#vpns
Text
Forcing your computer to rat you out

Powerful people imprisoned by the cluelessness of their own isolation, locked up with their own motivated reasoning: “It’s impossible to get a CEO to understand something when his quarterly earnings call depends on him not understanding it.”
Take Mark Zuckerberg. Zuckerberg insists that anyone who wanted to use a pseudonym online is “two-faced,” engaged in dishonest social behavior. The Zuckerberg Doctrine claims that forcing people to use their own names is a way to ensure civility. This is an idea so radioactively wrong, it can be spotted from orbit.
From the very beginning, social scientists (both inside and outside Facebook) told Zuckerberg that he was wrong. People have lots of reasons to hide their identities online, both good and bad, but a Real Names Policy affects different people differently:
https://memex.craphound.com/2018/01/22/social-scientists-have-warned-zuck-all-along-that-the-facebook-theory-of-interaction-would-make-people-angry-and-miserable/
For marginalized and at-risk people, there are plenty of reasons to want to have more than one online identity — say, because you are a #MeToo whistleblower hoping that Harvey Weinstein won’t sic his ex-Mossad mercenaries on you:
https://www.newyorker.com/news/news-desk/harvey-weinsteins-army-of-spies
Or maybe you’re a Rohingya Muslim hoping to avoid the genocidal attentions of the troll army that used Facebook to organize — under their real, legal names — to rape and murder you and everyone you love:
https://www.amnesty.org/en/latest/news/2022/09/myanmar-facebooks-systems-promoted-violence-against-rohingya-meta-owes-reparations-new-report/
But even if no one is looking to destroy your life or kill you and your family, there are plenty of good reasons to present different facets of your identity to different people. No one talks to their lover, their boss and their toddler in exactly the same way, or reveals the same facts about their lives to those people. Maintaining different facets to your identity is normal and healthy — and the opposite, presenting the same face to everyone in your life, is a wildly terrible way to live.
None of this is controversial among social scientists, nor is it hard to grasp. But Zuckerberg stubbornly stuck to this anonymity-breeds-incivility doctrine, even as dictators used the fact that Facebook forced dissidents to use their real names to retain power through the threat (and reality) of arrest and torture:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Why did Zuck cling to this dangerous and obvious fallacy? Because the more he could collapse your identity into one unitary whole, the better he could target you with ads. Truly, it is impossible to get a billionaire to understand something when his mega-yacht depends on his not understanding it.
This motivated reasoning ripples through all of Silicon Valley’s top brass, producing what Anil Dash calls “VC QAnon,” the collection of conspiratorial, debunked and absurd beliefs embraced by powerful people who hold the digital lives of billions of us in their quivering grasp:
https://www.anildash.com/2023/07/07/vc-qanon/
These fallacy-ridden autocrats like to disguise their demands as observations, as though wanting something to be true was the same as making it true. Think of when Eric Schmidt — then the CEO of Google — dismissed online privacy concerns, stating “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place”:
https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy
Schmidt was echoing the sentiments of his old co-conspirator, Sun Microsystems CEO Scott McNealy: “You have zero privacy anyway. Get over it”:
https://www.wired.com/1999/01/sun-on-privacy-get-over-it/
Both men knew better. Schmidt, in particular, is very jealous of his own privacy. When Cnet reporters used Google to uncover and publish public (but intimate and personal) facts about Schmidt, Schmidt ordered Google PR to ignore all future requests for comment from Cnet reporters:
https://www.cnet.com/tech/tech-industry/how-cnet-got-banned-by-google/
(Like everything else he does, Elon Musk’s policy of responding to media questions about Twitter with a poop emoji is just him copying things other people thought up, making them worse, and taking credit for them:)
https://www.theverge.com/23815634/tesla-elon-musk-origin-founder-twitter-land-of-the-giants
Schmidt’s actions do not reflect an attitude of “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Rather, they are the normal response that we all have to getting doxed.
When Schmidt and McNealy and Zuck tell us that we don’t have privacy, or we don’t want privacy, or that privacy is bad for us, they’re disguising a demand as an observation. “Privacy is dead” actually means, “When privacy is dead, I will be richer than you can imagine, so stop trying to save it, goddamnit.”
We are all prone to believing our own bullshit, but when a tech baron gets high on his own supply, his mental contortions have broad implications for all of us. A couple years after Schmidt’s anti-privacy manifesto, Google launched Google Plus, a social network where everyone was required to use their “real name.”
