#the character growth and development and becoming more well rounded people through world travel was my favorite part of the show!
Text
I'll be honest, if their idea of improving on the original ATLA is to remove the character traits the characters overcame within the narrative as part of their growth because they paint the characters in a bad light or whatever, I don't think they know the show well enough to be remaking it. What next? Are they gonna erase Iroh's military history because good people can't have ever made the wrong choice in their lives? Is Toph gonna be polite and cooperative the moment they meet her because you should never be rude to people? Is Zuko just gonna be a good guy pretending to be evil because no one understands character growth and nuance is too subtle?
#from the desk of anachron#ugh#the tentative hope I had for the remake is shriveling#the character growth and development and becoming more well rounded people through world travel was my favorite part of the show!#they experienced things and met people and learned how other people live and think and they LEARNED FROM THAT!#that was the POINT
9 notes
·
View notes
Text
black eagles relationships i like but don’t see talked about enough
Ferdinand and Petra - I adore their supports. You see a lot of Ferdinand’s dorky side with his reading about historic weapons, and you see that he is genuinely curious about Petra’s culture. He admits that he initially didn’t realize how sophisticated Brigidian techniques are and I just adore his vulnerability with her. And then there’s Petra in their A support, admitting she found a second home in Fòdlan, and the two discuss their loneliness? It’s such interesting insight into both characters (especially Ferdie; I’d say these are some of his most well-rounded supports)
Hubert and Dorothea - Dorothea sees right through Hubert’s edgy theatre kid persona. She approaches him like she would any friend right from the beginning and teases him about his love life. She also respects and believes him when he says that unrequited love isn’t his motivation. I would’ve liked a conclusion that wasn’t Dorothea suggesting they marry, but it is really funny that she did that. I love their paired ending too--completely platonic espionage opera! What could be better?
Hubert and Byleth - in my head they have a quirky sitcom where Byleth keeps trying to arrange Edeleth/Ferdibert double dates and Hubert has to attend them. (but seriously, the appeal of Hubert is looking at this man and saying “I’m gonna make you like me”, and then you do it). Outside of my shipping biases, his threats to you are funny as shit considering that he has no power over you and he’s always dying in battle, but once you win his trust he admits that despite looking Blatantly Evil, he truly abhors TWSTID and is already planning their follow-up war. I could easily see him and Byleth co-leading the war in the shadows (and that’s where the dialogue of the aforementioned platonic Huleth workplace comedy takes place). Also my friend who played as m!Byleth told me the “we could be a couplet of birds” line in the A-support still exists regardless of gender. Hubert is demiromantic bi and you CANNOT change my mind
Edelgard and Petra - “Don’t settle for being the bird. Be the arrow instead” Both have a great deal of mutual respect for each other, even though Edelgard is heir to the nation that has kept Petra’s country down for years. You see the same beliefs Petra holds in her supports with Caspar here--that being, “we are not our parents, we can make different choices”. It’s a shame they only have 2 supports. I think it would’ve been cool to see Petra asking Edelgard for Brigidian independence or otherwise talking about how she can achieve her goal.
Edelgard and Linhardt - I actually think people talk about this a bit, but it’s one of my favourite Black Eagles support chains so I have to mention it. This one is the key to understanding that Edelgard’s better world is only possible in her route, when she has the support and opportunity to trust others enough to learn how to listen to them and consider their perspectives. I advise anyone who thinks Edelgard would be a brutal dictator to watch these supports, because they so blatantly contradict that idea? Linhardt initially frustrates her because she knows he’s talented and smart but he doesn’t want to do anything to help the world with that. Characters like Linhardt are usually given an arc in which they overcome an initial selfishness to help others. This is not that. These supports are about Edelgard learning to understand Linhardt and accommodate him. Edelgard agonizes over finding the perfect way to allow him to do his research in a way that suits him--and when she senses his hesitation at her initial plan, she presses him for the problem and reconfigures the idea because she won’t put him in a situation he’s not fully content in. This is astounding character growth (from both of them, but mostly Edelgard). Also the struggle depicted in this chain is just something that spoke to me when I first saw it--”be useful” versus “learn for knowledge’s sake” is pretty much my exact struggle in life 😂 Seeing two of my favourite characters reach a resolution that satisfied both of them was hopeful, to say the least.
Caspar and Ferdinand - What strikes me about their supports is that it compares and contrasts these characters’ ideas of justice against each other. Honestly, the Black Eagles as a whole have takes on morality that are just slightly skewed, and these characters’ arguments about it exemplify it. Caspar just thinks that people who hurt others should be hit right away, head empty no thoughts but j u s t i c e. Ferdinand initially believes that all sense of justice comes from being nobility, and with that comes an obligation to be morally superior. Having Caspar just go “uh yeah, what does nobility have to do with it? I just had to hit that guy” is one way in which Ferdinand’s ideals are challenged. It’s a cool contrast that I think highlights an interesting aspect of the Black Eagles and what they were taught.
Dorothea and Bernie - I love everything about their interaction. If Dorothea were a lesser character, she’d be the mean popular girl who shames Bernie for her messy hair and her anxiety. Instead, Dorothea is patient and Bernie is like “oh no she’s Too Cool for me”. Dorothea also makes note of what Bernie says as she gets too anxious to continue the interaction and aims to comfort her in their next support. We get a good Bernie character moment in their B-support, where she mentions her father ruining her friendship with a commoner boy--and a cathartic moment where Dorothea tells her that her father’s an asshole and that they’re going to be friends anyway. Bernie cries in Dorothea’s arms and AHHHH why didn’t we get MORE of this???
Bernie and Petra - If I could add any support and ending to the game, it would be Bernie/Petra. They have such a good starting point--because of Bernie’s anxiety and Petra being a second language speaker of Fòdlandish, they are prone to miscommunications (which is the general theme of early Bleagles supports). They had a nice 2-support arc where they understand each other a little better--but then there’s the paralogue, where Petra encourages Bernie to come to her homeland with her and Bernie realizes she wants to travel and see amazing things like carnivorous plants. This is fantastic character development for her and is a satisfying conclusion to her arc. I feel like most of Bernie’s endings involve her just reverting back to her hermit self instead of developing a balance between who she was at the beginning and who she’s grown into. I think Petra would offer to let her come to Brigid again, where she helps her navigate a new language and culture. Bernie’s anxiety is still bad but Petra has been in her position and can offer advise and reassurance. Petra is also patient and would give Bernie a safe little house near the carnivorous plants for her to retreat to when overwhelmed. It becomes both of their refuge, with Petra taking time away from her regal duties to spend time with Bernie and her art and her stories. Whether it’s romantic or platonic is up to preference but I low-key ship them 😏
#black eagles#ferdinand von aegir#petra macneary#hubert von vestra#dorothea arnault#caspar von bergliez#bernadetta von varley#edelgard von hresvelg#linhardt von hevrig#byleth eisner#fe3h
178 notes
·
View notes
Note
Who are you two favourite cats in each clan you're in? And why?
ohhh man i answered an ask similar to this a little while ago but slimming it down to just two per clan is hard...most of my answers have remained the same but there are some alterations from last time!
NETTLECLAN
berryclaw
everyone knows how much i adore berryclaw. she’s been an absolute favorite character of mine for years now, and the more time that passes, the more fond of her i am. she’s so hardworking, striving to build the best life she can have, and i always want her to succeed. she has a level head and good judgement but still obviously struggles when it comes to feeling in control / like she’s making the right choices and that makes her particularly relatable, i feel.
rabbitpaw
rabbitpaw’s a new addition since the last round, and she’s been stealing my heart from her earliest days. she’s just so completely sweet that i can’t help but adore her. the generosity and understanding she extends to everyone she knows is so charming and also a brilliant contrast with her much more self centered sisters, and okay, sue me, i’m biased because of just how precious her dynamic with flintheart is. her love for her uncle and her total faith in a cat who really has a hard time believing in himself is just so heartwarming and really does highlight just how big of a heart rabbitpaw has.
CREEKCLAN
currentstar
i will be a currentstar stan until i die. he’s so well written as a breath of fresh air against a backdrop of cats who tend toward the more chaotic side of things. currentstar’s not devoid of his problems, but i adore how unique he is in his viewpoints and behaviors. it’s easy enough to be a rebel, but currentstar is incredibly special because of how devoted and dedicated he is. snow did an amazing job of picking him up after a streak of dropped adopters and has made him so interesting and so sympathetic. he has to be this upstanding figure for everyone else’s sake and does so much to support his clan that everyone kind of just seems to take him for granted...more people need to appreciate my lovely lovely boy.
applepaw
i was drawn to applepaw almost instantly, and for good reason! she’s such a complex character due to being placed in the role of a “hero” or figurehead for the whole eden cause. the contrast between her and her brothers is incredible because she is, in theory, a much more realized and... secure sort of cat, except just kidding, this girl is full of insecurities. i love the fact that she manages to maintain an air of being more closed off and reserved without showing outright hostility, and i’m always eager to read roleplays that she’s involved in.
JAGGEDCLAN
stonefang
what is there to say about stonefang that i haven’t already? she’s had such a brilliant arc of development, going through trials and all sorts of suffering to become the cat she is, and it’s all been written so stunningly. stonefang is absolutely the hero of the story that you adore, root for, and desperately want to see crawl her way out of the hell she’s been put through. her sharp wit and judgement paired with her selfless acts to protect her loved ones makes her so enjoyable, and i also adore getting to see her slip away from being the more warm and kindhearted sort of cat she usually is when her security / loved ones are threatened. stonefang going crazy on fogclan always brightens my day, you get ‘em, girl.
eveningstorm
miss sunshine herself, despite her name. eveningstorm’s a cat i had to come around to really adoring after just liking her casually for a while, and i am so glad i saw the light. she’s got a tender heart and a level of sensitivity that makes her capable of helping others without ever giving in herself. she’s not weakened by her kindness but is instead fueled by it, and that makes her stand out against more typical shy and soft personalities that you might see elsewhere. her relationships are compelling and interesting, especially when it comes to her tendency to just...break down the barriers of cats who have spent so long building them up. she’s really just a little fluffy treasure and i adore her wholeheartedly.
FOGCLAN
lilystar
lilystar is easily one of the most complex, morally gray characters in the group. so many of her decisions and her choices have been flawed, but that’s what makes her feel real and drives me to love her. i feel like more often than not people are wary of having their characters make mistakes or take a path less traveled by, but lilystar always seems to go where no one else will. she’s driven, fiery, and certainly not the easiest cat to get to know, but her actions all click into place and make logical sense considering what she’s been through. her storyline is undeniably tragic, and the echoes of palestar’s influence that still run through her life give her such an intriguing thought process.
bramblefang
who doesn’t have a soft spot for bramblefang? he’s a special brand of gruff but not outwardly hostile that i feel is difficult to keep a balance of, but it just works so well for him. he has super clear motivations and the way he’s now developing ties in fogclan that allow him to let go of past hurt with his sister and the manipulation palestar put him through is so sweet. he definitely hasn’t flipped completely over to being soft, but i like seeing touches of it in him now. he knows when he needs to have a hard head and when it’s better to step back and be understanding, which is such a good development for him considering the way he used to view the world in a more black and white sense.
TRIBE OF TWISTED TUNNELS
spark feather
sometimes you just have to cheer for a character whose life seems to go wrong at every possible turn. spark feather has never had it easy, and as time goes on, he’s started to play a more active role in screwing himself over, which is a super interesting thing to see develop. he went from basically being a victim of circumstances that built him up to a cat who was capable of making all the foolish, rash mistakes he’s made now. everything about his arc feels natural and he’s still incredibly easy to sympathize with even when he’s doing the opposite of what he should be. he doesn’t get to show it often anymore, but i love his tender side that is displayed to his kits. he’s gone through so much growth already, and i’m eager to see where else he ends up now that his life is sort of starting to get stable again.
butterfly
sort of similar to spark feather, butterfly started a victim of circumstance...and she’s stayed that way all along. her life is absolutely devastating to watch because it never seems to want to treat her right despite her best efforts to be so good, so honest, so true to herself. i’m obsessed with her fixation on truth telling, and it’s such a brilliant trait for her to develop considering that basically no one in her life has ever been entirely honest with her. she’s been forced to navigate so many complex feelings from the moment she was born, and i have so much love in my heart for this poor little darling...it’s insane to think she’s really growing up and getting older now, but seeing her mature and come into herself is comforting after all the struggles she’s been forced through.
#berryclaw#rabbitpaw#currentstar#applepaw#stonefang#eveningstorm#lilystar#bramblefang#spark feather#butterfly#nettleclan#creekclan#jaggedclan#fogclan#tott#anonymous#ask
4 notes
·
View notes
Text
kizuna countdown part 2! yup i just did them all in one go, everyone who’s doing it day by day, have fun! See y’all on Friday!
Favorite Chosen Child-Digimon bond
... uh... so I guess I already answered this in the last question XD I think it's because it's so difficult to think about the Digimon without thinking a lot about the relationship they have with their partners. So I'll just let this one lie, I guess.
Favorite Chosen Children friendship
I pretty much like any relationship dynamic that involves Taichi.
Taichi & Yamato show the most growth, both in themselves and in their appreciation and respect for each other. Taich comes at Yamato expecting to make friends just by being himself as always. Yamato's built up walls to keep himself from getting hurt, plus there's a side to him that wants to be as free Taichi, and he winds up feeling jealous. Then there are ways in which they are legit different which adds even more friction. Their friendship comes out on top because both of them are extremely loyal to their friends at their core. They rock. I loved them in Tri too, when Taichi was acharacteristically waffling around and Yamato was even more concerned about it than the confused viewers hahahaha.
Taichi & Koushirou because they're the opposite of him and Yamato, their friendship is steady and strong throughout. They already respect each other from day one. Taichi puts a lot of faith and trust in Koushirou's abilities and relies on him to get him out of a pickle, even one he's made on his own. Koushirou is a bit shy and not exactly afraid to speak up, but not 100% convinced that his contribution is valued. Taichi helps him see his own worth. And Koushirou believes in Taichi :')
I also love him and Sora and Hikari. For friendships that don't include Taichi, my favs are:
Takeru & Hikari because they're really POWERFUL when they're together (teasing Daisuke for example)
Sora & Koushirou Managing Things, Somehow
Koushirou & Mimi driving each other crazy while really valuing each other
Daisuke & Miyako ^ similar dynamic
Ken & Miyako, I know it becomes a romance, but I loved it when they were kids and it was like Ken and Hikari were off being angsty together and Miyako's like I FEEL LEFT OUT and whines about and then kicks their butts to make the sun shine
Favorite Adventure series villain
Etemon! just kidding. Though the Etemon arc was so great for Taichi that I really enjoy it XD
I'd definitely pick the Dark Masters. Devimon was your typical RPG villain, then Etemon was nonsense run amok. Myotismon was the most fun storyline, what with going back to the human world and the search for the eighth child... I especially loved the chaos when the kids are all separated throughout the city.
But yeah, it'd be the Dark Masters, mostly because I loved how much the kids' resolve got tested when they had to decide for themselves to go to the digital world instead of just being thrown in there. The only one who's had to do that before was Taichi. They fought and they lost a lot of friends, and their team splintered and we saw new sides to everyone. It was harsh. About the villains themselves, MetalSeadramon was whatever, but Puppetmon with his envy and vulnerability and weird relationship with Cherrymon was so interesting to me. Machinedramon was downright terrifying. And then Piedmon playing everyone like marionettes and taking down the trump card as soon as it appeared on the scene... it all led to my favorite moment when the kids are running away one by one and sacrifice themselves to save each other. Sora's moment saving Takeru and Hikari while grabbing Yamato's doll was absolutely epic.
Favorite non-partnered Digimon
Piximon! I loved and wanted more of his training sessions. Wish he'd been like Rafiki and just followed Taichi around smacking him on the head with his stick.
Does Gennai count? He's not a Digimon so I guess not, but I loved Gennai too. He was useful. And also useless. I mostly liked it when he was useless xD
Also Whamon. Traveling in the belly of a whale is awesome. And I was so upset when he got killed.
Also Leomon & Ogremon should count as one of my favorite friendships.
Favorite ship / OTP
So, my number one Digimon OTP is Joumi. Always has been. I like it for a lot of similar reasons that people like Koumi, I guess. But the reason I glued onto Joumi mainly happened in Dark Masters when they were traveling just the two of them for a while. Mimi is positive and outspoken and caring despite being a bit self-absorbed. Jou is reliable, steady, and protective, even though he's also perpetually stressed out. They can both be panicky, but they grow out of it a lot. I think they're pretty realistc in personality and that's one reason I like them together: no one's unusually adept at something or other, they're just kids. They confide in each other about their struggles and they pick each other up. (I loved Ketsui for those moments! Such gifts)
Other ships I really enjoy are Taishiro, Taito, Miyakari, Daiken, Takari, and Daikeru. I also love one-sided Taidai and Mimiyako!
A friendship you'd like to see developed
Honestly? Sora and Miyako. The 02 kids inherited the Adventure team's crests, and each seemed to have a slightly stronger bond with one predecessor than the other. Daisuke had interesting dynamics with both Taichi and Yamato, so that was okay. Iori seemed to have more significant moments with Jou than Koushirou, I think because the sort of knowledge that Iori quests for is a different kind. Miyako is really, really similar to Mimi, her passions are just more hard sciences than artsy-fartsy. But Miyako really never gets any moments with Sora at all? There's that one when she's panicking about being a Chosen in like episode 2, and I can't think of any after that. I would love to see Sora big sister-ing Mimi, helpig her bring out her sensible side, since Mimi's got the eccentric covered.
I'd ALSO like to see Hikari & Sora have a great friendship. One that isn't entirely based on worrying about Taichi x'D
Favorite Kizuna character profile
Takeru's because I just love that he's in a children's lit club!
Favorite Kizuna promotional art
I... haven't been paying attention, so this isn't a real answer, but that one with the boys eating ramen I guess. I even wrote a ficlet for it lol.
Favorite Tri. installment
Kokuhaku!!!! That destroyed any reservations I still had about Tri. It was epic. Somewhat undercut by the fact that we all knew the Digimon would wind up getting their memories back eventually, but I was okay with just enjoying the ride until we got to that point. It was great. I loved the sacrifice the Digimon were willing to make, I loved the secret farewells each partner took, I loved Takeru's protectiveness, Koushirou's breakdown, and Tentomon's strength. Like seriously, he gets all the MVP awards.
Favorite non-Tri. Adventure movie
Our War Game. It's just classic. Plus, Bolero.
Favorite character besides the 12 kids & their partners
Oh, I guess now I could pick Gennai if I want. But I think I'd pick Meiko. I was so not feeling her when Tri came out because I expected her to be the Typical Anime Movie Newbie, who's almost always a girl, bland and uninteresting, eating up valuable screen time from the characters we actually want to see, magically saves everyone and then never appears again.
Meiko did not end up being that girl. Her shyness and awkwardness might have been annoying if they hadn't been tempered by her personal journey through the six movies, and I ended up really liking having a shy girl on the cast. It was refreshing and it was beautifully cast against Mimi. Mimi/Meiko FTW. And she hd real female relationships - with both Sora and Mimi. Her protectiveness of Meicoomon, but also her selfishness, and the terrible decisions she had to make, the way she struggled with self-pity and real honest grief... it ended up really moving me. I think she became very well-rounded and added a lot to Tri.
If Tri had been just one movie, like those anime movies I was expecting, I think she would have been That Girl, but fortunately with six we had plenty of time to get to know her.
(Bonus) Freebie! Talk about something we didn't cover :)
Well, we did lots of favs, so how about a "least fav"?
Of course I don't have a least favorite Chosen, or Digimon. In fact the only thing I'd really pin as a big disappointment happened in Tri. I love Tri but it's certainly got its holes, and for me, Himekawa Maki is a big one. I hate that we just left her wandering in the dark ocean. I hate that were wasn't more expansion on the original Chosen team. I remember when I was a kid and we found out in the last ep or so of Adventure that there had been kids before Taichi and co, I was annoyed, I'd wanted them to be the first.
But I was also curious. With Tri, we finally found out some about that... but only scraps. Who were the others on the team? Where are they now? What's their relationship with Digimon, and if they don't have one anymore, why? What would they say about Daigo's death and Maki's disappearance? Honestly I didn't want to dedicate more time to them at that point (even with six movies they couldn't cram everything in - much as I love Ketsui, I think it should have been a bit different, and moved the plot along faster). But I also hate that we finally learned some stuff about them and in the end were just left with even more questions.
10 notes
·
View notes
Text
MARTHA JONES Is The Perfect DOCTOR WHO Supporting Character

Having recently rewatched Series 3 of Doctor Who, not only is it my favourite of new Who, but so is Martha Jones. I’d also go as far as saying she is the perfect supporting character.
First off, Freema Agyeman was the perfect casting decision. The showrunners were really impressed with her in the minor role she played at the end of Series 2. Instead of ignoring this fact, the writing brings up how it was Martha’s cousin who died at the Battle of Canary Warf. This accomplishes a couple of things; it explains how the same actress played two characters on the show without causing continuity errors. Then you have the Doctor forced to be reminded of said battle.
And Rose.

Which brings up to how the Doctor is still dealing with losing Rose at the end of Series 2. He needs a new companion and when a smart, clever, resourceful doctor presents herself to fill the spot, they both take it. The show gives us two doctors for the titular Doctor to choose from to accompany him. It’s obvious why he’d go for Martha given how scared the other candidate is. Unlike Rose, Martha was whisked into an adventure along with a hundred other people yet she’s the one who joins him in the TARDIS.



Rose’s shadow looms long over the Doctor. The Time Lord takes Martha to the same places he took Rose. People have criticized the showrunner Russell T. Davies of being obsessed with the character of Rose and the drama that came with it, but for me it just comes off as staying true to the character of the Doctor. He isn’t just going to forget about Rose and how in sync they were. That would be very disrespectful to Rose and her fans. Sadly this means Martha does get left behind as a character. She fulfills her purpose perfectly even though it means she cannot compete when it comes to Rose. It makes her character tragic and very sympathetic.

Snog her, you idiot!
Maybe it’s just me finding Freema and Martha attractive but as an audience member you really wish the Doctor could see Martha the way she sees him. Albeit, the Doctor shouldn’t really be dating any of his companions to be honest. Still, Martha isn’t getting enough out of their relationship or lack thereof which is sad.

Speaking of sad, Martha can show her vulnerability as easily as she can be sassy and funny. She can stare at the Doctor with puppy dog eyes in one scene yet demand answers about him and his past the next. All these emotions come off naturally, both in the writing and with Freema’s acting. She’s just a perfect blend of a supporting character. Balanced like all things should be.
Now, having said that, there is a problem with Martha. Despite being a balanced character that also means she doesn’t have the highest of highs or the lowest of low points. For the most part, Martha lacks major strengths and weaknesses that would solidify her as a great character.

Martha’s fun even when she tries too hard to be funny.
For that to happen, Series 3 would have needed a Martha-centric episode. If she had wanted to go back to being a doctor for a while then maybe her personality would have shone through more. This would cause a detour in the story and mess with the pacing though. One could argue that “Blink” does that, but who’d want to get rid of that episode? Plus the Doctor-lite episode was needed so both Tennant and Agyeman could do more shooting for other episodes.

I have loads of ideas for a Martha-centric episode...
Martha is a perfect supporting character, as in she services both the protagonist, story and plot. Supporting characters just tend to not be fleshed out well enough to be great characters. Arguably this changes when Martha decides to leave the Doctor. I haven’t seen her adventures in Torchwood but (I will check them out now!) Martha’s return in Series 4 was glorious. When we last see her in Ten’s last episode she’s an outright badass. So there is growth and character development, I just wonder how much of that is offscreen.
Martha’s main weakness, if you can call humanity that, is her feelings of inadequacy brought on by her unrequited crush/love for the Doctor. It humanizes Martha, adding to the juxtaposition between her and the inhuman Time Lord. Again, serving the protagonist and the story perfectly. The one-sided love story just never goes anywhere. Martha’s decision to just get out is sensible and it makes her extremely likeable and wise. It provides a character arc for her, but it’s not exactly memorable nor does it propel the story into new heights.

Martha literally gives her last breath to the Doctor as they are about to suffocate on the Moon.
That said, Martha went way beyond the call of duty, sacrificing herself to help the Doctor. Especially during the two-parter "Human Nature/Family of Blood” where Martha had to witness the Doctor falling in love with another woman while trying to keep the Time Lord safe from evil aliens. All the while having to put up with the prejudiced attitudes of the early 20th century England.

Right before Martha schools her on all the bones in her hand that’s about to pimp slap her.
In the same two-parter, when the amnesiac Doctor-turned-human falls down the stairs, Martha comes over as soon as she hears of it. Concern for the Doctor’s wellbeing is the first thing on her mind. Sure, Martha’s trapped there with the Doctor being her only way out, but it never comes across like that. The things Martha endures are sacrifices she’s deemed necessary. It really speaks volumes about the true grit of her character.

Waifu material.
She never becomes bitter or hardened by any of it either. Yet she isn’t without some sass either. When Martha’s told she should knock before entering, she steps back towards the door, knocks it and comes back. Martha Jones is such a well rounded character it’s a shame we only had her for a single season.
I’ll reiterate; all this this makes Martha my favourite New Who companion. It makes her the perfect supporting character.

I was going to make a joke about this, but I think the logo speaks for itself...
Martha’s own supporting cast reflects this as well. They all serve to paint a picture of Martha and pushing the story forward. Martha’s mother Francine is excelently utilized with very little screen time. Her skepticism towards the strange Doctor is only natural. It makes perfect sense for Francine to work with Saxon’s people who seemingly want to protect Martha like she does. This side plot in “42″ is actually the best part about the otherwise mundane enviromentalist episode.

Martha isn’t a jokester, but she has her moments. Kudos to Freema’s versatility as an actress.
As a character though, Jackie Tyler, annoying as she could be at times, is far better though. Jackie’s flirty personality, her accent and overall attitude towards life just shines through her every delivery of a line of dialogue. There are plot involving Jackie’s dead husband coming back to life and creating a deadly time paradox, too. Whereas Martha’s dad dating another woman doesn’t have effect on the plot. It doesn’t even phase Martha herself, she just tries to steer clear and juggle between her mom and dad which is easy because by now she lives on her own. Drama free.

