#offers cybersecurity services
Text
Cybersecurity News

In this dynamic space, we dive deep into the ever-evolving landscape of cybersecurity. From breaking news on the latest threats to insightful analyses of security breaches, this category is a goldmine of information for tech enthusiasts, IT professionals, and anyone keen on staying one step ahead in the digital age.
0 notes
Text
#msp#telehealth technology and services in usa#patient 360 solutions and tele technology in usa#healthcare cybersecurity risk management technology#telehealth services#technology#healthcare it support service offerings#digital transformation in healthcare it consulting#healthcare it infrastructure management#it infrastructure managed services
1 note
·
View note
Text
Gig apps trap reverse centaurs in Skinner boxes
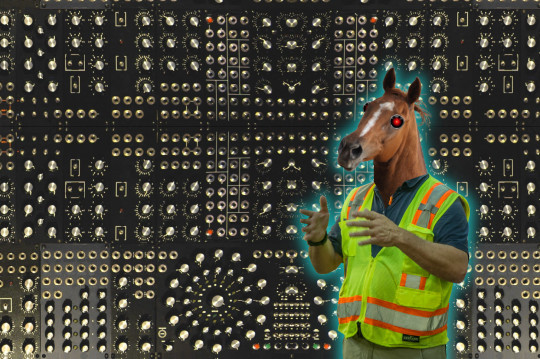
Enshittification is the process by which digital platforms devour themselves: first they dangle goodies in front of end users. Once users are locked in, the goodies are taken away and dangled before business customers who supply goods to the users. Once those business customers are stuck on the platform, the goodies are clawed away and showered on the platform’s shareholders:
https://pluralistic.net/2023/01/21/potemkin-ai/#hey-guys
If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/04/12/algorithmic-wage-discrimination/#fishers-of-men
Enshittification isn’t just another way of saying “fraud” or “price gouging” or “wage theft.” Enshittification is intrinsically digital, because moving all those goodies around requires the flexibility that only comes with a digital businesses. Jeff Bezos, grocer, can’t rapidly change the price of eggs at Whole Foods without an army of kids with pricing guns on roller-skates. Jeff Bezos, grocer, can change the price of eggs on Amazon Fresh just by twiddling a knob on the service’s back-end.
Twiddling is the key to enshittification: rapidly adjusting prices, conditions and offers. As with any shell game, the quickness of the hand deceives the eye. Tech monopolists aren’t smarter than the Gilded Age sociopaths who monopolized rail or coal — they use the same tricks as those monsters of history, but they do them faster and with computers:
https://doctorow.medium.com/twiddler-1b5c9690cce6
If Rockefeller wanted to crush a freight company, he couldn’t just click a mouse and lay down a pipeline that ran on the same route, and then click another mouse to make it go away when he was done. When Bezos wants to bankrupt Diapers.com — a company that refused to sell itself to Amazon — he just moved a slider so that diapers on Amazon were being sold below cost. Amazon lost $100m over three months, diapers.com went bankrupt, and every investor learned that competing with Amazon was a losing bet:
https://slate.com/technology/2013/10/amazon-book-how-jeff-bezos-went-thermonuclear-on-diapers-com.html
That’s the power of twiddling — but twiddling cuts both ways. The same flexibility that digital businesses enjoy is hypothetically available to workers and users. The airlines pioneered twiddling ticket prices, and that naturally gave rise to countertwiddling, in the form of comparison shopping sites that scraped the airlines’ sites to predict when tickets would be cheapest:
https://pluralistic.net/2023/02/27/knob-jockeys/#bros-be-twiddlin
The airlines — like all abusive businesses — refused to tolerate this. They were allowed to touch their knobs as much as they wanted — indeed, they couldn’t stop touching those knobs — but when we tried to twiddle back, that was “felony contempt of business model,” and the airlines sued:
https://www.cnbc.com/2014/12/30/airline-sues-man-for-founding-a-cheap-flights-website.html
And sued:
https://www.nytimes.com/2018/01/06/business/southwest-airlines-lawsuit-prices.html
Platforms don’t just hate it when end-users twiddle back — if anything they are even more aggressive when their business-users dare to twiddle. Take Para, an app that Doordash drivers used to get a peek at the wages offered for jobs before they accepted them — something that Doordash hid from its workers. Doordash ruthlessly attacked Para, saying that by letting drivers know how much they’d earn before they did the work, Para was violating the law:
https://www.eff.org/deeplinks/2021/08/tech-rights-are-workers-rights-doordash-edition
Which law? Well, take your pick. The modern meaning of “IP” is “any law that lets me use the law to control my competitors, competition or customers.” Platforms use a mix of anticircumvention law, patent, copyright, contract, cybersecurity and other legal systems to weave together a thicket of rules that allow them to shut down rivals for their Felony Contempt of Business Model:
https://locusmag.com/2020/09/cory-doctorow-ip/
Enshittification relies on unlimited twiddling (by platforms), and a general prohibition on countertwiddling (by platform users). Enshittification is a form of fishing, in which bait is dangled before different groups of users and then nimbly withdrawn when they lunge for it. Twiddling puts the suppleness into the enshittifier’s fishing-rod, and a ban on countertwiddling weighs down platform users so they’re always a bit too slow to catch the bait.
Nowhere do we see twiddling’s impact more than in the “gig economy,” where workers are misclassified as independent contractors and put to work for an app that scripts their every move to the finest degree. When an app is your boss, you work for an employer who docks your pay for violating rules that you aren’t allowed to know — and where your attempts to learn those rules are constantly frustrated by the endless back-end twiddling that changes the rules faster than you can learn them.
As with every question of technology, the issue isn’t twiddling per se — it’s who does the twiddling and who gets twiddled. A worker armed with digital tools can play gig work employers off each other and force them to bid up the price of their labor; they can form co-ops with other workers that auto-refuse jobs that don’t pay enough, and use digital tools to organize to shift power from bosses to workers:
https://pluralistic.net/2022/12/02/not-what-it-does/#who-it-does-it-to
Take “reverse centaurs.” In AI research, a “centaur” is a human assisted by a machine that does more than either could do on their own. For example, a chess master and a chess program can play a better game together than either could play separately. A reverse centaur is a machine assisted by a human, where the machine is in charge and the human is a meat-puppet.
Think of Amazon warehouse workers wearing haptic location-aware wristbands that buzz at them continuously dictating where their hands must be; or Amazon drivers whose eye-movements are continuously tracked in order to penalize drivers who look in the “wrong” direction:
https://pluralistic.net/2021/02/17/reverse-centaur/#reverse-centaur
The difference between a centaur and a reverse centaur is the difference between a machine that makes your life better and a machine that makes your life worse so that your boss gets richer. Reverse centaurism is the 21st Century’s answer to Taylorism, the pseudoscience that saw white-coated “experts” subject workers to humiliating choreography down to the smallest movement of your fingertip:
https://pluralistic.net/2022/08/21/great-taylors-ghost/#solidarity-or-bust
While reverse centaurism was born in warehouses and other company-owned facilities, gig work let it make the leap into workers’ homes and cars. The 21st century has seen a return to the cottage industry — a form of production that once saw workers labor far from their bosses and thus beyond their control — but shriven of the autonomy and dignity that working from home once afforded:
https://doctorow.medium.com/gig-work-is-the-opposite-of-steampunk-463e2730ef0d
The rise and rise of bossware — which allows for remote surveillance of workers in their homes and cars — has turned “work from home” into “live at work.” Reverse centaurs can now be chickenized — a term from labor economics that describes how poultry farmers, who sell their birds to one of three vast poultry processors who have divided up the country like the Pope dividing up the “New World,” are uniquely exploited:
https://onezero.medium.com/revenge-of-the-chickenized-reverse-centaurs-b2e8d5cda826
A chickenized reverse centaur has it rough: they must pay for the machines they use to make money for their bosses, they must obey the orders of the app that controls their work, and they are denied any of the protections that a traditional worker might enjoy, even as they are prohibited from deploying digital self-help measures that let them twiddle back to bargain for a better wage.
All of this sets the stage for a phenomenon called algorithmic wage discrimination, in which two workers doing the same job under the same conditions will see radically different payouts for that work. These payouts are continuously tweaked in the background by an algorithm that tries to predict the minimum sum a worker will accept to remain available without payment, to ensure sufficient workers to pick up jobs as they arise.
This phenomenon — and proposed policy and labor solutions to it — is expertly analyzed in “On Algorithmic Wage Discrimination,” a superb paper by UC Law San Franciscos Veena Dubal:
https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4331080
Dubal uses empirical data and enthnographic accounts from Uber drivers and other gig workers to explain how endless, self-directed twiddling allows gig companies pay workers less and pay themselves more. As @[email protected] explains in his LA Times article on Dubal’s research, the goal of the payment algorithm is to guess how often a given driver needs to receive fair compensation in order to keep them driving when the payments are unfair:
https://www.latimes.com/business/technology/story/2023-04-11/algorithmic-wage-discrimination
The algorithm combines nonconsensual dossiers compiled on individual drivers with population-scale data to seek an equilibrium between keeping drivers waiting, unpaid, for a job; and how much a driver needs to be paid for an individual job, in order to keep that driver from clocking out and doing something else.
@
Here’s how that works. Sergio Avedian, a writer for The Rideshare Guy, ran an experiment with two brothers who both drove for Uber; one drove a Tesla and drove intermittently, the other brother rented a hybrid sedan and drove frequently. Sitting side-by-side with the brothers, Avedian showed how the brother with the Tesla was offered more for every trip:
https://www.youtube.com/watch?v=UADTiL3S67I
Uber wants to lure intermittent drivers into becoming frequent drivers. Uber doesn’t pay for an oversupply of drivers, because it only pays drivers when they have a passenger in the car. Having drivers on call — but idle — is a way for Uber to shift the cost of maintaining a capacity cushion to its workers.