This decision — justified as a means of ensuring civility and a transparent ruse to improve ad targeting — kicked off the Nym Wars:
https://epeus.blogspot.com/2011/08/google-plus-must-stop-this-identity.html
One of the best documents to come out of that ugly conflict is “Falsehoods Programmers Believe About Names,” a profound and surprising enumeration of all the ways that the experiences of tech bros in Silicon Valley are the real edge-cases, unreflective of the reality of billions of their users:
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
This, in turn, spawned a whole genre of programmer-fallacy catalogs, falsehoods programmers believe about time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families:
https://github.com/kdeldycke/awesome-falsehood
But humility is in short supply in tech. It’s impossible to get a programmer to understand something when their boss requires them not to understand it. A programmer will happily insist that ordering you to remove your “mask” is for your own good — and not even notice that they’re taking your skin off with it.
There are so many ways that tech executives could improve their profits if only we would abandon our stubborn attachment to being so goddamned complicated. Think of Netflix and its anti-passsword-sharing holy war, which is really a demand that we redefine “family” to be legible and profitable for Netflix:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
But despite the entreaties of tech companies to collapse our identities, our families, and our online lives into streamlined, computably hard-edged shapes that fit neatly into their database structures, we continue to live fuzzy, complicated lives that only glancingly resemble those of the executives seeking to shape them.
Now, the rich, powerful people making these demands don’t plan on being constrained by them. They are conservatives, in the tradition of #FrankWilhoit, believers in a system of “in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect”:
https://crookedtimber.org/2018/03/21/liberals-against-progressives/#comment-729288
As with Schmidt’s desire to spy on you from asshole to appetite for his own personal gain, and his violent aversion to having his own personal life made public, the tech millionaires and billionaires who made their fortune from the flexibility of general purpose computers would like to end that flexibility. They insist that the time for general purpose computers has passed, and that today, “consumers” crave the simplicity of appliances:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
It is in the War On General Purpose Computing that we find the cheapest and flimsiest rhetoric. Companies like Apple — and their apologists — insist that no one wants to use third-party app stores, or seek out independent repair depots — and then spend millions to make sure that it’s illegal to jailbreak your phone or get it fixed outside of their own official channel:
https://doctorow.medium.com/apples-cement-overshoes-329856288d13
The cognitive dissonance of “no one wants this,” and “we must make it illegal to get this” is powerful, but the motivated reasoning is more powerful still. It is impossible to get Tim Cook to understand something when his $49 million paycheck depends on him not understanding it.
The War on General Purpose Computing has been underway for decades. Computers, like the people who use them, stubbornly insist on being reality-based, and the reality of computers is that they are general purpose. Every computer is a Turing complete, universal Von Neumann machine, which means that it can run every valid program. There is no way to get a computer to be almost Turing Complete, only capable of running programs that don’t upset your shareholders’ fragile emotional state.
There is no such thing as a printer that will only run the “reject third-party ink” program. There is no such thing as a phone that will only run the “reject third-party apps” program. There are only laws, like the Section 1201 of the Digital Millennium Copyright Act, that make writing and distributing those programs a felony punishable by a five-year prison sentence and a $500,000 fine (for a first offense).
That is to say, the War On General Purpose Computing is only incidentally a technical fight: it is primarily a legal fight. When Apple says, “You can’t install a third party app store on your phone,” what they means is, “it’s illegal to install that third party app store.” It’s not a technical countermeasure that stands between you and technological self-determination, it’s a legal doctrine we can call “felony contempt of business model”:
https://locusmag.com/2020/09/cory-doctorow-ip/
But the mighty US government will not step in to protect a company’s business model unless it at least gestures towards the technical. To invoke DMCA 1201, a company must first add the thinnest skin of digital rights management to their product. Since 1201 makes removing DRM illegal, a company can use this molecule-thick scrim of DRM to felonize any activity that the DRM prevents.
More than 20 years ago, technologists started to tinker with ways to combine the legal and technical to tame the wild general purpose computer. Starting with Microsoft’s Palladium project, they theorized a new “Secure Computing” model for allowing companies to reach into your computer long after you had paid for it and brought it home, in order to discipline you for using it in ways that undermined its shareholders’ interest.
Secure Computing began with the idea of shipping every computer with two CPUs. The first one was the normal CPU, the one you interacted with when you booted it up, loaded your OS, and ran programs. The second CPU would be a Trusted Platform Module, a brute-simple system-on-a-chip designed to be off-limits to modification, even by its owner (that is, you).
The TPM would ship with a limited suite of simple programs it could run, each thoroughly audited for bugs, as well as secret cryptographic signing keys that you were not permitted to extract. The original plan called for some truly exotic physical security measures for that TPM, like an acid-filled cavity that would melt the chip if you tried to decap it or run it through an electron-tunneling microscope:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
This second computer represented a crack in the otherwise perfectly smooth wall of a computer’s general purposeness; and Trusted Computing proposed to hammer a piton into that crack and use it to anchor a whole superstructure that could observe — and limited — the activity of your computer.