That is when she isn’t being jettisoned into the sun!
Side note, I’m glad the character got a happy ending, albeit not with the Doctor like she wished. After all the hardships she endured and sacrifices she made for the Doctor for very little reward, she’s earned a little peace and quiet. She wasn’t lost on a parallel Earth nor forgot her adventures. She didn’t “die” like Amy, Rory and Clara.
It would have been absolutely terrible had Martha died. She’s my favourite of the bunch so it’s good to know she’s still out there somewhere in the Whoverse. The fact she could be easily written back into the show some day warms my heart.
For future reference, should Martha come back to the show and should the writers decide to kill off her character... like they are doing with the show proper at the moment... then allow me to give the showrunners and writers some advice. If Martha has to die, make her sacrifice herself for the Doctor one last time. As a one final act of love towards the man (assuming he’s back to being a man).

She’s talking about Shakespeare, but Martha’s line is very indicative of her relationship with the Doctor.
Don’t give us Mad Martha who decides to burn down whole cities full of people, okay. Don’t give us that “Martha kinda forgot her Hippocratic Oath” crap. You got that? Just making sure...
Anyway, Series 3 wasn’t the end for Martha and I’m so glad the character came back in Series 4 and like I said, I’ll be checking out Torchwood for more Martha appearances. But we’re here to talk about her as a companion so let’s get back on track.

That’s what she said about my tangent.
Now, you could get a good episode about Martha’s family drama, much like how Rose changed time to save his dad. But it’s not really necessary. The family drama in Series 11 has certainly shown how dull and dreary stories like that can be. That is why, even though Martha and her family aren’t exactly great characters that provide great stories, they are perfect at providing a clear context to the imaginary world that the Doctor, the TARDIS and time travel represents.

Freema sells that magical moment of a companion stepping into the TARDIS for the first time perfectly.
Again, perfect supporting characters that don’t waste time away from the things people actually watch the show for. That said, I wouldn’t have minded seeing a cat fight between Francine and her ex husband’s new bimbo girlfriend!
Just a single scene like that would have been endlessly entertaining and damn memorable!

Imagine that but between her and the bimbo: “Keep away from my husband.”
Martha’s sister Tish fares a lot better as a character as far as personality goes. There isn’t really a sibling rivalry going on, but Tish’s remarks about Martha dating a science geek speaks a lot about both her and Martha’s characters. What they look for in a man. When the Doctor asks what a science geek means, Martha explains it’s just someone who’s passionate about science which makes the Doctor happy. Which is what Martha wants, whether she was telling him the truth or sparing his feelings with such an interpretation. Brilliant writing for the characters all around.

Tish working with both Lazarus and Saxon, even if both instances were brought about by Saxon himself, tells about Tish being drawn towards wealth and power.
She was even ready to “snog” a de-aged Lazarus!


Damn right, she is! Not just a pretty face but smart too!
I wish we’d have seen more of Tish. Her interaction with Martha really created a contrast that benefitted both characters. In “The Lazarus Experiment” especially, Martha gets to shine. After helping her family escape, she goes back for the Doctor against her mother’s wishes. Later, Tish comes along. Martha takes control and takes Tish with her so that the Doctor has time to defeat Lazarus himself. Martha let’s the Doctor shine and in doing so shines herself. Tish acts as a great supporting character herself by asking who the Time Lord is. At this point Martha already knows because she’s asked him herself, demanding answers.

“We need to talk.” Never a good sign except in fiction.
Martha or the handling of her character is often criticized for how she had a thing for the Doctor. Her character was much more. In an early episode “Gridlock” we get one of Martha’s best moments; when she demands answers about the Doctor. She forces the Time Lord to come out of his shell, to stop pretending everything was all right. The Doctor tells Martha about being the last of the Time Lords which fits perfectly to the story of the Series.
Namely that the Doctor is not the last of his kind.
The Doctor also mentions how the Time Lords were all lost in a Time War, battling against the Daleks. It’s a great segway into the next two-parter story about Daleks themselves. The story flows really well with one thing leading to the next. The pacing is really good while the characters remain true to themselves. That said, it’s good to have Martha around to challenge the Doctor.

Asking seemingly harmless questions like this is vital for good supporting characters. We get to see the Doctor’s reaction to his home planet being brought up.
That said, I should mention a couple of things. In the episode “Smith & Jones” the Doctor kisses Martha to mark her with some of his DNA. This is done on the fly and while the Doctor had a plan, I dislike how this puts Martha in danger. Now, she doesn’t get into any serious trouble but considering how trigger happy the Judoon platoon upon the moon are, things could have gone real bad. This kiss does start Martha’s infatuation with the Doctor so there’s that.

Wait, don’t snog her, you idiot! Now she’s in danger!
The Doctor’s indifference to cool and hot Martha does make him in return look cooler. Martha is essentially the Doctor’s cheerleader which, despite sounding as not complimentary, really is that. You need the audience to root for the main character and this is partly achieved through supporting characters singing their praises. Of course, the characters still have to earn that praise. You can’t just have characters emotionally validate themselves or others to the audience.

Though it doesn’t hurt when Shakespeare himself is singing your praises.
The downside to the Doctor’s indifference is that he does come across as a jerk at times. Now this can be either a good or a bad thing based on the audience. While Martha is perfect as a supporting character, you don’t want neither her or the protagonist to be perfect. The Doctor missing Rose, as annoying as that can be to some, is keeping true to the character. The Doctor is in mourning. It’s his grief period and Martha is there to help him through it. In doing so, Martha learns that she doesn’t want to wait forever for another person to notice her.

In one of the best episodes in New Who’s history, “Utopia” draws a parallel between Doctor and Martha and the Professor and his assistant Chantho. Much like Martha, Chantho is smart, kind and caring. Based on her interactions and demeanor, Chantho adores the Professor and like Martha with the Doctor, she has a crush on him. Both the Professor and the Doctor don’t notice these signs. For an individual episode this is all well and good, but given the secret about Professor Yana, this parallel is much more impactful than it seems at first.
Spoilers to a Series over ten years old; Yana is actually the Master. This twist alone, the callback to the concept of a fob watch allowing a Time Lord to masquerade as a human was a brilliant touch. Martha of course recognizes Yana’s fob watch instantly and again, Freema sells the feeling of terror and dread so damn well.
Later in the episode Martha recognizes the Master’s voice as Harold Saxon. The name we’ve heard all throughout the Series. A lesser show would not have given Martha’s character such insight. It’s one of the numerous details that make her character clever and likeable.
Unfortunately, likeable characters aren’t always the most compelling ones. This makes Martha an underappreciated companion in the series history. While Martha is my favourite, I can’t really blame the detractors. Martha Jones served her purpose on the show which meant couldn’t shine as brightly of a star of her caliber. I’d still take her any day over Clara Oswald who was such a bad supporting character that it encroached on becoming the Clara Who show. And I say this as someone who loved the past and future Claras and Jenna Coleman playing the character(s).
Anyway, back to the actual episodes. While context is key, I find it interesting how the Master kills Chantho, showing no regard for her life. Now, the Doctor does care about life and he’s risked his own life for Martha many times. Still, being around the Doctor, much like with the Master, is dangerous. Neither can truly love their companions the way they want. That parallel is fascinating and I’m glad Martha was allowed to walk away from it of her own free will. Definitely one of the reasons this Series has the best writing out of New Who.

One of the few times the Doctor rewards Martha’s loyalty and bravery. Her reaction to receiving a key to the TARDIS is everything!
Speaking of writing. Before Martha says her goodbye, she has to walk the Earth and spread the gospel of the Doctor to the people of the world. Many have criticized how the show made the Doctor out to be a god who regains his power through prayer essentially. Rightfully so because even in context the twist does feel outlandish albeit totally awesome. Subjectively I’d say it’s one of the best moments in New Who.
Basically, the people have been subliminaly made to vote Master/Saxon into office. Now the Doctor has tapped himself into the same telepathic field and receives prayers, the word “Doctor” across the world. This turns him basically invincible for a time. Time enough to defeat the Master.
Because the telepathic field had been established in a prior episode and its effects had been reincorporated over and over again in the form of a drumming that the Master himself heard inside his head, I find that the twist is properly set up. That and because Martha has spent a whole year travelling around the world acting as a cheerleader for the Doctor.

The best cheerleader you could ever hope for!
Though how the Doctor’s orders relayed by Martha never reached the Master’s ears is a mystery. Martha was aware of a traitor though and she spoke to her accordingly, feeding false information. I doubt she told the people about the telepathic field. The Master could not put two and two together when the Doctor himself told of the plan. To the Master it was just hope and prayer.
Suffice to say I have mixed feelings about the final twist. None of this detracts from Martha Jones as a companion though and that’s why I wrote this blog post about her. If you’ve managed to get this far I thank you.
Boy, that was a lot of out of order, wibbly wobbly rambling about a show that I love and a companion I adore. Started well, that blog post.


<3
19 notes
·
View notes
Text
WIP Prep (tag)
I was tagged by @paladin-andric -- thank you!!! I loved filling this out, and sorry for the delay!
Rules: Answer the questions, then tag as many people as there are questions (or as many as you can).
The Colors of War
FIRST LOOK
1. Describe your novel in 1-2 sentences (elevator pitch)
Sent from London, England to Maine, USA by her guardian to escape The Blitz of World War II, Marjorie Borchert is left to navigate her young adult years in a tight-knit and foreign town. As the years progress, she learns war stretches far beyond the front lines.
2. How long do you plan for your novel to be? (Is it a novella, single book, book series, etc.)
A single book with possibly a collection of shorts from the other character’s lives.
3. What is your novel’s aesthetic?
Chilly mountains and moose.
4. What other stories inspire your novel?
Little bits from Number The Stars by Lois Lowry and the character of Emily Bennet from the Molly American Girl series.
5. Share 3+ images that give a feel for your novel



MAIN CHARACTER
6. Who is your protagonist?
Marjorie Borchert. She is in her mid-teens at the beginning of the story. Moody to say the least, but she has a big heart.
7. Who is their closest ally?
Daniel Reynard. Nikita Savas is a close second but Marjorie’s had a special bond with Daniel from the beginning.
8. Who is their enemy?
Kate, Beatrice, and Gina. Kate is the worst despite the fact Marjorie shares a room with Beatrice.
9. What do they want more than anything?
For things to be as they were before the war.
10. Why can’t they have it?
Her parents were both killed.
11. What do they wrongly believe about themselves?
She believes nobody wants her -- which is understandable after being passed off to strangers by her guardian and, in a way, her brother.
12. Draw your protagonist! (Or share a description)
I’m not much of an artist and she’d look like a cartoon, do description it is.
Tall, though not towering over everyone. She keeps her brown hair short or shoulder length until she’s older. She’s thin, possibly malnourished, when she first comes to America. She fills out a bit the longer she’s at the farm and eating three full meals a day. She’s pale, partly due to locations she’s lived. She had prominent German features, most notable, her accent which is mixed with a British tongue.
PLOT POINTS
13. What is the internal conflict?
There’s different stages I’ll say. In the beginning, it’s about Marjorie trying to find her place in this small and established community. Her biggest conflict being a target for the prejudiced Kate. Then it moves on to the progression of the war and her fears around America’s involvement. But she comes to see that war doesn’t just affect those fighting or being captured and bombed. She also sees how different people handle things differently. Priorities fall into place through this.
14. What is the external conflict?
Trying to get by and adapting to the changes the war is bringing to the community. Acceptance, too. Internal and external kind of work together.
15. What is the worst thing that could happen to your protagonist?
Losing her brother for good and/or not being able to return to England.
16. What secret will be revealed that changes the course of the story?
My only secret might not end up working. There would have to be a second book. Either way, I’m not going to reveal it. It might end up being one of things only me and a couple of my writing friends will ever know....
17. Do you know how it ends?
Yes, unless Marjorie decides to change her course of action.
BITS AND BOBS
18. What is the theme?
Acceptance and making the best of a bad situation.
19. What is a recurring symbol?
Change.
20. Where is the story set? (Share a description!)
Jackman, Maine, USA. A small town with a population under 1,000 a few miles from the border of Canada. It’s a heavily wooded area with beautiful mountain and lake views. Lots of wildlife, too. The town is small, running along a single street branching out into houses.
21. Do you have any images or scenes in your mind already?
So. Many.
22. What excited you about this story?
The time period. I’m a history buff and the 1940s has always been my favorite era.
23. Tell us about your usual writing method!
Procrastination. That’s really it. I do my best writing at five in the morning and knowing I have to pick my little cousin up from the bus in a few hours.
I tag (if you’d like): @throughwordsiescape @silverscreenwriter and @rachelradner
7 notes
·
View notes
Text
I started the month in a really bad reading slump, so my main goal for the month was to get over that. Thankfully I successfully revived my love and enthusiasm for reading, and managed to have a really successful reading month. I’ve never read so many books in a month before in my entire life, and I’m feeling really good about it. I picked up what I felt like, and that meant I read a lot of graphic novels.
The House with Chicken Legs – by Sophie Anderson
All 12-year-old Marinka wants is a friend. A real friend. Not like her house with chicken legs. Sure, the house can play games like tag and hide-and-seek, but Marinka longs for a human companion. Someone she can talk to and share secrets with.
But that’s tough when your grandmother is a Yaga, a guardian who guides the dead into the afterlife. It’s even harder when you live in a house that wanders all over the world . . . carrying you with it. Even worse, Marinka is being trained to be a Yaga. That means no school, no parties–and no playmates that stick around for more than a day.
So when Marinka stumbles across the chance to make a real friend, she breaks all the rules . . . with devastating consequences. Her beloved grandmother mysteriously disappears, and it’s up to Marinka to find her–even if it means making a dangerous journey to the afterlife.
With a mix of whimsy, humor, and adventure, this debut novel will wrap itself around your heart and never let go.
This was such a quick, enjoyable read, and an interesting twist on the Baba Yaga story. It’s such a whimsical story, I loved all the interesting details that were woven throughout the book. I was quickly absorbed by Marinka’s life, and invested in her story. There are some really interesting themes explored throughout, and Marinka’s reactions always felt really genuine. I loved watching her character develop and grow throughout the story as she came to terms with her situation, and explored her identity. I can see why this book was released to so much praise, I’m just so glad I picked it up.
Rating: 4.5 Stars
Their Fractured Light – by Amie Kaufman & Megan Spooner
A year ago, Flynn Cormac and Jubilee Chase made the now-infamous Avon Broadcast, calling on the galaxy to witness LaRoux Industries’ corruption. A year before that, Tarver Merendsen and Lilac LaRoux were the only survivors of the Icarus shipwreck, forced to live a double life after their rescue.
Now, at the center of the galaxy on Corinth, all four are about to collide with two new players in the fight against LRI. Gideon Marchant is an underworld hacker known as the Knave of Hearts, ready to climb and abseil his way past the best security measures on the planet to expose LRI’s atrocities. Sofia Quinn, charming con artist, can work her way into any stronghold without missing a beat. When a foiled attempt to infiltrate LRI Headquarters forces them into a fragile alliance, it’s impossible to know who’s playing whom–and whether they can ever learn to trust each other. With their lives, loves, and loyalties at stake, only by joining forces with the Icarus survivors and Avon’s protectors do they stand a chance of taking down the most powerful corporation in the galaxy—before LRI’s secrets destroy them all. The New York Times best-selling Starbound trilogy comes to a close with this dazzling final installment about the power of courage and hope in humanity’s darkest hour.
This book took me so long to read, it just seemed to go on forever. I know that this is mostly because of my reading slump which hit right as I was reading this book, but I also feel like a lot of this book was about moving the characters towards a meeting point where they could then go on and finish the story. It almost feels like it could have been two books in that sense. One following Sophia and Gideon, and then a final book following all the characters once they meet.
Rating: 3.5 Stars
Before She Ignites – by Jodi Meadows
Before
Mira Minkoba is the Hopebearer. Since the day she was born, she’s been told she’s special. Important. Perfect. She’s known across the Fallen Isles not just for her beauty, but for the Mira Treaty named after her, a peace agreement which united the seven islands against their enemies on the mainland.
But Mira has never felt as perfect as everyone says. She counts compulsively. She struggles with crippling anxiety. And she’s far too interested in dragons for a girl of her station.
After
Then Mira discovers an explosive secret that challenges everything she and the Treaty stand for. Betrayed by the very people she spent her life serving, Mira is sentenced to the Pit–the deadliest prison in the Fallen Isles. There, a cruel guard would do anything to discover the secret she would die to protect.
No longer beholden to those who betrayed her, Mira must learn to survive on her own and unearth the dark truths about the Fallen Isles–and herself–before her very world begins to collapse.
Why aren’t more people talking about this book? It’s just so good, I loved every minute of it. I’m actually kind of mad that I don’t have the second book ready to start right away, but I will be pre-ordering that very soon. There is so much that I like about this book, firstly, this book has actual dragons in it!
Rating: 5 Stars
Bruja Born – by Zoraida Cordova
Three sisters. One spell. Countless dead.
Lula Mortiz feels like an outsider. Her sister’s newfound Encantrix powers have wounded her in ways that Lula’s bruja healing powers can’t fix, and she longs for the comfort her family once brought her. Thank the Deos for Maks, her sweet, steady boyfriend who sees the beauty within her and brings light to her life.
Then a bus crash turns Lula’s world upside down. Her classmates are all dead, including Maks. But Lula was born to heal, to fix. She can bring Maks back, even if it means seeking help from her sisters and defying Death herself. But magic that defies the laws of the deos is dangerous. Unpredictable. And when the dust settles, Maks isn’t the only one who’s been brought back…
This was everything I hoped it would be. I really enjoyed seeing more of the world in this book. I really love the magic system and the world building. I was worried about whether I would enjoy Lula’s perspective as much as I did Alex’s, but I needn’t have worried. This book was fantastic, and I already can’t wait for the next one.
Rating: 4.5 Stars
Fantastic Beasts and Where to Find Them – by
A brand new edition of this essential companion to the Harry Potter stories, with a new foreword from J.K. Rowling (writing as Newt Scamander), and 6 new beasts!
A set textbook at Hogwarts School of Witchcraft and Wizardry since publication, Newt Scamander’s masterpiece has entertained wizarding families through the generations. Fantastic Beasts and Where to Find Them is an indispensable introduction to the magical beasts of the wizarding world. Scamander’s years of travel and research have created a tome of unparalleled importance. Some of the beasts will be familiar to readers of the Harry Potter books – the Hippogriff, the Basilisk, the Hungarian Horntail…Others will surprise even the most ardent amateur Magizoologist. Dip in to discover the curious habits of magical beasts across five continents…
I borrowed the audiobook from my local library, and I really enjoyed it. I wasn’t sure if this book could work well as an audiobook, but it really does. It’s narrated excellently by Eddie Redmayne, who is in character as Newt Scamander for the entire book. The whole thing is just really well done.
Rating: 4 Stars
Giant Days: volume 4
It’s springtime at Sheffield University — the flowers are blooming, the birds are singing, and fast-pals Susan, Esther and Daisy continue to survive their freshman year of college. Susan is barely dealing with her recent breakup with McGraw, Esther is considering dropping out of school, and Daisy is trying to keep everyone and everything from falling apart! Combined with house-hunting, indie film festivals, and online dating, can the girls make it to second year?
The Eisner Award-nominated series from John Allison (Bad Machinery, Scary Go Round) with artist Max Sarin delivers another delightful slice-of-life adventure in Giant Days Volume 4. Collects issues 13-16.
This was a birthday gift from my auntie, and I was so excited that I read it that same day. I loved it just as much as the previous volumes. It’s highly entertaining, and I definitely consider this to be one of my favourite graphic novel series.
Rating: 4.5 Stars
Giant Days – by Non Pratt
Based on the hit graphic-novel series from BOOM! Studios, the publisher behind Lumberjanes, Giant Days follows the hilarious and heartfelt misadventures of three university first-years: Daisy, the innocent home-schooled girl; Susan, the sardonic wit; and Esther, the vivacious drama queen. While the girls seem very different, they become fast friends during their first week of university. And it’s a good thing they do, because in the giant adventure that is college, a friend who has your back is key–something Daisy discovers when she gets a little too involved in her extracurricular club, the Yogic Brethren of Zoise. When she starts acting strange and life around campus gets even stranger (missing students, secret handshakes, monogrammed robes everywhere . . .), Esther and Susan decide it’s up to them to investigate the weirdness and save their friend.
I really enjoyed this book, and was so happy when it lived up to the awesomeness of the comics. Non Pratt has done a fantastic job of writing something that can stand alone from the comics, while matching the tone of the comics, and making subtle nods to the source material.
My Review
Rating: 4.5 Stars
Giant Days: volume 5
Going off to university is always a time of change and growth, but for Esther, Susan, and Daisy, things are about to get a little weird.
Their freshman year is finally coming to a close and Daisy, Susan, and Esther say goodbye to Catterick Hall forever. Literally forever. It’s being bulldozed and re-purposed as a luxury dorm next semester. But as one door closes, another opens and between end of semester hookups, music festivals, and moving into their first home together, the life experiences are just getting started.
Written by Eisner Award nominee John Allison (Bad Machinery, Scary Go Round) and illustrated by Max Sarin, Giant Days Volume 5 finishes off freshman year in style, collecting issues #17-20 of the Eisner and Harvey Award-nominated series.
I’ve already said how much I love this series, and this volume changes nothing. It’s great. I love that they are showing the passage of time, and allowing the characters to move forward and progress through life. I’m really looking forward to finding out what the girls will get up to in their second year of university.
Rating: 4.5 Stars
Ms Marvel: volume 9 – by G. Willow Wilson, Nico Leon
Kamala Khan has vanished! But where has she gone, and why? Jersey City still has a need for heroes, and in the wake of Ms. Marvel’s disappearance, dozens have begun stepping up to the plate. The city’s newest super hero Red Dagger and even ordinary citizens attempt to carry on the brave fight in Kamala’s honor. Somehow, Ms. Marvel is nowhere…but also everywhere at once! Absent but not forgotten, Ms. Marvel has forged a heroic legacy to be proud of. But when an old enemy re-emerges, will anyone be powerful enough to truly carry the Ms. Marvel legacy – except Kamala herself?
COLLECTING: MS. MARVEL 25-30
This is another of my favourite ongoing graphic novel series’, and one of the only Marvel titles that I’m interested in keeping up with. I really enjoyed this volume. I liked that they focused on Kamala’s friends, and how they cope without her while also covering for the missing Ms Marvel. It was a lot of fun, and I can’t wait to see what happens next.
Rating: 4 Stars
Ancient Magus Bride volumes 2,3,4,5
Great power comes at a price…
Chise Hatori’s life has recently undergone shocking change. As a sleigh beggy–a person capable of generating and wielding tremendous magical power–she has transformed from an unwanted child to a magician’s apprentice who has been introduced to fae royalty. But Chise’s newly discovered abilities also mean a cruel fate awaits her.
I’m really enjoying this manga series, the anime is a pretty faithful adaptation so far, so no surprises, but I love the art, and I’m really enjoying reading the source material. I especially loved all the tiny details and explanations that weren’t in the anime, that really add to the story. I loved the anime, but I feel like I’m getting to know the characters and the world a bit better in this format, and I really like that. I love the magic, and the large, interesting world that’s being set out in these books. Also, I really like the bonus content in the collected volumes, it makes me so happy.
Ratings: 4 – 4.5 Stars
Sorry this post is a month late, I don’t know why I didn’t post it sooner, it’s been ready for a while. I’ve been such a mess this past month, I need to be more organised.
Want to chat, about books or anything else, here are some other places you can find me:
Twitter @reading_escape
Instagram: @readingsanctuary
Goodreads
Tumblr
August Reading Wrap Up I started the month in a really bad reading slump, so my main goal for the month was to get over that.
#book blog#book blogger#book recommendations#Book Review#bookish#books#bookworm#reading wrap up#Review#YA#ya books#young adult#young adult books
1 note
·
View note
Text
Top 20 Blogging Rules (I bet you are overlooking at least one rule!)

Hi Everyone,
Welcome to the round-up of the Top Twenty Blogging Rules you need to follow if you are to make a success of your blog.
Blog rule 20 is finally revealed below.
So let us begin.
Rule 1 Theme
If you cannot navigate your website then neither can your readers - Choose themes carefully.
Running a successful blog and website involves a lot of work. Here at The Go To Girls Blog we take every minute we can and make the most of it, whether it is having some downtime with our families or using the time to update our website or writing blog post ready for future posts.
If you make any changes to a theme, that lead you to believe it makes it harder to read or navigate for that matter then you must correct them. Remember If you cannot read it easily then neither can your readers!
We read a lot of books and blogs and watch videos on blogging during our research and one of the top things that lose you readers and potential customers is a website that is poorly presented.
We have got pretty good at developing our website as you can see by the results on our site.
Rule 2 Logo

The Go To Girls Blog Brand Logo Image
One thing you will find your self needing for your blog is a logo. This logo will help people recognise you and your brand across every social media app you use.
If you think about your brand when you are opening social media accounts, if you use random photos or characters then how will people know when they have found the correct account?
After all, there are plenty of copy cats out there who will use your brand to get recognition for their own. You can never stop this but you can brand cleverly by having your own logo.

The Go To Girls Blog Logo
Some established brands even copyright the logo they create for their brand. Here at The Go To Girls Blog we actually have two logos. Either of them can help readers recognise our brand and we even have them on our business cards.
Rule 3 Great photos
Bloggers who write great posts will already know what to include and what not to in their work. Following our blogging rules could help you be one of those bloggers.

