#multiprotocol
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text
Server Saturday: Demystifying MPLS - A Reliable Network Technology
🔐🌐✨
Welcome to Server Saturday, where we delve into the fascinating world of Multiprotocol Label Switching (MPLS). In this post, we’ll demystify MPLS, making it easy to understand even for non-tech enthusiasts. Think of MPLS as a reliable and efficient postal service for your data, ensuring it reaches its destination swiftly and securely. So, let’s embark on a journey through the inner workings…

View On WordPress
#MPLS#Multiprotocol Label Switching#network technology#Quality of Service#reliability#scalability#VPNs
0 notes
Link
What is Multiprotocol Label Switching (MPLS)?
Multiprotocol label switching is a traffic routing mechanism that helps mold traffic flows when data is sent between traffic nodes. MPLS ensures reliable connections for real-time applications. Since it is a technique and not a service, MPLS can deliver anything ranging from IP VPNs to metro Ethernet.
MPLS differs from other networks that route traffic based on source and destination address as it routes traffic based on predetermined labels. Due to these capabilities, businesses have used MPLS to connect their remote branch offices that require data access or applications located in the company’s headquarters.
How Does MPLS Work?
The packet is assigned to a specific forwarding class of service the first time it enters the network using a Multiprotocol Label Switching. This is indicated by forwarding a short bit sequence or label to the packet. The classes are often indicative of the type of traffic that they carry.
For instance, a business could label the classes depending on whether they represent voice and video, internet and email, among others. Each application will be placed in a different class. If no route is discovered for the packet, then a default route is used to send the packet back to its destination.
Packets with similar characteristics are assigned to the same label and routed according to the same rules. On each router is a routing table that provides information on how to handle specific packets as the data packet is passed from one router to the other. This way, data travels faster as it is skipped via the short path labels rather than the large network addresses.
Going forward, the best strategy is for businesses to use a hybrid of MPLS and SD-WAN since each has its benefits. You can consider using MPLS for sensitive applications while offloading as much traffic to the public internet.
We at OpenGrowth, are committed to keeping you updated with the best content on the latest trendy topics from any major field. Also, both your feedback and suggestions are valuable to us. So, do share them in the comment section below.
0 notes
Text
Multiprotocol Label Switching (MPLS)
Multiprotocol Label Switching (MPLS) adalah sebuah teknologi jaringan yang digunakan untuk memindahkan lalu lintas data dari suatu titik ke titik lain dalam jaringan secara cepat dan efisien. MPLS menggabungkan beberapa teknologi jaringan seperti circuit switching dan packet switching sehingga memungkinkan jaringan untuk memprioritaskan lalu lintas data berdasarkan jenis aplikasi atau kepentingannya dalam suatu jaringan.
Dalam MPLS, setiap paket data yang masuk ke dalam jaringan diberi label atau tanda khusus yang menunjukkan rute yang harus diambil untuk mencapai tujuan akhir. Dengan cara ini, MPLS dapat memindahkan data dengan lebih cepat karena tidak perlu melakukan routing paket secara terus-menerus saat melewati setiap node jaringan. Selain itu, MPLS juga dapat memprioritaskan lalu lintas data yang lebih penting seperti video atau voice call untuk memastikan kualitas layanan yang lebih baik.
MPLS tidak mengharuskan suatu topologi jaringan tertentu karena MPLS bekerja di lapisan 2 dan 3 dalam model referensi OSI, sehingga dapat diimplementasikan pada berbagai topologi jaringan seperti ring, mesh, dan star. Namun, untuk mengilustrasikan contoh konfigurasi MPLS, berikut adalah topologi jaringan dasar yang menggunakan MPLS:
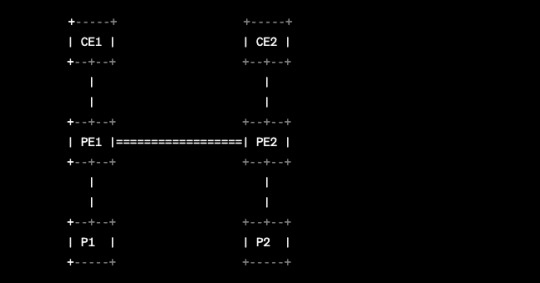
Pada topologi di atas, CE1 dan CE2 adalah customer edge routers yang terhubung ke provider edge routers PE1 dan PE2 melalui jalur Layer 2 atau Layer 3. Jalur ini disebut Virtual Private Wire Service (VPWS) untuk koneksi Layer 2 atau Virtual Private Network (VPN) untuk koneksi Layer 3. PE1 dan PE2 kemudian terhubung ke router core atau P routers, seperti P1 dan P2.
Untuk mengkonfigurasi MPLS pada topologi ini, beberapa langkah dasar yang perlu dilakukan adalah sebagai berikut:
Aktifkan fitur MPLS pada semua router di jaringan, yaitu CE1, CE2, PE1, PE2, P1, dan P2.
Atur label distribution protocol (LDP) pada semua router agar dapat saling mengenal dan membagikan label.
Terapkan label pada semua prefix (network address) di setiap router menggunakan LDP.
Atur penunjukan jalur (path) menggunakan label yang diberikan oleh LDP.
Terapkan MPLS traffic engineering jika diperlukan untuk memprioritaskan lalu lintas jaringan yang penting.
Langkah-langkah tersebut dapat diimplementasikan dengan menggunakan perangkat lunak router vendor tertentu, seperti Cisco IOS atau Juniper JunOS, yang biasanya memiliki konfigurasi MPLS yang mudah digunakan dan dipahami. Namun, karena MPLS merupakan teknologi jaringan yang kompleks, diperlukan pengetahuan dan pengalaman yang cukup untuk mengkonfigurasikannya dengan benar.
3 notes
·
View notes
Text
What Can I Do With A Cisco CCNA Certification?
Cisco Certified Network Associates (CCNA) are one of the world's most sought-after network professionals. Having a CCNA certification opens up a wide variety of job opportunities and can lead to higher salaries.

A Cisco CCNA certification is valuable in terms of the potential salary and employment opportunities that result from this certification. MyComputerCareer also offers his CCNA training as part of the Cybersecurity Specialist Curriculum. For more information, please contact us immediately.
This article explains what a CCNA certification is, what it includes, and the skills it teaches. We will also discuss the different positions you can get with a CCNA certificate and the salaries you can earn with this certificate.
What Is The CCNA Certification?
The Cisco Certified Network Associate (CCNA) certification is a well-known computer networking credential. CCNA certification helps entry-level network engineers, professional network engineers, support network engineers, and network administrators learn basic networking concepts.
Over one million CCNA certificates have been distributed to fully certified professionals since Cisco first introduced certificates in 1998. CCNA certifications cover a wide range of networking topics and help prepare learners for future advances in networking technology.
CCNA certification topics include:
OSI model: Physical Layer, Data Link Layer, Network Layer, Transport Layer, and Application Layer
IP routing: static and dynamic routing protocols
IP addressing: Fourth Generation IPv4 (IPv), Internet Control Message Protocol (ICMP), Address Resolution Protocol (ARP), and Cisco IOS
Network security: Firewalls, password security, virtual private networks (VPNs), and intrusion detection systems
VLANs and WLANs: Access Control Lists (ACLs), VLAN Trunking Protocol (VTP), and Cisco Wireless LAN Controller (WLC) IP Services
Routing protocols (OSPF, EIGRP, and RIP): Cisco IOS, Cisco Express Forwarding (CEF), and Cisco Dynamic Multiprotocol Label Switching (DMVPN) WAN
CCNA certification validates many of the skills a network engineer needs. You will also need various soft skills such as communication, problem solving, organization and customer service. CCNA certification also provides network professionals with the information and skills they need to effectively operate Cisco and Microsoft Office suite applications. This certification empowers aspiring and current network engineers to use industry-specific tools in their daily work.
However, please note that Cisco certifications are valid for three years. If the certification expires, the holder may retake her CCNA certification exam, obtain another Associate certification, pass the Core Technology exam, or for renewal she must complete 40 Continuing Education (CE) credit must be obtained.
What IT Jobs Can You Get With a CCNA Certification?
The Cisco Certified Network Associate (CCNA) certification validates a user's knowledge and skills in network administration. Salaries for this degree average about $80,000 per year. Many employees are looking for Cisco certified professionals because of their extensive experience with Cisco routers and switches. Cisco network equipment is used by most of the Fortune 500 companies.
Network administrator: Network administrators are responsible for the day-to-day operation of computer networks. Keep your network running smoothly and resolve any issues that may arise.
System Administrator: System administrators are responsible for the maintenance and operation of computer systems. It installs new software, patches existing software, and performs other tasks to keep your system running smoothly.
Network analyst: Network analysts are responsible for analyzing computer networks and making recommendations to improve their efficiency. They may also be responsible for designing new networks or implementing changes to existing networks.
Network design engineer: Network design engineers are responsible for designing and implementing computer networks. We work with our customers to understand their needs and design networks that meet those needs.
Infrastructure Engineer: Infrastructure engineers are responsible for the physical components of computer networks such as routers, switches, and cables. Install and maintain these components to keep your network running smoothly.
Unified Communications Engineer: Unified Communications Engineers are responsible for designing and implementing unified communications systems. Unified communication systems allow users to communicate across multiple devices such as phones, computers, and tablets.
Solution designer: Solution design engineers are responsible for designing and implementing solutions to problems encountered in computer networks. They work with customers to understand their needs and design solutions that meet those needs.
Cloud Engineer: Cloud engineers are responsible for designing and implementing cloud-based solutions. Cloud-based solutions allow users to access data and applications from anywhere in the world.
Data Center Engineer: Data center engineers are responsible for the operation of data centers. Install and maintain the hardware and software that make up your data center.
Network administrator: Network administrators are responsible for the day-to-day operation of computer networks. Ensure the smooth operation of your network and fix any problems that may arise.
Cloud Architect: Cloud architects are responsible for designing and implementing cloud-based solutions. Cloud-based solutions allow users to access data and applications from anywhere in the world.