What’s more, what Uber charges customers is not based on how much it pays its workers. As Uber’s head of product explained: Uber uses “machine-learning techniques to estimate how much groups of customers are willing to shell out for a ride. Uber calculates riders’ propensity for paying a higher price for a particular route at a certain time of day. For instance, someone traveling from a wealthy neighborhood to another tony spot might be asked to pay more than another person heading to a poorer part of town, even if demand, traffic and distance are the same.”
https://qz.com/990131/uber-is-practicing-price-discrimination-economists-say-that-might-not-be-a-bad-thing/
Uber has historically described its business a pure supply-and-demand matching system, where a rush of demand for rides triggers surge pricing, which lures out drivers, which takes care of the demand. That’s not how it works today, and it’s unclear if it ever worked that way. Today, a driver who consults the rider version of the Uber app before accepting a job — to compare how much the rider is paying to how much they stand to earn — is booted off the app and denied further journeys.
Surging, instead, has become just another way to twiddle drivers. One of Dubal’s subjects, Derrick, describes how Uber uses fake surges to lure drivers to airports: “You go to the airport, once the lot get kind of full, then the surge go away.” Other drivers describe how they use groupchats to call out fake surges: “I’m in the Marina. It’s dead. Fake surge.”
That’s pure twiddling. Twiddling turns gamification into gamblification, where your labor buys you a spin on a roulette wheel in a rigged casino. As a driver called Melissa, who had doubled down on her availability to earn a $100 bonus awarded for clocking a certain number of rides, told Dubal, “When you get close to the bonus, the rides start trickling in more slowly…. And it makes sense. It’s really the type of
shit that they can do when it’s okay to have a surplus labor force that is just sitting there that they don’t have to pay for.”
Wherever you find reverse-centaurs, you get this kind of gamblification, where the rules are twiddled continuously to make sure that the house always wins. As a contract driver Amazon reverse centaur told Lauren Gurley for Motherboard, “Amazon uses these cameras allegedly to make sure they have a safer driving workforce, but they’re actually using them not to pay delivery companies”:
https://www.vice.com/en/article/88npjv/amazons-ai-cameras-are-punishing-drivers-for-mistakes-they-didnt-make
Algorithmic wage discrimination is the robot overlord of our nightmares: its job is to relentlessly quest for vulnerabilities and exploit them. Drivers divide themselves into “ants” (drivers who take every job) and “pickers” (drivers who cherry-pick high-paying jobs). The algorithm’s job is ensuring that pickers get the plum assignments, not the ants, in the hopes of converting those pickers to app-dependent ants.
In my work on enshittification, I call this the “giant teddy bear” gambit. At every county fair, you’ll always spot some poor jerk carrying around a giant teddy-bear they “won” on the midway. But they didn’t win it — not by getting three balls in the peach-basket. Rather, the carny running the rigged game either chose not to operate the “scissor” that kicks balls out of the basket. Or, if the game is “honest” (that is, merely impossible to win, rather than gimmicked), the operator will make a too-good-to-refuse offer: “Get one ball in and I’ll give you this keychain. Win two keychains and I’ll let you trade them for this giant teddy bear.”
Carnies aren’t in the business of giving away giant teddy bears — rather, the gambit is an investment. Giving a mark a giant teddy bear to carry around the midway all day acts as a convincer, luring other marks to try to land three balls in the basket and win their own teddy bear.
In the same way, platforms like Uber distribute giant teddy bears to pickers, as a way of keeping the ants scurrying from job to job, and as a way of convincing the pickers to give up whatever work allows them to discriminate among Uber’s offers and hold out for the plum deals, whereupon then can be transmogrified into ants themselves.
Dubal describes the experience of Adil, a Syrian refugee who drives for Uber in the Bay Area. His colleagues are pickers, and showed him screenshots of how much they earned. Determined to get a share of that money, Adil became a model ant, driving two hours to San Francisco, driving three days straight, napping in his car, spending only one day per week with his family. The algorithm noticed that Adil needed the work, so it paid him less.
Adil responded the way the system predicted he would, by driving even more: “My friends they make it, so I keep going, maybe I can figure
it out. It’s unsecure, and I don’t know how people they do it. I don’t know how I am doing it, but I have to. I mean, I don’t
find another option. In a minute, if I find something else, oh man, I will be out immediately. I am a very patient person, that’s why I can continue.”
Another driver, Diego, told Dubal about how the winners of the giant teddy bears fell into the trap of thinking that they were “good at the app”: “Any time there’s some big shot getting high pay outs, they always shame everyone else and say you don’t know how to use the app. I think there’s secret PR campaigns going on that gives targeted payouts to select workers, and they just think it’s all them.”
That’s the power of twiddling: by hoarding all the flexibility offered by digital tools, the management at platforms can become centaurs, able to string along thousands of workers, while the workers are reverse-centaurs, puppeteered by the apps.
As the example of Adil shows, the algorithm doesn’t need to be very sophisticated in order to figure out which workers it can underpay. The system automates the kind of racial and gender discrimination that is formally illegal, but which is masked by the smokescreen of digitization. An employer who systematically paid women less than men, or Black people less than white people, would be liable to criminal and civil sanctions. But if an algorithm simply notices that people who have fewer job prospects drive more and will thus accept lower wages, that’s just “optimization,” not racism or sexism.
This is the key to understanding the AI hype bubble: when ghouls from multinational banks predict 13 trillion dollar markets for “AI,” what they mean is that digital tools will speed up the twiddling and other wage-suppression techniques to transfer $13T in value from workers and consumers to shareholders.
The American business lobby is relentlessly focused on the goal of reducing wages. That’s the force behind “free trade,” “right to work,” and other codewords for “paying workers less,” including “gig work.” Tech workers long saw themselves as above this fray, immune to labor exploitation because they worked for a noble profession that took care of its own.
But the epidemic of mass tech-worker layoffs, following on the heels of massive stock buybacks, has demonstrated that tech bosses are just like any other boss: willing to pay as little as they can get away with, and no more. Tech bosses are so comfortable with their market dominance and the lock-in of their customers that they are happy to turn out hundreds of thousands of skilled workers, convinced that the twiddling systems they’ve built are the kinds of self-licking ice-cream cones that are so simple even a manager can use them — no morlocks required.
The tech worker layoffs are best understood as an all-out war on tech worker morale, because that morale is the source of tech workers’ confidence and thus their demands for a larger share of the value generated by their labor. The current tech layoff template is very different from previous tech layoffs: today’s layoffs are taking place over a period of months, long after they are announced, and laid off tech worker is likely to be offered a months of paid post-layoff work, rather than severance. This means that tech workplaces are now haunted by the walking dead, workers who have been laid off but need to come into the office for months, even as the threat of layoffs looms over the heads of the workers who remain. As an old friend, recently laid off from Microsoft after decades of service, wrote to me, this is “a new arrow in the quiver of bringing tech workers to heel and ensuring that we’re properly thankful for the jobs we have (had?).”
Dubal is interested in more than analysis, she’s interested in action. She looks at the tactics already deployed by gig workers, who have not taken all this abuse lying down. Workers in the UK and EU organized through Worker Info Exchange and the App Drivers and Couriers Union have used the GDPR (the EU’s privacy law) to demand “algorithmic transparency,” as well as access to their data. In California, drivers hope to use similar provisions in the CCPA (a state privacy law) to do the same.
These efforts have borne fruit. When Cornell economists, led by Louis Hyman, published research (paid for by Uber) claiming that Uber drivers earned an average of $23/hour, it was data from these efforts that revealed the true average Uber driver’s wage was $9.74. Subsequent research in California found that Uber drivers’ wage fell to $6.22/hour after the passage of Prop 22, a worker misclassification law that gig companies spent $225m to pass, only to have the law struck down because of a careless drafting error:
https://www.latimes.com/california/newsletter/2021-08-23/proposition-22-lyft-uber-decision-essential-california
But Dubal is skeptical that data-coops and transparency will achieve transformative change and build real worker power. Knowing how the algorithm works is useful, but it doesn’t mean you can do anything about it, not least because the platform owners can keep touching their knobs, twiddling the payout schedule on their rigged slot-machines.
Data co-ops start from the proposition that “data extraction is an inevitable form of labor for which workers should be remunerated.” It makes on-the-job surveillance acceptable, provided that workers are compensated for the spying. But co-ops aren’t unions, and they don’t have the power to bargain for a fair price for that data, and coops themselves lack the vast resources — “to store, clean, and understand” — data.
Co-ops are also badly situated to understand the true value of the data that is extracted from their members: “Workers cannot know whether the data collected will, at the population level, violate the civil rights of others or amplifies their own social oppression.”
Instead, Dubal wants an outright, nonwaivable prohibition on algorithmic wage discrimination. Just make it illegal. If
firms cannot use gambling mechanisms to control worker behavior through variable pay systems, they will have to find ways to maintain flexible
workforces while paying their workforce predictable wages under an employment model. If a firm cannot manage wages through digitally-determined variable pay systems, then the firm is less likely to employ algorithmic management.”
In other words, rather than using market mechanisms too constrain platform twiddling, Dubal just wants to make certain kinds of twiddling illegal. This is a growing trend in legal scholarship. For example, the economist Ramsi Woodcock has proposed a ban on surge pricing as a per se violation of Section 1 of the Sherman Act:
https://ilr.law.uiowa.edu/print/volume-105-issue-4/the-efficient-queue-and-the-case-against-dynamic-pricing
Similarly, Dubal proposes that algorithmic wage discrimination violates another antitrust law: the Robinson-Patman Act, which “bans sellers from charging competing buyers different prices for the same commodity. Robinson-Patman enforcement was effectively halted under Reagan, kicking off a host of pathologies, like the rise of Walmart:
https://pluralistic.net/2023/03/27/walmarts-jackals/#cheater-sizes
I really liked Dubal’s legal reasoning and argument, and to it I would add a call to reinvigorate countertwiddling: reforming laws that get in the way of workers who want to reverse-engineer, spoof, and control the apps that currently control them. Adversarial interoperability (AKA competitive compatibility or comcom) is key tool for building worker power in an era of digital Taylorism:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
To see how that works, look to other jursidictions where workers have leapfrogged their European and American cousins, such as Indonesia, where gig workers and toolsmiths collaborate to make a whole suite of “tuyul apps,” which let them override the apps that gig companies expect them to use.
https://pluralistic.net/2021/07/08/tuyul-apps/#gojek
For example, ride-hailing companies won’t assign a train-station pickup to a driver unless they’re circling the station — which is incredibly dangerous during the congested moments after a train arrives. A tuyul app lets a driver park nearby and then spoof their phone’s GPS fix to the ridehailing company so that they appear to be right out front of the station.