#Picoftheday
One of those things we found here at The Go To Girls Blog is to ramp up the interest in your post you must include lots of good quality photos and videos. When you take photos chose the best ones, don't use blurry or badly lit photos.
Take more photos than you need as you never know when you will capture the extra special one. There are lots of places out there you can get stock photos for free but the best photos are taken by YOU!
While some bloggers do not use photos at all and some use the middle of the road photography you can make your blog stand out and keep ahead of all of your competition by just following this one blogging rule.
Rule 4 Hosting
Choosing the best host for your website and/or blog is probably the most important thing as this can determine how good your website runs and looks.
While there are lots of website hosts out there you should consider what you want from your website and host, when making this decision.
At The Go To Girls Blog we chose Bluehost to be our host as, when we read up on what we wanted from our website, Bluehost came out as the one for us.
For The Go To Girls Blog a couple of things we wanted our blog posts to look good across all platforms, so no matter if you are looking at us on your phone or your laptop the website would look amazing.
It needed to be quick and have enough tools to make sure our website was secure and protected from cyber-attacks. One of the good things about Bluehost is WordPress can be installed directly.
There are lots of different themes within WordPress so you can build the most beautiful websites through Bluehost
Have a look around our website to see all of the amazing features of Bluehost. The most important thing of all depends on you doing your homework. Read up on all hosting services and make a list of what you want from your website then you are fully prepared to make your decision.
(This post may contain affiliate links for which (at no additional cost to you) we may receive a small re-numeration from any purchases you make.)
Rule 5 Post Regularly.
The Go To Girls Blog posts every day and there is a good reason for this frequency. If you want to get a regular following posting regularly is a must.
Whether you post every day or 3-4 times a week, POST REGULARLY. It lets people know they can expect to hear from you on certain days.
One thing readers do not like is bloggers who are unreliable. Having readers who never know when or if you will post again won't come back.
If you do blog every day you must make sure you still keep up the quality of your writing though. Do not exchange quality for quantity and this will lose you readers just as quickly.
Don't forget to make sure you do the same on all of your social media too.
Keeping your brand out in the public domain means making sure it is posted regularly across all of the social media platforms you use for promoting your brand.
What is the point of writing a great post and then it stays on your laptop?
The whole point of blogging is to let as many people know about it as possible. Using social media is a proven way to advertise your post so make sure you share it around as much as possible.
Rule 6 Time Management.
Time must be the no one thing all bloggers struggle with especially If you have a full-time job as well as a full-time blog. What can you do about this? I hear you ask.
Do you have great time management skills or do you get a plugin to do it for you?
There are so many different jobs you must do to run your blog successfully. You have to find time to come up with great ideas for your blog posts, take photos, keep your website up to date as well as maintenance and updated regularly.
So time management can be time-consuming in itself. If you really want to keep on top of your time then you can always use a great plugin.
Here at The Go To Girls Blog, we use Timetable and Event Schedule by MotoPress.
This plugin is great for arranging your time into slots of various tasks plus those all-important meetings.
You can arrange the whole lot in one plugin which is good as who wants to be splitting themselves between multiple time management apps as well. If you have a Wordpress blog then give it a try.
Rule 7 Be Unique
With so many bloggers out there you have to consider what is going to make you stand out among all of the others. One thing we learned here at The Go To Girls Blog is to be ourselves when we write.
Be the unique person you were born to be. Don't join the blogger bandwagon and write the same old stuff you see day in, day out. Everyone has a different view on life all with our own back story and each with our own strengths and weaknesses.
Always play to your strengths. Write about what you know. What are you good at? What do your family and friends come to you for assistance with? I am yet to meet a person who does not have at least one skill.
We might not all value each other's skills but we have them nonetheless. We all have experiences in daily life.
We all travel, work, cook, clean, care for ourselves or others. Every one of these things can give you a very successful blog. Why? Because they are all unique to YOU!, and someone always needs help or advice on one of the millions of topics around the world.
You just need to choose which one you can help others with. BUT write about it with your own unique insight. This should help at least get you recognised for being unique and therefore more people will come to your blog.
Which means, TRAFFIC. The holy grail for bloggers. Ask any blogger what their top want/need is!
They will all say the same - TRAFFIC.
Rule 8 Use Analytics.
Any blogger loves to see how their website is doing across all of the social media platforms and especially their blog. To do this you need to have some form of analytics to record things like how many followers you have across all of your social media platforms.

Pinterest Analytics
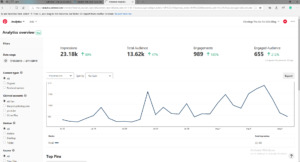
Pinterest Analytics
What method people used to find your site, did they search Google or did they click a link in Pinterest? How many pageviews a day do you have and even how much time on any given page within your posts or website. I know it sounds amazing doesn't it that you can actually see all of this information.
Well, you can and I can tell you it becomes quite addictive. Watching how many visitors you have on the blog you just posted, tracking daily figures to determine the growth of your blog.
It feels great when you see one, ten, a hundred, a thousand people visited your site today and you never know when it is going to stop. Maybe it won't, maybe in a few months you will have a million views but the analytics will still remain one of the most important tools you will ever have as a blogger.
It will also help you find your audience, how old they are, what devices they are looking at your website on and even what interests they have. This may not sound like the information you want but believe me, it is!
This is the breakdown of everything you will ever know to make a success of your blog. Use it wisely and it will help you build your brand.
Rule 9 Budget.
Another rule for any blogger but especially a new blogger is don't spend money you don't have! You will see everywhere companies who want to help you with apps and plugins, themes and advertising.
While these may be ok if you have a budget they are not so great if you are on a tight or no budget at all. The truth is if you pick the right host you can rely on them to help you with some of the technical features of building your website.
Although some do not include some of the design features of your website like colors and themes. The internet and in particular YouTube is also an amazing tool in helping create a great website.
All you need is a little technical knowledge and YouTube and you can get away with little or no budget and have a beautiful website. One of the things we do here at The Go To Girls Blog is to offer assistance to new and existing bloggers' and technical help.
We know how hard it is to get your website up and running especially when you are right at the beginning of the process.
If you find yourself in need of a bit of technical help then drop us an email and depending on the nature of your query we may be able to help for free (in more complicated cases there may be a small charge)
But we will help you on your way to getting your website looking beautiful and your blog running smoothly.
Rule 10 SEO or Search Engine Optimisation.
Something to consider when writing a blog or creating a webpage is how it is going to appear on the internet, in particular within search engine results.
Nobody wants to spend all the time they have creating content and then not appear in any searches. Everyone wants their posts and website to appear on the first page of Google search and this is attainable.
You just have to optimise your post for this. SEO or Search Engine Optimisation is maximising blog posts or website pages chances of appearing high on search engine searches and therefore getting more traffic for your brand. As I said in a previous post traffic is key to a successful blog/website/brand.
Here at The Go To Girls Blog we use a couple of SEO Plugins. Why use more than one I hear you ask? Well, I thought long and hard about this and I came up with this, one SEO plugin told me to do certain things to my blog like use internal links and image tags.
Then just out of curiosity I installed another one and that told me a totally different list of things that would 'optimise' my post, like use a focus key phrase and set the width of my title to so many characters. Confusing, Yes! Or is it? Could it be more useful information on search engine optimisation?
We thought what if we try to follow the suggestions on 2 of these SEO plugins and see what happens. So we did and guess what happened?
WE GOT TRAFFIC TO OUR SITE!
It actually works.
We use On-Page and Post SEO and Yoast SEO.
Why not give them a go, it can't hurt your brand but it can make the world of difference to your website.
Rule 11. Appreciate Interaction.
When you are a blogger one thing that makes your day is when your readers and followers interact with you. This can be by following you, leaving a comment, linking to your blog or simply liking your latest work.
Whatever the interaction, make the most of it. If someone comments on your work then reply and whether it is positive or negative. If it is negative just take it on the chin.
You chose to put your work out there on the internet for all to see and you will find that whatever you write it will not be everyone's 'cup of tea'.
If someone writes a negative comment thank them for their opinion and leave it at that. Other bloggers may ask you for help if you can then help them, DO SO! Interaction is key!
You will be surprised how far answering a question (which may be easy for you to answer) will take you with regard to your reputation as a good blogger.
Other bloggers will always appreciate interaction whether it is a bit of help or advice when they need it. Don't forget not all bloggers are 'techie' or good at all aspects of bogging so you never know what help a fellow blogger will ask for.
Here at The Go To Girls Blog we get asked all sorts of questions from what hosting do we use? to how do we center ourselves when we write? We always reply with as much information as we can.
Rule 12. Teamwork.
There are so many different jobs you need to have covered when you are running a successful blog which could make it impossible to do alone. With this in mind, you are going to need an amazing team of very skilled people. Just to name a few roles you need to fill are a web designer, a social media manager, a photographer, and a writer.
When we started we did not have any of these roles here at The Go To Girls Blog there were just two of us. Now we have a few more people helping out with all of the various jobs we have to do daily. I can tell you it feels great not having to fit in all of these roles ourselves.
Directing all of these amazing people is so much simpler than doing it all your self. The one thing we noticed is the teamwork aspect of our job has just transitioned from managing time to managing our team.
Great teamwork is key! Everyone who has ever worked in a team will know not only do you need a team with the right skills for the job, they also have to have the right personality for your team.
Here at The Go To Girls Blog our team fits perfectly together. Everyone knows the importance we place on teamwork and we like to have a laugh but we all know when it is time to get our heads down and get to work too. Our team all work really hard and are always ready to put in that bit extra when it is needed.
This has also helped The Go To Girls Blog expand into helping other fellow bloggers who contact us regularly for help with various queries about their blogs. If you find your self in need of any help drop us an email at [email protected] or use our contact us link on the website. We are always here to help.
Let us know your stories about teamwork whether it is a small or large team, we would love to hear all about it.
Rule 13 Use Links.
When writing a blog post you will hear people recommend that you use 'links'. Well, this is ok, if you know what they are and how to use them. What they are for is another thing you will need to understand.
Firstly to explain a link is a way bloggers can direct traffic to other posts whether they are their own or other bloggers. This is a great way of getting other posts and bloggers traffic which may have a similar topic or niche.
Linking to other bloggers is also a great way to make blogger friends and building your blogger community. Using them is relatively easy as on most platforms the symbol for links is recognisable.

link
Simply click on this symbol and enter the name of the post you wish to link your current post to. If you are using WordPress you don't even need the full post name just a word out of the title will do.
link
Click apply and that's it. You have now inserted a link.
I know it is easy and it is amazing how much more traffic it creates for the other posts you have linked to. Why not give it a try if you have not already. Again if you need any help with links or any other blog-related issues drop us an email. You will find this is a link to contact us on our website.
Rule 14 Niche.
An important part of starting a blog is choosing a niche. If you are not familiar with blogging, a niche is a chosen area to base a blog on. i.e. food or fashion.
When choosing the niche for your blog think about something you can write with ease about, something you are passionate about.
Write about something you know about. It will make your blog so much easier to write if it is something you know about. For example, a chef would not go for a job in an office doing accounts as he would not have the knowledge to do the job so why would you write a blog on a subject you do not know anything about.
Also, the internet is a brutal place if you get it wrong. Here at The Go To Girls Blog, we have had first-hand experience with readers criticising our writing when we get it wrong.
It is not nice but you have to just suck it up and be polite with any criticism you receive. Hence the reason for choosing something you know about. Also, research is key if you are expressing a point you are not sure about research it!
It will take a couple of minutes but it will be worth it. Especially when you are writing and giving people advice or tips you need to make sure you are giving the correct information. So choose your niche wisely.
You don't even need a niche to begin your blog if you are not sure what is your niche then just write about all sorts, to begin with, and then narrow down your area as you grow your blog. Your niche will eventually shine through in your writing.
Hopefully, you will end up with a niche you are knowledgable about and make your blog a success.
Good luck with choosing yours.
Rule 15. Visibility.
When you decide you are going to start any kind of internet-based business whether it is a website, a blog or a shop you will have other questions you will need to answer.
One of those questions is about visibility, how visible do you want to be on the internet. This is especially important when writing a blog.
You have to decide how much of yourself do you want people to see? how much do you want people to know? You may reduce your visibility if you are quite shy.
You may not want people knowing everything about you or you might not want to go to events and network with other bloggers. If this is the case then it is fine, however, if you don't mind being in the spotlight then you could be at home putting your world out on the internet for all to see.
Just remember that once you put something on the internet it is there FOREVER! You may take it down but you never know if it has already been copied and/or reposted somewhere else and you never know when it will resurface.
So whatever you choose to do remember there are no do-overs. Another thing to remember is you will not be everyone's cup of tea. You will get people who love what you do or what you sell or what you write but you will get haters too.
Be prepared to deal with all of these visibility issues before you publish that very first web page or blog post.
Don't forget, be careful out there on the internet.
It can be a weird or wonderful place.
Rule 16. Social Media.
As part of a blogger's daily life, you will probably use some form of social media. This may be Twitter, Instagram, Pinterest or any of the other social media platforms out there. You may even use some kind of application to schedule these posts.
Well if you do make sure you chose these applications wisely and even more importantly use them wisely. The can be a great tool for a blogger but if used incorrectly they can ruin your social media traffic.

Social Media Tags
We have first-hand experience of this and paid dearly for this mistake. In our case, it was truly just a technical error that looked like we had spammed our Pinterest account but it was a genuine error.
Nevertheless, The Go To Girls Blog was punished severely and lost half our traffic at a time when our blog was just taking off. So take this as a warning to use social media carefully and if you manage your own technical sides to your blogs and applications then make sure you check all of the settings very carefully!!
If you do not this can cost you dearly! Anyway, on the lighter side of social media, it can help increase traffic to your website/blog greatly.
Here at The Go To Girls Blog, we have several social media accounts where we post our daily blogs which returns us a reasonable amount of traffic.
The trick is to keep all of your social media apps updated daily or as often as you can. If you update them regularly it lets your readers know you have posted again and of course they come to your website as long as you keep your posts interesting. Using good images and exciting blog post titles.
Blogging Rule 17. Know Your Audience
Do you know who reads your blog? Male or female? Old or young? What country they are residing in? No! neither did I until recently.
As I discussed in my post the other day on Blogging Rule 8 analytics can help you with more things than the amount of traffic your website receives.
I particularly love the audience insights which gives you a breakdown of the age of your audience, their gender, location and even which devices they are looking at your website on!
How amazing is that? I love checking these figures out.
I was excited enough when I saw the figures for the number of impressions my website was receiving without the split of all the categories I found when I started digging.
The analytics I use even tell me the interests recorded by the individual reading my blog. This is amazing to see as you just can't imagine ever knowing this amount of information about your readers and followers.
I love knowing all about them. What analytics do you use? Do you know all about the people who read your posts?
You should as this can help you write more relevant posts and get more traffic which in turn can help you make your brand and website more successful.
I love it when I learn things as I can then spread the word on my blog and help all of my readers to use the tips and tricks I learn much quicker.
Rule 18. Design.
The design of your blog and website is the most important thing you will need to master if you want to produce a successful brand. You should make it easy for your readers to get around using menus is a great way to do this. They will guide you around your website with relative ease if you have formulated and organised them correctly.
Make sure your website is eye-catching, you can do this by picking the right colour theme to match with your blog theme this will make it look professional.
If you have a niche then make sure your theme, colours and even the font you use reflect your niche. An example of this is if your niche us gardening then a nice natural theme and colour palette will enhance your website whereas a bright neon palette would clash horrifically and ruin the natural look you would normally use for this kind of blog or website.
Just because you are trying to monetise your site don’t overload your posts with adverts, this annoys me so it must annoy other people.
Finally, according to my research, a lot of people now read blogs on phones and pads so make sure your theme design is responsive to being used on phones and pads otherwise you could lose a lot of readers. WordPress has loads of themes especially for this and they are really easy to install.
Rule 19. Security
This is one rule you must follow. Security for your blog is crucial.
DO NOT MAKE THE MISTAKE OF NOT HAVING SECURITY!!
I can not stress how important this rule is. Security for your website can mean the difference between your website being potentially taken over by hackers or even held hostage.
I know this sounds dramatic but it is a distinct possibility and is happening more and more. Just imagine if you spent a month or even a couple of weeks setting up your website and it is perfect.
You are getting ready to launch, then the unthinkable happens, your website gets hacked!! You lose all of your hard work, money and time! What do you do then? What can you do?
Well, I hate to say it but unless you have some amazing tech skills or know someone who does then you start building your website all over again. No one wants to do this, do they?
So take our advice and get your site some security from day one.
Security First
Before you do any work on your website get some form of security. If you are using Wordpress then security is easy as they have a lot of plugins for all of your security needs.
The Go To Girls Blog uses Bluehost as this provides all the security needed to make our website secure.
Rule 20 Research Everything.
While you may be writing a blog about something you are very knowledgeable about, you still need to do your research. Do not make the mistake of thinking you know everything. There are a lot of people in the world and you can almost guarantee someone will call you out on any errors you make!
Well, I hope this post will help you in creating a better blog/website and don't forget if you need any help with anything 'techy' drop us an email.
Love The Go To Girls Blog xxx
Read the full article
#rulebritannia#ruleof72#ruleoflaw#ruleofthirds#ruleofthumb#ruler#rulermovie#ruleronline#rules#ruleslyrics#rulesofbadminton#rulesofbasketball#rulesofchess#rulesofengagement#rulesofsurvival#rulesoftheinternet#rulesofuno#rulessynonym
0 notes
Text
Euro 2020, Alipay and the plan to change mobile payments in Europe and China
Soccer teams throughout Europe this week will continue their journey towards an unprecedented sporting event.
Across the continent, men’s national sides will play the next rounds of qualification for Uefa Euro 2020. The second 24-team edition of the international game’s second-richest tournament will be played at 12 venues in 12 different countries, as a special pan-European version is held for its 60thanniversary. Meanwhile, the reach of its commercial platform will be underlined by the presence of a second Chinese company among six lead partners.
Last November, Alipay joined consumer appliances manufacturer Hisense among Uefa’s national team soccer sponsors. The mobile payments giant signed an eight-year agreement with the European soccer confederation, becoming a partner of all tournaments played between 2018 and 2026 in a deal valued at €200 million.

“What we are doing is using technology to drive financial inclusiveness around the world,” says Rita Liu (right), the head of Alipay in the EMEA region. “And we think that football is a sport that can be played by everyone and it’s also something that stands for inclusiveness. So we think we share the same vision with Uefa and with football as a sport.”
It was an announcement notable not just for its scale, but also because of Alipay’s limited European presence. In China, it dominates the QR code-based mobile payment space alongside WePay. Owned by the US$150 billion fintech group Ant Financial, an affiliate of billionaire Jack Ma’s Alibaba, Alipay’s primary services are used by 800 million Chinese consumers, while another 588 million have put aside small amounts of money through its Yu’e Bao microsavings platform.
That user base grows to over a billion once its nine partnership with other Asian digital wallet providers – like PayTM in India, Pay in South Korea, GCash in the Philippines and Dana in Indonesia – are factored in.
Over the summer, it announced plans to launch a QR-based network across ten European countries, working with Bluecode, ePassi, Momo Pocket, Pagaqui, Pivo, and Vipps. Nevertheless, its relative inactivity on the continent suggests it is looking at its Uefa partnership differently than other sponsors.
Who is this partnership aimed at?
Alipay’s Uefa partnership includes its share of conventional elements. At June’s inaugural Uefa Nations League Finals in Portugal, its branding was visible pitchside while it also sponsored the player of the match trophy. The design for that award was meant to resemble the image of a player striking a ball, and also of the first character in Alipay’s Chinese name – which means both ‘payment’ and ‘support’.
Those promotional activities are targeted as much at users in China as soccer fans in Europe.
“Even though it’s European football, it’s actually a very well-known global event,” Liu says. “It’s definitely also us leveraging this global sports platform to grow our global brand influence.”
But the partnership also caters to Chinese users in another way. According to the United Nations World Tourism Organisation (UNWTO),Chinese touristsmade 149.7 millionoverseastrips in 2018 andspent $277.3billion. Europe is the second most popular region for Chinese travellers.
Last year Nielsen produced research – funded in part by Alipay – that suggested the average Chinese tourist spent US$762 on shopping during each trip, and that 90 per cent of them would prefer to use their mobile payment service of choice if possible.
“Even though Europeans cannot use Alipay yet, we are actually enabling the merchants and partners here to accept Alipay,” Liu explains. “As you can see in the news, we are growing very fast in Europe. More and more merchants are accepting Alipay to attract more Chinese business.”
Through hospitality and VIP experiences, then, Alipay will be spending next summer driving awareness among those merchants and expanding the network of those accepting payments through its system.
How will the partnership change Uefa’s digital operation?
Alipay has also been building technical elements into the partnership on Uefa’s behalf. Its mobile wallet is now the first to be accepted on Uefa.com, and was also in use at all venues during the Uefa Nations League Finals.
“So we are bringing digital experiences to the whole event,” Liu says. “That’s what we’re already doing. And in the future we’ll be connecting all these partners we have in Asia, these wallets and these users, to Uefa as well. Hopefully, next year you’ll see the users of all our wallets in south-east Asia or in Asia will be able to use their most familiar way to pay to interact with Asia.”

Alipay’s payment system was on show at the Uefa Nations League Finals in June
Uefa is also selling tickets to Euro 2020 in China through a new Alipay portal, becoming the first sports partner to set up on the Mini Program system.
“Before, you could only buy a ticket on Uefa.com and I think they’re building it on their app, but they don’t have a native Chinese-language app or website yet in China,” Liu explains. Through the Mini Program, they don’t really need to do much to achieve that experience in China.”
Mini Program, Liu continues, is a project aimed at building Alipay out from its origins as a payment system to become a “lifestyle super-app”.
She adds: “Mini Program is basically an open platform within Alipay where developers and businesses can use the modules or portals to build their own mini-app within the Alipay app. The interaction users have within the mini-app is very similar to them using a native app of that business but for the business and developers, they don’t have to start something brand new and build a native app from scratch. They can easily use the modules behind our mini-programme system to start offering that to their customers.
“So it’s something brand new for the ecosystem in China and it has been very popular. It’s getting very popular among our partners and merchants and users. In January this year, we announced that the number of daily active users of mini-programmes had already reached 230 million. That’s a big chunk of Alipay’s users. And also, there are already 120,000 mini-programmes live on the Alipay platform.”
The expectation is that having a body like Uefa involved will encourage others to follow, giving users more reasons to stay within the Alipay ecosystem. “We’re seeing very strong interest in the market,” Liu says, “not just from sports organisations from all over the world, but from merchants and partners – they are also looking to build Alipay mini-programmes to reach Chinese customers better. So I think there will probably be more.”
How is Alipay preparing for a pan-European Euro 2020?
“Success for us next year would be that the players in our ecosystem are all happy, whether it’s our users, our merchants here, our partners at Uefa – they’re all happy,” says Liu. “That’s the simple way to put it.”
Preparing for 51 matches across 12 cities in 31 days will present a stiff logistical task to any of the key partners.
“Obviously, it’s the first time Uefa’s done this, to do it across, basically, Europe – from the very east to the very west,” Liu adds. “I think, of course, that it’s challenging, but I think it’s a great idea for Uefa to do this.”

Uefa has become the first sports partner of Alipay’s Mini Program system to sell Euro 2020 tickets in China
Liu expects Alipay to focus its efforts on cities like London and Rome, where it has a high proportion of users and there is a high concentration of Chinese visitors, creating an incentive to expand merchant networks. Still, she believes the organisation is well set to deliver its activation plans across the continent.
“In Europe, Alipay does have quite a few offices,” she says. “Together with Alibaba we have offices in the UK, Germany, France, Italy, the Netherlands and Spain. So we have people on the ground across Europe. Of course, we will rely on our agencies. So I don’t think we will have people set up specifically for this project there for a few months but we will mobilise our agencies and also the Alipay team on the ground to do it.”
At the Uefa Nations League Finals, on-the-ground experiences for fans included technology-based soccer games and installations that took fans through the process of using QR code payments. Similar physical and digital experiences are planned for next summer.
“It doesn’t have to be that Europeans can’t use Alipay so we can’t engage with European fans,” Liu says. “There are actually many other ways and we’re exploring that.”
What’s the future for Alipay as a company and a sponsor?
Despite its considerable growth in the payments sector, Liu is careful to position Alipay as a “a tech enabler” with a mission “to make financial services more inclusive to the masses, to individuals and small businesses”. It is working closely with banks, she says, as well as with investment funds on its wealth management services.
“We’re not trying to change banks,” she adds, “we’re not trying to replace banks, we’re working with them.”
The term of the Uefa partnership, along with the company’s role in the new European digital wallet network, will inevitably fuel speculation about a wider launch in the region for Alipay. Liu, however, is non-committal about the prospect.
“There’s no clear timeline for whether or when Alipay will come and really offer our services to Europeans or through partners,” she says. “But our concept is to always start with the users. So what we do needs to solve certain pain points. If people here are very happy using contactless or using other ways of payment, and it’s convenient for them, then there’s no point of changing that. We’re not using technology for the sake of technology. We want to use technology to make people’s lives easier.
“So what’s the pain point of a UK customer? We start from the customers. In China, it’s not because we are offering the QR code as something new from a card or other ways of payment. We made the payment more convenient than traditional payment options in China and, also, the other functions we offer in the app, like wealth management tools and being able to get merchants’ coupons inside the app – the lifestyle enabler concept behind it that made people’s lives easier – that’s why people use Alipay.

