#5gsecurity
Text
5G networks advantages and disadvantages

If you work in the technology industry, or if your company uses digital technology in any way, you’ve probably heard about the hype around 5G. The most recent standard for high-speed cellular networks has the potential to completely change wireless connection and bring in a new era of digital transformation.
But before embracing any new technology, it’s a good idea to stand back and weigh the advantages and disadvantages. We’ll examine some of the benefits and drawbacks of 5G networks in this post so you can decide what’s best for your company.
What is it 5G network technology?
The newest specification for cellular networks is called 5G, or fifth-generation mobile technology. Like its forerunners 3G, 4G, and 4G LTE networks, it uses radio frequencies for data transmission and was first made available by mobile phone providers in 2019. 5G does, however, provide certain benefits including lightning-fast download and upload rates, enhanced connection, and more dependability due to improvements in latency and capacity.
What makes 5G so crucial?
5G has been hailed as a disruptive technology that can revolutionize industries comparable to those of artificial intelligence (AI), the Internet of Things (IoT), and machine learning (ML) in the four years since it first entered the market. The volume of data created daily is growing rapidly as mobile broadband technology advances, to the point that 3G and 4G network infrastructures are unable to manage it. Introducing 5G, which can handle far bigger amounts of data due to its wider bandwidths, quick upload and download speeds, and fast upload times.
Advantages of 5G
Apart from increased upload/download speeds, there are a few additional significant distinctions between 5G and 3G/4G networks that are worth mentioning:
Reduced physical footprint
Because 5G employs smaller transmitters than its predecessors, it is possible to covertly install them in trees, on buildings, and other awkward locations. In addition to being smaller and requiring less power to operate, 5G networks also use “small cells,” or wireless network nodes, for connection.
Decreased frequencies of errors
The modulation and coding scheme (MCS) for 5G, which is adaptive, is superior to that of 4G and 3G for data transmission from WiFi devices. As a consequence, the Block Error Rate (BER), which gauges how often mistakes occur in a network, is very low. In a 5G network, the transmitter reduces connection speed until the error rate decreases if the BER reaches a certain threshold. In essence, 5G networks compromise real-time accuracy for speed in order to maintain a near-zero bit error rate.
Increased bandwidth
Compared to earlier networks, 5G networks are capable of using a much wider variety of bandwidths. 5G may cover a wider frequency range by increasing the spectrum of resources it can use from sub-3 GHz to 100 GHz and beyond. This increases the number of devices the network can handle at once and increases its total capacity and throughput by enabling it to operate over a much broader range of bandwidths.
Reduced latency
The speeds that make tasks like downloading files or communicating with the cloud 10x quicker than on a 4G or 3G network are made possible by 5G’s low latency, which is the length of time it takes for data to move from one place to another on a network. 5G networks sometimes have latencies as low as one millisecond, while 4G networks typically give latency of over 200 milliseconds.
5G networks Disadvantages
As with any new technology, there are plenty of reasons to be excited about 5G but equally cautious as well. Let’s examine some of the issues that are keeping businesses and consumers from fully adopting it.
Online safety
Even with 5G’s more sophisticated algorithms than its predecessors, customers are still susceptible to hackers. One thing to be wary about is encryption. Although 5G networks provide secured applications, the 5G NR standard lacks end-to-end encryption, making it vulnerable to certain types of assaults.
Slicing a network
Although network slicing is a well-liked feature of 5G networks, it should be used with caution. When establishing a virtual network for a particular purpose, 5G software leaves itself open to possible intrusions from viruses and hackers. Malware or spyware may propagate across a carrier’s networked devices or infrastructure once a breach has happened, posing a threat to whole businesses.
Infrastructure
Businesses must consider the time and expense of upgrading existing equipment to make it 5G compliant before moving services and functions to a 5G network. This may be costly and time-consuming. An organization that has been using 3G or 4G networks for a while has probably already invested a significant amount of money in its equipment. A major challenge is replacing it and retraining employees to operate and maintain the new infrastructure.
Coverage gaps
There is already 5G coverage in many major cities thanks to the global deployment of 5G technology. It’s crucial to remember that 5G isn’t now widespread and probably won’t be for some time. For instance, a lot of isolated places only have spotty 5G connectivity or none at all. Businesses should consider where they want to use 5G before upgrading, particularly if they operate in rural locations, to make sure they will have 5G coverage.
Infiltration
Ensuring smooth pathways for 5G signals to move on may be challenging since ordinary things like buildings and/or trees can readily obstruct the high-frequency radio waves that the signals travel on. Due to the particular difficulties that factories and offices bring, several companies have redesigned their spaces to make them more compatible with 5G networks.
Read more on Govindhtech.com
#ibm#5gtechnology#5gnetwork#5gsecurity#5gsoftware#wifi#machinelearning#ai#technology#technews#govindhtech
0 notes
Photo

5G security open problems. At 5G security #DataHub session @Communitech #DataHub. #5Gsecurity #wireless #sevurity #5Gnetworks #5Gwireless #openproblems #identity #DataHubSessions @CityWaterloo #kwawesome #wrawesome (at Communitech Data Hub) https://www.instagram.com/p/B2134FyA1lO/?igshid=1umt6o7az1sdh
#datahub#5gsecurity#wireless#sevurity#5gnetworks#5gwireless#openproblems#identity#datahubsessions#kwawesome#wrawesome
0 notes
Text
How Safe is Our Quantum Future?

