#esxi
Text
Los enigmas | Jorge Luis Borges
Yo que soy el que ahora está cantando
seré mañana el misterioso, el muerto,
el morador de un mágico y desierto
orbe sin antes ni después ni cuándo.
Así afirma la mística. Me creo
indigno del Infierno o de la Gloria,
pero nada predigo. Nuestra historia
cambia como las formas de Proteo.
¿Qué errante laberinto, qué blancura
ciega de resplandor será mi suerte,
cuando me entregue el fin de esta aventura
la curiosa experiencia de la muerte?
Quiero beber su cristalino Olvido,
ser para siempre; pero no haber sido.

#escribiendo#esxi#escritos#citas#un chico que mira las estrellas#life quotes#culture#dead poetry#cosmos#letters#spilled ink#spilled thoughts#romance quotes#alternative#books libraries
32 notes
·
View notes
Text
VMware ESXi 手動更新版本
最近因為碰到 ESXi 8.0 U2 bug 的問題,要將原本的主機更新為 ESXi 8.0 U2b。本來想要重新裝一台主機再將 VM 過去,但伺服器原廠並未提供對應的 Custom ESXi 安裝包。再從VMware 的版本對應表 ( Build numbers and versions of VMware ESXi/ESX (2143832) )確認改版的 release 形式為 Patch,原則上也不會有伺服器原廠整合好的安裝包,故即便新安裝也還是要再手動進行升級。
先登入 VMware 官網後,連到下載 Patch 的頁面,下載ESXi 8.0 U2b 的 Depot 包 Zip 壓縮檔,並複製到 ESXi 主機的儲存區中:https://my.vmware.com/group/vmware/patch#search
確認 ESXi Server 有開啟 SSH 後,使用…
View On WordPress
0 notes
Text
Learned the video card I bought for my main server it too large and no way to power it.
The HP I got however has a 16x slot AND an open set of SAS power on the motherboard. $14 later and the specialize cable is in the mail.
Need to figure out how to get vSphere to manage both physical boxes.
0 notes
Text
Expert IT Services for All Your Operating System and Hosting Needs
Whether you need help installing and configuring Linux, CentOS, Windows, ESXI, or setting up RDP, Linux, CentOS VMs, ESXI, Hyper-V, VPS, or any other operating system or hosting platform, I'm here to assist you. With my extensive experience and expertise, I can handle even the most complex IT tasks seamlessly.
0 notes
Text
Backup ESXi Host configuration
Enable SSH
vim-cmd hostsvc/firmware/sync_config
vim-cmd hostsvc/firmware/backup_config
Copy and paste the download link and replace the "*" with your host IP address.
0 notes
Text
VMware vSphere: Empowering Modern Data Centers with Cutting-Edge Virtualization
Introduction
In the realm of enterprise-level virtualization, VMware vSphere stands tall as the industry leader, transforming the landscape of data centers worldwide. With its unparalleled suite of features and capabilities, vSphere has revolutionized the way businesses manage, deploy, and secure their IT infrastructures. In this blog, we will explore the power and uniqueness of VMware vSphere,…
View On WordPress
0 notes
Link
https://bit.ly/3BsE6gV - 🔒 In the first quarter of 2023, ransomware-as-a-service platforms such as Alphv, Lockbit, and Defray have been used to target VMware's ESXi, a popular virtualization and management system. ESXi does not support third-party antivirus software, making it an attractive target for adversaries. #Cybersecurity #Ransomware 🖥️ ESXi is a Type-1 hypervisor developed by VMware and is used to run and manage virtual machines (VMs). Unlike Type-2 hypervisors that run on a standard host operating system, a Type-1 hypervisor runs directly on a host's hardware. ESXi systems are often managed by vCenter, a server administration tool. #VMware #ESXi 🛡️ Despite the increasing threats to ESXi, VMware maintains that antivirus software is not required for the vSphere Hypervisor. A series of vulnerabilities have been exploited by threat actors, increasing the risk to ESXi systems. This lack of security measures is making ESXi an increasingly lucrative target for adversaries. #CyberThreats #InfoSec 🚨 The security issue is escalating. VMware products are being targeted due to their prevalence in the virtualization field and their integral role in many organizations' IT infrastructures. Threat actors are exploiting the lack of security tools, inadequate network