#interop
Text
Netflix wants to chop down your family tree

Netflix has unveiled the details of its new anti-password-sharing policy, detailing a suite of complex gymnastics that customers will be expected to undergo if their living arrangements trigger Netflix’s automated enforcement mechanisms:
https://thestreamable.com/news/confirmed-netflix-unveils-first-details-of-new-anti-password-sharing-measures
If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
Netflix says that its new policy allows members of the same “household” to share an account. This policy comes with an assumption: that there is a commonly understood, universal meaning of “household,” and that software can determine who is and is not a member of your household.
This is a very old corporate delusion in the world of technology. In the early 2000s, I spent years trying to bring some balance to an effort at DVB, whose digital television standards are used in most of the world (but not the USA) when they rolled out CPCM, a DRM system that was supposed to limit video-sharing to a single household.
Their term of art for this was the “authorized domain”: a software-defined family unit whose borders were privately negotiated by corporate executives from media companies, broadcasters, tech and consumer electronics companies in closed-door sessions all around the world, with no public minutes or proceedings.
https://onezero.medium.com/the-internet-heist-part-iii-8561f6d5a4dc
These guys (they were nearly all guys) were proud of how much “flexibility” they’d built into their definition of “household.” For example, if you owned a houseboat, or a luxury car with seatback displays, or a summer villa in another country, the Authorized Domain would be able to figure out how to get the video onto all those screens.
But what about other kinds of families? I suggested that one of our test cases should be a family based in Manila: where the dad travels to remote provinces to do agricultural labor; the daughter is a nanny in California; and the son is doing construction work in the UAE. This suggestion was roundly rejected as an “edge case.”
Of course, this isn’t an edge case. There are orders of magnitude more people whose family looks like this than there are people whose family owns a villa in another country. Owning a houseboat or a luxury car makes you an outlier. Having an itinerant agricultural breadwinner in your family does not.
But everyone who is in the room when a cartel draws up a standard definition of what constitutes a household is almost certainly drawn from a pool that is more likely to have a summer villa than a child doing domestic work or construction labor half a world away. These weirdos, so dissimilar from the global majority, get to define the boxes that computers will shove the rest of the world into. If your family doesn’t look like their family, that’s tough: “Computer says no.”
One day at a CPCM meeting, we got to talking about the problem of “content laundering” and how the way to prevent it would be to put limits on how often someone could leave a household and join another one. No one, they argued, would ever have to change households every week.
I put my hand up and said, “What about a child whose divorced parents share custody of her? She’s absolutely going to change households every week.” They thought about it for a moment, then the rep from a giant IT company that had recently been convicted of criminal antitrust violations said, “Oh, we can solve that: we’ll give her a toll-free number to call when she gets locked out of her account.”
That was the solution they went with. If you are a child coping with the dissolution of your parents’ marriage, you will have the obligation to call up a media company every month — or more often — and explain that Mummy and Daddy don’t love each other any more, but can I please have my TV back?
I never forgot that day. I even wrote a science fiction story about it called (what else?) “Authorized Domain”:
https://craphound.com/news/2011/10/31/authorised-domain/
I think everyone understood that this was an absurd “solution,” but they had already decided that they were going to complete the seemingly straightforward business of defining a category like “household” using software, and once that train left the station, nothing was going to stop it.
This is a recurring form of techno-hubris: the idea that baseline concepts like “family” have crisp definitions and that any exceptions are outliers that would never swallow the rule. It’s such a common misstep that there’s a whole enre* called “Falsehoods Programmers Believe About ______”:
https://github.com/kdeldycke/awesome-falsehood
In that list: names, time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families. These categories are touchstones in our everyday life, and we think we know what they mean — but then we try to define them, and the list of exceptions spirals out into a hairy, fractal infinity.
Historically, these fuzzy categorical edges didn’t matter so much, because they were usually interpreted by humans using common sense. My grandfather was born “Avrom Doctorovitch” (or at least, that’s one way to transliterate his name, which was spelled in a different alphabet, but which was also transliterating his first name from yet another alphabet). When he came to Canada as a refugee, his surname was anglicized to “Doctorow.” Other cousins are “Doctorov,” “Doctoroff,” and “Doktorovitch.”
Naturally, his first name could have been “Abraham” or “Abe,” but his first employer (a fellow Eastern European emigre) decided that was too ethnic and in sincere effort to help him fit in, he called my grandfather “Bill.” When my grandfather attained citizenship, his papers read “Abraham William Doctorow.” He went by “Abe,” “Billy,” “Bill,” “William,” “Abraham” and “Avrom.”
Practically, it didn’t matter that variations on all of these appeared on various forms of ID, contracts, and paperwork. His reparations check from the German government had a different variation from the name on the papers he used to open his bank account, but the bank still let him deposit it.
All of my relatives from his generation have more than one name. Another grandfather of mine was born “Aleksander,” and called “Sasha” by friends, but had his name changed to “Seymour” when he got to Canada. His ID was also a mismatched grab-bag of variations on that theme.
None of this mattered to him, either. Airlines would sell him tickets and border guards would stamp his passport and rental agencies would let him drive away in cars despite the minor variations on all his ID.
But after 9/11, all that changed, for everyone who had blithely trundled along with semi-matching names across their official papers and database entries. Suddenly, it was “computer says no” everywhere you turned, unless everything matched perfectly. There was a global rush for legal name-changes after 9/11 — not because people changed their names, but because people needed to perform the bureaucratic ritual necessary to have the name they’d used all along be recognized in these new, brittle, ambiguity-incinerating machines.
For important categories, ambiguity is a feature, not a bug. The fact that you can write anything on an envelope (including a direction to deliver the letter to the granny flat over the garage, not the front door) means that we don’t have to define “address” — we can leave it usefully hairy around the edges.
Once the database schema is formalized, then “address” gets defined too — the number of lines it can have, the number of characters each line can have, the kinds of characters and even words (woe betide anyone who lives in Scunthorpe).
If you have a “real” address, a “real” name, a “real” date of birth, all of this might seem distant to you. These “edge” cases — seasonal agricultural workers, refugees with randomly assigned “English” names — are very far from your experience.
That’s true — for now (but not forever). The “Shitty Technology Adoption Curve” describes the process by which abusive technologies work their way up the privilege gradient. Every bad technological idea is first rolled out on poor people, refugees, prisoners, kids, mental patients and other people who can’t push back.
Their bodies are used to sand the rough edges and sharp corners off the technology, to normalize it so that it can climb up through the social ranks, imposed on people with more and more power and influence. 20 years ago, if you ate your dinner under an always-on #CCTV, it was because you were in a supermax prison. Today, it’s because you bought a premium home surveillance system from Google, Amazon or Apple.
https://pluralistic.net/2021/07/29/impunity-corrodes/#arise-ye-prisoners
The Netflix anti-sharing tools are designed for rich people. If you travel for business and stay in the kind of hotel where the TV has its own Netflix client that you can plug your username and password into, Netflix will give you a seven-day temporary code to use.
But for the most hardcore road-warriors, Netflix has thin gruel. Unless you connect to your home wifi network every 31 days and stream a show, Netflix will lock out your devices. Once blocked, you have to “contact Netflix” (laughs in Big Tech customer service).
