#Data protection measures
Text
Features of the Most Reliable VPN Services
In today’s interconnected world, where privacy concerns and data breaches are rampant, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. However, not all VPN services are created equal. While some may offer flashy features or enticing deals, the true mark of reliability lies in a set of core features that distinguish the best from the rest. In…

View On WordPress
#A#Cross-Platform Compatibility#Customer Support#Customer support availability#Data encryption#Data encryption standards#Data Protection#Data protection measures#Encryption protocol security#Geo-restriction#Geo-restriction bypass#Geo-restriction circumvention#Internet safety#Internet safety assurance#Kill switch#Kill switch feature#Leak protection#Leak protection mechanism#Network reliability#Network reliability assessment#No-logs guarantee#No-Logs Policy#Online Privacy#Online privacy protection#Privacy policy assurance#Privacy protection#Secure Connection#Secure connection establishment#Security encryption#Server network
0 notes
Text
on the topic of privacy tips and ko-fi commissions, it sure seems to be these days that websites hide the log out button in a less enticing place than... every other action you would be reaching for, and some that you wouldn't otherwise be reaching for. if you aren't already clearing login data every time you close your browser, this further disincentivises people from logging out of things. giving more opportunities to collect data that you only agree to give as a user / that can now more easily be connected to you as a user.
#important piece of context i missed: i had to open a second menu to log out of ko-fi like i do with tumblr these days#o-ver-pow-ered. that spells op#firefox has total cookie protection that prevents most cross-site snooping (even if they can still find other common data & trade info)#but you may recall that chrome and derivatives still have the biggest market share. websites can count on its lack of privacy interests#they Will design with that in mind. continuing to use lowest common denominator privacy measures enables their data brokering
2 notes
·
View notes
Photo










‘being one of the only people in your entire area actually still taking the pandemic very seriously and following safety measures while every single person around you rapidly decides they completely no longer give a shit’ moodboard
#my bastard in hell i have fucking health conditions#maybe you want to gamble your shit but I simply cannot take those risks dude#and it is increasingly hard to interact with literally any other human being when it seems like we both live in alternate realities#AND if they won't even give the basic respect of just being careful around ME#just a basic 'okay I know we apparently disagree somehow but at least while you're around me could you take these precautions#to help protect me' then it's immediately just *deeply personal reason against it* *argument entirely based on how the person#feels and not any actual current data or pandemic statistics* *random personal anecdote* *reckless nihilism based in#reasonable and understandable exasperation but still missing the point and not ultimately practically helpful in terms of genuinely preventi#ng things from getting worse and simply worsening the conditions that foster the nihilism and exasperation in the first place* *ableism*#*the weirdest fucking argument you've ever heard in your life* *some other entirely personal sentimental reasoning*#*some argument that basically boils down to the fact that they don't trust or respect or care about you and your boundaries or health*#like gHHHGhhhhhhhhhh#JUST STAY AWAY FROM ME AND WEAR A MASK FOR 30 MINUTES whY does it have to be a debate WHY is that SOO hard#also people I know keep planning stuff and trying to force and guilt trip me and others in my household to go do stuff with them#and are like planning vacations and all this stupud bullshit and now I'm constantly having to put up with it and seem 'mean' or whatever#one of my roomates is fine but the other one is more emotionally volatile and definitely prone to being pulled in by being Lonely#or wanting to do stuff with loved ones and compromising on safety because they're being manipulated by the people around them#into feeling like they're being a burden by asking people to wear masks or etc. so its a constant trust issue where I have to just desparate#ly hoep that when left on their own they're ACTUALLY going to stand up for themselves and stick to their beliefs#and not just like come home and lie about following sfatey measures then secretly give me covid or something.. hhh... WHICH wouldnt be a pro#blem if EVERYONE on the earth wasnt just acting like the pandemic is over and deciding to be reckless - because then it's a matter of#social conformity and peer pressure and following the Culture instead of the data and even people who were safe before will see everyone aro#und them taking things less seriously and decide maybe now it's reasonable to do the same thing themselves or etc. etc.#and it's like... nothing with the VIRUS ITSELF changed lol.. the response changed and the culture changed but the part that matters is the#SAME....the virus isn't looking around like 'hey people seem more chill about this now - maybe I should just relax a little bit and not#infect people for a while. i really dont want to get in the way of their pool party summer vacation and all of that. i'll just step back'#HHHHHHHHHHHHH anyway.... oi am goin inshane lov...........#covid mention#covid tw
51 notes
·
View notes
Text
Because there are so many linked devices and the potential vulnerabilities they present, cybersecurity on the Internet of Things (IoT) is a concern. These devices are appealing targets for exploitation because they frequently lack integrated security protections. Thankfully, cybersecurity can help.