segmentation, and in-the-wild (ITW) vulnerabilities to create a target-rich environment. #CyberCrime #DataProtection 🔑 Credential theft is a primary attack vector against ESXi hypervisors. Once credentials are stolen, adversaries can authenticate against the server to further their attack based on their objectives. If an attacker has sufficient privileges, they can execute arbitrary code directly on the latest ESXi versions. #CyberAttack #CredentialTheft 💻 Virtual machine access is another method used to target ESXi. If a VM is not adequately segregated from the rest of the network, it can act as a proxy for lateral movement through the network. If the VM is the only entry point into a network, the attacker must directly target the ESXi hypervisor to run code at the hypervisor level. #VMwareSecurity #VirtualMachine 🛠️ To mitigate these risks, VMware recommends avoiding direct access to ESXi hosts, using a hardened jump server with multi-factor authentication, ensuring vCenter is not exposed to the internet, backing up ESXi datastore volumes regularly, and physically disconnecting the storage or cutting power to the ESXi host if encryption is suspected. #CyberDefense #CyberHygiene 🔮 It's anticipated that adversaries will continue to target VMware-based virtualization infrastructure due to the increasing adoption of virtualization technology, VMware’s dominance in the field, and the routine targeting of virtualization products. Regularly applying security updates and conducting security posture reviews are crucial measures for organizations to adopt.
#Cybersecurity#Ransomware#VMware#ESXi#CyberThreats#InfoSec#CyberCrime#DataProtection#CyberAttack#CredentialTheft#VMwareSecurity#VirtualMachine#CyberDefense#CyberHygiene#CyberSecurityTrends#ITSecurity
0 notes
Text
Babuk ransomware source code sparks 9 different strains targeting VMware ESXi systems
Embedded YouTube Video
Several threat actors have capitalized on the leak of ransomware source code from a company called Babuk in September 2021 to build as many as nine different ransomware families capable of infecting VMware ESXi systems. These variants emerged through 2022 and 2023, which shows an increasing trend in Babuk source code adoption. The leaked source code enables actors to…
View On WordPress
0 notes
Link
This week's issue contains some of the most interesting articles and news, selected from all the content published in the previous week on the Developers News website. You will read about Go 1.20, Polymer's Web Component, Proxmox vs. ESXi, TensorFlow, Programming Fonts, Java 19, Linux 6.1, Flutter BLOC, Containerization vs. Virtualization, and more
0 notes
Text
Campagne d’exploitation d’une vulnérabilité affectant VMware ESXi
Risque(s)
Exécution de code arbitraire à distance
Résumé
Le 03 février 2023, une campagne d’attaques ciblant les hyperviseurs VMware ESXi dans le but d’y déployer un rançongiciel a été découverte.
Dans l’état actuel des investigations, ces campagnes d’attaque semblent exploiter la vulnérabilité CVE-2021-21974, pour laquelle un correctif est disponible depuis le 23 février 2021. Cette…

View On WordPress
0 notes
Text
ESXi - 自動化重置 VM 虛擬機器
在 VM 的應用上,有時候需要定期將 VM 環境到特定的狀態,如設定還原、連線數量清零 … 等等的維護。下面為透過 crontab 自動還原 VM 狀態並啟動的做法。
使用軟體:ESXi管理工具 (ex: VMware Host Client, VMware Workstation, … )、SSH Client (ex: putty)
Automatic Reset ESXi VM State (Snapshot)
1. 確保 ESXi 的 SSH 服務已啟用
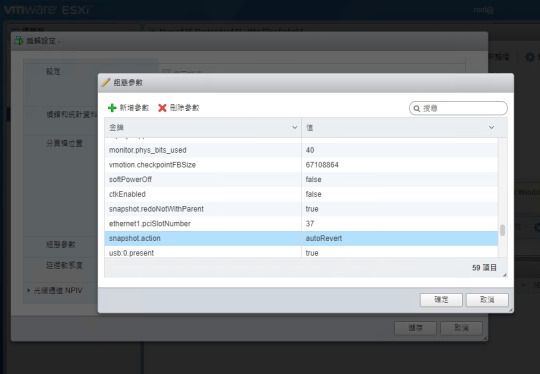
2. 設定 VM 重啟後自動還原到最後一個快照 snapshots。這裡可以透過 VMware Workstation 設定 VM 選項裡的快照設定,或是透過VMware Host Client 在 VM 編輯設定的組態參數中,直接新增參數:anapshot.action : autoRevert
3. 使用…
View On WordPress
0 notes
Text
New Python malware backdoors VMware ESXi servers for remote access
New Python malware backdoors VMware ESXi servers for remote access
A previously undocumented Python backdoor targeting VMware ESXi servers has been spotted, enabling hackers to execute commands remotely on a compromised system.