Why is Netflix putting the screws to its customers? It’s part of the enshittification cycle, where platform companies first allocate surpluses to their customers, luring them in and using them as bait for business customers. Once they turn up, the companies reallocate surpluses to businesses, lavishing them with low commissions and lots of revenue opportunities. And once they’re locked in, the company starts to claw back the surpluses for itself.
https://pluralistic.net/2023/01/21/potemkin-ai/#hey-guys
Remember when Netflix was in the business of mailing red envelopes full of DVDs around the country? That was allocating surpluses to users. The movie companies hated this, viewed it as theft — a proposition that was at least as valid as Netflix’s complaints about password sharing, but every pirate wants to be an admiral, and when Netflix did it to the studios, that was “progress,” but when you do it to Netflix, that’s theft.
Then, once Netflix had users locked in and migrated to the web (and later, apps), it shifted surpluses to studios, paying fat licensing fees to stream their movies and connect them to a huge audience.
Finally, once the studios were locked in, Netflix started to harvest the surplus for its shareholders: raising prices, lowering streaming rates, knocking off other studios’ best performing shows with in-house clones, etc. Users’ surpluses are also on the menu: the password “sharing” that let you define a household according to your family’s own idiosyncratic contours is unilaterally abolished in a quest to punish feckless Gen Z kids for buying avocado toast instead of their own Netflix subscriptions.
Netflix was able to ignore the studios’ outraged howls when it built a business by nonconsenually distributing their products in red envelopes. But now that Netflix has come for your family, don’t even think about giving Netfix some of what it gave to the MPAA.
As a technical matter, it’s not really that hard to modify Netflix’s app so that every stream you pull seems to come from your house, no matter where you are. But doing so would require reverse-engineering Netflix’s app, and that would violate Section 1201 of the DMCA, the CFAA, and eleventy-seven other horrible laws. Netflix’s lawyers would nuke you until the rubble bounced.
When Netflix was getting started, it could freely interoperate with the DVDs that the studios had put on the market. It could repurpose those DVDs in ways that the studios strenuously objected to. In other words, Netfix used adversarial interoperability (AKA Competitive Compatibility or ComCom) to launch its business:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
Today, Netflix is on the vanguard of the war to abolish adversarial interop. They helped lead the charge to pervert W3C web-standards, creating a DRM video standard called EME that made it a crime to build a full-featured browser without getting permission from media companies and restricting its functionality to their specifications:
https://blog.samuelmaddock.com/posts/the-end-of-indie-web-browsers/
When they used adversarial interoperability to build a multi-billion-dollar global company using the movie studios’ products in ways the studios hated, that was progress. When you define “family” in ways that makes Netflix less money, that’s felony contempt of business model.
[Image ID: A Victorian family tree template populated by tintypes of old-timey people. In the foreground stands a menacing, chainsaw-wielding figure, his face obscured by a hoodie. The blade of the chainsaw is poised to chop down the family tree. A Netflix 'N' logo has been superimposed over the man's face.]
#pluralistic#enshittification#shitty technology adoption curve#cpcm#interoperabiltiy#comcom#adversarial interoperability#interop#netflix#family#ambiguity#digitizatio#nym wars#authorized domain#dvb#dvds#password sharing
7K notes
·
View notes
Text
Bypassing Factory Reset Production on Microsoft Lumia 640
Bypassing Factory Reset Production on Microsoft Lumia 640
The problem:
Recently I had to factory reset my Lumia 640 with Windows 10 Build 14393. However the factory reset protection cannot be turned off in settings. I proceeded with a factory reset, then I am greeted with the reset protection notification screen (no surprise)
As the back end service for Windows Mobile has ended, I cannot turn off the protection by logging into my Microsoft Account…

View On WordPress
2 notes
·
View notes
Text
Intraoperative radiation therapy (IORT) is currently a breast cancer treatment technique that delivers radiation treatment at the same time as lumpectomy surgery. The radiation dose is delivered to an exposed tumor bed while surrounding healthy tissue is moved aside and spared from high dose radiation. The entire dose of radiation needed often can be given in one treatment, which may take from 20 to 60 minutes.
0 notes
Link
#ASP.NET Core#Blazor#C / .NET / dotnet#Programming#Software Engineering#Tutorial#ASP.NET#blazor#Blazor Web Assembly#code#coding#DotNet#dotnet core#JavaScript#JavaScript Interop#JS Interop#netcore#Web Assembly
0 notes
Text
C# 透過主要 Interop 元件存取Excel 檔案
C# 透過主要 Interop 元件存取Excel 檔案
微軟 Office 提供了主要Office Interop 物件,
讓開發者能透過 PIA 來存取 Office中的套裝軟體,
達到以程式編修此類檔案的效果,
今天則以 Excel 為範例教大家
C# 透過主要 Interop 元件存取Excel 檔案
開發者要使用 PIA (primary interop assemblies) 存取 Excel 文件,
在安裝 Office 時,
請安裝 Microsoft Office 主要 Interop 組件 (PIA),
建置 PIA相關的專案時,
PIA 會內嵌在解決方案中,
因此不需要將 PIA 散發給使用者作為專案的必要條件
要使用 namespace :Microsoft.Office.Interop.Excel
必須先從方案總管選擇”加入參考”,
從參考管理員的 COM頁找到 Microsoft Excel…
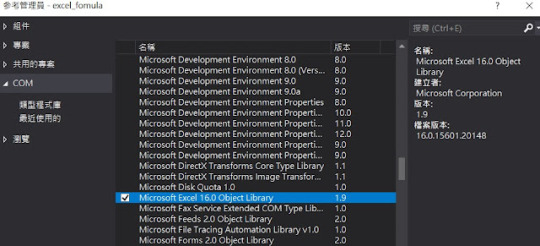
View On WordPress
#AutoFit()#c 入門#C範例程式#Microsoft.Office.Interop.Excel#mySheet.Cells#主要Office Interop 物件#加入參考#存取Excel 檔案#安裝相容的 Office#整資料行的寬度
0 notes
Text
Can the Loom Network (LOOM) make money from a Multichain Interop and Dapps?
Can the Loom Network (LOOM) make money from a Multichain Interop and Dapps?
The Loom Network (LOOM) hopes to make money by weaving different blockchains together. In particular, Loom helps decentralized apps (dapps) operate on different blockchains.
To elaborate, the Loom Network is a production-ready multichain interop platform for dapp develompment. To explain, an interop platform allows dapps to operate on several blockchains, such as Bitcoin, Ethereum, Tron, and…

View On WordPress
#Can the Loom Network (LOOM) make money from a Multichain Interop and Dapps?#Loom Network#Loom Network (LOOM)#Loom Network and CryptoZombies#multichain collateralized assets#Multichain Interop#The Loom Network (LOOM) Token#What is the Loom Network?#What Value does the Loom Network (LOOM) have?
