#comcom
Text
Netflix wants to chop down your family tree

Netflix has unveiled the details of its new anti-password-sharing policy, detailing a suite of complex gymnastics that customers will be expected to undergo if their living arrangements trigger Netflix’s automated enforcement mechanisms:
https://thestreamable.com/news/confirmed-netflix-unveils-first-details-of-new-anti-password-sharing-measures
If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
Netflix says that its new policy allows members of the same “household” to share an account. This policy comes with an assumption: that there is a commonly understood, universal meaning of “household,” and that software can determine who is and is not a member of your household.
This is a very old corporate delusion in the world of technology. In the early 2000s, I spent years trying to bring some balance to an effort at DVB, whose digital television standards are used in most of the world (but not the USA) when they rolled out CPCM, a DRM system that was supposed to limit video-sharing to a single household.
Their term of art for this was the “authorized domain”: a software-defined family unit whose borders were privately negotiated by corporate executives from media companies, broadcasters, tech and consumer electronics companies in closed-door sessions all around the world, with no public minutes or proceedings.
https://onezero.medium.com/the-internet-heist-part-iii-8561f6d5a4dc
These guys (they were nearly all guys) were proud of how much “flexibility” they’d built into their definition of “household.” For example, if you owned a houseboat, or a luxury car with seatback displays, or a summer villa in another country, the Authorized Domain would be able to figure out how to get the video onto all those screens.
But what about other kinds of families? I suggested that one of our test cases should be a family based in Manila: where the dad travels to remote provinces to do agricultural labor; the daughter is a nanny in California; and the son is doing construction work in the UAE. This suggestion was roundly rejected as an “edge case.”
Of course, this isn’t an edge case. There are orders of magnitude more people whose family looks like this than there are people whose family owns a villa in another country. Owning a houseboat or a luxury car makes you an outlier. Having an itinerant agricultural breadwinner in your family does not.
But everyone who is in the room when a cartel draws up a standard definition of what constitutes a household is almost certainly drawn from a pool that is more likely to have a summer villa than a child doing domestic work or construction labor half a world away. These weirdos, so dissimilar from the global majority, get to define the boxes that computers will shove the rest of the world into. If your family doesn’t look like their family, that’s tough: “Computer says no.”
One day at a CPCM meeting, we got to talking about the problem of “content laundering” and how the way to prevent it would be to put limits on how often someone could leave a household and join another one. No one, they argued, would ever have to change households every week.
I put my hand up and said, “What about a child whose divorced parents share custody of her? She’s absolutely going to change households every week.” They thought about it for a moment, then the rep from a giant IT company that had recently been convicted of criminal antitrust violations said, “Oh, we can solve that: we’ll give her a toll-free number to call when she gets locked out of her account.”
That was the solution they went with. If you are a child coping with the dissolution of your parents’ marriage, you will have the obligation to call up a media company every month — or more often — and explain that Mummy and Daddy don’t love each other any more, but can I please have my TV back?
I never forgot that day. I even wrote a science fiction story about it called (what else?) “Authorized Domain”:
https://craphound.com/news/2011/10/31/authorised-domain/
I think everyone understood that this was an absurd “solution,” but they had already decided that they were going to complete the seemingly straightforward business of defining a category like “household” using software, and once that train left the station, nothing was going to stop it.
This is a recurring form of techno-hubris: the idea that baseline concepts like “family” have crisp definitions and that any exceptions are outliers that would never swallow the rule. It’s such a common misstep that there’s a whole enre* called “Falsehoods Programmers Believe About ______”:
https://github.com/kdeldycke/awesome-falsehood
In that list: names, time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families. These categories are touchstones in our everyday life, and we think we know what they mean — but then we try to define them, and the list of exceptions spirals out into a hairy, fractal infinity.
Historically, these fuzzy categorical edges didn’t matter so much, because they were usually interpreted by humans using common sense. My grandfather was born “Avrom Doctorovitch” (or at least, that’s one way to transliterate his name, which was spelled in a different alphabet, but which was also transliterating his first name from yet another alphabet). When he came to Canada as a refugee, his surname was anglicized to “Doctorow.” Other cousins are “Doctorov,” “Doctoroff,” and “Doktorovitch.”
Naturally, his first name could have been “Abraham” or “Abe,” but his first employer (a fellow Eastern European emigre) decided that was too ethnic and in sincere effort to help him fit in, he called my grandfather “Bill.” When my grandfather attained citizenship, his papers read “Abraham William Doctorow.” He went by “Abe,” “Billy,” “Bill,” “William,” “Abraham” and “Avrom.”