(more…)

View On WordPress
1 note
·
View note
Text
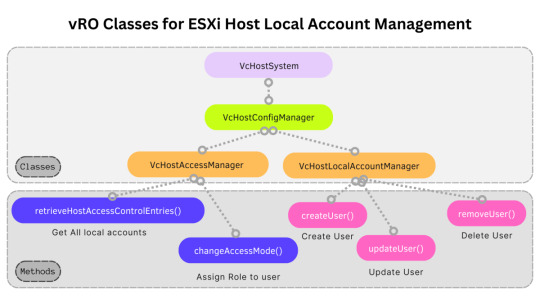
Create ESXi root account with vRO [CB10104]
Create ESXi root account with vRO [CB10104]
TL;DR If you would like to create ESXi local account using vRO, download this package (in.co.cloudblogger.crudEsxiLocalUser.package) to get started.
IntroductionClasses & MethodsScript for creating a local admin account in ESXiDemo VideovRO Package for CRUD operation
Introduction
Many organization uses vRO for Host Provisioning. Various hardware vendors provide vRO Scripting APIs via plugins…
View On WordPress
0 notes
Text
VMware Patches VM Escape Flaw Exploited at Geekpwn Event
VMware Patches VM Escape Flaw Exploited at Geekpwn Event
Home › Cyberwarfare
VMware Patches VM Escape Flaw Exploited at Geekpwn Event
By Ryan Naraine on December 13, 2022
Tweet
Virtualization technology giant VMware on Tuesday shipped urgent updates to fix a trio of security problems in multiple software products, including a virtual machine escape bug exploited at the GeekPwn 2022 hacking challenge.
The VM escape flaw, documented as CVE-2022-31705,…
View On WordPress
#code execution#CVE-2021-22005#CVE-2022-31705#cvss#ESXi#geekpwn#high-risk#keen team#patches#Tencent#updates#vcenter server#virtualization#vmware#vmx sandbox#vulnerability
0 notes
Text
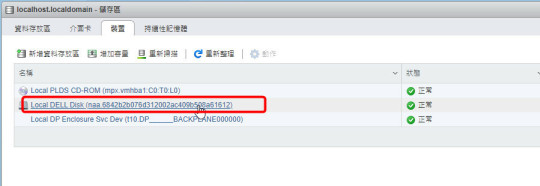
【數位3C】使用esxcfg-volume解決VMware ESXi資料存放區消失無法存取的問題
最近發生奇怪的狀況
就是一台Dell R610 ESXi 6.7 u2的主機
內部存放空間突然無法使用
這樣就造成放在上面的VM都無法正常運行
本來想說重開後就解決
不過重開機後發現問題依舊
期間還曾使用RAID管理介面還曾經重建RAID
重建後因為裝置內的名稱顯示還是正常地, 所以後來嘗試將他卸載後想說重新加回來
但從此就完全抓不到內容了
使用ssh連入看檔案格式似乎是還在的
但volumes卻是沒有顯示出來
透過介面嘗試修復
或是esxcli指令去掛載都無法顯示原本的內容
最後找到一個指令esxcfg-volume嘗試恢復vmfs的快照
esxcli storage vmfs snapshot list
連結指定的VMFS UUID
esxcfg-volume -M…
View On WordPress
0 notes