This would start with observation: the TPM would observe every step of your computer’s boot sequence, creating cryptographic hashes of each block of code as it loaded and executed. Each stage of the boot-up could be compared to “known good” versions of those programs. If your computer did something unexpected, the TPM could halt it in its tracks, blocking the boot cycle.
What kind of unexpected things do computers do during their boot cycle? Well, if your computer is infected with malware, it might load poisoned versions of its operating system. Once your OS is poisoned, it’s very hard to detect its malicious conduct, since normal antivirus programs rely on the OS to faithfully report what your computer is doing. When the AV program asks the OS to tell it which programs are running, or which files are on the drive, it has no choice but to trust the OS’s response. When the OS is compromised, it can feed a stream of lies to users’ programs, assuring these apps that everything is fine.
That’s a very beneficial use for a TPM, but there’s a sinister flipside: the TPM can also watch your boot sequence to make sure that there aren’t beneficial modifications present in your operating system. If you modify your OS to let you do things the manufacturer wants to prevent — like loading apps from a third-party app-store — the TPM can spot this and block it.
Now, these beneficial and sinister uses can be teased apart. When the Palladium team first presented its research, my colleague Seth Schoen proposed an “owner override”: a modification of Trusted Computing that would let the computer’s owner override the TPM:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
This override would introduce its own risks, of course. A user who was tricked into overriding the TPM might expose themselves to malicious software, which could harm that user, as well as attacking other computers on the user’s network and the other users whose data were on the compromised computer’s drive.
But an override would also provide serious benefits: it would rule out the monopolistic abuse of a TPM to force users to run malicious code that the manufacturer insisted on — code that prevented the user from doing things that benefited the user, even if it harmed the manufacturer’s shareholders. For example, with owner override, Microsoft couldn’t force you to use its official MS Office programs rather than third-party compatible programs like Apple’s iWork or Google Docs or LibreOffice.
Owner override also completely changed the calculus for another, even more dangerous part of Trusted Computing: remote attestation.
Remote Attestation is a way for third parties to request a reliable, cryptographically secured assurances about which operating system and programs your computer is running. In Remote Attestation, the TPM in your computer observes every stage of your computer’s boot, gathers information about all the programs you’re running, and cryptographically signs them, using the signing keys the manufacturer installed during fabrication.
You can send this “attestation” to other people on the internet. If they trust that your computer’s TPM is truly secure, then they know that you have sent them a true picture of your computer’s working (the actual protocol is a little more complicated and involves the remote party sending you a random number to cryptographically hash with the attestation, to prevent out-of-date attestations).
Now, this is also potentially beneficial. If you want to make sure that your technologically unsophisticated friend is running an uncompromised computer before you transmit sensitive data to it, you can ask them for an attestation that will tell you whether they’ve been infected with malware.
But it’s also potentially very sinister. Your government can require all the computers in its borders to send a daily attestation to confirm that you’re still running the mandatory spyware. Your abusive spouse — or abusive boss — can do the same for their own disciplinary technologies. Such a tool could prevent you from connecting to a service using a VPN, and make it impossible to use Tor Browser to protect your privacy when interacting with someone who wishes you harm.
The thing is, it’s completely normal and good for computers to lie to other computers on behalf of their owners. Like, if your IoT ebike’s manufacturer goes out of business and all their bikes get bricked because they can no longer talk to their servers, you can run an app that tricks the bike into thinking that it’s still talking to the mothership:
https://nltimes.nl/2023/07/15/alternative-app-can-unlock-vanmoof-bikes-popular-amid-bankruptcy-fears
Or if you’re connecting to a webserver that tries to track you by fingerprinting you based on your computer’s RAM, screen size, fonts, etc, you can order your browser to send random data about this stuff:
https://jshelter.org/fingerprinting/
Or if you’re connecting to a site that wants to track you and nonconsensually cram ads into your eyeballs, you can run an adblocker that doesn’t show you the ads, but tells the site that it did:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Owner override leaves some of the beneficial uses of remote attestation intact. If you’re asking a friend to remotely confirm that your computer is secure, you’re not going to use an override to send them bad data about about your computer’s configuration.
And owner override also sweeps all of the malicious uses of remote attestation off the board. With owner override, you can tell any lie about your computer to a webserver, a site, your boss, your abusive spouse, or your government, and they can’t spot the lie.
But owner override also eliminates some beneficial uses of remote attestation. For example, owner override rules out remote attestation as a way for strangers to play multiplayer video games while confirming that none of them are using cheat programs (like aimhack). It also means that you can’t use remote attestation to verify the configuration of a cloud server you’re renting in order to assure yourself that it’s not stealing your data or serving malware to your users.
This is a tradeoff, and it’s a tradeoff that’s similar to lots of other tradeoffs we make online, between the freedom to do something good and the freedom to do something bad. Participating anonymously, contributing to free software, distributing penetration testing tools, or providing a speech platform that’s open to the public all represent the same tradeoff.
