”
Examining it, he can see you’re right. There might be some internal bleeding that he can’t detect, but there is nothing else he can do at the moment.
As he finishes rezipping your flight suit, you grab his wrist. With tears forming in the corner of your eyes, you say, “This is the first time you’ve touched me since I came back.”
Rooster nods, turning his hand so he can thread his fingers with yours. “I know, and I’m sorry. I was so afraid if I touched you, you’d disappear again.”
“I told you, Roo. It’s me. I swear. And I’m not going anywhere.”
He reaches down and cups your face in his hand, his thumb rubbing gently over your cheek. “I know it is, and I’m sorry I refused to see it before. I was so afraid of being hurt that I pushed you away. And because of that, I almost lost you for a second time. But never again. I swear.”
Bending over, he presses his lips against yours, and any last doubts he has about who you are fly from his head. Your lips mold perfectly against his just like always, and the kiss tastes undeniably like you. He tries to deepen the embrace, pulling you in closer, but the soft groan in your throat makes him pause.
Reluctantly, he pulls away. “I’m sorry. I hope that didn’t hurt you.”
You smile at him. “I’ve been waiting to kiss you again since the moment you walked into my examination room a week ago. A little pain was worth it.”
He smiles back and places a soft kiss on the top of your head. Then he settles down next to you and gently eases you onto his lap so you aren’t sitting on the cold snow anymore. You rest your head against his chest as his arms envelop you, and he whispers into your ear, “I love you, Echo.”
He can hear the joy in your voice as you respond, “I love you too, Roo.”

Hangman finds you an hour later. The scene he stumbles onto is eerily similar to the one he witnessed two years ago with Rooster holding your limp body in his arms. But this time Rooster’s face isn’t streaked with tears and shattered into pieces. No, this time, he looks up at Hangman in relief and nods with a broad smile across his face. This time, you are still alive and this isn’t goodbye.

Part 2 out now!
Taglist:@valoraxxx-blog, @m3laniehearts, @autumnleaves1991-blog, @rule107, @vintageleather, @impossiblebagelcowboyfreak, @sugarcoated-lame, @slutforadambanks, @americaarse, @reneki, @ynbutbetter, @imagineadream, @sadpetalsstuff, @salty-thembo, @rachelizabethgraham, @duckandrobin, @queenbbarnes, @grincheveryday, @uselesslyromantic, @chouricojr, @king-of-milf-lovers, @high-fidelities, @shaded-echoes-recs, @dempy, @nik2blog, @dumb-fawkin-bitch, @uselesslyromantic, @choochoo284, @littlebadariell, @blue-aconite, @thescarletknight2014
#whumptober#whumptober2022#whumptober 2022#fic#no.8#no.26#back from the dead#why did you save me?#top gun#top gun maverick#top gun: maverick#rooster#bradley rooster bradshaw#rooster x reader#bradley rooster bradshaw x reader#f!reader#miles teller#angst#hurt/comfort#hurt & comfort
164 notes
·
View notes
Text
A Ghost From the Past (Part One)
Whumptober 2022: 8. Back from the Dead, 26. “Why did you save me?”
Fandom: Top Gun, Top Gun: Maverick, Bradley "Rooster" Bradshaw, f!reader
Word Count: 3337
TW: Angst, Whump, Injuries, Past Death, Grief, Hurt/Comfort, Language
Part One, Part Two

As Rooster heads out to the tarmac for another day of training, he suddenly hears shouts of disbelief and calls for help. Picking up his pace, he reaches the door to the hanger just when Phoenix steps in front of him, blocking his path. Her face is drained of all color, and her breathing is ragged as she opens and closes her mouth, trying to find the words to speak.
Rooster gently places his hands on her shoulders, “What’s wrong? Are you okay?”
Phoenix takes a deep breath before saying, “You need to stay here. Something’s happened but no one knows how and until they do, you need to stay out of the way.”
“Nat, what’s wrong? What happened?” Rooster repeats. Nothing ever shook Phoenix; she was one of the calmest, most adaptable pilots he knew. If she was this rattled, it must be something big.
Biting her lip nervously, Phoenix says, “I know it sounds impossible and if I didn’t see it with my own eyes, I never would have believed it. But someone just appeared on the tarmac.”
“What do you mean appeared? Like an unauthorized plane-”
“No,” Phoenix cuts him off. “I mean, one minute the tarmac was clear and the next she was lying in a heap on the ground. She just…. appeared.”
Rooster feels his blood run cold as he works up the courage to ask his next question. Because somehow, he knows. As impossible as it is, he already knows. “Who? Who appeared?”
With tears in her eyes, Phoenix whispers, “It’s Echo.”