Alipay could be integrated into Alibaba’s partnership with the IOC
“If we cannot solve a pain point, then we wouldn’t push the wallet to the users here. It doesn’t make sense.”
Whatever its corporate intentions, Liu believes Alipay has plenty it can bring to its role as a Uefa sponsor between now and 2026. Much as Alibaba is using its sponsorship of the International Olympic Committee (IOC) to overhaul the digital operation of the Games, Liu sees potential in an integrated approach.
“We do believe there are many ways that tech can digitise, can improve or can optimise sports fans’ experience,” she says, pointing to Alipay’s research in areas like blockchain, AI and the Internet of Things. “This is something that we’re also exploring – how to use tech to digitise and to optimise sports.”
Alipay, much like Alibaba, sees sport and wellbeing as a “big growth area in China” and one that will create its share of possibilities, even if the company takes a steady approach to adding further partnerships.
“Lots of people are coming to introduce themselves and see if there is more of an opportunity for working together,” Liu says. “Currently, we’re very focused on Uefa because they’re a great partner and it’s a great deal. It’s new for us so we want to do it properly. There’s so much we can do with them.”
Source link . More news
via wordpress https://ift.tt/2ZR0bof
0 notes
Text
Son Goku // Kakarot

Age: 43 (Main verse, accounts for lost years in Hyperbolic Time Chamber, Goku’s physical age places him somewhere in his mid-30s)(Saiyans retain a physical prime for much longer than humans so Goku can easily be mistook for a person in his late 20s)(As of Age 780)
Aliases: Gokawah (Mispronunciation by The World Tournament Announcer), Kong
Date of Birth: April 16
Place of Birth: Birthing Facility 4, Vegetopolis, Planet Vegeta
Species: Saiyan
Universe Inspiration: Manga/DBS Anime-Inspired Composite Goku (may have traits from GT and Xenoverse games occasionally)
Appearance
Goku is an adult of above average height (175 cm/5′9″), with dark hair and eyes. His expression is generally friendly and amicable. Goku’s eyes are often compared to other saiyans for usually being softer, and more rounded, only growing narrow and intense during moments of emotional heat. When going super saiyan, Goku’s eyes take on a tealish-green color.
Like all saiyans, Goku’s hair is notably distinct, having a wild shape to it, being composed of larger spikes, having a windswept appearance almost permanently. Another hallmark attribute of his species is the fact that Goku’s hair largely maintains its characteristics as he ages, not being disproportionate at any age, negating his need to cut hair, and keeping its shape non-rigidly, making other styles almost impossible. When his hair IS shortened unduly, either in part or as a whole, it will grow back to its natural state like typical hair.
As a child Goku was very short and stocky, so much so that through his adolescence he was often mistook for a child of under ten, but after experiencing several significant growth spurts that are consistent among full-blooded saiyans, Goku’s build became more slim, still having muscle built from practicing martial arts and strength training. Upon taking on more intense training, for a time, Goku became notably bulkier, though this has receded as Goku’s refocused on more technical training, and endurance-based tests, as his body has seemed to acclimate to the intense conditions that he developed his herculean strength under. When transforming into higher levels of super saiyan, Goku’s muscles shore in size once more.
When charging his chi, Goku’s aura is largely colorless, not taking on any particular visual element besides the direct results of his energy manifestation. However, upon transforming, Goku’s aura often changes according to the transformation at-hand. It’s implied that he has conscious control over the color of his aura in this way. When using Super Saiyan at any level, his aura takes on a yellow-gold color, growing darker with each subsequent form, until 4 where it becomes pink-red. After becoming a Super Saiyan God his chi becomes a fiery red. Once he’s learned how to pressurize his chi and use it like a GoD, Goku’s energy often has a light lining of white at the edges, this may be a subconscious result of the way he’s utilizing his energy. When using Super Saiyan Blue, Goku’s chi becomes intensely blue. At any time that he uses Kaioken, Goku’s aura becomes so powerful that even his body appears to be the same deep crimson as his aura.
Goku usually dresses comfortably, often favoring a gi, with trousers, a pair of boots in which he’s tucked the legs of his gi, wristbands, and underclothing. Most commonly, Goku wears a gi that’s orange in color, although from time to time he changes to a blue outfit instead. When not wearing martial arts clothing, Goku will favor simple farming clothes, including a favorite leather jacket with a fur lining, or a jumpsuit for training, on occasion.
Personality
Laid-back and friendly, Son Goku is a personable individual who makes friends easily. With an eager desire to see new things, and fight strong opponents, he is a wandering soul, often confused for a flake, or a deadbeat by others who hold certain expectations for people to contribute to society in typical ways. This drive to experience often leads Goku to leave with little notice, for long stretches of time, to have adventures. Coupled with having only had passing relationships as a youth, Goku often doesn’t invest a great amount of time with his loved ones, having not even seen his closest friend for nearly half a decade following the final battle with Piccolo.
With a drive to grow stronger, and test that strength, Goku often wishes to spend the majority of his time training. It seems that Goku is at his happiest then, or when he’s utilizing the fruits of his labors against a powerful opponent. It’s easy for the saiyan to grow excitable at the mere mention that an individual may be strong. In the past, Goku has proven to be selfish in this pursuit as well. Disregarding the safety of others, or the very consequences of his battles, he will often endanger nearly anyone to have a chance at an opponent.
Like all saiyans, Goku has a powerful love of food, with a voracious appetite that demands to be sated. If his hunger goes unsatisfied for too long, Goku’s even been known to become physically weak or ill. This informs his marriage to Chi-Chi who, being a highly proficient chef, rarely has a hard time keeping Goku happy for long with her cooking.
Biography
(I’ll be real? A bio for Son Goku would be VERY lengthy even to include non-filler content, as the three main series installments themselves had quite a bit of length as well. In the interest of saving time, after having only managed to finish Dragon Ball, this bio was shaping up to be WAY too long for anyone to bother to read. In the interest of saving time, if you individually do not know what happened in Goku’s life, please refer to his article on the wiki.)
Skills, Abilities, and Powers
-Superhuman Physical State: As a saiyan, Goku’s physical abilities naturally exceed that of a regular human adult, even as a child. While still twelve years-old Goku was shot with a handgun at fairly close range, with only a stinging pain for his trouble. In the same scene, he had lifted an automobile with some strain, and threw it onto its side.
Over the course of the series, Goku continues to perform similar and more impressive feats of physicality, eventually scaling into a degree of immeasurability during Dragon Ball Super, having nearly matched the forces of Lord Beerus’s punches, creating tsunami-like shockwaves that grew stronger the further they traveled from their origin, becoming so destructive that if the two met again in a similar sort of bout, that very universe would fall apart.
As Dragon Ball as a whole doesn’t often get hung up on specific measurements, or even concretely establishing WHAT the upper-limits of its characters are, it’s simply better to understand how Goku’s physicality stacks up in his own universe, relative to others of a similar nature.
Goku is a generally balanced fighter, not placing a particular emphasis on strength, durability, or speed, at least over each other. He understands the necessity of all three, and the importance they play in any fight, and while he’s able to modulate them through his chi, Goku often seems to boost them all fairly equally, although I’m inclined to say if any, he favors durability and quickness slightly more than raw attacking power. If given 15 points, Goku would spread as-follows:
Power: 4
Speed: 6
Durability: 5
-Superhuman Senses: Goku is able to perceive, and react, to things much more quickly and acutely than a normal human. This seems to be somewhat a result of his being a saiyan, but has been further honed through martial arts and chi training. Additionally, Goku has a very sensitive sense of smell, being able to smell food from far distances.
-Martial Arts Master: Goku is considered a master of martial arts, having developed a formless, improvisational, style that was largely influenced by Toriyama’s love of Jackie Chan films. As a child, Goku was taught a type of kung-fu that focused on function over form, using his small size against opponents in order to dodge his adult opponent’s attacks, while applying leverage to compensate for his size, despite a lack of need for this.
Beyond this, Goku would have several teachers, Roshi would teach him the importance of his physical conditioning and mental sharpness/intelligence; Korin would teach Goku how to predict and anticipate the movements of others; Kami and Popo would focus on training Goku’s abilities with Chi, as well as helping him learn how to fight as an adult; and King Kai would further cement Goku’s need for conditioning, helping him master his speed, and ultimately his ability to use chi masterfully.
In terms of overall style, Goku doesn’t have a firm one, but favors smooth and fluid motions, with a significant amount of counter-attacking and interception. While some might perceive Goku’s style to be simple and more akin to brawling, but this is simply due to Goku favoring economic movement, and strategy, both of which are more difficult to execute when focusing on maintaining a style, rather than simply fighting.
-Combat Genius: Due to a natural proclivity towards combat that Goku is possessed of, exceeding even that of more powerful saiyans, he is able to prepare effective strategies in the heat of battle. He has often used this to defeat foes who he would normally not be able to defeat. Additionally, repeated use of tactics don’t seem to work on Goku, as he can adapt to them, exploiting repetitive fighters.
-Technique Mimicry: Despite his relative weakness when compared to other saiyans, Goku is a natural knack for replicating the techniques of others. Needing to only seen most techniques performed once, be they physical or chi-based, Goku can replicate them effectively. He has even mimicked Berrus’s Hakai, although to a weaker degree. Goku cannot perfectly replicate complex or overly-powerful chi techniques, needing time and training to even master the Kamehameha.
-Chi Manipulation and Generation: A metaphysical energy that embodies life itself, mystical in nature but not strictly magic, Chi is influenced by many factor, both mental, physical, and spiritual. Saiyans have the inborn ability to manipulate their chi, allowing Goku to harness it into orbs of plasma, to then fire and create explosions, despite only seeing the kamehameha performed once.
Chi is able to be used in a variety of functions, such as flight, blasts of energy, sabotage the chi and energy-based attacks of others, and enhancing physical attributes. The latter is something Goku does often, but must be aware in order to do so. Goku has been caught off-guard by relatively weak attacks, when not using his chi, so that he’d suffer injury.
The depth of Goku’s chi-based abilities is currently unknown, but he has managed to manifest numerous physical and mental abilities through it. He has long-since passed the power of beings who could destroy planets many times larger than Earth without effort, and has managed to dwarf that of an individual who was said to be able to destroy an entire solar system with his full power.
In truth, the only limitation to Goku’s abilities with chi does seem to be that he cannot exert more energy at once than he himself can sustain, as the force of his attacks never push or move him unless he allows it to.
In the event that Goku does push himself too far, tax his chi too much, or otherwise uses his power too recklessly, Goku’s chi use can have consequences.
-Ultra Instinct: A state of being that is present in real-world martial arts, Ultra Instinct allows its user to react to their foes, attacking and defending without thought, in the most effective way possible. This state enhances his physical and mental abilities as well, akin to that of a transformation. Ultra Instinct is only accessible to Goku when he’s in a sufficiently dangerous situation, being unable to use it at-will, not making it a reliable technique. Goku once achieved a mastered state that allowed him to bridge the seemingly-impossible gap between himself and Jiren, a being who was more powerful than even the Gods of Destruction.
Chi-Based Abilities and Techniques:
-Flight
-Chi Sensing
-Chi Transferal
-Godly Chi Mastery
-Regeneration
-Energy Nullification
-Telepathy
-Chi Blasts
--Finger Beams
--Chi Waves
-Kamehameha
--Continuous Kamehameha (A variation which involves Goku firing multiple Kamehameha blasts from each hand)
--Bending Kamehameha (A Kamehameha variation which more easily changes course)
--Flying Kamehameha (A utilization of Kamehameha that Goku uses to fly through the air)
--Twin Dragon Shot (A manipulated, spherical, version of the Kamehameha. Requires fine control)
--MAX Power Kamehameha (A version of the Kamehameha in which Goku uses the full version of the technique. Produces the most power of a base form Kamehameha, but requires too much time to execute correctly)
--Super Kamehameha (An advanced version of the Kamehameha, inefficient)
--Kaio-Ken Kamehameha (A Kamehameha influenced by the multiplied Chi of Goku’s Kaio-ken)
--Instant Kamehameha (A version of any Kamehameha fired directly following a use of his Instant Transmission)
--True Kamehameha (An even stronger variation of Super Kamehameha, even less efficient, requires Goku to be in Super Saiyan 3 to use effectively)
--Limitbreaker Kamehameha (A variation of Super Kamehameha that Goku uses during his Super Saiyan God form)
---Limit Break x10 Kamehameha (A variation of the Limitbreaker Kamehameha which Goku can fire in his Super Saiyan 4 transformation)
--God Kamehameha (The base Kamehameha fired with godly power, during any Godly transformation. Individually as powerful as any Super Kamehameha, but as efficient as the base technique)
---10x God Kamehameha (A variation of the God Kamehameha that is roughly ten times stronger than the original. Can only be used is Super Saiyan Blue Kaio-ken or stronger forms)
---Transcendent God Kamehameha (A variation of the Super Kamehameha fired in a godly form, is extremely potent)
--Final Kamehameha (A combined technique between Goku’s Kamehameha and Vegeta’s Final Flash)
--Imperfect Instinct Kamehameha (A variant of the kamehameha that is fired in any of the incomplete versions of Goku’s Ultra Instinct technique. The output is greater than a standard God Kamehameha)
---Supreme Kamehameha (An enhanced version of the Imperial Instinct Kamehameha used during Goku’s perfected Ultra Instinct)
---Ultimate Instinct Kamehameha (The Super Kamehameha fired in Goku’s Perfected Ultra Instinct form. The strongest variant of the technique)
--Kamehameha Blaster (A variant of the Kamehameha that is followed with a series of smaller blasts)
--10x Kamehameha (A variation of Kamehameha that requires more charging, but takes on a red color, and is ten times as strong as the base technique)
--Dimension Breaker (A Kamehameha that rips through dimensional barriers)
-Kiai
--Spirit Shot
--Invisible Eye Blast
--Soaring Fist
-Destructo Disc
--Destructo Disc Hexa Blast
-Explosive Wave
--Super Explosive Wave
-Spirit Bomb
--Fusion Spirit Bomb
--Large Spirit Bomb
--Instant Spirit Bomb
--Super Spirit Bomb
--Universe 7′s Spirit Bomb
-Hakai (Goku’s version of the GoD’s Destructive technique. Goku must put all of his SSB aura into a single attack. This attack leaves him fully drained after use)
-Evil Containment Wave
-Energy Barrier
--Super Guard (Xenoverse 2)
--Vanisher Guard (Xenoverse 2)
-Chi Landmine
-God Bind
-Solar Flare
-Fusion Dance
-Black Power Ball (Xenoverse 2)
-Black Kamehameha (Xenoverse 2)
-Azure Dragon Sword: model Energy Blade (Xenoverse 2)
-Divine Lasso (Xenoverse 2)
-Evil Eyes (Xenoverse 2)
-Oozaru
--Golden Oozaru (A use of Super Saiyan while in his Oozaru form)
---Super Saiyan 4 (A Super Saiyan transformation that ascends through Oozaru. Its strength relative to the other forms, but is presumably at least 10x stronger than Super Saiyan 3)
----Super Full Power Saiyan 4 (By absorbing extremely large amounts of power from other saiyans, Super Saiyan 4 is enhanced further)
-Kaio-ken (A technique that multiplies Goku’s Chi for a “heart beat”. His power and speed are multiplied by two at base, but can be enhanced further, and maintained for longer. The greater the multiplier, or time that the technique is used, the more backlash Goku will suffer)
-Super Saiyan (An ancient prophecy personified, this transformation increases Goku’s chi by roughly 50x. This form also enhances his physical attributes similarly. If used without mastery, Goku begins to lose his composure and actively has to keep himself from losing control)
--Spirit Bomb Super Saiyan (By absorbing his Spirit Bomb, Goku is able to enhance his Super Saiyan form briefly)
--Super Saiyan Second Grade (An enhancement of the base Super Saiyan form, Goku’s speed and strength are further enhanced through the stimulation of his nervous system by his chi. Is much faster and stronger than base Super Saiyan, but tires more quickly)
---Super Saiyan Third Grade (A further advanced version of Second Grade. The body no longer inhibits itself, acting at full power, at 100% strength and stamina. This form makes Goku slower, and drains his body’s energy drastically)
--Super Saiyan Full Power (A mastered, most efficient, version of the Super Saiyan form)
--Super Kaio-ken (Super Saiyan with the Kaio-ken multiplier used on top of it. Dangerous to use for extended periods)
--Super Saiyan 2 (The “Fourth Grade” of Super Saiyan. A breaking of the base Super Saiyan form’s limit, enhanced 2x from the Super Saiyan form [100x the user’s base form]. Does not suffer from the Second Grade or Third Grade weaknesses. It grows difficult to control oneself while using this form)
---Super Saiyan: Berserk (A version of Super Saiyan 2 that takes advantage of its lessened inhibitions. This form is corrupted by outside chi)
--Super Saiyan 3 (The “Fifth Grade” of Super Saiyan. A further more powerful form of Super Saiyan 2, its hair grows longer, and the user’s eyebrows seem to disappear. 4x more powerful than Super Saiyan 2 [400x the base user], the user’s inhibitions further decrease. This form’s output is so significant that it puts a large strain on Goku’s body and lifeforce, to the point that it shortened his time on Earth as a spirit)
-Super Saiyan God (Goku’s base form enhanced by the power of five other saiyans, stronger than any of his previous Super Saiyan forms, this transformation is accessible to him, and allows Goku to easily access Godly Chi)
--Godly Saiyan (Goku using his chi efficiently, with pressure, to use Godly Chi without using Super Saiyan God)
--Super Saiyan Blue (A form of Super Saiyan God in which Goku activates his Super Saiyan form while possessing Godly Chi)
---Super Saiyan Blue Kaio-ken (Variations of Super Saiyan Blue in which Kaio-ken is multiplying Goku’s power. At maximum, Goku can manage x20)
---Perfected Super Saiyan Blue (Similar to Perfected Super Saiyan, a version of SSB that doesn’t drain Goku’s reserves at all, unless he’s in combat)
--God-to-Blue Switch (An efficient use of Goku’s Godly forms, Goku rapidly switches between SSG and SSB so as to use SSB at its fullest power, without draining his reserves as quickly)
-Ultra Instinct -Sign-
--Ultra Instinct
Martial Abilities and Techniques
-Rock, Scissors, Paper!
-Tail Attack
-Super God Fist
--Silver Dragon Flash
-Double Axe Handle
-Pressure Point Attack
-Headshot
-Super God Shock Flash (One-Inch-Punch)
-Grudgeless Strike
-Ginyu Fighting Pose
-Dragonthrow
-Full-Nelson
-Kaio-ken Finish
-Kaio-ken Attack
-Meteor Combination
--Meteor Smash
-Eight-Arm Fist
-Crazy Fist
-Tornado!
-Afterimage Technique
--Wild Sense
--Instant Transmission
--Afterimage Strike
-Blast Fist
-Dragon Fist
--Super Dragon Fist
---Final Strike
---Super Dragon Twin Fists
---Dragon Hammer
0 notes
Photo