In an ideal world, those workers would have a union, and be able to dictate the app’s functionality to their bosses. But workers shouldn’t have to wait for an ideal world: they don’t just need jam tomorrow — they need jam today. Tuyul apps, and apps like Para, which allow workers to extract more money under better working conditions, are a prelude to unionization and employer regulation, not a substitute for it.
Employers will not give workers one iota more power than they have to. Just look at the asymmetry between the regulation of union employees versus union busters. Under US law, employees of a union need to account for every single hour they work, every mile they drive, every location they visit, in public filings. Meanwhile, the union-busting industry — far larger and richer than unions — operate under a cloak of total secrecy, Workers aren’t even told which union busters their employers have hired — let alone get an accounting of how those union busters spend money, or how many of them are working undercover, pretending to be workers in order to sabotage the union.
Twiddling will only get an employer so far. Twiddling — like all “AI” — is based on analyzing the past to predict the future. The heuristics an algorithm creates to lure workers into their cars can’t account for rapid changes in the wider world, which is why companies who relied on “AI” scheduling apps (for example, to prevent their employees from logging enough hours to be entitled to benefits) were caught flatfooted by the Great Resignation.
Workers suddenly found themselves with bargaining power thanks to the departure of millions of workers — a mix of early retirees and workers who were killed or permanently disabled by covid — and they used that shortage to demand a larger share of the fruits of their labor. The outraged howls of the capital class at this development were telling: these companies are operated by the kinds of “capitalists” that MLK once identified, who want “socialism for the rich and rugged individualism for the poor.”
https://twitter.com/KaseyKlimes/status/821836823022354432/
There's only 5 days left in the Kickstarter campaign for the audiobook of my next novel, a post-cyberpunk anti-finance finance thriller about Silicon Valley scams called Red Team Blues. Amazon's Audible refuses to carry my audiobooks because they're DRM free, but crowdfunding makes them possible.

Image:
Stephen Drake (modified)
https://commons.wikimedia.org/wiki/File:Analog_Test_Array_modular_synth_by_sduck409.jpg
CC BY 2.0
https://creativecommons.org/licenses/by/2.0/deed.en
—
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
—
Louis (modified)
https://commons.wikimedia.org/wiki/File:Chestnut_horse_head,_all_excited.jpg
CC BY-SA 2.0
https://creativecommons.org/licenses/by-sa/2.0/deed.en
[Image ID: A complex mandala of knobs from a modular synth. In the foreground, limned in a blue electric halo, is a man in a hi-viz vest with the head of a horse. The horse's eyes have been replaced with the sinister red eyes of HAL9000 from Kubrick's '2001: A Space Odyssey.'"]
#pluralistic#great resignation#twiddler#countertwiddling#wage discrimination#algorithmic#scholarship#doordash#para#Veena Dubal#labor#brian merchant#app boss#reverse centaurs#skinner boxes#enshittification#ants vs pickers#tuyul#steampunk#cottage industry#ccpa#gdpr#App Drivers and Couriers Union#shitty technology adoption curve#moral economy#gamblification#casinoization#taylorization#taylorism#giant teddy bears
3K notes
·
View notes
Text
Search Parameters:
Part Time
Remote, Any Location
Entry Level
No Experience Required
Search Results:
MORTGAGE LOAN ORIGINATOR - 5 years experience required
REMOTE CSR-HVAC/Plumbing Service MUST BE INTIMATELY FAMILIAR WITH EVERY HVAC SYSTEM BUILT IN THE LAST FIFTY YEARS
The Actual Perfect Job - Location: Bumfuck Nowhere, 350 miles away (Required)
Customer Service Rep - In-Office, Full Time, 9 dollars an hour
LICENSED REAL ESTATE AGENT (MUST HAVE A DOUBLE MAJOR IN BUSINESS ADMINISTRATION AND CYBERSECURITY)
Roadie for my Band - "My last guy died of chirrosis, RIP Brad Jones aka Remote."
Email Inbox:
Sender: Canadian Government
Subject: Special Limited Time Offer!
Body: We know you're American, but we noticed through highly unethical but still very legal data scraping technologies that things are pretty bleak for you! Have you considered killing yourself?
228 notes
·
View notes
Text
Your Planet and Careers (Vedic Astrology)💼

The 10th house in Vedic Astrology is known as the Karma Bhava. This celestial abode holds the key to one's career, profession, reputation, and public image. Now let's uncover the profound impact that planets residing in the 10th house can have on an individual's career path and their potential for success in the professional realm.
Sun (Surya)
When the Sun graces the 10th house, it signifies qualities of leadership, ambition, and a strong drive for success. Those with this placement may find success in government roles, politics, administration, management, or any field that demands authority and visibility.
Moon (Chandra)
The Moon in the 10th house suggests a career in nurturing, caregiving, or public service. Individuals with this placement may excel in professions like nursing, social work, psychology, or any occupation involving interaction with the public.
Mars (Mangala)
Mars in the 10th house indicates a competitive and determined nature, making individuals suitable for careers in sports, military, law enforcement, engineering, or entrepreneurship. They may thrive in dynamic environments that require quick action and initiative.
Mercury (Budha)
Individuals with Mercury in the 10th house possess strong communication skills, analytical abilities, and a flair for intellectual pursuits. This placement can lead to success in fields such as writing, journalism, teaching, public speaking, or any profession that involves critical thinking and problem-solving.
Jupiter (Guru)
Jupiter's presence in the 10th house is considered auspicious for career growth and success. Those with this placement may excel in areas like education, law, finance, spirituality, or advisory roles. They may also find success in positions of authority and leadership
Venus (Shukra)
Those with Venus in the 10th house may find themselves drawn to careers in the arts, fashion, or beauty industries. They could excel in fields like modeling, music, or event planning, showcasing their creativity and aesthetic sense.
Saturn (Shani)
Saturn in the 10th house signifies a strong work ethic and a disciplined approach to career goals. Individuals with this placement may thrive in professions that demand patience and long-term planning, such as engineering, government roles, or business management.
Rahu or Ketu (North Node / South Node)
When Rahu or Ketu are positioned in the 10th house, individuals may face unexpected twists and turns in their professional journey. They might need to navigate through unconventional career paths and industries, adapting to challenges and changes along the way.
it can bring a sense of unpredictability and sudden changes in one's career path. Individuals with this placement may have unconventional career choices and may find themselves drawn to unique or innovative fields. Rahu in the 10th house can indicate a strong desire for recognition, fame, and success, leading individuals towards careers in media, entertainment, technology, or research. However, it can also bring challenges related to deception, illusion, and unexpected twists in one's professional life.
You may find success in careers that involve innovation, technology, and creativity. Suitable career paths may include:
Technology: Fields such as IT, software development, cybersecurity, and digital marketing where creativity and innovation are valued.
Media and Entertainment: Careers in film, television, advertising, social media, or content creation that require a flair for creativity and a desire for recognition.
Entrepreneurship: Starting a business in a cutting-edge industry or launching a startup that offers innovative solutions to existing problems.
Research and Exploration: Pursuing a career in scientific research, space exploration, or cutting-edge technologies that push the boundaries of knowledge.
Occult Sciences: Delving into astrology, metaphysics, or other mystical practices that tap into hidden knowledge and unconventional wisdom.
Ketu [South Node]
Spiritual Guidance: Becoming a spiritual leader, counselor, or teacher who helps others on their spiritual journey and inner growth.
Alternative Healing: Practicing holistic therapies, energy healing, or alternative medicine to promote physical, emotional, and spiritual well-being.
Meditation and Yoga: Teaching meditation, yoga, mindfulness practices, or leading retreats that focus on inner peace and self-discovery.
Charity and Nonprofit Work: Engaging in humanitarian efforts, social work, or volunteering for causes that align with one's values and principles.
Psychology and Counseling: Pursuing a career in psychology, therapy, or counseling to support individuals in their emotional healing and personal growth.
Overall, the placement of Rahu or Ketu in the 10th house can bring both opportunities and challenges in one's career journey. By embracing the unique qualities and lessons associated with these lunar nodes, individuals can navigate their professional paths with resilience, adaptability, and a willingness to explore uncharted territories in pursuit of their true calling.
Remember This is a General Analysis , Whole Chart is to be consider for Accurate Personalized Predictions.
For Paid Personalized Analysis & Reviews ➤ Check Here
Masterlist ➤ Check Here
#vedic astrology#career#jobs#astrology#astro notes#astro observations#astro community#astroworld#astroloji#astroblr#10th house
117 notes
·
View notes
Text
Introduction to Armchair Activism
Current feelings about the state of radblr.
Fundamentals
"Yes, Everyone on the Internet Is a Loser." Luke Smith. Sep 3, 2022. YouTube.
An activist movement can be a place to build community with like-minded people, but action is its foremost purpose, not community. To allow yourself and other activists to remain effective, you are obliged to abandon your personal dislikes of other individual activists. Disagreements are worth discussion, but interpersonal toxicity is not.
Connect with in-person community and do not unhealthily over-prioritize online community. Over-prioritization of online community is self-harm.
Luke is a loser, but his channel is teeming with entry-level digital literacy information and advice pertaining to healthy use of technology for us cyborgs.
"Surveillance Self-Defense: Tips, Tools and How-Tos For Safer Online Communication." Electronic Frontier Foundation.