Rooster stands with his arms crossed over his chest as he stares at your sleeping form through the window of your examination room. You’re fast asleep, one leg thrown across the other as you lay on your side, your right arm curled under your pillow as your left arm reaches out in front of you. Towards the side of the bed Rooster usually laid.
He hears Phoenix approaching, but his eyes never leave you. Before she can say anything, Rooster bluntly states, “It’s not her. It can’t be her.”
Phoenix sighs. “I know. Yet based on all the tests they’ve run, it is her. Same blood type, same fingerprints, same retinal scan. From what they can tell, that is Echo.”
“It can’t be! She’s dead!” Rooster hisses as he jabs his finger at your sleeping body. “Two years ago, I held her in my arms as she struggled to take her final breath! Whoever that is, whatever that is, it can’t be her!”
Placing her hand gently on his shoulder, Phoenix says, “I remember. But I don’t know what else to say. It’s her, Rooster. I talked to her, and it was just like talking to Echo. She knows things that only Echo would know. However she got here, that woman in there is the one we lost. Believe me, I can’t begin to comprehend how this happened, but it did. And if that’s the case…. Maybe you got a second chance.”
“Fuck you!” Rooster rips his arm away from Phoenix’s grasp. “What? You really expect me to just accept this? To say screw how it happened and just buy into the idea that she’s back? This isn’t like she just disappeared or went MIA. We had a funeral. Her ashes are still in an urn at her mother’s house. I spent every day of the last two years forcing myself to leave her in the past and now, she’s just somehow back in the present? How am I supposed to buy that?”
“Listen, I can’t even imagine what you’re feeling right now. She was my friend, and this is overwhelming. But for you….” Phoenix sighs. “She’s been asking to see you….. a lot. You’ve been cleared to talk to her but only if you feel up to it. No one expects you to do anything, but I think it would help if you spoke to her. Maybe it’ll convince you that this is what it seems. A miracle.”
She gives him a small smile before leaving him alone to think. Rooster stares at you once more. It doesn’t make any sense. It seems like something out of the fucking Twilight Zone. And yet… if there was a chance — even a fraction of a percent of a chance — that it was true and the woman asleep on that bed was you, how could he walk away without finding out the truth?
Rooster quietly eases into the room, hoping to examine you closer before you wake up. Phoenix was right. You look exactly like the woman he said goodbye to two years ago. Every single detail was the same, down to the way you murmured softly in your sleep or the small scar on your finger from where you cut it while making him a surprise dinner for his birthday. He knows every inch of your body as well as he knowa his own, and everything is exactly as it should be, but he still can’t believe it is really you.
Standing with his back against the wall across from the bed, he clears his throat. Slowly, your eyes flicker open and you roll over to see what woke you. The second your eyes meet his, both of you freeze. Your eyes…. There is no doubt that they’re your eyes; the ones that captivated him the night you met, the ones he stared deeply into as you made love, the ones he watched the light fade from as he held you–
Rooster’s eyes dart to the floor, unable to hold your gaze. Yet he hears you exclaim in breathy relief, “Rooster, thank God! I was getting so worried.”
You start to climb off the bed but he stiffens and shakes his head. Glancing at you out of the corner of his eye, he sees you slowly lower yourself back down as your lip begins to tremble. “No, Roo…. Not you too. What’s going on? Why is everyone treating me like I have the fucking plague o-or I’ve grown a second head! A few hours ago, we were making out in front of the locker rooms, while Bagman and Phoenix teased us, and now…. You can’t even look at me!”
Rooster takes a deep breath and meets your gaze once again. Keeping his voice as steady and unemotional as possible, he says, “I need you to tell me what happened. How did you get here?”
“Wh-what do you mean ‘how did I get here’? I never left!” you cry out desperately. “I was on the tarmac heading to my plane for our next exercise when all of a sudden, I felt really dizzy and I guess I collapsed. The next thing I knew, I’m waking up on the ground and people were yelling and giving me these crazy looks. Then they rushed me in here and started doing all sorts of tests on me. But I told them I’m fine! It was probably just heat stroke or nerves or some shit. Now no one will tell me what’s going on or why they won’t let me leave this room. Why I couldn’t see you until now.”
Suddenly, you pause. Scooting to the end of the bed and leaning in closer, you say, “Roo, what happened? When did you get these scars?” You reach out to touch his face but Rooster jerks away just before your fingers brush his skin.
You collapse back onto the bed once more. “Okay, what the fuck is going on? You seem too repulsed to even let me touch you, yet hours ago you…” The first tears begin to stream down your face and you cry, “I don’t know what’s happening! Everything’s slightly off and no one will tell me why. Like, those scars are old– old enough to have plenty of time to heal. Yet, they weren’t there this morning. And this is the same Top Gun from before but I don’t recognize half the staff or officers. Did I hit my head when I passed out on the tarmac? Did I lose time or am I forgetting things or-or….. I don’t know. But Roo, I’m scared, and I need you right now, so please… just, whatever it is, please tell me what the fuck is going on.”
It takes everything in him for Rooster not to give in, crawl onto the bed, and gather you into his arms. There was nothing he hated more in the world than seeing you cry, yet he still can’t buy into the idea that this was really you. If he allowed himself to believe that and it turned out this was all a lie or a trick…. He wouldn’t survive that.
So, he remains with his back pressed firmly against the wall as he says, “We don’t know what happened or what’s going on. We don’t even know for sure who or what you are.”
You look as if he had just slapped you. “What I am? Rooster, what the hell does that mean?”
“The Top Gun cadet known as Echo died two years ago during a training exercise.” Your eyes grow wide and you shake your head but Rooster continues. “One of the fuel lines in her plane was damaged and her plane crashed.”
“Tha-that’s not possible,” you whisper. “You’re wrong.”
Rooster’s jaw tightens. “I was the first one to the wreckage. She wasn’t able to eject so I had to pull her out of what was left of her plane just for her to die in my arms minutes later. So don’t tell me I’m wrong.”
“But it can’t be… I’m Echo. Just ask me anything. Something about my childhood? How I got the callsign Echo? The day we meet at the Naval Academy? Our first kiss? The first time you told me you loved me? I can tell you anything you want to know. Do you want to search my body for something out of place? Examine every last inch of me? It’s not anything you haven’t seen hundreds of times before. If what you are saying is true, I don’t know how it happened or how it’s even possible. But I do know who I am. I’m the same girl you fell in love with years ago. Who has loved you back for just as long. Who’s begging you to believe me now. I’m Echo.”
Rooster stares at you long and hard for a moment before shaking his head. “No, it can’t be true. You are not my Echo.” Pushing himself off the wall, he walks towards the door.
But just as he wraps his hand around the door handle, your voice calls out from behind him. “Do you remember our conversation right before we walked out onto the tarmac? Because I do. For me, it only happened a few hours ago, so I remember every word.”
Without turning around, Rooster says, “Don’t.”
“You pulled me aside and reminded me that you loved me and as soon as Top Gun was over, you wanted us to start looking for rings.”
“Stop it!”
“And I said that was the stupidest proposal I had ever heard, but nothing would make me happier. Then you kissed me-“
“I said stop!”
“- and told me you would spend the rest of our lives making up for it…. Starting with that night.”
“That’s enough!” Rooster roars as he whirls around to face you, though you didn’t as much as flinch. Your eyes stare unblinkingly into his even as he towers over you, glaring and panting heavily.
Softly, you whisper, “I guess we never got that night, did we?”
He stares at you for another minute before backing out of the room. Rooster never takes his eyes from your heartbroken face until he is out the door and it closes, giving him a barrier between you. Only then does he allow himself to collapse against the wall, breathing heavily as he tries to process what you just said.
Rooster had never told anyone about the conversation he had with you just before he watched you climb into your plane for the last time. He had kept that moment, that promise buried deep down inside himself for the past two years, along with the dreams for the future that went with it. You had agreed to be his wife and when he watched you take your last breath, he hadn’t lost his girlfriend but his fiance. And no one knew. No one except you.

The next week is a whirlwind of activity. Not only is the team busy preparing for their upcoming mission, but they are also preoccupied with the mystery surrounding you. Hangman, Phoenix, and Coyote had all been with you and Rooster at Top Gun when you died. Hangman had even been the one to find Rooster cradling your dead body next to the wreckage of your plane. They all quickly buy into the story that the woman who appeared on the tarmac was the same one they had lost two years ago, but Rooster still refuses to accept it.
After a few days, the Navy reluctantly agrees to allow you back into a plane. After all, you had been the best of the best, practically guaranteed the top spot in your graduating class before your death. And with the mission coming up, they need someone with your talents. Seeing you in the sky erases any lingering doubt in people’s minds that this wasn’t the same Echo as before. The precision and skill are impeccable, with a flair only you can possess. Yet still, Rooster refuses to believe.
So far, he has done his best to avoid you, but your paths have crossed more than a few times over the last week. At first, you try talking to him or get him to believe your story. But after a few days of him ignoring you, you gave up. Yet, seeing you interact with Phoenix, Hangman, and Coyote, laughing and joking as if nothing had ever happened, it is agony for Rooster. But it did make his resolve slip just a little. Could it be true? He still didn’t believe it was really you but what if….?
There is a long discussion on if you should be allowed on the mission or not. After all, you are still legally dead and are no longer active in the military. However, as you point out, that is why you are perfect for the mission: if you don’t make it back, then it’s like nothing changes. So, you are chosen to fly cover behind Dagger 1 – 4, to Rooster’s dismay. He is already nervous enough about this mission and having you along just makes it worse.
However, the mission is completed perfectly. The squad manages to destroy the target just as instructed and they make it out of the valley safely. But the real trouble starts as soon as they fly out of Coffin Corner and into the path of the SAMs. Soon the sky is full of missiles and everyone is desperately trying to stay out of their way.
Rooster shoots off round after round of flares until he presses the button and nothing happens. “Shit! I’m out of flares!” He tries a barrel roll and a few other evasive tactics but nothing is slowing the missiles on his tail. “I can’t shake ‘em, they’re on me!”
Suddenly, his coms come to life. “It’s okay, Roo. I’ll give them another target.”
Panic seizes his heart as he cries desperately, “What? No, Echo, don’t!”
But your reply is oddly calm and resigned. “It’s okay, Rooster. After all….I’m already dead.”
Before he can say anything else, he watches in horror as your plane explodes in a ball of flames. “NO!”
But then Rooster notices a parachute open far below him. You got out this time! And as he turns his plane around, he swears to himself that he’s not going to lose you again.
Mav and the other Daggers all scream at him to continue on and head back to the ship, but he just turns the coms off. He doesn’t care what this will mean for him or his career. Right now, there is only one thing on his mind.