New Post has been published here https://is.gd/65lHi1
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
This post was originally published here
James Bridle is a writer working across technologies and disciplines and author of “The New Dark Age: Technology and the End of the Future.” His work can be found at http://jamesbridle.com. The following work will appear as an introduction to “The White Paper by Satoshi Nakamoto” to be published by Ignota Books.
For more on bitcoin’s 10th anniversary, check out our new interactive feature Bitcoin At 10.
————-
It’s difficult to know when humans first started securing or ‘encrypting’ messages to hide them from unwanted readers; the practice must, by human nature, be almost as old as written language, although examples are sparse. We know, for example, that Julius Caesar used a simple form of letter substitution to communicate with his generals, shifting each character three steps down the alphabet in order to scramble it.
The ancient Greeks, particularly the military-minded Spartans, used a device called a scytale, which allowed a hidden text to be read by wrapping a strip of parchment around a cylinder of a particular size so that the letters lined up in a particular order. Tales of the Greco-Persian Wars are full of secret messages, not least the story of Histiaeus, a commander who, according to Herodotus, shaved the head of his favorite slave and had it tattooed with a message urging revolution in the city of Miletus.
When the slave’s hair grew back he was dispatched to the city, with the instructions that the recipient should shave him once again and read the message there revealed.
Such extreme measures were taken due to the fear of government surveillance, a justification often cited today. The Persian king controlled the roadways, and had the power to examine any message – and messenger – that travelled on them. From the very beginning, cryptography has been both a military technology and a tool for undermining existing powers.
Cryptography’s value as a military tool is double-edged, of course.
Like other weapons, its effectiveness depends on the ability of one side to outgun the other. For a long time, this balance mostly held, with efforts by one side to crack the secrets of the other forming long-running and fascinating backstories to many conventional conflicts. It was an act of decryption that brought the United States into the First World War when British intelligence services decoded the infamous Zimmermann Telegram proposing an alliance between Germany and Mexico.
In the closing months of the war, the cracking of Germany’s ADFGVX cipher by French cryptanalysts enabled the Allies to stave off a final German offensive on Paris.
Cryptography was first mass-manufactured in the Second World War, in the form of the Third Reich’s Enigma machines, and then digitized in the form of the Colossus, the world’s first programmable electronic computer, developed to break the German military’s Lorenz cipher. The wild invention and ultimate success of the Bletchley codebreakers over their Nazi adversaries can be read as the first of many instances of the digital overcoming the physical; the Lorenz SZ42 was a massive, complex machine of rotating cogs and wheels which defied codebreakers for years.
By the end of the war, it was completely readable by an electronic machine. The secrecy around the Colossus itself meant that its existence had little influence on future computer design, but it marks the point at which cryptography changed radically in nature – because what is digital is ultimately distributable, although it would take the growth of the internet in the 1990s for this to become widely understood.
In 1991, a computer security researcher called Phil Zimmermann created a programme called Pretty Good Privacy (PGP), which enabled users of home computers to strongly encrypt email messages using a combination of numerous well-known algorithms. What turned PGP from another homemade software product into one of the most contentious artifacts of the decade wasn’t how it was made, but how it was distributed. Since the Second World War, nations had been forced to legally define cryptography as a weapon; like any other munition, cryptography was subject to something called the Arms Export Control Act.
At the time of PGP’s release, any cryptosystem which used keys – the strings of randomly generated numbers which secured hidden messages – longer than 40 bits required a licence for export.
PGP used keys which were 128 bits long and almost impossible to crack at the time, and this made it precisely the kind of technology that US authorities wanted to prevent falling into foreign hands. Zimmermann never intended to export PGP, but, fearing that it would be banned outright, he started distributing it to friends, saying, “I wanted to strengthen democracy, to ensure that Americans could continue to protect their privacy.”
Shortly after that, PGP found its way onto the internet and then abroad. In 1993, the US government started a formal investigation into Zimmermann – for exporting munitions without a license. As knowledge of the case spread, it became a flashpoint for early digital activists who insisted on the rights of everyone to protect their own secrets and their own private lives.
The freedoms and dangers of code became the subject of earnest debate, and in another foreshadowing of future digital style, of hacks, pranks and stunts. Zimmermann had the software’s source code printed as a hardback book, allowing anyone to purchase a copy and type up the software themselves.
As he was fond of pointing out, export of products commonly considered munitions – bombs, guns and planes – could be restricted, but books were protected by the First Amendment. Variants on the RSA algorithm – the 128-bit process at the heart of PGP – were printed on T-shirts bearing the message ‘This shirt is classified as a munition’. Some went further, having lines of code tattooed onto their arms and chests.
The crypto wars
The Crypto Wars, as they became known, galvanized a community around the notion of personal – rather than national – security, which tied into the utopian imagination of a new, more free, more equal and more just society developing in cyberspace.
Another development that prompted widespread public disquiet was the US government’s proposal for a chipset for mobile phones. The Clipper chip was designed by the NSA to provide encryption for users while allowing law enforcement to eavesdrop on communications – a situation that was ripe for abuse, either by corrupt officials or by skilled hackers.
Clipper chip via Wikimedia.
The idea that a government would deliberately weaken the protections available to its citizens made for an even more powerful and accessible argument for the individualists than the attack on PGP. By the late 1990s, Clipper was dead – and so was the case against Zimmermann. The hackers and privacy activists declared victory in the Crypto Wars.
Yet what’s often regarded as a victory for everyone against government overreach can also be read as a moment of terrifying breach: when the state’s most powerful weapons escaped government control and fell into the hands of anyone who wanted to use them. Today, thanks to the rise in digital communications, cryptography is everywhere, not least in banking systems, protecting the billions of electronic transactions that flow around the planet every day.
Even more than in the 1990s, the idea that anyone would deliberately make it easier for someone to steal money seems like an attack on the basic functions of society, and so it should come as no surprise that it’s a technology best known for – but by no means limited to – the distribution of currency that should be the focus of a new outbreak of the Crypto Wars, as well as the full flood of individualist, utopian thinking that accompanied the first round. There’s something about money that focuses the mind.
When Marco Polo first encountered paper money on his travels to China in the 13th century, he was astounded. In his Book of the Marvels of the World, he spends a great length of time explaining, and wondering at, the monetary system established by the Great Khan. Until recently, and as was still the case in Europe, the Chinese had used a range of value-bearing commodities to settle commerce and taxation: copper ingots, iron bars, gold coins, pearls, salt and the like.
In 1260, Kublai Khan decreed that instead, his subjects would use apparently valueless paper, printed and certified by a central mint, and, writes Polo, “the way it is wrought is such that you might say he has the secret of alchemy in perfection, and you would be right.” Through a carefully choreographed process of manufacture, design and official imprimatur, “all these pieces of paper are issued with as much solemnity and authority as if they were of pure gold or silver.”
The process was alchemical in the truest sense, as it did not merely transform material, but also elevated the Khan himself to even more unassailable heights of power: the only arbiter of finance. Those who refused to accept the new currency were punished with death, and all trade flowed through the state’s coffers. Like the Persian king before him, the Khan had realized that controlling traffic – in commerce and in information – was the way to situate oneself at the true heart of power.
True magic
The processing and accounting of money – fiat money, created by decree rather than having inherent value – is essentially the manipulation of symbols, and the gradual but ever-accelerating authority of capitalism, money’s belief system, tracks the development of symbol-manipulating technologies, from the double-entry bookkeeping of the European Renaissance to the development of databases and planet-spanning electronic networks; from physical technologies to virtual ones.
Money also involves the magical transformation of symbols into value. It requires belief to operate.
Around such belief systems other beliefs tend to gather, and the industrial quantities of belief required to breathe life into new systems of value tends to gives succor to any number of outlandish ideas, whether these be the divine right of kings, the supremacy of the nation state or the inviolable will of technology itself.
Money, then, is a belief system backed by state infrastructure which, for a long time, assured centralized power. But as computational technologies, long the sole province of the state, became less about asserting government power than asserting individual freedom – in other words, as the weapons forged in the crucible of the Second World War became increasingly available to the common citizen – it became clear to the veterans of the Crypto Wars how they might make other adjustments to ancient power dynamics.
The idea for digital money and virtual currencies had been floating around for some time before the Crypto Wars. Money has been
tending towards the virtual for some time, from the first ATMs and cards in the 1960s, to the spread of digital networks and connections between retailers and banks in the 1980s and 1990s. For anyone with a little technological foresight, it was easy to see which direction we were heading in.
For those concerned with privacy and individual sovereignty, it was a worrying development.
The first ATM via TIME
Digital money, significantly, has none of the advantages of cash; it can’t be stored and exchanged outside of the system of banks and third parties, such as credit card companies, which can regulate and impede its flow. To a cryptographer, or anyone who has imbibed cryptography’s lessons on the potential to separate oneself from overbearing powers, this arrangement looks like a kind of enslavement. So what would digital cash actually look like?
The first quality of digital cash is that it needs to be private, in the sense that no one other than the spender and receiver should be party to the transaction: no bank or security agency should know who is spending the money, who is receiving it, what it is for or at what time and place the exchange is taking place. Because no physical assets, such as notes or coins, are being exchanged, it should also be secure. The receiver should be able to verify they were paid and the spender that they had paid – a two-way receipt for the transaction.
In this way, digital cash would have all the privacy of physical cash, with the added benefit of the participants being able to prove that a transaction had actually taken place.
The opening shot
One of the earliest proponents of digital cash was an American computer scientist called David Chaum.
Chaum believed that both the privacy and the security problems of digital currencies could be solved by using cryptography: encoding messages between the two parties, the sender and the receiver, in such a way that nobody else can read them. Chaum’s solution to this problem involved both parties digitally signing the transaction with a private key, akin to an unforgeable and unguessable digital signature. In this way, both parties validate the transaction. In addition, they communicate through encrypted channels, so that nobody else can see that the transaction has taken place.
Chaum’s system worked, and was implemented by a number of companies and even one bank, but it never took off.
Chaum’s own company, DigiCash, went bankrupt in 1998 and there was little incentive to compete against the growing power of credit card companies. Chaum felt that people didn’t understand what they were losing as digital networks and the money that flowed across them became more centralized: “As the web grew, the average level of sophistication of users dropped. It was hard to explain the importance of privacy to them,” he said in 1999.
David Chaum via Elixxir project.
Yet some people, including those radicalized by the Crypto Wars of the early 1990s, did understand the value of privacy.
A group which came to be known as the Cypherpunks gathered first in San Francisco, and then online, with the intent of picking up from Chaum’s work the tools that could be used to disempower governments. From the very beginning, Chaum’s ideas about privacy and security had been tied to ideas about society and the way it was being changed by digitization.
“Computerisation is robbing individuals of the ability to monitor and control the ways information about them is used,” he wrote in 1985, foreseeing a Big Brother-like “dossier society” where everything was known about individuals but individuals knew little about the information held over them.
Yet Chaum was forced to partner with existing institutions to get DigiCash of the ground – and this was very far from the Cypherpunk dream. Eric Hughes, a Berkeley mathematician and one of the original Cypherpunks group, published ‘A Cypherpunk’s Manifesto’ in 1993, arguing that privacy was a requirement for an open society, and privacy on electronic networks could only be achieved through the use of cryptography.
Tim May, another member of the group and a former chief scientist at Intel, went further in the The Crypto Anarchist Manifesto:
“The State will, of course, try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be traded freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions.”
Throughout the 1990s and into the 2000s, the Cypherpunks elaborated on the principles that would bring their utopia of encryption into being, as well as the technical innovations required to make digital currency possible.
One of the biggest hurdles to doing so was the double-spending problem. Physical cash can only be spent once; when a banknote is handed over to a merchant, the buyer can’t at the same time use the same note at another shop around the corner. Virtual currencies face the problem that while encryption can guarantee that this specific piece of data is a form of money belonging to this specific person, it can’t say whether that data has been copied and is also in circulation elsewhere.
In other words, it can’t say whether or not someone is trying to spend the same coin twice at the same time. The need to have a central register to check each transaction was what forced David Chaum to partner with banks.
This necessitated routing all electronic transactions through credit card companies, and re-introduce dthe Cypherpunks’ worst enemies: loss of privacy and the need to trusts some hierarchical organization, a government, bank or corporation, with the authority to verify and, if necessary, roll back transactions.
The blockchain
The solution to the double-spending problem appeared quite suddenly in October 2008, with the publication of a paper on the The Cryptography Mailing List entitled “Bitcoin: “A Peer-to-Peer Electronic Cash System.” Citing several forerunners in the field, the author of the paper, the previously unknown Satoshi Nakamoto, proposed one key innovation which solved the double-spending problem while preserving anonymity and preventing the need for trusting third parties.
This was called the ‘blockchain’: a distributed ledger, or record of transactions, which would be maintained by everyone participating in the system. It’s called the blockchain because groups of transactions are gathered together into ‘blocks’ as they occur, and as each block is turned out it is added to the ‘chain’ of all transactions. That’s it. It’s simply a list of things that happened.
If everyone can see every transaction, then there is no need to hand over control to banks or governments, and if everyone follows the encryption practices of the Cypherpunks, there is no way to know who is spending the money.
Of course, if everyone has a copy of this ledger, we need to know it hasn’t been forged or tampered with in any way. So in order to extend the blockchain, in other words to write in the ledger, a certain amount of computational ‘work’ has to be done: the computer doing the writing has to solve a particularly complex mathematical problem.
Bloomberg Magazine, 2015
The fact that it’s relatively easy for everyone else’s computers to check if this problem really was solved makes it very difficult – in fact, practically impossible – for anyone to create a fake version of the ledger. In a particularly clever twist, participants are incentivized to help maintain the ledger by receiving a small number of bitcoins when they do solve the mathematical problem. This is where the notional value of Bitcoin comes from: someone has to put in an amount of time and energy to produce it, which is why this process is known as ‘mining’.
Over time, more and more coins are produced, to an eventual total of 21 million sometime in or around 2140. Satoshi’s paper had the good fortune to appear at a particular time. Encoded into the very first block on the Bitcoin chain is a timestamp, the kind of timestamp more familiar from ransom demands: a proof of life.
The phrase embedded forever into the beginning of the blockchain is ‘The Times 03/Jan/2009 Chancellor on brink of second bailout for banks,’ a reference to the front page headline of The Times newspaper on that date.
On one level, it’s a simple proof that no valid coins were mined before that date. On another, it’s an ironic comment on the state of the standard economic system that bitcoin set out to replace. It’s also, for those fascinated by such things, one of the earliest clues to the identity of Satoshi Nakamoto. Satoshi Nakamoto appeared in the world, as far as anyone is aware, with the publication of the Bitcoin white paper. There is no trace of the name before that date, and after a few months of interacting with other developers on the project, Satoshi Nakamoto disappeared just as abruptly from public view at the end of 2010.
With the exception of a couple of private emails (indicating that the developer had ‘moved onto other things’), and a forum post disavowing an attempt to ‘out’ the developer in 2014, Satoshi Nakamoto has not been heard from since. Perhaps instead, more accurately, we might say that the entity referring to itself as Satoshi Nakamoto has not been heard from since 2010.
For less interesting than the ‘real’ identity of Satoshi is the way in which that identity operates in the world – in a way that perfectly accords with Cypherpunk and blockchain doctrine.
Eating the dog food
In Section 10 of the Bitcoin white paper, Satoshi outlines the privacy model of the system. In the traditional banking model, the flow of money through an exchange is anonymized by the third party administering the transactions; they hide what they know from everyone else. However, on the blockchain, where all transactions are public, the anonymity happens between the identity and the transaction; everyone can see the money moving, but nobody knows whose money it is.
The common idea of cryptocurrencies is that they set assets free, but a cryptocurrency is a monetary unit like in any other currency system – one that, because of the blockchain, is closely monitored and controlled. What’s really liberated is identity. It is liberated from responsibility for the transaction and liberated from the ‘real’ person or persons performing it. Identity, in fact, becomes an asset itself. This is also what marks out the idea of the blockchain from earlier cryptosystems like PGP; it’s not the messages that are being hidden, but the actors behind them.
A necessary part of software development is the use of the technology in real-life situations for the purposes of testing.
This is often done by the developers themselves in a process known as ‘eating your own dog food.’ While the developers of bitcoin could test mining and transacting coins between them, the real ‘product’ of bitcoin – a decentralized, deniable identity – could only be tested by someone (or a group) willing to build and sustain such an identity asset over a long period of time – and who better to perform that test than the creator of bitcoin themselves?
Satoshi Nakomoto is an exercise in dogfooding – and proof of its efficacy.
Newsweek Magazine, 2014
When Satoshi disappeared into the ether, they left on the blockchain, unspent, the piles of bitcoins they’d personally mined in the early days of the project – over a million of them. These bitcoins are still there, and only someone who holds Satoshi’s private keys can access them. Today, Satoshi ‘exists’ only to the extent someone can prove to be that individual – the only proof of which is possession of those private keys. There is no ‘real’ Satoshi.
There is only a set of assets and a key. ‘Satoshi Nakamoto’ is creator, product and proof of bitcoin, all wrapped up in one.
Once again, the creation of money is the creation of a myth. In his book “Debt: The First 5,000 Years,” the anthropologist David Graeber proposes that the connection between finance and sacrifice runs deep in Western culture: ‘Why, for instance, do we refer to Christ as the ‘redeemer’? The primary meaning of ‘redemption’ is to buy something back, or to recover something that had been given up in security for a loan; to acquire something by paying of a debt. It is rather striking to think that the very core of the Christian message, salvation itself, the sacrifice of God’s own son to rescue humanity from eternal damnation, should be framed in the language of a financial transaction.’
Satoshi’s sacrifice is something different, but in the anarchic frame from which the individual emerged, not dissimilar. In order to secure the future of bitcoin, Satoshi gave up all personal gains from its invention: some 980,000 bitcoins, valued at $4 billion in late 2018. This is a gesture that will continue to inspire many in the bitcoin community, even if few of them understand or even consider its true meaning.
The power of brands
Back in 1995, another regular Cypherpunk contributor, Nick Szabo, proposed a term for the kind of sacrificial identity deployed so successfully by Satoshi: a ‘nym’. A nym was defined as ‘an identifier that links only a small amount of related information about a person, usually that information deemed by the nym holder to be relevant to a particular organization or community’. Thus the nym is opposed to a true name, which links together all kinds of information about the holder, making them vulnerable to someone who can obtain information that is, in the context of the transaction, irrelevant.
Or as Szabo put it: ‘As in magick, knowing a true name can confer tremendous power to one’s enemies.’
Szabo used as examples of nyms the nicknames people used on electronic bulletin boards and the brand names deployed by corporations. The purpose of the nym, in Szabo’s reading, is to aggregate and hold reputation in particular contexts: in online discussions on particular topics, or in a marketplace of niche products. But online handles and brand names are not the same things, and their elision is an early echo of the reductionism which the ideology forming around the blockchain would attempt to perform on everything it touched.
Brand names are a particular kind of untrue name, one associated not merely with reputation but also with financial value. If the brand attracts the wrong kind of attention, its reputation goes down, and so does its value – at least in theory. But because of their value (financial, not reputational), brands also bestow power on the corporations that own them – that know their real name – while often hiding behind them. Brands can sue. They can bribe. They can have activists harassed and killed. Because of their value, brands become things worth maintaining and worth defending. Their goal becomes one of survival, and they warp the world around them to that end.
Online handles are a different kind of untrue name. Their value lies precisely in the fact that they are not tied to assets, not associated with convertible value. They exist only as reputation, which has its own power, but a very different kind. They can be picked up and put down at any time without cost. The key attribute of online handles is not that they render one free through rendering one anonymous, but that they render one free through the possibility of change.
It is precisely this distinction, between financial freedoms and individual autonomy, that underlies many of the debates that have emerged around bitcoin in recent years, as it struggles to articulate a political vision that is not immured in a technological one. While bitcoin has proved to be a powerful application for the idea of the blockchain, it has also distorted in the minds of both its practitioners and many observers what the blockchain might actually be capable of.
In many of its practical applications, bitcoin has so far failed to deliver on its emancipatory promises. For example, one strand of bitcoin thinking is premised on its accessibility: the widely touted aim of ‘banking the unbanked’ claims that the technology will give access to financial services to the full half of the world who are currently excluded from real market participation. And yet the reality of bitcoin’s implementation, both technological and socio-political, makes this claim hard to justify.
To use the currency effectively still requires a level of technological proficiency and autonomy, specifically network access and expensive hardware, which put up as many barriers to access as the traditional banking system. Regulatory institutions in the form of existing financial institutions, national governments and transnational laws regarding money-laundering and taxation form another barrier to adoption, meaning that to use bitcoin is either to step far outside the law, into the wild west of narcotics, credit card fraud and the oft-fabled assassination markets, or to participate legally, handing over one’s actual ID to brokers and thus linking oneself to transactions in a way that undermines the entire point of an anonymous, cryptographically secure system.
What is blockchain for?
Even if Bitcoin can’t emancipate everyone, it might at least do less harm than current systems. Yet in the last couple of years, bitcoin has made as many headlines for its environmental impact as for its political power.
The value of bitcoin supposedly comes from the computational work required to mine it, but it might more accurately be said that it derives from a more traditional type of mining: the vast consumption and combustion of cheap Chinese coal.
It’s become terrifyingly clear that the ‘mining’ of bitcoin is an inescapably wasteful process. Vast amounts of computational energy, consuming vast quantities of electricity, and outgassing vast quantities of heat and carbon dioxide, are devoted to solving complex equations in return for money. The total power consumption of the network exceeds that of a small country – 42TWh in 2016, equivalent to a million transatlantic flights – and continues to grow.
Bitcoin mining facility, from CoinDesk archives
As the value of bitcoin rises, mining becomes more and more profitable, and the incentive to consume ever more energy increases. This, too, is surely in opposition to any claim to belong to the future, even if one is to take into account the utter devastation imposed upon the earth by our current systems of government and finance.
These complaints, which are both uncomfortably true in the present and addressable in time by adjustments to the underlying system, mask the larger unsolved problem posed by the blockchain: what is it really for? Somewhere between the establishment of the Cypherpunk mailing list and the unveiling of the first bitcoin exchange, a strange shift, even a forgetting, occurred in the development of the technology.
What had started out as a wild experiment in autonomous self-government became an exercise in wealth creation for a small coterie of tech-savvy enthusiasts and those insightful early adopters willing to take a risk on an entirely untested new technology. While bitcoin is largely to blame for this, by putting all of the potential of a truly distributed, anonymous network in the service of the market, to focus purely on this aspect of its unfolding is to ignore the potential that remains latent in Satoshi’s invention and example. It is to ignore the opportunity, rare in our time, to transform something conceived as a weapon into its opposite.
The arguments over the use of wartime weapons in a time of relative peace, made explicit in the Crypto Wars, have a clear analogue: nuclear technology. While the Allies’ desire for global dominance through atomic power was scuppered by Soviet espionage before it began, and the world settled into a Cold War backed by the horrifying possibility of mutually assured destruction, the nuclear powers agreed on one thing: if ever these weapons were to fall into the hands of non-state actors, the results would destroy not merely the social order, but life itself.
Similar arguments were made, at the end of the 20th century, about certain algorithms: the wide availability of cryptography would render toothless the apparatuses of state security and lead to the collapse of ordered society. While it’s easy to scoff now at the idea that the availability of certain complex mathematical processes would bring down governments, we are nevertheless faced with a different, more insidious, threat in the present: that of the substitution of one form of oppressive government with another.
While Tim May, part of the original Cypherpunk triumvirate, attested in The Crypto Anarchist Manifesto that assassination and extortion markets were ‘abhorrent’, he had little time for those who weren’t part of the crypto utopia. In the sprawling Cyphernomicon, a wider exploration of crypto anarchy posted to the Cypherpunks mailing list, May was far clearer on the world he foresaw: ‘Crypto anarchy means prosperity for those who can grab it, those competent enough to have something of value to offer for sale; the clueless 95 percent will suffer, but that is only just.
With crypto anarchy, we can painlessly, without initiation of aggression, dispose of the nonproductive, the halt and the lame.
Lessons from the Atomic Age
Make no mistake: the possibility of cryptographically-enforced fascism is very real indeed.
A future where every transaction, financial or social, public or private, is irrevocably encoded in a public ledger which is utterly transparent to those in power is the very opposite of a democratic, egalitarian crypto utopia. Rather, it is the reinstatement of the divine right of kings, transposed to an elevated elite class where those with the money, whether they be state actors, central bankers, winner-takes-all libertarians or property-absolutist anarcho-capitalists, have total power over those who do not.
And yet, as in the nuclear age, there remains space for other imaginaries.
In the 1960s, in the name of the ‘friendly atom’, the United States instituted a series of test programs to ascertain whether the awesome power of the atomic bomb could be turned to peaceful ends. Their proposals, some of which were actually carried out, included the excavation of vast reservoirs for drinking water, the exploitation of shale gas (an extreme form of contemporary fracking) and the construction of new roadways. Another idea involved interstellar travel, using the intermittent displacement of atomic bombs in the trail of spacecraft to propel them to distant stars.
The former programme was given the name Project Plowshare, in reference to the Prophet Isaiah’s injunction to beat swords into plowshares. Long after the cancellation of the project in the face of keen public opposition, the name was taken up by the Plowshares movement, an anti-nuclear weapons and Christian pacifist organization that became well-known for direct action against nuclear facilities.
Meanwhile, ‘peaceful’ nuclear energy became a mainstay of everyday life, in the form of the greenest, if most deeply controversial, large-scale energy generation technology we possess. Its outputs, in the form of toxic, radioactive waste, became in turn a source of new contestations over the roles and responsibilities we have to one another, and to the environment.
There is no separation of our technology from the world. Bitcoin, in the decade since Satoshi Nakamoto first announced it, has succeeded technologically but failed politically, because we have failed to understand a central tenet, long established in political theory, that free markets do not create free people – only, and only occasionally, the other way round. A technology developed according to the founding principles of true anarchism – No Gods, No Masters – has already been suborned by capital, because of a lack of imagination and education, and a failure to organize ourselves in the service of true liberation, rather than personal enrichment. This is not a problem of technology, or technological understanding, but of politics.
Bitcoin’s touted environmental offenses are not a rogue emergent effect, nor the hubristic yet predictable outcome of techno-utopianism. Rather, they are a result of failing to grapple with the central problem of human relations, long diagnosed but rarely put to the test in such dramatic fashion: how to work together in the light of radical equality without falling back into the domination of the rich over the poor, the strong over the weak.
But the emergence of that particular offense at this particular time should chime with our position in history. The problem of taking effective global action in leaderless networks is not a problem confined to bitcoin; in the face of global climate change, it is the primary problem facing humanity today. Like language, the printed word, steam, nuclear power and the internet, another miraculous savior technology is revealed to be a timely question asked directly to our capacity for change.
At the time of writing, and despite the best, the worst, the most unconsidered and the most deliberate intentions of its progenitors, the blockchain is primarily being used to drive the creation of a new class of monopolists, to securitise existing asset structures, to produce carbon dioxide and to set in stone a regime of surveillance and control unprecedented in the dreams of autocrats.
And yet, and yet.
The problem created by blockchain, and dramatized by bitcoin, is fundamentally inseparable from the political situation it emerged from: the eternal battle between power structures and individual rights. The solution to this problem is not to be found in the technology alone, but in radically different political imaginaries. A word often heard in the corridors of the new blockchain industry seems to encapsulate the inherent contradictions of a cryptologically ordered future; that word is ‘trustless’. The concept of trustlessness is at the heart of a vision which seeks to escape from established systems of power by making each individual sovereign to themselves, cryptographically secured, anonymous, untraceable and thus ungovernable.
Yet lack of government is but one plank in the construction of freedom: commonality, community and mutual support are equally, if not more, important. This is demonstrated, ultimately, even in the market: as David Graeber has put it, ‘the value of a unit of currency is not the measure of the value of an object, but the measure of one’s trust in other human beings’.
Blockchain, whatever products it might engender in the short term, poses a necessary problem that we should seek to answer not through technological fixes and traditional political forms but through the participation of the widest and most diverse public possible, and the creation of new forms of political relationships between one another.
Bitcoin image via CoinDesk archives
#crypto #cryptocurrency #btc #xrp #litecoin #altcoin #money #currency #finance #news #alts #hodl #coindesk #cointelegraph #dollar #bitcoin View the website
New Post has been published here https://is.gd/65lHi1
0 notes
Text
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
James Bridle is a writer working across technologies and disciplines and author of “The New Dark Age: Technology and the End of the Future.” His work can be found at http://jamesbridle.com. The following work will appear as an introduction to “The White Paper by Satoshi Nakamoto” to be published by Ignota Books.
For more on bitcoin’s 10th anniversary, check out our new interactive feature Bitcoin At 10.
————-