Hackblossom, outdated, is discontinued. The EFF project Surveillance Self-Defense is up-to-date, comprehensive, and follows personal educational principles of simplicity and concision.
To learn more about general (not focused solely on personal action) cybersecurity, visit Cybersecurity by Codecademy and Cyber Security Tutorial by W3Schools. Both contain further segueways into other important digital literacies.
Direct recommendation: Install and set up the linux distribution Tails on a cheap flash drive.
Direct recommendation: Develop your own home network security schema.
Direct recommendation: Always enable 2FA security for Tumblr, disable active / inactive status sharing, and learn to queue reblogs and posts to protect against others' interpretations of your time zone.
Direct recommendation: It's both possible and relatively simple to host your own instance of a search engine using SearXNG.
Zero-Knowledge Architecture.
As a remote activist (even if also a hybrid activist), none of your action should be taken on, using, or interfacing with non-zero-knowledge-architecture services. Tumblr is, of course, a risk in and of itself, but you should not be using services provided by companies such as Google, Microsoft, or any others based in or with servers hosted in 13-eyes agreement nations.
Search for services (email, word processor, cloud storage) which emphasize zero-knowledge architecture. Businesses whose services are structured as such cannot hand over your data and information, as they cannot access it in the first place. If they cannot access the majority of your metadata, either - all the better.
Communications for Armchair Activism
"Technical Writing." Google.
Contained within the linked page at Google Developers, the self-paced, online, pre-class material for courses Technical Writing One, Technical Writing Two, and Tech Writing for Accessibility teach activists to communicate technical concepts in plain English.
"Plain Language." U.S. General Services Administration.
Plain language is strictly defined by U.S. government agencies, which are required to communicate in it for simplicity and quick, thorough comprehension of information.
"Explore Business Law." Study.com.
Extensive courses are offered to quickly uptake principles of business law such as antitrust law, contract law, financial legislation, copyright law, etc. Legal literacy is often the difference between unethical action of a business and its inaction. Legal literacy is also often the difference between consideration and investment in your policy idea and lack thereof.
"Business Communication." Study.com.
Now that you're able to communicate your prioritized information, you may also initiate writing with bells and whistles. While other activists care most about the information itself, business communication allows you to communicate your ideas and needs to those who you must convince worthiness of investment to and win over.
Logic.
Learn it through and through. Start with fallacies if you're better at language and work your way backwards to discrete mathematics; start with discrete mathematics if you're better at maths and work your way forwards to fallacies, critical literacy, and media literacy. State that which you intend to state. Recognize empiricism and rationalism for what they are. Congratulations: you are both a mathematician and a law student.
Economic Literacy for Armchair Activism
"Microeconomics." Khan Academy.
"Macroeconomics." Khan Academy.
The globe operates on profitability. Women's unpaid labor is a massive slice of the profitability pie. While it's possible to enact change without understanding all that drives the events around you, it's impossible to direct or meaningfully manipulate the events around you beyond your scope of comprehension.
Understand economics or be a sheep to every movement you're active in and to every storm that rolls your way.
#masterpost#armchair activism#remote activism#hybrid activism#cybersecurity#literacy#digital literacy#women in tech#radical feminist community#mine
65 notes
·
View notes
Text

Amidst the ongoing legal jabs from both Twitter and Elon Musk’s legal teams, it becomes pretty easy to lose the narrative. But while media coverage would likely give the impression that Musk is simply trying to weasel out of a $44 billion deal, the two parties’ conflict is actually based on a key issue: Twitter bots.
Twitter has maintained that less than 5% of its users are spam or fake accounts, even in its filings to the US Securities and Exchange Commission (SEC). Musk has scoffed at this estimate as the Tesla CEO believes that the number of bots on the social media platform is far higher. An estimate from Dan Woods, the Global Head of Intelligence at F5 and a former FBI special agent specializing in cybersecurity, suggests that Musk’s hunch is spot-on.
In a post on F5’s official website, Woods, who also worked for the CIA as a technical operations officer specializing in cyber operations, estimated that over 80% of Twitter’s accounts are actually bots. Woods was able to come to this conclusion after analyzing the social media platform and its countermeasures against automated accounts.
“When I consider the volume and velocity of automation we’re seeing today, the sophistication of bots that a given set of incentives is likely to attract, and the relative lack of countermeasures I saw in my own research, I can only come to one conclusion: In all likelihood, more than 80% of Twitter accounts are actually bots. This, of course, is my opinion,” Woods wrote.
The former FBI agent noted that bots are generally designed to accomplish a goal. In Twitter’s case, a key goal is to gain followers. More followers mean that an account becomes more influential, which could potentially be a security risk. What’s interesting is that there’s a means to get bots for Twitter, with countless entities offering Twitter accounts, followers, likes, and retweets for a fee. Some are even offered in the dark or deep web.
For research purposes, Woods tried these services on a Twitter account he created. And sure enough, they do work. The former FBI agent paid less than $1,000, but the account has now gained almost 100,000 followers. Woods even tried posting straight gibberish and paying a fee to have his followers retweet it — and they did. With this experience in mind, Woods took his tests further, and the results were pretty damning for Twitter’s anti-bot measures.
“I began to wonder how easy it would be to create a Twitter account using automation. I am not a programmer, but I researched automation frameworks on YouTube and Stack Overflow. Turns out, it’s easy.
“Taking my testing to the next level, over a weekend, I wrote a script that automatically creates Twitter accounts. My rather unsophisticated script was not blocked by any countermeasures. I didn’t try to change my IP address or user agent or do anything to conceal my activities. If it’s that easy for a person with limited skills, imagine how easy it is for an organization of highly skilled, motivated individuals,” Woods wrote.
396 notes
·
View notes
Text
The Biden administration is asking the world’s largest technology companies to publicly commit to tightening the digital security of their software and cloud services.
The voluntary pledge, first reported by WIRED, represents the latest effort by the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) to build support for its Secure by Design initiative, which encourages tech vendors to prioritize cybersecurity while developing and configuring their products.
By signing the pledge, companies promise to make a “good-faith effort” to implement seven critical cybersecurity improvements, ranging from soliciting reports of vulnerabilities in their products to expanding the use of multi-factor authentication, a technology that adds an extra login step to the traditional password.
The pledge—which CISA plans to announce at the RSA cybersecurity conference in San Francisco next week—poses a major test for CISA, which last week marked the one-year anniversary of its Secure by Design campaign. The initiative is a top priority of CISA’s leadership, but it has produced mixed results, with some companies continuing to flout its urgent advice. The tech industry’s reaction to the pledge—and especially the number of software giants that sign it—will serve as a litmus test for how the private sector views CISA’s continuing push for increased corporate investment in cybersecurity.
“We're really excited about the companies that are on board,” Eric Goldstein, CISA’s executive assistant director for cybersecurity, tells WIRED. He declined to say how many vendors have already signed the pledge, but he says they include some “really significant” players in the tech industry.
WIRED asked more than three dozen of the biggest software companies whether they had signed or planned to sign the pledge. Only a handful responded. Login technology provider Okta said it had signed, while security vendor BlackBerry said it was considering doing so. Notably, software giants Amazon, Google, and Microsoft did not say whether they were signing.
“CISA says they have 50 companies that are signing and giving quotations to put on the website,” says a tech industry official familiar with the matter, who requested anonymity to speak candidly. “I don’t know any company that has signed.”
The seven goals laid out in the pledge represent security practices that experts say would dramatically improve companies’ cyberdefenses and make it easier for customers to safely use their products.
The goals include significantly increasing users’ use of multi-factor authentication, including by automatically enabling it or prodding users to activate it; eliminating default passwords, including by requiring users to choose strong passwords at product setup; and making it easier for customers to understand hacks of products they use, including by letting them review logs of suspicious network activity for free.
Companies signing the pledge would also commit to hardening their products against entire classes of vulnerabilities, such as by using memory-safe programming languages that completely block memory-based attacks; fostering better software patching, including by making patching easier and automating it when possible; creating vulnerability disclosure programs that encourage users to find and report product flaws; and publishing timely alerts about major new vulnerabilities, as well as including detailed information in all new vulnerability alerts.
The pledge offers examples of how companies can meet the goals, although it notes that companies “have the discretion to decide how best” to do so. The document also emphasizes the importance of companies publicly demonstrating “measurable progress” on their goals, as well as documenting their techniques “so that others can learn.”
CISA developed the pledge in consultation with tech companies, seeking to understand what would be feasible for them while also meeting the agency’s goals, according to Goldstein. That meant making sure the commitments were feasible for companies of all sizes, not just Silicon Valley giants.
The agency originally tried using its Joint Cyber Defense Collaborative to prod companies into signing the pledge, according to the tech industry official, but that backfired when companies questioned the use of an operational cyberdefense collaboration group for “a policy and legal issue,” the industry official says.
“Industry expressed frustration about trying to use the JCDC to obtain pledges,” the official says, and CISA “wisely pulled back on that effort.”
CISA then held discussions with companies through the Information Technology Sector Coordinating Council and tweaked the pledge based on their feedback. Originally, the pledge contained more than seven goals, and CISA wanted signatories to commit to “firm metrics” for showing progress, according to the industry official. In the end, this person says, CISA removed several goals and “broadened the language” about measuring progress.
John Miller, senior vice president of policy, trust, data, and technology at the Information Technology Industry Council, a major industry trade group, says that change was smart, because concrete progress metrics—like the number of users using multi-factor authentication—could be “easily misconstrued.”
Goldstein says the number of pledge signatories is “exceeding my expectations about where we’d be” at this point. The industry official says they’re not aware of any company that has definitively refused to sign the pledge, in part because vendors want to “keep open the option of signing on” after CISA’s launch event at RSA. “Everyone’s in a kind of wait-and-see mode.”
Legal liability is a top concern for potential signatory companies. “If there ends up being, inevitably, some type of security incident,” Miller says, “anything [a] company has said publicly could be used in lawsuits.”