As soon as Rooster touches down, he is tearing through the woods screaming your name. He doesn’t think about the enemies in the area. All he cares about is finding you before it’s too late.
“Echo! Echo, where are you?” There is no response. Just the still quiet of the snowy forest. He screams again, “Goddamn it, Echo! Please! Answer me!”
“Rooster….” The sound is weak and pained, but it’s yours.
Scrambling towards the direction of your voice, he finally spots you propped against a tree with one hand pressed to your stomach. He is by your side in seconds, carefully removing your helmet and holding your face in his hand. “Are you okay? Why the hell did you do that? After everything I put you through for this last week, you still risked your life to save mine. Why?”
“Because I love you, you idiot. I always have.” You smile at him but it quickly turns into a grimace of pain.
“Here, let me see.” Rooster begins unzipping your flight suit and lifting up the shirt you are wearing underneath to examine the area under your hand.
You groan softly as he jostles you. “I don’t think there’s anything to see. A piece of debris hit me on the way down. I’m sure it’s just a bruise but it hurts like a motherfucker.”
Examining it, he can see you’re right. There might be some internal bleeding that he can’t detect, but there is nothing else he can do at the moment.
As he finishes rezipping your flight suit, you grab his wrist. With tears forming in the corner of your eyes, you say, “This is the first time you’ve touched me since I came back.”
Rooster nods, turning his hand so he can thread his fingers with yours. “I know, and I’m sorry. I was so afraid if I touched you, you’d disappear again.”
“I told you, Roo. It’s me. I swear. And I’m not going anywhere.”
He reaches down and cups your face in his hand, his thumb rubbing gently over your cheek. “I know it is, and I’m sorry I refused to see it before. I was so afraid of being hurt that I pushed you away. And because of that, I almost lost you for a second time. But never again. I swear.”
Bending over, he presses his lips against yours, and any last doubts he has about who you are fly from his head. Your lips mold perfectly against his just like always, and the kiss tastes undeniably like you. He tries to deepen the embrace, pulling you in closer, but the soft groan in your throat makes him pause.
Reluctantly, he pulls away. “I’m sorry. I hope that didn’t hurt you.”
You smile at him. “I’ve been waiting to kiss you again since the moment you walked into my examination room a week ago. A little pain was worth it.”
He smiles back and places a soft kiss on the top of your head. Then he settles down next to you and gently eases you onto his lap so you aren’t sitting on the cold snow anymore. You rest your head against his chest as his arms envelop you, and he whispers into your ear, “I love you, Echo.”
He can hear the joy in your voice as you respond, “I love you too, Roo.”

Hangman finds you an hour later. The scene he stumbles onto is eerily similar to the one he witnessed two years ago with Rooster holding your limp body in his arms. But this time Rooster’s face isn’t streaked with tears and shattered into pieces. No, this time, he looks up at Hangman in relief and nods with a broad smile across his face. This time, you are still alive and this isn’t goodbye.

Part 2 out now!
Taglist:@loverhymeswith, @babblydrabbly, @lorecraft, @green-socks, @mayhem24-7forever,@11thstreetvigilante,@the-untamed-soul, @inglourious-imagines, @airhogger, @straightforwardly, @bonnieelizabethparker, @srry-itshockeyszn, @flyinlove, @fandomhopped, @sweetheartlizzie07, @yjwnoot, @wanderdreamer, @pansexualwitchwhoneedstherapy, @fangirlinc, @sparrows-corner, @mads-weasley, @trencher4lyfe, @merlehs, @sunshineflowerchild789, @imjess-themess, @callsign-phoenix, @maggie8002sq, @je-suis-prest-rachel, @tellrock35
#whumptober#whumptober2022#whumptober 2022#fic#no.8#no.26#back from the dead#why did you save me?#top gun#top gun maverick#top gun: maverick#rooster#bradley rooster bradshaw#rooster x reader#bradley rooster bradshaw x reader#f!reader#miles teller#angst#hurt & comfort#hurt/comfort
162 notes
·
View notes
Text
PC Systems Utility Software: Enhancing Performance And Efficiency

PC systems utility software plays a crucial role in maintaining, optimizing, and securing computers. These tools help users manage their systems more effectively, ensuring smooth operation and enhanced performance. This article delves into the various types of PC Systems Utility Software, their functions, benefits, and some popular examples.
Types of PC Systems Utility Software
Utility software can be broadly categorized into several types, each serving a specific function to keep the system running efficiently. The main categories include:
System Optimization Tools
Disk Management Utilities
Security and Privacy Tools
Backup and Recovery Software
System Monitoring Tools
File Management Utilities
1. System Optimization Tools
System optimization tools are designed to enhance the overall performance of a computer by managing system resources and removing unnecessary files.
Registry Cleaners: These tools clean the Windows registry by removing obsolete and redundant entries, which can slow down the system. Popular registry cleaners include CCleaner and Wise Registry Cleaner.
Defragmentation Tools: Over time, files on a hard drive can become fragmented, causing the system to slow down. Defragmentation tools reorganize fragmented data, improving access speed and system performance. Examples include Defraggler and Auslogics Disk Defrag.
Startup Managers: Startup managers help users control which applications run at startup, reducing boot time and freeing up system resources. Autoruns and Startup Delayer are well-known tools in the category of PC Systems Utility Software.
2. Disk Management Utilities
Disk management utilities assist in managing hard drive space, partitioning disks, and ensuring data integrity.

Disk Cleanup Tools: Disk cleanup utilities remove temporary files, system cache, and other unnecessary data to free up disk space. Windows built-in Disk Cleanup and CleanMyPC are examples of such tools.
Disk Checking Tools: These utilities scan the hard drive for errors and bad sectors, ensuring data integrity and preventing potential data loss. CHKDSK (Check Disk) is a built-in Windows utility, while SpinRite is a third-party option.
3. Security and Privacy Tools
Security and privacy tools protect the system from malware, unauthorized access, and data breaches.
Antivirus Software: Antivirus programs detect and remove malware, protecting the system from viruses, worms, and other malicious software. Popular antivirus software includes Norton, Bitdefender, and Kaspersky.
Firewall Software: Firewalls monitor incoming and outgoing network traffic, blocking unauthorized access and protecting the system from cyber threats. Comodo Firewall and ZoneAlarm are well-regarded firewall solutions.
Privacy Tools: Privacy tools help users protect their personal information by securely deleting files, clearing browsing history, and managing cookies. Examples include BleachBit and Privacy Eraser.
4. Backup and Recovery Software

Backup and recovery software ensures data safety by creating copies of important files and providing recovery options in case of data loss.
Backup Tools: Backup utilities create copies of files and folders, allowing users to restore data in case of hardware failure or accidental deletion. Acronis True Image and EaseUS Todo Backup are popular backup solutions.
Recovery Tools: Data recovery tools help retrieve lost or deleted files from hard drives, USB drives, and other storage devices. Recuva and Disk Drill are commonly used recovery tools.
5. System Monitoring Tools
System monitoring tools provide real-time information about system performance, helping users identify and resolve issues quickly.
Resource Monitors: These tools display detailed information about CPU, memory, disk, and network usage, helping users identify resource-hungry applications. Task Manager (built-in Windows utility) and Process Explorer are widely used resource monitors.
Temperature Monitors: Temperature monitoring tools help prevent overheating by displaying real-time temperature data for CPU, GPU, and other components. HWMonitor and Core Temp are popular choices.
Benchmarking Tools: Benchmarking utilities measure the performance of system components, allowing users to compare their hardware against industry standards. Examples include 3DMark and Cinebench.
6. File Management Utilities
File management utilities assist in organizing, searching, and managing files more efficiently.
File Compression Tools: These tools compress files to reduce their size, making them easier to store and transfer. WinRAR and 7-Zip are popular file compression tools.
Duplicate File Finders: Duplicate file finders scan the system for duplicate files, helping users free up disk space. Duplicate Cleaner and Auslogics Duplicate File Finder are commonly used tools.
File Search Tools: File search utilities provide advanced search capabilities, making it easier to find files and folders on the system. Everything and UltraSearch are popular file search tools.
Benefits of Using Utility Software
Using utility software offers numerous benefits, including:
Improved Performance: By cleaning up the system, optimizing resources, and managing startup programs, utility software can significantly improve system performance and responsiveness.
Enhanced Security: Security and privacy tools protect the system from malware, unauthorized access, and data breaches, ensuring the safety of personal and sensitive information.
Efficient Disk Management: Disk management utilities help users manage their storage space more effectively, preventing disk errors and ensuring data integrity.