It’s difficult to know when humans first started securing or ‘encrypting’ messages to hide them from unwanted readers; the practice must, by human nature, be almost as old as written language, although examples are sparse. We know, for example, that Julius Caesar used a simple form of letter substitution to communicate with his generals, shifting each character three steps down the alphabet in order to scramble it.
The ancient Greeks, particularly the military-minded Spartans, used a device called a scytale, which allowed a hidden text to be read by wrapping a strip of parchment around a cylinder of a particular size so that the letters lined up in a particular order. Tales of the Greco-Persian Wars are full of secret messages, not least the story of Histiaeus, a commander who, according to Herodotus, shaved the head of his favorite slave and had it tattooed with a message urging revolution in the city of Miletus.
When the slave’s hair grew back he was dispatched to the city, with the instructions that the recipient should shave him once again and read the message there revealed.
Such extreme measures were taken due to the fear of government surveillance, a justification often cited today. The Persian king controlled the roadways, and had the power to examine any message – and messenger – that travelled on them. From the very beginning, cryptography has been both a military technology and a tool for undermining existing powers.
Cryptography’s value as a military tool is double-edged, of course.
Like other weapons, its effectiveness depends on the ability of one side to outgun the other. For a long time, this balance mostly held, with efforts by one side to crack the secrets of the other forming long-running and fascinating backstories to many conventional conflicts. It was an act of decryption that brought the United States into the First World War when British intelligence services decoded the infamous Zimmermann Telegram proposing an alliance between Germany and Mexico.
In the closing months of the war, the cracking of Germany’s ADFGVX cipher by French cryptanalysts enabled the Allies to stave off a final German offensive on Paris.
Cryptography was first mass-manufactured in the Second World War, in the form of the Third Reich’s Enigma machines, and then digitized in the form of the Colossus, the world’s first programmable electronic computer, developed to break the German military’s Lorenz cipher. The wild invention and ultimate success of the Bletchley codebreakers over their Nazi adversaries can be read as the first of many instances of the digital overcoming the physical; the Lorenz SZ42 was a massive, complex machine of rotating cogs and wheels which defied codebreakers for years.
By the end of the war, it was completely readable by an electronic machine. The secrecy around the Colossus itself meant that its existence had little influence on future computer design, but it marks the point at which cryptography changed radically in nature – because what is digital is ultimately distributable, although it would take the growth of the internet in the 1990s for this to become widely understood.
In 1991, a computer security researcher called Phil Zimmermann created a programme called Pretty Good Privacy (PGP), which enabled users of home computers to strongly encrypt email messages using a combination of numerous well-known algorithms. What turned PGP from another homemade software product into one of the most contentious artifacts of the decade wasn’t how it was made, but how it was distributed. Since the Second World War, nations had been forced to legally define cryptography as a weapon; like any other munition, cryptography was subject to something called the Arms Export Control Act.
At the time of PGP’s release, any cryptosystem which used keys – the strings of randomly generated numbers which secured hidden messages – longer than 40 bits required a licence for export.
PGP used keys which were 128 bits long and almost impossible to crack at the time, and this made it precisely the kind of technology that US authorities wanted to prevent falling into foreign hands. Zimmermann never intended to export PGP, but, fearing that it would be banned outright, he started distributing it to friends, saying, “I wanted to strengthen democracy, to ensure that Americans could continue to protect their privacy.”
Shortly after that, PGP found its way onto the internet and then abroad. In 1993, the US government started a formal investigation into Zimmermann – for exporting munitions without a license. As knowledge of the case spread, it became a flashpoint for early digital activists who insisted on the rights of everyone to protect their own secrets and their own private lives.
The freedoms and dangers of code became the subject of earnest debate, and in another foreshadowing of future digital style, of hacks, pranks and stunts. Zimmermann had the software’s source code printed as a hardback book, allowing anyone to purchase a copy and type up the software themselves.
As he was fond of pointing out, export of products commonly considered munitions – bombs, guns and planes – could be restricted, but books were protected by the First Amendment. Variants on the RSA algorithm – the 128-bit process at the heart of PGP – were printed on T-shirts bearing the message ‘This shirt is classified as a munition’. Some went further, having lines of code tattooed onto their arms and chests.
The crypto wars
The Crypto Wars, as they became known, galvanized a community around the notion of personal – rather than national – security, which tied into the utopian imagination of a new, more free, more equal and more just society developing in cyberspace.
Another development that prompted widespread public disquiet was the US government’s proposal for a chipset for mobile phones. The Clipper chip was designed by the NSA to provide encryption for users while allowing law enforcement to eavesdrop on communications – a situation that was ripe for abuse, either by corrupt officials or by skilled hackers.
Clipper chip via Wikimedia.
The idea that a government would deliberately weaken the protections available to its citizens made for an even more powerful and accessible argument for the individualists than the attack on PGP. By the late 1990s, Clipper was dead – and so was the case against Zimmermann. The hackers and privacy activists declared victory in the Crypto Wars.
Yet what’s often regarded as a victory for everyone against government overreach can also be read as a moment of terrifying breach: when the state’s most powerful weapons escaped government control and fell into the hands of anyone who wanted to use them. Today, thanks to the rise in digital communications, cryptography is everywhere, not least in banking systems, protecting the billions of electronic transactions that flow around the planet every day.
Even more than in the 1990s, the idea that anyone would deliberately make it easier for someone to steal money seems like an attack on the basic functions of society, and so it should come as no surprise that it’s a technology best known for – but by no means limited to – the distribution of currency that should be the focus of a new outbreak of the Crypto Wars, as well as the full flood of individualist, utopian thinking that accompanied the first round. There’s something about money that focuses the mind.
When Marco Polo first encountered paper money on his travels to China in the 13th century, he was astounded. In his Book of the Marvels of the World, he spends a great length of time explaining, and wondering at, the monetary system established by the Great Khan. Until recently, and as was still the case in Europe, the Chinese had used a range of value-bearing commodities to settle commerce and taxation: copper ingots, iron bars, gold coins, pearls, salt and the like.
In 1260, Kublai Khan decreed that instead, his subjects would use apparently valueless paper, printed and certified by a central mint, and, writes Polo, “the way it is wrought is such that you might say he has the secret of alchemy in perfection, and you would be right.” Through a carefully choreographed process of manufacture, design and official imprimatur, “all these pieces of paper are issued with as much solemnity and authority as if they were of pure gold or silver.”
The process was alchemical in the truest sense, as it did not merely transform material, but also elevated the Khan himself to even more unassailable heights of power: the only arbiter of finance. Those who refused to accept the new currency were punished with death, and all trade flowed through the state’s coffers. Like the Persian king before him, the Khan had realized that controlling traffic – in commerce and in information – was the way to situate oneself at the true heart of power.
True magic
The processing and accounting of money – fiat money, created by decree rather than having inherent value – is essentially the manipulation of symbols, and the gradual but ever-accelerating authority of capitalism, money’s belief system, tracks the development of symbol-manipulating technologies, from the double-entry bookkeeping of the European Renaissance to the development of databases and planet-spanning electronic networks; from physical technologies to virtual ones.
Money also involves the magical transformation of symbols into value. It requires belief to operate.
Around such belief systems other beliefs tend to gather, and the industrial quantities of belief required to breathe life into new systems of value tends to gives succor to any number of outlandish ideas, whether these be the divine right of kings, the supremacy of the nation state or the inviolable will of technology itself.
Money, then, is a belief system backed by state infrastructure which, for a long time, assured centralized power. But as computational technologies, long the sole province of the state, became less about asserting government power than asserting individual freedom – in other words, as the weapons forged in the crucible of the Second World War became increasingly available to the common citizen – it became clear to the veterans of the Crypto Wars how they might make other adjustments to ancient power dynamics.
The idea for digital money and virtual currencies had been floating around for some time before the Crypto Wars. Money has been
tending towards the virtual for some time, from the first ATMs and cards in the 1960s, to the spread of digital networks and connections between retailers and banks in the 1980s and 1990s. For anyone with a little technological foresight, it was easy to see which direction we were heading in.
For those concerned with privacy and individual sovereignty, it was a worrying development.
The first ATM via TIME
Digital money, significantly, has none of the advantages of cash; it can’t be stored and exchanged outside of the system of banks and third parties, such as credit card companies, which can regulate and impede its flow. To a cryptographer, or anyone who has imbibed cryptography’s lessons on the potential to separate oneself from overbearing powers, this arrangement looks like a kind of enslavement. So what would digital cash actually look like?
The first quality of digital cash is that it needs to be private, in the sense that no one other than the spender and receiver should be party to the transaction: no bank or security agency should know who is spending the money, who is receiving it, what it is for or at what time and place the exchange is taking place. Because no physical assets, such as notes or coins, are being exchanged, it should also be secure. The receiver should be able to verify they were paid and the spender that they had paid – a two-way receipt for the transaction.
In this way, digital cash would have all the privacy of physical cash, with the added benefit of the participants being able to prove that a transaction had actually taken place.
The opening shot
One of the earliest proponents of digital cash was an American computer scientist called David Chaum.
Chaum believed that both the privacy and the security problems of digital currencies could be solved by using cryptography: encoding messages between the two parties, the sender and the receiver, in such a way that nobody else can read them. Chaum’s solution to this problem involved both parties digitally signing the transaction with a private key, akin to an unforgeable and unguessable digital signature. In this way, both parties validate the transaction. In addition, they communicate through encrypted channels, so that nobody else can see that the transaction has taken place.
Chaum’s system worked, and was implemented by a number of companies and even one bank, but it never took off.
Chaum’s own company, DigiCash, went bankrupt in 1998 and there was little incentive to compete against the growing power of credit card companies. Chaum felt that people didn’t understand what they were losing as digital networks and the money that flowed across them became more centralized: “As the web grew, the average level of sophistication of users dropped. It was hard to explain the importance of privacy to them,” he said in 1999.
David Chaum via Elixxir project.
Yet some people, including those radicalized by the Crypto Wars of the early 1990s, did understand the value of privacy.
A group which came to be known as the Cypherpunks gathered first in San Francisco, and then online, with the intent of picking up from Chaum’s work the tools that could be used to disempower governments. From the very beginning, Chaum’s ideas about privacy and security had been tied to ideas about society and the way it was being changed by digitization.
“Computerisation is robbing individuals of the ability to monitor and control the ways information about them is used,” he wrote in 1985, foreseeing a Big Brother-like “dossier society” where everything was known about individuals but individuals knew little about the information held over them.
Yet Chaum was forced to partner with existing institutions to get DigiCash of the ground – and this was very far from the Cypherpunk dream. Eric Hughes, a Berkeley mathematician and one of the original Cypherpunks group, published ‘A Cypherpunk’s Manifesto’ in 1993, arguing that privacy was a requirement for an open society, and privacy on electronic networks could only be achieved through the use of cryptography.
Tim May, another member of the group and a former chief scientist at Intel, went further in the The Crypto Anarchist Manifesto:
“The State will, of course, try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be traded freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions.”
Throughout the 1990s and into the 2000s, the Cypherpunks elaborated on the principles that would bring their utopia of encryption into being, as well as the technical innovations required to make digital currency possible.
One of the biggest hurdles to doing so was the double-spending problem. Physical cash can only be spent once; when a banknote is handed over to a merchant, the buyer can’t at the same time use the same note at another shop around the corner. Virtual currencies face the problem that while encryption can guarantee that this specific piece of data is a form of money belonging to this specific person, it can’t say whether that data has been copied and is also in circulation elsewhere.
In other words, it can’t say whether or not someone is trying to spend the same coin twice at the same time. The need to have a central register to check each transaction was what forced David Chaum to partner with banks.
This necessitated routing all electronic transactions through credit card companies, and re-introduce dthe Cypherpunks’ worst enemies: loss of privacy and the need to trusts some hierarchical organization, a government, bank or corporation, with the authority to verify and, if necessary, roll back transactions.
The blockchain
The solution to the double-spending problem appeared quite suddenly in October 2008, with the publication of a paper on the The Cryptography Mailing List entitled “Bitcoin: “A Peer-to-Peer Electronic Cash System.” Citing several forerunners in the field, the author of the paper, the previously unknown Satoshi Nakamoto, proposed one key innovation which solved the double-spending problem while preserving anonymity and preventing the need for trusting third parties.
This was called the ‘blockchain’: a distributed ledger, or record of transactions, which would be maintained by everyone participating in the system. It’s called the blockchain because groups of transactions are gathered together into ‘blocks’ as they occur, and as each block is turned out it is added to the ‘chain’ of all transactions. That’s it. It’s simply a list of things that happened.
If everyone can see every transaction, then there is no need to hand over control to banks or governments, and if everyone follows the encryption practices of the Cypherpunks, there is no way to know who is spending the money.
Of course, if everyone has a copy of this ledger, we need to know it hasn’t been forged or tampered with in any way. So in order to extend the blockchain, in other words to write in the ledger, a certain amount of computational ‘work’ has to be done: the computer doing the writing has to solve a particularly complex mathematical problem.
Bloomberg Magazine, 2015
The fact that it’s relatively easy for everyone else’s computers to check if this problem really was solved makes it very difficult – in fact, practically impossible – for anyone to create a fake version of the ledger. In a particularly clever twist, participants are incentivized to help maintain the ledger by receiving a small number of bitcoins when they do solve the mathematical problem. This is where the notional value of Bitcoin comes from: someone has to put in an amount of time and energy to produce it, which is why this process is known as ‘mining’.
Over time, more and more coins are produced, to an eventual total of 21 million sometime in or around 2140. Satoshi’s paper had the good fortune to appear at a particular time. Encoded into the very first block on the Bitcoin chain is a timestamp, the kind of timestamp more familiar from ransom demands: a proof of life.
The phrase embedded forever into the beginning of the blockchain is ‘The Times 03/Jan/2009 Chancellor on brink of second bailout for banks,’ a reference to the front page headline of The Times newspaper on that date.
On one level, it’s a simple proof that no valid coins were mined before that date. On another, it’s an ironic comment on the state of the standard economic system that bitcoin set out to replace. It’s also, for those fascinated by such things, one of the earliest clues to the identity of Satoshi Nakamoto. Satoshi Nakamoto appeared in the world, as far as anyone is aware, with the publication of the Bitcoin white paper. There is no trace of the name before that date, and after a few months of interacting with other developers on the project, Satoshi Nakamoto disappeared just as abruptly from public view at the end of 2010.
With the exception of a couple of private emails (indicating that the developer had ‘moved onto other things’), and a forum post disavowing an attempt to ‘out’ the developer in 2014, Satoshi Nakamoto has not been heard from since. Perhaps instead, more accurately, we might say that the entity referring to itself as Satoshi Nakamoto has not been heard from since 2010.
For less interesting than the ‘real’ identity of Satoshi is the way in which that identity operates in the world – in a way that perfectly accords with Cypherpunk and blockchain doctrine.
Eating the dog food
In Section 10 of the Bitcoin white paper, Satoshi outlines the privacy model of the system. In the traditional banking model, the flow of money through an exchange is anonymized by the third party administering the transactions; they hide what they know from everyone else. However, on the blockchain, where all transactions are public, the anonymity happens between the identity and the transaction; everyone can see the money moving, but nobody knows whose money it is.
The common idea of cryptocurrencies is that they set assets free, but a cryptocurrency is a monetary unit like in any other currency system – one that, because of the blockchain, is closely monitored and controlled. What’s really liberated is identity. It is liberated from responsibility for the transaction and liberated from the ‘real’ person or persons performing it. Identity, in fact, becomes an asset itself. This is also what marks out the idea of the blockchain from earlier cryptosystems like PGP; it’s not the messages that are being hidden, but the actors behind them.
A necessary part of software development is the use of the technology in real-life situations for the purposes of testing.
This is often done by the developers themselves in a process known as ‘eating your own dog food.’ While the developers of bitcoin could test mining and transacting coins between them, the real ‘product’ of bitcoin – a decentralized, deniable identity – could only be tested by someone (or a group) willing to build and sustain such an identity asset over a long period of time – and who better to perform that test than the creator of bitcoin themselves?
Satoshi Nakomoto is an exercise in dogfooding – and proof of its efficacy.
Newsweek Magazine, 2014
When Satoshi disappeared into the ether, they left on the blockchain, unspent, the piles of bitcoins they’d personally mined in the early days of the project – over a million of them. These bitcoins are still there, and only someone who holds Satoshi’s private keys can access them. Today, Satoshi ‘exists’ only to the extent someone can prove to be that individual – the only proof of which is possession of those private keys. There is no ‘real’ Satoshi.
There is only a set of assets and a key. ‘Satoshi Nakamoto’ is creator, product and proof of bitcoin, all wrapped up in one.
Once again, the creation of money is the creation of a myth. In his book “Debt: The First 5,000 Years,” the anthropologist David Graeber proposes that the connection between finance and sacrifice runs deep in Western culture: ‘Why, for instance, do we refer to Christ as the ‘redeemer’? The primary meaning of ‘redemption’ is to buy something back, or to recover something that had been given up in security for a loan; to acquire something by paying of a debt. It is rather striking to think that the very core of the Christian message, salvation itself, the sacrifice of God’s own son to rescue humanity from eternal damnation, should be framed in the language of a financial transaction.’
Satoshi’s sacrifice is something different, but in the anarchic frame from which the individual emerged, not dissimilar. In order to secure the future of bitcoin, Satoshi gave up all personal gains from its invention: some 980,000 bitcoins, valued at $4 billion in late 2018. This is a gesture that will continue to inspire many in the bitcoin community, even if few of them understand or even consider its true meaning.
The power of brands
Back in 1995, another regular Cypherpunk contributor, Nick Szabo, proposed a term for the kind of sacrificial identity deployed so successfully by Satoshi: a ‘nym’. A nym was defined as ‘an identifier that links only a small amount of related information about a person, usually that information deemed by the nym holder to be relevant to a particular organization or community’. Thus the nym is opposed to a true name, which links together all kinds of information about the holder, making them vulnerable to someone who can obtain information that is, in the context of the transaction, irrelevant.
Or as Szabo put it: ‘As in magick, knowing a true name can confer tremendous power to one’s enemies.’
Szabo used as examples of nyms the nicknames people used on electronic bulletin boards and the brand names deployed by corporations. The purpose of the nym, in Szabo’s reading, is to aggregate and hold reputation in particular contexts: in online discussions on particular topics, or in a marketplace of niche products. But online handles and brand names are not the same things, and their elision is an early echo of the reductionism which the ideology forming around the blockchain would attempt to perform on everything it touched.
Brand names are a particular kind of untrue name, one associated not merely with reputation but also with financial value. If the brand attracts the wrong kind of attention, its reputation goes down, and so does its value – at least in theory. But because of their value (financial, not reputational), brands also bestow power on the corporations that own them – that know their real name – while often hiding behind them. Brands can sue. They can bribe. They can have activists harassed and killed. Because of their value, brands become things worth maintaining and worth defending. Their goal becomes one of survival, and they warp the world around them to that end.
Online handles are a different kind of untrue name. Their value lies precisely in the fact that they are not tied to assets, not associated with convertible value. They exist only as reputation, which has its own power, but a very different kind. They can be picked up and put down at any time without cost. The key attribute of online handles is not that they render one free through rendering one anonymous, but that they render one free through the possibility of change.
It is precisely this distinction, between financial freedoms and individual autonomy, that underlies many of the debates that have emerged around bitcoin in recent years, as it struggles to articulate a political vision that is not immured in a technological one. While bitcoin has proved to be a powerful application for the idea of the blockchain, it has also distorted in the minds of both its practitioners and many observers what the blockchain might actually be capable of.
In many of its practical applications, bitcoin has so far failed to deliver on its emancipatory promises. For example, one strand of bitcoin thinking is premised on its accessibility: the widely touted aim of ‘banking the unbanked’ claims that the technology will give access to financial services to the full half of the world who are currently excluded from real market participation. And yet the reality of bitcoin’s implementation, both technological and socio-political, makes this claim hard to justify.
To use the currency effectively still requires a level of technological proficiency and autonomy, specifically network access and expensive hardware, which put up as many barriers to access as the traditional banking system. Regulatory institutions in the form of existing financial institutions, national governments and transnational laws regarding money-laundering and taxation form another barrier to adoption, meaning that to use bitcoin is either to step far outside the law, into the wild west of narcotics, credit card fraud and the oft-fabled assassination markets, or to participate legally, handing over one’s actual ID to brokers and thus linking oneself to transactions in a way that undermines the entire point of an anonymous, cryptographically secure system.
What is blockchain for?
Even if Bitcoin can’t emancipate everyone, it might at least do less harm than current systems. Yet in the last couple of years, bitcoin has made as many headlines for its environmental impact as for its political power.
The value of bitcoin supposedly comes from the computational work required to mine it, but it might more accurately be said that it derives from a more traditional type of mining: the vast consumption and combustion of cheap Chinese coal.
It’s become terrifyingly clear that the ‘mining’ of bitcoin is an inescapably wasteful process. Vast amounts of computational energy, consuming vast quantities of electricity, and outgassing vast quantities of heat and carbon dioxide, are devoted to solving complex equations in return for money. The total power consumption of the network exceeds that of a small country – 42TWh in 2016, equivalent to a million transatlantic flights – and continues to grow.
Bitcoin mining facility, from CoinDesk archives
As the value of bitcoin rises, mining becomes more and more profitable, and the incentive to consume ever more energy increases. This, too, is surely in opposition to any claim to belong to the future, even if one is to take into account the utter devastation imposed upon the earth by our current systems of government and finance.
These complaints, which are both uncomfortably true in the present and addressable in time by adjustments to the underlying system, mask the larger unsolved problem posed by the blockchain: what is it really for? Somewhere between the establishment of the Cypherpunk mailing list and the unveiling of the first bitcoin exchange, a strange shift, even a forgetting, occurred in the development of the technology.
What had started out as a wild experiment in autonomous self-government became an exercise in wealth creation for a small coterie of tech-savvy enthusiasts and those insightful early adopters willing to take a risk on an entirely untested new technology. While bitcoin is largely to blame for this, by putting all of the potential of a truly distributed, anonymous network in the service of the market, to focus purely on this aspect of its unfolding is to ignore the potential that remains latent in Satoshi’s invention and example. It is to ignore the opportunity, rare in our time, to transform something conceived as a weapon into its opposite.
The arguments over the use of wartime weapons in a time of relative peace, made explicit in the Crypto Wars, have a clear analogue: nuclear technology. While the Allies’ desire for global dominance through atomic power was scuppered by Soviet espionage before it began, and the world settled into a Cold War backed by the horrifying possibility of mutually assured destruction, the nuclear powers agreed on one thing: if ever these weapons were to fall into the hands of non-state actors, the results would destroy not merely the social order, but life itself.
Similar arguments were made, at the end of the 20th century, about certain algorithms: the wide availability of cryptography would render toothless the apparatuses of state security and lead to the collapse of ordered society. While it’s easy to scoff now at the idea that the availability of certain complex mathematical processes would bring down governments, we are nevertheless faced with a different, more insidious, threat in the present: that of the substitution of one form of oppressive government with another.
While Tim May, part of the original Cypherpunk triumvirate, attested in The Crypto Anarchist Manifesto that assassination and extortion markets were ‘abhorrent’, he had little time for those who weren’t part of the crypto utopia. In the sprawling Cyphernomicon, a wider exploration of crypto anarchy posted to the Cypherpunks mailing list, May was far clearer on the world he foresaw: ‘Crypto anarchy means prosperity for those who can grab it, those competent enough to have something of value to offer for sale; the clueless 95 percent will suffer, but that is only just.
With crypto anarchy, we can painlessly, without initiation of aggression, dispose of the nonproductive, the halt and the lame.
Lessons from the Atomic Age
Make no mistake: the possibility of cryptographically-enforced fascism is very real indeed.
A future where every transaction, financial or social, public or private, is irrevocably encoded in a public ledger which is utterly transparent to those in power is the very opposite of a democratic, egalitarian crypto utopia. Rather, it is the reinstatement of the divine right of kings, transposed to an elevated elite class where those with the money, whether they be state actors, central bankers, winner-takes-all libertarians or property-absolutist anarcho-capitalists, have total power over those who do not.
And yet, as in the nuclear age, there remains space for other imaginaries.
In the 1960s, in the name of the ‘friendly atom’, the United States instituted a series of test programs to ascertain whether the awesome power of the atomic bomb could be turned to peaceful ends. Their proposals, some of which were actually carried out, included the excavation of vast reservoirs for drinking water, the exploitation of shale gas (an extreme form of contemporary fracking) and the construction of new roadways. Another idea involved interstellar travel, using the intermittent displacement of atomic bombs in the trail of spacecraft to propel them to distant stars.
The former programme was given the name Project Plowshare, in reference to the Prophet Isaiah’s injunction to beat swords into plowshares. Long after the cancellation of the project in the face of keen public opposition, the name was taken up by the Plowshares movement, an anti-nuclear weapons and Christian pacifist organization that became well-known for direct action against nuclear facilities.
Meanwhile, ‘peaceful’ nuclear energy became a mainstay of everyday life, in the form of the greenest, if most deeply controversial, large-scale energy generation technology we possess. Its outputs, in the form of toxic, radioactive waste, became in turn a source of new contestations over the roles and responsibilities we have to one another, and to the environment.
There is no separation of our technology from the world. Bitcoin, in the decade since Satoshi Nakamoto first announced it, has succeeded technologically but failed politically, because we have failed to understand a central tenet, long established in political theory, that free markets do not create free people – only, and only occasionally, the other way round. A technology developed according to the founding principles of true anarchism – No Gods, No Masters – has already been suborned by capital, because of a lack of imagination and education, and a failure to organize ourselves in the service of true liberation, rather than personal enrichment. This is not a problem of technology, or technological understanding, but of politics.
Bitcoin’s touted environmental offenses are not a rogue emergent effect, nor the hubristic yet predictable outcome of techno-utopianism. Rather, they are a result of failing to grapple with the central problem of human relations, long diagnosed but rarely put to the test in such dramatic fashion: how to work together in the light of radical equality without falling back into the domination of the rich over the poor, the strong over the weak.
But the emergence of that particular offense at this particular time should chime with our position in history. The problem of taking effective global action in leaderless networks is not a problem confined to bitcoin; in the face of global climate change, it is the primary problem facing humanity today. Like language, the printed word, steam, nuclear power and the internet, another miraculous savior technology is revealed to be a timely question asked directly to our capacity for change.
At the time of writing, and despite the best, the worst, the most unconsidered and the most deliberate intentions of its progenitors, the blockchain is primarily being used to drive the creation of a new class of monopolists, to securitise existing asset structures, to produce carbon dioxide and to set in stone a regime of surveillance and control unprecedented in the dreams of autocrats.
And yet, and yet.
The problem created by blockchain, and dramatized by bitcoin, is fundamentally inseparable from the political situation it emerged from: the eternal battle between power structures and individual rights. The solution to this problem is not to be found in the technology alone, but in radically different political imaginaries. A word often heard in the corridors of the new blockchain industry seems to encapsulate the inherent contradictions of a cryptologically ordered future; that word is ‘trustless’. The concept of trustlessness is at the heart of a vision which seeks to escape from established systems of power by making each individual sovereign to themselves, cryptographically secured, anonymous, untraceable and thus ungovernable.
Yet lack of government is but one plank in the construction of freedom: commonality, community and mutual support are equally, if not more, important. This is demonstrated, ultimately, even in the market: as David Graeber has put it, ‘the value of a unit of currency is not the measure of the value of an object, but the measure of one’s trust in other human beings’.
Blockchain, whatever products it might engender in the short term, poses a necessary problem that we should seek to answer not through technological fixes and traditional political forms but through the participation of the widest and most diverse public possible, and the creation of new forms of political relationships between one another.
Bitcoin image via CoinDesk archives
!function(f,b,e,v,n,t,s){if(f.fbq)return;n=f.fbq=function(){n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments)};if(!f._fbq)f._fbq=n; n.push=n;n.loaded=!0;n.version='2.0';n.queue=[];t=b.createElement(e);t.async=!0; t.src=v;s=b.getElementsByTagName(e)[0];s.parentNode.insertBefore(t,s)}(window, document,'script','//connect.facebook.net/en_US/fbevents.js'); fbq('init', '239547076708948'); fbq('track', "PageView");
This news post is collected from CoinDesk
Recommended Read
Editor choice
BinBot Pro – Safest & Highly Recommended Binary Options Auto Trading Robot
Do you live in a country like USA or Canada where using automated trading systems is a problem? If you do then now we ...
9.5
Demo & Pro Version Try It Now
Read full review
The post Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure appeared first on Click 2 Watch.
More Details Here → https://click2.watch/free-markets-dont-create-free-people-bitcoins-tech-success-masks-its-failure-7
0 notes
Text
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
James Bridle is a writer working across technologies and disciplines and author of “The New Dark Age: Technology and the End of the Future.” His work can be found at http://jamesbridle.com. The following work will appear as an introduction to “The White Paper by Satoshi Nakamoto” to be published by Ignota Books.
For more on bitcoin’s 10th anniversary, check out our new interactive feature Bitcoin At 10.
————-