Practically, it didn’t matter that variations on all of these appeared on various forms of ID, contracts, and paperwork. His reparations check from the German government had a different variation from the name on the papers he used to open his bank account, but the bank still let him deposit it.
All of my relatives from his generation have more than one name. Another grandfather of mine was born “Aleksander,” and called “Sasha” by friends, but had his name changed to “Seymour” when he got to Canada. His ID was also a mismatched grab-bag of variations on that theme.
None of this mattered to him, either. Airlines would sell him tickets and border guards would stamp his passport and rental agencies would let him drive away in cars despite the minor variations on all his ID.
But after 9/11, all that changed, for everyone who had blithely trundled along with semi-matching names across their official papers and database entries. Suddenly, it was “computer says no” everywhere you turned, unless everything matched perfectly. There was a global rush for legal name-changes after 9/11 — not because people changed their names, but because people needed to perform the bureaucratic ritual necessary to have the name they’d used all along be recognized in these new, brittle, ambiguity-incinerating machines.
For important categories, ambiguity is a feature, not a bug. The fact that you can write anything on an envelope (including a direction to deliver the letter to the granny flat over the garage, not the front door) means that we don’t have to define “address” — we can leave it usefully hairy around the edges.
Once the database schema is formalized, then “address” gets defined too — the number of lines it can have, the number of characters each line can have, the kinds of characters and even words (woe betide anyone who lives in Scunthorpe).
If you have a “real” address, a “real” name, a “real” date of birth, all of this might seem distant to you. These “edge” cases — seasonal agricultural workers, refugees with randomly assigned “English” names — are very far from your experience.
That’s true — for now (but not forever). The “Shitty Technology Adoption Curve” describes the process by which abusive technologies work their way up the privilege gradient. Every bad technological idea is first rolled out on poor people, refugees, prisoners, kids, mental patients and other people who can’t push back.
Their bodies are used to sand the rough edges and sharp corners off the technology, to normalize it so that it can climb up through the social ranks, imposed on people with more and more power and influence. 20 years ago, if you ate your dinner under an always-on #CCTV, it was because you were in a supermax prison. Today, it’s because you bought a premium home surveillance system from Google, Amazon or Apple.
https://pluralistic.net/2021/07/29/impunity-corrodes/#arise-ye-prisoners
The Netflix anti-sharing tools are designed for rich people. If you travel for business and stay in the kind of hotel where the TV has its own Netflix client that you can plug your username and password into, Netflix will give you a seven-day temporary code to use.
But for the most hardcore road-warriors, Netflix has thin gruel. Unless you connect to your home wifi network every 31 days and stream a show, Netflix will lock out your devices. Once blocked, you have to “contact Netflix” (laughs in Big Tech customer service).
Why is Netflix putting the screws to its customers? It’s part of the enshittification cycle, where platform companies first allocate surpluses to their customers, luring them in and using them as bait for business customers. Once they turn up, the companies reallocate surpluses to businesses, lavishing them with low commissions and lots of revenue opportunities. And once they’re locked in, the company starts to claw back the surpluses for itself.
https://pluralistic.net/2023/01/21/potemkin-ai/#hey-guys
Remember when Netflix was in the business of mailing red envelopes full of DVDs around the country? That was allocating surpluses to users. The movie companies hated this, viewed it as theft — a proposition that was at least as valid as Netflix’s complaints about password sharing, but every pirate wants to be an admiral, and when Netflix did it to the studios, that was “progress,” but when you do it to Netflix, that’s theft.
Then, once Netflix had users locked in and migrated to the web (and later, apps), it shifted surpluses to studios, paying fat licensing fees to stream their movies and connect them to a huge audience.
Finally, once the studios were locked in, Netflix started to harvest the surplus for its shareholders: raising prices, lowering streaming rates, knocking off other studios’ best performing shows with in-house clones, etc. Users’ surpluses are also on the menu: the password “sharing” that let you define a household according to your family’s own idiosyncratic contours is unilaterally abolished in a quest to punish feckless Gen Z kids for buying avocado toast instead of their own Netflix subscriptions.
Netflix was able to ignore the studios’ outraged howls when it built a business by nonconsenually distributing their products in red envelopes. But now that Netflix has come for your family, don’t even think about giving Netfix some of what it gave to the MPAA.