Real-Time Monitoring: System monitoring tools provide real-time information about system performance, allowing users to identify and resolve issues quickly.
Better File Management: File management utilities assist in organizing, searching, and managing files more efficiently, saving time and effort.
Popular PC Systems Utility Software
Here are some popular utility software programs widely used by PC Systems Utility Software users:
1. CCleaner: A comprehensive system optimization tool that includes a registry cleaner, disk cleanup utility, and startup manager.
2. Norton Antivirus: A robust antivirus solution that protects against malware, viruses, and other cyber threats.
3. Acronis True Image: A reliable backup tool that offers full system backups, incremental backups, and cloud storage options.
4. HWMonitor: A temperature monitoring tool that displays real-time temperature data for CPU, GPU, and other components.
5. WinRAR: A powerful file compression tool that supports various file formats and offers high compression ratios.
6. Recuva: A data recovery tool that can retrieve lost or deleted files from various storage devices.
Conclusion
PC systems utility software is essential for maintaining, optimizing, and securing computers. These tools help users manage their systems more effectively, ensuring smooth operation and enhanced performance. By understanding the various types of utility software and their benefits, users can choose the right tools to keep their systems running efficiently. Whether it’s optimizing system resources, protecting against cyber threats, managing disk space, or ensuring data safety, utility software plays a vital role in the overall health and performance of PC systems utility software.
0 notes
Link
Check out this listing I just added to my Poshmark closet: Genuine Leather Slim Trifold Wallet For Men Card Holder Minimalist RFID Blocking.
0 notes
Text
WP Defense Review – Protects Your Websites & Contents

WP Defense Review — Introduction
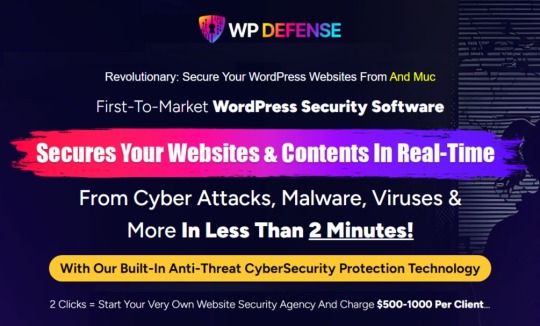
Welcome To My WP Defense Review Post. WP Defense is a first-to-market WordPress security software that provides real-time website and content protection. It safeguards your WordPress sites from cyber attacks, malware, viruses, and more, all within just two minutes. With its built-in anti-threat cybersecurity protection technology, you can have peace of mind knowing that your websites are secure. WP Defense also offers features like 360° SQLi site protection, advanced proxy protection, live spam alerts, domain IP protection, protection from bad bots and crawlers, and much more.
WP Defense Review — Overview
Product: WP Defense
Vendor: Uddhab Pramanik
Official Website: Click Here
Date Of Launch: 2024-May-10
Time Of Launch: 11:00 EDT
Front-End Price: $17
Niche: Software
Coupon Code: $3 Off Discount Coupon “DEFENSE3”
Recommendation: Highly Recommended
Refund: 30 Days Money-Back Guarantee
$3 Off Discount Coupon DEFENSE3
<< Get Access Now WP Defense Discount Price Here >>
WP Defense Review — What Is WP Defense?
WP Defense is a revolutionary WordPress security software that protects your websites and content in real time from cyber attacks, malware, viruses, and more. With just two clicks, you can start your website security agency and charge $500–1000 per client. It offers 360° SQLi site protection, advanced proxy protection, spam alerts, DNSBL integration, protection from bad bots, fake bots protection, and more. It has a user-friendly dashboard, easy installation, and a 30-day money-back guarantee.