It’s difficult to know when humans first started securing or ‘encrypting’ messages to hide them from unwanted readers; the practice must, by human nature, be almost as old as written language, although examples are sparse. We know, for example, that Julius Caesar used a simple form of letter substitution to communicate with his generals, shifting each character three steps down the alphabet in order to scramble it.
The ancient Greeks, particularly the military-minded Spartans, used a device called a scytale, which allowed a hidden text to be read by wrapping a strip of parchment around a cylinder of a particular size so that the letters lined up in a particular order. Tales of the Greco-Persian Wars are full of secret messages, not least the story of Histiaeus, a commander who, according to Herodotus, shaved the head of his favorite slave and had it tattooed with a message urging revolution in the city of Miletus.
When the slave’s hair grew back he was dispatched to the city, with the instructions that the recipient should shave him once again and read the message there revealed.
Such extreme measures were taken due to the fear of government surveillance, a justification often cited today. The Persian king controlled the roadways, and had the power to examine any message – and messenger – that travelled on them. From the very beginning, cryptography has been both a military technology and a tool for undermining existing powers.
Cryptography’s value as a military tool is double-edged, of course.
Like other weapons, its effectiveness depends on the ability of one side to outgun the other. For a long time, this balance mostly held, with efforts by one side to crack the secrets of the other forming long-running and fascinating backstories to many conventional conflicts. It was an act of decryption that brought the United States into the First World War when British intelligence services decoded the infamous Zimmermann Telegram proposing an alliance between Germany and Mexico.
In the closing months of the war, the cracking of Germany’s ADFGVX cipher by French cryptanalysts enabled the Allies to stave off a final German offensive on Paris.
Cryptography was first mass-manufactured in the Second World War, in the form of the Third Reich’s Enigma machines, and then digitized in the form of the Colossus, the world’s first programmable electronic computer, developed to break the German military’s Lorenz cipher. The wild invention and ultimate success of the Bletchley codebreakers over their Nazi adversaries can be read as the first of many instances of the digital overcoming the physical; the Lorenz SZ42 was a massive, complex machine of rotating cogs and wheels which defied codebreakers for years.
By the end of the war, it was completely readable by an electronic machine. The secrecy around the Colossus itself meant that its existence had little influence on future computer design, but it marks the point at which cryptography changed radically in nature – because what is digital is ultimately distributable, although it would take the growth of the internet in the 1990s for this to become widely understood.
In 1991, a computer security researcher called Phil Zimmermann created a programme called Pretty Good Privacy (PGP), which enabled users of home computers to strongly encrypt email messages using a combination of numerous well-known algorithms. What turned PGP from another homemade software product into one of the most contentious artifacts of the decade wasn’t how it was made, but how it was distributed. Since the Second World War, nations had been forced to legally define cryptography as a weapon; like any other munition, cryptography was subject to something called the Arms Export Control Act.
At the time of PGP’s release, any cryptosystem which used keys – the strings of randomly generated numbers which secured hidden messages – longer than 40 bits required a licence for export.
PGP used keys which were 128 bits long and almost impossible to crack at the time, and this made it precisely the kind of technology that US authorities wanted to prevent falling into foreign hands. Zimmermann never intended to export PGP, but, fearing that it would be banned outright, he started distributing it to friends, saying, “I wanted to strengthen democracy, to ensure that Americans could continue to protect their privacy.”
Shortly after that, PGP found its way onto the internet and then abroad. In 1993, the US government started a formal investigation into Zimmermann – for exporting munitions without a license. As knowledge of the case spread, it became a flashpoint for early digital activists who insisted on the rights of everyone to protect their own secrets and their own private lives.
The freedoms and dangers of code became the subject of earnest debate, and in another foreshadowing of future digital style, of hacks, pranks and stunts. Zimmermann had the software’s source code printed as a hardback book, allowing anyone to purchase a copy and type up the software themselves.
As he was fond of pointing out, export of products commonly considered munitions – bombs, guns and planes – could be restricted, but books were protected by the First Amendment. Variants on the RSA algorithm – the 128-bit process at the heart of PGP – were printed on T-shirts bearing the message ‘This shirt is classified as a munition’. Some went further, having lines of code tattooed onto their arms and chests.
The crypto wars
The Crypto Wars, as they became known, galvanized a community around the notion of personal – rather than national – security, which tied into the utopian imagination of a new, more free, more equal and more just society developing in cyberspace.
Another development that prompted widespread public disquiet was the US government’s proposal for a chipset for mobile phones. The Clipper chip was designed by the NSA to provide encryption for users while allowing law enforcement to eavesdrop on communications – a situation that was ripe for abuse, either by corrupt officials or by skilled hackers.
Clipper chip via Wikimedia.
The idea that a government would deliberately weaken the protections available to its citizens made for an even more powerful and accessible argument for the individualists than the attack on PGP. By the late 1990s, Clipper was dead – and so was the case against Zimmermann. The hackers and privacy activists declared victory in the Crypto Wars.
Yet what’s often regarded as a victory for everyone against government overreach can also be read as a moment of terrifying breach: when the state’s most powerful weapons escaped government control and fell into the hands of anyone who wanted to use them. Today, thanks to the rise in digital communications, cryptography is everywhere, not least in banking systems, protecting the billions of electronic transactions that flow around the planet every day.
Even more than in the 1990s, the idea that anyone would deliberately make it easier for someone to steal money seems like an attack on the basic functions of society, and so it should come as no surprise that it’s a technology best known for – but by no means limited to – the distribution of currency that should be the focus of a new outbreak of the Crypto Wars, as well as the full flood of individualist, utopian thinking that accompanied the first round. There’s something about money that focuses the mind.
When Marco Polo first encountered paper money on his travels to China in the 13th century, he was astounded. In his Book of the Marvels of the World, he spends a great length of time explaining, and wondering at, the monetary system established by the Great Khan. Until recently, and as was still the case in Europe, the Chinese had used a range of value-bearing commodities to settle commerce and taxation: copper ingots, iron bars, gold coins, pearls, salt and the like.
In 1260, Kublai Khan decreed that instead, his subjects would use apparently valueless paper, printed and certified by a central mint, and, writes Polo, “the way it is wrought is such that you might say he has the secret of alchemy in perfection, and you would be right.” Through a carefully choreographed process of manufacture, design and official imprimatur, “all these pieces of paper are issued with as much solemnity and authority as if they were of pure gold or silver.”
The process was alchemical in the truest sense, as it did not merely transform material, but also elevated the Khan himself to even more unassailable heights of power: the only arbiter of finance. Those who refused to accept the new currency were punished with death, and all trade flowed through the state’s coffers. Like the Persian king before him, the Khan had realized that controlling traffic – in commerce and in information – was the way to situate oneself at the true heart of power.
True magic
The processing and accounting of money – fiat money, created by decree rather than having inherent value – is essentially the manipulation of symbols, and the gradual but ever-accelerating authority of capitalism, money’s belief system, tracks the development of symbol-manipulating technologies, from the double-entry bookkeeping of the European Renaissance to the development of databases and planet-spanning electronic networks; from physical technologies to virtual ones.
Money also involves the magical transformation of symbols into value. It requires belief to operate.
Around such belief systems other beliefs tend to gather, and the industrial quantities of belief required to breathe life into new systems of value tends to gives succor to any number of outlandish ideas, whether these be the divine right of kings, the supremacy of the nation state or the inviolable will of technology itself.
Money, then, is a belief system backed by state infrastructure which, for a long time, assured centralized power. But as computational technologies, long the sole province of the state, became less about asserting government power than asserting individual freedom – in other words, as the weapons forged in the crucible of the Second World War became increasingly available to the common citizen – it became clear to the veterans of the Crypto Wars how they might make other adjustments to ancient power dynamics.
The idea for digital money and virtual currencies had been floating around for some time before the Crypto Wars. Money has been
tending towards the virtual for some time, from the first ATMs and cards in the 1960s, to the spread of digital networks and connections between retailers and banks in the 1980s and 1990s. For anyone with a little technological foresight, it was easy to see which direction we were heading in.
For those concerned with privacy and individual sovereignty, it was a worrying development.
The first ATM via TIME
Digital money, significantly, has none of the advantages of cash; it can’t be stored and exchanged outside of the system of banks and third parties, such as credit card companies, which can regulate and impede its flow. To a cryptographer, or anyone who has imbibed cryptography’s lessons on the potential to separate oneself from overbearing powers, this arrangement looks like a kind of enslavement. So what would digital cash actually look like?
The first quality of digital cash is that it needs to be private, in the sense that no one other than the spender and receiver should be party to the transaction: no bank or security agency should know who is spending the money, who is receiving it, what it is for or at what time and place the exchange is taking place. Because no physical assets, such as notes or coins, are being exchanged, it should also be secure. The receiver should be able to verify they were paid and the spender that they had paid – a two-way receipt for the transaction.
In this way, digital cash would have all the privacy of physical cash, with the added benefit of the participants being able to prove that a transaction had actually taken place.
The opening shot
One of the earliest proponents of digital cash was an American computer scientist called David Chaum.
Chaum believed that both the privacy and the security problems of digital currencies could be solved by using cryptography: encoding messages between the two parties, the sender and the receiver, in such a way that nobody else can read them. Chaum’s solution to this problem involved both parties digitally signing the transaction with a private key, akin to an unforgeable and unguessable digital signature. In this way, both parties validate the transaction. In addition, they communicate through encrypted channels, so that nobody else can see that the transaction has taken place.
Chaum’s system worked, and was implemented by a number of companies and even one bank, but it never took off.
Chaum’s own company, DigiCash, went bankrupt in 1998 and there was little incentive to compete against the growing power of credit card companies. Chaum felt that people didn’t understand what they were losing as digital networks and the money that flowed across them became more centralized: “As the web grew, the average level of sophistication of users dropped. It was hard to explain the importance of privacy to them,” he said in 1999.
David Chaum via Elixxir project.
Yet some people, including those radicalized by the Crypto Wars of the early 1990s, did understand the value of privacy.
A group which came to be known as the Cypherpunks gathered first in San Francisco, and then online, with the intent of picking up from Chaum’s work the tools that could be used to disempower governments. From the very beginning, Chaum’s ideas about privacy and security had been tied to ideas about society and the way it was being changed by digitization.
“Computerisation is robbing individuals of the ability to monitor and control the ways information about them is used,” he wrote in 1985, foreseeing a Big Brother-like “dossier society” where everything was known about individuals but individuals knew little about the information held over them.
Yet Chaum was forced to partner with existing institutions to get DigiCash of the ground – and this was very far from the Cypherpunk dream. Eric Hughes, a Berkeley mathematician and one of the original Cypherpunks group, published ‘A Cypherpunk’s Manifesto’ in 1993, arguing that privacy was a requirement for an open society, and privacy on electronic networks could only be achieved through the use of cryptography.
Tim May, another member of the group and a former chief scientist at Intel, went further in the The Crypto Anarchist Manifesto:
“The State will, of course, try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be traded freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions.”
Throughout the 1990s and into the 2000s, the Cypherpunks elaborated on the principles that would bring their utopia of encryption into being, as well as the technical innovations required to make digital currency possible.
One of the biggest hurdles to doing so was the double-spending problem. Physical cash can only be spent once; when a banknote is handed over to a merchant, the buyer can’t at the same time use the same note at another shop around the corner. Virtual currencies face the problem that while encryption can guarantee that this specific piece of data is a form of money belonging to this specific person, it can’t say whether that data has been copied and is also in circulation elsewhere.
In other words, it can’t say whether or not someone is trying to spend the same coin twice at the same time. The need to have a central register to check each transaction was what forced David Chaum to partner with banks.
This necessitated routing all electronic transactions through credit card companies, and re-introduce dthe Cypherpunks’ worst enemies: loss of privacy and the need to trusts some hierarchical organization, a government, bank or corporation, with the authority to verify and, if necessary, roll back transactions.
The blockchain
The solution to the double-spending problem appeared quite suddenly in October 2008, with the publication of a paper on the The Cryptography Mailing List entitled “Bitcoin: “A Peer-to-Peer Electronic Cash System.” Citing several forerunners in the field, the author of the paper, the previously unknown Satoshi Nakamoto, proposed one key innovation which solved the double-spending problem while preserving anonymity and preventing the need for trusting third parties.
This was called the ‘blockchain’: a distributed ledger, or record of transactions, which would be maintained by everyone participating in the system. It’s called the blockchain because groups of transactions are gathered together into ‘blocks’ as they occur, and as each block is turned out it is added to the ‘chain’ of all transactions. That’s it. It’s simply a list of things that happened.
If everyone can see every transaction, then there is no need to hand over control to banks or governments, and if everyone follows the encryption practices of the Cypherpunks, there is no way to know who is spending the money.
Of course, if everyone has a copy of this ledger, we need to know it hasn’t been forged or tampered with in any way. So in order to extend the blockchain, in other words to write in the ledger, a certain amount of computational ‘work’ has to be done: the computer doing the writing has to solve a particularly complex mathematical problem.
Bloomberg Magazine, 2015
The fact that it’s relatively easy for everyone else’s computers to check if this problem really was solved makes it very difficult – in fact, practically impossible – for anyone to create a fake version of the ledger. In a particularly clever twist, participants are incentivized to help maintain the ledger by receiving a small number of bitcoins when they do solve the mathematical problem. This is where the notional value of Bitcoin comes from: someone has to put in an amount of time and energy to produce it, which is why this process is known as ‘mining’.
Over time, more and more coins are produced, to an eventual total of 21 million sometime in or around 2140. Satoshi’s paper had the good fortune to appear at a particular time. Encoded into the very first block on the Bitcoin chain is a timestamp, the kind of timestamp more familiar from ransom demands: a proof of life.
The phrase embedded forever into the beginning of the blockchain is ‘The Times 03/Jan/2009 Chancellor on brink of second bailout for banks,’ a reference to the front page headline of The Times newspaper on that date.
On one level, it’s a simple proof that no valid coins were mined before that date. On another, it’s an ironic comment on the state of the standard economic system that bitcoin set out to replace. It’s also, for those fascinated by such things, one of the earliest clues to the identity of Satoshi Nakamoto...
http://bit.ly/2Hvu8SU
0 notes
Text
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
James Bridle is a writer working across technologies and disciplines and author of “The New Dark Age: Technology and the End of the Future.” His work can be found at http://jamesbridle.com. The following work will appear as an introduction to “The White Paper by Satoshi Nakamoto” to be published by Ignota Books.
For more on bitcoin’s 10th anniversary, check out our new interactive feature Bitcoin At 10.
————-
It’s difficult to know when humans first started securing or ‘encrypting’ messages to hide them from unwanted readers; the practice must, by human nature, be almost as old as written language, although examples are sparse. We know, for example, that Julius Caesar used a simple form of letter substitution to communicate with his generals, shifting each character three steps down the alphabet in order to scramble it.
The ancient Greeks, particularly the military-minded Spartans, used a device called a scytale, which allowed a hidden text to be read by wrapping a strip of parchment around a cylinder of a particular size so that the letters lined up in a particular order. Tales of the Greco-Persian Wars are full of secret messages, not least the story of Histiaeus, a commander who, according to Herodotus, shaved the head of his favorite slave and had it tattooed with a message urging revolution in the city of Miletus.
When the slave’s hair grew back he was dispatched to the city, with the instructions that the recipient should shave him once again and read the message there revealed.
Such extreme measures were taken due to the fear of government surveillance, a justification often cited today. The Persian king controlled the roadways, and had the power to examine any message – and messenger – that travelled on them. From the very beginning, cryptography has been both a military technology and a tool for undermining existing powers.
Cryptography’s value as a military tool is double-edged, of course.
Like other weapons, its effectiveness depends on the ability of one side to outgun the other. For a long time, this balance mostly held, with efforts by one side to crack the secrets of the other forming long-running and fascinating backstories to many conventional conflicts. It was an act of decryption that brought the United States into the First World War when British intelligence services decoded the infamous Zimmermann Telegram proposing an alliance between Germany and Mexico.
In the closing months of the war, the cracking of Germany’s ADFGVX cipher by French cryptanalysts enabled the Allies to stave off a final German offensive on Paris.
Cryptography was first mass-manufactured in the Second World War, in the form of the Third Reich’s Enigma machines, and then digitized in the form of the Colossus, the world’s first programmable electronic computer, developed to break the German military’s Lorenz cipher. The wild invention and ultimate success of the Bletchley codebreakers over their Nazi adversaries can be read as the first of many instances of the digital overcoming the physical; the Lorenz SZ42 was a massive, complex machine of rotating cogs and wheels which defied codebreakers for years.
By the end of the war, it was completely readable by an electronic machine. The secrecy around the Colossus itself meant that its existence had little influence on future computer design, but it marks the point at which cryptography changed radically in nature – because what is digital is ultimately distributable, although it would take the growth of the internet in the 1990s for this to become widely understood.
In 1991, a computer security researcher called Phil Zimmermann created a programme called Pretty Good Privacy (PGP), which enabled users of home computers to strongly encrypt email messages using a combination of numerous well-known algorithms. What turned PGP from another homemade software product into one of the most contentious artifacts of the decade wasn’t how it was made, but how it was distributed. Since the Second World War, nations had been forced to legally define cryptography as a weapon; like any other munition, cryptography was subject to something called the Arms Export Control Act.
At the time of PGP’s release, any cryptosystem which used keys – the strings of randomly generated numbers which secured hidden messages – longer than 40 bits required a licence for export.
PGP used keys which were 128 bits long and almost impossible to crack at the time, and this made it precisely the kind of technology that US authorities wanted to prevent falling into foreign hands. Zimmermann never intended to export PGP, but, fearing that it would be banned outright, he started distributing it to friends, saying, “I wanted to strengthen democracy, to ensure that Americans could continue to protect their privacy.”
Shortly after that, PGP found its way onto the internet and then abroad. In 1993, the US government started a formal investigation into Zimmermann – for exporting munitions without a license. As knowledge of the case spread, it became a flashpoint for early digital activists who insisted on the rights of everyone to protect their own secrets and their own private lives.
The freedoms and dangers of code became the subject of earnest debate, and in another foreshadowing of future digital style, of hacks, pranks and stunts. Zimmermann had the software’s source code printed as a hardback book, allowing anyone to purchase a copy and type up the software themselves.
As he was fond of pointing out, export of products commonly considered munitions – bombs, guns and planes – could be restricted, but books were protected by the First Amendment. Variants on the RSA algorithm – the 128-bit process at the heart of PGP – were printed on T-shirts bearing the message ‘This shirt is classified as a munition’. Some went further, having lines of code tattooed onto their arms and chests.
The crypto wars
The Crypto Wars, as they became known, galvanized a community around the notion of personal – rather than national – security, which tied into the utopian imagination of a new, more free, more equal and more just society developing in cyberspace.
Another development that prompted widespread public disquiet was the US government’s proposal for a chipset for mobile phones. The Clipper chip was designed by the NSA to provide encryption for users while allowing law enforcement to eavesdrop on communications – a situation that was ripe for abuse, either by corrupt officials or by skilled hackers.
Clipper chip via Wikimedia.
The idea that a government would deliberately weaken the protections available to its citizens made for an even more powerful and accessible argument for the individualists than the attack on PGP. By the late 1990s, Clipper was dead – and so was the case against Zimmermann. The hackers and privacy activists declared victory in the Crypto Wars.
Yet what’s often regarded as a victory for everyone against government overreach can also be read as a moment of terrifying breach: when the state’s most powerful weapons escaped government control and fell into the hands of anyone who wanted to use them. Today, thanks to the rise in digital communications, cryptography is everywhere, not least in banking systems, protecting the billions of electronic transactions that flow around the planet every day.
Even more than in the 1990s, the idea that anyone would deliberately make it easier for someone to steal money seems like an attack on the basic functions of society, and so it should come as no surprise that it’s a technology best known for – but by no means limited to – the distribution of currency that should be the focus of a new outbreak of the Crypto Wars, as well as the full flood of individualist, utopian thinking that accompanied the first round. There’s something about money that focuses the mind.
When Marco Polo first encountered paper money on his travels to China in the 13th century, he was astounded. In his Book of the Marvels of the World, he spends a great length of time explaining, and wondering at, the monetary system established by the Great Khan. Until recently, and as was still the case in Europe, the Chinese had used a range of value-bearing commodities to settle commerce and taxation: copper ingots, iron bars, gold coins, pearls, salt and the like.
In 1260, Kublai Khan decreed that instead, his subjects would use apparently valueless paper, printed and certified by a central mint, and, writes Polo, “the way it is wrought is such that you might say he has the secret of alchemy in perfection, and you would be right.” Through a carefully choreographed process of manufacture, design and official imprimatur, “all these pieces of paper are issued with as much solemnity and authority as if they were of pure gold or silver.”
The process was alchemical in the truest sense, as it did not merely transform material, but also elevated the Khan himself to even more unassailable heights of power: the only arbiter of finance. Those who refused to accept the new currency were punished with death, and all trade flowed through the state’s coffers. Like the Persian king before him, the Khan had realized that controlling traffic – in commerce and in information – was the way to situate oneself at the true heart of power.
True magic
The processing and accounting of money – fiat money, created by decree rather than having inherent value – is essentially the manipulation of symbols, and the gradual but ever-accelerating authority of capitalism, money’s belief system, tracks the development of symbol-manipulating technologies, from the double-entry bookkeeping of the European Renaissance to the development of databases and planet-spanning electronic networks; from physical technologies to virtual ones.
Money also involves the magical transformation of symbols into value. It requires belief to operate.
Around such belief systems other beliefs tend to gather, and the industrial quantities of belief required to breathe life into new systems of value tends to gives succor to any number of outlandish ideas, whether these be the divine right of kings, the supremacy of the nation state or the inviolable will of technology itself.
Money, then, is a belief system backed by state infrastructure which, for a long time, assured centralized power. But as computational technologies, long the sole province of the state, became less about asserting government power than asserting individual freedom – in other words, as the weapons forged in the crucible of the Second World War became increasingly available to the common citizen – it became clear to the veterans of the Crypto Wars how they might make other adjustments to ancient power dynamics.
The idea for digital money and virtual currencies had been floating around for some time before the Crypto Wars. Money has been
tending towards the virtual for some time, from the first ATMs and cards in the 1960s, to the spread of digital networks and connections between retailers and banks in the 1980s and 1990s. For anyone with a little technological foresight, it was easy to see which direction we were heading in.
For those concerned with privacy and individual sovereignty, it was a worrying development.
The first ATM via TIME
Digital money, significantly, has none of the advantages of cash; it can’t be stored and exchanged outside of the system of banks and third parties, such as credit card companies, which can regulate and impede its flow. To a cryptographer, or anyone who has imbibed cryptography’s lessons on the potential to separate oneself from overbearing powers, this arrangement looks like a kind of enslavement. So what would digital cash actually look like?
The first quality of digital cash is that it needs to be private, in the sense that no one other than the spender and receiver should be party to the transaction: no bank or security agency should know who is spending the money, who is receiving it, what it is for or at what time and place the exchange is taking place. Because no physical assets, such as notes or coins, are being exchanged, it should also be secure. The receiver should be able to verify they were paid and the spender that they had paid – a two-way receipt for the transaction.
In this way, digital cash would have all the privacy of physical cash, with the added benefit of the participants being able to prove that a transaction had actually taken place.
The opening shot
One of the earliest proponents of digital cash was an American computer scientist called David Chaum.
Chaum believed that both the privacy and the security problems of digital currencies could be solved by using cryptography: encoding messages between the two parties, the sender and the receiver, in such a way that nobody else can read them. Chaum’s solution to this problem involved both parties digitally signing the transaction with a private key, akin to an unforgeable and unguessable digital signature. In this way, both parties validate the transaction. In addition, they communicate through encrypted channels, so that nobody else can see that the transaction has taken place.
Chaum’s system worked, and was implemented by a number of companies and even one bank, but it never took off.
Chaum’s own company, DigiCash, went bankrupt in 1998 and there was little incentive to compete against the growing power of credit card companies. Chaum felt that people didn’t understand what they were losing as digital networks and the money that flowed across them became more centralized: “As the web grew, the average level of sophistication of users dropped. It was hard to explain the importance of privacy to them,” he said in 1999.
David Chaum via Elixxir project.
Yet some people, including those radicalized by the Crypto Wars of the early 1990s, did understand the value of privacy.
A group which came to be known as the Cypherpunks gathered first in San Francisco, and then online, with the intent of picking up from Chaum’s work the tools that could be used to disempower governments. From the very beginning, Chaum’s ideas about privacy and security had been tied to ideas about society and the way it was being changed by digitization.
“Computerisation is robbing individuals of the ability to monitor and control the ways information about them is used,” he wrote in 1985, foreseeing a Big Brother-like “dossier society” where everything was known about individuals but individuals knew little about the information held over them.
Yet Chaum was forced to partner with existing institutions to get DigiCash of the ground – and this was very far from the Cypherpunk dream. Eric Hughes, a Berkeley mathematician and one of the original Cypherpunks group, published ‘A Cypherpunk’s Manifesto’ in 1993, arguing that privacy was a requirement for an open society, and privacy on electronic networks could only be achieved through the use of cryptography.
Tim May, another member of the group and a former chief scientist at Intel, went further in the The Crypto Anarchist Manifesto:
“The State will, of course, try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be traded freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions.”
Throughout the 1990s and into the 2000s, the Cypherpunks elaborated on the principles that would bring their utopia of encryption into being, as well as the technical innovations required to make digital currency possible.
One of the biggest hurdles to doing so was the double-spending problem. Physical cash can only be spent once; when a banknote is handed over to a merchant, the buyer can’t at the same time use the same note at another shop around the corner. Virtual currencies face the problem that while encryption can guarantee that this specific piece of data is a form of money belonging to this specific person, it can’t say whether that data has been copied and is also in circulation elsewhere.
In other words, it can’t say whether or not someone is trying to spend the same coin twice at the same time. The need to have a central register to check each transaction was what forced David Chaum to partner with banks.
This necessitated routing all electronic transactions through credit card companies, and re-introduce dthe Cypherpunks’ worst enemies: loss of privacy and the need to trusts some hierarchical organization, a government, bank or corporation, with the authority to verify and, if necessary, roll back transactions.
The blockchain
The solution to the double-spending problem appeared quite suddenly in October 2008, with the publication of a paper on the The Cryptography Mailing List entitled “Bitcoin: “A Peer-to-Peer Electronic Cash System.” Citing several forerunners in the field, the author of the paper, the previously unknown Satoshi Nakamoto, proposed one key innovation which solved the double-spending problem while preserving anonymity and preventing the need for trusting third parties.
This was called the ‘blockchain’: a distributed ledger, or record of transactions, which would be maintained by everyone participating in the system. It’s called the blockchain because groups of transactions are gathered together into ‘blocks’ as they occur, and as each block is turned out it is added to the ‘chain’ of all transactions. That’s it. It’s simply a list of things that happened.
If everyone can see every transaction, then there is no need to hand over control to banks or governments, and if everyone follows the encryption practices of the Cypherpunks, there is no way to know who is spending the money.
Of course, if everyone has a copy of this ledger, we need to know it hasn’t been forged or tampered with in any way. So in order to extend the blockchain, in other words to write in the ledger, a certain amount of computational ‘work’ has to be done: the computer doing the writing has to solve a particularly complex mathematical problem.
Bloomberg Magazine, 2015
The fact that it’s relatively easy for everyone else’s computers to check if this problem really was solved makes it very difficult – in fact, practically impossible – for anyone to create a fake version of the ledger. In a particularly clever twist, participants are incentivized to help maintain the ledger by receiving a small number of bitcoins when they do solve the mathematical problem. This is where the notional value of Bitcoin comes from: someone has to put in an amount of time and energy to produce it, which is why this process is known as ‘mining’.
Over time, more and more coins are produced, to an eventual total of 21 million sometime in or around 2140. Satoshi’s paper had the good fortune to appear at a particular time. Encoded into the very first block on the Bitcoin chain is a timestamp, the kind of timestamp more familiar from ransom demands: a proof of life.
The phrase embedded forever into the beginning of the blockchain is ‘The Times 03/Jan/2009 Chancellor on brink of second bailout for banks,’ a reference to the front page headline of The Times newspaper on that date.
On one level, it’s a simple proof that no valid coins were mined before that date. On another, it’s an ironic comment on the state of the standard economic system that bitcoin set out to replace. It’s also, for those fascinated by such things, one of the earliest clues to the identity of Satoshi Nakamoto...
http://bit.ly/2Hvu8SU
0 notes
Text
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
James Bridle is a writer working across technologies and disciplines and author of “The New Dark Age: Technology and the End of the Future.” His work can be found at http://jamesbridle.com. The following work will appear as an introduction to “The White Paper by Satoshi Nakamoto” to be published by Ignota Books.