0 notes
Text
Data transfers based on the old EU SCC’s must be replaced before 21 March 2024
In February 2022, the UK introduced the International Data Transfer Agreement (IDTA) and the UK Addendum to the European Commission’s new standard contractual clauses (new EU SCCs).
These documents, essential for data protection in the post-Brexit era, are designed to ensure that personal data transfers from the UK to countries not covered by the UK’s adequacy regulations comply with the UK…

View On WordPress
#Brexit#data processing agreement#Data protection#data transfer#EU standard contractual clauses#GDPR Article 46#ICO revisions#ICO UK GDPR guide#International Data Transfer Agreement#multinational organisations#new EU SCCs#processor requirements#restricted transfer#Schrems II#supplementary measures#Transfer Risk Assessment#UK Addendum#UK adequacy decisions#UK adequacy regulations#UK GDPR#UK GDPR transfer arrangements#UK-based organisations#valid SCCs
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare.
Healthcare under Cyber Attack
I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text
Unlock Fort Knox for Your Laptop: The Definitive Guide to Bulletproof Security

What steps can I take to enhance my laptop's security?
Dive into my latest Blog post and discover the ultimate secrets to fortifying your laptop's defenses! Transform your device into a digital fortress and safeguard your data like never before.
From foolproof password strategies to state-of-the-art encryption techniques, explore a treasure trove of tips and tricks to keep hackers at bay. Say goodbye to cyber worries and hello to peace of mind!
Ready to take control of your laptop's security? Arm yourself with knowledge now!
Read the full post and become the guardian of your digital domain. #LaptopFortress #SecureYourData #ReadMore
#LaptopSecurity#DataProtection#CybersecurityTips#Laptop security#Data protection#Cybersecurity tips#Digital privacy#Encryption#Password management#Cyber threats#Data security measures#Online safety#Tech security#Information security#Secure computing#IT security#Protecting sensitive data#Internet safety
1 note
·
View note
Text
Threads Privacy and Security: Safeguarding Your Online Presence
In the age of social media, privacy and security have become paramount concerns for users. Meta Platforms’ Threads understands the importance of protecting users’ online presence and prioritizes privacy and security features. In this article, we will explore how Threads safeguards your online presence, empowering users to engage in microblogging while maintaining control over their personal…

View On WordPress
#Cyber Threats#Cybersecurity#Data Protection#Internet Privacy#Online Identity#Online Presence#Online Privacy Best Practices#Online Privacy Tips#Online Safety#Online Security Measures#Personal Information#Privacy Awareness#Thread Safety#Threads
0 notes
Text
Wearable Technology in the Construction Industry: Enhancing Safety and Efficiency
Introduction
The construction industry is known for its physically demanding and high-risk nature. However, with the advancements in technology, new tools are emerging to address safety concerns and enhance efficiency. One such innovation is wearable technology, which has gained traction in recent years due to its potential to revolutionize the construction sector. This article explores the…

View On WordPress
#AR Technology#Battery Life#Collaboration Tools#construction industry#Construction Productivity#Construction Projects#Construction Safety#Cybersecurity Measures#Data Insights#data protection#Data Security#Durability#Environmental Resistance#Exoskeletons#Future Prospects#Implementation Challenges#Job Site Efficiency#On-site Support#Performance Metrics#Privacy Concerns#Productivity Boost#Real-time Communication#Remote Monitoring#Resource Optimization#Rugged Devices#Safety Compliance#Smart Glasses#Smart Helmets#Smart Vests#Wearable Costs
0 notes
Text
Ensuring Data Privacy: European Union & United States Agreement Strengthens Transatlantic Data Flows Introduction
Secure your data in the digital era. The EU-U.S. Data Privacy Framework ensures strong safeguards, trust, and privacy rights. Protecting your information is our priority. #DataPrivacy #EUUSFramework