That said, Miller predicts that some global companies facing strict new European security requirements will sign the US pledge to “get that credit” for something they already have to do.
CISA’s Secure by Design campaign is the centerpiece of the Biden administration’s ambitious plan to shift the burden of cybersecurity from users to vendors, a core theme of the administration’s National Cybersecurity Strategy. The push for corporate cyber responsibility follows years of disruptive supply-chain attacks on critical software makers like Microsoft, SolarWinds, Kaseya, and Change Healthcare, as well as a mounting list of widespread software vulnerabilities that have powered ransomware attacks on schools, hospitals, and other essential services. White House officials say the pattern of costly and often preventable breaches demonstrates the need for increased corporate accountability.
The Biden administration is using the federal government’s contracting power to set new minimum security standards for the software that agencies buy, with the goal of modeling responsible behavior for the entire industry. White House officials are also studying proposals to make all vendors, not just federal contractors, liable for security failures, but that effort faces an uphill battle in Congress.
With no authority to require better cybersecurity for the entire software industry, the White House has tasked CISA with prodding companies to commit to voluntary improvements. That effort began last April with the publication of specific recommendations for incorporating cybersecurity into the product design, development, and configuration process. CISA consulted with the tech industry and the security research community on refinements to that document and released an updated version last October. At around the same time, CISA announced that it had obtained Secure by Design commitments from six major K-12 educational technology vendors. That move, while limited to one industry, signaled CISA’s clear desire to convert its guidance into public corporate pledges.
“It has long been our goal … to move from just the white papers and the guidance to get companies to say, ‘Yes, we agree, and here’s what we're doing,’” Goldstein says. “The pledge really is that concrete manifestation of the guidance that we’ve been developing for a year.”
But the efficacy of the voluntary pledge remains to be seen. “Pledging companies will self-assess and self-report,” says Katie Moussouris, CEO and founder of Luta Security, “so only time will tell if they’ve effectively applied the measures and if the pledge proved to be an effective accountability mechanism.”
Miller says he expects the pledge to keep companies accountable because of the potential legal consequences of neglecting promised improvements. In the meantime, government officials are counting on customers to pressure vendors to both sign and abide by the pledge.
“Right now, we see the demand for safe and secure products to really be significant,” Goldstein says. “We think that … customer demand will drive that progress for us.”
6 notes
·
View notes
Text
Clever Girl
Summary: In where [Y/n] is terrified about an upcoming muggle exam and Severus does his best to calm her.
Pairing: FemReader x Severus Snape
Warning(s): None at all just fluff!
Word Count: 1.9K
A/N: GUYSSSSS!!! This is suuuuuuper self indulgent haahha! No one asked but I work in cybersecurity and have been studying for this certification for 4 months and took my exam today and passed!! Afterward, all I could think about was Sev and him being all like 'of course you would pass you're my clever girl'🥺😭. So here we are : ).
A/N:+ I know the plot makes absolutely no sense because the reader is a witch but also trying to pass the exam 🤣🤣. But hey nothing wrong with trying to get job security in the muggle world if wizarding world careers aren't it. Enjoy!

Severus could practically feel the stress that was emitting off [Y/n] as she sat at her desk, leg bouncing, quill tip between her lips and a deep frown etched on her face. It had been the same for the last few days as she neared closer and closer to some muggle exam she had signed up for. And today was that exam day
“Love, tell me again what exactly this is for?”
“Well, you know how the Aurors are like law enforcement for magical laws and such and they usually have to take some exams?”
“Yes.”
“Well just consider this as like the exam so that I can maybe become an Auror but for like muggle electronics and systems.”
He just stared at her for a second, mind turning and spinning before he quickly turned on his heel and walked away. The pitiful whining of his name was the only thing that had him stopping in his tracks and going back to her side. A faint chuckle left him as her head fell on his shoulder while an exasperated sigh left her due to the knowledge of how much studying would be in her future.
Though till this day, he was still confused as to why she, a witch, was studying to be a muggle electronics Auror or a cybersecurity analyst as she had explained later on. Whatever the case had been, he had been roped into helping her study and revise for the exam.
It had been a memorable few months no doubt as he had also learned quite a bit just from quizzing her at random times of the day and listening to her explain various subjects that encompassed the exam.
“And there are multiple different types of clouds like public, private, hybrid-”
“Stop, stop, stop. Why is it called a cloud? What does that even mean, a private cloud? You cannot just buy a cloud no matter what some of those deranged pure-bloods say.”
“Sev no no no! It’s just a term that’s used to encompass all the little storage places and such that are on the internet! And technically you can own one of these, you just have to have enough money for the cloud service provider!”
“The what?”
It was memorable. But after months of her repeating the cycle of studying, testing herself, crying, and having to have him give her cuddles so that she would calm down. The day had finally come.
“Sev, I think I’m going to go ahead and go.”
[Y/n] announced finally getting up from her spot at the desk and stretching a little before going to Severus who was seated comfortably on the sofa with a book in his lap.
He could hear the shake in her voice, a tell-tale sign of how anxious she was as it had been some time since she had taken an exam or some sort and it was surely giving her not so pleasant memories of being a student again.
“Would you like me to accompany you?” He offered up, leaving his book and spot on the sofa to go to her and ready to throw on his coat and wait for her outside the testing building just so he could offer some comfort if things did go upside down. (He knew they wouldn’t though.)
“No it’s fine but just be ready for me to break our door down if I fail.” It was a joke but there was a little bit of truth behind her words as she went to hug Severus, her head tilted up to look at him as he wrapped his arms around her waist.
“Darling you are not going to fail, you’re a clever girl and have put in quite the amount of work considering the subject.”
“But Sev, what if I fail? Four months of work wasted and then I have to take it again. I don’t want to take it again,” the last sentence came out as a pitiful cry as she laid her head on his chest trying to find some last minute comfort.
And he did feel a bit bad for her knowing that no matter how well she had revised she wouldn’t feel good until the exam was passed but there wasn’t much else to do at this point. Well actually…
“You could always use a memory charm.”
Her head snapped back up at that, a glare evident in her eyes and a scowl to accompany it as any thought of not passing an exam fairly was very much not an option.
“Severus Snape! I’m not cheating on a muggle exam!”
The involuntary chuckle that left him at her reaction was met with her grousing to herself about fairness and integrity and how she rather just fail. She was adorable honestly and he couldn’t help but to quickly lean down and press his lips against hers just to quiet her grumbles.
And maybe just maybe it would calm her down. It did seem to work as when he pulled away he noticed her shoulders sag a little and she had yet to continue on with her rambles so he instead spoke up with a gentle reminder.
“It was just a fun suggestion but I assure you, you’ll be fine. You've studied so hard for such a long time so I have no doubts that you, my brilliant love, will do wonderfully.”
Not wanting to fuss anymore about it because she needed to go into the exam with confidence that was being sapped away with each thought of failure, she gave Severus a weak smile before asking
“Can I have a good luck kiss then?”
A smirk appeared on his face before he leaned down once more, brushing his lips against hers before pressing them gently against her soft skin. Eyes fluttering close, [Y/n] arms tightened around his waist a little and she tiptoed just a bit to deepen the kiss letting her mind settle as much as it could and just enjoy the feeling of his lips on hers.
Unfortunately, the moment ended too soon for her liking and a resigned sigh left her lips as he pulled away from her.
“I’ll be waiting for you here [Y/n]. You’ll do wonderful.”
Still unsure, she could only give him a nervous smile and a soft ‘see you’ before untwining her arms from him and making her way out of the room leaving him alone waiting to see if she would actually break the door down.
It couldn’t have been more than an hour since she had left that he heard the audible ‘pop’ of an apparition happening. That was odd as he didn’t expect anyone at this time of day or that day in general. And it wasn’t until he heard the front door opening and the hurried sound of shoes being discarded on the floor and then footsteps quickly approaching him did he realize it was [Y/n].
“Sev!”
The bright sound of her voice, which was a contrast from this morning, made it into the room before she did and before he knew it, she was throwing herself at him, arms wrapping around his shoulder and a joyful giggle emanating from her.
“I did it! I passed!”
Each phrase came out in excitement as she wiggled in his arms that went to wrap around her to ensure she didn’t fall off his lap. She couldn’t help but pepper his face with soft kisses and glow the entire time as she cuddled close to him radiating joy.
“Thank you so much for all the help you gave me sweetheart,” she continued quickly, giving him no chance to congratulate her as she still was swimming in the aftermath of her positive exam results. “I know you probably hated every minute of it but you’re always so sweet to me helping me with all my studies. Oh I just love you!”
She couldn’t help but bury her face in the crook of his neck, this time an excited squeal leaving her lips as she practically vibrated in his arms.
“Well of course you passed you did have my help after all,” he jokingly responded and he was quickly met with her pulling away from him and laughing before placing another delighted kiss on his cheek.
“Oh hush! You were practically as confused as I was!” It was true and he still kind of was but that was beside the point.
“But you know I'm not surprised you did well,” he hummed lowly, as [Y/n] started to come down from her little high, her eyes still sparkling as she grinned ear to ear practically beaming at him, “and you know why?”
“And why is that?” She answered back, a playful tone of mock curiosity in her voice as one of his hands went to cup her chin and bring her face close to his.
“Because you [Y/n], are my sweet-”
Kiss.
“Clever-”
Kiss.
“Brilliant love,” he purred, kissing [Y/n] once again who was absolutely trembling with giddiness from his kisses and was very eager for each one of them. “Who always works hard for what she wants which keeps me in awe of her. And that's why you did so well and also why I love you so much.”
Each word of praise had her face heating up from the adoration he was showering her with, and it was his turn to repay her for all the kisses she had given him earlier on.
So he did the same and peppered her face softly with light kisses which she absolutely loved considering the happy noise that left her throat each time he pressed his lips on her skin.
Lighting up with each kiss, she giggled loving the affection he was giving to her and being absolutely grateful that he had been so patient with her throughout the whole journey that was had.