WP Defense Review — Features
WP Defense is a first-to-market WordPress security software that offers revolutionary features to secure your websites and content in real time.
Built-in Anti-Threat Cybersecurity Protection Technology: Protects your websites from cyber attacks, malware, viruses, and more.
360° SQLi Site Protection: Ensures that your WordPress site is protected from SQL injection attacks.
Advanced Proxy Protection System: Guarantees 100% site anonymity with cutting-edge proxy technology.
Iron-Clad Anti-Spam Protection Technology: Provides live spam alerts on your site and effectively blocks spam.
DNSBL Integration: Protects your domain name’s IP addresses from being exposed.
Protection from Bad Bots and Crawlers: Safeguards your websites from harmful bots and crawlers.
Built-in Fake Bots Protection Technology: Prevents hacking bots from accessing your site with advanced fake bot protection.
1-Click PHP Configuration Check: Easily check and optimize your site’s PHP configuration with just one click.
Real-Time Login History: Get instant alerts about new logins to your site to detect any unauthorized access.
Block Suspicious IPs: Block suspicious IP addresses with a single mouse click to prevent potential threats.
Built-In Country Blocker: Block specific countries from accessing your website to enhance security.
WordPress Firewall Protection Technology: Provides real-time, world-class firewall protection for your WordPress site.
“Hide Your Login History” Feature: Keeps your login history hidden from unauthorized access.
1-Click ReCAPTCHA Activation: Enhance your site’s security by 10X with easy activation of reCAPTCHA.
Built-In Anti-Virus Scanner: Scan your WordPress site for viruses, malware, and unwanted files, and remove them.
Fully Optimized and Responsive: WP Defense is optimized and responsive for all devices and screen sizes.
Easy 1-Click Installation: Install the WP Defense software on your WordPress site with just one click.
Commercial License Included: Start your website security agency and charge clients $500–1000 per client.
Newbie-Friendly, Easy-to-Use Dashboard: WP Defense is designed with simplicity in mind, making it easy for anyone to use.
Iron-Clad 30-Day Money-Back Guarantee: If you’re not satisfied with WP Defense, you can get a full refund within 30 days.
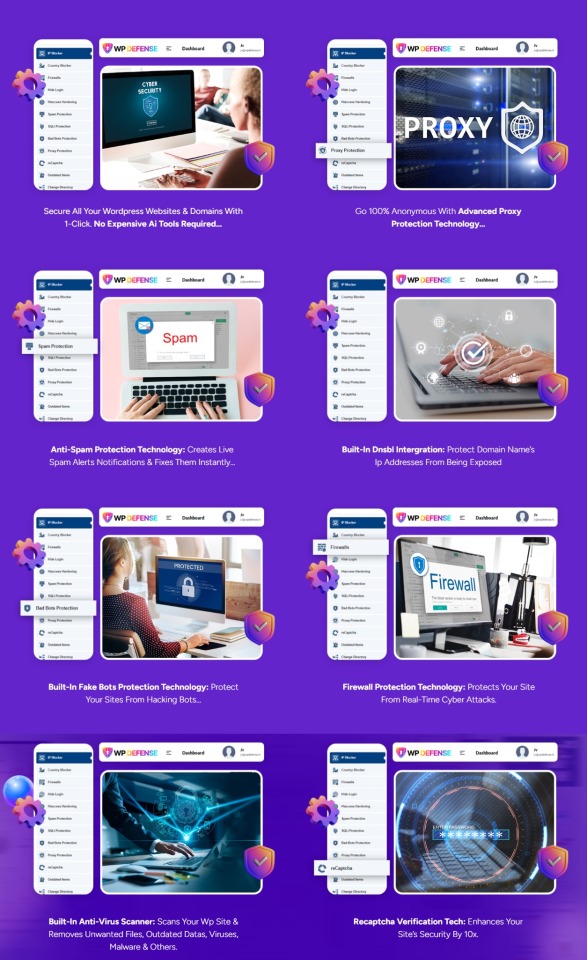
WP Defense Review — Benefits For You
Protects your websites and contents in real-time from cyber attacks, malware, viruses, and more
Built-in 360° SQLi site protection for enhanced security
Guarantees 100% site anonymity with advanced proxy protection system
Get live spam alerts on your site with iron-clad anti-spam protection technology
Protect domain name’s IP addresses from being exposed with DNSBL integration
Secure your sites from bad bots and crawlers
Built-in fake bots protection technology to protect your sites from hacking bots
Check your site’s PHP configuration with just one click
Real-time login history to receive instant alerts about new logins to your site
Block suspicious IPs with one mouse click
Built-in country blocker to block countries of your choice from accessing your website
Real-time protection using world-class WordPress firewall protection technology
Hide your login history for added security
Activate reCAPTCHA on your site to enhance your site’s security
Built-in anti-virus scanner to scan and remove unwanted files, viruses, malware, and more from your WP site
Fully optimized and responsive for all devices
$3 Off Discount Coupon DEFENSE3
<< Get Access Now WP Defense Discount Price Here >>
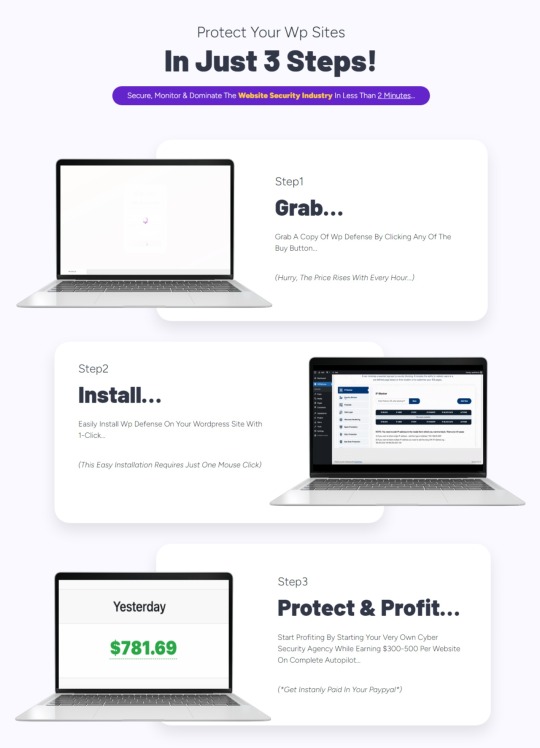
WP Defense Review — How Does It Work?
WP Defense is a revolutionary WordPress security software that is designed to protect your websites and contents in real time from cyber attacks, malware, viruses, and more. It offers built-in anti-threat cybersecurity protection technology to ensure the security of your WordPress websites.
Grab a copy: Get WP Defense by clicking on the buy button and secure your copy at a discounted price.
Install: Easily install WP Defense on your WordPress site with just one click. The installation process is simple and user-friendly.
Protect and profit: Once installed, WP Defense starts securing your website and its content from hackers, cyber attacks, viruses, and more. You can also start your website security agency and charge clients 500−500−1000 per client.
Within minutes, you can have your WordPress website fully secured and protected.
WP Defense Review — Who Should Use it?
WP Defense is designed for anyone who owns or manages WordPress websites and wants to protect them from cyber attacks, malware, viruses, and other security threats.
Website owners and managers who want to ensure the security and integrity of their websites and data.
Freelancers and web developers who provide website management and security services to clients.
Digital agencies and marketing professionals who want to add website security services to their offerings and generate additional revenue.
E-commerce store owners who handle sensitive customer information and want to protect it from data breaches and identity theft.
Bloggers and content creators who want to secure their websites and protect their intellectual property.
Small business owners may not have the technical expertise or resources to implement and manage website security measures but want to protect their online presence.
Anyone who values the security and privacy of their website and wants peace of mind knowing that their site is protected against cyber threats.

WP Defense Review — What’s In It For You?
Secure your WordPress websites and protect them from cyber attacks, malware, viruses, and more in less than 2 minutes.
Built-in anti-threat cybersecurity protection technology ensures real-time website and content security.
Start your website security agency and charge $500–1000 per client with just 2 clicks.
Built-in features such as 360° SQLi site protection, advanced proxy protection system for 100% site anonymity, live spam alerts, DNSBL integration, protection against bad bots and hackers, and more.
One-click installation and an easy-to-use dashboard make it beginner-friendly.
Say goodbye to expensive monthly fees for site protection tools and services.
Commercial license included, allowing you to start your site protection agency.
Fully optimized and responsive for all devices.
A 30-day money-back guarantee ensures your satisfaction with the product.
Limited spots are available, so act now to secure your copy of WP Defense.
$3 Off Discount Coupon DEFENSE3
<< Get Access Now WP Defense Discount Price Here >>
WP Defense Review — Pros and Cons
Pros:
First-to-market WordPress security software that provides real-time protection from cyber attacks, malware, viruses, and more.
Built-in features like 360° SQLi site protection, advanced proxy protection, anti-spam protection, and anti-virus scanning.
Easy installation with just one click and a user-friendly dashboard.
Offers a commercial license for starting your own website security agency and charging clients $500–1000 per client.
Provides live spam alerts and real-time login history for added security.
Includes a built-in country blocker and the ability to hide login history.
Offers a 30-day money-back guarantee and 24/7 support.
Cons:
Limited functionality compared to some other security plugins or services.
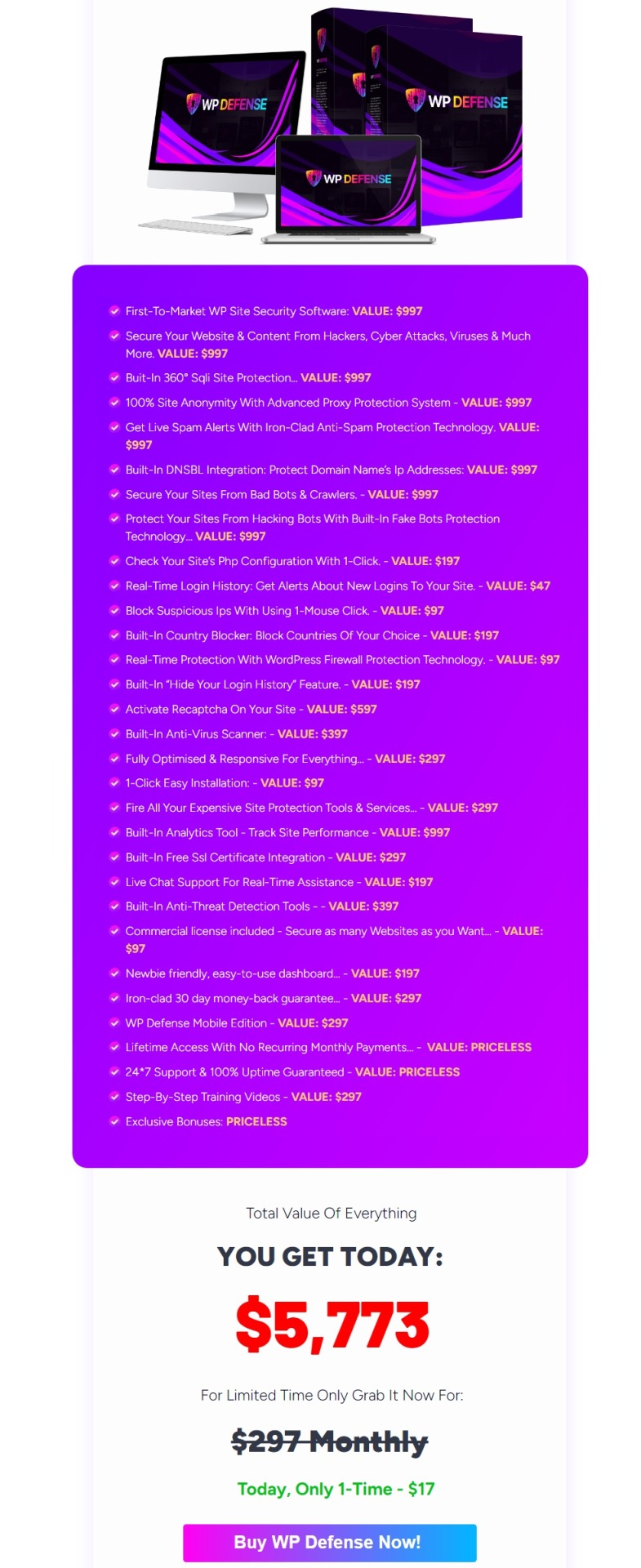
WP Defense Review — Pricing & OTOS
Front-End Offer: WP Defense — $17 (one-time payment)
OTO 1: WP Defense Turbo Upgrade — $9.95 (one-time payment)
OTO 2: WP Defense Reseller License — $97 (one-time payment)
OTO 3: WP Defense DFY Agency Kit — $47 (one-time payment)
OTO 4: WP Defense Whitelabel Rights — $197 (one-time payment)
WP Defense Review — About the Vendor
WP Defense is a revolutionary WordPress security software developed by Uddhab Pramanik. With this powerful software, users can secure their WordPress websites and protect their content in real time from cyber attacks, malware, viruses, and more. WP Defense comes with built-in anti-threat cybersecurity protection technology that ensures the safety of websites and their contents.