In today’s digital age, protecting personal data has become increasingly important. Both individuals and businesses rely on the safe and secure transfer of data across borders, especially between the European Union and the United States. Recognizing the significance of this issue, the European Commission has adopted a new decision ensuring that personal data transferred from the European Union to…

View On WordPress
#arbitration panel#collaboration#compliance#cooperation#criminal law enforcement#cross-border data transfer#data governance#data handling#data integrity#Data Privacy#data privacy framework#data privacy standards#Data Protection#data protection review court#data retention#data security#data security measures#data sovereignty#data transfer#digital privacy#economic ties#EU data regulations#EU-U.S. Data Privacy Framework#European Commission#European Court of Justice#European Union#GDPR#independent dispute resolution#international data flows#legal framework
0 notes
Text
"The coral reefs of south Sulawesi are some of the most diverse, colorful and vibrant in the world. At least, they used to be, until they were decimated by dynamite fishing in the 1990s.
As part of a team of coral reef ecologists based in Indonesia and the UK, we study the reefs around Pulau Bontosua, a small Indonesian island in south Sulawesi...
In many places around the world, damage like this might be described as irreparable. But at Pulau Bontosua, the story is different. Here, efforts by the Mars coral restoration program have brought back the coral and important ecosystem functions, as outlined by our new study, published in Current Biology. We found that within just four years, restored reefs grow at the same rate as nearby healthy reefs.
Speedy recovery
The transplanted corals grow remarkably quickly. Within a year, fragments have developed into proper colonies. After two years, they interlock branches with their neighbors. After just four years, they completely overgrow the reef star structures and restoration sites are barely distinguishable from nearby healthy reefs.
The combined growth of many corals generates a complex limestone (calcium carbonate) framework. This provides a habitat for marine life and protects nearby shorelines from storm damage by absorbing up to 97% of coastal wave energy.
We measured the overall growth of the reef framework by calculating its carbonate budget. That's the balance between limestone production (by calcifying corals and coralline algae) and erosion (by grazing sea urchins and fishes, for example). A healthy reef produces up to 20kg of reef structure per square meter per year, while a degraded reef is shrinking rather than growing as erosion exceeds limestone production. Therefore, overall reef growth gives an indication of reef health.
At Pulau Bontosua, our survey data shows that in the years following restoration, coral cover, coral colony sizes, and carbonate production rates tripled. Within four years, restored reefs were growing at the same speed as healthy reefs, and thereby provided the same important ecosystem functions...
Outcomes of any reef restoration project will depend on environmental conditions, natural coral larvae supply, restoration techniques and the effort invested in maintaining the project. This Indonesian project shows that when conditions are right and efforts are well placed, success is possible. Hopefully, this inspires further global efforts to restore functioning coral reefs and to recreate a climate in which they can thrive."
-via Phys.org, March 11, 2024
#coral#coral reef#marine life#marine biology#sea creatures#aquatic#environment#ecology#environmental news#environmental science#climate action#climate hope#ecosystem#conservation#endangered species#indonesia#sulawesi#good news#hope#overfishing#hopepunk#hope posting
3K notes
·
View notes
Text
Often when I post an AI-neutral or AI-positive take on an anti-AI post I get blocked, so I wanted to make my own post to share my thoughts on "Nightshade", the new adversarial data poisoning attack that the Glaze people have come out with.