As he finally slowed down on the kisses, she couldn’t help but to give him a mischievous look, that matched the impish grin that had grown on her features. And he knew she was about to ask a silly question.
“So…since you love me so much, do you think you’ll help me study for some more stuff?”
“Now that I’m uncertain about.”
It had come out as soon as she finished her question and he was met with a feigned look of hurt and disbelief though it wasn’t there long as she let out a laugh and gently swatted his chest.
“Severus, don't be like that!”
Now it was his turn to have that feigned look of hurt, but it left as quick as it came as the frown morphed into a tiny smile while a deep chuckle left his throat. Bringing his hand to her cheek, he caressed the skin while [Y/n] just smiled at him, head tilting a bit so that it was resting in his palm.
“You know I will,” he answered truthfully as he was always happy to help the sweet girl sitting in his lap who was currently looking at him with unyielding adoration. “And that’s even if I have to see perfectly normal words being spelled strangely just because someone decided so.”
Her brain was no doubt piqued at that as she quickly lifted her face from his hand.
“Well-”
She interjected, starting to explain why some of them were spelled differently. But before she could even start, his fingers had grasped her chin again and he was smashing their lips together in a bruising kiss to silence her.
“Mmph!”
The gasp of surprise quickly turned into a delighted moan as she threw her arms around his shoulders again so that he could deepen the kiss. A kiss that allowed all the stress and anxiety from the day to melt away just as how she allowed herself to melt into his arms and finally relax after being so stressed.
A/N: I'm still running on adrenaline so ignore any mistakes!!! Let me know if you enjoyed it as I was just squealing the entire time writing this. ❤❤❤
#severus snape x reader#severus x reader#snape x reader#severus snape x you#severus x you#severus snape fic#blossoms writing
138 notes
·
View notes
Text
Do you know about All Access Technologies 402-699-2575?
Exploring the Versatility of All Access Technologies 402-699-2575: A Comprehensive Overview
In today's rapidly evolving technological landscape, accessibility and connectivity are paramount. From seamless communication to efficient information dissemination, businesses and individuals alike rely on innovative solutions to stay connected and productive. Among the myriad of companies catering to these needs, one name stands out: All Access Technologies. With their commitment to excellence and a wide array of services, All Access Technologies has become a trusted partner for individuals and organizations seeking reliable connectivity solutions.

The All Access Advantage
At the forefront of All Access Technologies' offerings is their dedication to providing comprehensive solutions tailored to their clients' needs. Whether it's establishing robust communication networks or implementing cutting-edge security measures, All Access Technologies excels in delivering results that exceed expectations.
Their suite of services encompasses various domains, including:
1. Telecommunication Solutions: All Access Technologies specializes in providing telecommunication services that enable seamless connectivity. From voice communication to high-speed internet access, their solutions are designed to keep individuals and businesses connected, regardless of their location.
2. Network Infrastructure: With expertise in network design and implementation, All Access Technologies helps clients build scalable and resilient network infrastructures. Whether it's deploying wired or wireless networks, their solutions are geared towards optimizing performance and ensuring reliability.
3. Security Solutions: In an era where cybersecurity threats are prevalent, All Access Technologies offers robust security solutions to safeguard data and privacy. From firewall protection to intrusion detection systems, their comprehensive approach to security mitigates risks and protects against cyber threats.
4. Unified Communications: All Access Technologies empowers organizations with unified communications solutions that streamline collaboration and enhance productivity. By integrating voice, video, and messaging platforms, they enable seamless communication across multiple channels, fostering efficiency and agility.
Customer-Centric Approach
What sets All Access Technologies apart is their unwavering commitment to customer satisfaction. From initial consultation to ongoing support, they prioritize client needs every step of the way. Their team of experienced professionals works closely with clients to understand their requirements and devise tailored solutions that align with their objectives.
Moreover, All Access Technologies places a premium on reliability and responsiveness. With a dedicated support team available round-the-clock, clients can rest assured that assistance is always within reach. Whether it's troubleshooting technical issues or providing guidance on system optimization, their prompt and efficient support ensures minimal disruption to operations.
Driving Innovation Forward
Innovation lies at the heart of All Access Technologies' ethos. Continuously staying abreast of emerging technologies and industry trends, they strive to deliver cutting-edge solutions that empower their clients to thrive in a rapidly evolving digital landscape. By embracing innovation, All Access Technologies remains at the forefront of technological advancements, driving progress and transformation across industries.
Conclusion
In an age where connectivity is indispensable, All Access Technologies emerges as a beacon of excellence, offering comprehensive solutions that empower individuals and organizations to navigate the complexities of the digital realm with confidence. Through their commitment to innovation, reliability, and customer satisfaction, they continue to redefine the boundaries of technological possibility, enriching lives and shaping the future of connectivity.
For those seeking unparalleled access to transformative technology solutions, All Access Technologies stands ready to deliver, bridging the gap between vision and reality in an interconnected world.
Click given link to read more information:
#canada#india#tech#techcore#technews#technically#technoblade#technology#usa#100 days of productivity#seo services#seo#emailmarketing#digital marketing#online marketing#smm
5 notes
·
View notes
Text
Cybersecurity Giant Zscaler Investigates Alleged Data Breach

UPDATE - Zscaler reiterates no impact or compromise to customers, production, or corporate environments. Zscaler and an independent third-party incident response firm continue to work on forensics analysis of the quarantined test environment.
Cybersecurity powerhouse Zscaler launched an investigation on Wednesday after a notorious hacker, known as IntelBroker, announced on a popular cybercrime forum that they were "selling access to one of the largest cyber security companies". Although the hacker's post did not explicitly name the company, they later confirmed in the forum's shoutbox that the target was Zscaler.
IntelBroker has offered to sell "confidential and highly critical logs packed with credentials", including SMTP access, PAuth access, and SSL passkeys and certificates, for $20,000 in crypto. This alarming claim has raised concerns about the potential severity of the alleged breach.
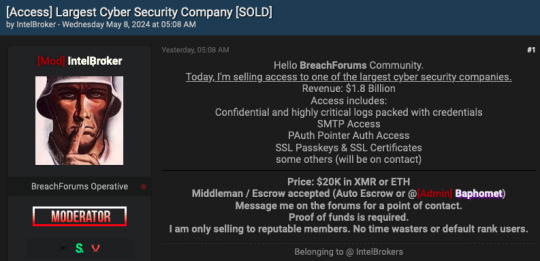
Zscaler's Initial Response and Investigation
Upon learning about the hacker's claims, Zscaler promptly announced the launch of an investigation. A few hours after the investigation commenced, the company announced that it had found no evidence of its customer and production environments being compromised.
Update on Investigation Findings
In its latest update, Zscaler confirmed that its production, customer, and corporate environments were not impacted. The company stated, "Our investigation discovered an isolated test environment on a single server (without any customer data) which was exposed to the internet. The test environment was not hosted on Zscaler infrastructure and had no connectivity to Zscaler's environments. The test environment was taken offline for forensic analysis."
IntelBroker's Recent Claims and Track Record
IntelBroker recently claimed to have stolen US State Department and other government data from the tech firm Acuity. While Acuity confirmed a breach, the company stated that only non-sensitive, old information was compromised. IntelBroker has been making claims about obtaining US government data for more than a year. In several cases, the data has been confirmed to come from third-party service providers, but in some instances, the data was allegedly obtained directly from government systems. However, some of the hacker's claims seemed false or exaggerated.
Read the full article
2 notes
·
View notes
Text
Can you explain the differences between A+, Network+, and Security+ certifications from CompTIA? Which certification is considered more valuable and why?
Certainly! CompTIA offers several certifications that are widely recognized in the IT industry. A+, Network+, and Security+ are three of the most popular certifications, each focusing on different areas of IT. Here's a breakdown of each:
A+ Certification:
Focus: This certification is geared towards entry-level IT professionals and covers foundational skills in IT hardware, software, networking, and troubleshooting.
Topics: A+ covers areas such as PC hardware, operating systems (Windows, Linux, macOS), networking, mobile devices, security, and troubleshooting.
Job Roles: A+ certification holders often work in roles such as technical support specialists, help desk technicians, and field service technicians.
Value: A+ is valuable for individuals starting their IT careers as it provides a solid foundation of IT knowledge and skills. It's often a prerequisite for more advanced certifications.
Network+ Certification:
Focus: Network+ focuses specifically on networking concepts and skills required for IT professionals working with networks, both wired and wireless.
Topics: Network+ covers areas such as network technologies, installation and configuration, media and topologies, management, security, and troubleshooting.
Job Roles: Network+ certification holders typically work in roles such as network administrators, network technicians, and systems engineers.
Value: Network+ is valuable for individuals seeking to specialize in networking. It provides a comprehensive understanding of networking fundamentals and is recognized by employers as validation of networking knowledge and skills.
Security+ Certification:
Focus: Security+ is focused on cybersecurity concepts and skills, covering best practices in securing networks, systems, and applications.
Topics: Security+ covers areas such as network security, compliance and operational security, threats and vulnerabilities, application, data, and host security, access control, identity management, and cryptography.
Job Roles: Security+ certification holders often work in roles such as security analysts, security specialists, security administrators, and network security engineers.
Value: Security+ is highly valuable in today's cybersecurity landscape. It demonstrates proficiency in cybersecurity principles and practices and is often required or recommended for cybersecurity-related roles.
In terms of which certification is considered more valuable, it largely depends on your career goals and the specific job role you're targeting. However, comptia Security+ certification is often regarded as more valuable in terms of salary and job prospects due to the increasing demand for cybersecurity professionals and the critical importance of cybersecurity in modern IT environments. That said, all three certifications have their own merit and can be valuable depending on your career path and interests.
#online certification and training#cybersecuritycourse#comptia security plus#comptia#comptiasecuritypluscertification
2 notes
·
View notes
Text
IT Services in Pennsylvania
At Circle Square, we redefine IT solutions for businesses across Pennsylvania, offering a comprehensive suite of services tailored to your organization's needs. From robust cybersecurity measures to seamless network integration, our team of experts ensures that your technology infrastructure operates at its peak efficiency. Experience unparalleled support and innovative solutions as Circle Square becomes your trusted partner in navigating the ever-evolving landscape of IT services.