VoIP Engineer: VoIP engineers are responsible for designing and implementing Voice over IP (VoIP) solutions. VoIP solutions allow users to communicate using voice and video over the Internet.
Cooperating engineer: Collaboration engineers are responsible for designing and implementing solutions that enable users to collaborate. Collaboration solutions allow users to share data, applications, and files.
Telecom Engineer: Telecommunications engineers are responsible for the design and implementation of telecommunications systems. Telecommunications systems allow users to communicate using voice, video, and data.
Depending on your skills, years of experience, valid qualifications, and other criteria, you may be better suited for one job than another. The Cisco Certified Network Associate (CCNA) is a great place to start for anyone looking to get into networking.
Conclusion
Earning the Cisco Certified Network Associate (CCNA) certification is a great way to start your networking career. A CCNA certification contains a wealth of knowledge that will help you in your career. A CCNA certification can lead to higher salaries and help you find jobs in a variety of occupations. There are a variety of Cisco certifications you can earn, each useful in your career. A CCNA certification is just the beginning of your journey to a successful networking career.
591cert offers a certification program that includes CCNA Certification. If you're interested in becoming a CCNA and growing your IT career, take a free career assessment. We are happy to answer your questions.
2 notes
·
View notes
Text
Revolutionizing Connectivity: Sify's SD-WAN Solutions Redefine Networking in India
In today’s digitally-driven landscape, connectivity is the backbone of success for businesses across all industries. As enterprises embrace cloud services, IoT devices, and remote work, the demand for robust, agile, and secure networking solutions has never been higher. Sify Technologies, a leading ICT service provider in India, rises to the challenge with its cutting-edge SD-WAN (Software-Defined Wide Area Network) solutions, poised to transform the way businesses connect and collaborate.
Unveiling the Future of Networking: Sify’s SD-WAN solutions stand at the forefront of technological innovation, offering businesses unparalleled control, flexibility, and performance optimization. By leveraging software-defined networking principles, Sify empowers enterprises to dynamically manage and optimize their wide area networks, regardless of geographical constraints.
Key Features and Benefits:
Agility: Traditional networking architectures are often rigid and cumbersome, hindering adaptability to evolving business needs. Sify’s SD-WAN solutions break free from these constraints, providing enterprises with the agility to scale bandwidth, add new branch locations, and deploy applications seamlessly.
Optimized Performance: In the era of real-time applications and data-driven decision-making, network performance is non-negotiable. Sify’s SD-WAN employs intelligent traffic steering and path selection algorithms to optimize application performance, ensuring low latency and high throughput across the network.
Enhanced Security: With cyber threats growing in complexity and frequency, safeguarding sensitive data and critical assets is paramount. Sify’s SD-WAN integrates advanced security features such as encryption, firewall, and threat detection, providing end-to-end protection against cyber attacks and breaches.
Cost Efficiency: Traditional MPLS (Multiprotocol Label Switching) networks can be cost-prohibitive for businesses, especially those with distributed operations. Sify’s SD-WAN leverages cost-effective broadband connections alongside MPLS, enabling enterprises to achieve significant cost savings without compromising performance or reliability.
Simplified Management: Complexity is the enemy of efficiency in network management. Sify’s SD-WAN simplifies network orchestration and monitoring through a centralized management console, empowering IT teams to streamline operations, troubleshoot issues, and enforce policies effortlessly.
Customer-Centric Approach: At Sify, customer satisfaction is paramount. From initial consultation to deployment and ongoing support, Sify’s team of experts works closely with clients to understand their unique requirements and deliver tailored SD-WAN solutions that exceed expectations. Whether it’s optimizing application performance, enhancing security posture, or reducing operational costs, Sify is committed to driving tangible business outcomes for its customers.
Driving Digital Transformation: In an era defined by digital transformation, connectivity is the linchpin that drives innovation, collaboration, and growth. Sify’s SD-WAN solutions serve as a catalyst for businesses embarking on their digital journey, empowering them to embrace emerging technologies, enhance operational efficiency, and stay ahead of the competition.
Experience the Future Today: As businesses navigate the complexities of modern networking, Sify stands ready to be their trusted partner in success. With its visionary approach, relentless innovation, and unwavering commitment to excellence, Sify is transforming the networking landscape in India and beyond, one connection at a time.
Discover the power of Sify’s SD-WAN solutions and embark on a journey towards a more connected, agile, and secure future for your business.
0 notes
Text
what is mpls vpn connectivity
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is mpls vpn connectivity
MPLS VPN Introduction
Title: MPLS VPN Introduction: Enhancing Secure and Efficient Networking
In today's digital landscape, where businesses are expanding globally and remote work is becoming increasingly prevalent, the need for secure and efficient networking solutions has never been more critical. MPLS VPN, or Multiprotocol Label Switching Virtual Private Network, emerges as a robust solution to address these demands.
MPLS VPN is a technology that combines the benefits of Multiprotocol Label Switching (MPLS) and Virtual Private Network (VPN) to create a secure and reliable network infrastructure. MPLS efficiently directs data packets along predetermined routes through the network, using labels instead of IP addresses, which enhances performance and reduces latency. Meanwhile, the VPN aspect ensures that data transmitted over the network remains encrypted and isolated from unauthorized access.
One of the primary advantages of MPLS VPN is its ability to provide seamless connectivity across geographically dispersed locations. Whether employees are working from headquarters, branch offices, or remote locations, MPLS VPN ensures that they can access company resources securely and efficiently. This connectivity is particularly valuable for businesses with multiple offices or a global presence, as it eliminates the need for multiple point-to-point connections and simplifies network management.
Moreover, MPLS VPN offers enhanced Quality of Service (QoS) capabilities, allowing businesses to prioritize critical applications such as voice and video conferencing over less time-sensitive traffic. This ensures that essential services receive the necessary bandwidth and latency requirements, resulting in a superior user experience.
Security is another key benefit of MPLS VPN. By encrypting data transmitted over the network and segregating traffic from different customers, MPLS VPN provides a secure environment for confidential communications and protects against unauthorized access or eavesdropping.
In conclusion, MPLS VPN is a versatile networking solution that combines the efficiency of MPLS with the security of VPN, making it ideal for businesses seeking to optimize their network infrastructure for performance, reliability, and security in today's interconnected world.
MPLS VPN Architecture
MPLS VPN (Multiprotocol Label Switching Virtual Private Network) architecture is a network mechanism that efficiently delivers data between multiple locations in a secure and scalable manner. It combines the flexibility of IP routing with the speed and reliability of switching to create a seamless and robust network infrastructure.
In an MPLS VPN architecture, labels are assigned to packets to determine the best path for data transmission across the network. This process eliminates the need for complex routing tables and improves network performance by enabling traffic prioritization and optimized routing.
One of the key advantages of MPLS VPN architecture is its ability to provide secure communication between geographically dispersed sites. By creating virtual private networks over a shared infrastructure, organizations can securely connect their offices, data centers, and cloud resources without compromising on data privacy or network performance.
Furthermore, MPLS VPN architecture offers scalability by allowing organizations to easily expand their networks as their business grows. With support for Quality of Service (QoS) mechanisms, MPLS VPNs ensure that critical applications receive the necessary bandwidth and priority to maintain optimal performance.
Overall, MPLS VPN architecture streamlines network management, enhances data security, and improves network efficiency, making it a popular choice for businesses looking to establish reliable and secure communication channels between their various locations.
MPLS VPN Components
A Multiprotocol Label Switching Virtual Private Network (MPLS VPN) is a technology that enables secure communication across multiple locations. This network relies on various components to function efficiently and provide users with a seamless browsing experience.
One of the key components of an MPLS VPN is the Provider Edge (PE) router. This device acts as the interface between the customer's network and the service provider's network. The PE router is responsible for establishing VPN connections, applying VPN labels, and forwarding data packets securely. It ensures that data is transmitted only to the intended recipients, maintaining the confidentiality and integrity of the communication.
Another crucial component is the Provider (P) router, which operates within the service provider's network to transmit data between different customer sites. The P router uses labels to efficiently route traffic through the MPLS network, reducing congestion and improving network performance. By forwarding data based on labels instead of IP addresses, the P router enhances network scalability and flexibility.
In addition to PE and P routers, MPLS VPNs also rely on Label Distribution Protocols (LDP) to assign and distribute labels throughout the network. LDP establishes label-switched paths (LSPs) between routers, allowing data to be forwarded along the most efficient route. This dynamic label assignment mechanism optimizes network traffic flow and minimizes latency, ensuring a seamless browsing experience for users.
Overall, the successful operation of an MPLS VPN relies on these essential components working together to provide secure, reliable, and efficient communication across distributed networks. By leveraging PE routers, P routers, and LDP protocols, organizations can establish a robust MPLS VPN infrastructure that meets their connectivity needs effectively.
MPLS VPN Connectivity Protocols
MPLS VPN connectivity protocols play a critical role in facilitating secure and efficient communication within a network. MPLS, which stands for Multiprotocol Label Switching, is a mechanism used in telecommunications networks to direct data packets along predefined paths, ensuring fast and reliable data transmission.
One of the key connectivity protocols used in MPLS VPNs is the Border Gateway Protocol (BGP). BGP is crucial for establishing communication between different network domains by exchanging routing information. It helps in determining the optimal path for data packets to reach their intended destinations, enhancing network efficiency and performance.
Another essential protocol in MPLS VPN connectivity is the Label Distribution Protocol (LDP). LDP is responsible for assigning labels to data packets as they enter the MPLS network, enabling routers to make forwarding decisions based on these labels. This process helps in streamlining traffic flow and reducing network congestion, leading to improved overall network quality of service.
Additionally, the Multi-Protocol BGP (MP-BGP) protocol is employed in MPLS VPNs to support the exchange of routing information for multiple network protocols. By utilizing MP-BGP, service providers can deliver complex services over the MPLS infrastructure, catering to diverse networking requirements of businesses and organizations.
