#commandline
Text
How to dot matrix ascii art.
#dot matrix#ascii art#asciiart#retro tech#retrotech#oldschool#80s#90s#vintage#vintage hardware#dotmatrix#dot matrix printer#floppy disks#floppy disk#nostaliga#retrocomputing#retrocomputer#linux#command line#commandline#terminal#linux terminal
24 notes
·
View notes
Photo

Some computer viruses can get really bad 😷 . . . #comics #puns #punstagram #punintended #programmingmemes #programmerhumor #programmerdadjokes #programmerjokes #programminglife #coder #comicstrip #comicsofinstagram #computers #commandline #computervirus #infosec #doctormemes #softwaredeveloper #softwareengineer https://www.instagram.com/p/CeJczpFuGYr/?igshid=NGJjMDIxMWI=
#comics#puns#punstagram#punintended#programmingmemes#programmerhumor#programmerdadjokes#programmerjokes#programminglife#coder#comicstrip#comicsofinstagram#computers#commandline#computervirus#infosec#doctormemes#softwaredeveloper#softwareengineer
6 notes
·
View notes
Text
Useful commands for your Mac
A living post about commandline tools for your Mac.
Episode 1: Set your hostname on zsh.
#apple #terminal #cli #zsh
Terminal is one of my favorite applications in the Mac and I’ve been getting familiar with zsh. This post is a living post where I will keep updating what I learn on the commandline.
Update hostname
What’s the hostname? The word that shows up right after your username if you open “Terminal.”
mac OS used to update the hostname when you update the Computer Name:
Settings > General > About
Or…
View On WordPress
0 notes
Text
What Kind of Tools Should I Use as a Beginner Software Developer
What Kind of Tools Should I Use as a Beginner Software Developer. Embarking on the journey as a novice in the realm of software development opens up a world filled with both excitement and challenges. The vast array of development tools available can be both thrilling and overwhelming, as each tool serves a unique purpose in the multifaceted process of building software. The significance of selecting the right set of tools cannot be overstated, as it plays a pivotal role in shaping your development experience. These tools are not mere accessories but powerful instruments that directly impact your productivity, facilitate seamless collaboration with others, and contribute to the overall quality of your code.
Read Full Content Here 👇👇
What Kind of Tools Should I Use as a Beginner Software Developer

#SoftwareDevelopment#CodingTools#IDE#VersionControl#Collaboration#CommandLine#TextEditors#DatabaseManagement#Documentation#TestingFrameworks#Containerization#ProjectManagement#ContinuousLearning#WebDevelopment#ProgrammingLanguages#automotive tools#programming tools
0 notes
Text
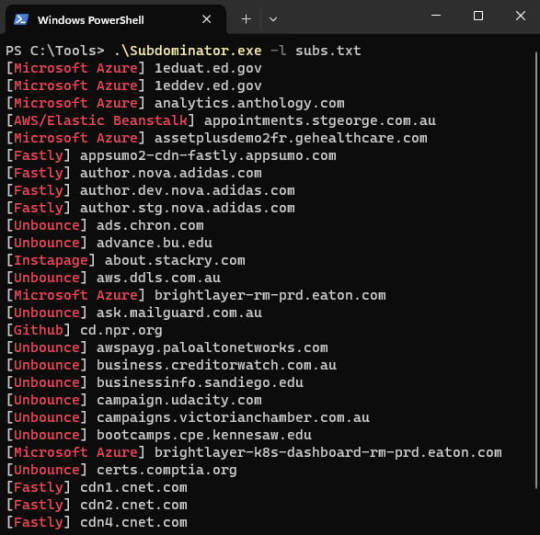
Subdominator: Open-source tool for detecting subdomain takeovers - Help Net Security
Subdominator is a dependable and fast open-source command-line interface tool to identify subdomain takeovers. It boasts superior accuracy and reliability, offering improvements compared to other tools.
“Initially, Subdominator was created internally because all the current subdomain takeover tools had gaps in their functionality. No tool had a complete set of accurate service fingerprints or…
View On WordPress
0 notes
Text
youtube
0 notes
Text
"git sweep" Alias - Delete All Local Branches Linked To Deleted Remote Branches With Just One Command!
I used to waste so much time deleting local and remote branches I was done with.
Now I just delete my remote branches (e.g. on GitHub) then run this command:
git sweep
and just like that, my local branches that track remote branches are automatically deleted!
Now let's go over how you can add this command...
What is "git sweep"?
"git sweep" is a git alias I created that is a shortcut that does the following:
Runs the "git fetch --prune" command to delete all references to remote branches.
Find local branches linked to deleted remote branches (these are marked as "gone") then deletes them.
Setting the alias
You can set it using the "git config" command or by editIng the git config file directly.
Here's the command to set the alias with the "git config" command:
git config --global alias.sweep "! git fetch -p && git for-each-ref --format '%(refname:short) %(upstream:track)' | awk '\$2 == \"[gone]\" {print \$1}' | xargs -r git branch -D"
Here's an example of what the config file should look like with the alias added:
[alias]
sweep = ! "git fetch -p && git for-each-ref --format '%(refname:short) %(upstream:track)' | awk '$2 == \"[gone]\" {print $1}' | xargs -r git branch -D"
Conclusion
Check out Erik Schierboom's article on this to learn more about how all of this works in detail.
If you found this post useful in anyway, please like, repost and/or share it.
Thanks for reading!
#programming#git#github#repository#repositories#coding#commandline#command line#linux#open source#opensource#computerscience#computer science
0 notes
Text


Nirvana in Fire | Ep 49
A remake of this gifset.
#nirvana in fire#circ gifs#remake#mei changsu#xiao jingyan#the original gifs were made purely with commandline and Preview#they weren't that bad considering
207 notes
·
View notes
Text
Trying to use ghostscript a cli tool to extract the text layer from a pdf (of a dead frenchman memoir) because I generally trust Google's OCR
ghostscript works fine, extraction works-

uh

this is art

help
this is google ocr's fault tbh
#cadmus rambles#cad rambles about dead frenchmen on main#im not good at commandline stuff and commandline text editors make me cry but it is satisfying when it works
13 notes
·
View notes
Text
bashing my head against the wall trying to figure out how 16yo lem installed a whole different operating system on a laptop that won't recognise my usb as a bootable disk
#mine#it's my dad's old notebook circa ~2002 that I stole when he jumped out the window#it runs ubuntu 14 which I'm trying to replace w puppy linux#unfortunately I'm stuck at the grub menu bc it won't recognise my pen drive#I checked on my main laptop. it boots up fine. it even shows up as a boot option on dad's notebook#but I can't find it in grub and have to use the commandline to find it#it's there but not a bootable disk#screaming and crying and throwing up#I don't understand what I'm doing wrong the bios is in legacy mode and it didn't have an option for efi/uefi to toggle#I think it's too old idk#the pen drive is old too I've had it since hs. I formatted it properly as fat32#trying to research this is giving me a headache too much of it is windows which isn't applicable#and what is ux based is going way over my head so idk what to do#I might try a different usb but I don't know where I put my other one 🙃
4 notes
·
View notes
Text
Linux Version of Qilin Ransomware Focuses on VMware ESXi
The Linux encryptor includes extensive command-line options for customization, allowing threat actors to specify exclusion and encryption criteria, as well as configure virtual machines that should not be encrypted.
View On WordPress
0 notes