I've read the paper and here are my takeaways:
Firstly, this is not necessarily or primarily a tool for artists to "coat" their images like Glaze; in fact, Nightshade works best when applied to sort of carefully selected "archetypal" images, ideally ones that were already generated using generative AI using a prompt for the generic concept to be attacked (which is what the authors did in their paper). Also, the image has to be explicitly paired with a specific text caption optimized to have the most impact, which would make it pretty annoying for individual artists to deploy.
While the intent of Nightshade is to have maximum impact with minimal data poisoning, in order to attack a large model there would have to be many thousands of samples in the training data. Obviously if you have a webpage that you created specifically to host a massive gallery poisoned images, that can be fairly easily blacklisted, so you'd have to have a lot of patience and resources in order to hide these enough so they proliferate into the training datasets of major models.
The main use case for this as suggested by the authors is to protect specific copyrights. The example they use is that of Disney specifically releasing a lot of poisoned images of Mickey Mouse to prevent people generating art of him. As a large company like Disney would be more likely to have the resources to seed Nightshade images at scale, this sounds like the most plausible large scale use case for me, even if web artists could crowdsource some sort of similar generic campaign.
Either way, the optimal use case of "large organization repeatedly using generative AI models to create images, then running through another resource heavy AI model to corrupt them, then hiding them on the open web, to protect specific concepts and copyrights" doesn't sound like the big win for freedom of expression that people are going to pretend it is. This is the case for a lot of discussion around AI and I wish people would stop flagwaving for corporate copyright protections, but whatever.
The panic about AI resource use in terms of power/water is mostly bunk (AI training is done once per large model, and in terms of industrial production processes, using a single airliner flight's worth of carbon output for an industrial model that can then be used indefinitely to do useful work seems like a small fry in comparison to all the other nonsense that humanity wastes power on). However, given that deploying this at scale would be a huge compute sink, it's ironic to see anti-AI activists for that is a talking point hyping this up so much.
In terms of actual attack effectiveness; like Glaze, this once again relies on analysis of the feature space of current public models such as Stable Diffusion. This means that effectiveness is reduced on other models with differing architectures and training sets. However, also like Glaze, it looks like the overall "world feature space" that generative models fit to is generalisable enough that this attack will work across models.
That means that if this does get deployed at scale, it could definitely fuck with a lot of current systems. That said, once again, it'd likely have a bigger effect on indie and open source generation projects than the massive corporate monoliths who are probably working to secure proprietary data sets, like I believe Adobe Firefly did. I don't like how these attacks concentrate the power up.
The generalisation of the attack doesn't mean that this can't be defended against, but it does mean that you'd likely need to invest in bespoke measures; e.g. specifically training a detector on a large dataset of Nightshade poison in order to filter them out, spending more time and labour curating your input dataset, or designing radically different architectures that don't produce a comparably similar virtual feature space. I.e. the effect of this being used at scale wouldn't eliminate "AI art", but it could potentially cause a headache for people all around and limit accessibility for hobbyists (although presumably curated datasets would trickle down eventually).
All in all a bit of a dick move that will make things harder for people in general, but I suppose that's the point, and what people who want to deploy this at scale are aiming for. I suppose with public data scraping that sort of thing is fair game I guess.
Additionally, since making my first reply I've had a look at their website:
Used responsibly, Nightshade can help deter model trainers who disregard copyrights, opt-out lists, and do-not-scrape/robots.txt directives. It does not rely on the kindness of model trainers, but instead associates a small incremental price on each piece of data scraped and trained without authorization. Nightshade's goal is not to break models, but to increase the cost of training on unlicensed data, such that licensing images from their creators becomes a viable alternative.