In conclusion, MPLS VPN connectivity protocols such as BGP, LDP, and MP-BGP are foundational elements that contribute to the secure and efficient operation of modern networks. By leveraging these protocols, organizations can establish robust VPN connections, enhance network performance, and ensure seamless communication across their distributed network environments.
MPLS VPN Deployment Options
MPLS (Multiprotocol Label Switching) VPNs offer a secure and efficient way to connect multiple locations within a network, providing a reliable communication infrastructure for businesses. When deploying MPLS VPNs, there are several options available, each with its own benefits and considerations.
One deployment option is the Layer 3 MPLS VPN, which utilizes IP routing to forward packets between sites. This option offers scalability and flexibility, making it suitable for large enterprises with complex network architectures. Layer 3 MPLS VPNs provide end-to-end connectivity and support a wide range of applications and protocols.
Another option is the Layer 2 MPLS VPN, which operates at the data link layer and maintains the original Ethernet frames throughout the network. This option is ideal for organizations that require seamless integration with existing Ethernet-based networks, such as those using VLANs or Ethernet-based services. Layer 2 MPLS VPNs offer low latency and high performance, making them suitable for real-time applications like voice and video conferencing.
Additionally, MPLS VPNs can be deployed using either a provider-managed or customer-managed approach. With a provider-managed VPN, the service provider handles all aspects of the network, including configuration, maintenance, and troubleshooting. This option offers simplicity and convenience for businesses that prefer to outsource their network management tasks.
On the other hand, a customer-managed MPLS VPN provides more control and customization options for the organization, allowing them to tailor the network to their specific requirements. While this approach requires more resources and expertise to manage, it offers greater flexibility and autonomy in network operations.
In conclusion, MPLS VPN deployment options vary based on factors such as network size, performance requirements, and management preferences. By carefully evaluating these factors, businesses can choose the option that best suits their needs and ensures a successful implementation of MPLS VPN technology.
0 notes
Text
what is the difference between mpls and vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is the difference between mpls and vpn
MPLS definition
MPLS, short for Multiprotocol Label Switching, is a crucial technology in modern networking, facilitating efficient data transmission across complex networks. At its core, MPLS involves the labeling of data packets to expedite their routing through the network. This labeling process enables routers to make forwarding decisions based on the labels, rather than solely relying on the packet's destination IP address.
One of the key advantages of MPLS is its ability to establish predetermined paths for data packets, known as Label Switched Paths (LSPs). By doing so, MPLS can optimize network traffic flow, reduce congestion, and improve overall network performance. This deterministic routing mechanism is particularly beneficial for real-time applications such as voice and video streaming, where consistent latency and packet delivery are critical.
Moreover, MPLS supports Quality of Service (QoS) mechanisms, allowing network administrators to prioritize certain types of traffic over others. This feature is instrumental in ensuring that mission-critical applications receive the necessary bandwidth and network resources to operate smoothly, even during periods of heavy traffic.
Furthermore, MPLS enables the creation of virtual private networks (VPNs) over a shared infrastructure, providing secure and reliable communication channels for businesses and organizations. By segregating traffic into distinct VPNs, MPLS helps maintain data confidentiality and integrity, essential for sensitive information transmission.
Overall, MPLS offers a versatile and robust solution for managing and optimizing network traffic in both enterprise and service provider environments. Its ability to streamline data forwarding, support QoS requirements, and facilitate secure communication makes it a cornerstone technology in today's interconnected world.
VPN explanation
A VPN, or Virtual Private Network, is a technology that allows users to create a secure and encrypted connection to another network over the internet. It provides a safe way to browse the internet, access restricted websites, and protect your sensitive data from potential hackers and surveillance.
When you connect to a VPN server, your device creates a secure tunnel through which your data travels. This encrypted connection ensures that your online activities, such as browsing history, passwords, and personal information, remain private and secure from prying eyes.
One of the key benefits of using a VPN is the ability to mask your IP address. This means that your actual location and identity are hidden, allowing you to browse the internet anonymously. This feature is particularly useful when accessing geo-restricted content, such as streaming services and websites that are not available in your region.
Moreover, VPNs are widely used by businesses to allow remote employees to securely access corporate networks and confidential information from anywhere in the world. By encrypting the data transmitted between the employee's device and the company's network, VPNs provide an additional layer of security to prevent data breaches and cyber attacks.
In conclusion, VPNs play a crucial role in ensuring online privacy, security, and freedom. Whether you want to protect your personal information, bypass censorship, or secure your business communications, using a VPN can help you stay safe and anonymous in the digital world.
MPLS vs VPN comparison
MPLS (Multiprotocol Label Switching) and VPN (Virtual Private Network) are two commonly used technologies for establishing secure and efficient network connections. Understanding the differences between MPLS and VPN can help in choosing the right solution for your specific needs.
MPLS is a dedicated connection that uses labels to quickly route data across a network. It is known for its reliability and quality of service, making it ideal for businesses that require stable and high-performance network connections. MPLS works well for large corporations that need to transmit large amounts of data securely between multiple locations.
On the other hand, VPN is a more cost-effective solution that uses the public internet to create a secure connection between remote users and the central network. VPNs are flexible and can be set up quickly, making them suitable for smaller businesses or individuals who need secure access to resources from any location.
In terms of speed and performance, MPLS generally offers better reliability and bandwidth compared to VPN. MPLS is a dedicated network connection, which means users are not competing for bandwidth with other internet traffic. VPN, although cost-effective, may experience slower speeds during peak usage times or when network congestion occurs.
While MPLS provides a higher level of security due to its dedicated connection, VPN can also offer strong encryption protocols to ensure data confidentiality. Businesses handling sensitive information may opt for MPLS for its enhanced security features.
In conclusion, the choice between MPLS and VPN depends on factors such as network requirements, budget, and security considerations. MPLS is suitable for businesses that prioritize performance and reliability, while VPN is a versatile solution for those looking to establish secure connections over the internet.
MPLS advantages
Multiprotocol Label Switching (MPLS) offers numerous advantages for businesses seeking efficient and secure network solutions. One of the primary benefits of MPLS is its ability to prioritize network traffic, ensuring that critical applications receive the necessary bandwidth for optimal performance. This Quality of Service (QoS) feature allows companies to prioritize voice, video, and data traffic based on their importance, reducing latency and ensuring a consistent user experience.
Another advantage of MPLS is its inherent security features. MPLS networks operate within a private environment, isolating traffic from the public internet and minimizing the risk of unauthorized access or data breaches. Additionally, MPLS supports traffic encryption, adding an extra layer of security to sensitive information transmitted across the network.
Scalability is another key benefit of MPLS. As businesses grow and their network requirements evolve, MPLS allows for seamless expansion without significant infrastructure changes. This scalability is particularly valuable for organizations with multiple locations or remote offices, as MPLS can easily accommodate increased bandwidth demands and additional sites.
Furthermore, MPLS offers improved network performance and reliability compared to traditional IP-based networks. By establishing predetermined paths for data packets through label switching, MPLS reduces the risk of network congestion and packet loss, resulting in faster and more reliable data transmission.
Additionally, MPLS enables efficient traffic engineering, allowing network administrators to optimize network utilization and route traffic along the most efficient paths. This dynamic routing capability enhances network performance and resource utilization, ultimately improving overall productivity and user satisfaction.
In conclusion, MPLS provides businesses with a versatile and robust networking solution that offers numerous advantages, including prioritized traffic, enhanced security, scalability, improved performance, and efficient traffic engineering. By leveraging MPLS technology, organizations can optimize their network infrastructure to meet the demands of today's digital business landscape.
VPN benefits
Virtual Private Networks (VPNs) offer a plethora of benefits for users seeking online security, privacy, and freedom. VPNs encrypt your internet connection, ensuring that your data remains secure and protected from potential cyber threats such as hackers, identity thieves, and government surveillance. By masking your IP address and encrypting your online activity, VPNs help you browse the web anonymously, safeguarding your identity and sensitive information from prying eyes.
In addition to enhancing your online security, VPNs also enable you to access geo-restricted content by bypassing censorship and content blocks. Whether you want to stream your favorite movies and TV shows from abroad, access region-locked websites, or circumvent internet restrictions in restrictive countries, a VPN allows you to do so freely and securely. Moreover, VPNs shield your online activities from your internet service provider (ISP), preventing them from monitoring and selling your browsing data to third parties.
Furthermore, VPNs are invaluable tools for remote workers and frequent travelers, as they provide a secure and private connection to public Wi-Fi networks, protecting your sensitive data from cyber threats while on the go. Whether you're working from a coffee shop, airport, or hotel, a VPN ensures that your online communications remain encrypted and secure.
Overall, the benefits of using a VPN are clear: enhanced online security, privacy protection, unrestricted access to global content, and peace of mind while browsing the internet. By investing in a reliable VPN service, you can enjoy a safer, freer, and more secure online experience.
0 notes
Text
what is ethernet vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is ethernet vpn
Ethernet VPN Definition
Ethernet VPN, also known as EVPN, is a cutting-edge technology that revolutionizes the way businesses connect their networks securely and efficiently. In essence, Ethernet VPN is a type of virtual private network (VPN) that utilizes Ethernet connections to link multiple sites or devices over a wide area network (WAN).
Unlike traditional VPNs that rely on Internet Protocol (IP) routing, Ethernet VPN operates at Layer 2 of the OSI model, which means it can transmit data more quickly and securely, making it ideal for large-scale enterprises with high bandwidth requirements.
One of the key advantages of Ethernet VPN is its ability to provide a seamless and transparent extension of a local area network (LAN) across geographically dispersed locations. This means that users can access resources and applications as if they were on the same physical network, regardless of their location.
Furthermore, Ethernet VPN offers enhanced security features such as encryption and authentication protocols to protect data transmitted over the network. This ensures that sensitive information remains confidential and inaccessible to unauthorized users.
Moreover, Ethernet VPNs are highly scalable, allowing businesses to easily expand their network infrastructure as their needs grow. This scalability makes Ethernet VPNs a cost-effective solution for businesses of all sizes, from small startups to large multinational corporations.