We have lots of experience with making the tradeoff in favor of restrictions rather than freedom: powerful bad actors are happy to attach their names to their cruel speech and incitement to violence. Their victims are silenced for fear of that retaliation.
When we tell security researchers they can’t disclose defects in software without the manufacturer’s permission, the manufacturers use this as a club to silence their critics, not as a way to ensure orderly updates.
When we let corporations decide who is allowed to speak, they act with a mixture of carelessness and self-interest, becoming off-the-books deputies of authoritarian regimes and corrupt, powerful elites.
Alas, we made the wrong tradeoff with Trusted Computing. For the past twenty years, Trusted Computing has been creeping into our devices, albeit in somewhat denatured form. The original vision of acid-filled secondary processors has been replaced with less exotic (and expensive) alternatives, like “secure enclaves.” With a secure enclave, the manufacturer saves on the expense of installing a whole second computer, and instead, they draw a notional rectangle around a region of your computer’s main chip and try really hard to make sure that it can only perform a very constrained set of tasks.
This gives us the worst of all worlds. When secure enclaves are compromised, we not only lose the benefit of cryptographic certainty, knowing for sure that our computers are only booting up trusted, unalterted versions of the OS, but those compromised enclaves run malicious software that is essentially impossible to detect or remove:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
But while Trusted Computing has wormed its way into boot-restrictions — preventing you from jailbreaking your computer so it will run the OS and apps of your choosing — there’s been very little work on remote attestation…until now.
Web Environment Integrity is Google’s proposal to integrate remote attestation into everyday web-browsing. The idea is to allow web-servers to verify what OS, extensions, browser, and add-ons your computer is using before the server will communicate with you:
https://github.com/RupertBenWiser/Web-Environment-Integrity/blob/main/explainer.md
Even by the thin standards of the remote attestation imaginaries, there are precious few beneficial uses for this. The googlers behind the proposal have a couple of laughable suggestions, like, maybe if ad-supported sites can comprehensively refuse to serve ad-blocking browsers, they will invest the extra profits in making things you like. Or: letting websites block scriptable browsers will make it harder for bad people to auto-post fake reviews and comments, giving users more assurances about the products they buy.
But foundationally, WEI is about compelling you to disclose true facts about yourself to people who you want to keep those facts from. It is a Real Names Policy for your browser. Google wants to add a new capability to the internet: the ability of people who have the power to force you to tell them things to know for sure that you’re not lying.
The fact that the authors assume this will be beneficial is just another “falsehood programmers believe”: there is no good reason to hide the truth from other people. Squint a little and we’re back to McNealy’s “Privacy is dead, get over it.” Or Schmidt’s “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
And like those men, the programmers behind this harebrained scheme don’t imagine that it will ever apply to them. As Chris Palmer — who worked on Chromium — points out, this is not compatible with normal developer tools or debuggers, which are “incalculably valuable and not really negotiable”:
https://groups.google.com/a/chromium.org/g/blink-dev/c/Ux5h_kGO22g/m/5Lt5cnkLCwAJ
This proposal is still obscure in the mainstream, but in tech circles, it has precipitated a flood of righteous fury:
https://arstechnica.com/gadgets/2023/07/googles-web-integrity-api-sounds-like-drm-for-the-web/
As I wrote last week, giving manufacturers the power to decide how your computer is configured, overriding your own choices, is a bad tradeoff — the worst tradeoff, a greased slide into terminal enshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is how you get Unauthorized Bread:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
All of which leads to the question: what now? What should be done about WEI and remote attestation?
Let me start by saying: I don’t think it should be illegal for programmers to design and release these tools. Code is speech, and we can’t understand how this stuff works if we can’t study it.
But programmers shouldn’t deploy it in production code, in the same way that programmers should be allowed to make pen-testing tools, but shouldn’t use them to attack production systems and harm their users. Programmers who do this should be criticized and excluded from the society of their ethical, user-respecting peers.
Corporations that use remote attestation should face legal restrictions: privacy law should prevent the use of remote attestation to compel the production of true facts about users or the exclusion of users who refuse to produce those facts. Unfair competition law should prevent companies from using remote attestation to block interoperability or tie their products to related products and services.
Finally, we must withdraw the laws that prevent users and programmers from overriding TPMs, secure enclaves and remote attestations. You should have the right to study and modify your computer to produce false attestations, or run any code of your choosing. Felony contempt of business model is an outrage. We should alter or strike down DMCA 1201, the Computer Fraud and Abuse Act, and other laws (like contract law’s “tortious interference”) that stand between you and “sole and despotic dominion” over your own computer. All of that applies not just to users who want to reconfigure their own computers, but also toolsmiths who want to help them do so, by offering information, code, products or services to jailbreak and alter your devices.
