#end to end encrypted
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
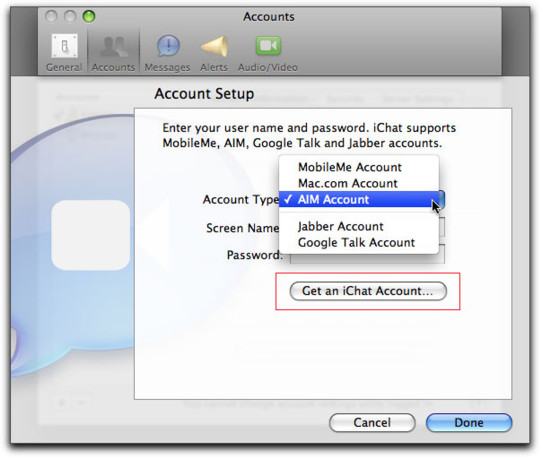
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text
UPDATE! REBLOG THIS VERSION!
#reaux speaks#zoom#terms of service#ai#artificial intelligence#privacy#safety#internet#end to end encryption#virtual#remote#black mirror#joan is awful#twitter#instagram#tiktok#meetings#therapy
23K notes
·
View notes
Text
I am master
I am slave
I am the solace that you crave
i bet you thought this was some pithy ass cloying piece of shit love poetry. it's not. it's about the joys of redundancy-enabled encrypted-at-rest-and-in-transit storage systems.
#nahesa#n4h354#poetry#poem#storage system#redundancy#end to end encrypted#comp sci#i am so funny#ahahahahahaha#i is cute#i is adorable baby snek cat and i need blanky and pillow and hugs
0 notes
Text

This crossed my dash again and like ... we all understand why you should not press that link, yeah? Infosec can be hard, but this example isn't. Right?
Even if this is not a honey pot, praxis is need-to-know basis. A whole Discord server does never need to know. You should just not organize over the internet in general, but if you still want to (why would you want to?), Discord is not the way to do it.
45 notes
·
View notes
Text



not enough zommoth content lately. in fact there is never enough zommoth content. have a fungus /ref
the alive version is based on atlas moths because they are big and cool and about the same color as alive leif
#bug fables#bug fables spoilers#zommoth#bf leif#stuff i made tag#everytime we draw ophie (<-silly nickname) it gets like 10% fluffier#at this rate she's going to be more fuzz than fungus by the end of october#translations for the zombie speak >#img 1: our son who has every disease#img 2: little sibling. little baby sibling#that was written using an encryption code from a book we read in middle school lol#reblogs>likes again. look at our sibling boy
139 notes
·
View notes
Text

real
#the thick of it#no idea what emma ended up doing after 4x07 but i bet it was something high-up and scary.#if ollie got to be caesar she must have done. by series 4 she had an encrypted phone to no. 10 that stewart didn't
9 notes
·
View notes
Text
Did Rita fill the guys in on their eye and why they have ice powers later…?
#if they did it'd be one sentence in the emergency encrypted groupchat to discuss who's holding which word in the prank reveal#a single line of text.#'ah. just so you know.#that ice storm was me. that's the gokkan's king's power.'#(like how they just open the meeting with 'i think the world ia going to end' i. ep6)#a single true sentence that explained nothing#*rita is offline… typing… typing… offline*#*Moffun 'keep it a secret' line stamp*#kingohger#wrong blog whatever#myechoes
4 notes
·
View notes
Text
HAH

HAHAHAHA I AM VICTORIOUS, GOT THE LINKLE MOD WORKING ON ACTUAL HARDWARE
#it was a pain in the ass figuring out what went wrong the first few times#i think the files ended up corrupted during the decryption and re-encryption most likely#BUT I WIN#BRIAR WINS IN THE END#HAHA
5 notes
·
View notes
Text
.
#does anyone else use fb messenger#i woke up and saw that they randomly added end to end encryption to a bunch of my chats ????#and now i can't see a lot of messages ???!?!?????#what the actual fuck#mehrtalks
1 note
·
View note
Text
i love you open source software... i love you open source and user-repairable hardware... i love you things that are not super aesthetically pleasing but function well and do their job... i love you websites that don't harvest my data...
#I LOVE YOU CLOUDS THAT ARE END TO END ENCRYPTED AND NOT OWNED BY A MEGACORPORATION THAT IS INTENT ON TAKING OVER THE WORLD#I LOVE NOT BEING A PRODUCT!!!!
6 notes
·
View notes
Text
i love working here!!!! i love having to figure out which character the writer was thinking of when i look at the 3pts text!!!! is that an ㄹ??? ㅋ?? ㅂ??? YOU WILL NEVER KNOW BC THE WHOLE FONT IS SIZED DOWN TO THE SMALLEST POSSIBLE OPTION
#and i couldnt copy out the text into another document to size up#bc of stupid company safety policy#''the contents of encrypted document can not be pasted' SHUT UP LET ME LIIIIVE#i did figure it out in the end and it had nothing to so with nutting into a room sadly
1 note
·
View note
Note
also 31. pinky swear with psyche and one piece guy of your choice :]
“vel,” psyche says, “i'm okay.”
vel's ears twitch, its hands shaking as it traces the uneven, rough-hewn stitches it made along their neck. their head is back on, and it's staying that way—and they're happy with that, or so they tell it. but vel isn't like them, velveteen as it is like this, and seeing their head fall off scared it.
it's not a new sentiment. psyche has been trying to reassure it for an hour, but they only managed to really start holding themself together when vel finished the stitching five minutes ago. “i thought- you said he cared about you. i don't- i don't get it, and i- i don't want you to leave—”
psyche reaches up to hug it, gentle even as they tug it down so it can curl up against them—body too big to be held in half-zoan form, but god are they both trying. “i'm alive. 'm here.”
“you- not forever! you're—” vel sniffles, shaky and distressed at its own tears. “one day you're gonna leave here, and- and then i'm—”
“you can come with!”
vel shudders to a stop, breathing paused, like if it moves too much psyche will take it back. they don't. “i'm- i'm sorry i didn't offer before. but- if you- if you want to stay with me, even after all this, i'd love that, okay? i'll take care of you, vel.”
“... promise?”
psyche smiles, lopsided and warm. “i promise,” they echo, holding out their pinky finger.
it feels as small as it is, when it loops its finger around theirs, and it transforms out of its half-zoan form to match. psyche readjusts their arms, and keeps holding on.
#kbitycus art#psyche tag#encrypted-cryptid#thank you crow!!!#context: psyche got injured in a fight against their husband (who is temporarily antagonistic); vel is a kid theyve been taking care of#who ended up very freaked out by the injury even though psyche is a stuffed animal & heals easy#both are original characters :] vel is my little guy who i love#prompt reward
2 notes
·
View notes
Text
anonymity is a sweet sexy little blanket and unfortunately it is being gradually ripped away by the biggest and stupidest motherfucker corporations out there
2 notes
·
View notes
Text
fucking love youtube shorts
0 notes
Text
Secure Your Communication With End-to-End Encrypted Messaging Solutions