0 notes
Text
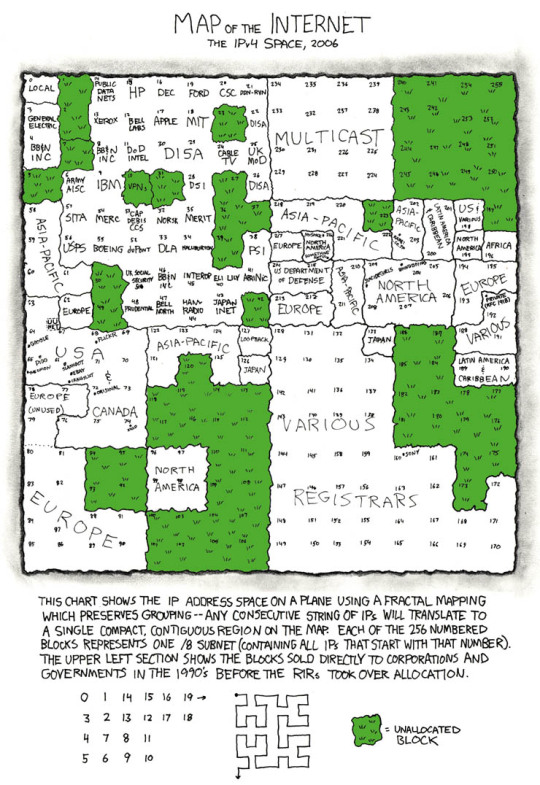
For the IPv6 map just imagine the XP default desktop picture.
Map of the Internet [Explained]
Transcript Under the Cut
Map of the Internet The IPv4 Space, 2006This chart shows the IP address space on a plane using a fractal mapping which preserves grouping--any consecutive string of IPs will translate to a single, compact, contiguous region on the map. Each of the 256 numbered blocks represents one 8 subnet (containing all IPs that start with that number). The upper left section shows the blocks sold directly to corporations and goverments in the 1990's before the RIRs took over allocation.
Diagram showing IP ownership:
0: Local
1-2: Unallocated
3: General Electric
4: BB&N INC
5: Unallocated
6: Army AISC
7: Unallocated
8: BB&N INC
9: IBM
10: VPNs
11: DoD Intel
12: Bell Labs
13: Xerox
14: Public data nets
15: HP
16: DEC
17: Apple
18: MIT
19: Ford
20: CSC
21: DDN-RYN
22: DISA
23: Unallocated
24: Cable TV
25: UK MoD
26: DISA
27: Unallocated
28: DSI
29-30: DISA
31: Unallocated
32: NORSK
33: DLA
34: Halliburton
35: Merit
36-37: Unallocated
38: PSI
39: Unallocated
40: Eli Lily
41: ARINIC
42: Unallocated
43: Japan INET
44: HAM Radio
45: INTEROP
46: BB&N INC
47: Bell North
48: Prudential
49-50: Unallocated
51: UK Social Security
52: duPont
55: Boeing
56: USPS
57: SITA
58-61: Asia-Pacific
62: Europe
63-76: USA & Canada (contains: UUNET, Google, Digg, Slashdot, Ebay, Craigslist, XKCD, Flickr)
77-79: Europe (unused)
80-91: Europe
92-95: Unallocated
96-99: North America
100-120: Unallocated
121-125: Asia-Pacific
126: Japan
127: Loopback
128-132: Various Registrars
133: Japan
134-172: Various Registrars
173-189: Unallocated
188: Various
189-190: Latin America & Caribbean
191-192: Various (contains Private (RFC 1918))
193-195: Europe
196: Africa
197: Unallocated
198: US & Various
199: North America
200-201: Latin America & Caribbean
202-203: Asia-Pacific
204-209: North America (contains Suicide Girls, BoingBoing)
210-211: Asia-Pacific
212-213: Europe
214-215: U.S. Department of Defense
216: North America (Contains Myspace, SomethingAwful)
217: Europe
218-222: Asia-Pacific
223: Unallocated
224-239: Multicast
240-255: Unallocated
43 notes
·
View notes
Text
Tumblr will add support for ActivityPub, the open, decentralized social networking protocol that today is powering social networking software like Twitter alternative Mastodon, the Instagram-like Pixelfed, video streaming service PeerTube, and others. The news was revealed in response to a Twitter user’s complaint about Mastodon’s complexities. Automattic CEO Matt Mullenweg — whose company acquired Tumblr from Verizon in 2019 — suggested the user “come to Tumblr” as the site would soon “add activitypub for interconnect.”
“Don’t stress,” he said, before clarifying that Tumblr first has to deal with the waves of new users coming in right now from Twitter but that support for “interop and activitypub” were due to come “ASAP.”
In short, this announcement means Tumblr would move from being only a niche blogging platform to becoming a part of a larger, decentralized social network of sorts — and one whose user base has grown in size in recent days as people flee Elon Musk’s Twitter in search of new communities.
#activitypub#tech memes#tech news#technology#open source#decentralization#twitter#news#techcrunch#computers#software engineering
137 notes
·
View notes
Note
5 best things about C++ that aren't constexpr
5 worst things about C++
Best compared to what though
You always gotta look at what the competition forgot to bring.
--- Best:
RAII/Deterministic destruction
const
templates and template metaprogramming (in the interest of fairness to other languages that cannot pretend to compete I will make this one item)
perf
C Interop
--- Meh:
C Interop
--- Worst:
C interop
ABI back compat is killing me slowly
UB, especially UB NDR fuck NDR all my homies hate NDR
the "noexcept" specifier is hot garbage and yet it could have been so good
the build system
the build system
the build system
the build system
the build system
the build system
the build system
the build system
18 notes
·
View notes
Text
PMT01: Scaffold nano & Trowel pico
Scaffold nano & Trowel pico v1.1.0 have been released tonight.
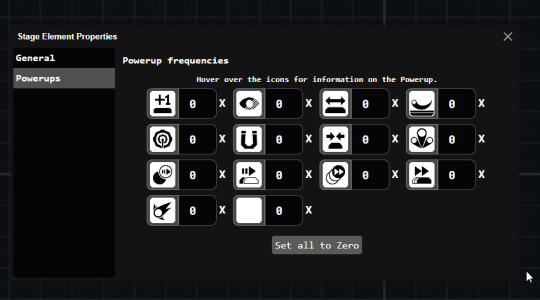
Updates add a myStages to Scaffold, and QoL improvements to the powerup editing experience in Trowel pico.
Now that it's out, I'd like to also take this moment to talk about the development and release of both.
One year minus one day ago I had announced in Twitter I would work on the level editor for the demo version of BRICKBREAKER SPRINT (nano) so fans could breathe in more life to the game even in its limited state and to also showcase how much it can do with its limited toolset at the current time.
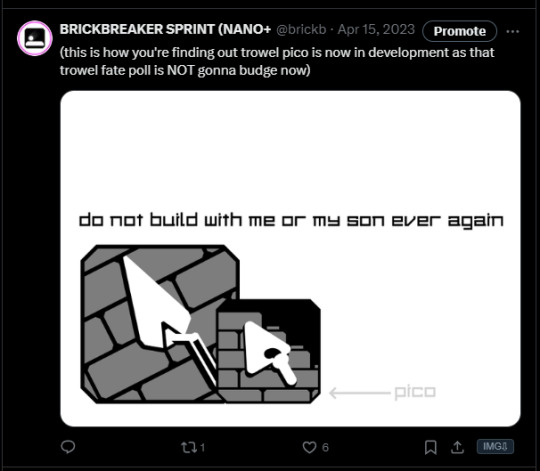
The reasoning for a completely separate technology version was simple, WebGL. WebGL in Unity is so limited for even the most basic things (I had to install a package to support cross-app copy/paste before nano+'s release!) and I said "hey, might as well give the multiplatform users something to be able to edit with, doesn't need to be just windows which is what the currently unpolished-ish trowel desktop is!"