For more on bitcoin’s 10th anniversary, check out our new interactive feature Bitcoin At 10.
————-
It’s difficult to know when humans first started securing or ‘encrypting’ messages to hide them from unwanted readers; the practice must, by human nature, be almost as old as written language, although examples are sparse. We know, for example, that Julius Caesar used a simple form of letter substitution to communicate with his generals, shifting each character three steps down the alphabet in order to scramble it.
The ancient Greeks, particularly the military-minded Spartans, used a device called a scytale, which allowed a hidden text to be read by wrapping a strip of parchment around a cylinder of a particular size so that the letters lined up in a particular order. Tales of the Greco-Persian Wars are full of secret messages, not least the story of Histiaeus, a commander who, according to Herodotus, shaved the head of his favorite slave and had it tattooed with a message urging revolution in the city of Miletus.
When the slave’s hair grew back he was dispatched to the city, with the instructions that the recipient should shave him once again and read the message there revealed.
Such extreme measures were taken due to the fear of government surveillance, a justification often cited today. The Persian king controlled the roadways, and had the power to examine any message – and messenger – that travelled on them. From the very beginning, cryptography has been both a military technology and a tool for undermining existing powers.
Cryptography’s value as a military tool is double-edged, of course.
Like other weapons, its effectiveness depends on the ability of one side to outgun the other. For a long time, this balance mostly held, with efforts by one side to crack the secrets of the other forming long-running and fascinating backstories to many conventional conflicts. It was an act of decryption that brought the United States into the First World War when British intelligence services decoded the infamous Zimmermann Telegram proposing an alliance between Germany and Mexico.
In the closing months of the war, the cracking of Germany’s ADFGVX cipher by French cryptanalysts enabled the Allies to stave off a final German offensive on Paris.
Cryptography was first mass-manufactured in the Second World War, in the form of the Third Reich’s Enigma machines, and then digitized in the form of the Colossus, the world’s first programmable electronic computer, developed to break the German military’s Lorenz cipher. The wild invention and ultimate success of the Bletchley codebreakers over their Nazi adversaries can be read as the first of many instances of the digital overcoming the physical; the Lorenz SZ42 was a massive, complex machine of rotating cogs and wheels which defied codebreakers for years.
By the end of the war, it was completely readable by an electronic machine. The secrecy around the Colossus itself meant that its existence had little influence on future computer design, but it marks the point at which cryptography changed radically in nature – because what is digital is ultimately distributable, although it would take the growth of the internet in the 1990s for this to become widely understood.
In 1991, a computer security researcher called Phil Zimmermann created a programme called Pretty Good Privacy (PGP), which enabled users of home computers to strongly encrypt email messages using a combination of numerous well-known algorithms. What turned PGP from another homemade software product into one of the most contentious artifacts of the decade wasn’t how it was made, but how it was distributed. Since the Second World War, nations had been forced to legally define cryptography as a weapon; like any other munition, cryptography was subject to something called the Arms Export Control Act.
At the time of PGP’s release, any cryptosystem which used keys – the strings of randomly generated numbers which secured hidden messages – longer than 40 bits required a licence for export.
PGP used keys which were 128 bits long and almost impossible to crack at the time, and this made it precisely the kind of technology that US authorities wanted to prevent falling into foreign hands. Zimmermann never intended to export PGP, but, fearing that it would be banned outright, he started distributing it to friends, saying, “I wanted to strengthen democracy, to ensure that Americans could continue to protect their privacy.”
Shortly after that, PGP found its way onto the internet and then abroad. In 1993, the US government started a formal investigation into Zimmermann – for exporting munitions without a license. As knowledge of the case spread, it became a flashpoint for early digital activists who insisted on the rights of everyone to protect their own secrets and their own private lives.
The freedoms and dangers of code became the subject of earnest debate, and in another foreshadowing of future digital style, of hacks, pranks and stunts. Zimmermann had the software’s source code printed as a hardback book, allowing anyone to purchase a copy and type up the software themselves.
As he was fond of pointing out, export of products commonly considered munitions – bombs, guns and planes – could be restricted, but books were protected by the First Amendment. Variants on the RSA algorithm – the 128-bit process at the heart of PGP – were printed on T-shirts bearing the message ‘This shirt is classified as a munition’. Some went further, having lines of code tattooed onto their arms and chests.
The crypto wars
The Crypto Wars, as they became known, galvanized a community around the notion of personal – rather than national – security, which tied into the utopian imagination of a new, more free, more equal and more just society developing in cyberspace.
Another development that prompted widespread public disquiet was the US government’s proposal for a chipset for mobile phones. The Clipper chip was designed by the NSA to provide encryption for users while allowing law enforcement to eavesdrop on communications – a situation that was ripe for abuse, either by corrupt officials or by skilled hackers.
Clipper chip via Wikimedia.
The idea that a government would deliberately weaken the protections available to its citizens made for an even more powerful and accessible argument for the individualists than the attack on PGP. By the late 1990s, Clipper was dead – and so was the case against Zimmermann. The hackers and privacy activists declared victory in the Crypto Wars.
Yet what’s often regarded as a victory for everyone against government overreach can also be read as a moment of terrifying breach: when the state’s most powerful weapons escaped government control and fell into the hands of anyone who wanted to use them. Today, thanks to the rise in digital communications, cryptography is everywhere, not least in banking systems, protecting the billions of electronic transactions that flow around the planet every day.
Even more than in the 1990s, the idea that anyone would deliberately make it easier for someone to steal money seems like an attack on the basic functions of society, and so it should come as no surprise that it’s a technology best known for – but by no means limited to – the distribution of currency that should be the focus of a new outbreak of the Crypto Wars, as well as the full flood of individualist, utopian thinking that accompanied the first round. There’s something about money that focuses the mind.
When Marco Polo first encountered paper money on his travels to China in the 13th century, he was astounded. In his Book of the Marvels of the World, he spends a great length of time explaining, and wondering at, the monetary system established by the Great Khan. Until recently, and as was still the case in Europe, the Chinese had used a range of value-bearing commodities to settle commerce and taxation: copper ingots, iron bars, gold coins, pearls, salt and the like.
In 1260, Kublai Khan decreed that instead, his subjects would use apparently valueless paper, printed and certified by a central mint, and, writes Polo, “the way it is wrought is such that you might say he has the secret of alchemy in perfection, and you would be right.” Through a carefully choreographed process of manufacture, design and official imprimatur, “all these pieces of paper are issued with as much solemnity and authority as if they were of pure gold or silver.”
The process was alchemical in the truest sense, as it did not merely transform material, but also elevated the Khan himself to even more unassailable heights of power: the only arbiter of finance. Those who refused to accept the new currency were punished with death, and all trade flowed through the state’s coffers. Like the Persian king before him, the Khan had realized that controlling traffic – in commerce and in information – was the way to situate oneself at the true heart of power.
True magic
The processing and accounting of money – fiat money, created by decree rather than having inherent value – is essentially the manipulation of symbols, and the gradual but ever-accelerating authority of capitalism, money’s belief system, tracks the development of symbol-manipulating technologies, from the double-entry bookkeeping of the European Renaissance to the development of databases and planet-spanning electronic networks; from physical technologies to virtual ones.
Money also involves the magical transformation of symbols into value. It requires belief to operate.
Around such belief systems other beliefs tend to gather, and the industrial quantities of belief required to breathe life into new systems of value tends to gives succor to any number of outlandish ideas, whether these be the divine right of kings, the supremacy of the nation state or the inviolable will of technology itself.
Money, then, is a belief system backed by state infrastructure which, for a long time, assured centralized power. But as computational technologies, long the sole province of the state, became less about asserting government power than asserting individual freedom – in other words, as the weapons forged in the crucible of the Second World War became increasingly available to the common citizen – it became clear to the veterans of the Crypto Wars how they might make other adjustments to ancient power dynamics.
The idea for digital money and virtual currencies had been floating around for some time before the Crypto Wars. Money has been
tending towards the virtual for some time, from the first ATMs and cards in the 1960s, to the spread of digital networks and connections between retailers and banks in the 1980s and 1990s. For anyone with a little technological foresight, it was easy to see which direction we were heading in.
For those concerned with privacy and individual sovereignty, it was a worrying development.
The first ATM via TIME
Digital money, significantly, has none of the advantages of cash; it can’t be stored and exchanged outside of the system of banks and third parties, such as credit card companies, which can regulate and impede its flow. To a cryptographer, or anyone who has imbibed cryptography’s lessons on the potential to separate oneself from overbearing powers, this arrangement looks like a kind of enslavement. So what would digital cash actually look like?
The first quality of digital cash is that it needs to be private, in the sense that no one other than the spender and receiver should be party to the transaction: no bank or security agency should know who is spending the money, who is receiving it, what it is for or at what time and place the exchange is taking place. Because no physical assets, such as notes or coins, are being exchanged, it should also be secure. The receiver should be able to verify they were paid and the spender that they had paid – a two-way receipt for the transaction.
In this way, digital cash would have all the privacy of physical cash, with the added benefit of the participants being able to prove that a transaction had actually taken place.
The opening shot
One of the earliest proponents of digital cash was an American computer scientist called David Chaum.
Chaum believed that both the privacy and the security problems of digital currencies could be solved by using cryptography: encoding messages between the two parties, the sender and the receiver, in such a way that nobody else can read them. Chaum’s solution to this problem involved both parties digitally signing the transaction with a private key, akin to an unforgeable and unguessable digital signature. In this way, both parties validate the transaction. In addition, they communicate through encrypted channels, so that nobody else can see that the transaction has taken place.
Chaum’s system worked, and was implemented by a number of companies and even one bank, but it never took off.
Chaum’s own company, DigiCash, went bankrupt in 1998 and there was little incentive to compete against the growing power of credit card companies. Chaum felt that people didn’t understand what they were losing as digital networks and the money that flowed across them became more centralized: “As the web grew, the average level of sophistication of users dropped. It was hard to explain the importance of privacy to them,” he said in 1999.
David Chaum via Elixxir project.
Yet some people, including those radicalized by the Crypto Wars of the early 1990s, did understand the value of privacy.
A group which came to be known as the Cypherpunks gathered first in San Francisco, and then online, with the intent of picking up from Chaum’s work the tools that could be used to disempower governments. From the very beginning, Chaum’s ideas about privacy and security had been tied to ideas about society and the way it was being changed by digitization.
“Computerisation is robbing individuals of the ability to monitor and control the ways information about them is used,” he wrote in 1985, foreseeing a Big Brother-like “dossier society” where everything was known about individuals but individuals knew little about the information held over them.
Yet Chaum was forced to partner with existing institutions to get DigiCash of the ground – and this was very far from the Cypherpunk dream. Eric Hughes, a Berkeley mathematician and one of the original Cypherpunks group, published ‘A Cypherpunk’s Manifesto’ in 1993, arguing that privacy was a requirement for an open society, and privacy on electronic networks could only be achieved through the use of cryptography.
Tim May, another member of the group and a former chief scientist at Intel, went further in the The Crypto Anarchist Manifesto:
“The State will, of course, try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be traded freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions.”
Throughout the 1990s and into the 2000s, the Cypherpunks elaborated on the principles that would bring their utopia of encryption into being, as well as the technical innovations required to make digital currency possible.
One of the biggest hurdles to doing so was the double-spending problem. Physical cash can only be spent once; when a banknote is handed over to a merchant, the buyer can’t at the same time use the same note at another shop around the corner. Virtual currencies face the problem that while encryption can guarantee that this specific piece of data is a form of money belonging to this specific person, it can’t say whether that data has been copied and is also in circulation elsewhere.
In other words, it can’t say whether or not someone is trying to spend the same coin twice at the same time. The need to have a central register to check each transaction was what forced David Chaum to partner with banks.
This necessitated routing all electronic transactions through credit card companies, and re-introduce dthe Cypherpunks’ worst enemies: loss of privacy and the need to trusts some hierarchical organization, a government, bank or corporation, with the authority to verify and, if necessary, roll back transactions.
The blockchain
The solution to the double-spending problem appeared quite suddenly in October 2008, with the publication of a paper on the The Cryptography Mailing List entitled “Bitcoin: “A Peer-to-Peer Electronic Cash System.” Citing several forerunners in the field, the author of the paper, the previously unknown Satoshi Nakamoto, proposed one key innovation which solved the double-spending problem while preserving anonymity and preventing the need for trusting third parties.
This was called the ‘blockchain’: a distributed ledger, or record of transactions, which would be maintained by everyone participating in the system. It’s called the blockchain because groups of transactions are gathered together into ‘blocks’ as they occur, and as each block is turned out it is added to the ‘chain’ of all transactions. That’s it. It’s simply a list of things that happened.
If everyone can see every transaction, then there is no need to hand over control to banks or governments, and if everyone follows the encryption practices of the Cypherpunks, there is no way to know who is spending the money.
Of course, if everyone has a copy of this ledger, we need to know it hasn’t been forged or tampered with in any way. So in order to extend the blockchain, in other words to write in the ledger, a certain amount of computational ‘work’ has to be done: the computer doing the writing has to solve a particularly complex mathematical problem.
Bloomberg Magazine, 2015
The fact that it’s relatively easy for everyone else’s computers to check if this problem really was solved makes it very difficult – in fact, practically impossible – for anyone to create a fake version of the ledger. In a particularly clever twist, participants are incentivized to help maintain the ledger by receiving a small number of bitcoins when they do solve the mathematical problem. This is where the notional value of Bitcoin comes from: someone has to put in an amount of time and energy to produce it, which is why this process is known as ‘mining’.
Over time, more and more coins are produced, to an eventual total of 21 million sometime in or around 2140. Satoshi’s paper had the good fortune to appear at a particular time. Encoded into the very first block on the Bitcoin chain is a timestamp, the kind of timestamp more familiar from ransom demands: a proof of life.
The phrase embedded forever into the beginning of the blockchain is ‘The Times 03/Jan/2009 Chancellor on brink of second bailout for banks,’ a reference to the front page headline of The Times newspaper on that date.
On one level, it’s a simple proof that no valid coins were mined before that date. On another, it’s an ironic comment on the state of the standard economic system that bitcoin set out to replace. It’s also, for those fascinated by such things, one of the earliest clues to the identity of Satoshi Nakamoto...
http://bit.ly/2Hvu8SU
0 notes
Text
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
Free Markets Don’t Create Free People: Bitcoin’s Tech Success Masks Its Failure
James Bridle is a writer working across technologies and disciplines and author of “The New Dark Age: Technology and the End of the Future.” His work can be found at http://jamesbridle.com. The following work will appear as an introduction to “The White Paper by Satoshi Nakamoto” to be published by Ignota Books.
For more on bitcoin’s 10th anniversary, check out our new interactive feature Bitcoin At 10.
————-
It’s difficult to know when humans first started securing or ‘encrypting’ messages to hide them from unwanted readers; the practice must, by human nature, be almost as old as written language, although examples are sparse. We know, for example, that Julius Caesar used a simple form of letter substitution to communicate with his generals, shifting each character three steps down the alphabet in order to scramble it.
The ancient Greeks, particularly the military-minded Spartans, used a device called a scytale, which allowed a hidden text to be read by wrapping a strip of parchment around a cylinder of a particular size so that the letters lined up in a particular order. Tales of the Greco-Persian Wars are full of secret messages, not least the story of Histiaeus, a commander who, according to Herodotus, shaved the head of his favorite slave and had it tattooed with a message urging revolution in the city of Miletus.
When the slave’s hair grew back he was dispatched to the city, with the instructions that the recipient should shave him once again and read the message there revealed.
Such extreme measures were taken due to the fear of government surveillance, a justification often cited today. The Persian king controlled the roadways, and had the power to examine any message – and messenger – that travelled on them. From the very beginning, cryptography has been both a military technology and a tool for undermining existing powers.
Cryptography’s value as a military tool is double-edged, of course.
Like other weapons, its effectiveness depends on the ability of one side to outgun the other. For a long time, this balance mostly held, with efforts by one side to crack the secrets of the other forming long-running and fascinating backstories to many conventional conflicts. It was an act of decryption that brought the United States into the First World War when British intelligence services decoded the infamous Zimmermann Telegram proposing an alliance between Germany and Mexico.
In the closing months of the war, the cracking of Germany’s ADFGVX cipher by French cryptanalysts enabled the Allies to stave off a final German offensive on Paris.
Cryptography was first mass-manufactured in the Second World War, in the form of the Third Reich’s Enigma machines, and then digitized in the form of the Colossus, the world’s first programmable electronic computer, developed to break the German military’s Lorenz cipher. The wild invention and ultimate success of the Bletchley codebreakers over their Nazi adversaries can be read as the first of many instances of the digital overcoming the physical; the Lorenz SZ42 was a massive, complex machine of rotating cogs and wheels which defied codebreakers for years.
By the end of the war, it was completely readable by an electronic machine. The secrecy around the Colossus itself meant that its existence had little influence on future computer design, but it marks the point at which cryptography changed radically in nature – because what is digital is ultimately distributable, although it would take the growth of the internet in the 1990s for this to become widely understood.
In 1991, a computer security researcher called Phil Zimmermann created a programme called Pretty Good Privacy (PGP), which enabled users of home computers to strongly encrypt email messages using a combination of numerous well-known algorithms. What turned PGP from another homemade software product into one of the most contentious artifacts of the decade wasn’t how it was made, but how it was distributed. Since the Second World War, nations had been forced to legally define cryptography as a weapon; like any other munition, cryptography was subject to something called the Arms Export Control Act.
At the time of PGP’s release, any cryptosystem which used keys – the strings of randomly generated numbers which secured hidden messages – longer than 40 bits required a licence for export.
PGP used keys which were 128 bits long and almost impossible to crack at the time, and this made it precisely the kind of technology that US authorities wanted to prevent falling into foreign hands. Zimmermann never intended to export PGP, but, fearing that it would be banned outright, he started distributing it to friends, saying, “I wanted to strengthen democracy, to ensure that Americans could continue to protect their privacy.”
Shortly after that, PGP found its way onto the internet and then abroad. In 1993, the US government started a formal investigation into Zimmermann – for exporting munitions without a license. As knowledge of the case spread, it became a flashpoint for early digital activists who insisted on the rights of everyone to protect their own secrets and their own private lives.
The freedoms and dangers of code became the subject of earnest debate, and in another foreshadowing of future digital style, of hacks, pranks and stunts. Zimmermann had the software’s source code printed as a hardback book, allowing anyone to purchase a copy and type up the software themselves.
As he was fond of pointing out, export of products commonly considered munitions – bombs, guns and planes – could be restricted, but books were protected by the First Amendment. Variants on the RSA algorithm – the 128-bit process at the heart of PGP – were printed on T-shirts bearing the message ‘This shirt is classified as a munition’. Some went further, having lines of code tattooed onto their arms and chests.
The crypto wars
The Crypto Wars, as they became known, galvanized a community around the notion of personal – rather than national – security, which tied into the utopian imagination of a new, more free, more equal and more just society developing in cyberspace.
Another development that prompted widespread public disquiet was the US government’s proposal for a chipset for mobile phones. The Clipper chip was designed by the NSA to provide encryption for users while allowing law enforcement to eavesdrop on communications – a situation that was ripe for abuse, either by corrupt officials or by skilled hackers.
Clipper chip via Wikimedia.
The idea that a government would deliberately weaken the protections available to its citizens made for an even more powerful and accessible argument for the individualists than the attack on PGP. By the late 1990s, Clipper was dead – and so was the case against Zimmermann. The hackers and privacy activists declared victory in the Crypto Wars.
Yet what’s often regarded as a victory for everyone against government overreach can also be read as a moment of terrifying breach: when the state’s most powerful weapons escaped government control and fell into the hands of anyone who wanted to use them. Today, thanks to the rise in digital communications, cryptography is everywhere, not least in banking systems, protecting the billions of electronic transactions that flow around the planet every day.
Even more than in the 1990s, the idea that anyone would deliberately make it easier for someone to steal money seems like an attack on the basic functions of society, and so it should come as no surprise that it’s a technology best known for – but by no means limited to – the distribution of currency that should be the focus of a new outbreak of the Crypto Wars, as well as the full flood of individualist, utopian thinking that accompanied the first round. There’s something about money that focuses the mind.
When Marco Polo first encountered paper money on his travels to China in the 13th century, he was astounded. In his Book of the Marvels of the World, he spends a great length of time explaining, and wondering at, the monetary system established by the Great Khan. Until recently, and as was still the case in Europe, the Chinese had used a range of value-bearing commodities to settle commerce and taxation: copper ingots, iron bars, gold coins, pearls, salt and the like.
In 1260, Kublai Khan decreed that instead, his subjects would use apparently valueless paper, printed and certified by a central mint, and, writes Polo, “the way it is wrought is such that you might say he has the secret of alchemy in perfection, and you would be right.” Through a carefully choreographed process of manufacture, design and official imprimatur, “all these pieces of paper are issued with as much solemnity and authority as if they were of pure gold or silver.”
The process was alchemical in the truest sense, as it did not merely transform material, but also elevated the Khan himself to even more unassailable heights of power: the only arbiter of finance. Those who refused to accept the new currency were punished with death, and all trade flowed through the state’s coffers. Like the Persian king before him, the Khan had realized that controlling traffic – in commerce and in information – was the way to situate oneself at the true heart of power.
True magic
The processing and accounting of money – fiat money, created by decree rather than having inherent value – is essentially the manipulation of symbols, and the gradual but ever-accelerating authority of capitalism, money’s belief system, tracks the development of symbol-manipulating technologies, from the double-entry bookkeeping of the European Renaissance to the development of databases and planet-spanning electronic networks; from physical technologies to virtual ones.
Money also involves the magical transformation of symbols into value. It requires belief to operate.
Around such belief systems other beliefs tend to gather, and the industrial quantities of belief required to breathe life into new systems of value tends to gives succor to any number of outlandish ideas, whether these be the divine right of kings, the supremacy of the nation state or the inviolable will of technology itself.
Money, then, is a belief system backed by state infrastructure which, for a long time, assured centralized power. But as computational technologies, long the sole province of the state, became less about asserting government power than asserting individual freedom – in other words, as the weapons forged in the crucible of the Second World War became increasingly available to the common citizen – it became clear to the veterans of the Crypto Wars how they might make other adjustments to ancient power dynamics.
The idea for digital money and virtual currencies had been floating around for some time before the Crypto Wars. Money has been
tending towards the virtual for some time, from the first ATMs and cards in the 1960s, to the spread of digital networks and connections between retailers and banks in the 1980s and 1990s. For anyone with a little technological foresight, it was easy to see which direction we were heading in.
For those concerned with privacy and individual sovereignty, it was a worrying development.
The first ATM via TIME
Digital money, significantly, has none of the advantages of cash; it can’t be stored and exchanged outside of the system of banks and third parties, such as credit card companies, which can regulate and impede its flow. To a cryptographer, or anyone who has imbibed cryptography’s lessons on the potential to separate oneself from overbearing powers, this arrangement looks like a kind of enslavement. So what would digital cash actually look like?
The first quality of digital cash is that it needs to be private, in the sense that no one other than the spender and receiver should be party to the transaction: no bank or security agency should know who is spending the money, who is receiving it, what it is for or at what time and place the exchange is taking place. Because no physical assets, such as notes or coins, are being exchanged, it should also be secure. The receiver should be able to verify they were paid and the spender that they had paid – a two-way receipt for the transaction.
In this way, digital cash would have all the privacy of physical cash, with the added benefit of the participants being able to prove that a transaction had actually taken place.
The opening shot
One of the earliest proponents of digital cash was an American computer scientist called David Chaum.
Chaum believed that both the privacy and the security problems of digital currencies could be solved by using cryptography: encoding messages between the two parties, the sender and the receiver, in such a way that nobody else can read them. Chaum’s solution to this problem involved both parties digitally signing the transaction with a private key, akin to an unforgeable and unguessable digital signature. In this way, both parties validate the transaction. In addition, they communicate through encrypted channels, so that nobody else can see that the transaction has taken place.
Chaum’s system worked, and was implemented by a number of companies and even one bank, but it never took off.
Chaum’s own company, DigiCash, went bankrupt in 1998 and there was little incentive to compete against the growing power of credit card companies. Chaum felt that people didn’t understand what they were losing as digital networks and the money that flowed across them became more centralized: “As the web grew, the average level of sophistication of users dropped. It was hard to explain the importance of privacy to them,” he said in 1999.
David Chaum via Elixxir project.
Yet some people, including those radicalized by the Crypto Wars of the early 1990s, did understand the value of privacy.
A group which came to be known as the Cypherpunks gathered first in San Francisco, and then online, with the intent of picking up from Chaum’s work the tools that could be used to disempower governments. From the very beginning, Chaum’s ideas about privacy and security had been tied to ideas about society and the way it was being changed by digitization.
“Computerisation is robbing individuals of the ability to monitor and control the ways information about them is used,” he wrote in 1985, foreseeing a Big Brother-like “dossier society” where everything was known about individuals but individuals knew little about the information held over them.
Yet Chaum was forced to partner with existing institutions to get DigiCash of the ground – and this was very far from the Cypherpunk dream. Eric Hughes, a Berkeley mathematician and one of the original Cypherpunks group, published ‘A Cypherpunk’s Manifesto’ in 1993, arguing that privacy was a requirement for an open society, and privacy on electronic networks could only be achieved through the use of cryptography.
Tim May, another member of the group and a former chief scientist at Intel, went further in the The Crypto Anarchist Manifesto:
“The State will, of course, try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be traded freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions.”
Throughout the 1990s and into the 2000s, the Cypherpunks elaborated on the principles that would bring their utopia of encryption into being, as well as the technical innovations required to make digital currency possible.
One of the biggest hurdles to doing so was the double-spending problem. Physical cash can only be spent once; when a banknote is handed over to a merchant, the buyer can’t at the same time use the same note at another shop around the corner. Virtual currencies face the problem that while encryption can guarantee that this specific piece of data is a form of money belonging to this specific person, it can’t say whether that data has been copied and is also in circulation elsewhere.
In other words, it can’t say whether or not someone is trying to spend the same coin twice at the same time. The need to have a central register to check each transaction was what forced David Chaum to partner with banks.
This necessitated routing all electronic transactions through credit card companies, and re-introduce dthe Cypherpunks’ worst enemies: loss of privacy and the need to trusts some hierarchical organization, a government, bank or corporation, with the authority to verify and, if necessary, roll back transactions.
The blockchain
The solution to the double-spending problem appeared quite suddenly in October 2008, with the publication of a paper on the The Cryptography Mailing List entitled “Bitcoin: “A Peer-to-Peer Electronic Cash System.” Citing several forerunners in the field, the author of the paper, the previously unknown Satoshi Nakamoto, proposed one key innovation which solved the double-spending problem while preserving anonymity and preventing the need for trusting third parties.
This was called the ‘blockchain’: a distributed ledger, or record of transactions, which would be maintained by everyone participating in the system. It’s called the blockchain because groups of transactions are gathered together into ‘blocks’ as they occur, and as each block is turned out it is added to the ‘chain’ of all transactions. That’s it. It’s simply a list of things that happened.
If everyone can see every transaction, then there is no need to hand over control to banks or governments, and if everyone follows the encryption practices of the Cypherpunks, there is no way to know who is spending the money.
Of course, if everyone has a copy of this ledger, we need to know it hasn’t been forged or tampered with in any way. So in order to extend the blockchain, in other words to write in the ledger, a certain amount of computational ‘work’ has to be done: the computer doing the writing has to solve a particularly complex mathematical problem.
Bloomberg Magazine, 2015
The fact that it’s relatively easy for everyone else’s computers to check if this problem really was solved makes it very difficult – in fact, practically impossible – for anyone to create a fake version of the ledger. In a particularly clever twist, participants are incentivized to help maintain the ledger by receiving a small number of bitcoins when they do solve the mathematical problem. This is where the notional value of Bitcoin comes from: someone has to put in an amount of time and energy to produce it, which is why this process is known as ‘mining’.
Over time, more and more coins are produced, to an eventual total of 21 million sometime in or around 2140. Satoshi’s paper had the good fortune to appear at a particular time. Encoded into the very first block on the Bitcoin chain is a timestamp, the kind of timestamp more familiar from ransom demands: a proof of life.
The phrase embedded forever into the beginning of the blockchain is ‘The Times 03/Jan/2009 Chancellor on brink of second bailout for banks,’ a reference to the front page headline of The Times newspaper on that date.
On one level, it’s a simple proof that no valid coins were mined before that date. On another, it’s an ironic comment on the state of the standard economic system that bitcoin set out to replace. It’s also, for those fascinated by such things, one of the earliest clues to the identity of Satoshi Nakamoto...
http://bit.ly/2Hvu8SU
0 notes