Once again we see that the intended impact of Nightshade is not to eliminate generative AI but to make it infeasible for models to be created and trained by without a corporate money-bag to pay licensing fees for guaranteed clean data. I generally feel that this focuses power upwards and is overall a bad move. If anything, this sort of model, where only large corporations can create and control AI tools, will do nothing to help counter the economic displacement without worker protection that is the real issue with AI systems deployment, but will exacerbate the problem of the benefits of those systems being more constrained to said large corporations.
Kinda sucks how that gets pushed through by lying to small artists about the importance of copyright law for their own small-scale works (ignoring the fact that processing derived metadata from web images is pretty damn clearly a fair use application).
1K notes
·
View notes
Text
The Swiss Cheese Model of Covid Prevention

An edited version of the swiss cheese model tailored towards the measures that you as an individual can take to minimize your risk of infection. Public health is ultimately what its name implies, public, but that doesn't mean you're powerless.
Covid prevention is not all-or-nothing. Think of it as risk reduction, rather than a binary.
Let's go through these step by step.
VACCINES
The current vaccines are meant primarily to reduce chances of severe illness, hospitalization, and death. They will reduce your chance of infection a bit--but not nearly as much as you might think. You should still get your boosters regularly, because avoiding severe illness is of course worth doing.
If you haven't gotten the updated monovalent vaccine yet, go get it. It is not a booster. Think of it as a new vaccine. It's targeted towards the XBB lineages, which are now the most common variants. Your last boosters were likely of the bivalent type, aimed at both the original Covid strain from 2020 and Omicron. The new vaccine is monovalent, meaning it targets one family in particular.
Some studies suggest that the Novavax vaccine, which is a more traditional protein-based vaccine, is more effective and safer than mRNA vaccines, and offers better protection against future variants. Of course, the data we have so far isn't 100% conclusive (the last paper I linked is a preprint). Make of these findings what you will, just something to keep in mind. The new Novavax vaccine's availability is still limited, especially outside of the US.
MASKS
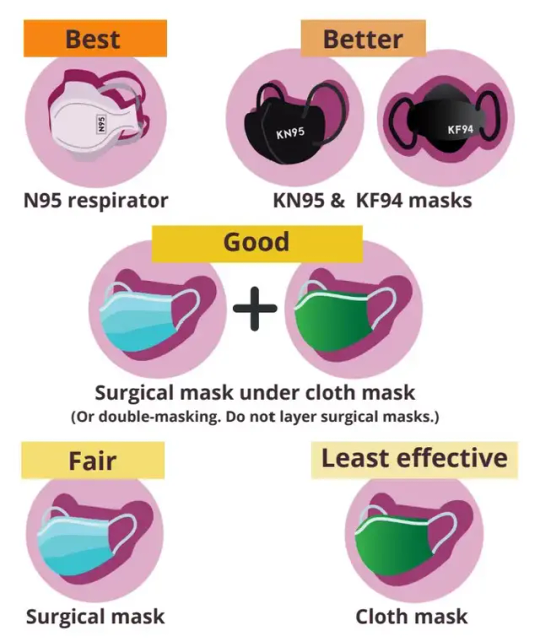
Masking is one of the most effective ways to protect yourself. While it is true that masking and reducing Covid transmission protects those around you, the idea that masks can't protect the wearer is outdated information from the early days of the pandemic when medical authorities refused to acknowledge that Covid is airborne.
The key to protecting yourself is to wear a well-fitting respirator. You want to minimize any gaps where air might leak out. If your glasses get fogged up, that's a sign that air is leaking.
Headbands will always have a tighter fit than earloop masks (and therefore provide better protection). However, you can use earloop extenders to improve the fit of earloop masks. You can find these online. Your comfort in wearing a mask is important, but there are options for compromise.
The above graphic doesn't include elastomeric respirators. While some (like the Flo Mask) are expensive, they can be much more affordable than buying disposables--look for P100 respirators at your local hardware store, but make sure it fits your face well.