Quantum computers will be revolutionary in their compute capability, so much that they can undermine the foundation of internet security. They are not just a technical achievement to be proud of, but a phenomenon that requires us to plan for without delay since they can undermine internet security.
We should adopt agile, integrated cybersecurity strategies now to ensure we are prepared for the age quantum computers will usher in.
Do share your thoughts and comments
#quantumcomputing #quantumiscoming #quantumcryptography #quantumcomputers #5gtechnology #5gsecurity #cybersecuritythreats #algorithms #keymanagement #cryptography #bitcoin #fintechinnovation #cybersecurity #dataprotection #informationsecurity #datasecurity #infosec
https://samiran-ghosh.medium.com/how-safe-is-our-quantum-future-787dbd13e7c5
1 note
·
View note
Photo
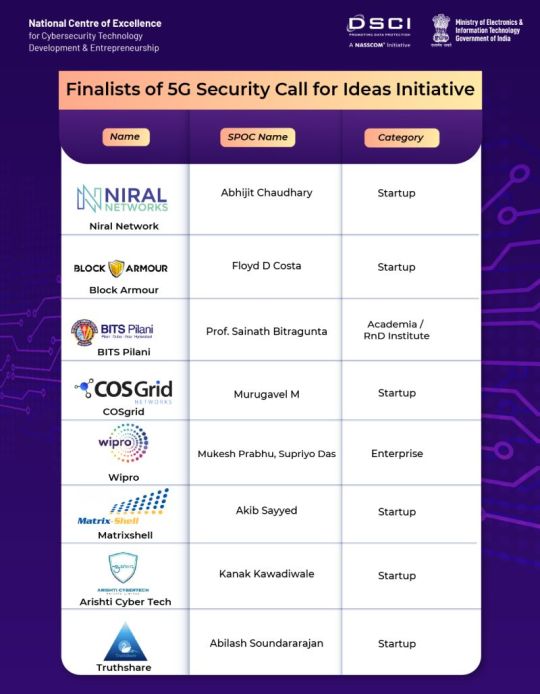
Excited to announce the finalists of Idea Stage #5G Security Call for Ideas Initiative! The program aimed at creating visibility of ideas in 5G Security to accelerate collaboration among startups, academia & industry towards their productization & deployment. Congratulations on your achievements!
#5GSecurity #Cybersecurity #5Gnetworks #networksecurity
0 notes
Photo

Properties of 5G wireless network. At 5G security #DataHub session @Communitech #DataHub. #5Gsecurity #wireless #5Gnetworks #5Gwireless #4Gnetworks #4Gwireless #DataHubSessions @CityWaterloo #kwawesome #wrawesome (at Communitech Data Hub) https://www.instagram.com/p/B213Us7givC/?igshid=vecg2e7m8urf
#datahub#5gsecurity#wireless#5gnetworks#5gwireless#4gnetworks#4gwireless#datahubsessions#kwawesome#wrawesome
0 notes
Photo

Wireless security. At 5G security #DataHub session @Communitech #DataHub. #5Gsecurity #wireless #security #5Gnetworks #5Gwireless #4Gnetworks #4Gwireless #DataHubSessions @CityWaterloo #kwawesome #wrawesome (at Communitech Data Hub) https://www.instagram.com/p/B213JjfgAOA/?igshid=1mhwgl0prisse
#datahub#5gsecurity#wireless#security#5gnetworks#5gwireless#4gnetworks#4gwireless#datahubsessions#kwawesome#wrawesome
0 notes
Photo

5G wireless network slicing. At 5G security #DataHub session @Communitech #DataHub. #5Gsecurity #wireless #5Gnetworks #5Gwireless #4Gnetworks #4Gwireless #DataHubSessions @CityWaterloo #kwawesome #wrawesome (at Communitech Data Hub) https://www.instagram.com/p/B2125yrgF3b/?igshid=1xmfkkg7jbcjs
#datahub#5gsecurity#wireless#5gnetworks#5gwireless#4gnetworks#4gwireless#datahubsessions#kwawesome#wrawesome
0 notes
Photo

5G use cases At 5G security #DataHub session @Communitech #DataHub. #5Gsecurity #usecases #wireless #5Gnetworks #5Gwireless #4Gnetworks #4Gwireless #DataHubSessions @CityWaterloo #kwawesome #wrawesome (at Communitech Data Hub) https://www.instagram.com/p/B212HZ5Aia4/?igshid=137133jkrn1ot
#datahub#5gsecurity#usecases#wireless#5gnetworks#5gwireless#4gnetworks#4gwireless#datahubsessions#kwawesome#wrawesome
0 notes
Photo

Comparing 4G & 5G requirements. At 5G security #DataHub session @Communitech #DataHub. #5Gsecurity #wireless #5Gnetworks #5Gwireless #4Gnetworks #4Gwireless #DataHubSessions @CityWaterloo #kwawesome #wrawesome (at Communitech Data Hub) https://www.instagram.com/p/B210R3cAz6_/?igshid=zi1dzaosg7by
#datahub#5gsecurity#wireless#5gnetworks#5gwireless#4gnetworks#4gwireless#datahubsessions#kwawesome#wrawesome
0 notes
Photo

Evolution of wireless standards. At 5G security #DataHub session @Communitech #DataHub. #5Gsecurity #DataHubSessions @CityWaterloo #kwawesome #wrawesome (at Communitech Data Hub) https://www.instagram.com/p/B21yqKmAFeU/?igshid=1ki7ki5gp13xj
0 notes
Photo

5G security #DataHub session about to begin @Communitech #DataHub. #5Gsecurity #DataHubSessions @CityWaterloo #kwawesome #wrawesome (at Communitech Data Hub) https://www.instagram.com/p/B21yBHMAigg/?igshid=1hcxxthbmriie
0 notes