WP Defense Review — FAQ
Q: What is WP Defense?
A: WP Defense is a first-to-market WordPress security software that protects websites and their content in real time from cyber attacks, malware, viruses, and more.
Q: Do I need any prior skills or experience to use WP Defense?
A: No, WP Defense is designed to be user-friendly and does not require any prior skills or experience.
Q: Can WP Defense be used on both PC and Mac?
A: Yes, WP Defense can be used on both PC and Mac, as well as Android and iOS devices.
Q: Does WP Defense come with a money-back guarantee?
A: Yes, WP Defense comes with a 30-day money-back guarantee to ensure your satisfaction.
Q: Is customer support available for WP Defense?
A: Yes, WP Defense offers 24/7 support to assist you with any questions or concerns you may have.
Q: Can I use WP Defense to secure multiple websites?
A: Yes, WP Defense allows you to secure unlimited websites, making it suitable for individuals and agencies.
$3 Off Discount Coupon DEFENSE3
<< Get Access Now WP Defense Discount Price Here >>
WP Defense Review — Conclusion
In conclusion, WP Defense is a revolutionary WordPress security software that offers real-time protection for your websites and content. It secures your sites from cyber attacks, malware, viruses, and more in just two minutes. With built-in anti-threat cybersecurity protection technology, WP Defense offers 360° SQLi site protection, guaranteed site anonymity with an advanced proxy protection system, live spam alerts, DNSBL integration for protecting domain IP addresses, protection from bad bots and crawlers, and much more.
Thank you for reading my WP Defense Review till the end. Hope it will help you to make the purchase decision perfectly.
Check Out My Previous Reviews: Profitsoci Review, AI FameRush Review, AcquireWeb AI Review, Gen AI Review, AI WebProfit Review, VidSupremacy Review, MintSuite Review, Artisia Review, Coursiify Review, Infinite Hub Review, WP Defense Review
#WPDefense#WPDefenseupgrades#WPDefensereview#WPDefensefeatures#WPDefenseworks#whatisWPDefense#buyWPDefense#WPDefenseprice#WPDefensedemo#WPDefensediscount#WPDefensehonestreview#WPDefensefe#WPDefensesoftwarereview#WPDefensepros#reelrampageaioto#WPDefensepreview#WPDefensescam#WPDefensesoftware#getWPDefense#WPDefensereviews#WPDefenselegal
0 notes
Text
Email Security Market Projections: Global Industry Analysis and Forecast (2023-2032)