Tech giants will squeal at this, insisting that they serve your interests when they prevent rivals from opening up their products. After all, those rivals might be bad guys who want to hurt you. That’s 100% true. What is likewise true is that no tech giant will defend you from its own bad impulses, and if you can’t alter your device, you are powerless to stop them:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Companies should be stopped from harming you, but the right place to decide whether a business is doing something nefarious isn’t in the boardroom of that company’s chief competitor: it’s in the halls of democratically accountable governments:
https://www.eff.org/wp/interoperability-and-privacy
So how do we get there? Well, that’s another matter. In my next book, The Internet Con: How to Seize the Means of Computation (Verso Books, Sept 5), I lay out a detailed program, describing which policies will disenshittify the internet, and how to get those policies:
https://www.versobooks.com/products/3035-the-internet-con
Predictably, there are challenges getting this kind of book out into the world via our concentrated tech sector. Amazon refuses to carry the audio edition on its monopoly audiobook platform, Audible, unless it is locked to Amazon forever with mandatory DRM. That’s left me self-financing my own DRM-free audio edition, which is currently available for pre-order via this Kickstarter:
http://seizethemeansofcomputation.org

I’m kickstarting the audiobook for “The Internet Con: How To Seize the Means of Computation,” a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It’s a DRM-free book, which means Audible won’t carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation

If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai

[Image ID: An anatomical drawing of a flayed human head; it has been altered to give it a wide-stretched mouth revealing a gadget nestled in the back of the figure's throat, connected by a probe whose two coiled wires stretch to an old fashioned electronic box. The head's eyes have been replaced by the red, menacing eye of HAL 9000 from Stanley Kubrick's '2001: A Space Odyssey.' Behind the head is a code waterfall effect as seen in the credits of the Wachowskis' 'The Matrix.']

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#chaffing#spoofing#remote attestation#rene descartes#adversarial interoperability#war on general purpose computing#canvas attacks#vpns#compelled speech#onion routing#owner override#stalkerware#ngscb#palladium#trusted computing#secure enclaves#tor#interop#net neutrality#taking the fifth#right to remain silent#real names policy#the zuckerberg doctrine#none of your business#the right to lie#right to repair#bossware#spyware#wei web environment integrity
2K notes
·
View notes
Text
VPNs aren't just for pirates and company data anymore
A friend complained to me that they couldn't access pr0n anymore because the government is now requiring ID to verify age where they are, and due to data leaks and privacy issues, didn't want to share their ID even though they're of legal age.
Shit like this doesn't work on the intended target. It only frustrates people who are aren't tech savvy while a lot of kids have already found their way around it because that's what kids do ¯\_(ツ)_/¯
When I talk about VPNs (virtual private networks), non-tech savvy people's eyes glaze over 😂
It sounds like complicated, unknowable magic. It's not! And you don't even have to understand it to use it!
With the government and ISPs (internet service providers) invading privacy more and more and hackers breaking in and stealing user data from companies, VPNs are becoming necessary.
Some Things a VPN Does for You:
hides your data from others
can make your internet speeds faster if your ISP does speed throttling (purposely making your speed slower)
hides what you're doing from your ISP
keeps you safer from some malware, viruses, hackers, and trackers
allows you to access things that are either restricted in your area or not available in your area (such as content in other countries)
keeps you safer when you're out in public connected to wifi
Below is a basic infographic on how VPNs work. When you access the internet, a VPN encrypts your data - making it into a secret code that can't be read by anyone else including your ISP.
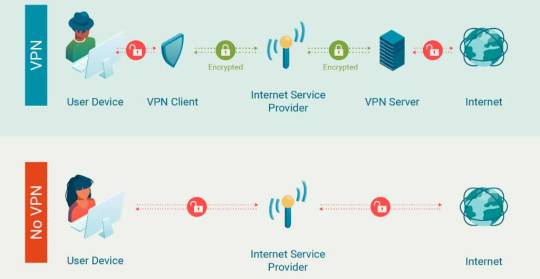
Tech companies, ISPs, etc. want you to think VPNs are complicated so that you won't use them.
When searching for a free VPN, please be aware that a lot of the free VPN services out there are malware or full of viruses and trackers.
Either do some research into which one to choose or use a paid VPN service. You can either pay monthly or yearly - the yearly is always cheaper in the long run.
Some of the Top Rated VPN Services:
ExpressVPN $7 - $13/month
NordVPN $3 - $13/month
Surfshark $2 - $14/month
PrivateInternetAccess $2 - $12/month
ProtonVPN (some sites block this one) $4 - $10/month
CyberGhost $2 - $13/month
I use ExpressVPN, so for the purposes of this post, I'm going to use screenshots from ExpressVPN.
Once you have an account, download the program from the website to your desktop/laptop or find the app on Android or iOS app stores.