Overall, Ethernet VPN represents the future of networking technology, providing businesses with a flexible, secure, and scalable solution for connecting their distributed networks and enabling seamless communication and collaboration across the globe.
Ethernet VPN Architecture
Ethernet VPN (Virtual Private Network) architecture is a robust and versatile solution for connecting geographically dispersed locations within a single network infrastructure. This architecture leverages Ethernet technology to create secure and reliable connections between different sites, providing businesses with efficient communication and data transfer capabilities.
At its core, Ethernet VPN architecture operates by establishing virtual connections over a shared or dedicated Ethernet network. These connections are typically facilitated by service providers who manage the network infrastructure and ensure its performance and security.
One of the key components of Ethernet VPN architecture is the use of MPLS (Multiprotocol Label Switching) technology. MPLS enables the creation of virtual private networks within the larger Ethernet network, allowing for the segregation of traffic and the implementation of quality of service (QoS) policies to prioritize critical data traffic.
Ethernet VPN architecture offers several advantages for businesses. Firstly, it provides a cost-effective solution for connecting multiple locations, eliminating the need for expensive dedicated circuits or leased lines. Additionally, Ethernet VPNs offer scalability, allowing businesses to easily add new sites or increase bandwidth as their network requirements grow.
Security is another crucial aspect of Ethernet VPN architecture. By encrypting data traffic and implementing access control mechanisms, Ethernet VPNs ensure the confidentiality and integrity of sensitive information transmitted between different locations.
Furthermore, Ethernet VPN architecture supports various connectivity options, including point-to-point, point-to-multipoint, and multipoint-to-multipoint configurations, allowing businesses to tailor their network infrastructure to suit their specific requirements.
In conclusion, Ethernet VPN architecture provides businesses with a flexible, scalable, and secure solution for connecting geographically dispersed locations. By leveraging Ethernet technology and MPLS technology, Ethernet VPNs enable efficient communication and data transfer while reducing costs and simplifying network management.
Ethernet VPN Benefits
Ethernet VPN (Virtual Private Network) services offer a myriad of benefits for businesses seeking secure and efficient connectivity solutions. Unlike traditional VPNs, Ethernet VPNs operate at the data link layer (Layer 2) of the OSI model, enabling seamless and secure communication between geographically dispersed locations. Here are some key benefits of Ethernet VPNs:
Scalability: Ethernet VPNs are highly scalable, allowing businesses to easily expand their network infrastructure as their operations grow. Whether adding new branch offices or increasing bandwidth requirements, Ethernet VPNs can accommodate evolving business needs without significant overhaul.
Security: Security is paramount in today's digital landscape. Ethernet VPNs provide a secure platform for transmitting sensitive data between locations over a private network infrastructure. By leveraging advanced encryption protocols and dedicated connections, Ethernet VPNs mitigate the risk of unauthorized access and data breaches.
Reliability: Downtime can be detrimental to business productivity. Ethernet VPNs offer high reliability with guaranteed service level agreements (SLAs) that ensure consistent performance and uptime. With redundant network paths and failover mechanisms, Ethernet VPNs minimize the impact of network disruptions and ensure uninterrupted connectivity.
Cost-effectiveness: Compared to traditional leased lines or MPLS (Multiprotocol Label Switching) networks, Ethernet VPNs offer a cost-effective alternative for interconnecting multiple locations. By consolidating network infrastructure and leveraging existing Ethernet connections, businesses can reduce operational costs while maintaining high-performance connectivity.
Quality of Service (QoS): Ethernet VPNs support Quality of Service (QoS) mechanisms, allowing businesses to prioritize critical applications and ensure optimal performance for voice, video, and data traffic. With QoS capabilities, businesses can maintain consistent network performance even during peak usage periods.
Flexibility: Ethernet VPNs offer flexibility in network design and deployment, allowing businesses to tailor their connectivity solutions to meet specific requirements. Whether implementing point-to-point, point-to-multipoint, or mesh topologies, Ethernet VPNs provide the flexibility needed to adapt to changing business needs.
In conclusion, Ethernet VPNs offer a versatile and reliable solution for interconnecting geographically dispersed locations while ensuring security, scalability, and cost-effectiveness. By leveraging Ethernet VPN services, businesses can enhance their network infrastructure and drive operational efficiency in today's interconnected world.
Ethernet VPN Implementation
Ethernet VPN (Virtual Private Network) is a widely used technology that allows businesses to securely connect multiple locations over a network infrastructure. It provides a cost-effective solution for organizations that need to share data and resources between different sites while maintaining a high level of security and reliability.
Implementing an Ethernet VPN involves setting up a network using Ethernet connections to create a virtual private network. This allows businesses to prioritize network traffic, ensure high-speed connectivity, and maintain data security. By implementing an Ethernet VPN, companies can seamlessly connect their branch offices, data centers, and cloud resources to streamline operations and improve communication between teams.
One of the key benefits of Ethernet VPN implementation is its scalability. Businesses can easily expand their network as their operations grow without incurring significant costs. This scalability makes Ethernet VPN an ideal solution for businesses of all sizes, from small startups to large enterprises.
Furthermore, Ethernet VPN provides a level of security that is essential for businesses operating in today's digital landscape. By encrypting data transmitted over the network, businesses can safeguard sensitive information and protect it from unauthorized access. This ensures that data remains confidential and secure, reducing the risk of cyberattacks and data breaches.
In conclusion, Ethernet VPN implementation offers businesses a reliable, secure, and cost-effective solution for connecting multiple locations and enhancing collaboration across the organization. By leveraging Ethernet VPN technology, businesses can optimize their network infrastructure, improve productivity, and drive business growth in a highly competitive market.
Ethernet VPN Security
Ethernet Virtual Private Network (VPN) security is a critical aspect of ensuring the confidentiality, integrity, and availability of data transmitted over an Ethernet network. VPNs create a secure connection over a public network such as the internet, allowing users to send and receive data as if their devices were directly connected to a private network.
One of the key components of Ethernet VPN security is encryption. Encryption ensures that data transmitted between the sender and the receiver is secure and cannot be intercepted by unauthorized parties. This is achieved through the use of algorithms that scramble the data into an unreadable format, which can only be decrypted by the intended recipient.
Another important aspect of Ethernet VPN security is authentication. Authentication verifies the identity of users and devices before allowing them to access the network. This helps prevent unauthorized access and ensures that only authorized users can send or receive data over the VPN.
Furthermore, Ethernet VPN security also involves data integrity checks. Data integrity ensures that the information sent over the network has not been altered or tampered with during transit. This is achieved by adding a unique identifier to the data, which is used to verify its integrity upon arrival at the destination.
In conclusion, Ethernet VPN security plays a crucial role in safeguarding sensitive information transmitted over Ethernet networks. By implementing encryption, authentication, and data integrity measures, organizations can create a secure and reliable communication channel for their data traffic.
0 notes
Text
what is vpn and its types
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is vpn and its types
VPN Definition
A VPN, or Virtual Private Network, is an essential tool for protecting your online privacy and security. In simple terms, a VPN creates a secure and encrypted connection between your device and the internet. This connection is established by routing your internet traffic through a server owned by the VPN service provider. By doing so, a VPN shields your online activities from prying eyes such as hackers, government agencies, and internet service providers.
One of the primary reasons why individuals and businesses use VPNs is to ensure their sensitive data remains confidential. When you connect to a VPN, all the data transmitted between your device and the internet is encrypted. This means that even if someone manages to intercept your data, they won't be able to decipher it without the encryption key.
Moreover, a VPN allows you to browse the internet anonymously by masking your IP address. Your IP address reveals your location and can be used to track your online activities. By using a VPN, you can choose to connect to servers in different locations, making it appear as though you are browsing from a different country.
In addition to privacy and security benefits, VPNs also enable users to bypass geo-restrictions and censorship. For example, you can access region-locked content on streaming platforms or bypass internet censorship in countries with restricted online access.
Overall, a VPN is a powerful tool that safeguards your online presence, protects your sensitive data, and grants you unrestricted access to the global internet. It is a must-have for anyone looking to maintain their privacy and security in the digital age.
Types of VPN
A VPN, or Virtual Private Network, is a technology that allows you to create a secure and encrypted connection over a less secure network, such as the internet. There are several types of VPNs available, each with its unique characteristics and use cases.
Remote Access VPN:
Remote access VPNs are one of the most common types used by individuals and businesses. This type of VPN allows remote users to connect to a private network from any location. It provides a secure gateway for users to access resources on the network as if they were directly connected to it.
Site-to-Site VPN:
Site-to-Site VPNs are often used by businesses to connect multiple offices or networks located in different geographical locations. This type of VPN establishes an encrypted connection between two or more networks, allowing them to communicate securely over the internet.
Mobile VPN:
Mobile VPNs are designed for mobile devices such as smartphones and tablets. They enable users to securely connect to a network while on the go, ensuring that their data remains protected even when using public Wi-Fi hotspots.
SSL VPN:
SSL VPNs provide secure remote access to web applications, files, and other resources using the Secure Sockets Layer (SSL) protocol. This type of VPN is typically easier to set up and use since it doesn't require the installation of specialized client software.
MPLS VPN:
MPLS VPNs are often used by service providers to securely connect multiple locations within a private network. This type of VPN leverages Multiprotocol Label Switching (MPLS) to route traffic between different sites, ensuring fast and reliable communication.
In conclusion, the different types of VPNs cater to various needs and requirements, offering secure connectivity solutions for individuals and organizations alike. Whether you are looking to protect your online privacy, access restricted content, or connect multiple offices, there is a VPN type that suits your specific needs.
VPN Protocols
VPN protocols are essential for safeguarding online privacy and security. These protocols determine how data is transmitted between devices and servers through the virtual private network (VPN). Understanding the different VPN protocols can help users make informed decisions on which protocol to choose based on their specific needs.