For more general information, see this FAQ. For mask recommendations (NA-centric, sorry!), see my list here or Mask Nerd's YouTube channel.
For situations where you need to hydrate but don't want to take your mask off, consider the SIP valve.
Not even N95s are foolproof (N95 means it filters at least 95% of particles--with the other 5% potentially reaching you). Most people will likely not have a perfect fit. There will be situations where you'll have to take your mask off. The key is risk reduction, and that's why the Swiss cheese model is crucial.
If you can't afford high-quality masks, look for a local mask bloc or other organization that gives out free masks. Project N95 has unfortunately shut down. In Canada, there's donatemask.ca.
AVOID CROWDED INDOOR SPACES
This is rather self-explanatory. Indoor transmission is much, much, much more likely than outdoor transmission. If it's possible to move an activity outdoors instead, consider doing so.
If possible, try going to places like stores or the post office during less busy hours.
Viral particles can stay in the air for a considerable amount of time even after the person who expelled them has left. Do not take off your mask just because no one is currently present, if you know that it was previously crowded.
A CO2 monitor is a decent proxy for how many viral particles may have accumulated in the air around you. The gold standard is the Aranet4, but it's expensive, so here are some more affordable alternatives.
VENTILATION AND AIR FILTERS

Ventilation is effective for the same reason that outdoors is safer than indoors. If it's warm enough, keep windows open whenever possible. If it's cold, even cracking them open occasionally is better than nothing. Try to open windows or doors on different sides of a room to maximize airflow.
HEPA air filters can significantly reduce viral transmission indoors. Make sure to find one suitable for the room size, and replace the filters regularly. You want to look for devices with HEPA-13 filters.
You can use websites like these to calculate how long it takes for a device to change all the air in a room. Remember what I said about viral particles being able to hang around even after people have left? If an air purifier provides 2 air changes per hour, that means that after 30 minutes, any potential viral particles should be gone.
If you can't afford a commercial air filter, here's a useful DIY filter you can make with relatively simple materials. The filtration capacity is great--but due to being built with duct tape, replacing filters will be a challenge.
If you have to hold meetings or meet with people at work, having a smaller filter on the desk between you will also reduce chances of infection.
As a bonus, HEPA filters will also filter out other things like dust and allergens!
REDUCE LENGTH OF EXPOSURE IF EXPOSURE IS UNAVOIDABLE
Viral load refers to the amount of virus in a person's blood. If you've been exposed to someone with Covid, how much you've been exposed matters.
You might escape infection if the viral load you've been exposed to is very small. Or, even if you get infected, there will be less virus in you overall, leading to milder illness--and crucially, a lower chance of the virus penetrating deep into your body, creating reservoirs in your organs and wreaking long-term havoc.
A low viral load is also less contagious.
This is the same reason that wearing your mask most of the time, but having to take it off for eating, is still much better than not wearing your mask at all.
RECHARGEABLE PORTABLE AIR FILTERS
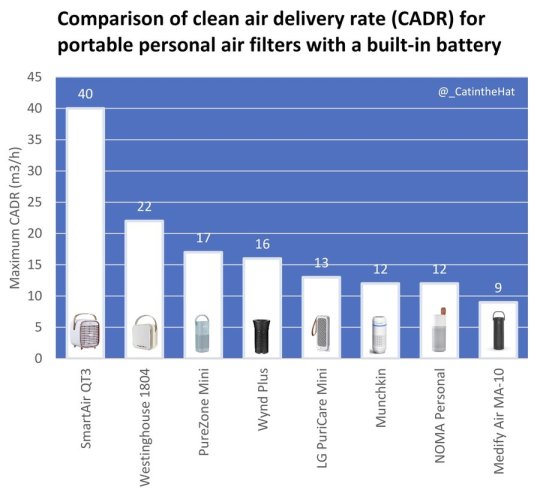
You might attract some odd looks. But if you're at high risk or just want to be as protected as possible, small portable air filters can help. Try to find models small enough to take with you on public transportation, to school, or while traveling.