Signing in requires a code that the VPN will email to you that unlocks all the features. Pay attention when the program installs because it'll ask you about preferences, and you can easily check yes on blocking pr0n when that's the reason you wanted a VPN in the first place 😂
When the program is open, you'll see this:

As you can see in the screenshot, not only do I have the program, but I have an ExpressVPN icon on my browser. The program installs this automatically, and when the program is running, the icon will have a green checkmark on it so you know it's working in your browser.
You'll notice I've recently connected using Japan. I did this so I could watch a series that isn't available outside of Japan.
The program automatically chooses a location near you, but if you want to access things that are restricted to you, make sure you click on the three dots to the right of the selected location (see screenshot below) and search for a state/country/place that your content will be available in.

Once your location is selected, click on the start/power button, and you'll get a popup notification from your computer that ExpressVPN is connected.
Go to the site you want to use and use it like you normally would.
Here's what it should look like when it's running correctly:

Keep in mind that if you leave a VPN running all the time (which is perfectly fine to do), search engines like Google will assume you live wherever ExpressVPN tells it you live, so searching for "stores near me" will give you results that aren't close to you.
When you're done using the VPN, just hit the power button again and it shuts off.
I use this on all my handheld devices, my desktop, and my laptop for business and personal reasons. I'm a pirate, and I've been using VPNs for a long time, yet none of the ISPs I've used have ever given me a warning about torrenting.
Good luck, and enjoy all the new things you can access!
BTW for anybody wondering, my desktop wallpaper is a map of the world's time zones. So pretty!! 😍
56 notes
·
View notes
Text
Do you actually need a VPN?
probably not
Possible bias: this tool IS made by a VPN company, however I feel like it's accurate anyway.
It does say you need a VPN to access blocked websites and services, but you should be able to be access them with Tor (free) as well.
"Untrusted Wifi" as well, most of your internet traffic is already encrypted through https, though they can still see the domain (tumblr.com) you connect to (but not tumblr.com/whatever). Turn on HTTPS-only mode in firefox settings to be sure.
youtube
37 notes
·
View notes
Text
One of the funnier parts of using a VPN: going to a different VPN's website and getting a banner at the top that's like "You aren't protected! I can see that your IP address is (VPN's address) and your location is (datacenter 1000 miles away from where I live)!!!"
15 notes
·
View notes
Note
Hello! I just found your post on pirating. I'm relatively experienced and I think most everything you suggested is smart.
I just wanted to ask, in regards to the VPN, do you have in particular gripes about Proton in regards to the privacy aspect?
I was trying to find a good VPN recently and thought that Proton's offers were pretty good, if expensive in comparison to the competition.
(I promise I'm not a shill, I'm actually wondering if I should regret my purchase lol. I also get that the post is dated last year and things may have gotten worse or better with them since)
Hi!! Sorry for the very very late reply, I didn't check tumblr for months.
To be honest, I did write that post a while ago and should I write it now, my position would be different and much milder. While throwing shade at Proton I was thinking of this incident specifically where, facing a court order, Proton was asked to log and provide the IP address of one of its clients, a French climate activist.
I take issue with companies that market themselves as useful tools to keep you safe and protected instead of actually disclosing what their service truly is about and what data they do have about you, as people might fall into a false sense of security and have no idea what they're actually paying for.
I am generally more warm towards Mullvad since they're extremely transparent about what kind of data they have on you and actively try to get as little data from you as possible, even favouring payment methods where they won't have to store any data on you whatsoever. They also allegedly were subject to a search warrant and were simply unable to give any data whatsoever as they truly had none, which if we want to assume good faith that they aren't making that up, is a good look on them as a whole. Though they've recently started to market themselves as some kind of saviours from "mass surveillance and censorship" in a way that seems... to be really alarmist and out of nowhere and might fool more people into thinking they need a vpn than they actually do, and I'm not happy about that direction at all, though their services still seem like some of the best around.
Still - I recognize that this is a big discussion, one I don't have enough knowledge over to completely discuss it either! And that for torrenting... this doesn't matter at all. In fact, Mullvad is not being recommended for torrenting anymore as it dropped support for port forwarding - for some apparently legit concerns - and it makes the torrenting experience much worse for many people. (My internet is slow as shit so I don't notice either way lol!)
All in all, I'm not a very experienced or savvy user at all. I try to learn about things as much as my lil brain allows me to understand, but were I to rewrite that post now, I wouldn't mention things that are still so murky/difficult to understand for me as well. Hope I sent you some interesting links to start some more research from though! Here's to understanding more of how things work as we go on :D
12 notes
·
View notes
Text
Okay, so. I finally downloaded a VPN so I could watch Doctor Who on the BBC site, but even with my location set to London, it's still not working. I clicked on the little troubleshooting link (of course I'm in the UK BBC, don't you see my IP address?), and one of the suggestions was to turn off any VPNs. Is this just in case a British person forgot their IP address was set to somewhere else, and maybe the VPN I got isn't very good, or is it not possible to watch on the BBC site with a VPN at all? Is anybody out there having any luck with this, and if so, what VPN are you using? Or does anybody have any... other suggestions for somewhere else I could maybe watch Doctor Who online?