Visit us : https://www.circlesquareconsulting.com/
2 notes
·
View notes
Text
Unveiling the Job Market: How Many Jobs Are Available in Finance Services in 2024?

In the ever-evolving landscape of finance, the job market plays a pivotal role in shaping career aspirations and industry trends. As we step into 2024, professionals and aspiring individuals are eager to uncover the opportunities awaiting them in the realm of finance services, particularly in the United States. This article sheds light on the abundance of opportunities available in the finance services.
Exploring the Finance Job Market Landscape:
Quantifying Opportunities:
How many jobs are available in finance in the USA?
Analyzing recent statistics and projections to gauge the scale of employment opportunities.
Factors influencing job availability, such as economic conditions, technological advancements, and regulatory changes.
Diverse Sectors, Diverse Opportunities:
Breaking down the finance sector into subcategories, including banking, investment management, insurance, and consumer services.
Highlighting the unique job prospects within each sector and the skill sets required to excel.
Identifying emerging roles and specialties that are gaining prominence in response to market demands and industry shifts.
Finance in the Digital Age:
Examining the impact of technology on job creation and the transformation of traditional finance roles.
The rise of fintech companies and their contribution to job growth, particularly in areas like digital banking, payment processing, and financial analytics.
The demand for professionals with expertise in data analysis, cybersecurity, and artificial intelligence within the finance sector.
Investment Management: A Thriving Field:
How many jobs are available in investment management?
Unveiling the job opportunities within investment firms, asset management companies, and hedge funds.
The significance of skilled portfolio managers, financial analysts, and risk assessment specialists in driving investment strategies and maximizing returns.
Exploring the global reach of investment management careers and the potential for growth in international markets.
Consumer Services: Meeting the Needs of Individuals:
Evaluating the job market within consumer-focused finance services, including retail banking, wealth management, and financial advising.
The demand for client relationship managers, financial planners, and retirement advisors in assisting individuals with their financial goals.
The role of personalized financial services and digital platforms in catering to the diverse needs of consumers and enhancing their financial literacy.
Trends Shaping the Future:
Anticipating future job trends in finance services and the skills that will be in high demand.
The growing importance of sustainable finance and environmental, social, and governance (ESG) investing, leading to opportunities in green finance and impact investing.
The influence of geopolitical factors, regulatory reforms, and demographic shifts on the finance job market landscape.
Conclusion:
As we go through 2024, the finance job market in the United States continues to offer a lot of opportunities across various sectors. Whether aspiring to go into investment management, consumer services, or the dynamic world of fintech, individuals with the right skills and expertise are well-positioned to thrive in this ever-evolving industry. By staying abreast with market trends, honing relevant skills, and embracing innovation, professionals can seize the abundant opportunities awaiting them in the realm of finance services.
3 notes
·
View notes
Text
The Evolution and Impact of ERP Software in the UAE: A Comprehensive Analysis
ERP stands for Enterprise Resource Planning. It is a type of software system that integrates and manages core business processes and functions within an organization. ERP software typically provides a centralized database and a suite of applications that automate and streamline business activities across various departments such as finance, human resources, supply chain management, manufacturing, sales, and customer service.
In the fast-paced landscape of business operations, efficient management of resources and information is critical for success. Enterprises in the United Arab Emirates (UAE) have witnessed a remarkable transformation in their operational efficiency and competitiveness through the adoption of Enterprise Resource Planning (ERP) software. This article delves into the evolution, benefits, challenges, and future trends of ERP software within the UAE context.
In recent decades, Enterprise Resource Planning (ERP) software has played a transformative role in how businesses in the United Arab Emirates (UAE) operate and manage their resources. This article delves into the evolution, adoption, and impact of ERP systems within the UAE's business landscape. By exploring the unique challenges and opportunities presented by the UAE's dynamic economy, we can better understand how ERP software has become an indispensable tool for organizations seeking efficiency, integration, and scalability.
Evolution of ERP Software
The adoption of ERP software in the UAE mirrors global trends but is uniquely shaped by regional business requirements and technological advancements. In the early 2000s, ERP systems gained traction among larger corporations seeking to streamline their complex processes. Major multinational ERP providers like SAP, Oracle, and Microsoft Dynamics established a strong presence in the region, catering to diverse industry needs including finance, manufacturing, retail, and logistics.
A notable development in recent times is the movement towards cloud-centric ERP solutions.This transition offers scalability, flexibility, and cost-effectiveness, allowing businesses in the UAE to manage their operations more efficiently. Local ERP vendors have also emerged, offering tailored solutions that cater specifically to the nuances of the UAE market, such as compliance with local regulations and cultural practices.
Challenges and Obstacles
Despite the numerous benefits, ERP implementation in the UAE is not devoid of challenges. One prominent obstacle is the high initial investment required for ERP deployment, including software licensing, customization, and training costs. For smaller businesses, this financial commitment can be prohibitive, leading to slower adoption rates among SMEs.
Cultural factors and change management also pose challenges. Embracing new technology often requires a shift in organizational culture and employee mindsets. Resistance to change, coupled with the need for extensive training, can hinder the successful implementation of ERP systems in the UAE.
Furthermore, data security and privacy concerns are paramount, especially in light of stringent regulatory frameworks such as the UAE's Data Protection Law. Ensuring compliance with local data protection regulations adds complexity to ERP deployment, necessitating robust cybersecurity measures and data governance protocols.
The Business Landscape of the UAE
The UAE is renowned for its vibrant economy, diversified industries, and strategic geographical location. Over the years, the country has emerged as a global business hub attracting multinational corporations, SMEs, and startups alike. Key sectors such as finance, real estate, construction, logistics, tourism, and manufacturing contribute significantly to the nation's GDP. However, this diversification has also brought complexities in managing business operations efficiently.
The Emergence of ERP Solutions
As businesses in the UAE expanded and diversified, traditional methods of managing operations became inadequate. The need for integrated systems that could streamline processes across departments led to the rise of ERP solutions. Initially developed to manage manufacturing processes, ERP systems evolved to encompass finance, human resources, supply chain, customer relationship management, and more. This evolution mirrored the growth and diversification of UAE businesses.
Factors Driving ERP Adoption
Several factors have fueled the adoption of ERP software among businesses in the UAE:
Global Competition: The UAE's aspiration to compete on a global scale necessitated advanced operational efficiencies that ERP systems could deliver.
Regulatory Compliance: The UAE's regulatory environment, including VAT implementation, required robust financial and reporting capabilities that ERP systems could provide.
Scalability: With rapid economic growth, businesses needed scalable solutions to manage increasing complexities.
Integration Needs: As businesses diversified, the need for seamless integration across functions became crucial.
Challenges in ERP Implementation
While the benefits of ERP systems are substantial, implementing them poses challenges:
Cultural Factors: Embracing technological change and adopting new systems can face resistance due to cultural factors.
Resource Constraints: SMEs may struggle with the limited resources required for ERP implementation and customization.
Data Security and Privacy: The UAE's focus on data security and privacy necessitates robust ERP solutions compliant with local regulations.
Impact of ERP on UAE Businesses
The impact of ERP software on businesses in the UAE has been profound:
Improved Efficiency: Streamlined processes lead to increased productivity and reduced operational costs.
Enhanced Decision Making: Real-time data availability empowers businesses to make informed decisions.
Better Customer Experience: Integrated systems ensure seamless customer interactions and improved service delivery.
Regulatory Compliance: ERP systems aid in meeting regulatory requirements efficiently.
Key ERP Players in the UAE
Several global and regional ERP providers cater to the UAE market, offering tailored solutions to meet local business needs. Major players include SAP, Oracle, Microsoft Dynamics, Sage, and Epicor, among others.
Future Trends and Innovations
Looking ahead, several trends are poised to shape the future of ERP software in the UAE. Artificial Intelligence (AI) and Machine Learning (ML) are increasingly integrated into ERP systems, enabling predictive analytics and automation of routine tasks. This enhances decision-making capabilities and further optimizes business processes.
Mobile ERP applications are also gaining popularity, allowing stakeholders to access critical business data on the go. The rise of Industry 4.0 and the Internet of Things (IoT) is driving demand for ERP solutions that can seamlessly integrate with smart devices and sensors, enabling real-time monitoring and control of operations.
Moreover, the convergence of ERP with other technologies like blockchain promises enhanced transparency and security in supply chain management, crucial for industries like healthcare and finance.
Conclusion
In conclusion, ERP software has become an integral component of the UAE's business ecosystem, driving efficiency, integration, and growth across diverse sectors. While challenges exist, the transformative impact of ERP systems on businesses in the UAE underscores their importance in navigating complex operational landscapes. As technology continues to evolve, so too will the role of ERP in shaping the future of business in the UAE.ERP software has emerged as a transformative tool for businesses in the UAE, driving efficiency, innovation, and competitiveness across industries. Despite challenges such as high costs and cultural adaptation, the benefits of ERP implementation are substantial, ranging from streamlined operations to improved customer satisfaction. Looking ahead, the evolution of ERP software in the UAE is poised to align with global technological advancements, incorporating AI, IoT, and blockchain to unlock new possibilities for business growth and development. As enterprises continue to navigate the digital landscape, ERP remains a cornerstone of strategic management, enabling organizations to thrive in an increasingly complex and dynamic marketplace.
In summary, ERP software has been a game-changer for businesses in the UAE, enabling them to streamline operations, enhance decision-making, and adapt to a rapidly evolving marketplace. As the UAE continues to position itself as a global economic powerhouse, the role of ERP systems will remain pivotal in supporting the growth and sustainability of businesses across various sectors.