One commonly used VPN protocol is OpenVPN, known for its strong security features and open-source nature. It supports various encryption algorithms and is compatible with a wide range of devices and platforms. Another popular protocol is IPSec (Internet Protocol Security), which operates at the network layer and offers robust encryption and authentication mechanisms.
SSTP (Secure Socket Tunneling Protocol) is favored for its ability to bypass firewalls and proxy servers, making it a suitable choice for users facing network restrictions. L2TP/IPSec (Layer 2 Tunnel Protocol with IPSec) combines the best features of L2TP and IPSec to provide high security and stable connectivity.
For users seeking a blend of security and speed, WireGuard is a modern VPN protocol gaining popularity for its efficient performance and streamlined code. It utilizes state-of-the-art cryptographic protocols to ensure data protection while delivering fast connection speeds.
Ultimately, the choice of VPN protocol depends on the user's priorities, whether it be stringent security measures, bypassing restrictions, or achieving optimal speed performance. By understanding the key characteristics of each protocol, users can select the most suitable option to enhance their online privacy and security.
VPN Encryption
VPN Encryption: Safeguarding Your Online Privacy
With the increasing threats to online privacy and security, the use of Virtual Private Networks (VPNs) has become more crucial than ever. VPN encryption plays a pivotal role in ensuring that your sensitive data remains secure while you browse the internet.
VPN encryption works by creating a secure tunnel between your device and the VPN server. This encryption process involves encoding your data to make it indecipherable to anyone trying to intercept it. By utilizing complex algorithms, VPNs ensure that your online activities, such as browsing history, passwords, and personal information, are shielded from prying eyes.
There are several encryption protocols used by VPNs, including OpenVPN, IPSec, L2TP, and SSTP, among others. These protocols vary in terms of strength and speed, with OpenVPN being one of the most secure options available. It is essential to choose a VPN provider that offers robust encryption protocols to enhance the protection of your data.
In addition to securing your data, VPN encryption also allows you to bypass geo-restrictions and censorship. By masking your IP address and encrypting your connection, VPNs enable you to access region-locked content and browse the internet freely and anonymously.
However, it is important to note that while VPN encryption is a potent tool for safeguarding your online privacy, it is not foolproof. It is crucial to select a reputable VPN provider with a strict no-logs policy to ensure that your data is not stored or compromised in any way.
In conclusion, VPN encryption is a vital component of maintaining your online security and anonymity. By employing robust encryption protocols and choosing a trustworthy VPN service, you can enjoy a safer and more private browsing experience in today's digital age.
VPN Applications
VPN applications are tools that have become increasingly popular in today's digital world. VPN stands for Virtual Private Network, and these applications allow users to secure their internet connection, protect their privacy, and access geo-restricted content.
One of the main reasons people use VPN applications is to enhance their online security and privacy. By using a VPN, all internet traffic is encrypted, making it difficult for hackers or third parties to intercept sensitive information such as passwords, financial details, or personal data. This encryption also ensures that users can browse the internet anonymously, without their online activities being tracked by advertisers or internet service providers.
Additionally, VPN applications enable users to bypass geo-restrictions and access content that may be blocked in their region. Whether it's streaming services, social media platforms, or websites, a VPN allows users to change their virtual location and appear as if they are browsing from a different country, granting them access to otherwise restricted content.
Moreover, VPN applications are valuable tools for individuals traveling or working remotely. By connecting to a VPN server, users can ensure a secure and private internet connection, even when using public Wi-Fi networks in airports, cafes, or hotels.
Overall, VPN applications offer a wide range of benefits, from protecting online privacy and security to accessing unrestricted content. As internet users become more aware of the importance of safeguarding their digital presence, the popularity and usage of VPN applications continue to grow.
0 notes
Text
what is multicast vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is multicast vpn
Multicast VPN Definition
Multicast VPN, also known as Multicast Virtual Private Network, is a technology that allows efficient and secure distribution of multicast traffic within a Virtual Private Network (VPN). This technology is commonly used in modern networks to replicate and transport multicast traffic across different sites while maintaining privacy and security.
In traditional multicast networks, multicast traffic is forwarded to all network segments, leading to unnecessary bandwidth consumption and potential security risks. Multicast VPN addresses these challenges by enabling the creation of private multicast groups within a VPN, ensuring that traffic is only delivered to intended recipients.
One of the key benefits of Multicast VPN is its ability to optimize network bandwidth utilization by eliminating unnecessary traffic replication. By using a combination of multicast routing protocols and VPN technologies, Multicast VPN ensures that multicast traffic is only forwarded to specific network segments that require the data, reducing network congestion and improving overall network performance.
Furthermore, Multicast VPN enhances network security by isolating multicast traffic within the VPN, protecting sensitive data from unauthorized access or interception. This is particularly important for organizations that deal with confidential information and require a secure network environment to communicate efficiently.
In conclusion, Multicast VPN is a powerful technology that enables organizations to efficiently distribute multicast traffic within a secure and private network environment. By reducing bandwidth consumption, enhancing network performance, and improving security, Multicast VPN plays a crucial role in modern networking infrastructure.
Multicast VPN Protocols
Multicast VPN protocols are crucial in optimizing network efficiency and enabling seamless communication across distributed networks. These protocols facilitate the transmission of multicast traffic over VPN (Virtual Private Network) infrastructures, ensuring that data reaches intended recipients efficiently and securely.
One of the key multicast VPN protocols is Protocol Independent Multicast (PIM). PIM operates at the network layer and is designed to efficiently route multicast traffic within a VPN environment. It dynamically builds multicast distribution trees to ensure that data is delivered only to the interested receivers, reducing unnecessary traffic and conserving network bandwidth.
Another important protocol is the Next Generation Multicast VPN (NG-MVPN). NG-MVPN enhances multicast support in VPN environments by providing a more scalable and efficient solution compared to traditional approaches. It leverages BGP (Border Gateway Protocol) to distribute multicast routing information, enabling optimal multicast traffic delivery across VPN boundaries.
MPLS (Multiprotocol Label Switching) Multicast VPN is another widely used protocol that utilizes MPLS technology to facilitate multicast traffic across VPNs. By assigning labels to multicast packets, MPLS enables efficient routing and forwarding of multicast traffic within VPN networks, improving network performance and scalability.
Overall, multicast VPN protocols play a critical role in modern networking environments by enabling efficient and secure multicast communication across distributed networks. Whether it's PIM, NG-MVPN, or MPLS Multicast VPN, organizations have a range of protocols to choose from based on their specific requirements for scalability, efficiency, and security. By implementing multicast VPN protocols, businesses can optimize their network infrastructure to support the growing demands of multicast communication in today's digital landscape.
Multicast VPN Architecture
Multicast VPN Architecture: Enhancing Network Efficiency and Security
Multicast VPN (MVPN) architecture is a sophisticated framework designed to optimize network efficiency and security in modern communication infrastructures. It addresses the challenges of transmitting data to multiple recipients efficiently while ensuring confidentiality and integrity.
At its core, MVPN employs a combination of multicast and VPN technologies to enable the scalable distribution of data to multiple receivers across a network. It utilizes IP multicast protocols to efficiently deliver data streams to multiple endpoints simultaneously, reducing network congestion and bandwidth utilization.
One of the key components of MVPN architecture is the concept of provider tunnels, which establish secure communication paths between different segments of the network. These tunnels facilitate the transmission of multicast traffic across the VPN infrastructure, ensuring that data remains confidential and protected from unauthorized access.
Another crucial aspect of MVPN architecture is the implementation of multicast distribution trees. These trees define the paths that multicast traffic takes within the network, optimizing the delivery process and minimizing latency. By dynamically adjusting these distribution trees based on network conditions and traffic patterns, MVPN ensures efficient and reliable data transmission.
Furthermore, MVPN architecture offers robust security features to safeguard sensitive information. It incorporates encryption mechanisms to protect data in transit, preventing eavesdropping and unauthorized interception. Additionally, access controls and authentication mechanisms ensure that only authorized users can access multicast streams, enhancing overall network security.
Overall, multicast VPN architecture provides a scalable and secure solution for distributing data to multiple recipients efficiently. By combining multicast and VPN technologies, it addresses the unique challenges of modern communication networks, offering enhanced efficiency, scalability, and security.
Multicast VPN Applications
Multicast VPN (Virtual Private Network) applications are crucial tools for businesses and organizations that rely on efficient and secure communication over networks. Multicast VPN technology enables the transmission of data simultaneously to multiple recipients, optimizing bandwidth usage and ensuring seamless delivery of content.
One primary application of Multicast VPN is in the realm of video conferencing and live streaming. In scenarios where a large number of users need to access live events or participate in video conferences, Multicast VPN ensures efficient delivery of video streams without overwhelming the network. This is particularly beneficial for companies conducting webinars, training sessions, or live broadcasts, where real-time interaction and engagement are paramount.
Another significant application is in content distribution networks (CDNs). Multicast VPN allows CDNs to efficiently deliver multimedia content, such as video streams, software updates, or large files, to multiple users simultaneously. By reducing network congestion and optimizing bandwidth utilization, Multicast VPN enhances the overall performance and reliability of content delivery, ensuring a seamless user experience even during peak traffic periods.
In addition to video conferencing and content distribution, Multicast VPN finds applications in industries such as finance, healthcare, and education, where secure and efficient communication of data is essential. Whether it's transmitting financial data to multiple branches securely or facilitating collaborative medical consultations among healthcare professionals, Multicast VPN provides a reliable and scalable solution for diverse networking needs.
Overall, Multicast VPN applications play a vital role in optimizing network performance, enhancing security, and facilitating seamless communication across various industries. As businesses and organizations continue to rely on digital platforms for collaboration and information exchange, the importance of Multicast VPN technology is expected to grow, driving innovation and efficiency in network communication.
Multicast VPN Advantages
A Multicast Virtual Private Network (VPN) offers several advantages for businesses looking to enhance their network communications. One of the key benefits of Multicast VPN is its ability to efficiently deliver bulk data to multiple recipients simultaneously. Instead of sending separate data streams to individual recipients, Multicast VPN allows for the transmission of data packets to be shared among multiple users in one go. This is particularly beneficial for applications such as video streaming or online gaming, where the same data needs to be distributed to multiple users at the same time.