But then it hit me that the same limitations would likely make it hell for me to support just levels downloaded as files (internally stored with "bxtp" extension btw :) ) so then... I came at a crossroads
just say FKIT and not do it, make ppl wait for BB Lite
still say FKIT and kickstart the foundation of the online service that I had planned since the first design iteration of the game
guess what I took?
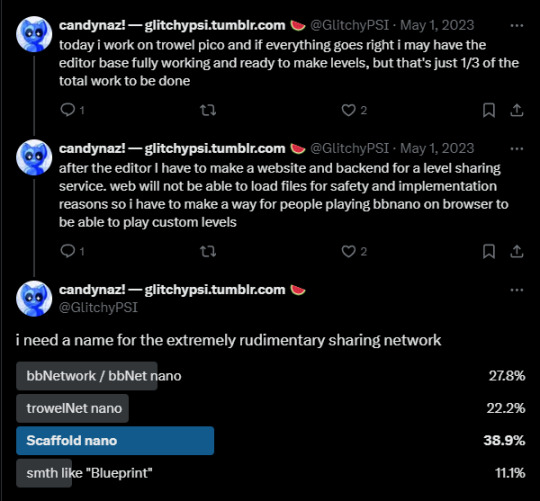
I don't regret it.
Currently, Scaffold's login system is attached to itch.io. In the future, this will use my own account system (called Luna, still in development)
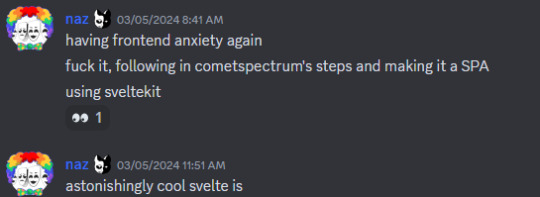
Now then... developing Scaffold's frontend was a challenge in itself, because I'm a masochist. I chose yet another technology to make the frontend in, this time Svelte, Sveltekit as backend saying "okay, no more fear of ServerSideRendering now that I can afford a VPS for this"
but... Svelte has been an absolute joy to work with. Its learning curve even smoother than React's (my first frontend framework, which powers cometSpectrum!), and I got everything rolling very quickly
At first, I was going to use my regular website design language, but it's kinda jank, so I said NO and started from scratch with a simpler façade. For the style I wanted to pursue... it was perfect. Some people have complimented the graphic aspect of the site, and I'm happy I could deliver exactly what I wanted. (and yes the icons being in opposite directions compared to bbsprint's UI is entirely on purpose)
BTW, the site is made in such a way that a BB theme could be used as the site's theme and every color will change except for PNG icons, i love it (this functionality is used for people using their OS's Light theme)
This is actually the first made-by-me website project that has "public" facing write actions to a database and stores actual files. It works... very well, and I am very happy about it. It's like a combination of everything I've learnt up to this point, down to API design and interop between programs.
I did say this was the foundation for Scaffold, and I plan for this game to keep Scaffold as its prime way of getting stages, even when getting to storefronts like Steam or GOG. Kind of like an osu! situation.
You're at this part of the message... wanna see how Scaffold's logo used to look like?


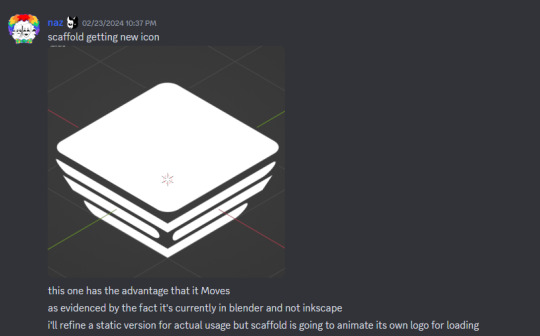
5 notes
·
View notes
Text
Forcing your computer to rat you out

Powerful people imprisoned by the cluelessness of their own isolation, locked up with their own motivated reasoning: “It’s impossible to get a CEO to understand something when his quarterly earnings call depends on him not understanding it.”
Take Mark Zuckerberg. Zuckerberg insists that anyone who wanted to use a pseudonym online is “two-faced,” engaged in dishonest social behavior. The Zuckerberg Doctrine claims that forcing people to use their own names is a way to ensure civility. This is an idea so radioactively wrong, it can be spotted from orbit.
From the very beginning, social scientists (both inside and outside Facebook) told Zuckerberg that he was wrong. People have lots of reasons to hide their identities online, both good and bad, but a Real Names Policy affects different people differently:
https://memex.craphound.com/2018/01/22/social-scientists-have-warned-zuck-all-along-that-the-facebook-theory-of-interaction-would-make-people-angry-and-miserable/
For marginalized and at-risk people, there are plenty of reasons to want to have more than one online identity — say, because you are a #MeToo whistleblower hoping that Harvey Weinstein won’t sic his ex-Mossad mercenaries on you:
https://www.newyorker.com/news/news-desk/harvey-weinsteins-army-of-spies
Or maybe you’re a Rohingya Muslim hoping to avoid the genocidal attentions of the troll army that used Facebook to organize — under their real, legal names — to rape and murder you and everyone you love:
https://www.amnesty.org/en/latest/news/2022/09/myanmar-facebooks-systems-promoted-violence-against-rohingya-meta-owes-reparations-new-report/
But even if no one is looking to destroy your life or kill you and your family, there are plenty of good reasons to present different facets of your identity to different people. No one talks to their lover, their boss and their toddler in exactly the same way, or reveals the same facts about their lives to those people. Maintaining different facets to your identity is normal and healthy — and the opposite, presenting the same face to everyone in your life, is a wildly terrible way to live.
None of this is controversial among social scientists, nor is it hard to grasp. But Zuckerberg stubbornly stuck to this anonymity-breeds-incivility doctrine, even as dictators used the fact that Facebook forced dissidents to use their real names to retain power through the threat (and reality) of arrest and torture:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Why did Zuck cling to this dangerous and obvious fallacy? Because the more he could collapse your identity into one unitary whole, the better he could target you with ads. Truly, it is impossible to get a billionaire to understand something when his mega-yacht depends on his not understanding it.
This motivated reasoning ripples through all of Silicon Valley’s top brass, producing what Anil Dash calls “VC QAnon,” the collection of conspiratorial, debunked and absurd beliefs embraced by powerful people who hold the digital lives of billions of us in their quivering grasp:
https://www.anildash.com/2023/07/07/vc-qanon/
These fallacy-ridden autocrats like to disguise their demands as observations, as though wanting something to be true was the same as making it true. Think of when Eric Schmidt — then the CEO of Google — dismissed online privacy concerns, stating “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place”:
https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy
Schmidt was echoing the sentiments of his old co-conspirator, Sun Microsystems CEO Scott McNealy: “You have zero privacy anyway. Get over it”:
https://www.wired.com/1999/01/sun-on-privacy-get-over-it/
Both men knew better. Schmidt, in particular, is very jealous of his own privacy. When Cnet reporters used Google to uncover and publish public (but intimate and personal) facts about Schmidt, Schmidt ordered Google PR to ignore all future requests for comment from Cnet reporters:
https://www.cnet.com/tech/tech-industry/how-cnet-got-banned-by-google/
(Like everything else he does, Elon Musk’s policy of responding to media questions about Twitter with a poop emoji is just him copying things other people thought up, making them worse, and taking credit for them:)
https://www.theverge.com/23815634/tesla-elon-musk-origin-founder-twitter-land-of-the-giants
Schmidt’s actions do not reflect an attitude of “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Rather, they are the normal response that we all have to getting doxed.