2 notes
·
View notes
Text
WebWise Review - Create & Sell Cyber Secured Websites (Anirudh Baavra)

Welcome to my WebWise Review. This is it! Use AI To Instantly Create & Sell Mind Blowing Websites To Credit Card Ready Clients & Use Proven Arbitrage System To Bank In BIG Offering Red Hot Services.
Every entrepreneur craves attention-grabbing websites that are secure and filled with engaging content to turn casual visitors into loyal customers for life.
However, Developing or acquiring websites tailored to your specific niche and capable of driving customer enthusiasm can be challenging.
WebWise Review: What Is It?
WebWise Is the innovative AI website creator that pioneers the market, crafting over 50,000 ready-to-sell DFY WordPress websites fully fortified with cybersecurity measures and enriched with SEO-optimized content. What’s more? It comes with access to a pool of over 1 million eager clients poised to purchase them, all without requiring any coding or design expertise, and at an unbeatable low one-time price.

Anyone can effortlessly generate and market stunning websites to clients ready to transact with credit cards, leveraging a proven arbitrage system to make substantial profits by providing highly sought-after services.
>> Get WebWise + My $17,000 Bonus To Boost Up Your Earnings MORE and you won’t find these bonuses anywhere >>
WebWise Review: Overview
Creator: Anirudh Baavra
Product: WebWise
Date Of Launch: 2024-Mar-28
Time Of Launch: 10:00 EDT
Front-End Price: $19
Refund: YES, 30 Days Money-Back Guarantee
Product Type: Software (online)
Discount : >> GET THE BEST DISCOUNT HERE <<
Recommended: Highly Recommended
Skill Level Needed: All Levels
WebWise Review: Key Features
First Market Technology Creates Mind Blowing Lightning Fast 50000+ DFY WordPress Websites With AI-Generated Content
Instantly Create Ready Use Stunning WordPress Websites, AI Content, Advanced Persistent Threat Protection, SSL, SEO, and Many More Premium Services To 1 Million+ Desperate Red Hot Audience In 3 EASY Clicks
Let AI do All the Work with Service Providers For You While You Bill Your Clients Again & Again In a Few Clicks For Delivering Services
Get Advanced Persistent Threat Protection To Ensure 100% Security Against Hackers, Spammers, Cyber Threats on Your Websites Etc
Let AI Create SEO Optimized Content For Your Blogs, Websites, Offers & Anywhere Else Instantly on WebWise Sites
Get Over 1000 Hand Picked Website Templates To Create Industry Leading Websites In Red Hot Business Niches
Get 100% Protection For Personal Data, Trade Secrets, Intellectual Property And Any Sensitive Business Information.
Find Desperate Customers Running After You to Buy These Amazing Websites and Services
Use the Inbuilt Army Of Designers, Coding Experts, SEO Professionals, Content Writers, SSL Experts, Advertising Experts, Video Makers, Traffic Scientists etc. Ready to Deliver Exceptional Services To Your Clients
Inbuilt DFY Client outreach Software Included (DFY service intro, Delivery & Sales Service)
Live Fulfilment System included that shows you Instant Flip services to Offer your Clients (buy for $10 and Flip for $100 and more instantly)
Zero Hard Selling, Zero Cold Calling & Zero Configuration – Get Hordes Of Hungry Clients In A Jiffy
100% Easy To Use, Newbie Friendly Technology That’s Never Seen Before
>> Get WebWise + My $17,000 Bonus To Boost Up Your Earnings MORE and you won’t find these bonuses anywhere >>
WebWise Review: How Does It Work?
You’re ONLY 3 Steps Away From Finding Premium Clients & Building 100% Cyber Secured Websites For Them Like A Pro.

WebWise Review: Can Do For You
Use Artificial Intelligence To Create Tons Of Professional, Business-Friendly WordPress Websites
Find 50,000+ Credit Card Ready Customers to Buy These Amazing Websites and Services
Sell Multiple Services Like AI Content, Images, SEO, SSL, Videos Etc To Hungry Audience
Pay $0 To Get 1000+ Converting Templates Crafted By Experts In Red Hot Niches
No Extra Cost To Create & Sell Advanced Threat Protection Websites That Auto Rank For Multiple Keywords
Instantly Create Mind-Blowing Websites With No Time & Investment
Use Artificial Intelligence To Create Tons Of Professional, Business-Friendly WordPress Websites
Find 50,000+ Credit Card Ready Customers to Buy These Amazing Websites and Services
Sell Multiple Services Like AI Content, Images, SEO, SSL, Videos Etc To Hungry Audience
Pay $0 To Get 1000+ Converting Templates Crafted By Experts In Red Hot Niches
No Extra Cost To Create & Sell Advanced Threat Protection Websites That Auto Rank For Multiple Keywords
Instantly Create Mind-Blowing Websites With No Time & Investment
WebWise Review: Who Should Use It?
Digital Product Sellers
Website Owners
Social Media Marketers
Affiliate Marketers
E-com Store Owners
Video Marketers
Small Business Owners
Bloggers & Vloggers
Coaches/Trainers
>> Get WebWise + My $17,000 Bonus To Boost Up Your Earnings MORE and you won’t find these bonuses anywhere >>
WebWise Review: OTO And Pricing
Front End: WebWise ($19)
OTO1: Premium ($47)
OTO2: Unlimited ($37)
OTO3: Max ($37)
OTO4: Enterprise ($47)
OTO5: DFY ($67)
OTO6: Agency ($67)
OTO7: Reseller ($97)
After purchasing, you’ll get my Special Bonus Instantly on your access page as an Affiliate Bonus button on WarriorPlus.
And before ending my legit WebWise Review, I promised to give you my very Special Unique Own Developed PFTSES Formula for FREE.
WebWise Review: Free Bonuses
Bonus 1: WordPress Plugin Maker + Code Generator
WordPress Plugin Maker (stand-alone tool) can build a complete plugin code and also you can develop a WordPress Plugin that customizes features very quickly.
Bonus 2: WhatsApp Chat On Your Websites
This is Non-stop messaging with clients on your site with on the website. This is one of the best ways to connect and interact with your customers, you can offer support directly as well as build trust and increase customer loyalty.
Bonus 3: WebWise LivePreview
LivePreview is used to manage, and switch between your digital products like WordPress themes, HTML templates, HTML5 games, etc
Bonus 4: WebWise Documentation Builder
This is a powerful documentation builder and book publishing application that allows users to create professional-grade documentation with no coding required
Bonus 5: WebWise Article Rewriter
WebWise is an advanced automatic article spinner that can instantly rewrite any data into SEO-friendly unique content. Helps to avoid duplicate content penalties from search engines.
>> Get WebWise + My $17,000 Bonus To Boost Up Your Earnings MORE and you won’t find these bonuses anywhere >>
WebWise Review: Money Back Guarantee
Rest assured, your investment is safeguarded by our 30-day money-back guarantee!
They designed WebWise to empower our users to effortlessly craft professional AI websites brimming with SEO-optimized content, images, videos, and much more in just three clicks.
Even if you harbor the slightest uncertainty, we want to reassure you that our 100% money-back guarantee stands firmly beside you.
Simply put it to the test over the next 30 days, and if you find that our technology doesn’t meet your expectations, we’ll refund your entire purchase amount, no questions asked.
WebWise Review: Conclusion
WebWise seamlessly identifies enthusiastic clients and constructs fully-fledged websites in popular niches, featuring AI-generated content, images, videos, and other essential elements, all with minimal effort through a few clicks.
The most significant aspect to note is that the incredibly low price displayed on this page is available for a limited time only during this launch phase. Once this launch period concludes, the price will inevitably increase to its true value without any hesitation.
Frequently Asked Questions
Do I need experience or tech/design skills to get started?
WebWise was created keeping newbies in mind. So, it’s 100% newbie-friendly & requires no prior design or tech skills.
Is WebWise an easy-to-use platform?
The biggest benefit is that you just need to follow the 3 easy steps we’ve mentioned on the page, & be on the right track to create premium, 100% cyber-secured WordPress websites loaded with SEO-optimized content, images, content, etc without being a geek.
Do you provide a money-back guarantee?
Absolutely yes. We’ve already mentioned on the page that you’re getting a 30-day money-back guarantee. Be rest assured, your investment is in safe hands.
Is step-by-step training included?
YEAH- WebWise comes with step-by-step video training that makes it simple, and easy & guides you through the entire process with no turbulence.
Do you provide any support?
Yes, we’re always on our toes to deliver you an unmatched experience. Drop us an email if you ever have any queries, and we’ll be more than happy to help.
>> Get WebWise + My $17,000 Bonus To Boost Up Your Earnings MORE and you won’t find these bonuses anywhere >>
See my other reviews: ProfitCell Review, Gen AI Review, And MobiApp AI Review.
Thanks for reading my WebWise Review till the end and I hope it will help you to make your purchase decision.
Source: WebWise Review - Create & Sell Cyber Secured Websites (Anirudh Baavra)
Affiliate Disclaimer :
Some of the links in this article may be affiliate links, which means I receive a small commission at NO ADDITIONAL cost to you if you decide to purchase something. While we receive affiliate compensation for reviews/promotions on this article, we always offer honest opinions, user experiences, and real views related to the product or service itself. Our goal is to help readers make the best purchasing decisions, however, the testimonies and opinions expressed are ours only. As always you should do your own thoughts to verify any claims, results, and stats before making any kind of purchase. Clicking links or purchasing products recommended in this article may generate income for this product from affiliate commissions and you should assume we are compensated for any purchases you make. We review products and services you might find interesting. If you purchase them, we might get a share of the commission from the sale from our partners. This does not drive our decision as to whether or not a product is featured or recommended.
#webwise#webwisereview#webwisepreview#webwiseoverview#webwiseappreview#webwisehonestreview#webwisehowdoesitwork#webwiselegit#webwisescam#webwiseoto#webwisedemo#webwisebonus#webwisediscount#webwiseisitreal#asrafulsaikat#getwebwise#buywebwise#bywebwiseAnirudhBaavra
4 notes
·
View notes