Another advantage of Multicast VPN is its cost-effectiveness. By minimizing bandwidth usage and network congestion, Multicast VPN helps reduce network costs and improve overall network performance. This is especially important for businesses that rely on real-time data transmission or large-scale content delivery.
Furthermore, Multicast VPN enhances network security by enabling secure group communication within a closed user group. Data encryption and authentication protocols ensure that sensitive information remains protected and only accessible to authorized users. This makes Multicast VPN an ideal solution for businesses handling confidential data or conducting secure communications over their network.
Overall, Multicast VPN offers efficiency, cost savings, and enhanced security for businesses seeking to optimize their network communications. By leveraging the advantages of Multicast VPN, organizations can streamline their data delivery processes, improve network performance, and enhance overall cybersecurity measures.
0 notes
Text
how does mpls vpn work
🔒🌍✨ Erhalten Sie 3 Monate GRATIS VPN - Sicherer und privater Internetzugang weltweit! Hier klicken ✨🌍🔒
how does mpls vpn work
MPLS Technologie
MPLS (Multiprotocol Label Switching) ist eine Technologie, die in modernen Netzwerken weit verbreitet ist und zur effizienten und sicheren Übertragung von Daten verwendet wird. Diese Technologie ermöglicht es, Datenpakete anhand von Labels schnell und zuverlässig durch ein Netzwerk zu leiten.
Ein Hauptvorteil von MPLS ist die Möglichkeit, verschiedene Arten von Datenverkehr über ein gemeinsames Netzwerk zu transportieren, ohne dass dabei die Leistung beeinträchtigt wird. Durch die Verwendung von Labels können Datenpakete den optimalen Weg durch das Netzwerk finden, was zu einer effizienten Nutzung der verfügbaren Bandbreite führt.
Darüber hinaus bietet MPLS auch eine höhere Sicherheit, da Datenpakete innerhalb des Netzwerks isoliert und vor unerwünschten Zugriffen geschützt werden können. Dies ist besonders wichtig in Unternehmen, die vertrauliche Informationen übermitteln müssen.
Durch die Implementierung von MPLS können Unternehmen von einer verbesserten Netzwerkleistung, höherer Sicherheit und einfacheren Verwaltung profitieren. Diese Technologie wird daher weiterhin eine wichtige Rolle in der Entwicklung moderner Netzwerke spielen und dazu beitragen, dass Datenübertragungen effizient und sicher erfolgen.
VPN Funktionsweise
Ein Virtual Private Network (VPN) ist ein Dienst, der Ihre Internetverbindung verschlüsselt und Ihnen Anonymität, Sicherheit und Privatsphäre im Internet bietet. Aber wie funktioniert ein VPN eigentlich?
Die Funktionsweise eines VPNs basiert auf der Erstellung einer sicheren Verbindung zwischen Ihrem Gerät und einem Remote-Server, der von Ihrem VPN-Anbieter bereitgestellt wird. Wenn Sie das VPN aktivieren, wird der gesamte Datenverkehr von Ihrem Gerät über diesen verschlüsselten Tunnel geleitet, was bedeutet, dass Dritte, wie beispielsweise Ihr Internetdienstanbieter oder Hacker, nicht in der Lage sind, Ihre Aktivitäten online zu verfolgen.
Der VPN-Client auf Ihrem Gerät verschlüsselt die Daten, bevor sie über das Internet gesendet werden. Dies wird mithilfe verschiedener Verschlüsselungsprotokolle erreicht, die sicherstellen, dass Ihre Daten vor neugierigen Blicken geschützt sind.
Ein weiterer wichtiger Aspekt der VPN-Funktionsweise ist die Möglichkeit, Ihre virtuelle Position zu ändern. Indem Sie eine Verbindung zu einem VPN-Server in einem anderen Land herstellen, können Sie den Anschein erwecken, als ob Sie sich tatsächlich an diesem Standort befinden. Dies ist besonders hilfreich, wenn es um den Zugriff auf geo-blockierte Inhalte oder das Umgehen von Zensur in bestimmten Ländern geht.
Insgesamt bietet ein VPN eine vielschichtige Funktionsweise, die Ihre Online-Privatsphäre schützt, Ihre Verbindung sichert und Ihnen dabei hilft, Ihre wahre Identität zu verbergen. Es ist ein unverzichtbares Tool in der heutigen vernetzten Welt, um sicher im Internet zu surfen.
Netzwerk Routing
Netzwerk Routing bezeichnet den Prozess des Weiterleitens von Datenpaketen von einer Quelle zu einem Ziel innerhalb eines Netzwerks. Dieser Vorgang wird durch spezielle Geräte wie Router ermöglicht, die den optimalen Weg für die Daten bestimmen und sie entlang dieses Pfades weiterleiten.
Es gibt verschiedene Arten von Netzwerk Routing-Protokollen, die je nach den Anforderungen und der Komplexität des Netzwerks eingesetzt werden. Eines der bekanntesten Routing-Protokolle ist das Border Gateway Protocol (BGP), das häufig in großen Unternehmensnetzwerken und im Internet verwendet wird.
Das Internet besteht aus zahlreichen miteinander verbundenen Netzwerken, und das Routing spielt eine entscheidende Rolle bei der Gewährleistung der Konnektivität und der effizienten Datenübertragung zwischen diesen Netzwerken. Durch das Routing werden Datenpakete auf dem schnellsten und sichersten Weg zu ihrem Bestimmungsort geleitet, wodurch eine reibungslose Kommunikation und Datenübertragung gewährleistet wird.
Netzwerk Routing kann entweder statisch oder dynamisch konfiguriert werden. Statisches Routing erfordert die manuelle Konfiguration von Routen, während dynamisches Routing automatisch die besten verfügbaren Wege für die Datenübertragung ermittelt und anpasst.
Insgesamt spielt das Netzwerk Routing eine Schlüsselrolle bei der effizienten Datenübertragung und der Gewährleistung einer reibungslosen Kommunikation in modernen Netzwerken. Es ist ein essenzieller Bestandteil der Netzwerkinfrastruktur und ermöglicht die zuverlässige Übertragung von Daten in lokalen Netzwerken sowie im Internet.
Datenpriorisierung
Bei der Datenpriorisierung handelt es sich um einen wichtigen Prozess im Bereich der Datenverarbeitung und -analyse. Durch die Priorisierung von Daten können Unternehmen sicherstellen, dass wichtige Informationen zuerst verarbeitet und genutzt werden, um fundierte Geschäftsentscheidungen zu treffen.
Ein effektives Datenpriorisierungssystem kann Unternehmen dabei unterstützen, ihre Ressourcen optimal zu nutzen und sicherzustellen, dass wichtige Daten in Echtzeit verfügbar sind. Dies kann dazu beitragen, Engpässe bei der Datenverarbeitung zu vermeiden und die Effizienz der gesamten Organisation zu steigern.
Es gibt verschiedene Methoden der Datenpriorisierung, darunter die automatische Klassifizierung von Daten nach ihrer Relevanz und Dringlichkeit, die Einrichtung von Alarmen für wichtige Ereignisse oder die Festlegung von Prioritäten basierend auf vordefinierten Kriterien.
Durch die Implementierung eines klaren Datenpriorisierungssystems können Unternehmen auch sicherstellen, dass ihre Daten sicher und geschützt sind. Indem sensible Daten priorisiert und entsprechend geschützt werden, können Unternehmen die Einhaltung von Datenschutzbestimmungen gewährleisten und das Risiko von Datenschutzverletzungen minimieren.
Insgesamt spielt die Datenpriorisierung eine entscheidende Rolle für den Erfolg eines Unternehmens im digitalen Zeitalter. Indem Daten effektiv priorisiert und genutzt werden, können Unternehmen ihre Wettbewerbsfähigkeit steigern und ein besseres Verständnis für ihre Kunden und Märkte gewinnen.
Sicherheitsprotokolle
Sicherheitsprotokolle sind wichtige Mechanismen, die zum Schutz von Daten und Informationen in verschiedenen digitalen Systemen eingesetzt werden. Diese Protokolle dienen dazu, die Sicherheit und Integrität von Kommunikationen und Transaktionen zu gewährleisten und unbefugten Zugriff auf vertrauliche Daten zu verhindern.
Es gibt verschiedene Arten von Sicherheitsprotokollen, die je nach Bedarf und Anforderungen implementiert werden können. Ein häufig genutztes Protokoll ist beispielsweise das SSL/TLS-Protokoll, das hauptsächlich für die sichere Übertragung von Daten im Internet eingesetzt wird. Durch die Verschlüsselung von Daten wird sichergestellt, dass Informationen während der Übertragung nicht von Dritten abgefangen oder manipuliert werden können.
Ein weiteres wichtiges Sicherheitsprotokoll ist das VPN-Protokoll, das eine sichere Verbindung über öffentliche Netzwerke herstellt und so den Datenschutz gewährleistet. Durch die Verschlüsselung des Datenverkehrs wird verhindert, dass sensible Informationen von Hackern oder anderen böswilligen Akteuren abgefangen werden können.
Zusätzlich zu diesen Protokollen gibt es auch Sicherheitsstandards wie beispielsweise die ISO/IEC 27001-Zertifizierung, die Unternehmen dabei unterstützt, ein umfassendes Informationssicherheitsmanagement umzusetzen.
Insgesamt sind Sicherheitsprotokolle unerlässlich für den Schutz sensibler Daten und die Wahrung der Privatsphäre in einer zunehmend digitalisierten Welt. Durch die Implementierung geeigneter Protokolle können Organisationen sicherstellen, dass ihre Daten vor Bedrohungen geschützt sind und sie das Vertrauen ihrer Kunden und Partner bewahren.