The protection of private information during communication has become critical in the current digital era. Due to the ever-changing nature of cyber threats, both individuals and organisations are looking for reliable data protection solutions. A potent tool for guaranteeing security and privacy in online discussions is end-to-end encrypted messaging. Let us examine how these solutions can improve your communication channels, as exemplified by the encryptyourmobile platforms.
Comprehending End-to-End Cryptography:
A security precaution known as end-to-end encryption guarantees that the contents of a message are only accessible by the sender and the intended recipient. Data on the sender's device is encrypted, and it stays that way until it gets to the recipient's device, where it is decrypted. This implies that the message remains incomprehensible to unauthorised persons even if intercepted during transit.
The Value of Personal Space:
In the digital sphere, privacy is a fundamental human right. Users can converse openly without worrying about their messages being read or intercepted by nefarious parties, thanks to end-to-end encryption. Privacy protects the confidentiality and security of information, whether it is shared in delicate commercial dealings, intimate interactions, or sensitive data transfers.
Increased Security Protocols:
Additional security features like multi-factor authentication, secure file sharing, and strong encryption methods are frequently included with end-to-end messaging solutions. These security tiers offer complete defence against a range of online dangers, such as malware, phishing scams, and data breaches. Security is given top priority on websites like encryptyourmobile to provide users with peace of mind.
Observance and Guidelines:
Adherence to laws like HIPAA and GDPR is essential in industries managing sensitive data, like healthcare and finance. End-to-end encrypted solutions guarantee the safe transfer of sensitive data while upholding compliance standards, which can help enterprises comply with these regulations.
Accessibility and Usability:
End-to-end messaging systems are made to be accessible and user-friendly on a variety of devices, even with their sophisticated security features. This guarantees easy integration with regular communication practices without sacrificing effectiveness or comfort.
Conclusion:
Solutions for end-to-end encrypted messaging provide a strong barrier against online attacks, preserving the integrity and privacy of your channels of communication. Because of their features that guarantee compliance, enhance security, and promote privacy, platforms such as those offered by EncryptYourMobile are essential tools for individuals and organisations seeking to secure sensitive data in today's connected world. Adopting such solutions is a proactive move to strengthen your digital defences and safeguard your most important information, not just a convenience.
0 notes
Text
AU where people have complete control over their body and can change settings like a computer games, but it takes time for the effects to show irl.
Trolls would tell people to ctrl A all cells and delete (all cells undergo apoptosis and die) or alt f4 your heart to boost efficiency (stops your heart and die)
A progressive unlocking system so babies don't fiddle with settings and fuck themselves up
Immature teens trying out different settings that irrevocably affects the rest of their life (trends to make yourself as tall as humanly possible to cosplay slenderman and unable to degrade those bones later)
Surgeries where patients are told to unequip body parts and the body would disconnect blood vessels, arteries and nerves etc so the surgery just involves it's removal
People falling for brain enhancing hacks the same way people fall for p*nis enlargement ads
People downloading mods to include new settings (additional chromosomes for every cell) for more customisation (different textured skins, colours, additional arms etc) for the ultra rich
People locking themselves in by turning on short term memory loss at 2 seconds, cannot remember to turn it back off
New occupations that focus on researching the effects of each settings, to help consumers adjust individual settings (eg. Produce telomerase at select cells of select organs) to optimise your desires
Hacking of your settings by tricking people into enabling third party access and setting modifications
Underground market where people are configured forcefully to become body parts producers (replace all non essential part of their body to produce livers for example)
Same thing but for drugs, some requiring mods to force the body to produce and store them for sellers
Weird kinks are enabled
Body inability to detect cancer cells become a game people play when bored to identify and target cells for deletion (screen presents random section of cells, user can select to kill or leave be)
Jobs demand certain settings turned on to enter the workforce (eg. Super reaction time for athletes, extremely fine motor skills for surgeons)
Parents teaching children to change settings since an early age to orient them to a certain occupation to gain as much an advantage as possible
Surge in identity theft of celebrities, making their settings a closely guarded secret
#random thoughts#au#settings au#this would probably solve a ton of problems and illnesses#but knowing the stupidity of the world population#we would end up ruining ourselves to make monsters before anything#which is frankly horrifying#not only accidentally frying yourself and screwing yourself over#but capitalism making abuse of others easier#memories would probably be the only way to distinguish people then#sort of like encryption or something#but you have to make sure it changes every time otherwise it could just get stolen
0 notes