When Schmidt and McNealy and Zuck tell us that we don’t have privacy, or we don’t want privacy, or that privacy is bad for us, they’re disguising a demand as an observation. “Privacy is dead” actually means, “When privacy is dead, I will be richer than you can imagine, so stop trying to save it, goddamnit.”
We are all prone to believing our own bullshit, but when a tech baron gets high on his own supply, his mental contortions have broad implications for all of us. A couple years after Schmidt’s anti-privacy manifesto, Google launched Google Plus, a social network where everyone was required to use their “real name.”
This decision — justified as a means of ensuring civility and a transparent ruse to improve ad targeting — kicked off the Nym Wars:
https://epeus.blogspot.com/2011/08/google-plus-must-stop-this-identity.html
One of the best documents to come out of that ugly conflict is “Falsehoods Programmers Believe About Names,” a profound and surprising enumeration of all the ways that the experiences of tech bros in Silicon Valley are the real edge-cases, unreflective of the reality of billions of their users:
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
This, in turn, spawned a whole genre of programmer-fallacy catalogs, falsehoods programmers believe about time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families:
https://github.com/kdeldycke/awesome-falsehood
But humility is in short supply in tech. It’s impossible to get a programmer to understand something when their boss requires them not to understand it. A programmer will happily insist that ordering you to remove your “mask” is for your own good — and not even notice that they’re taking your skin off with it.
There are so many ways that tech executives could improve their profits if only we would abandon our stubborn attachment to being so goddamned complicated. Think of Netflix and its anti-passsword-sharing holy war, which is really a demand that we redefine “family” to be legible and profitable for Netflix:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
But despite the entreaties of tech companies to collapse our identities, our families, and our online lives into streamlined, computably hard-edged shapes that fit neatly into their database structures, we continue to live fuzzy, complicated lives that only glancingly resemble those of the executives seeking to shape them.
Now, the rich, powerful people making these demands don’t plan on being constrained by them. They are conservatives, in the tradition of #FrankWilhoit, believers in a system of “in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect”:
https://crookedtimber.org/2018/03/21/liberals-against-progressives/#comment-729288
As with Schmidt’s desire to spy on you from asshole to appetite for his own personal gain, and his violent aversion to having his own personal life made public, the tech millionaires and billionaires who made their fortune from the flexibility of general purpose computers would like to end that flexibility. They insist that the time for general purpose computers has passed, and that today, “consumers” crave the simplicity of appliances:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
It is in the War On General Purpose Computing that we find the cheapest and flimsiest rhetoric. Companies like Apple — and their apologists — insist that no one wants to use third-party app stores, or seek out independent repair depots — and then spend millions to make sure that it’s illegal to jailbreak your phone or get it fixed outside of their own official channel:
https://doctorow.medium.com/apples-cement-overshoes-329856288d13
The cognitive dissonance of “no one wants this,” and “we must make it illegal to get this” is powerful, but the motivated reasoning is more powerful still. It is impossible to get Tim Cook to understand something when his $49 million paycheck depends on him not understanding it.
The War on General Purpose Computing has been underway for decades. Computers, like the people who use them, stubbornly insist on being reality-based, and the reality of computers is that they are general purpose. Every computer is a Turing complete, universal Von Neumann machine, which means that it can run every valid program. There is no way to get a computer to be almost Turing Complete, only capable of running programs that don’t upset your shareholders’ fragile emotional state.
There is no such thing as a printer that will only run the “reject third-party ink” program. There is no such thing as a phone that will only run the “reject third-party apps” program. There are only laws, like the Section 1201 of the Digital Millennium Copyright Act, that make writing and distributing those programs a felony punishable by a five-year prison sentence and a $500,000 fine (for a first offense).
That is to say, the War On General Purpose Computing is only incidentally a technical fight: it is primarily a legal fight. When Apple says, “You can’t install a third party app store on your phone,” what they means is, “it’s illegal to install that third party app store.” It’s not a technical countermeasure that stands between you and technological self-determination, it’s a legal doctrine we can call “felony contempt of business model”:
https://locusmag.com/2020/09/cory-doctorow-ip/
But the mighty US government will not step in to protect a company’s business model unless it at least gestures towards the technical. To invoke DMCA 1201, a company must first add the thinnest skin of digital rights management to their product. Since 1201 makes removing DRM illegal, a company can use this molecule-thick scrim of DRM to felonize any activity that the DRM prevents.
More than 20 years ago, technologists started to tinker with ways to combine the legal and technical to tame the wild general purpose computer. Starting with Microsoft’s Palladium project, they theorized a new “Secure Computing” model for allowing companies to reach into your computer long after you had paid for it and brought it home, in order to discipline you for using it in ways that undermined its shareholders’ interest.
Secure Computing began with the idea of shipping every computer with two CPUs. The first one was the normal CPU, the one you interacted with when you booted it up, loaded your OS, and ran programs. The second CPU would be a Trusted Platform Module, a brute-simple system-on-a-chip designed to be off-limits to modification, even by its owner (that is, you).
The TPM would ship with a limited suite of simple programs it could run, each thoroughly audited for bugs, as well as secret cryptographic signing keys that you were not permitted to extract. The original plan called for some truly exotic physical security measures for that TPM, like an acid-filled cavity that would melt the chip if you tried to decap it or run it through an electron-tunneling microscope:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
This second computer represented a crack in the otherwise perfectly smooth wall of a computer’s general purposeness; and Trusted Computing proposed to hammer a piton into that crack and use it to anchor a whole superstructure that could observe — and limited — the activity of your computer.
This would start with observation: the TPM would observe every step of your computer’s boot sequence, creating cryptographic hashes of each block of code as it loaded and executed. Each stage of the boot-up could be compared to “known good” versions of those programs. If your computer did something unexpected, the TPM could halt it in its tracks, blocking the boot cycle.
What kind of unexpected things do computers do during their boot cycle? Well, if your computer is infected with malware, it might load poisoned versions of its operating system. Once your OS is poisoned, it’s very hard to detect its malicious conduct, since normal antivirus programs rely on the OS to faithfully report what your computer is doing. When the AV program asks the OS to tell it which programs are running, or which files are on the drive, it has no choice but to trust the OS’s response. When the OS is compromised, it can feed a stream of lies to users’ programs, assuring these apps that everything is fine.
That’s a very beneficial use for a TPM, but there’s a sinister flipside: the TPM can also watch your boot sequence to make sure that there aren’t beneficial modifications present in your operating system. If you modify your OS to let you do things the manufacturer wants to prevent — like loading apps from a third-party app-store — the TPM can spot this and block it.
Now, these beneficial and sinister uses can be teased apart. When the Palladium team first presented its research, my colleague Seth Schoen proposed an “owner override”: a modification of Trusted Computing that would let the computer’s owner override the TPM:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
This override would introduce its own risks, of course. A user who was tricked into overriding the TPM might expose themselves to malicious software, which could harm that user, as well as attacking other computers on the user’s network and the other users whose data were on the compromised computer’s drive.