These devices will be far too small to clean the air in the whole room. The goal is to have it filter air in your immediate vicinity. Be sure to angle the device so that the air is blowing in your face.
Unfortunately, rechargeable devices are much rarer and harder to find than normal air filters, and many are also expensive.
The best option at the moment, apart from DIY (which is possible, but you need to know what you're doing), seems to be the SmartAir QT3. The size and shape are a bit clunky, but it fits in a backpack. Its battery life isn't long, but it can be supplemented with a power bank.
NASAL SPRAYS
There's some research that suggests that some nasal sprays may be effective in reducing risk of infection by interfering with viruses' ability to bind to your cells.
These sprays are generally affordable, easy to find, and safe. The key ingredient is carrageenan, which is extracted from seaweed. So there are no potential risks or side effects.
Be sure to follow the instructions on the packaging carefully. Here's a video on how to properly use nasal sprays if you've never used them before.
Covixyl is another type of nasal spray that uses a different key ingredient, ethyl lauroyl arginate HCI. It also aims to disrupt viruses' ability to bind to cell walls. Unfortunately, I think it's difficult to obtain outside of the US.
CONCLUSION
None of the methods listed here are foolproof on their own. But by layering them, you can drastically reduce your chances of infection.
The most important layers, by far, are masking and air quality. But you should also stay conscientious when engaging with those layers. Don't let yourself become complacent with rules of thumb, and allow yourself to assess risk and make thought out decisions when situations arise where you might have to take off your mask or enter a high-risk indoor area, such as a hospital.
Remember that the goal is risk reduction. It's impossible to live risk-free, because we live among countless other people. But you can use knowledge and tools to keep yourself as safe as possible.
1K notes
·
View notes
Text
When Facebook came for your battery, feudal security failed

When George Hayward was working as a Facebook data-scientist, his bosses ordered him to run a “negative test,” updating Facebook Messenger to deliberately drain users’ batteries, in order to determine how power-hungry various parts of the apps were. Hayward refused, and Facebook fired him, and he sued:
https://nypost.com/2023/01/28/facebook-fires-worker-who-refused-to-do-negative-testing-awsuit/
If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
Hayward balked because he knew that among the 1.3 billion people who use Messenger, some would be placed in harm’s way if Facebook deliberately drained their batteries — physically stranded, unable to communicate with loved ones experiencing emergencies, or locked out of their identification, payment method, and all the other functions filled by mobile phones.
As Hayward told Kathianne Boniello at the New York Post, “Any data scientist worth his or her salt will know, ‘Don’t hurt people…’ I refused to do this test. It turns out if you tell your boss, ‘No, that’s illegal,’ it doesn’t go over very well.”
Negative testing is standard practice at Facebook, and Hayward was given a document called “How to run thoughtful negative tests” regarding which he said, “I have never seen a more horrible document in my career.”
We don’t know much else, because Hayward’s employment contract included a non-negotiable binding arbitration waiver, which means that he surrendered his right to seek legal redress from his former employer. Instead, his claim will be heard by an arbitrator — that is, a fake corporate judge who is paid by Facebook to decide if Facebook was wrong. Even if he finds in Hayward’s favor — something that arbitrators do far less frequently than real judges do — the judgment, and all the information that led up to it, will be confidential, meaning we won’t get to find out more:
https://pluralistic.net/2022/06/12/hot-coffee/#mcgeico
One significant element of this story is that the malicious code was inserted into Facebook’s app. Apps, we’re told, are more secure than real software. Under the “curated computing” model, you forfeit your right to decide what programs run on your devices, and the manufacturer keeps you safe. But in practice, apps are just software, only worse:
https://pluralistic.net/2022/06/23/peek-a-boo/#attack-helicopter-parenting
Apps are part what Bruce Schneier calls “feudal security.” In this model, we defend ourselves against the bandits who roam the internet by moving into a warlord’s fortress. So long as we do what the warlord tells us to do, his hired mercenaries will keep us safe from the bandits:
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
But in practice, the mercenaries aren’t all that good at their jobs. They let all kinds of badware into the fortress, like the “pig butchering” apps that snuck into the two major mobile app stores:
https://arstechnica.com/information-technology/2023/02/pig-butchering-scam-apps-sneak-into-apples-app-store-and-google-play/
It’s not merely that the app stores’ masters make mistakes — it’s that when they screw up, we have no recourse. You can’t switch to an app store that pays closer attention, or that lets you install low-level software that monitors and overrides the apps you download.