0 notes
Text
how to establish vpn connection between two computers
🔒🌍✨ Erhalten Sie 3 Monate GRATIS VPN - Sicherer und privater Internetzugang weltweit! Hier klicken ✨🌍🔒
how to establish vpn connection between two computers
VPN-Protokolle
VPN-Protokolle sind ein wesentlicher Bestandteil von Virtual Private Networks (VPNs). Sie dienen dazu, die Sicherheit und Privatsphäre der übertragenen Daten zu gewährleisten. Es gibt verschiedene Arten von VPN-Protokollen, die jeweils unterschiedliche Funktionen und Eigenschaften haben.
Ein bekanntes VPN-Protokoll ist das Point-to-Point Tunneling Protocol (PPTP). Es ist einfach einzurichten und eignet sich gut für den persönlichen Gebrauch. Allerdings wird PPTP oft als unsicher angesehen, da es Schwachstellen aufweisen kann.
Ein weiteres weit verbreitetes VPN-Protokoll ist das Layer 2 Tunneling Protocol (L2TP). Es bietet eine hohe Sicherheit, da es die Daten mit starken Verschlüsselungstechniken schützt. Allerdings kann L2TP aufgrund der hohen Sicherheitsstufe langsamer sein als andere Protokolle.
Das Secure Socket Tunneling Protocol (SSTP) ist ein VPN-Protokoll, das von Microsoft entwickelt wurde. Es nutzt den SSL/TLS-Standard für die Verschlüsselung und bietet eine sichere Verbindung, die besonders für Windows-Benutzer geeignet ist.
Das OpenVPN-Protokoll ist eines der sichersten und vielseitigsten VPN-Protokolle. Es ist Open Source und wird daher häufig von VPN-Anbietern verwendet. OpenVPN unterstützt verschiedene Verschlüsselungsstandards und bietet eine hohe Sicherheit sowie eine gute Leistung.
Insgesamt gibt es eine Vielzahl von VPN-Protokollen, die jeweils ihre eigenen Vor- und Nachteile haben. Bei der Auswahl eines VPN-Anbieters ist es wichtig, das Protokoll zu berücksichtigen, das am besten zu den individuellen Anforderungen an Sicherheit, Geschwindigkeit und Kompatibilität passt.
Standortvernetzung
Die Standortvernetzung ist ein wichtiger Aspekt für Unternehmen, die mehrere Standorte miteinander verbinden müssen, um einen reibungslosen Datenaustausch und eine effiziente Kommunikation zu gewährleisten. Durch die Vernetzung der Standorte können Mitarbeiter an verschiedenen Orten nahtlos zusammenarbeiten und auf gemeinsame Ressourcen zugreifen.
Es gibt verschiedene Technologien und Ansätze für die Standortvernetzung, darunter Virtual Private Networks (VPNs), Multiprotocol Label Switching (MPLS) und Software-defined Wide Area Networks (SD-WAN). Jede dieser Technologien hat ihre eigenen Vor- und Nachteile, je nach den Anforderungen und dem Budget des Unternehmens.
VPNs sind eine beliebte Lösung für die Standortvernetzung, da sie eine sichere und kostengünstige Möglichkeit bieten, um Standorte über das öffentliche Internet miteinander zu verbinden. MPLS hingegen bietet eine dedizierte Verbindung zwischen den Standorten und kann eine bessere Leistung und Qualitätssicherung bieten, ist aber in der Regel teurer.
SD-WAN ist eine aufstrebende Technologie, die es Unternehmen ermöglicht, ihre Weitverkehrsnetze über eine zentralisierte, softwaregesteuerte Plattform zu verwalten. SD-WAN kann die Netzwerkflexibilität verbessern, die Kosten senken und die Bereitstellung neuer Standorte vereinfachen.
Insgesamt ist die Standortvernetzung ein entscheidender Faktor für den Geschäftserfolg in einer zunehmend vernetzten Welt. Durch die Auswahl der richtigen Technologie und die sorgfältige Planung können Unternehmen sicherstellen, dass ihre Standorte effektiv miteinander verbunden sind und reibungslos zusammenarbeiten können.
VPN-Konfiguration
Eine VPN-Konfiguration oder Virtual Private Network-Konfiguration ist ein wichtiger Bestandteil, um die Sicherheit und Privatsphäre Ihrer Internetverbindung zu gewährleisten. Durch die Konfiguration eines VPN-Dienstes können Sie Ihre Online-Aktivitäten verschlüsseln und anonymisieren, um Ihre Daten vor neugierigen Blicken zu schützen.
Die VPN-Konfiguration beinhaltet normalerweise die Auswahl eines VPN-Anbieters, die Installation der entsprechenden Software und die Einrichtung Ihrer Verbindung. Es ist wichtig, einen vertrauenswürdigen und zuverlässigen VPN-Anbieter auszuwählen, der eine starke Verschlüsselung und keine Protokollierung der Nutzeraktivitäten anbietet. Nach der Auswahl des Anbieters müssen Sie die Software herunterladen und auf Ihrem Gerät installieren. Die meisten VPN-Dienste sind mit verschiedenen Betriebssystemen und Geräten kompatibel, so dass Sie Ihre Verbindung auf Ihrem Computer, Smartphone oder Tablet einrichten können.
Sobald die Software installiert ist, müssen Sie sich mit den Anmeldedaten Ihres VPN-Kontos einloggen und einen Serverstandort auswählen, über den Ihre Verbindung geleitet wird. Ein VPN ermöglicht es Ihnen, Ihre virtuelle Position zu ändern und auf geo-blockierte Inhalte zuzugreifen, indem es vortäuscht, dass Sie sich in einem anderen Land befinden.
Zusammenfassend ist die VPN-Konfiguration ein entscheidender Schritt, um Ihre Online-Privatsphäre zu schützen und sicher im Internet zu surfen. Indem Sie einen VPN-Dienst nutzen, können Sie Ihre Verbindung absichern und Ihre persönlichen Daten vor potenziellen Bedrohungen schützen.
Sichere Verbindung
Eine sichere Verbindung im Internet ist von entscheidender Bedeutung, um die Privatsphäre und die Daten der Benutzer zu schützen. Mit einer sicheren Verbindung wird sichergestellt, dass die übertragenen Informationen verschlüsselt sind und nicht von Dritten abgefangen oder manipuliert werden können.
Es gibt verschiedene Technologien, die zur Sicherung von Verbindungen im Internet eingesetzt werden, darunter SSL (Secure Sockets Layer) und TLS (Transport Layer Security). Diese Protokolle sorgen dafür, dass die Daten zwischen dem Benutzer und der Website verschlüsselt werden, so dass sie nicht von Hackern oder anderen böswilligen Personen gelesen werden können.
Eine sichere Verbindung wird besonders wichtig, wenn sensitive Daten wie persönliche Informationen, Passwörter, Kreditkarteninformationen oder andere vertrauliche Daten über das Internet übertragen werden. Ohne eine sichere Verbindung besteht die Gefahr, dass diese Daten gestohlen oder missbraucht werden können.
Es ist daher ratsam, beim Surfen im Internet auf sichere Verbindungen zu achten, insbesondere beim Eingeben von sensiblen Daten. Websites mit einer sicheren Verbindung sind in der Regel durch ein Schlosssymbol in der Adressleiste gekennzeichnet und beginnen mit "https://" anstelle von "http://".
Durch die Nutzung von sicheren Verbindungen im Internet können Benutzer ihre Privatsphäre schützen und sicherstellen, dass ihre Daten geschützt sind. Es ist wichtig, sich der Bedeutung einer sicheren Verbindung bewusst zu sein und entsprechende Maßnahmen zu ergreifen, um die Sicherheit im Internet zu gewährleisten.
Remote-Zugriff
Remote-Zugriff bezieht sich auf die Möglichkeit, von einem entfernten Standort aus auf ein Computersystem oder ein Netzwerk zuzugreifen. Dies kann durch verschiedene Technologien wie VPNs, Fernwartungssoftware oder Remote-Desktop-Verbindungen ermöglicht werden.
Es gibt viele Vorteile beim Remote-Zugriff. Zum Beispiel können Mitarbeiter flexibler arbeiten, da sie nicht an einen festen Arbeitsplatz gebunden sind. Dies kann zu erhöhter Produktivität und Zufriedenheit am Arbeitsplatz führen. Zudem ermöglicht Remote-Zugriff Unternehmen, Fachkräfte aus der Ferne einzustellen, ohne dass sie vor Ort sein müssen.
Sicherheit ist jedoch ein wichtiger Aspekt beim Remote-Zugriff. Es ist entscheidend, dass angemessene Sicherheitsmaßnahmen wie starke Passwörter, Zwei-Faktor-Authentifizierung und Verschlüsselung implementiert werden, um Daten vor unbefugten Zugriffen zu schützen.
Für viele Unternehmen ist Remote-Zugriff in der heutigen digitalen Welt unerlässlich. Insbesondere während der globalen Pandemie hat sich gezeigt, wie wichtig es ist, flexibel auf Veränderungen reagieren zu können und den Mitarbeitern die Möglichkeit zu geben, von überall aus zu arbeiten.
Insgesamt bietet Remote-Zugriff viele Chancen und Herausforderungen. Durch eine sorgfältige Planung und Umsetzung können Unternehmen jedoch von den Vorteilen dieser Technologie profitieren und ihre Effizienz steigern.
0 notes
Text
which vpn type is a service provider managed vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
which vpn type is a service provider managed vpn
Managed VPN service
A managed VPN service offers businesses a secure and reliable way to connect their remote offices, employees, and clients over the internet. Unlike traditional VPNs, which require extensive setup and maintenance, managed VPN services are fully outsourced to a third-party provider, allowing businesses to focus on their core operations while enjoying the benefits of a secure network.
One of the key advantages of a managed VPN service is its ease of use. With a managed solution, businesses don't need to worry about configuring servers, managing encryption protocols, or troubleshooting connectivity issues. Instead, everything is handled by the service provider, from initial setup to ongoing maintenance and support.