But an override would also provide serious benefits: it would rule out the monopolistic abuse of a TPM to force users to run malicious code that the manufacturer insisted on — code that prevented the user from doing things that benefited the user, even if it harmed the manufacturer’s shareholders. For example, with owner override, Microsoft couldn’t force you to use its official MS Office programs rather than third-party compatible programs like Apple’s iWork or Google Docs or LibreOffice.
Owner override also completely changed the calculus for another, even more dangerous part of Trusted Computing: remote attestation.
Remote Attestation is a way for third parties to request a reliable, cryptographically secured assurances about which operating system and programs your computer is running. In Remote Attestation, the TPM in your computer observes every stage of your computer’s boot, gathers information about all the programs you’re running, and cryptographically signs them, using the signing keys the manufacturer installed during fabrication.
You can send this “attestation” to other people on the internet. If they trust that your computer’s TPM is truly secure, then they know that you have sent them a true picture of your computer’s working (the actual protocol is a little more complicated and involves the remote party sending you a random number to cryptographically hash with the attestation, to prevent out-of-date attestations).
Now, this is also potentially beneficial. If you want to make sure that your technologically unsophisticated friend is running an uncompromised computer before you transmit sensitive data to it, you can ask them for an attestation that will tell you whether they’ve been infected with malware.
But it’s also potentially very sinister. Your government can require all the computers in its borders to send a daily attestation to confirm that you’re still running the mandatory spyware. Your abusive spouse — or abusive boss — can do the same for their own disciplinary technologies. Such a tool could prevent you from connecting to a service using a VPN, and make it impossible to use Tor Browser to protect your privacy when interacting with someone who wishes you harm.
The thing is, it’s completely normal and good for computers to lie to other computers on behalf of their owners. Like, if your IoT ebike’s manufacturer goes out of business and all their bikes get bricked because they can no longer talk to their servers, you can run an app that tricks the bike into thinking that it’s still talking to the mothership:
https://nltimes.nl/2023/07/15/alternative-app-can-unlock-vanmoof-bikes-popular-amid-bankruptcy-fears
Or if you’re connecting to a webserver that tries to track you by fingerprinting you based on your computer’s RAM, screen size, fonts, etc, you can order your browser to send random data about this stuff:
https://jshelter.org/fingerprinting/
Or if you’re connecting to a site that wants to track you and nonconsensually cram ads into your eyeballs, you can run an adblocker that doesn’t show you the ads, but tells the site that it did:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Owner override leaves some of the beneficial uses of remote attestation intact. If you’re asking a friend to remotely confirm that your computer is secure, you’re not going to use an override to send them bad data about about your computer’s configuration.
And owner override also sweeps all of the malicious uses of remote attestation off the board. With owner override, you can tell any lie about your computer to a webserver, a site, your boss, your abusive spouse, or your government, and they can’t spot the lie.
But owner override also eliminates some beneficial uses of remote attestation. For example, owner override rules out remote attestation as a way for strangers to play multiplayer video games while confirming that none of them are using cheat programs (like aimhack). It also means that you can’t use remote attestation to verify the configuration of a cloud server you’re renting in order to assure yourself that it’s not stealing your data or serving malware to your users.
This is a tradeoff, and it’s a tradeoff that’s similar to lots of other tradeoffs we make online, between the freedom to do something good and the freedom to do something bad. Participating anonymously, contributing to free software, distributing penetration testing tools, or providing a speech platform that’s open to the public all represent the same tradeoff.
We have lots of experience with making the tradeoff in favor of restrictions rather than freedom: powerful bad actors are happy to attach their names to their cruel speech and incitement to violence. Their victims are silenced for fear of that retaliation.
When we tell security researchers they can’t disclose defects in software without the manufacturer’s permission, the manufacturers use this as a club to silence their critics, not as a way to ensure orderly updates.
When we let corporations decide who is allowed to speak, they act with a mixture of carelessness and self-interest, becoming off-the-books deputies of authoritarian regimes and corrupt, powerful elites.
Alas, we made the wrong tradeoff with Trusted Computing. For the past twenty years, Trusted Computing has been creeping into our devices, albeit in somewhat denatured form. The original vision of acid-filled secondary processors has been replaced with less exotic (and expensive) alternatives, like “secure enclaves.” With a secure enclave, the manufacturer saves on the expense of installing a whole second computer, and instead, they draw a notional rectangle around a region of your computer’s main chip and try really hard to make sure that it can only perform a very constrained set of tasks.
This gives us the worst of all worlds. When secure enclaves are compromised, we not only lose the benefit of cryptographic certainty, knowing for sure that our computers are only booting up trusted, unalterted versions of the OS, but those compromised enclaves run malicious software that is essentially impossible to detect or remove:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
But while Trusted Computing has wormed its way into boot-restrictions — preventing you from jailbreaking your computer so it will run the OS and apps of your choosing — there’s been very little work on remote attestation…until now.
Web Environment Integrity is Google’s proposal to integrate remote attestation into everyday web-browsing. The idea is to allow web-servers to verify what OS, extensions, browser, and add-ons your computer is using before the server will communicate with you:
https://github.com/RupertBenWiser/Web-Environment-Integrity/blob/main/explainer.md
Even by the thin standards of the remote attestation imaginaries, there are precious few beneficial uses for this. The googlers behind the proposal have a couple of laughable suggestions, like, maybe if ad-supported sites can comprehensively refuse to serve ad-blocking browsers, they will invest the extra profits in making things you like. Or: letting websites block scriptable browsers will make it harder for bad people to auto-post fake reviews and comments, giving users more assurances about the products they buy.
But foundationally, WEI is about compelling you to disclose true facts about yourself to people who you want to keep those facts from. It is a Real Names Policy for your browser. Google wants to add a new capability to the internet: the ability of people who have the power to force you to tell them things to know for sure that you’re not lying.
The fact that the authors assume this will be beneficial is just another “falsehood programmers believe”: there is no good reason to hide the truth from other people. Squint a little and we’re back to McNealy’s “Privacy is dead, get over it.” Or Schmidt’s “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
And like those men, the programmers behind this harebrained scheme don’t imagine that it will ever apply to them. As Chris Palmer — who worked on Chromium — points out, this is not compatible with normal developer tools or debuggers, which are “incalculably valuable and not really negotiable”:
https://groups.google.com/a/chromium.org/g/blink-dev/c/Ux5h_kGO22g/m/5Lt5cnkLCwAJ
This proposal is still obscure in the mainstream, but in tech circles, it has precipitated a flood of righteous fury:
https://arstechnica.com/gadgets/2023/07/googles-web-integrity-api-sounds-like-drm-for-the-web/
As I wrote last week, giving manufacturers the power to decide how your computer is configured, overriding your own choices, is a bad tradeoff — the worst tradeoff, a greased slide into terminal enshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is how you get Unauthorized Bread:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
All of which leads to the question: what now? What should be done about WEI and remote attestation?
Let me start by saying: I don’t think it should be illegal for programmers to design and release these tools. Code is speech, and we can’t understand how this stuff works if we can’t study it.
But programmers shouldn’t deploy it in production code, in the same way that programmers should be allowed to make pen-testing tools, but shouldn’t use them to attack production systems and harm their users. Programmers who do this should be criticized and excluded from the society of their ethical, user-respecting peers.