Indeed, Apple’s Developer Agreement bans apps that violate other services’ terms of service, and they’ve blocked apps like OG App that block Facebook’s surveillance and other enshittification measures, siding with Facebook against Apple device owners who assert the right to control how they interact with the company:
https://pluralistic.net/2022/12/10/e2e/#the-censors-pen
When a company insists that you must be rendered helpless as a condition of protecting you, it sets itself up for ghastly failures. Apple’s decision to prevent every one of its Chinese users from overriding its decisions led inevitably and foreseeably to the Chinese government ordering Apple to spy on those users:
https://pluralistic.net/2022/11/11/foreseeable-consequences/#airdropped
Apple isn’t shy about thwarting Facebook’s business plans, but Apple uses that power selectively — they blocked Facebook from spying on Iphone users (yay!) and Apple covertly spied on its customers in exactly the same way as Facebook, for exactly the same purpose, and lied about it:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
The ultimately, irresolvable problem of Feudal Security is that the warlord’s mercenaries will protect you against anyone — except the warlord who pays them. When Apple or Google or Facebook decides to attack its users, the company’s security experts will bend their efforts to preventing those users from defending themselves, turning the fortress into a prison:
https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model
Feudal security leaves us at the mercy of giant corporations — fallible and just as vulnerable to temptation as any of us. Both binding arbitration and feudal security assume that the benevolent dictator will always be benevolent, and never make a mistake. Time and again, these assumptions are proven to be nonsense.
Image:
Anthony Quintano (modified)
https://commons.wikimedia.org/wiki/File:Mark_Zuckerberg_F8_2018_Keynote_%2841118890174%29.jpg
CC BY 2.0:
https://creativecommons.org/licenses/by/2.0/deed.en
[Image ID: A painting depicting the Roman sacking of Jerusalem. The Roman leader's head has been replaced with Mark Zuckerberg's head. The wall has Apple's 'Think Different' wordmark and an Ios 'low battery' icon.]
Next week (Feb 8-17), I'll be in Australia, touring my book *Chokepoint Capitalism* with my co-author, Rebecca Giblin. We'll be in Brisbane on Feb 8, and then we're doing a remote event for NZ on Feb 9. Next is Melbourne, Sydney and Canberra. I hope to see you!
https://chokepointcapitalism.com/
#pluralistic#manorial security#feudal security#apple#mobile#apps#security through obscurity#binding arbitration#arbitration waivers#transparency#danegeld#surveillance lag
4K notes
·
View notes
Text
Things we won't ever do (including, but not limited to):
- Sell user data to third party advertisers.
- Sell user data to be data mined for AI.
Things we will do:
- Listen to our users and take measures against Generative AI.
- Build the best platform for our users we can with the limited funds we have.
Why? Because our community is worth it to us. We have to do what we can to try to protect our community from the alarming acceptance of Generative AI stealing from artists, authors, and creators.
Even if that means it hurts our funding (and don't get us wrong: we still really need funded to continue to exist) in the long run. We are very aware Pillowfort's existence is an uphill battle.
But you are worth fighting for.
663 notes
·
View notes