The global email security market is anticipated to grow at a substantial CAGR of 12.20% in the upcoming years. The global email security industry was estimated to be worth USD 3.10 billion in 2022 and was expected to be worth USD 6.93 billion by 2028.
Email Security Market encompasses solutions and services designed to protect email communications from external threats, including phishing attacks, malware, spam, and data breaches. As email remains a primary communication tool for businesses and individuals alike, its security has become crucial due to the sensitive information it often contains. This market has seen substantial growth due to the rising number of email-based attacks and the increasing sophistication of cyber threats.
Key products in this market include email encryption, anti-spam and anti-malware software, data loss prevention (DLP) technologies, and threat intelligence systems. These solutions are deployed across various platforms, including on-premises, cloud-based, and hybrid environments, catering to the diverse needs of different organizations. Additionally, the adoption of regulatory compliance standards, which mandate the protection of sensitive information, further drives the demand for robust email security solutions. The market is characterized by continuous innovation, as providers strive to stay ahead of cybercriminals with advanced features like artificial intelligence and machine learning to detect and prevent threats more effectively.
Top Key Players-
Cisco Systems
Proofpoint, Symantec
Trend Micro
Zix
CryptZone
DataMotion
EchoWorx
Egress Software Technologies
Entrust
Email security is a critical component of cybersecurity strategies, designed to protect email communications from various threats.
Here are key points about email security:
Common Threats
Phishing: Fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity.
Malware: Malicious software sent via email attachments or links, intended to damage or gain unauthorized access to a system.
Spam: Unsolicited and often irrelevant messages sent in bulk, which can congest email traffic and carry malware.
Business Email Compromise (BEC): Targeted attacks involving the hacking or spoofing of business email accounts to defraud the company, its employees, customers, or partners.
Key Technologies:
Email Encryption: Encrypts email content to protect sensitive information during transmission.
Anti-Spam Filters: Automatically detect and block spam emails, reducing clutter and risk of exposure to harmful content.
Anti-Malware Tools: Scan and remove malicious software from incoming emails.
Data Loss Prevention (DLP): Monitors and controls sensitive data that is being sent via email to prevent data breaches.
Threat Intelligence: Uses global threat data to identify and respond to emerging security threats targeting email systems.
Deployment Models:
On-Premises: Email security solutions installed directly on the company's hardware.
Cloud-Based: Services hosted by third-party providers, offering scalability and ease of management.
Hybrid: Combines on-premises and cloud-based solutions for flexible deployment based on security needs and resources.
Regulatory Compliance: Ensures that email practices comply with legal and regulatory standards like GDPR, HIPAA, and others, which mandate the protection of private information.
Benefits:
Protection Against Data Breaches: Reduces the risk of financial loss and reputational damage from data leaks.
Enhanced Privacy: Protects sensitive information from being accessed by unauthorized parties.
Improved Compliance: Helps organizations meet regulatory requirements and avoid penalties.
Future Trends:
Integration of AI and Machine Learning: Enhancing the detection and response capabilities of email security systems.
Increasing Use of Behavioral Analytics: To identify abnormal actions that could indicate a security threat.
More About Report- https://www.credenceresearch.com/report/email-security-market
Segmentation:
By Component
Products
Services
By Deployment Mode
Cloud
On-Premise
By Industry Vertical
BFSI
Healthcare
Government
IT & Telecom and Others
Email Security Market Dynamics
Market Drivers
Rising Email Threats: The increasing frequency and sophistication of email-based cyberattacks, such as phishing, spear-phishing, and ransomware, drive the demand for robust email security solutions.
Regulatory Compliance: Stricter data protection laws (like GDPR, HIPAA) necessitate the adoption of secure email practices to avoid substantial fines and legal issues, pushing organizations towards comprehensive email security solutions.
Digital Transformation: As businesses increasingly move their operations online, the need to protect email communications intensifies, particularly in sectors handling sensitive data like healthcare, finance, and government.
Growing Awareness of Cyber Risks: Widespread media coverage of major breaches and the direct experience of cyberattacks have heightened awareness of the risks associated with insecure email practices, compelling businesses to invest in security measures.
Market Challenges
Complexity of Security Management: As email threats evolve, managing email security becomes more complex, requiring continuous updates and monitoring which can be resource-intensive for organizations.
High Cost of Advanced Solutions: Implementing state-of-the-art email security solutions can be expensive, especially for small and medium-sized enterprises (SMEs) that might lack the necessary budget.
Integration Issues: Integrating advanced email security solutions with existing IT infrastructure can be challenging, particularly in organizations with outdated systems or those using a diverse array of software tools.
User Behavior: Human error remains a significant vulnerability in email security. Employees may inadvertently click on malicious links or ignore security protocols, undermining even the most robust security measures.
Emerging Trends
Adoption of Artificial Intelligence and Machine Learning: AI and ML are increasingly being utilized to enhance threat detection capabilities, improve the accuracy of spam filters, and automate response to suspicious activities.
Cloud-Based Email Security Solutions: With the shift towards cloud computing, there's a growing preference for cloud-based email security solutions that offer scalability, lower maintenance costs, and enhanced protection against threats.
Greater Focus on Insider Threats: As insider threats become more common, email security solutions are increasingly incorporating tools that monitor for unusual internal activities, helping prevent data leaks from within an organization.
Multi-Factor Authentication (MFA): MFA is becoming a standard security practice for accessing email systems, adding an extra layer of security to protect against unauthorized access.
Integration with Broader Security Frameworks: Email security is being integrated with broader security measures, including endpoint security and network management systems, to provide a holistic approach to organizational security.
Browse the full report – https://www.credenceresearch.com/report/email-security-market
Browse Our Blog; https://www.linkedin.com/pulse/email-security-market-analysis-global-industry-trends-priyanshi-singh-bvjff
Contact Us:
Phone: +91 6232 49 3207
Email: [email protected]
Website: https://www.credenceresearch.com
0 notes
Text
Safeguarding Your Digital Infrastructure: The Role of Candid8’s Cutting-Edge Security Services
In today’s interconnected world, the integrity and security of your digital infrastructure are paramount. With cyber threats on the rise and data breaches becoming increasingly common, businesses need robust security solutions to protect their assets and maintain customer trust. Enter Candid8, a leading provider of innovative infrastructure security services designed to safeguard your organization against evolving cyber threats.
Understanding Infrastructure Security
Infrastructure security refers to the measures and protocols put in place to protect the underlying components of a network, including servers, routers, switches, and data centers, from unauthorized access, malicious attacks, and other security risks. These components form the backbone of your organization’s IT infrastructure, making their protection essential for maintaining business continuity and ensuring data confidentiality, integrity, and availability.
Candid8’s Comprehensive Security Solutions
Candid8 offers a comprehensive suite of infrastructure security services tailored to meet the unique needs and challenges of modern businesses. From risk assessment and vulnerability management to intrusion detection and incident response, Candid8’s team of experts employs industry-leading technologies and best practices to fortify your digital infrastructure against cyber threats.
Key Features of Candid8’s Infrastructure Security Services
Risk Assessment: Candid8 conducts thorough risk assessments to identify potential vulnerabilities and weaknesses in your infrastructure, allowing proactive mitigation measures to be implemented.
Vulnerability Management: Candid8 helps organizations prioritize and remediate vulnerabilities through continuous monitoring, patch management, and vulnerability scanning.
Intrusion Detection and Prevention: Candid8 uses modern intrusion detection and prevention systems to detect and block malicious activity in real time, allowing it to prevent cyber attacks before they cause damage.
Incident Response: In the event of a security incident, Candid8 provides rapid incident response services to minimize downtime, mitigate damage, and restore normal operations as quickly as possible.
Security Awareness Training: Candid8 offers comprehensive security awareness training programs to educate employees about cybersecurity best practices and empower them to recognize and respond to potential threats effectively.
Conclusion:
Candid8’s infrastructure security services offer a proactive and holistic approach to protecting your organization’s digital assets. With Candid8 as your trusted security partner, you can rest assured that your infrastructure is fortified against cyber threats, allowing you to focus on driving business growth and innovation with confidence. Don’t leave your digital infrastructure vulnerable safeguard it with Candid8’s cutting-edge security solutions today.
#Candid8Secure#SecureInfrastructure#CyberDefense#DataProtection#NetworkSecurity#CloudSecurity#ITSecurity#SecureOperations#ThreatDetection#CyberResilience#InfoSecSolutions#SecureArchitecture#DigitalProtection#SecureCommunications#InfrastructureDefense
0 notes
Text
Blockchain in Distribution Management: Transparency and Security.
Blockchain technology, once synonymous solely with cryptocurrencies, has now transcended its original purpose and is making significant strides in revolutionizing various industries. In the realm of distribution management systems (DMS), blockchain technology is emerging as a game-changer, offering unparalleled transparency, security, and efficiency. This article explores the rise of blockchain technology in DMS and its profound impact on enhancing transparency and security across the supply chain.
Understanding Blockchain Technology
At its core, blockchain technology is a decentralized and immutable ledger that records transactions across multiple computers in a tamper-proof manner. Each block in the chain contains a cryptographic hash of the previous block, creating a secure and transparent record of transactions.
The Role of Blockchain in Distribution Management Systems
Supply Chain Transparency: Blockchain enables end-to-end transparency by providing a secure and immutable record of every transaction and movement of goods across the supply chain. From raw material sourcing to manufacturing, distribution, and delivery, stakeholders can trace the entire journey of a product with unprecedented visibility.
Secure Data Management: Blockchain’s decentralized nature eliminates the need for a central authority, reducing the risk of data tampering, fraud, and unauthorized access. By securely encrypting and storing data across multiple nodes, blockchain ensures data integrity and confidentiality, enhancing security throughout the distribution process.
Key Benefits of Blockchain in DMS
Enhanced Traceability: Blockchain enables real-time tracking and tracing of products, allowing businesses to verify the authenticity, origin, and journey of each item. This level of traceability is particularly crucial in industries like food and pharmaceuticals, where product safety and compliance are paramount.
Streamlined Transactions: Blockchain facilitates seamless and secure transactions between supply chain partners, eliminating intermediaries and reducing transaction costs and delays. Smart contracts, self-executing contracts with predefined conditions, automate contract execution, payment, and compliance, further streamlining transactions.
Improved Supply Chain Efficiency : By providing a single source of truth and eliminating data silos, blockchain enhances collaboration and coordination among supply chain participants. This leads to improved efficiency, reduced errors, and faster decision-making, ultimately driving operational excellence across the supply chain.
Real-World Applications of Blockchain in DMS
Product Authentication: Blockchain enables product authentication through unique digital identifiers or “digital twins” assigned to each product. Customers can verify the authenticity and provenance of products by scanning QR codes or NFC tags, fostering trust and combating counterfeit goods.
Track and Trace: Blockchain-powered track-and-trace solutions enable real-time monitoring of product movement, temperature, and other relevant data throughout the supply chain. This visibility helps businesses identify bottlenecks, optimize routes, and respond swiftly to disruptions, ensuring timely delivery and customer satisfaction.
Challenges and Future Outlook
Integration Challenges: Despite its potential, widespread adoption of blockchain technology in DMS faces challenges related to interoperability, scalability, and integration with existing systems. Overcoming these challenges requires collaboration among stakeholders and investment in interoperable blockchain platforms.
Future Outlook: As blockchain technology matures and standards evolve, its integration into DMS is expected to accelerate. Innovations such as tokenization, decentralized autonomous organizations (DAOs), and blockchain-based marketplaces hold promise for further enhancing transparency, efficiency, and trust in distribution management.
Conclusion
In conclusion, blockchain technology is poised to disrupt the traditional paradigms of distribution management by providing unprecedented transparency, security, and efficiency. By leveraging blockchain’s decentralized ledger and smart contract capabilities, businesses can transform their distribution processes, streamline transactions, and build trust with customers and partners.
As the adoption of blockchain technology continues to grow, organizations must stay abreast of emerging trends, invest in blockchain education and infrastructure, and collaborate with industry partners to unlock the full potential of blockchain in distribution management.
Embrace the rise of blockchain technology in distribution management system and embark on a journey towards enhanced transparency, security, and efficiency in your supply chain operations.
0 notes
Text
Peace of Mind in Your Pocket: My Review of the RFID Protector
In today's digital world, convenience often comes with a side of security concerns. Contactless cards, while undeniably handy, can be vulnerable to electronic pickpocketing. This is where the RFID Protector comes in. I recently started using this product, and I'm impressed by its effectiveness and ease of use.