Corporations that use remote attestation should face legal restrictions: privacy law should prevent the use of remote attestation to compel the production of true facts about users or the exclusion of users who refuse to produce those facts. Unfair competition law should prevent companies from using remote attestation to block interoperability or tie their products to related products and services.
Finally, we must withdraw the laws that prevent users and programmers from overriding TPMs, secure enclaves and remote attestations. You should have the right to study and modify your computer to produce false attestations, or run any code of your choosing. Felony contempt of business model is an outrage. We should alter or strike down DMCA 1201, the Computer Fraud and Abuse Act, and other laws (like contract law’s “tortious interference”) that stand between you and “sole and despotic dominion” over your own computer. All of that applies not just to users who want to reconfigure their own computers, but also toolsmiths who want to help them do so, by offering information, code, products or services to jailbreak and alter your devices.
Tech giants will squeal at this, insisting that they serve your interests when they prevent rivals from opening up their products. After all, those rivals might be bad guys who want to hurt you. That’s 100% true. What is likewise true is that no tech giant will defend you from its own bad impulses, and if you can’t alter your device, you are powerless to stop them:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Companies should be stopped from harming you, but the right place to decide whether a business is doing something nefarious isn’t in the boardroom of that company’s chief competitor: it’s in the halls of democratically accountable governments:
https://www.eff.org/wp/interoperability-and-privacy
So how do we get there? Well, that’s another matter. In my next book, The Internet Con: How to Seize the Means of Computation (Verso Books, Sept 5), I lay out a detailed program, describing which policies will disenshittify the internet, and how to get those policies:
https://www.versobooks.com/products/3035-the-internet-con
Predictably, there are challenges getting this kind of book out into the world via our concentrated tech sector. Amazon refuses to carry the audio edition on its monopoly audiobook platform, Audible, unless it is locked to Amazon forever with mandatory DRM. That’s left me self-financing my own DRM-free audio edition, which is currently available for pre-order via this Kickstarter:
http://seizethemeansofcomputation.org

I’m kickstarting the audiobook for “The Internet Con: How To Seize the Means of Computation,” a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It’s a DRM-free book, which means Audible won’t carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation

If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai

[Image ID: An anatomical drawing of a flayed human head; it has been altered to give it a wide-stretched mouth revealing a gadget nestled in the back of the figure's throat, connected by a probe whose two coiled wires stretch to an old fashioned electronic box. The head's eyes have been replaced by the red, menacing eye of HAL 9000 from Stanley Kubrick's '2001: A Space Odyssey.' Behind the head is a code waterfall effect as seen in the credits of the Wachowskis' 'The Matrix.']

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#chaffing#spoofing#remote attestation#rene descartes#adversarial interoperability#war on general purpose computing#canvas attacks#vpns#compelled speech#onion routing#owner override#stalkerware#ngscb#palladium#trusted computing#secure enclaves#tor#interop#net neutrality#taking the fifth#right to remain silent#real names policy#the zuckerberg doctrine#none of your business#the right to lie#right to repair#bossware#spyware#wei web environment integrity
2K notes
·
View notes
Text
Intraoperative radiation therapy (IORT) is currently a breast cancer treatment technique that delivers radiation treatment at the same time as lumpectomy surgery. The radiation dose is delivered to an exposed tumor bed while surrounding healthy tissue is moved aside and spared from high dose radiation.
0 notes
Text
This Week in Rust 518
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Project/Tooling Updates
Strobe Crate
System dependencies are hard (so we made them easier)
Observations/Thoughts
Trying to invent a better substring search algorithm
Improving Node.js with Rust-Wasm Library
Mixing C# and Rust - Interop
A fresh look on incremental zero copy serialization
Make the Rust compiler 5% faster with this one weird trick
Part 3: Rowing Afloat Datatype Boats
Recreating concurrent futures combinators in smol
Unpacking some Rust ergonomics: getting a single Result from an iterator of them
Idea: "Using Rust", a living document
Object Soup is Made of Indexes
Analyzing Data 180,000x Faster with Rust
Issue #10: Serving HTML
Rust vs C on an ATTiny85; an embedded war story
Rust Walkthroughs
Analyzing Data /,000x Faster with Rust
Fully Automated Releases for Rust Projects
Make your Rust code unit testable with dependency inversion
Nine Rules to Formally Validate Rust Algorithms with Dafny (Part 2): Lessons from Verifying the range-set-blaze Crate
[video] Let's write a message broker using QUIC - Broke But Quick Episode 1
[video] Publishing Messages over QUIC Streams!! - Broke But Quick episode 2
Miscellaneous
[video] Associated types in Iterator bounds
[video] Rust and the Age of High-Integrity Languages
[video] Implementing (part of) a BitTorrent client in Rust
Crate of the Week
This week's crate is cargo-show-asm, a cargo subcommand to show the optimized assembly of any function.
Thanks to Kornel for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
* Hyperswitch (Hacktoberfest)- [FEATURE] separate payments_session from payments core * Hyperswitch (Hacktoberfest)- [NMI] Use connector_response_reference_id as reference to merchant * Hyperswitch (Hacktoberfest)- [Airwallex] Use connector_response_reference_id as reference to merchant * Hyperswitch (Hacktoberfest)- [Worldline] Use connector_response_reference_id as reference to merchant * Ockam - Make ockam project delete (no args) interactive by asking the user to choose from a list of space and project names to delete (tuify) * Ockam - Validate CBOR structs according to the cddl schema for authenticator/direct/types * Ockam - Slim down the NodeManagerWorker for node / node status
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
397 pull requests were merged in the last week
rewrite gdb pretty-printer registration
add FileCheck annotations to mir-opt tests
add MonoItems and Instance to stable_mir
add a csky-unknown-linux-gnuabiv2hf target
add a test showing failing closure signature inference in new solver
add new simpler and more explicit syntax for check-cfg
add stable Instance::body() and RustcInternal trait
automatically enable cross-crate inlining for small functions
avoid a track_errors by bubbling up most errors from check_well_formed
avoid having rustc_smir depend on rustc_interface or rustc_driver
coverage: emit mappings for unused functions without generating stubs
coverage: emit the filenames section before encoding per-function mappings
coverage: fix inconsistent handling of function signature spans
coverage: move most per-function coverage info into mir::Body
coverage: simplify the injection of coverage statements
disable missing_copy_implementations lint on non_exhaustive types
do not bold main message in --error-format=short
don't ICE when encountering unresolved regions in fully_resolve
don't compare host param by name
don't crash on empty match in the nonexhaustive_omitted_patterns lint
duplicate ~const bounds with a non-const one in effects desugaring
eliminate rustc_attrs::builtin::handle_errors in favor of emitting errors directly
fix a performance regression in obligation deduplication
fix implied outlives check for GAT in RPITIT
fix spans for removing .await on for expressions
fix suggestion for renamed coroutines feature
implement an internal lint encouraging use of Span::eq_ctxt
implement jump threading MIR opt
implement rustc part of RFC 3127 trim-paths
improve display of parallel jobs in rustdoc-gui tester script
initiate the inner usage of cfg_match (Compiler)