#Doctor Who#VPNs#streaming advice#bbc iplayer#troubleshooting#see I did buy the 13th Doctor's first season on Amazon but it's soooo annoying to have to buy every season and special individually#and I see that the 60th special is available on Disney Plus now which is great! but I don't want to jump ahead in the new series!#I jump around in the classic stuff all the time but so far I've always watched NuWho in order. and for me that means Resolution is next#and like I know spoilers from later in 13's run sure but I just want to watch it in order still#and I thought I'd figured it out but this is still all very frustrating#also the VPN I got is called Super Unlimited Proxy. I was just looking for a free one that let me do England and that's the first I found#I'm putting Thirteen's DVD box collection on my Christmas list but all of this chatter about the 60th makes me want to catch up ASAP#it's actually the first time I've bothered to filter Doctor Who spoiler tags on my tumblr dash#but I know I can only hold them off for so long...#plus I'm just in a mood for binging#even in the tags I ramble#anyways thanks in advance for any advice!#but yeah it's funny when I came back to tumblr with my vpn on it asked me about cookies and I'm like why is tumblr asking about cookies#all of a sudden? oh it thinks I'm British. lol. shouldn't it be saying biscuits then? ;)
7 notes
·
View notes
Text
Me: I need a free vpn for the time being because I actually don't have any money being [undisclosed teenager] years old. Any recs
Literally everyone: that's untrustworthy just buy-
Me: I am ALREADY ignoring you I DO NOT HAVE DOLLARS,
Like first off did you read the original thing. Second if you don't have anything actually useful that isn't j "BUY PRODUCT" like. Shh. Shhhh. I would rather have no answers than answers from people who missed the actual most important part of the post,
17 notes
·
View notes
Note
hey, i went through your pinned post and i had a couple questions abt vpns? which ones are free (i was just planning to stream off of hbo max and i don't have access to money), and how does it work after i've downloaded one? do i just go to the website of the streaming service and try to watch something? anyway thank you for your time!!
I don’t recommend any free VPNs as they are not secure with your privacy and any identifying information you give them. They will sell all your user data to advertising companies to make a profit. If you are not paying for a product, YOU are the product.
My suggestion for your use case, since you’re not torrenting and looking only to get around geo-restrictions, is to use Mullvad. It’s very very cheap for a month (only 5 Euros) and has tons of servers all around the world. You’re going to want a lot since I know recently streaming services are starting to detect and ban IP addresses they know are associated with certain VPNs. After you connect to their server it should theoretically be as easy as refreshing the website and using it like normal.
(but why go through all that trouble and pay for a VPN when you don’t have to? Have a look at the streaming sites available in FMHY wiki and make sure to use an ad blocker. Then you can watch whatever you want for free without jumping through all those hoops ;) )
4 notes
·
View notes
Text
STOP USING BIOMETRICS TO UNLOCK YOUR TECH BEFORE GOING TO A PROTEST, RALLY, OR ACCESSING BIRTH CONTROL OPTIONS
Encrypt your tech. If you are US based, or in a country that does not protect your rights when it comes to cops, please read these article. There are not currently laws stopping the police from using your thumb or face to unlock your phone without consent or a warrant. Especially if you are taking any part in any protests throughout America, or accessing birth control needs.
Or you're, you know, queer, disabled, a person of colour, a woman, or generally just know how horrible the cops and government can be. They can pull you over for no reason, unlock your phone, and look for something to charge you with later. They can and will and have.
Cops will do ANYTHING they want, and chances are, the courts will let them.
(this might be relevant for other countries, too-- the protest rights are completely fucked here in the UK, so please be careful out there!!)
Helpfully, there is also a cop-proof your phone article as well:
#biometrics#phone biometrics#techinology#cop proof your phone#stop using biometrics to unlock your tech#protests#protestors#stay safe at protests#stay safe accessing birth control#cops are unlocking your phone#encrypt your shit#vpns#all cops are bastards#all cops are bad#no good cops#stay silent and ask for representation no matter what they grab you for#police state#please spread#how to protest#columbia university#students#gaza genocide#ukraine#please keep yourselves as safe as possible#good luck but stay safe
3 notes
·
View notes
Text
Do you like VPNs? Yes? Be prepared to face a (minimum) $250,000 fine and 20 years in prison if the restrict act gets passed!