Unbeatable Protection Against Electronic Theft
The primary function of the RFID Protector is to safeguard your contactless cards from unauthorized scanning. It achieves this through a special material that blocks radio frequencies used by RFID scanners. During the past few weeks, I've carried my credit cards and passport in an RFID Protector sleeve. I've tested it with various RFID readers, and none were able to detect the cards within the sleeve. This provides immense peace of mind, knowing my financial information and personal details are shielded from potential thieves.
Compact and Convenient Design
The RFID Protector is surprisingly thin and lightweight. It easily fits into my wallet alongside my cards without causing any bulkiness. The material feels durable and well-made, and I'm confident it will withstand everyday wear and tear. Additionally, the design is sleek and minimalistic, making it a discreet yet effective security measure.
Multiple Application Options
The beauty of the RFID Protector lies in its versatility. While I primarily use it for my credit cards, it can also safeguard other RFID-enabled items like passports and key fobs. This makes it a one-stop solution for protecting all your sensitive information.
A Small Investment for Big Security
The RFID Protector is a relatively inexpensive product, especially considering the value it offers. For a small price, you gain peace of mind knowing your financial information and personal details are shielded from unauthorized access. Compared to the potential losses from electronic theft, the RFID Protector is an absolute steal.
Overall Satisfaction
Overall, I'm highly satisfied with the RFID Protector. It's a simple yet effective solution for safeguarding your contactless cards and other RFID-enabled items. The product is well-designed, convenient to use, and offers excellent value for money. If you're concerned about electronic theft, I highly recommend investing in an RFID Protector. It's a small addition to your wallet that can make a big difference in protecting your financial security.
0 notes
Text
Peace of Mind in a Pocket: My Review of the RFID Protector Deliverable.
As a security-conscious individual living in a world where digital theft is an ever-present threat, I was thrilled to discover the RFID Protector Deliverable. This innovative product has become an essential part of my daily life, offering unparalleled protection against electronic pickpocketing and ensuring my financial information remains secure.

A Technological Guardian Against Theft
The RFID Protector Deliverable utilizes cutting-edge technology to safeguard your contactless cards from unauthorized scans. These cards, which include credit cards, debit cards, and even passports, contain RFID chips that transmit data wirelessly. Unfortunately, this convenience also creates a vulnerability, as unscrupulous individuals can use RFID scanners to steal your information from a distance.
The RFID Protector Deliverable acts as a shield, effectively blocking the signals emitted by RFID scanners. Its compact and stylish design allows you to incorporate it effortlessly into your everyday routine. I simply keep it in my wallet alongside my cards, and I can rest assured that my personal and financial data is safeguarded.
Unparalleled Convenience and Peace of Mind
The RFID Protector Deliverable is not only effective but also incredibly convenient. Its lightweight and slim profile ensures it doesn't add unnecessary bulk to your wallet or purse. Additionally, the product requires no maintenance or charging, making it a hassle-free solution for everyday use.
Since incorporating the RFID Protector Deliverable into my life, I've experienced a newfound sense of security. Whether I'm commuting on public transport, shopping at crowded stores, or simply running errands, I no longer have to worry about becoming a victim of electronic theft. This peace of mind is invaluable, and it allows me to navigate the world with greater confidence.
A Smart Investment in Security
While some might consider the RFID Protector Deliverable a small investment, I view it as a crucial safeguard against a significant financial loss. Identity theft can be a devastating experience, and the potential costs associated with stolen financial information can be substantial. The RFID Protector Deliverable offers an inexpensive and reliable way to mitigate this risk, making it a wise investment for anyone who values their financial security.
In conclusion, the RFID Protector Deliverable is an exceptional product that delivers on its promise of superior RFID protection. Its effectiveness, convenience, and affordability make it an indispensable tool for anyone who wants to safeguard their personal and financial information in today's digital age. I highly recommend this product to anyone who prioritizes security and peace of mind.pen_sparktunesharemore_vert
0 notes
Text
A Digital Shield: My Experience with the RFID Protector
In today's increasingly digital world, protecting our personal information is paramount. With contactless payment methods and chip-enabled cards becoming the norm, concerns about RFID (Radio-Frequency Identification) skimming have grown. That's why I decided to explore the RFID Protector. This innovative product promises to safeguard your personal information from unauthorized scans, and let me tell you, it's given me peace of mind in a digital age.

A Discreet Barrier Against Digital Theft
The RFID Protector isn't a bulky or intrusive device. It comes in various forms, from sleeves for credit cards to wallets with built-in blocking technology. The option I chose is a slim and stylish cardholder that easily fits in my pocket or bag. The blocking technology is seamlessly integrated into the design, ensuring protection without compromising on convenience. This discreet approach allows me to carry my cards with confidence, knowing they're shielded from potential RFID theft.
Peace of Mind in a Digital Wallet
While the chances of RFID skimming might seem low, the potential consequences are significant. The idea of someone stealing my credit card information through a contactless scan was a growing concern. The RFID Protector has alleviated that anxiety. Knowing my cards are shielded from unauthorized scans allows me to embrace contactless payment methods with confidence. It's a small investment that offers significant peace of mind in a world increasingly reliant on digital transactions.
Beyond Credit Cards: A Broader Shield
The beauty of the RFID Protector is that its applications extend beyond credit cards. Many passports and ID cards now contain RFID chips, making them vulnerable to unauthorized scans. The RFID Protector offers a layer of security for these essential documents as well. This broader protection ensures peace of mind not just for financial information but also for personal identification.
Quality Construction and Long-lasting Protection
The RFID Protector I chose is well-made and feels durable. The high-quality materials ensure it can withstand daily wear and tear, making it a worthwhile investment. Plus, the blocking technology is built to last, offering long-term protection against evolving RFID threats.
Is the RFID Protector Right for You?
The decision to use an RFID Protector is a personal one. However, if you're concerned about the potential for digital theft and want to safeguard your personal information, then the RFID Protector is definitely worth considering. Remember, it's always a good idea to stay vigilant about your digital security practices. However, for me, the RFID Protector has been a simple and effective way to add an extra layer of protection to my digital wallet and important documents.
#rfidprotector#digitalsecurity#rfidtheft#contactlesspayments#identityprotection#peaceofmindtech#dataprivacy#digitalwallet#financialsecurity#techprotection#yellowjackets#welcome home#wally darling#ted lasso#artists on tumblr
0 notes