lint non_exhaustive_omitted_patterns by columns
location-insensitive polonius: consider a loan escaping if an SCC has member constraints applied only
make #[repr(Rust)] incompatible with other (non-modifier) representation hints like C and simd
make rustc_onunimplemented export path agnostic
mention into_iter on borrow errors suggestions when appropriate
mention the syntax for use on mod foo; if foo doesn't exist
panic when the global allocator tries to register a TLS destructor
point at assoc fn definition on type param divergence
preserve unicode escapes in format string literals when pretty-printing AST
properly account for self ty in method disambiguation suggestion
report unused_import for empty reexports even it is pub
special case iterator chain checks for suggestion
strict provenance unwind
suggest ; after bare match expression E0308
suggest constraining assoc types in more cases
suggest relaxing implicit type Assoc: Sized; bound
suggest removing redundant arguments in format!()
uplift movability and mutability, the simple way
miri: avoid a linear scan over the entire int_to_ptr_map on each deallocation
miri: fix rounding mode check in SSE4.1 round functions
miri: intptrcast: remove information about dead allocations
disable effects in libcore again
add #[track_caller] to Option::unwrap_or_else
specialize Bytes<R>::next when R is a BufReader
make TCP connect handle EINTR correctly
on Windows make read_dir error on the empty path
hashbrown: add low-level HashTable API
codegen_gcc: add support for NonNull function attribute
codegen_gcc: fix #[inline(always)] attribute and support unsigned comparison for signed integers
codegen_gcc: fix endianness
codegen_gcc: fix int types alignment
codegen_gcc: optimize popcount implementation
codegen_gcc: optimize u128/i128 popcounts further
cargo add: Preserve more comments
cargo remove: Preserve feature comments
cargo replace: Partial-version spec support
cargo: Provide next steps for bad -Z flag
cargo: Suggest cargo-search on bad commands
cargo: adjust -Zcheck-cfg for new rustc syntax and behavior
cargo: if there's a version in the lock file only use that exact version
cargo: make the precise field of a source an Enum
cargo: print environment variables for build script executions with -vv
cargo: warn about crate name's format when creating new crate
rustdoc: align stability badge to baseline instead of bottom
rustdoc: avoid allocating strings primitive link printing
clippy: map_identity: allow closure with type annotations
clippy: map_identity: recognize tuple identity function
clippy: add lint for struct field names
clippy: don't emit needless_pass_by_ref_mut if the variable is used in an unsafe block or function
clippy: make multiple_unsafe_ops_per_block ignore await desugaring
clippy: needless pass by ref mut closure non async fn
clippy: now declare_interior_mutable_const and borrow_interior_mutable_const respect the ignore-interior-mutability configuration entry
clippy: skip if_not_else lint for '!= 0'-style checks
clippy: suggest passing function instead of calling it in closure for option_if_let_else
clippy: warn missing_enforced_import_renames by default
rust-analyzer: generate descriptors for all unstable features
rust-analyzer: add command for only opening external docs and attempt to fix vscode-remote issue
rust-analyzer: add incorrect case diagnostics for module names
rust-analyzer: fix VS Code detection for Insiders version
rust-analyzer: import trait if needed for unqualify_method_call assist
rust-analyzer: pick a better name for variables introduced by replace_is_some_with_if_let_some
rust-analyzer: store binding mode for each instance of a binding independently
perf: add NES emulation runtime benchmark
Rust Compiler Performance Triage
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Add f16 and f128 float types
Unicode and escape codes in literals
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
[disposition: merge] Consider alias bounds when computing liveness in NLL (but this time sound hopefully)
[disposition: close] regression: parameter type may not live long enough
[disposition: merge] Remove support for compiler plugins.
[disposition: merge] rustdoc: Document lack of object safety on affected traits
[disposition: merge] Stabilize Ratified RISC-V Target Features
[disposition: merge] Tracking Issue for const mem::discriminant
New and Updated RFCs
[new] eRFC: #[should_move] attribute for per-function opting out of Copy semantics
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2023-10-25 - 2023-11-22 🦀
Virtual
2023-10-30 | Virtual (Melbourne, VIC, AU) | Rust Melbourne
(Hybrid - online & in person) October 2023 Rust Melbourne Meetup
2023-10-31 | Virtual (Europe / Africa) | Rust for Lunch
Rust Meet-up
2023-11-01 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
ECS with Bevy Game Engine
2023-11-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2023-11-02 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-07 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2023-11-09 | Virtual (Nuremberg, DE) | Rust Nuremberg
Rust Nürnberg online
2023-11-14 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2023-11-15 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
Building Our Own Locks (Atomics & Locks Chapter 9)
2023-11-15 | Virtual (Richmond, VA, US) | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-15 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2023-11-16 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-21 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
Europe
2023-10-25 | Dublin, IE | Rust Dublin
Biome, web development tooling with Rust
2023-10-25 | Paris, FR | Rust Paris
Rust for the web - Paris meetup #61
2023-10-25 | Zagreb, HR | impl Zagreb for Rust
Rust Meetup 2023/10: Lunatic
2023-10-26 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
Augsburg Rust Meetup #3
2023-10-26 | Copenhagen, DK | Copenhagen Rust Community
Rust metup #41 sponsored by Factbird
2023-10-26 | Delft, NL | Rust Nederland
Rust at TU Delft
2023-10-26 | Lille, FR | Rust Lille
Rust Lille #4 at SFEIR
2022-10-30 | Stockholm, SE | Stockholm Rust
Rust Meetup @Aira + Netlight
2023-11-01 | Cologne, DE | Rust Cologne
Web-applications with axum: Hello CRUD!
2023-11-07 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake
2023-11-07 | Brussels, BE | Rust Aarhus
Rust Aarhus - Rust and Talk beginners edition
2023-11-07 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #7
2023-11-09 | Barcelona, ES | BcnRust
11th BcnRust Meetup
2023-11-09 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2023-11-21 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
GPU processing in Rust
2023-11-23 | Biel/Bienne, CH | Rust Bern
Rust Talks Bern @ Biel: Embedded Edition
North America
2023-10-25 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2023-10-25 | Chicago, IL, US | Deep Dish Rust
Rust Happy Hour
2023-11-01 | Brookline, MA, US | Boston Rust Meetup
Boston Common Rust Lunch
2023-11-08 | Boulder, CO, US | Boulder Rust Meetup
Let's make a Discord bot!
2023-11-14 | New York, NY, US | Rust NYC
Rust NYC Monthly Mixer: Share, Show, & Tell! 🦀
2023-11-14 | Seattle, WA, US | Cap Hill Rust Coding/Hacking/Learning
Rusty Coding/Hacking/Learning Night
2023-11-15 | Richmond, VA, US + Virtual | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-16 | Nashville, TN, US | Music City Rust Developers
Python loves Rust!
2023-11-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2023-11-21 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2023-11-22 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
Oceania
2023-10-26 | Brisbane, QLD, AU | Rust Brisbane
October Meetup
2023-10-30 | Melbourne, VIC, AU + Virtual | Rust Melbourne
(Hybrid - in person & online) October 2023 Rust Melbourne Meetup
2023-11-21 | Christchurch, NZ | Christchurch Rust Meetup Group
Christchurch Rust meetup meeting
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
When your Rust build times get slower after adding some procedural macros:
We call that the syn tax :ferris:
– Janet on Fosstodon
Thanks to Jacob Pratt for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
9 notes
·
View notes
Video
Spokane, Portland & Seattle SPS 802 (EMD F3-A) Stevenson, Washington por Terry Redeker
Por Flickr:
Columbia Gorge Interoperative Center
7 notes
·
View notes