As a technical matter, it’s not really that hard to modify Netflix’s app so that every stream you pull seems to come from your house, no matter where you are. But doing so would require reverse-engineering Netflix’s app, and that would violate Section 1201 of the DMCA, the CFAA, and eleventy-seven other horrible laws. Netflix’s lawyers would nuke you until the rubble bounced.
When Netflix was getting started, it could freely interoperate with the DVDs that the studios had put on the market. It could repurpose those DVDs in ways that the studios strenuously objected to. In other words, Netfix used adversarial interoperability (AKA Competitive Compatibility or ComCom) to launch its business:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Today, Netflix is on the vanguard of the war to abolish adversarial interop. They helped lead the charge to pervert W3C web-standards, creating a DRM video standard called EME that made it a crime to build a full-featured browser without getting permission from media companies and restricting its functionality to their specifications:
https://blog.samuelmaddock.com/posts/the-end-of-indie-web-browsers/
When they used adversarial interoperability to build a multi-billion-dollar global company using the movie studios’ products in ways the studios hated, that was progress. When you define “family” in ways that makes Netflix less money, that’s felony contempt of business model.
[Image ID: A Victorian family tree template populated by tintypes of old-timey people. In the foreground stands a menacing, chainsaw-wielding figure, his face obscured by a hoodie. The blade of the chainsaw is poised to chop down the family tree. A Netflix 'N' logo has been superimposed over the man's face.]
#pluralistic#enshittification#shitty technology adoption curve#cpcm#interoperabiltiy#comcom#adversarial interoperability#interop#netflix#family#ambiguity#digitizatio#nym wars#authorized domain#dvb#dvds#password sharing
7K notes
·
View notes
Quote
Governments can — and should — have rules about interoperability in their procurement policies. They should require companies hoping to receive public money to supply the schematics, error codes, keys and other technical matter needed to maintain and improve the things they sell and provide to our public institutions.
Freeing Ourselves From The Clutches Of Big Tech
6 notes
·
View notes
Video
vimeo
¨¨¨¨¨¨ 2020-pivilion-exeno-60fps-alpha-RGB_appended_mosh2-crf13.mp4 ~>> https://ift.tt/wcTS5qR ,/´¨¨¨¨¨¨
0 notes
Text
(why do i have these pictures again)


#ooc | (written and loved and forgotten);#tbd;#(going through my folders for some refs for comcom purposes and wow what even is half the stuff in here)
6 notes
·
View notes
Text
Oooooo you wanna read Alucards backstory soooo bad
#ooc#// itll only be temp until canon info comcomes out but i like it as is rn :)#the burn part is honestly my favorite. fun to draw and super fun to write <33
5 notes
·
View notes
Text
I love the fashion of long nails, manicures, the French tips, the fact I could have pointy nails like a vampire
Absolutely hate the reality of them though
#rant#like i would hate to have a fake nail glued on that affects my range of touch#that could scratch things i dont mean to#make banging harder lol#make me micromanage something attached to myself for when it needs maintwnance or falls off#hate it all hate itttt#im also personally not into coveruo for same reason. why have something above my skin i cant touch my skin thry#why need to touch it up and worry if it melts or smears#that could clog my pores. yikes yikes yikes#a reason i like eyemakeup is its temporary and comcomes right off the next day with water#and even then i dont wear mascara cause its the easiest eye makeup to rub and fuck up#i like hair dying because until roots grow out it affects nothing its just ur hair a new color#but i dislike extensions cause its additional stuff i have to micromanage#so i only wear nails or extensions as temporary statwment pieces for like A DAY#i couldnt do nails on for a month. nope nope nope
3 notes
·
View notes
Text
Wassup my fellow bitches (affectionate) y'all should buy katana zero and play it it's pretty good
Okay bye
#literally a banger game#LITERALLY SO GOOD#KATANA ZERO IS SO GOOD I HOPE THE DLC COMCOMES OUT SOON#more 15 action pls#i love 15 he's my husband
6 notes
·
View notes
Text
Ok today was a lil better than last time, as long as my cholesterol isnt higher again hopefully no WL talk will be in mychart tomorrow
#juniper.txt#fibro and the myalgias#getting PT referral snd hopefully this onone will actually comcome thru#STILL waiting for water therapy referral from my rheum#fuck osu they're so slow
2 notes
·
View notes
Text
I'd never make it as a commentary youtuber I wouldn't be able to hold in my cuntiness and would inevitably get doxxed by the rabid fanbase of someone I hated on. like jarvis is SO nice to this ethan dude in his latest video. if I had to talk abt this guy for half an hour it'd just be like "LOL LOSER! clout chaser!! incel!! kys!!!"