Security is another major benefit of using a managed VPN service. These services employ advanced encryption techniques to protect data as it travels between devices and across networks. Additionally, many providers offer features such as intrusion detection, malware protection, and multi-factor authentication to further enhance security and safeguard against cyber threats.
Managed VPN services also offer scalability and flexibility, allowing businesses to easily adjust their network capacity and resources as needed. Whether adding new users, expanding into new geographic regions, or integrating with cloud-based applications, a managed VPN service can adapt to the changing needs of a growing business.
Furthermore, managed VPN services often come with dedicated support teams that are available around the clock to assist with any issues or concerns. This level of support ensures that businesses can rely on their VPN infrastructure to stay connected and productive, even in the face of technical challenges.
In conclusion, a managed VPN service offers businesses a convenient, secure, and scalable solution for connecting their distributed workforce and resources. By outsourcing VPN management to a trusted provider, businesses can streamline operations, enhance security, and focus on achieving their business objectives.
Service provider-controlled VPN
A service provider-controlled VPN, also known as an MPLS VPN (Multiprotocol Label Switching Virtual Private Network), is a type of VPN that allows businesses to securely connect multiple locations over a service provider's network. This type of VPN is often used by businesses to connect offices in different locations or to provide secure access to company resources for remote employees.
In a service provider-controlled VPN, the service provider manages the VPN infrastructure, including the routers, switches, and other networking equipment. This means that businesses do not have to worry about maintaining the VPN infrastructure themselves, which can save time and resources.
One of the key advantages of a service provider-controlled VPN is that it offers a high level of security. Service providers use encryption and other security measures to protect data as it travels over the VPN, reducing the risk of data breaches or unauthorized access.
Another benefit of a service provider-controlled VPN is that it can offer better performance than traditional VPNs. Service providers can prioritize traffic on their networks to ensure that critical applications have the bandwidth and low latency they need to operate effectively.
Overall, a service provider-controlled VPN can be a valuable tool for businesses looking to connect multiple locations or provide secure remote access to company resources. By outsourcing the management of the VPN infrastructure to a service provider, businesses can focus on their core operations while benefitting from a secure and reliable network connection.
Outsourced VPN management
Outsourced VPN management has emerged as a strategic solution for businesses looking to enhance their cybersecurity posture while streamlining operations. VPNs, or Virtual Private Networks, play a crucial role in safeguarding sensitive data and ensuring secure communication channels, particularly in today's digital landscape marked by increased cyber threats.
Outsourcing VPN management involves entrusting the configuration, maintenance, and monitoring of VPN infrastructure to third-party service providers. This arrangement offers several advantages for businesses of all sizes. Firstly, it allows organizations to leverage the expertise of seasoned professionals who specialize in cybersecurity and network management. These experts possess in-depth knowledge of VPN technologies and can implement best practices to fortify defenses against cyber threats.
Furthermore, outsourcing VPN management enables businesses to focus on their core competencies without the burden of managing complex network infrastructure internally. This can lead to cost savings and increased operational efficiency as resources are allocated more effectively.
Another benefit of outsourced VPN management is scalability. As businesses grow or encounter fluctuating demand, outsourcing providers can quickly adapt VPN configurations to accommodate changing needs. This flexibility ensures that organizations can scale their cybersecurity capabilities without experiencing downtime or compromising on security.
Additionally, outsourcing VPN management can enhance regulatory compliance. Many industries are subject to stringent data protection regulations, and working with experienced providers can help ensure adherence to compliance requirements, reducing the risk of costly fines and reputational damage.
In conclusion, outsourced VPN management offers businesses a strategic approach to bolstering cybersecurity defenses while optimizing resources and maintaining compliance. By leveraging the expertise of external providers, organizations can enhance their security posture, streamline operations, and focus on driving business growth.
Provider-managed virtual private network
A provider-managed virtual private network (VPN) offers businesses a secure and reliable solution for connecting remote offices, employees, and resources across various locations. Unlike self-managed VPNs, where the burden of setup, maintenance, and security falls on the organization itself, a provider-managed VPN places these responsibilities in the hands of a trusted third-party service provider.
One of the primary advantages of a provider-managed VPN is the expertise and resources it brings to the table. Service providers specialize in network infrastructure and security, ensuring that VPN connections are optimized for performance and protected against cyber threats. This allows businesses to focus on their core operations without worrying about the technical complexities of managing a VPN.
Additionally, provider-managed VPNs often come with service level agreements (SLAs) that guarantee uptime, performance, and support responsiveness. These SLAs provide businesses with peace of mind, knowing that their critical network connections are backed by contractual commitments from the provider.
Another benefit is scalability. Provider-managed VPNs can easily accommodate growing business needs by adjusting bandwidth, adding new locations, or implementing additional security measures as required. This scalability is particularly valuable for businesses experiencing rapid growth or fluctuations in demand.
Security is paramount in any VPN solution, and provider-managed VPNs excel in this area. Providers employ advanced encryption protocols, multi-factor authentication, and intrusion detection/prevention systems to safeguard data in transit. They also stay abreast of the latest security threats and best practices, ensuring that VPN connections remain resilient against evolving cyber threats.
In conclusion, a provider-managed VPN offers businesses a comprehensive and hassle-free solution for establishing secure network connections between dispersed locations and resources. By leveraging the expertise, resources, and scalability of a trusted service provider, organizations can enhance productivity, streamline operations, and mitigate security risks associated with remote connectivity.
Vendor-administered VPN service
Vendor-administered VPN services offer businesses a convenient and secure solution for protecting their sensitive data and ensuring seamless remote access for employees. In today's digital landscape, where cyber threats are increasingly sophisticated, utilizing a VPN service provided by a trusted vendor can be crucial for safeguarding confidential information.
One of the primary benefits of opting for a vendor-administered VPN service is the expertise and infrastructure that comes with it. Vendors specializing in VPN solutions invest heavily in robust encryption protocols, server networks, and security measures, which may surpass what an individual organization can afford or manage internally. This ensures that data transmitted through the VPN remains encrypted and protected from unauthorized access, reducing the risk of data breaches and cyberattacks.
Moreover, vendor-administered VPN services often offer scalability and flexibility to accommodate the evolving needs of businesses. Whether an organization needs to add new users, expand its geographical reach, or integrate with other IT systems, a reputable VPN vendor can tailor their services accordingly. This scalability is particularly beneficial for growing businesses or those with fluctuating bandwidth requirements.
Another advantage is the convenience of having a single point of contact for support and maintenance. Instead of dealing with multiple vendors or managing the VPN infrastructure internally, businesses can rely on the vendor to handle software updates, troubleshooting, and technical support. This frees up valuable resources and allows internal IT teams to focus on other strategic initiatives.
In conclusion, vendor-administered VPN services offer businesses a cost-effective, secure, and convenient solution for protecting their data and facilitating secure remote access. By leveraging the expertise and infrastructure of a trusted vendor, organizations can enhance their cybersecurity posture and streamline their operations in an increasingly interconnected world.
0 notes
Text
https://www.sifytechnologies.com/network-services/sdwan/

Revolutionizing Connectivity: Sify's SD-WAN Solutions Redefine Networking in India
In today's digitally-driven landscape, connectivity is the backbone of success for businesses across all industries. As enterprises embrace cloud services, IoT devices, and remote work, the demand for robust, agile, and secure networking solutions has never been higher. Sify Technologies, a leading ICT service provider in India, rises to the challenge with its cutting-edge SD-WAN (Software-Defined Wide Area Network) solutions, poised to transform the way businesses connect and collaborate.
Unveiling the Future of Networking: Sify's SD-WAN solutions stand at the forefront of technological innovation, offering businesses unparalleled control, flexibility, and performance optimization. By leveraging software-defined networking principles, Sify empowers enterprises to dynamically manage and optimize their wide area networks, regardless of geographical constraints.
Key Features and Benefits:
Agility: Traditional networking architectures are often rigid and cumbersome, hindering adaptability to evolving business needs. Sify's SD-WAN solutions break free from these constraints, providing enterprises with the agility to scale bandwidth, add new branch locations, and deploy applications seamlessly.
Optimized Performance: In the era of real-time applications and data-driven decision-making, network performance is non-negotiable. Sify's SD-WAN employs intelligent traffic steering and path selection algorithms to optimize application performance, ensuring low latency and high throughput across the network.
Enhanced Security: With cyber threats growing in complexity and frequency, safeguarding sensitive data and critical assets is paramount. Sify's SD-WAN integrates advanced security features such as encryption, firewall, and threat detection, providing end-to-end protection against cyber attacks and breaches.
Cost Efficiency: Traditional MPLS (Multiprotocol Label Switching) networks can be cost-prohibitive for businesses, especially those with distributed operations. Sify's SD-WAN leverages cost-effective broadband connections alongside MPLS, enabling enterprises to achieve significant cost savings without compromising performance or reliability.
Simplified Management: Complexity is the enemy of efficiency in network management. Sify's SD-WAN simplifies network orchestration and monitoring through a centralized management console, empowering IT teams to streamline operations, troubleshoot issues, and enforce policies effortlessly.
Customer-Centric Approach: At Sify, customer satisfaction is paramount. From initial consultation to deployment and ongoing support, Sify's team of experts works closely with clients to understand their unique requirements and deliver tailored SD-WAN solutions that exceed expectations. Whether it's optimizing application performance, enhancing security posture, or reducing operational costs, Sify is committed to driving tangible business outcomes for its customers.
Driving Digital Transformation: In an era defined by digital transformation, connectivity is the linchpin that drives innovation, collaboration, and growth. Sify's SD-WAN solutions serve as a catalyst for businesses embarking on their digital journey, empowering them to embrace emerging technologies, enhance operational efficiency, and stay ahead of the competition.
Experience the Future Today: As businesses navigate the complexities of modern networking, Sify stands ready to be their trusted partner in success. With its visionary approach, relentless innovation, and unwavering commitment to excellence, Sify is transforming the networking landscape in India and beyond, one connection at a time.
Discover the power of Sify's SD-WAN solutions and embark on a journey towards a more connected, agile, and secure future for your business.
0 notes