19 notes
·
View notes
Note
So if we watch it in YouTube, that start 30 mins behind, we’ll be spoiled about everything! Do you have livestreams??? Thanks Daisie 🤍🤍
Hi dear,
I don't have another livestream :( I just tried to use a VPN to watch it live and it works again (they had blocked VPNs before). So you can download one if you don't have it already. Make an account on iTV and put in a UK address and that you have a TV license.
Here are some suggestions for free VPNs (Proton doesn't work for the UK).
If you can't figure out a VPN, then I recommend just watching the Youtube stream. It's really high quality. If you don't want spoilers, stay off social media while you watch :/
18 notes
·
View notes
Text
Not only is Russia banning websites but it is now trying to block sites which describe how to get around those blocks.
The Russian government has granted the country’s federal censorship agency, Roskomnadzor, permission to restrict access to websites that contain information about circumventing Internet censorship.
According to the resolution, which is accessible on the government’s official legal information portal, Rosomnadzor is now allowed to block sites with materials “about ways [and] methods of obtaining access to information resources and/or information-telecommunications networks to which access is restricted within the territory of the Russian Federation.”
Of course there are always VPNs. And people can apparently make YouTube vids where they can describe how to get around Putin's censors.
Speaking of Putin's dictatorship in Russia, yet another high ranking member of the country's military has been found dead under suspicious circumstances.
Former Russian Commander Who Criticized Putin Found Dead in Mysterious Circumstances
A former Russian commander who once critizised President Putin for running a “third-rate” air force, has been found dead alongside his wife at their home in the village of Adzhievsky in Stavropol region.
According to reports, Lieutenant General Vladimir Sviridov, 68, and his wife Tatyana, 72, had been dead for around a week before their bodies were found on Nov. 15.
The Russian Telegram channel Baza said there were no signs of violence and no toxic substances were found in the blood of either victim, according to preliminary tests.
“Gas service workers have already taken measurements and no excess of the permissible concentration of harmful substances has been detected,” Baza wrote.
It added: “What caused the death of Vladimir and Tatyana Sviridov is still unknown.”
Putin is running a terrorist mafia-style state. The number of high ranking business executives, officials, and military people who have died under suspicious circumstances has been unusually high since the start of 2022. Being even mildly critical of Putin is a capital offense in Russia.
According to a Wikipedia page on the topic, the late Gen. Sviridov is death number 46 (if I counted correctly) of prominent Russians to die suspiciously since January of 2022.
Yeah, if you like Putin's Russia, you'd love a second term of his stooge Donald Trump in the US.
#invasion of ukraine#russia#censorship#blocking websites#vpns#rosomnadzor#vladimir putin#putin's dictatorship#russia is a mafia state#suspicious deaths in russia#vladimir sviridov#россия#роскомнадзор#минкомсвязь#владимир свиридов#цензура#мафиозное государство#владимир путин#путин хуйло#путлер#союз постсоветских клептократических ватников#россия - террористическая страна#оркостан#руки прочь от украины!#геть з україни#україна переможе#слава україні!#героям слава!
2 notes
·
View notes
Text
I COULD make a post talking about that Ban TikTok bill and how it contains articles that include criminalizing VPNs and basically giving the government access to basically all of your incoming data including your video game markets and online services and how it’s something people should be extremely worried about as a low-key Patriot Act for the Internet
But the last time I made a post about lawmakers meddling with the internet’s infrastructure I got a ton of angry DMs calling me a clout-chasing fearmonger so I’m just gonna let this one sit
8 notes
·
View notes
Note
Sorry if this is a weird question, but since you're always telling people to use firefox you seem to have strong privacy-related feelings regarding online stuff (as you should) and I'm wondering if you'd also recommend a specific VPN? There are so many options out there that I'm getting kinda lost :/
I use protonvpn! I forget why I decided on it lmao but yeah. I even cough up for one of the paid plans. It also comes with secure e-mail and a calendar, plus they've got protondrive now (it might just be beta rn? and there's no app for it...yet. but it's a thing).
There's also a new vpn service thru firefox, though I haven't read up on it recently. When I was looking at vpns I think it was brand new.
6 notes
·
View notes
Note
hey synthia, id be interested to hear your thoughts on mullvad as a vpn if thats ok. does it meet your own good vpn criteria?
it's on my recommended list on this post !
disclaimer: I haven't personally used the service but ik someone who has (and trust their opinion) and the available info about the service is both encouraging (such as server location and configuration) and unlikely to be lies (it would ve safer and legally advisable to say nothing at all rather than directly lie about eg user data privacy)
1 note
·
View note
Note
what’s a good vpn app to use?
Hi dear,
Here's a list of some free ones. I haven't tried those, so idk if they're good.
I use NordVPN but that's a paid one.
ExpressVPN has a 30-day money back trial.
If you want one of the paid ones, google coupon codes for them bc there are tons for over 70% off etc. A lot of youtubers have codes too.
3 notes
·
View notes