#but really tho god he just comcomes across as such an absolutely pathetic excuse for a person#texticles
1 note
·
View note
Text
Siblings ❤️ ❤️ TomSturridge #actors #Actor #thesandmanofficial #Netflix #netflixseries #neilgaiman #comicbooks #comiclover #mazikeen #amazing #lordmorpheusedit #lordofdreams #Morpheus #follow4followback #followformore #likeforlikeback #likesforlikesback #liketime #waitingfornewseason #season2 #threewayjunction #comcom #kainandabel #lucienne #kain #abel #sweetbitter
Follow new WhatsApp chanel:
https://whatsapp.com/channel/0029VaGGg9cFsn0YjxsZ6L3
Link in bio
30 notes
·
View notes
Text
U DONT KNOW URE BEAUTIFUL IF ONLY U SAW WHAT I CAN SEE YOULL UNDERTAND WHY I WNAT U SO DEPSERATLRT RN IM LOOKING AT U AND I CANT EBELIEBE U DONT KNOW OHOHOH U DONT KNOW YOURE BEAITUFK NOO OOHOHOH THATS WHAT MAKE U EVAITIFUL SO COMCOME ON U GOT IT WORNF TO PROVE IM RIGTB I PUT IT IN A SONGGGG I DONT KNOW WHYY URE BEING SHYY AND TURN AWAY WHEN I LOOK INTO UR EYEYEYESSS
8 notes
·
View notes
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text
Okay, so. I've knocked off everything else on my list, as I've been saying for some time, I want to start a new long-running thing. I had a few things I was considering, and I've narrowed it down to four potential ones. I've decided to download 22 episodes of each so I can try them out. Not that I'm going to listen to 22 episodes of all three. Just that that's enough so if I really really like one, I can listen to as many episodes as I'd like to test it out before committing to spending like 100 hours of my life on it. Though that number of hours is different depending on the podcast - it seems like there are 1000 hours of Elis and John, while Do the Right Thing only has 53 half-hour episodes.
Why did I choose to start with 22 episodes of each specifically? Because 22 is the number of episodes of Pappy's Flatshare Slamdown that are not archived in the podcast feed, so I had to manually download them from the British Comedy website and then put them in a folder and import that folder into my podcast app, and then I downloaded an equal number from those other podcasts so they'd match. 22 episodes is way too many to just try a few out, but it was easier to import the whole Pappy's folder, and then I wanted them to match.
Here's what I've got now in my comedy podcast app (I made it separate from my news podcasts because it's nice to listen to those and then not have to look at them again until some new fresh hell comes out tomorrow):

Taskmaster, Night Vale, Within the Wires, The Bugle, and ComCom are ones where I've already heard them all (well, only select episodes of ComCom but all the ones I want to hear of what's come out so far) and are only there so I get new episodes as they come. The question marks are those last four.
I figure I'll try out the first few episodes of all of them before deciding if I want to dedicate my life to any. What do people think? Any recommendations?
(Obviously, all of this will start after I listen to that Bugle episode that came out today.)
9 notes
·
View notes
Text
ntntoice: therehs's somsoemthing in One's calaleldner calledled "Sisyphean Saturday" comcoming uppu nenenxx weeke?
2 notes
·
View notes
Text
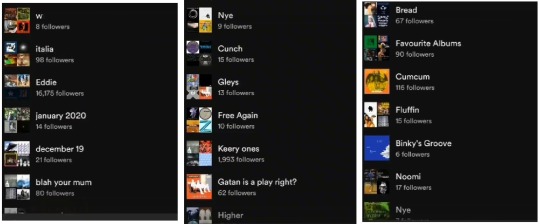
just some of the playlist's names on Joseph Quinns spotify. but ehh, what's about the comcom one??
21 notes
·
View notes
Text
COMEBACKCOMEBACKCOMEBACKCOMEBACKCOMEBACKCOME BA ACK COMEB ACK COME BACK COMEBACK DONT COME BACK DONT COME BACK COME BACK DONT DONT DONT COMEBACK COME BACK COME BACK DONT COME BA DONT COME BACK DONT COME BACK
COME B A CK COMEBACK COMCOME CCOEM BACK BACK BACK DONT DO NT COME BACK COME BACK COME BACK COME BACK COME BACKCKCKKKKKKKKKKKKKKKKKK D
o NT t
c o me b a
ck
2 notes
·
View notes